Bra podcast
Sveriges mest populära poddar
Overview
For our 199th episode Andrei looks at Fuzzing Configurations of Program Options
plus we discuss Google’s findings on the io_uring kernel subsystem and we look
at vulnerability fixes for Netatalk, Jupyter Core, Vim, SSSD, GNU binutils, GLib
and more.
This week in Ubuntu Security Updates
53 unique CVEs addressed
[USN-6145-1] Sysstat vulnerabilities (00:55)
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- system performance tools - integer overflow leading to possible buffer overflow - original fix was incomplete so a second CVE was issued
[USN-6146-1] Netatalk vulnerabilities (01:22)
- 9 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- Implementation of the Apple Filing Protocol - allows a Ubuntu server to share files with macOS clients - similar to Samba for Windows
- Lots of different buffer overflows - some / most disclosed via ZDI
- Almost all due to missing length checks on the input data - some OOB write, others OOB read - sadly there is no AppArmor profile for netatalk but it would be interesting to try and create one
[USN-6147-1] SpiderMonkey vulnerability (02:21)
- 1 CVEs addressed in Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- Latest release of mozjs-102.12.0 (Mozilla’s SpiderMonkey JS engine)
- Used by gnome-shell etc
- Upstream mozilla describes this issue as ‘memory safety bugs’
[USN-6149-1] Linux kernel vulnerabilities (02:52)
- 6 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- 4.4 based kernel (Xenial GA kernel)
- All interesting CVEs discussed last week - [USN-6130-1] Linux kernel vulnerabilities in Episode 198
- OOB read in the USB handling code for Broadcom FullMAC USB WiFi driver
- KVM mishandling of control registers for nested guest VMs
- OOB write in network queuing scheduler - able to be triggered though an unprivileged user namespace (again)
- race condition -> UAF -> privesc in netfilter
[USN-6150-1, USN-6162-1] Linux kernel vulnerabilities (03:55)
- 5 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- 5.15 Raspi + Intel-IoTG 22.04 LTS,
- 5.4 Raspi + Intel-IoTG 20.04 LTS
[USN-6151-1] Linux kernel (Xilinx ZynqMP) vulnerabilities (04:13)
- 4 CVEs addressed in Focal (20.04 LTS)
- 5.4
[USN-6152-1] Linux kernel (GKE) regression (04:21)
- Affecting Focal (20.04 LTS), Jammy (22.04 LTS)
- 5.15 - NFS cache issue causing a severe degradation in performance under certain conditions
[USN-6153-1] Jupyter Core vulnerability (04:42)
- 1 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- Executed untrusted files from current working directory - possible RCE - would unconditionally prepend the current working dir to the search path
[USN-6154-1] Vim vulnerabilities (04:58)
- 3 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- Moar vim CVEs
- Seems we talk about vim every month or so lately
- Only a few CVEs per year until 2021 - then 20, 113 for 2022, so far only 15 for 2023 - is this the sign that the rate of vim CVEs are decreasing?
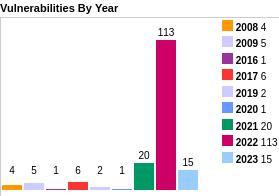
Figure 1: Vulnerabilities by year in vim from https://www.cvedetails.com/product/14270/VIM-VIM.html?vendor_id=8218
[USN-6155-1] Requests vulnerability (05:56)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- Python requests library - leaked Proxy-Authorization headers to the destination server when redirected by a HTTPS endpoint
[USN-6156-1] SSSD vulnerability (06:11)
- 1 CVEs addressed in Focal (20.04 LTS)
- Failed to sanitise certificate attributes before issuing an LDAP search -
ie. a certificate may contain parenthesis in say the
Subject DNfield - this would then be used directly in the query and would be interpreted as parameters in the LDAP query - could then allow a malicious client to provide a crafted certificate which performs arbitrary LDAP queries etc - such that when used in conjunction with FreeIPA they could elevate their privileges
[USN-6148-1] SNI Proxy vulnerability (06:54)
- 1 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- Buffer overflow when handling a crafted HTTP packet that specifies an IPv6 address longer than the maximum possible - since parses it into a fixed size buffer
[USN-6157-1] GlusterFS vulnerability
- 1 CVEs addressed in Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- Stack buffer overread - generally protected by stack protector on Ubuntu - crash -> DoS
[USN-6143-2] Firefox regressions (07:25)
- 4 CVEs addressed in Focal (20.04 LTS)
- 114.0.1 - crash on startup if on disk metadata is corrupted / invalid - fixed to just indicate an error occurred and continue without the data
[USN-6158-1] Node Fetch vulnerability (07:45)
- 1 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- If redirected to another site, would leak the cookie of the originating site to the other - violation of same origin policy
[USN-6159-1] Tornado vulnerability (07:59)
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Lunar (23.04)
- Open redirect - allows an attacker to craft a URL to a site that when visited will redirect the user to a different arbitrary site - can then be used to phish the user
[USN-6160-1] GNU binutils vulnerability (08:27)
- 1 CVEs addressed in Focal (20.04 LTS)
- Heap based buffer overflow when reading certain debugging information - could then possibly get code execution - requires the user to run objdump or similar on an attacker controlled binary - in general binutils is expected to only be run on trusted inputs - so if you are using objdump etc for reverse engineering arbitrary binaries, should do this in an isolated environment - VM
[USN-6161-1] .NET vulnerabilities (09:02)
- 5 CVEs addressed in Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- Latest .NET point releases from Microsoft for .NET 6 and 7 fixing various issues in the language runtime (not a lot of details provided by MS on these)
[USN-6164-1] c-ares vulnerabilities (09:24)
- 2 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- library for async DNS lookups - used by apt-cacher-ng, frr, wireshark, sssd and more
- Buffer underflow when looking up crafted IPv6 addresses - appears to be able to be tricked into writing infront of an allocated buffer - memory corruption -> DoS / RCE
- DoS via an attacker forging a zero length UDP packet in response to a query - then cause the resolver to shutdown the “connection” as it sees a 0 byte read - however that code path assumes the transport protocol is TCP - this is not a valid assumption for UDP as UDP is connectionless
[USN-6165-1] GLib vulnerabilities (11:07)
- 7 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- Various issues in the handling of GVariants - looks like someone has been fuzzing glib - GVariant used for on-the-wire encoding of parameters in DBus etc - similar to protobuf’s etc
[USN-6166-1] libcap2 vulnerabilities (11:35)
- 2 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- DoS via a memory leak through thread creation plus an integer overflow when handling really large strings
Goings on in Ubuntu Security Community
Google disables io_uring in ChromeOS and their production servers (12:00)
- https://security.googleblog.com/2023/06/learnings-from-kctf-vrps-42-linux.html
- Google runs kCTF as part of the vuln rewards program, offering a bug-bounty / monetary rewards for researchers who find exploitable bugs in Google Kubernetes Engine (GKE) or the underlying Linux kernel
- Has paid out $1.8m USD - 60% of submissions exploited
io_uring- with around $1m USD rewarded forio_uringsubmissions alone - andio_uringwas used in all submissions which bypassed their mitigations- followed by net and then fs subsystems
- clearly is a target rich environment
- As such, disabled
io_uringin ChromeOS (was originally enabled back in November 2022 to increase performance of theirarcvmwhich is used to run Android apps on ChromeOS) but then now disabled 4 months later in Feb this year - Use seccomp-bpf to block access to
io_uringto Android applications and in the future will also use SELinux to restrict access even further to only select system processes - Will likely disable it also on GKE AutoPilot - where Google manages the config of your GKE Kubernetes cluster
- And have disabled
io_uringon their production servers - Essentially due to the newness of
io_uringand ongoing development of features for it, it presents too much of a risk for use by untrusted applications etc
Andrei discusses Fuzzing Configurations of Program Options (15:06)
- https://doi.org/10.1145/3580597
- https://google.github.io/fuzzbench/
- https://github.com/google/AFL
- https://github.com/AFLplusplus/AFLplusplus
- https://llvm.org/docs/CommandGuide/llvm-cov.html
- https://github.com/google/AFL/tree/master/experimental/argv_fuzzing
- https://github.com/AFLplusplus/AFLplusplus/tree/stable/utils/argv_fuzzing
Get in contact
00:00
-00:00